| File name: | vod.m3u |
| Full analysis: | https://app.any.run/tasks/043e59da-ae9e-458d-87aa-a51ce1388ea5 |
| Verdict: | Malicious activity |
| Analysis date: | July 24, 2019, 17:53:17 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | text/plain |
| File info: | M3U playlist, ASCII text, with very long lines, with CRLF line terminators |
| MD5: | F5F55C539152D6931D515246A43DB82A |
| SHA1: | F1F2B997443F90812234FBE5A859276109CEE83D |
| SHA256: | B95811DC095C247015CBB3CDA2705C1FA4AAFCA81CE93EEE8BD96FE8D6DC2C4D |
| SSDEEP: | 1536:/1zL4VNJusDLXEtyOWK6+2CSNHgKmj9S5X7ANuSKmXu6nvhwUA+eqeDhO4YiI48s:/0D14Rk |
MALICIOUS
No malicious indicators.SUSPICIOUS
Creates files in the user directory
- vlc.exe (PID: 2812)
INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .m3u | | | Extended M3U playlist (100) |
|---|
Total processes
33
Monitored processes
1
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2812 | "C:\Program Files\VideoLAN\VLC\vlc.exe" --started-from-file "C:\Users\admin\AppData\Local\Temp\vod.m3u" | C:\Program Files\VideoLAN\VLC\vlc.exe | explorer.exe | ||||||||||||
User: admin Company: VideoLAN Integrity Level: MEDIUM Description: VLC media player Exit code: 0 Version: 2.2.6 Modules
| |||||||||||||||
Total events
360
Read events
359
Write events
1
Delete events
0
Modification events
