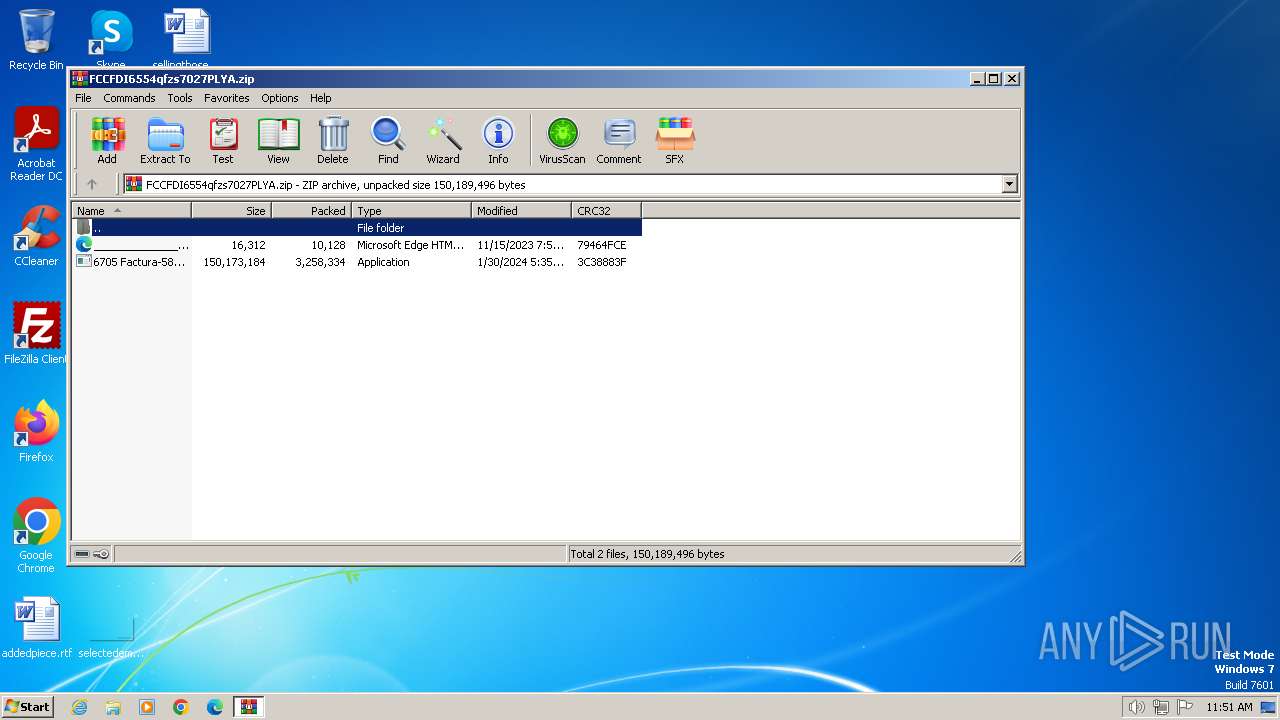
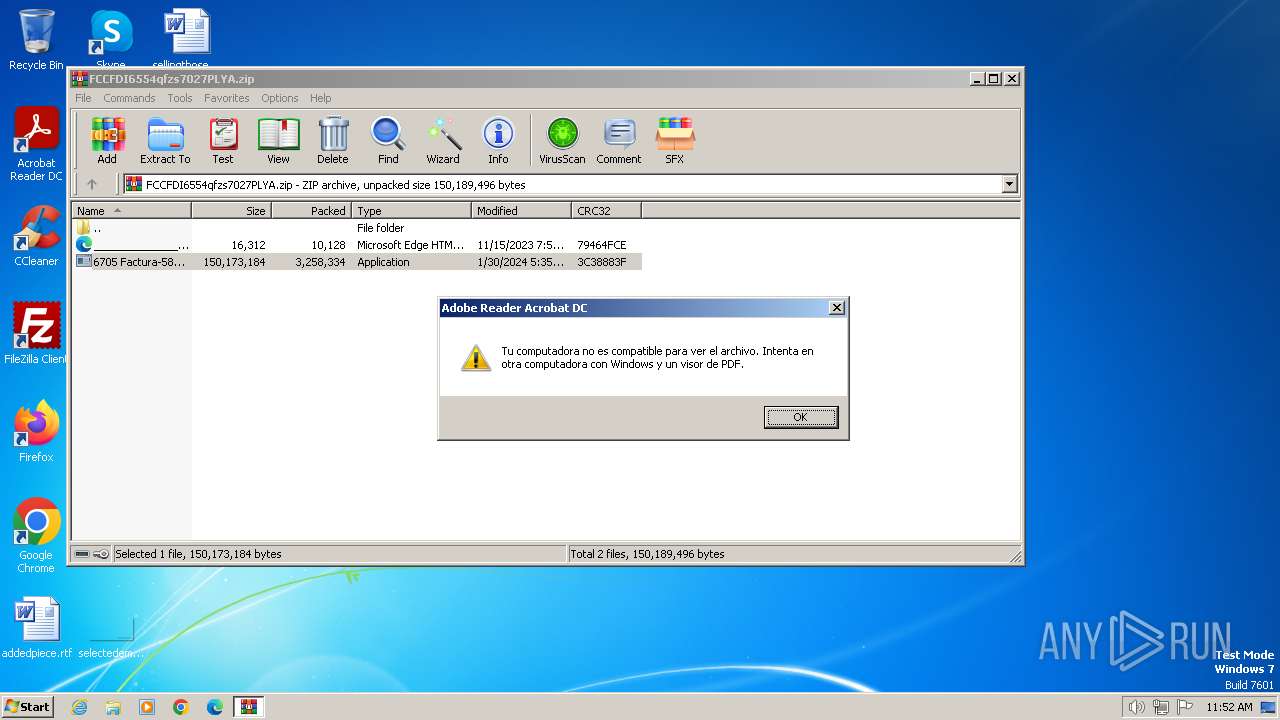
| File name: | FCCFDI6554qfzs7027PLYA.zip |
| Full analysis: | https://app.any.run/tasks/33515d22-ac7a-4ad6-bb0c-e2e53b37b4cf |
| Verdict: | Malicious activity |
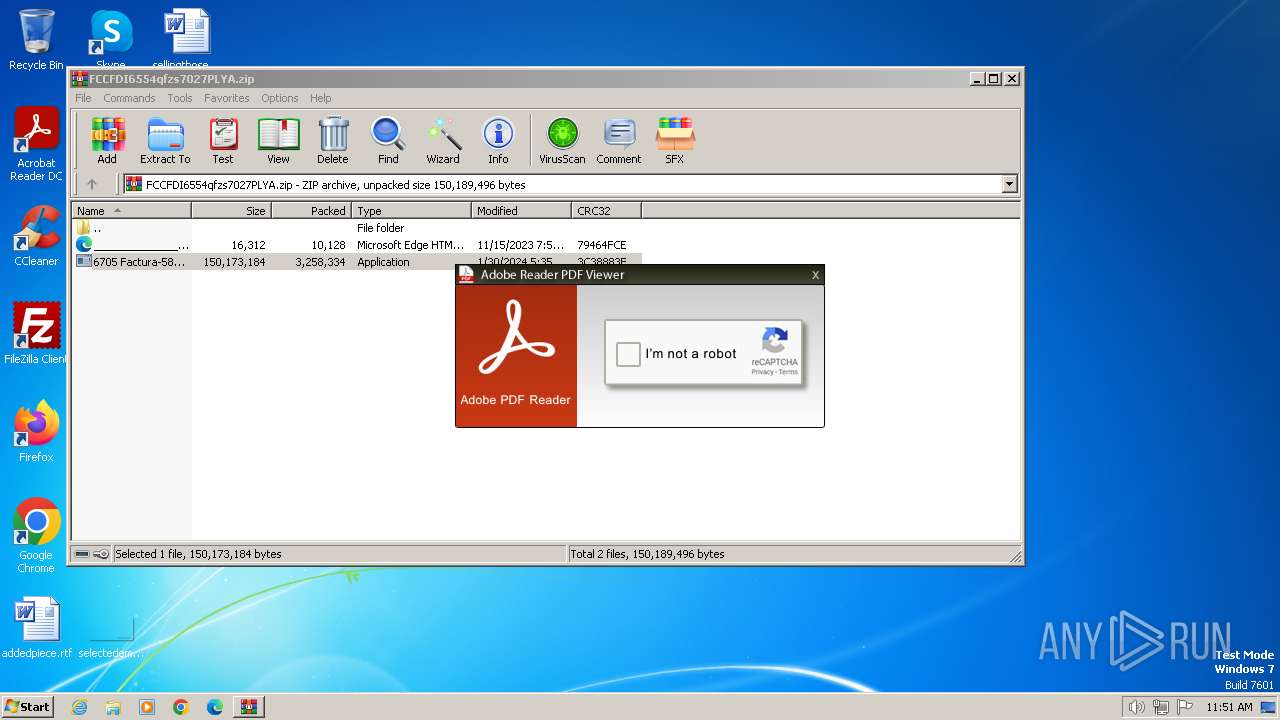
| Threats: | Grandoreiro is a Latin American banking trojan first observed in 2016. It targets mostly Spanish-speaking countries, such as Brazil, Spain, Mexico and Peru. This malware is operated as a Malware-as-a-Service (MaaS), which makes it easily accessible for cybercriminals. Besides, it uses advanced techniques to evade detection. |
| Analysis date: | January 31, 2024, 11:51:03 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | BBD3EC1668EC8AEE698882FAD1C1A8C7 |
| SHA1: | 350D1C6D9BCF80BE55C867FDCF88CB4987DE593F |
| SHA256: | B974EC92FBEFA68E90314E9DBFBDF1135B4C89DF5CD3A2BB283825B1C95F6B3A |
| SSDEEP: | 98304:0SmjdMaf85h6SHbIpP1IE4Ie8LOsKl5YU5STQ2+OEYN33A6gWI2b0v1IWvwQdbSt:QOj98dAOJ |
MALICIOUS
Actions looks like stealing of personal data
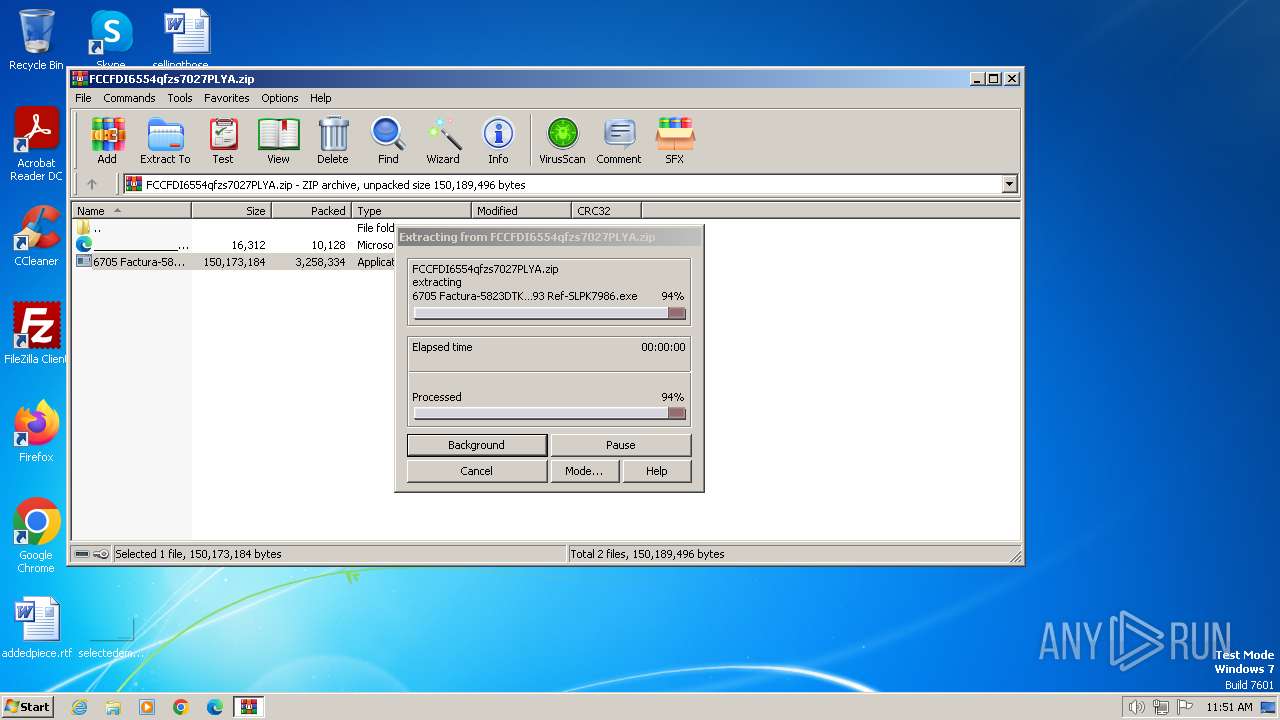
- 6705 Factura-5823DTKN Serie A-4785 Folio VYCV9093 Ref-SLPK7986.exe (PID: 548)
GRANDOREIRO has been detected (SURICATA)
- 6705 Factura-5823DTKN Serie A-4785 Folio VYCV9093 Ref-SLPK7986.exe (PID: 548)
Drops the executable file immediately after the start
- 6705 Factura-5823DTKN Serie A-4785 Folio VYCV9093 Ref-SLPK7986.exe (PID: 548)
SUSPICIOUS
Checks for external IP
- 6705 Factura-5823DTKN Serie A-4785 Folio VYCV9093 Ref-SLPK7986.exe (PID: 548)
Executable content was dropped or overwritten
- 6705 Factura-5823DTKN Serie A-4785 Folio VYCV9093 Ref-SLPK7986.exe (PID: 548)
Process drops legitimate windows executable
- 6705 Factura-5823DTKN Serie A-4785 Folio VYCV9093 Ref-SLPK7986.exe (PID: 548)
Reads the Internet Settings
- 6705 Factura-5823DTKN Serie A-4785 Folio VYCV9093 Ref-SLPK7986.exe (PID: 548)
Reads settings of System Certificates
- 6705 Factura-5823DTKN Serie A-4785 Folio VYCV9093 Ref-SLPK7986.exe (PID: 548)
