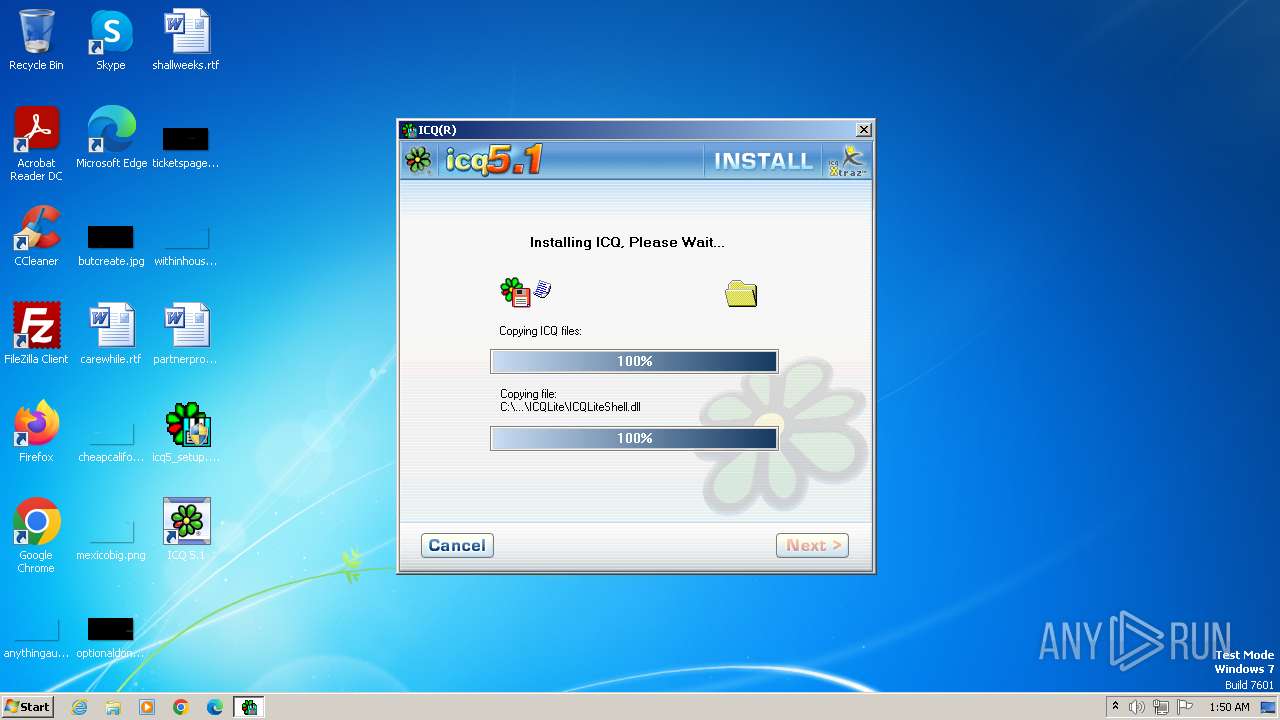
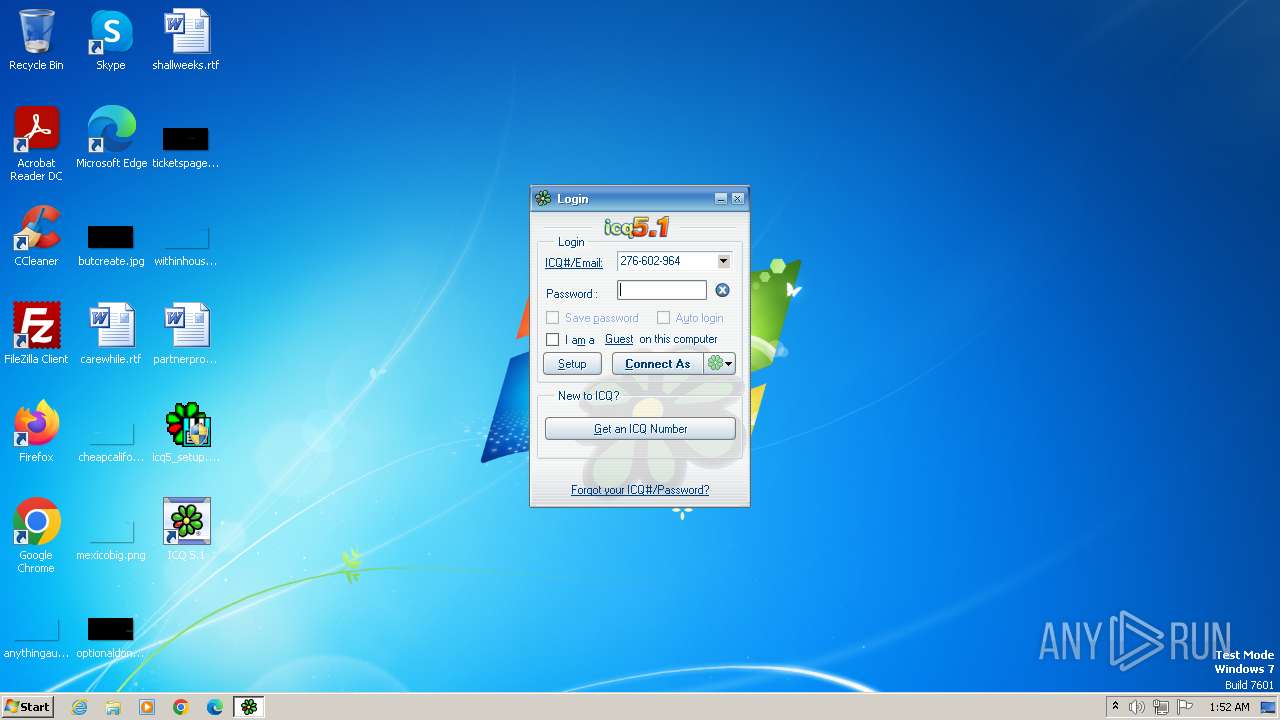
| File name: | icq5_setup.exe |
| Full analysis: | https://app.any.run/tasks/0293c2f3-fa30-451f-8951-fbc5fec426d3 |
| Verdict: | Malicious activity |
| Analysis date: | December 10, 2023, 01:48:14 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | D84469DED4FB838A5839E05829A3304A |
| SHA1: | 0BC5DCCB71ACFDF24938D3603C711E91390DCD66 |
| SHA256: | B95AC09730D2F1959E9E758D992AE869DB453040AC3ED4952724E0117F915359 |
| SSDEEP: | 98304:aRipgNCh0rxPkhYiOrUGQTAau6AP1N7bMC3TQnsPCU83qPILd7FZD7XaahOunPG1:r2sJGjj |
MALICIOUS
Drops the executable file immediately after the start
- icq5_setup.exe (PID: 1352)
- GLBFF44.tmp (PID: 1840)
Actions looks like stealing of personal data
- GLBFF44.tmp (PID: 1840)
SUSPICIOUS
Starts application with an unusual extension
- icq5_setup.exe (PID: 1352)
- GLBFF44.tmp (PID: 1840)
Reads the Internet Settings
- GLBFF44.tmp (PID: 1840)
- ICQInstall.exe (PID: 1988)
- ICQInstall.exe (PID: 2520)
- ICQInstall.exe (PID: 3228)
- ICQLite.exe (PID: 3576)
Searches for installed software
- GLBFF44.tmp (PID: 1840)
Process drops legitimate windows executable
- GLBFF44.tmp (PID: 1840)
The process creates files with name similar to system file names
- GLBFF44.tmp (PID: 1840)
The process drops C-runtime libraries
- GLBFF44.tmp (PID: 1840)
Creates a software uninstall entry
- GLBFF44.tmp (PID: 1840)
Creates/Modifies COM task schedule object
- GLJFF83.tmp (PID: 2972)
Reads security settings of Internet Explorer
- ICQLite.exe (PID: 3576)
Reads Internet Explorer settings
- ICQLite.exe (PID: 3576)
Checks Windows Trust Settings
- ICQLite.exe (PID: 3576)
Reads settings of System Certificates
- ICQLite.exe (PID: 3576)
Reads Microsoft Outlook installation path
- ICQLite.exe (PID: 3576)
Connects to unusual port
- ICQLite.exe (PID: 3576)
INFO
Checks supported languages
- icq5_setup.exe (PID: 1352)
- GLBFF44.tmp (PID: 1840)
- ICQInstall.exe (PID: 1988)
- wmpnscfg.exe (PID: 240)
- ICQInstall.exe (PID: 2520)
- ICQLiteDBConverter.exe (PID: 3092)
- GLJFF83.tmp (PID: 3492)
- GLJFF83.tmp (PID: 3340)
- GLJFF83.tmp (PID: 1872)
- ICQInstall.exe (PID: 3228)
- ICQLite.exe (PID: 3576)
- GLJFF83.tmp (PID: 2972)
- GLJFF83.tmp (PID: 3944)
- GLJFF83.tmp (PID: 4000)
- GLJFF83.tmp (PID: 3556)
- ICQLite.exe (PID: 280)
- ICQLite.exe (PID: 2860)
- ICQLite.exe (PID: 1860)
- ICQLiteDBConverter.exe (PID: 1328)
- ICQLite.exe (PID: 2224)
Reads the computer name
- GLBFF44.tmp (PID: 1840)
- ICQInstall.exe (PID: 1988)
- wmpnscfg.exe (PID: 240)
- ICQInstall.exe (PID: 2520)
- ICQInstall.exe (PID: 3228)