| (PID) Process: | (2812) vlc.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Direct3D\MostRecentApplication |
| Operation: | write | Name: | Name |
Value: vlc.exe | |||
Executable files
0
Suspicious files
0
Text files
2
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2812 | vlc.exe | C:\Users\admin\AppData\Local\Temp\VLCDBEB.tmp | — | |
MD5:— | SHA256:— | |||
| 2812 | vlc.exe | C:\Users\admin\AppData\Local\Temp\VLCDCE6.tmp | — | |
MD5:— | SHA256:— | |||
| 2812 | vlc.exe | C:\Users\admin\AppData\Local\Temp\VLCDCE7.tmp | — | |
MD5:— | SHA256:— | |||
| 2812 | vlc.exe | C:\Users\admin\AppData\Local\Temp\VLCDCE8.tmp | — | |
MD5:— | SHA256:— | |||
| 2812 | vlc.exe | C:\Users\admin\AppData\Local\Temp\VLCDCE9.tmp | — | |
MD5:— | SHA256:— | |||
| 2812 | vlc.exe | C:\Users\admin\AppData\Local\Temp\VLCDCF9.tmp | — | |
MD5:— | SHA256:— | |||
| 2812 | vlc.exe | C:\Users\admin\AppData\Roaming\vlc\vlcrc.2812 | — | |
MD5:— | SHA256:— | |||
| 2812 | vlc.exe | C:\Users\admin\AppData\Local\Temp\VLC1521.tmp | — | |
MD5:— | SHA256:— | |||
| 2812 | vlc.exe | C:\Users\admin\AppData\Local\Temp\VLC1522.tmp | — | |
MD5:— | SHA256:— | |||
| 2812 | vlc.exe | C:\Users\admin\AppData\Local\Temp\VLC1523.tmp | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
12
TCP/UDP connections
23
DNS requests
8
Threats
8
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
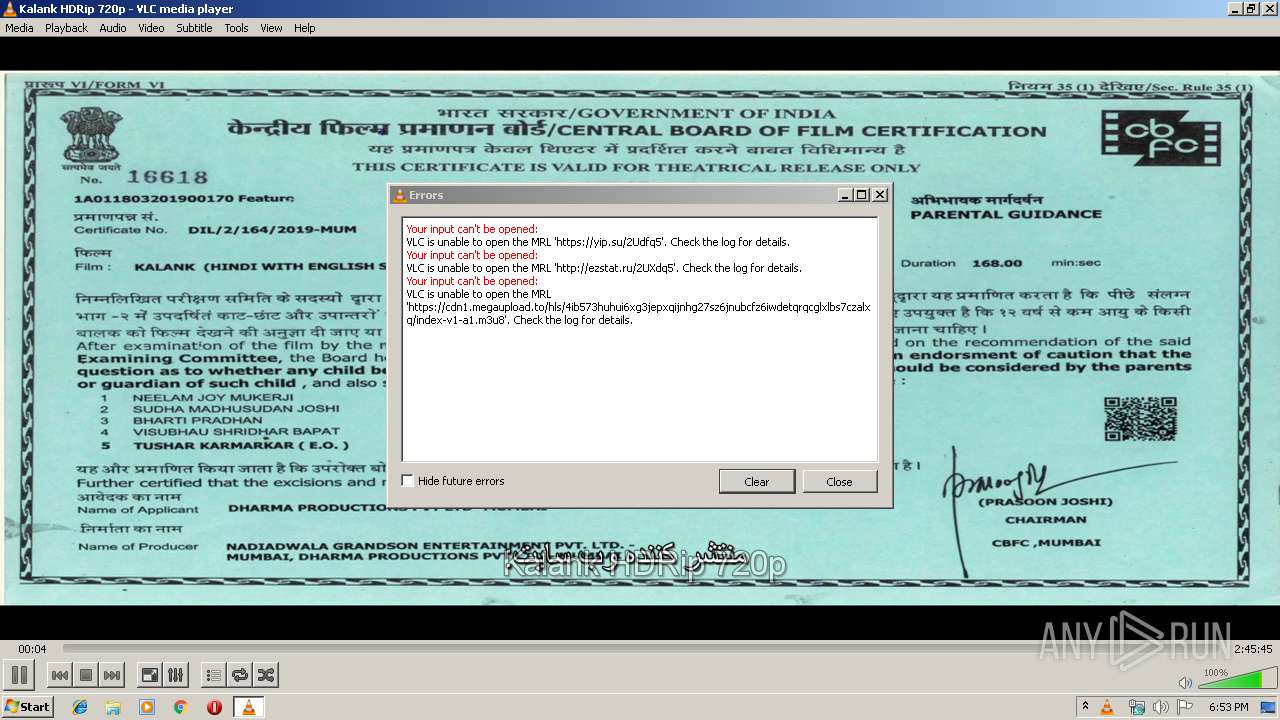