Connects to unusual port
- 6705 Factura-5823DTKN Serie A-4785 Folio VYCV9093 Ref-SLPK7986.exe (PID: 548)
Drops a system driver (possible attempt to evade defenses)
- 6705 Factura-5823DTKN Serie A-4785 Folio VYCV9093 Ref-SLPK7986.exe (PID: 548)
INFO
Drops the executable file immediately after the start
- WinRAR.exe (PID: 1652)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 1652)
Reads CPU info
- 6705 Factura-5823DTKN Serie A-4785 Folio VYCV9093 Ref-SLPK7986.exe (PID: 548)
- DriverSearchExpertdldDriverBoostManager.exe (PID: 2380)
Reads the computer name
- 6705 Factura-5823DTKN Serie A-4785 Folio VYCV9093 Ref-SLPK7986.exe (PID: 548)
- DriverSearchExpertdldDriverBoostManager.exe (PID: 2380)
Reads the machine GUID from the registry
- 6705 Factura-5823DTKN Serie A-4785 Folio VYCV9093 Ref-SLPK7986.exe (PID: 548)
Checks supported languages
- 6705 Factura-5823DTKN Serie A-4785 Folio VYCV9093 Ref-SLPK7986.exe (PID: 548)
- DriverSearchExpertdldDriverBoostManager.exe (PID: 2380)
Creates files in the program directory
- 6705 Factura-5823DTKN Serie A-4785 Folio VYCV9093 Ref-SLPK7986.exe (PID: 548)
- DriverSearchExpertdldDriverBoostManager.exe (PID: 2380)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2024:01:30 17:35:14 |
| ZipCRC: | 0x3c38883f |
| ZipCompressedSize: | 3258334 |
| ZipUncompressedSize: | 150173184 |
| ZipFileName: | 6705 Factura-5823DTKN Serie A-4785 Folio VYCV9093 Ref-SLPK7986.exe |
Total processes
38
Monitored processes
3
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 548 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa1652.36156\6705 Factura-5823DTKN Serie A-4785 Folio VYCV9093 Ref-SLPK7986.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa1652.36156\6705 Factura-5823DTKN Serie A-4785 Folio VYCV9093 Ref-SLPK7986.exe | WinRAR.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: Pdf Storage Synchroniza (JIDOCPS) Exit code: 0 Version: 6.8703.12.7 Modules
| |||||||||||||||