- ICQLite.exe (PID: 3576)
- GLJFF83.tmp (PID: 4000)
- GLJFF83.tmp (PID: 3340)
- GLJFF83.tmp (PID: 3944)
- GLJFF83.tmp (PID: 1872)
- ICQLite.exe (PID: 280)
- GLJFF83.tmp (PID: 2972)
- ICQLite.exe (PID: 2860)
- ICQLite.exe (PID: 1860)
- ICQLiteDBConverter.exe (PID: 1328)
Create files in a temporary directory
- GLBFF44.tmp (PID: 1840)
- icq5_setup.exe (PID: 1352)
- ICQLite.exe (PID: 3576)
- ICQLiteDBConverter.exe (PID: 1328)
Creates files in the program directory
- GLBFF44.tmp (PID: 1840)
Checks proxy server information
- ICQInstall.exe (PID: 1988)
- ICQInstall.exe (PID: 2520)
- ICQInstall.exe (PID: 3228)
- ICQLite.exe (PID: 3576)
Reads the machine GUID from the registry
- ICQInstall.exe (PID: 1988)
- ICQInstall.exe (PID: 2520)
- ICQInstall.exe (PID: 3228)
- ICQLite.exe (PID: 3576)
- GLJFF83.tmp (PID: 2972)
- ICQLite.exe (PID: 2860)
- ICQLite.exe (PID: 1860)
- ICQLite.exe (PID: 280)
- ICQLiteDBConverter.exe (PID: 1328)
Manual execution by a user
- wmpnscfg.exe (PID: 240)
- ICQLite.exe (PID: 1860)
Application launched itself
- iexplore.exe (PID: 3440)
Reads CPU info
- ICQLite.exe (PID: 3576)
Creates files or folders in the user directory
- ICQLite.exe (PID: 3576)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Wise Installer executable (91.7) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (5.3) |
| .dll | | | Win32 Dynamic Link Library (generic) (1.2) |
| .exe | | | Win32 Executable (generic) (0.8) |
| .exe | | | Generic Win/DOS Executable (0.3) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 1999:04:08 22:24:47+02:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 512 |
| InitializedDataSize: | 6057984 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x1000 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.0.0.0 |
| ProductVersionNumber: | 1.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Windows 16-bit |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Windows, Latin1 |
| CompanyName: | ICQ Ltd. |
| FileDescription: | ICQ(R) |
| FileVersion: | - |
| LegalCopyright: | ICQ Ltd. |
Total processes
77
Monitored processes
23
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 240 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 280 | C:\PROGRA~1\ICQLite\ICQLite.exe -Embedding | C:\Program Files\ICQLite\ICQLite.exe | — | svchost.exe | |||||||||||
User: admin Company: ICQ Ltd. Integrity Level: MEDIUM Description: ICQLite Exit code: 0 Version: 20, 52, 2573, 0 Modules
| |||||||||||||||
| 1328 | C:\PROGRA~1\ICQLite\ICQLIT~2.EXE -Embedding | C:\Program Files\ICQLite\ICQLiteDBConverter.exe | svchost.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: ICQLiteDBConverter MFC Application Exit code: 0 Version: 20, 52, 2573, 0 Modules