2812 | vlc.exe | GET | 301 | 88.99.66.31:80 | http://ezstat.ru/2UXdq5 | DE | — | — | shared |
2812 | vlc.exe | GET | — | 104.31.91.79:80 | http://cdn1.megaupload.to:80/hls/4ib573huhui6xg3jepxqijnhg27sz6jnubcfz6iwdetqrqcglxlbs7czalxq/index-v1-a1.m3u8 | US | — | — | shared |
2812 | vlc.exe | GET | 403 | 54.39.124.28:80 | http://54.39.124.28/pro.php/https://hses.akamaized.net:443/videos/movies/hindi/1000239103/1562681282652/5d0f83c3ccbf4501cf952bdfc8c0d785/media-4/index.m3u8 | FR | — | — | unknown |
2812 | vlc.exe | GET | — | 185.112.32.146:80 | http://dl12.f2m.co/film/Kalank.2019.720p.WEB-DL.Film2Movie_WS.mkv | IR | — | — | unknown |
2812 | vlc.exe | GET | — | 185.112.32.146:80 | http://dl12.f2m.co/film/Kalank.2019.720p.WEB-DL.Film2Movie_WS.mkv | IR | — | — | unknown |
2812 | vlc.exe | GET | 301 | 88.99.66.31:80 | http://02ip.ru/2U4dq5 | DE | — | — | malicious |
2812 | vlc.exe | GET | 403 | 54.39.124.28:80 | http://54.39.124.28/pro.php/https://hses.akamaized.net:443/videos/movies/hindi/1000239103/1562681282652/5d0f83c3ccbf4501cf952bdfc8c0d785/media-4/index.m3u8 | FR | — | — | unknown |
2812 | vlc.exe | GET | — | 185.112.32.146:80 | http://dl12.f2m.co/film/Kalank.2019.720p.WEB-DL.Film2Movie_WS.mkv | IR | — | — | unknown |
2812 | vlc.exe | GET | 206 | 185.112.32.146:80 | http://dl12.f2m.co/film/Kalank.2019.720p.WEB-DL.Film2Movie_WS.mkv | IR | binary | 52.0 Kb | unknown |