| 1652 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\FCCFDI6554qfzs7027PLYA.zip" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 2380 | "C:\ProgramData\TotalDriverUtilitywcateDriverCheckElite\DriverSearchExpertdldDriverBoostManager.exe" | C:\ProgramData\TotalDriverUtilitywcateDriverCheckElite\DriverSearchExpertdldDriverBoostManager.exe | — | 6705 Factura-5823DTKN Serie A-4785 Folio VYCV9093 Ref-SLPK7986.exe | |||||||||||
User: admin Company: Advanced Micro Devices, Inc. Integrity Level: MEDIUM Description: Radeon Settings: Host Service Exit code: 0 Version: 4.10.7.1964 Modules
| |||||||||||||||
Total events
5 236
Read events
5 196
Write events
40
Delete events
0
Modification events
| (PID) Process: | (1652) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (1652) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (1652) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (1652) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (1652) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\curl-8.5.0_1-win32-mingw.zip | |||
| (PID) Process: | (1652) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (1652) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (1652) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (1652) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (1652) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
74
Suspicious files
0
Text files
1
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1652 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa1652.36156\6705 Factura-5823DTKN Serie A-4785 Folio VYCV9093 Ref-SLPK7986.exe | — | |
MD5:— | SHA256:— | |||
| 548 | 6705 Factura-5823DTKN Serie A-4785 Folio VYCV9093 Ref-SLPK7986.exe | C:\ProgramData\TotalDriverUtilitywcateDriverCheckElite\NlsASnzyJhc | — | |
MD5:— | SHA256:— | |||
| 548 | 6705 Factura-5823DTKN Serie A-4785 Folio VYCV9093 Ref-SLPK7986.exe | C:\ProgramData\TotalDriverUtilitywcateDriverCheckElite\ZaKyslyS.exe | — | |
MD5:— | SHA256:— | |||
