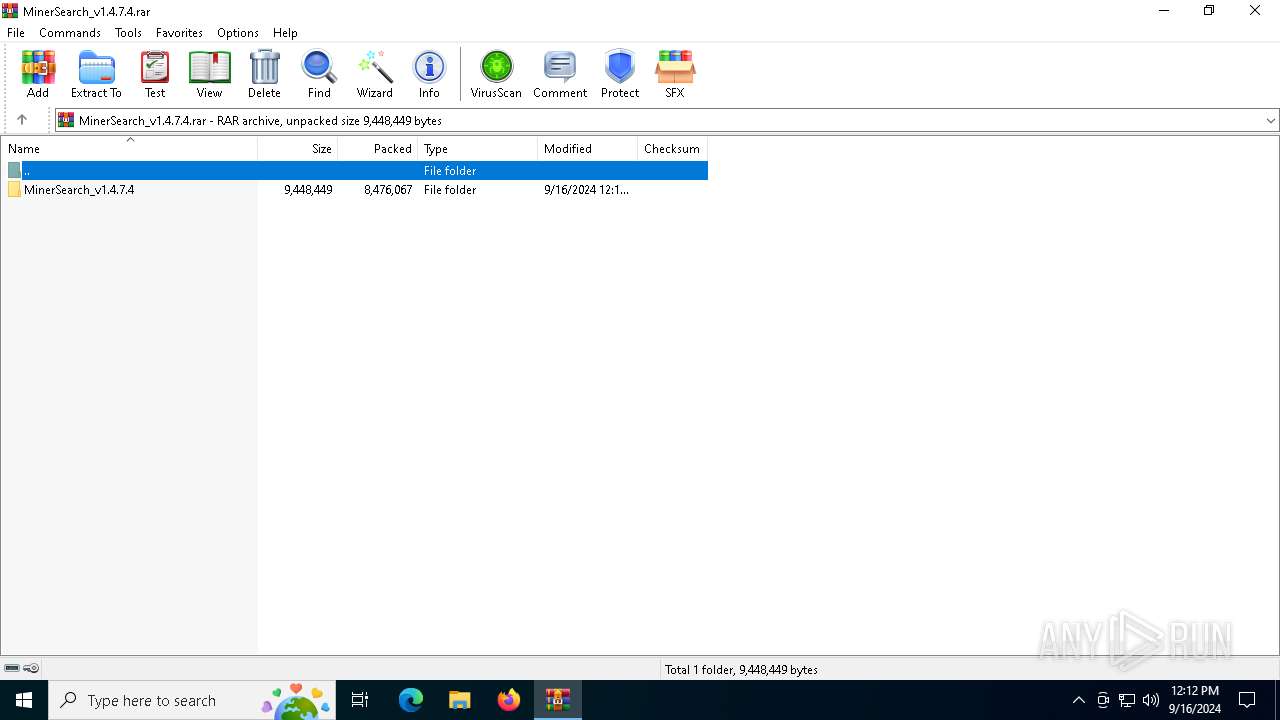
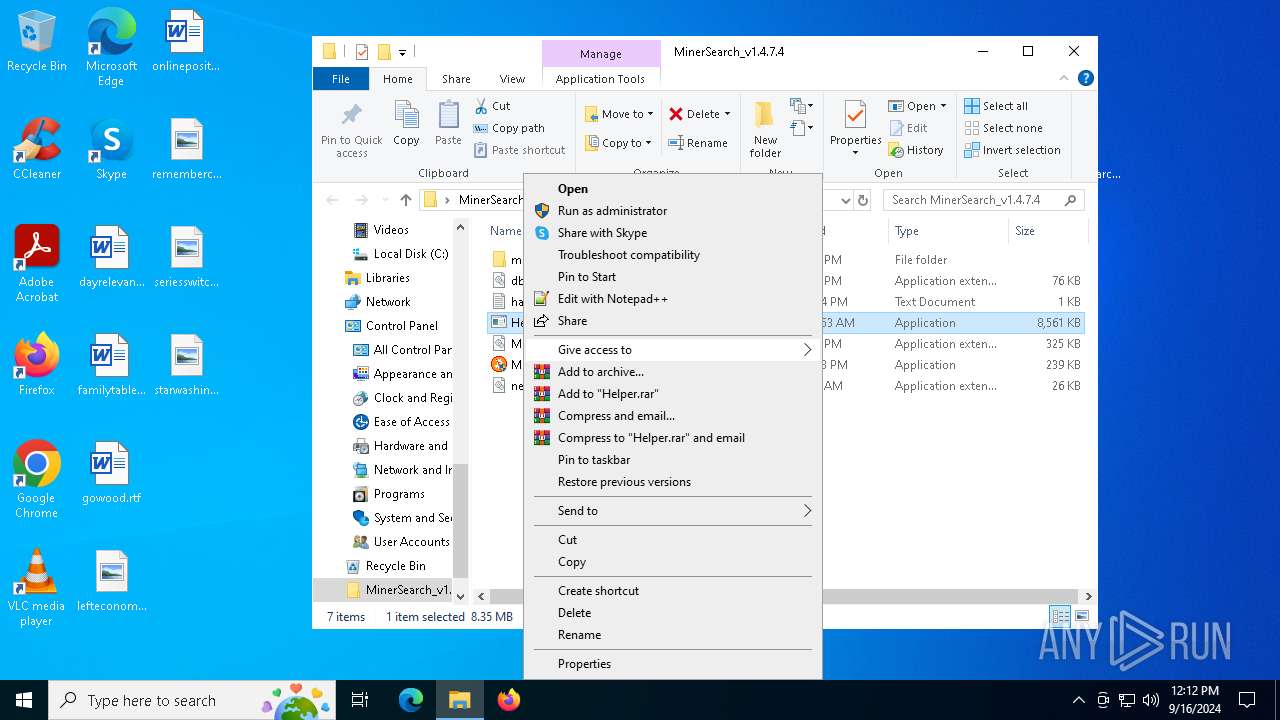
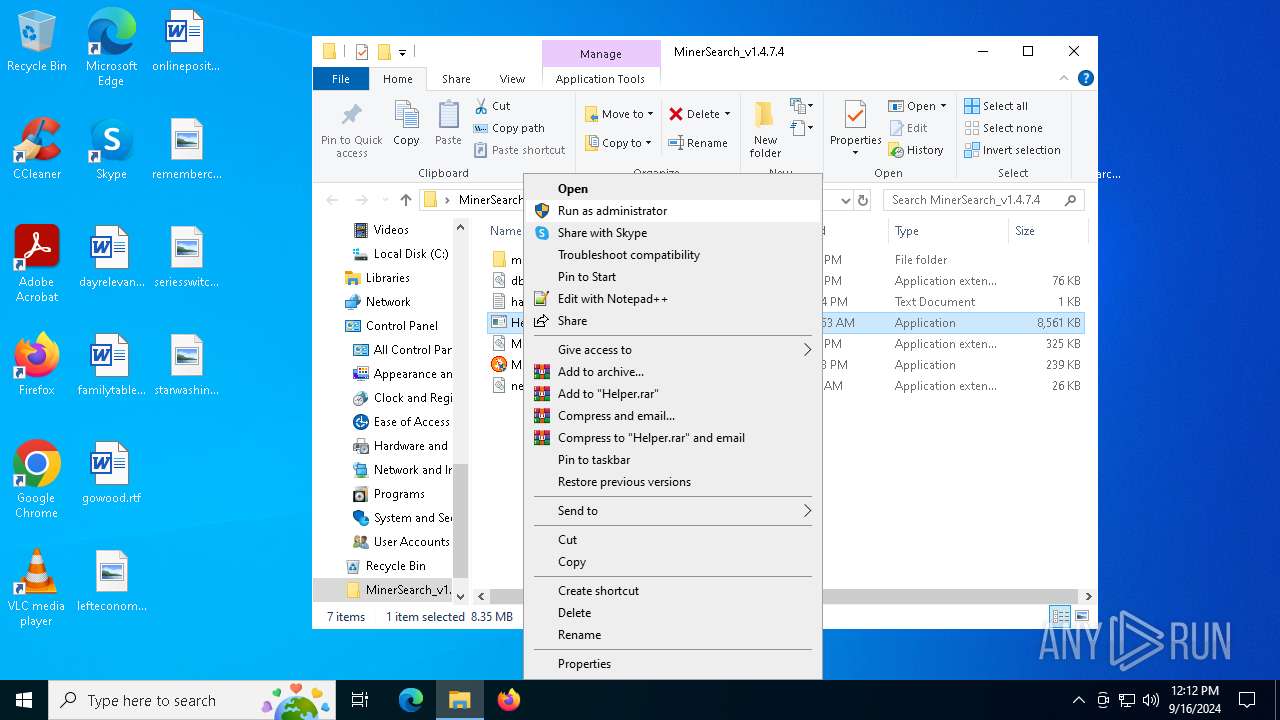
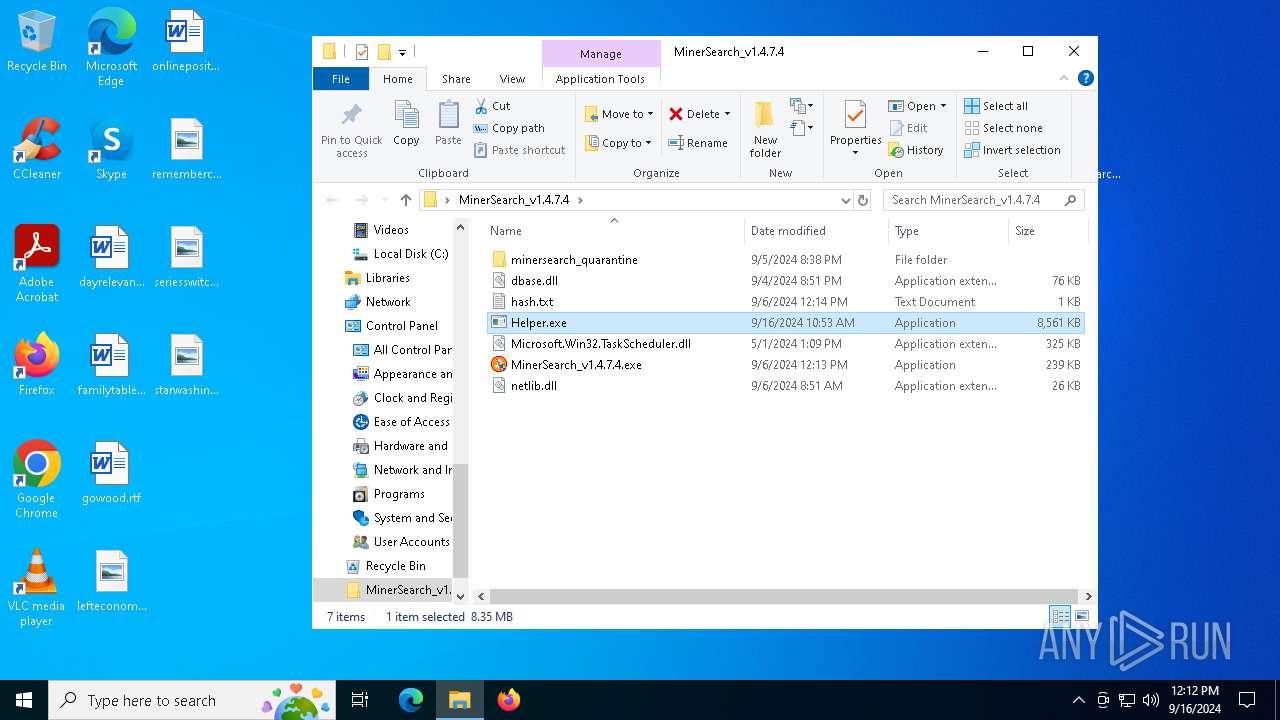