2812 | vlc.exe | GET | — | 185.112.32.146:80 | http://dl12.f2m.co/film/Kalank.2019.720p.WEB-DL.Film2Movie_WS.mkv | IR | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2812 | vlc.exe | 88.99.66.31:443 | yip.su | Hetzner Online GmbH | DE | malicious |
2812 | vlc.exe | 2.16.186.73:443 | hses.akamaized.net | Akamai International B.V. | — | whitelisted |
2812 | vlc.exe | 2.16.186.74:443 | hses.akamaized.net | Akamai International B.V. | — | whitelisted |
2812 | vlc.exe | 88.99.66.31:80 | yip.su | Hetzner Online GmbH | DE | malicious |
2812 | vlc.exe | 54.39.124.28:80 | — | OVH SAS | FR | unknown |
2812 | vlc.exe | 104.31.91.79:80 | cdn1.megaupload.to | Cloudflare Inc | US | shared |
2812 | vlc.exe | 104.31.91.79:443 | cdn1.megaupload.to | Cloudflare Inc | US | shared |
2812 | vlc.exe | 185.112.32.146:80 | dl12.f2m.co | Asiatech Data Transfer Inc PLC | IR | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
yip.su |
| whitelisted |
hses.akamaized.net |
| whitelisted |
ezstat.ru |
| shared |
02ip.ru |
| malicious |
cdn1.megaupload.to |
| suspicious |
iplogger.org |
| shared |
dl12.f2m.co |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1044 | svchost.exe | Potentially Bad Traffic | ET DNS Query for .su TLD (Soviet Union) Often Malware Related |