| |||||||||||||||
| 1352 | "C:\Users\admin\Desktop\icq5_setup.exe" | C:\Users\admin\Desktop\icq5_setup.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 1840 | C:\Users\admin\AppData\Local\Temp\GLBFF44.tmp 4736 C:\Users\admin\Desktop\ICQ5_S~1.EXE | C:\Users\admin\AppData\Local\Temp\GLBFF44.tmp | icq5_setup.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 1860 | "C:\Program Files\ICQLite\ICQLite.exe" | C:\Program Files\ICQLite\ICQLite.exe | explorer.exe | ||||||||||||
User: admin Company: ICQ Ltd. Integrity Level: HIGH Description: ICQLite Exit code: 0 Version: 20, 52, 2573, 0 Modules
| |||||||||||||||
| 1872 | "C:\Users\admin\AppData\Local\Temp\GLJFF83.tmp" C:\Program Files\ICQLite\ICQLiteShell.dll | C:\Users\admin\AppData\Local\Temp\GLJFF83.tmp | — | GLBFF44.tmp | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 1988 | "C:\Users\admin\AppData\Local\Temp\ICQINS~1.EXE" STPARAM=0 2052-1085-3000 | C:\Users\admin\AppData\Local\Temp\ICQInstall.exe | GLBFF44.tmp | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 1996 | "C:\Users\admin\Desktop\icq5_setup.exe" | C:\Users\admin\Desktop\icq5_setup.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 2224 | "C:\PROGRA~1\ICQLite\ICQLite.exe" -RegServer | C:\Program Files\ICQLite\ICQLite.exe | — | GLBFF44.tmp | |||||||||||
User: admin Company: ICQ Ltd. Integrity Level: HIGH Description: ICQLite Exit code: 0 Version: 20, 52, 2573, 0 Modules
| |||||||||||||||
Total events
17 623
Read events
17 359
Write events
257
Delete events
7
Modification events
| (PID) Process: | (1840) GLBFF44.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (1840) GLBFF44.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (1840) GLBFF44.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (1840) GLBFF44.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (1988) ICQInstall.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (1988) ICQInstall.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 460000005A010000090000000000000000000000000000000400000000000000C0E333BBEAB1D3010000000000000000000000000100000002000000C0A8016B000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (1988) ICQInstall.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (1988) ICQInstall.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (1988) ICQInstall.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (1988) ICQInstall.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
Executable files
97
Suspicious files