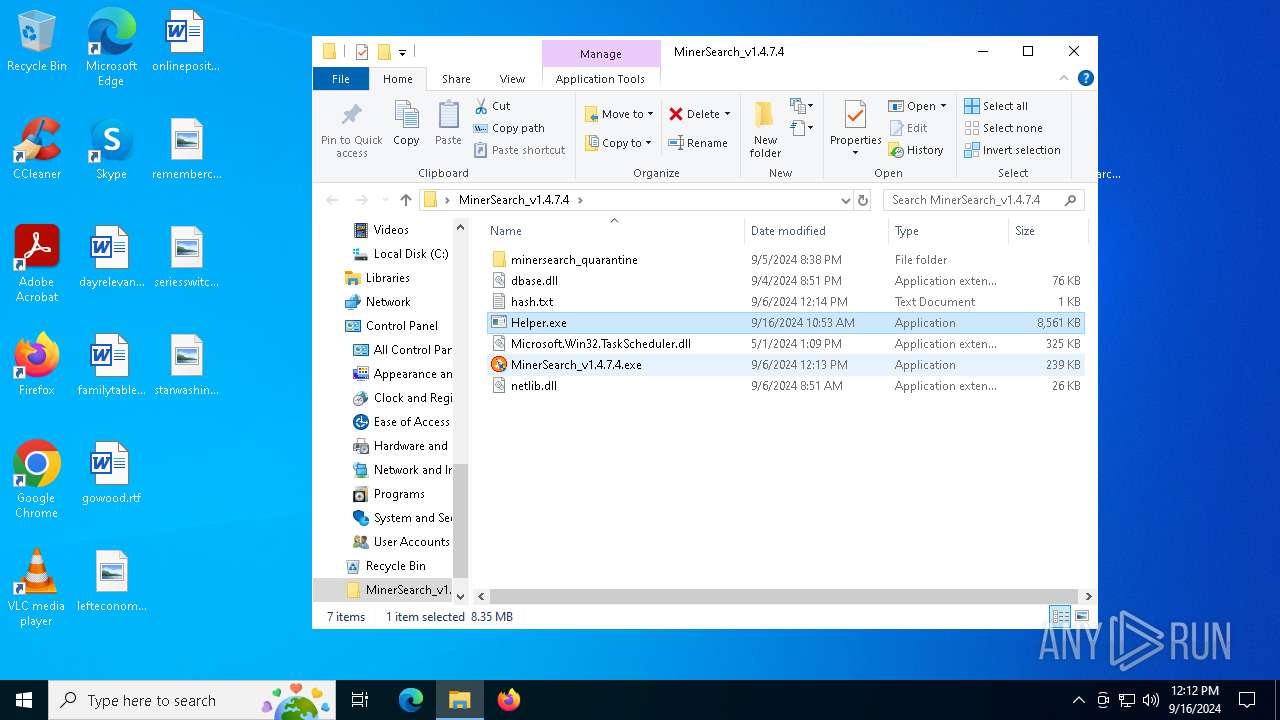
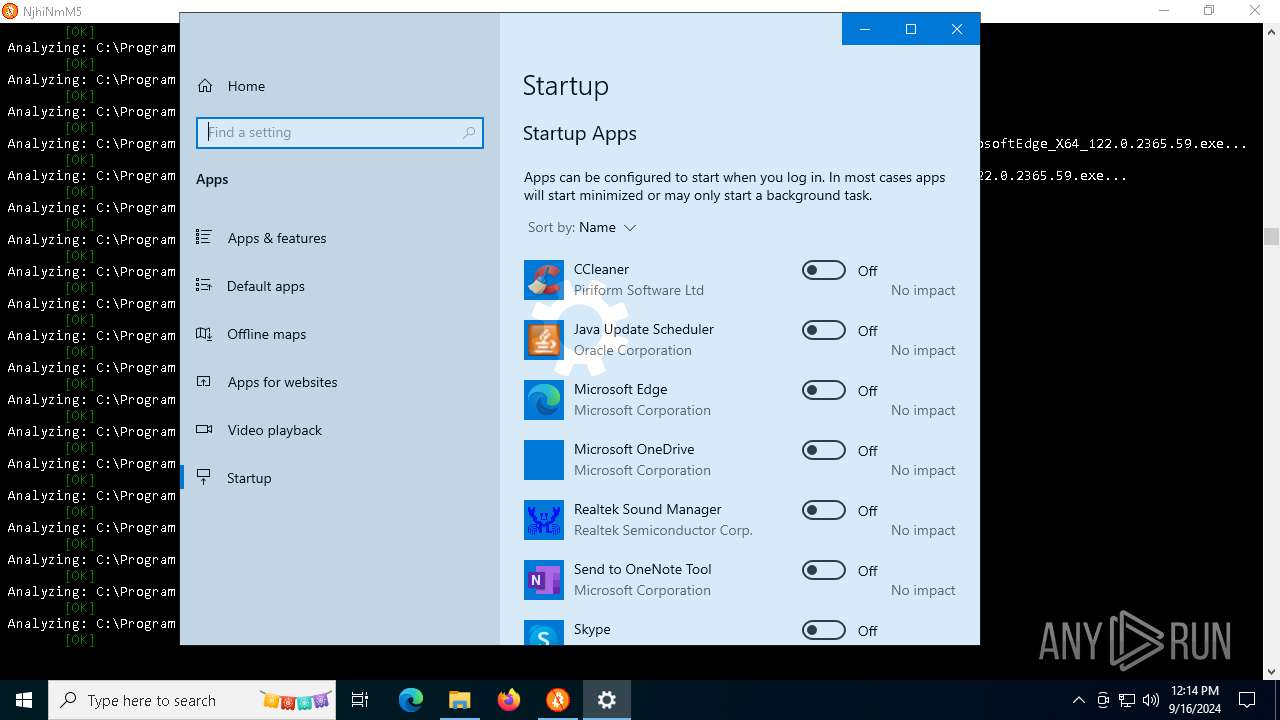
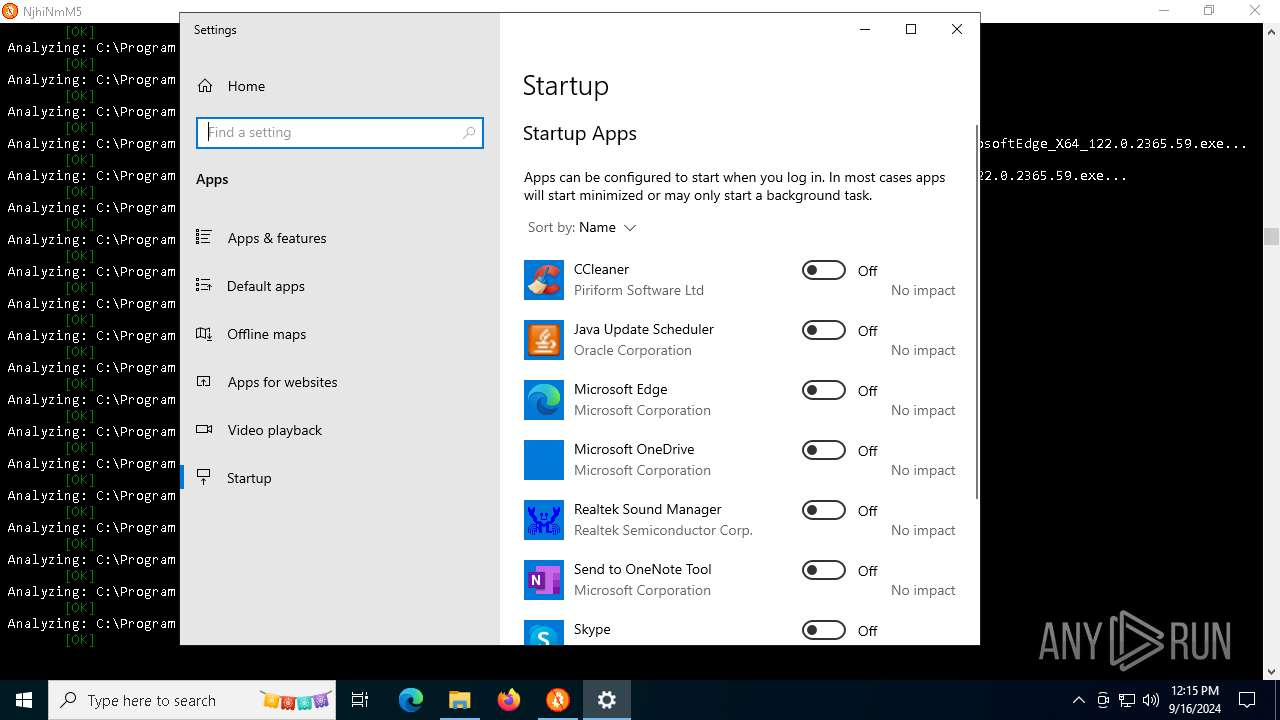
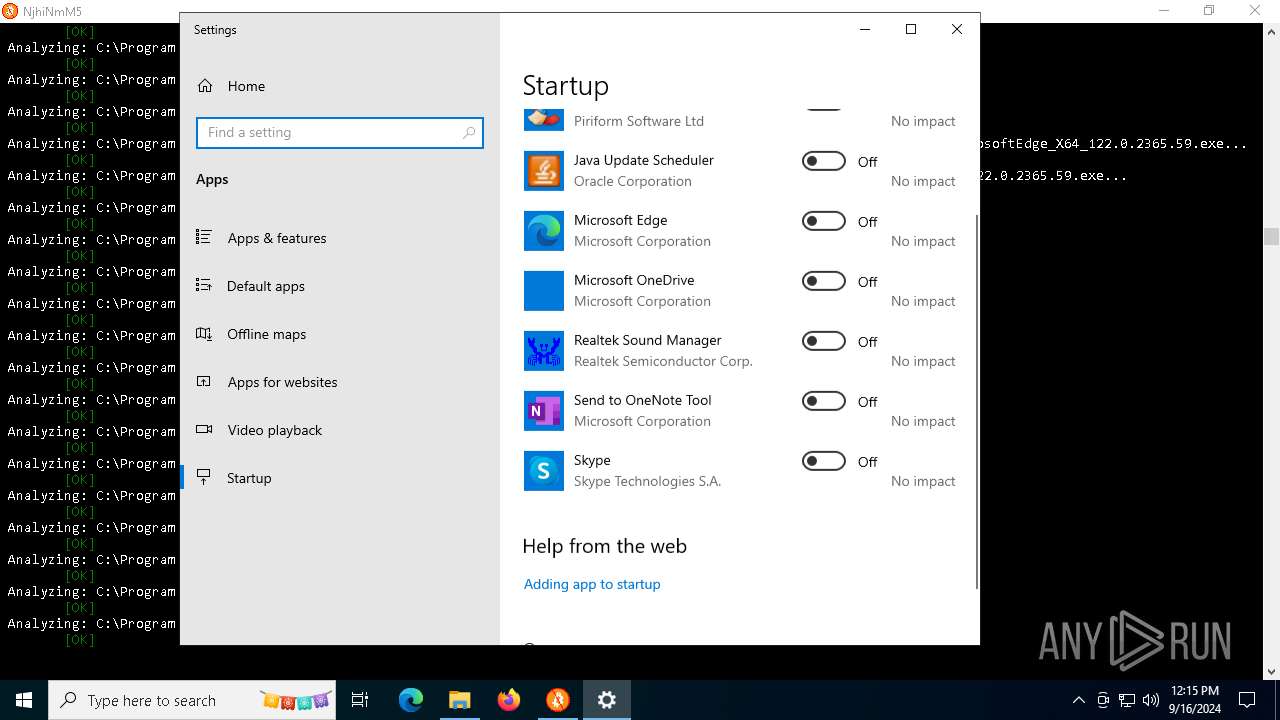