2812 | vlc.exe | Potential Corporate Privacy Violation | POLICY [PTsecurity] IP Check Domain SSL certificate |
2812 | vlc.exe | Potential Corporate Privacy Violation | POLICY [PTsecurity] IP Check Domain SSL certificate |
2812 | vlc.exe | Generic Protocol Command Decode | SURICATA HTTP URI terminated by non-compliant character |
2812 | vlc.exe | Potential Corporate Privacy Violation | POLICY [PTsecurity] IP Check Domain SSL certificate |
2812 | vlc.exe | Potential Corporate Privacy Violation | POLICY [PTsecurity] IP Check Domain SSL certificate |
2 ETPRO signatures available at the full report
Process | Message |
|---|---|
vlc.exe | core libvlc: one instance mode ENABLED
|
vlc.exe | core libvlc: Running vlc with the default interface. Use 'cvlc' to use vlc without interface.
|
vlc.exe | core playlist: stopping playback
|
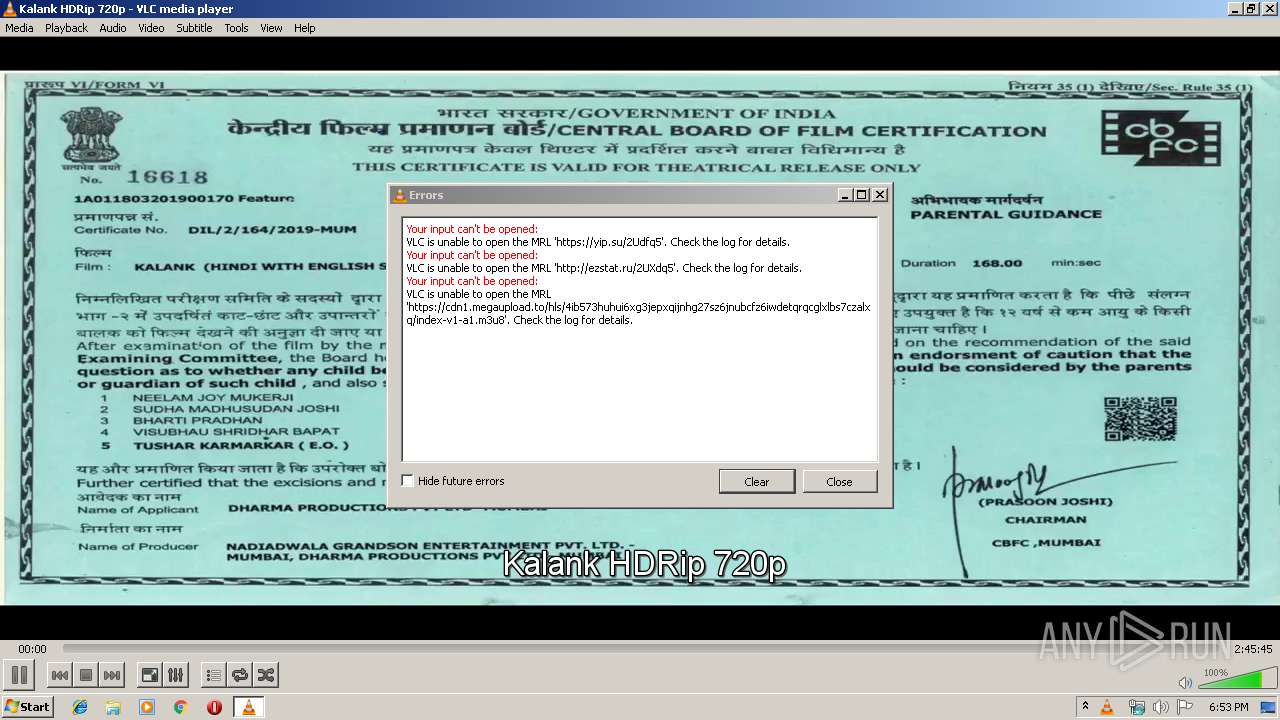
vlc.exe | http access error: error: HTTP/1.1 403 Forbidden
|
vlc.exe | http access error: error: HTTP/1.0 403 Forbidden
|
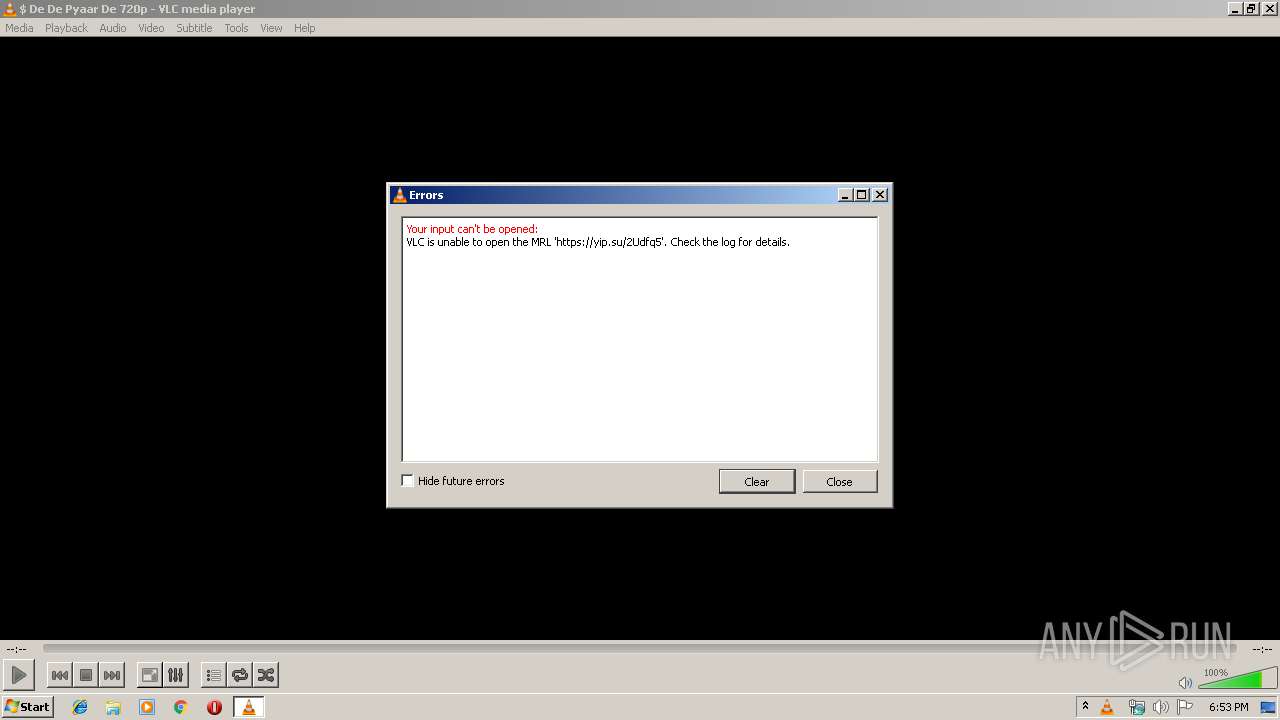
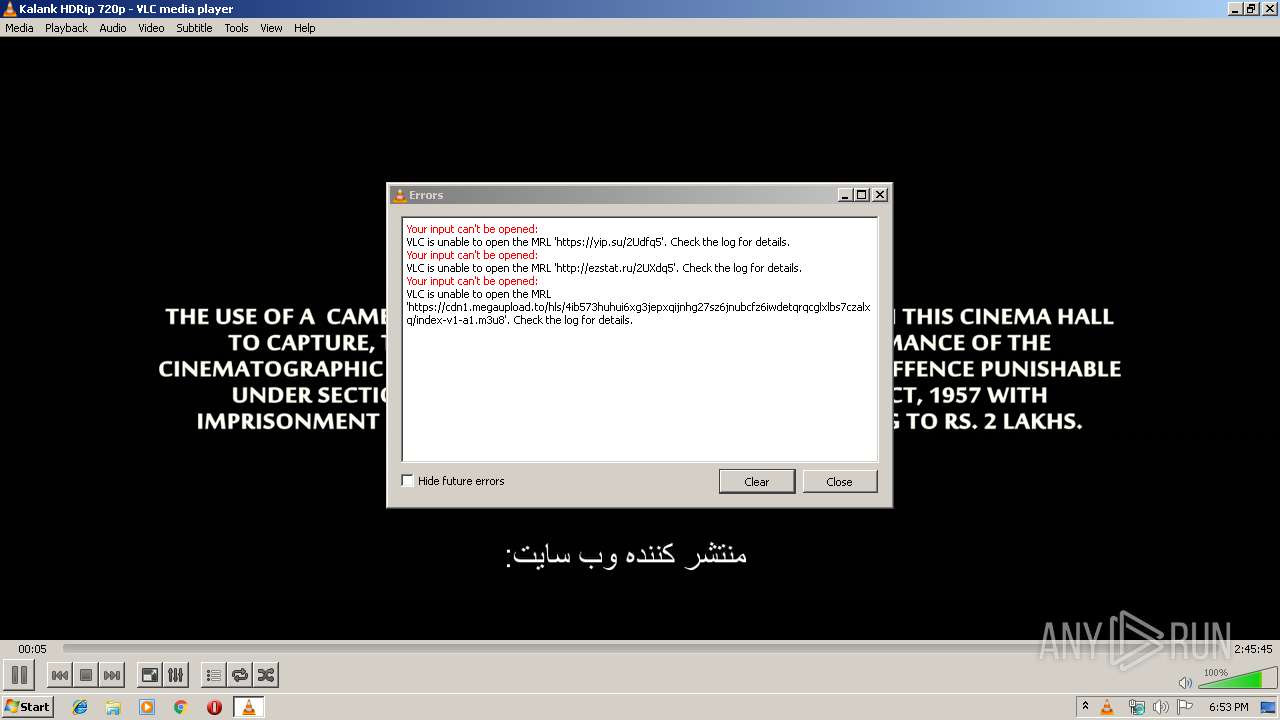
vlc.exe | core input error: open of `https://yip.su/2Udfq5' failed
|
vlc.exe | http access error: error: HTTP/1.1 403 Forbidden
|
vlc.exe | http access error: error: HTTP/1.1 403 Forbidden
|
vlc.exe | access_mms access error: error: HTTP/1.1 403 Forbidden
|
vlc.exe | core input error: open of `http://ezstat.ru/2UXdq5' failed
|