| 548 | 6705 Factura-5823DTKN Serie A-4785 Folio VYCV9093 Ref-SLPK7986.exe | C:\ProgramData\TotalDriverUtilitywcateDriverCheckElite\AcpiDev.sys | executable | |
MD5:1BA19D7AF3DCB34F4EF12A8EAD1521BD | SHA256:E4C5495E2619E67E4EFA171D072079AE27C732C1180327B0630BCCDCD9E5476D | |||
| 548 | 6705 Factura-5823DTKN Serie A-4785 Folio VYCV9093 Ref-SLPK7986.exe | C:\ProgramData\TotalDriverUtilitywcateDriverCheckElite\acpipmi.sys | executable | |
MD5:83ADAC8EC1C54A24ED4AABD39C3175E2 | SHA256:85A809079C64AA7160ADB1C423BA1FE89D7650879E5E9CADC74A1E9C52E596FB | |||
| 1652 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa1652.36156\_________________________________________________________________________8495COXH9193NXEL.xml | executable | |
MD5:4A77FB2014F6D9A165A139BD550916AE | SHA256:F2D850025DD7B65C44D979EC74A3F5A77E1C15B4070812BE5656887CEE95DC59 | |||
| 548 | 6705 Factura-5823DTKN Serie A-4785 Folio VYCV9093 Ref-SLPK7986.exe | C:\ProgramData\TotalDriverUtilitywcateDriverCheckElite\amdgpio2.sys | executable | |
MD5:55578CF027B0AE9F0D653B209C9F1B6D | SHA256:46A53925BAA34FA9D87E7C3157504A4557D81CD8B8608E7AB6CAF02F482F7792 | |||
| 548 | 6705 Factura-5823DTKN Serie A-4785 Folio VYCV9093 Ref-SLPK7986.exe | C:\ProgramData\TotalDriverUtilitywcateDriverCheckElite\acpitime.sys | executable | |
MD5:1E3AA6E71FC72290352E415B0F99ED44 | SHA256:35ECCB1C8E3039B07DE3B0DA58BFEAC7F77EF87E0724221A12F93E4C9F85D743 | |||
| 548 | 6705 Factura-5823DTKN Serie A-4785 Folio VYCV9093 Ref-SLPK7986.exe | C:\ProgramData\TotalDriverUtilitywcateDriverCheckElite\CtaChildDriver.sys | executable | |
MD5:938C59B39A27AA9370B95D00D4611518 | SHA256:EB10E049F68359747B6EE1259B8745059A66D859A6B30DAD92F338605DCCE38E | |||
| 548 | 6705 Factura-5823DTKN Serie A-4785 Folio VYCV9093 Ref-SLPK7986.exe | C:\ProgramData\TotalDriverUtilitywcateDriverCheckElite\bcmfn2.sys | executable | |
MD5:739D089777D2B66DBE7201E5EA4BA2D7 | SHA256:9AD12E18A042C5B8EFB19297BC2E7BD1FEF75A138FEFB64C6BF0261FD3E53AB1 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
9
TCP/UDP connections
14
DNS requests
2
Threats
26