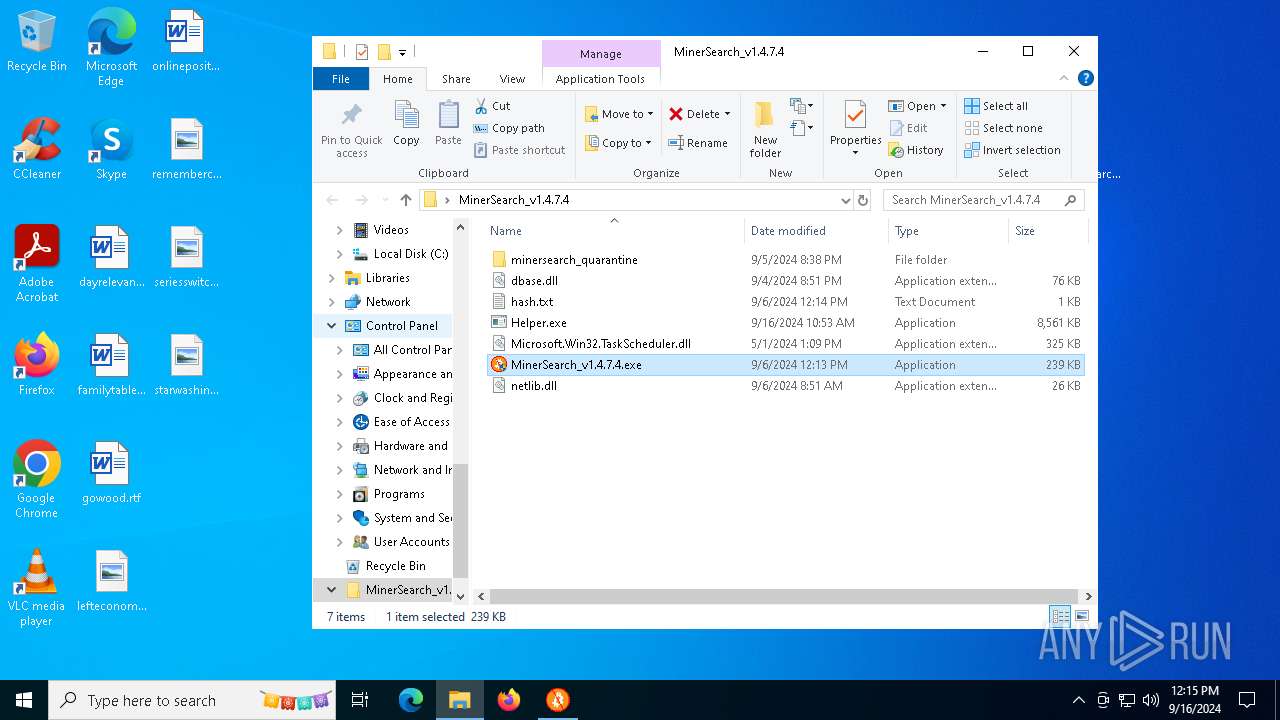
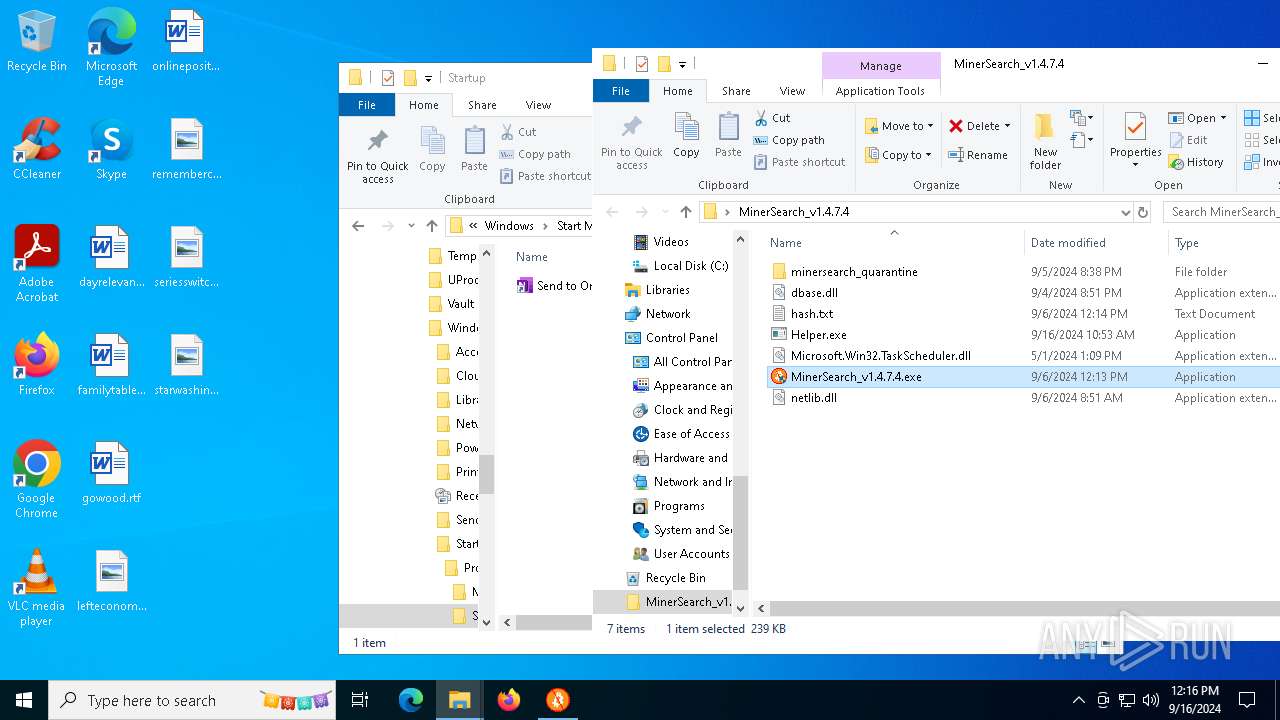
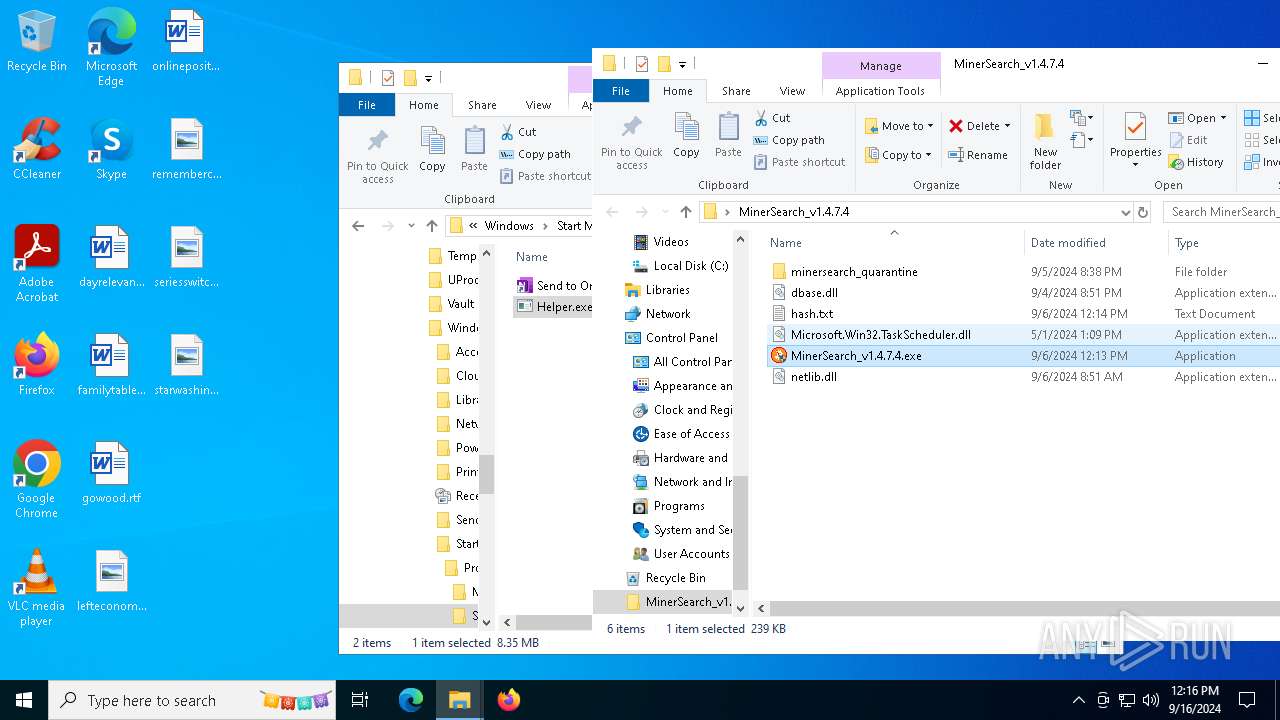
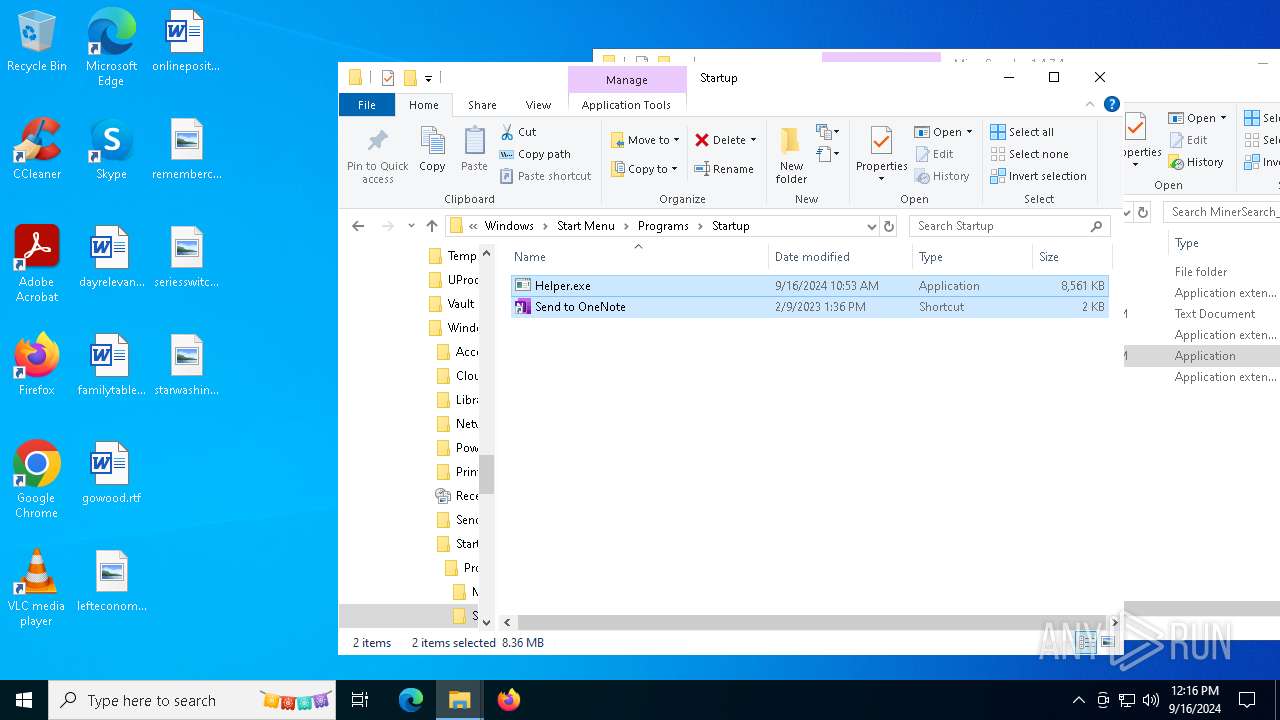