331
Text files
1 498
Unknown types
19
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1840 | GLBFF44.tmp | C:\Users\admin\AppData\Local\Temp\GLK188.tmp | executable | |
MD5:4F355C177DDABAD5D7079F10503006AB | SHA256:BC91D160C7B0FC9E40D8DB9B248A9FD6DD9489F4246415B98BCD6FB9B806DC74 | |||
| 1352 | icq5_setup.exe | C:\Users\admin\AppData\Local\Temp\GLBFF44.tmp | executable | |
MD5:6653C3AA8A7F32BE6D8FA42DDCC9470D | SHA256:6C336379ECE12FDA036BBC44D20136089A6988E576606132322497B1940D2F63 | |||
| 1840 | GLBFF44.tmp | C:\Users\admin\AppData\Local\Temp\GLM5A0.tmp | executable | |
MD5:484CB68472473A1A84FF07996BB8C1F6 | SHA256:15BB390AF019D92E1D02771B02335FA360DB1BB34BCF4F0C72705027428F4FF1 | |||
| 1840 | GLBFF44.tmp | C:\Program Files\ICQLite\temp\~GLH0008.TMP | — | |
MD5:— | SHA256:— | |||
| 1840 | GLBFF44.tmp | C:\Program Files\ICQLite\temp\ICQLite.emo | — | |
MD5:— | SHA256:— | |||
| 1840 | GLBFF44.tmp | C:\Users\admin\AppData\Local\Temp\GLFB30.tmp | executable | |
MD5:3B2E23D259394C701050486E642D14FA | SHA256:166D7156142F3EE09FA69EB617DD22E4FD248AA80A1AC08767DB6AD99A2705C1 | |||
| 1840 | GLBFF44.tmp | C:\Users\admin\AppData\Local\Temp\~GLH0000.TMP | executable | |
MD5:3B2E23D259394C701050486E642D14FA | SHA256:166D7156142F3EE09FA69EB617DD22E4FD248AA80A1AC08767DB6AD99A2705C1 | |||
| 1840 | GLBFF44.tmp | C:\Users\admin\AppData\Local\Temp\GLCFF72.tmp | executable | |
MD5:8C97D8BB1470C6498E47B12C5A03CE39 | SHA256:A87F19F9FEE475D2B2E82ACFB4589BE6D816B613064CD06826E1D4C147BEB50A | |||
| 1840 | GLBFF44.tmp | C:\Users\Public\Desktop\Click here to restart ICQ 5.1 Setup.lnk | binary | |
MD5:D1A3E7C21D07E1B7C181E40683B86186 | SHA256:740AD5F788370CC20479C3499687502AF242D58872AD1EB61FA525866E7D7709 | |||
| 1840 | GLBFF44.tmp | C:\Users\admin\AppData\Local\Temp\LA.txt | text | |
MD5:0657C7D86242A81CA433BCBE764F7142 | SHA256:0C76F5694FDCD4C530D7152FFC646046DDE865CCD84AB94487420F621FB41073 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
16
TCP/UDP connections
25
DNS requests
9
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3228 | ICQInstall.exe | GET | 404 | 178.237.20.30:80 | http://cb.icq.com/cb/icqsrp/2052/srp.cb?GUID=B5E42400-9761-4ABA-B86D-6DD486DAFFF7&TIME_T=6575195c&GUIDCRC=F24580F9F6C30338&STAGE=02&DIST=1085&BUILDID=3000&SKINID=&COOKIE=0&OS=2,1,6&PARAM= | unknown | html | 162 b | unknown |
3576 | ICQLite.exe | GET | 404 | 178.237.20.30:80 | http://cb.icq.com/cb/icqsrp/2052/srp.cb?GUID=B5E42400-9761-4ABA-B86D-6DD486DAFFF7&TIME_T=65751961&GUIDCRC=034580F9D9C30338&STAGE=03&DIST=1085&BUILDID=3000&SKINID=Default_Skin&COOKIE=0&OS=2,1,6&PARAM= | unknown | html | 162 b | unknown |