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
548 | 6705 Factura-5823DTKN Serie A-4785 Folio VYCV9093 Ref-SLPK7986.exe | GET | 200 | 208.95.112.1:80 | http://ip-api.com/json | unknown | binary | 312 b | unknown |
548 | 6705 Factura-5823DTKN Serie A-4785 Folio VYCV9093 Ref-SLPK7986.exe | GET | 200 | 208.95.112.1:80 | http://ip-api.com/json | unknown | binary | 312 b | unknown |
548 | 6705 Factura-5823DTKN Serie A-4785 Folio VYCV9093 Ref-SLPK7986.exe | GET | 200 | 208.95.112.1:80 | http://ip-api.com/json | unknown | binary | 312 b | unknown |
548 | 6705 Factura-5823DTKN Serie A-4785 Folio VYCV9093 Ref-SLPK7986.exe | GET | 200 | 208.95.112.1:80 | http://ip-api.com/json | unknown | binary | 312 b | unknown |
548 | 6705 Factura-5823DTKN Serie A-4785 Folio VYCV9093 Ref-SLPK7986.exe | GET | 200 | 15.228.255.38:4917 | http://15.228.255.38:4917/C@P*%25,XGGCGWV$CP*XU%25C,SU)@UCPG@%25P$@$%25)SS$)U%25CGVS$SQWP,%25WWGGGS)P)PTCG**TVW%25@,Q@*QT$*USVPUPU%25WW,SQ$SX$W$%25P*$X@VQ*@SSP)%25@QG$%25U*$)W%25@)STC,@PQGPQ,PXPG%25*,WS)GG%25T@QUPP)V),QQ,GX*V,*TVPS,,WQUPGPP@G%25)TGWWS$,)UV$QSC%25$US$CUP$@SU*%25WSWPG$,UUVP%25CQPS*GV)P,@CSX@GPTQ*PC)UTWWC),))%25*@XVT*TTC%25CXGG@PQ)CS*,WW%25S))))S)$G$W$%25QW*VG,V)GCVVVG%25CX@,*PQGPG$PTXV*$XQ)CTCU)QQWPGC*W)%25STQ%25TQW$VQC$TX*WXV%25,@UPPQ%25XS$PW$@ST$,X)W%25T)WQTGT$)PV)PV,CTVW)WQV@@X)T%25%25UX$,G*,UXUT*),VW,CG*,SWG*GU,%25W)%25XVVP%25)TCG)XVG@$STPGG,WV*,CU%25$TU%25)PQ$CG*XTGSS,STCXCTU*TVCPS$XWCVQ%25V%25VWU@%25GX%25*Q@,%25W)W$,)Q)*XU%25*CX@Q)P)UP@$SW$XQC*)TPVS,*TQUU$SSVCW)WUX$PQ%25,)S)$*X)%25SSTP*%25*UXCXGQ)%25V@*VXSWVQ*$*G*,)QU,UT@S%25CP)SWSX)*@XSWW)QGUWGGWWQSPP$PC$QQ@CPVC%25*QG$VQ@P$S,$XQP$QS$WU),TX@UV,XTUTG*SSG$%25TC*@X%25QCP*W,VP*$TPS,,XT)%25TXUQC,$TPTWV*@*G*W)WSXXS,$)TU@QP@@V,@QS,WX)XGW$W*QCCT,@Q$%25XW)GQC*V$C)*SWPVC,ST)WWTWGC$SX$W*%25T%25XGUPX@U))XVGTCXP)CXV$SQ@@,%25,Q*P@$)U@CV | unknown | text | 838 b | unknown |