| File name: | MinerSearch_v1.4.7.4.rar |
| Full analysis: | https://app.any.run/tasks/3aa2699b-772e-4a0d-8052-d61ff8bc3c8d |
| Verdict: | Malicious activity |
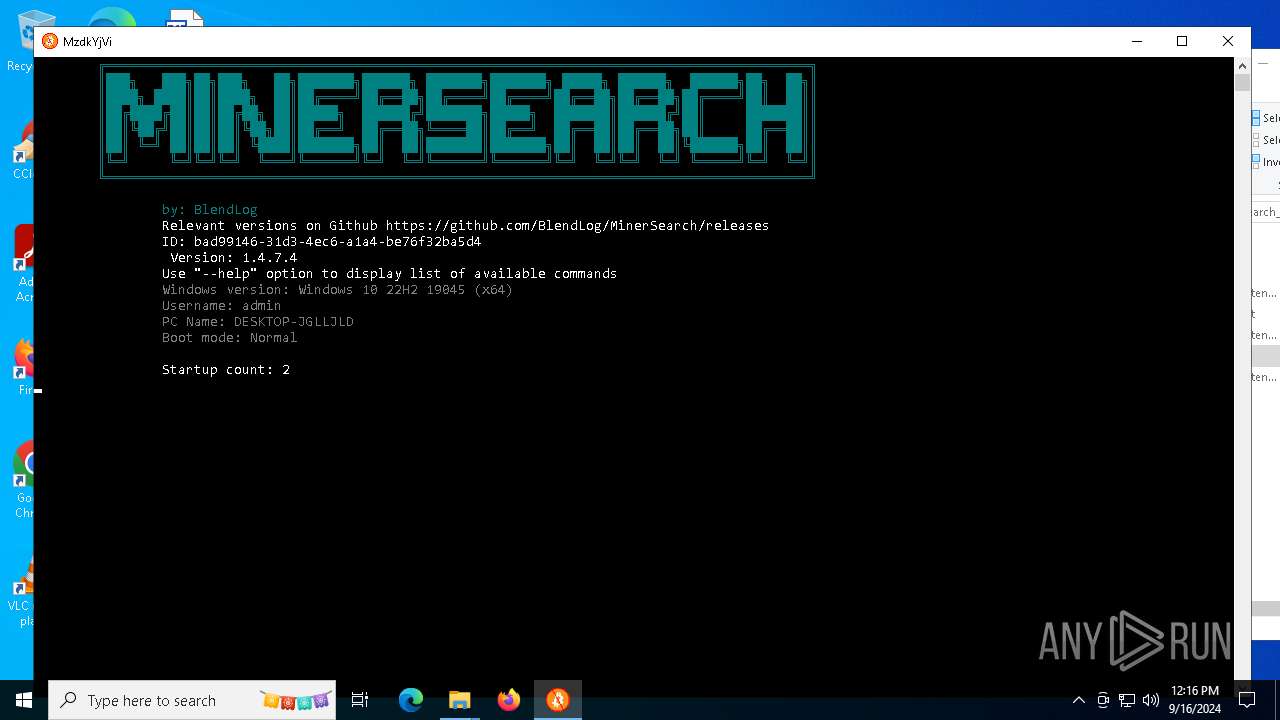
| Analysis date: | September 16, 2024, 12:12:25 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | 568EA060DBB22BE53C892F3E24E95763 |
| SHA1: | FB1FD06236AD7531D23735ADE22CC05447E9D348 |
| SHA256: | B94BA59ECD09A48C43E7B6ED52C0AA5121E4DE8AF0411D52FAF43BDD5A4788C7 |
| SSDEEP: | 98304:6Lq9TOdDOfal+wVgY2zqbYBrGH0yHRbt53yxex5T9qsd+iiT1SviJpkQJPoS7NDD:jxGuMHFNYETtug6E7c |
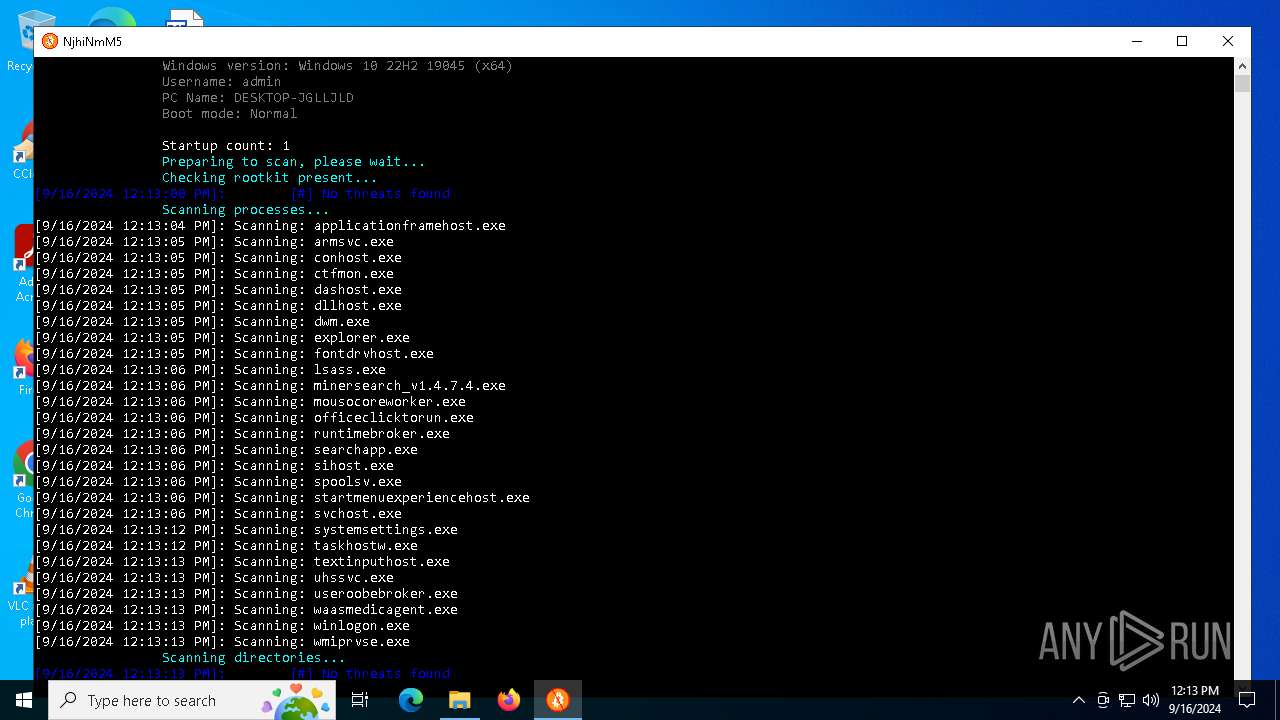