3576 | ICQLite.exe | GET | 200 | 23.32.238.201:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?665a89dcb709bda3 | unknown | compressed | 4.66 Kb | unknown |
3576 | ICQLite.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA0HeCoTP8b5pXKW4TH%2F0Xk%3D | unknown | binary | 471 b | unknown |
2520 | ICQInstall.exe | GET | 404 | 178.237.20.30:80 | http://cb.icq.com/cb/icqsrp/2052/srp.cb?GUID=B5E42400-9761-4ABA-B86D-6DD486DAFFF7&TIME_T=65751903&GUIDCRC=A24580F9F9C30338&STAGE=01&DIST=1085&BUILDID=3000&SKINID=&COOKIE=0&OS=2,1,6&PARAM= | unknown | html | 162 b | unknown |
3576 | ICQLite.exe | POST | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/ | unknown | binary | 471 b | unknown |
3576 | ICQLite.exe | POST | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/ | unknown | binary | 471 b | unknown |
3576 | ICQLite.exe | GET | 301 | 5.61.236.229:80 | http://www.icq.com/xtraz/products/coreg/Cactus/testConnection.xml | unknown | html | 178 b | unknown |
3576 | ICQLite.exe | GET | 200 | 192.229.221.95:80 | http://status.geotrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS6FKmrgWTGr7Q8nSk4Oub50ler6QQUlE%2FUXYvkpOKmgP792PkA76O%2BAlcCEALa82sinG45HWKv3oILixk%3D | unknown | binary | 471 b | unknown |
3576 | ICQLite.exe | POST | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/ | unknown | binary | 471 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
2588 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1988 | ICQInstall.exe | 178.237.20.30:80 | cb.icq.com | LLC VK | RU | unknown |
2520 | ICQInstall.exe | 178.237.20.30:80 | cb.icq.com | LLC VK | RU | unknown |
3228 | ICQInstall.exe | 178.237.20.30:80 | cb.icq.com | LLC VK | RU | unknown |
3576 | ICQLite.exe | 5.61.236.229:80 | xtraz.icq.com | LLC VK | RU | unknown |
3576 | ICQLite.exe | 178.237.20.30:80 | cb.icq.com | LLC VK | RU | unknown |
3576 | ICQLite.exe | 5.61.236.229:443 | xtraz.icq.com | LLC VK | RU | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
cb.icq.com |
| unknown |
xtraz.icq.com |
| unknown |
www.icq.com |
| unknown |
ctldl.windowsupdate.com |
| whitelisted |
geo2.adobe.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
status.geotrust.com |
| whitelisted |
fpdownload.macromedia.com |
| whitelisted |
login.icq.com |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1988 | ICQInstall.exe | A Network Trojan was detected | ET USER_AGENTS Suspicious User Agent (Microsoft Internet Explorer) |
2520 | ICQInstall.exe | A Network Trojan was detected | ET USER_AGENTS Suspicious User Agent (Microsoft Internet Explorer) |