548 | 6705 Factura-5823DTKN Serie A-4785 Folio VYCV9093 Ref-SLPK7986.exe | GET | 200 | 15.228.255.38:4917 | http://15.228.255.38:4917/V%25%25UXXW,*XSC$Q,,*S$CCVC%25$TUX$%25WP,CS,*Q,,WX@UQCWPT$@T@V@@*S$C*,$X@X,QS$)X)QVCPGP%25WQ$CVPVPWPX*VXCXCGCWXG*PPCPGUWG%25$W%25C%25SW%25%25UQ,$XWT*%25UXGTVX@G$)SUGPVPQ$UUW$QSUWWQGCS@GSG*UQ*,PX)WGSP,%25UG,*TVW@V)$CWT@CW%25*VT)W)GCVPCX@QCTP),%25X$SS*PUQCX,QWV*TV*),QG)@VP%25CT@*S)TUW,,SW$@UX$XQP$VTP%25,QVC%25%25GSXP%25PVCX*STWU,*GU$CW%25G)Q)@WP)PUTG%25Q$,TXPV@%25UXWGT)GTT)CW$%25*GQ,*GWTQW%25@Q@T%25CQSP,$SSV%25%25STPS$W,S*$WTGXWS%25C@%25*QGPSPS)SV%25PTCCVS,GQS%25@WPS,PS)W@G$)V,*QQ*P))CQVC)*CV@$XUP@P*GXSQ)C)GWSC%25PXVV$%25V*GU*%25Q,VXCTCWCGC*GUP)P),T)W$%25$SC@X%25@WSW,CXV@$VGQ%25VXXQP$XT$GU@*%25*WC)VSG$,UC@XS%25%25GUP,TX$V%25*)Q@*)PC$T%25G%25%25WVTCVWTXXX*V%25$)UX)Q@$@%25VS@USS**TVXXTUWT@PX$%25T@UW*)UPQP@$T%25PCT)GS$PX,QV$SSGCWS*$QX,WQWQGV)WTUXGQW,GU@PCCXCT*PT*%25S@,@QVG,@U%25C,S*C,,*U%CC$)XSU@%25XUWPTP%25CVCC@QVC%25G@GG*%25W*VUXCG$%25V%25%25%25XQG$P@@XS@CWP)%25%25XSU$)*QTCC*UQ*CW,CQUVUTSWVGT%25)T%25G@G*)%25TXQS$TG%25)*UP**UP%25VT$UG$CQ$P$CUPCC@V$XU@@),@TV))UG@WG%25,TXXWX%25XVPCTC*,QQGPG)CW)GW@P)T@,Q)@SWCV$CWPG$VXUUT@X@U@*WGXTXXQW$CU%25,XVQ%25@SVC*,TQ)$X%CCS@)VQ@UPVP%25),@U%25,X%25WVWC%25G@$UW$VX*)X@P*)UV,GXWXPUC,GSCCXVTG,%25S%25SVV$TX)VU)UVQ*)SP$)TGGC$)Q@CG)WSXVC$CQQC$*%25Q$,VUTP@$@W%25GQ,%25UG,@QPTG%25*TTSP*SSW,WQUTQS)P%25*%25WPQSW*,%25QG,PX)XSW,%25*X%25SSP*S,,TXGQG,WU,%25UGX,XT$X,VW@XW$SX)QTTV*)%25TS*UUC@CSV,UVV$PVW,$TQ)G*)T$*)T)@$VP)GVG@S,,TCGPGQ*TQ@CT$*TGS,P@CQPCSX$,XVXPX@VVP*CUCXC*)G))T%25U**WSP)GT%25GV%25GS)PSC$,XQ$C@PP | unknown | html | 83 b | unknown |
548 | 6705 Factura-5823DTKN Serie A-4785 Folio VYCV9093 Ref-SLPK7986.exe | GET | 200 | 15.228.255.38:157 | http://15.228.255.38:157/)P@)WV%25WU*PS%25)@GWU@Q%25XUX@XVP*,TWG,WSU*$TV*)XVWXGGWVGS@$GU%25QGSVU,SQ@CC)UV$)PQG,,XCWCW@T,U%25PQ*,UGCUVPGT%25%25TPWP@QCXS*CCGW%25S))VTG@$%25TP%25WX%25T)TGWXSV,*XTXSUQ$VUG*GC,,$WQGW,*UXPS*XQGC)*XQGPC$UT,WXVT$UT$@UW,*WTCW*G)V@CW@VCGPC,,X*SU*@UX,@G)$XWVGGSVP,P*CQC)WP%25U@GVVG%25P$PU,VU**VV),WTS*@X)Q%25$PSG*$Q%25$TX,UW,$T)W,@$C@PQ**UQ@%25$)W$WT%25CXPXSV$PQ,,Q%25,WUQP@$WWP$VQ)$TQP,UX,GC)WCT)T@$)UQ%25CQSC)X@$S,$SQPCQ%25TU$,TGP,XUU@@)WS@$PS,*GWTVU,,XVTSQS$SU,%25QQ*C)VQ$CUP,VQ*$VW$SPCC%25UU,*XGPWC@VW,WSUXCC,@%25XQ*$*X,TVGQ*QTCT$))V,,,UPPG,*XWVCP)VT$W)%25CXUQG$STPG%25@P%25QWQVC%25UQS%25GUU)QQVCPPT,,Q%25$)V@G)WPT%25GP%25XS**)UT%25S@V)TWGWXS%25PW$GQTCC$)GC%25TQP*VQWU%25*UU%25)V)VT@VX$CU,$*G*XVWQWCGW%25U@GGSCW*GT,)TVG,*Q,,%25U)*$U@$CT))SVS*%25QW,$XVW,GUW$*)XSS@$%25GG$VTVSQ$QV,*QG$CX)Q@CUCCCV@GV%25%25Q@VGW*UWW@UV)GVPS$GW$*VQW%25$QCPW@*GUC$%25*UUP%25CS*UVC%25%25GCG*UC%25USX%25XV%25C@PCPT*%25GWC,)VC,,WU)CSV,)WTXUSP*SX@@S*PTC%25CS@T)*QQ,WU$*WVQ,PXXGQC%25))Q%25P$SU,WXGTVXCGPSU%25*GVW**SQXPV*CXWQSPW$SUCCPCTCPVU$WWQ*SQ$SX%25TSTCWTGTG@V,PTPU@X,%25T,TGSCC,*QV)%25TT%25)CS@CT@V@,@U@)),%25VSGCQ,$XP)W*CXXUWP$PQVQ,VQTPQ@WS*,TX%25S%25P,ST$TTVW*%25%25QXCW@XPVCC*CUG@P)TWSWX@WC**UU@$VGVWS**QGC,@QC),@QU,*XCX)W%25W%25SQ$TXWWU$%25)X)V%25%25))UV@*GSC)TGCW**$X%25WSSUCXP$*WT@GC,)U)CS%25$XUQ@,VWXSXCQW*%25GQQPX),Q%25%25SVGSW$SWWQ*CW,CSWGXSS,*XUTC@PW*GG%25USP,@Q*CV*TVC)WUWP)SW%25%25W@TCXTWT),W)*CXGGX,SX$STX@VT$PTS)%25UQPQ@VVC$%25XWXTQ%25$Q | unknown | text | 50 b | unknown |
548 | 6705 Factura-5823DTKN Serie A-4785 Folio VYCV9093 Ref-SLPK7986.exe | GET | 200 | 208.95.112.1:80 | http://ip-api.com/json | unknown | binary | 312 b | unknown |
548 | 6705 Factura-5823DTKN Serie A-4785 Folio VYCV9093 Ref-SLPK7986.exe | GET | 200 | 15.228.255.38:50814 | http://15.228.255.38:50814/ZaKyslyS.xml | unknown | binary | 6.25 Mb | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
548 | 6705 Factura-5823DTKN Serie A-4785 Folio VYCV9093 Ref-SLPK7986.exe | 208.95.112.1:80 | ip-api.com | TUT-AS | US | unknown |
548 | 6705 Factura-5823DTKN Serie A-4785 Folio VYCV9093 Ref-SLPK7986.exe | 8.8.8.8:443 | dns.google | GOOGLE | US | unknown |
548 | 6705 Factura-5823DTKN Serie A-4785 Folio VYCV9093 Ref-SLPK7986.exe | 15.228.255.38:4917 | — | AMAZON-02 | BR | unknown |
548 | 6705 Factura-5823DTKN Serie A-4785 Folio VYCV9093 Ref-SLPK7986.exe | 15.228.255.38:50814 | — | AMAZON-02 | BR | unknown |
548 | 6705 Factura-5823DTKN Serie A-4785 Folio VYCV9093 Ref-SLPK7986.exe | 15.228.255.38:157 | — | AMAZON-02 | BR | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
ip-api.com |
| shared |
dns.google |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
548 | 6705 Factura-5823DTKN Serie A-4785 Folio VYCV9093 Ref-SLPK7986.exe | A Network Trojan was detected | ET USER_AGENTS Suspicious User-Agent (Clever Internet Suite) |
548 | 6705 Factura-5823DTKN Serie A-4785 Folio VYCV9093 Ref-SLPK7986.exe | Potential Corporate Privacy Violation | AV POLICY Internal Host Retrieving External IP Address (ip-api. com) |
548 | 6705 Factura-5823DTKN Serie A-4785 Folio VYCV9093 Ref-SLPK7986.exe | Device Retrieving External IP Address Detected | ET POLICY External IP Lookup ip-api.com |
548 | 6705 Factura-5823DTKN Serie A-4785 Folio VYCV9093 Ref-SLPK7986.exe | A Network Trojan was detected | ET USER_AGENTS Suspicious User-Agent (Clever Internet Suite) |
548 | 6705 Factura-5823DTKN Serie A-4785 Folio VYCV9093 Ref-SLPK7986.exe | Potential Corporate Privacy Violation | AV POLICY Internal Host Retrieving External IP Address (ip-api. com) |
548 | 6705 Factura-5823DTKN Serie A-4785 Folio VYCV9093 Ref-SLPK7986.exe | Device Retrieving External IP Address Detected | ET POLICY External IP Lookup ip-api.com |
548 | 6705 Factura-5823DTKN Serie A-4785 Folio VYCV9093 Ref-SLPK7986.exe | A Network Trojan was detected | ET USER_AGENTS Suspicious User-Agent (Clever Internet Suite) |
548 | 6705 Factura-5823DTKN Serie A-4785 Folio VYCV9093 Ref-SLPK7986.exe | Potential Corporate Privacy Violation | AV POLICY Internal Host Retrieving External IP Address (ip-api. com) |
548 | 6705 Factura-5823DTKN Serie A-4785 Folio VYCV9093 Ref-SLPK7986.exe | Device Retrieving External IP Address Detected | ET POLICY External IP Lookup ip-api.com |
548 | 6705 Factura-5823DTKN Serie A-4785 Folio VYCV9093 Ref-SLPK7986.exe | A Network Trojan was detected | ET USER_AGENTS Suspicious User-Agent (Clever Internet Suite) |