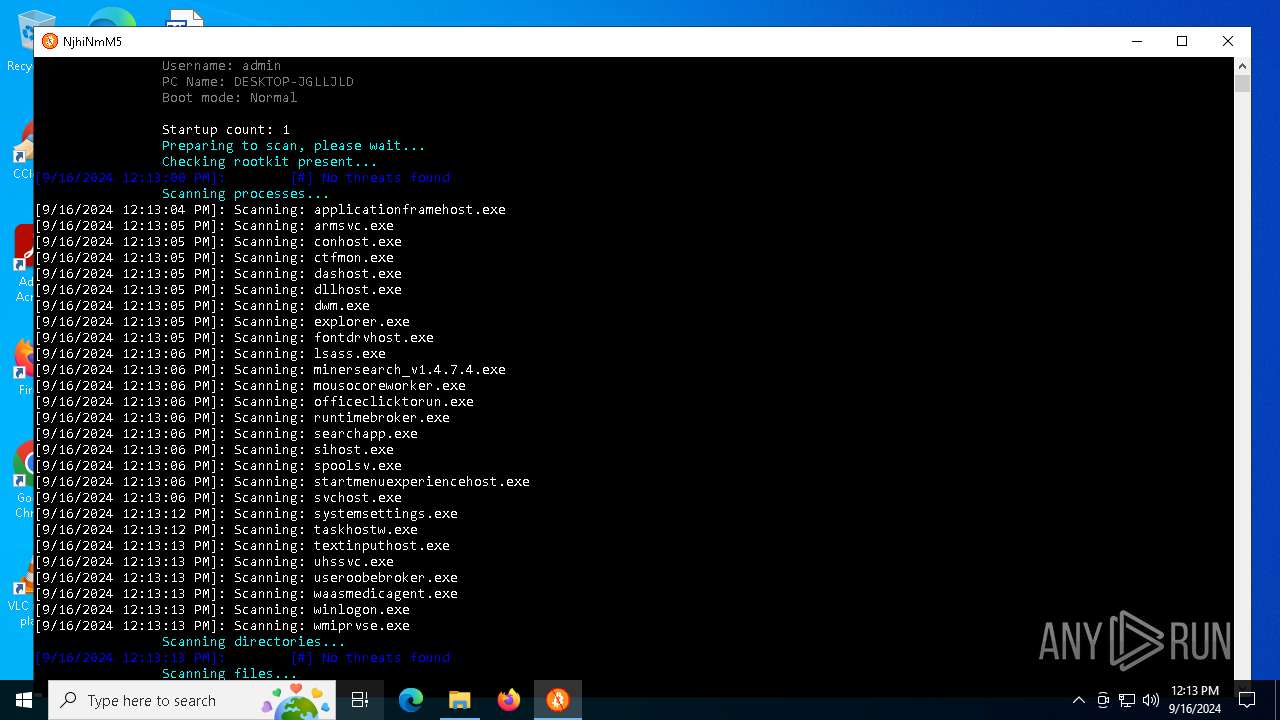
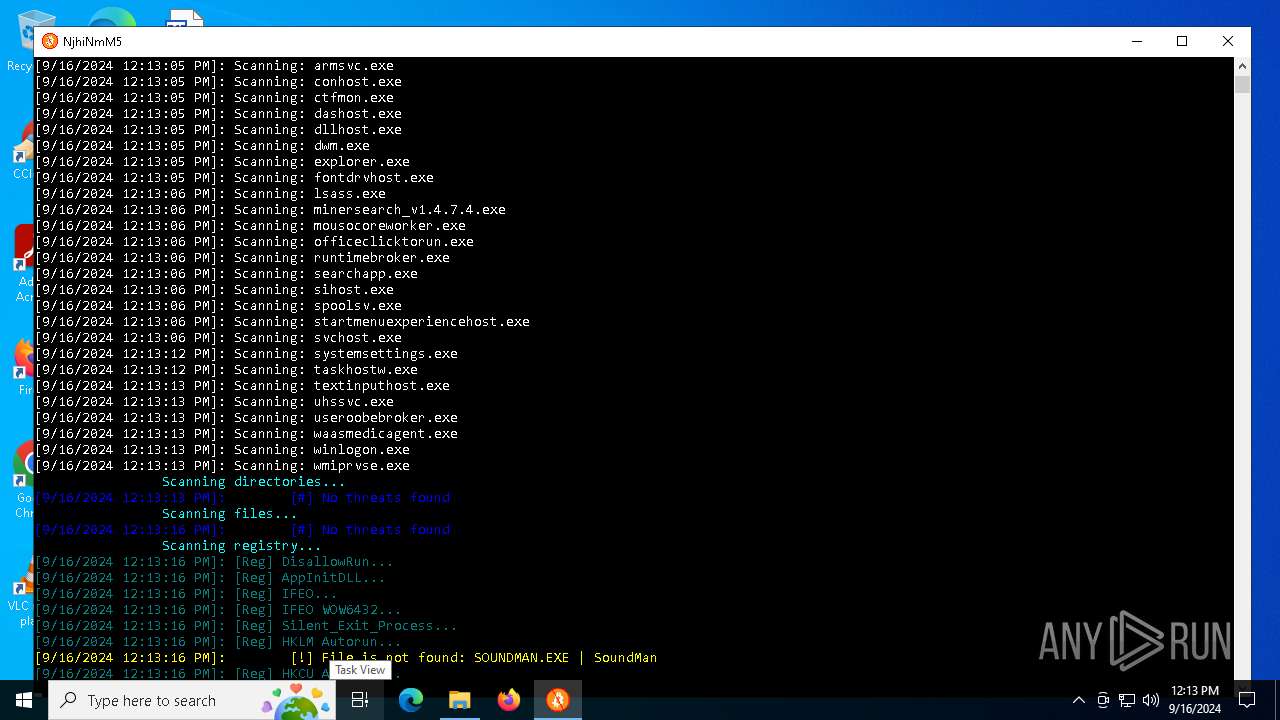
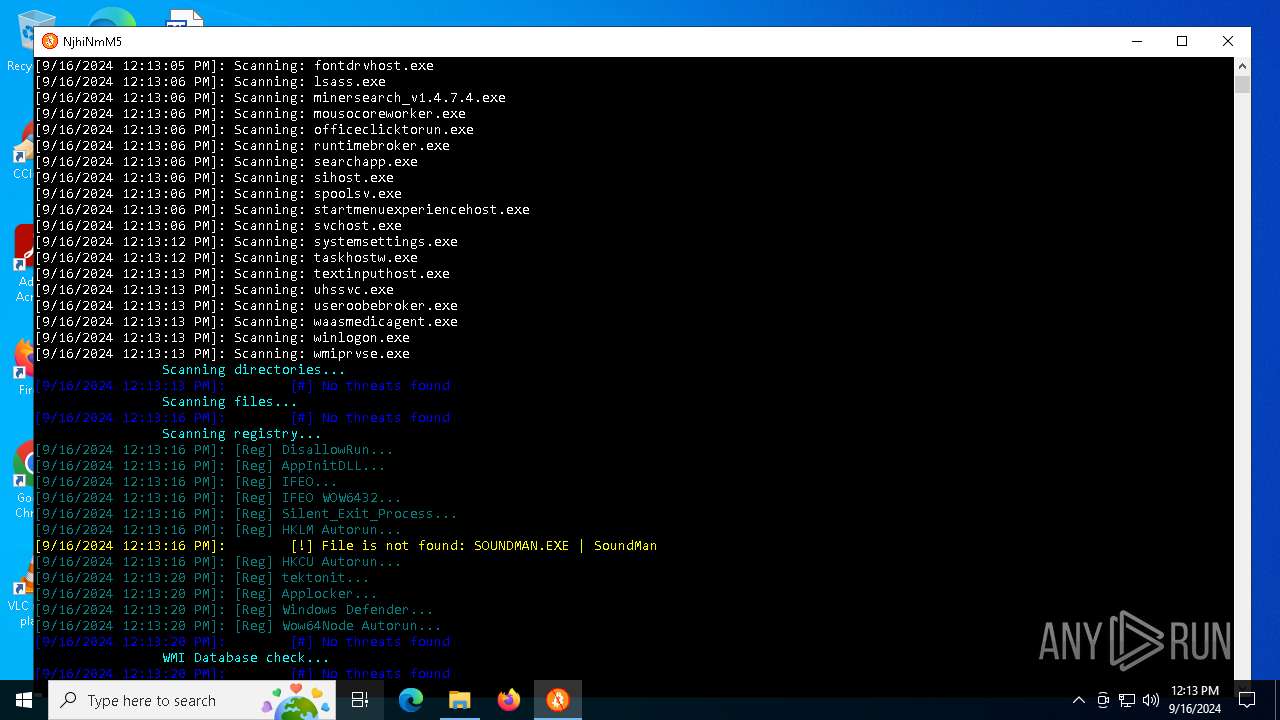
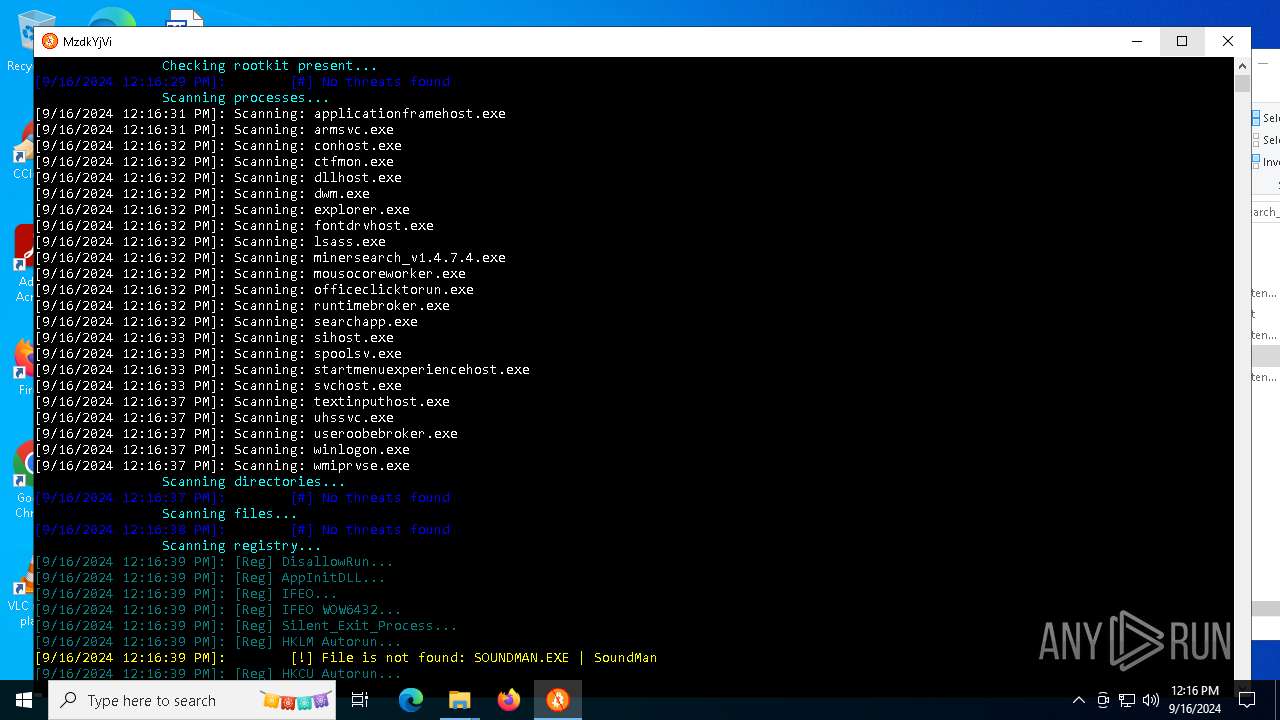
MALICIOUS
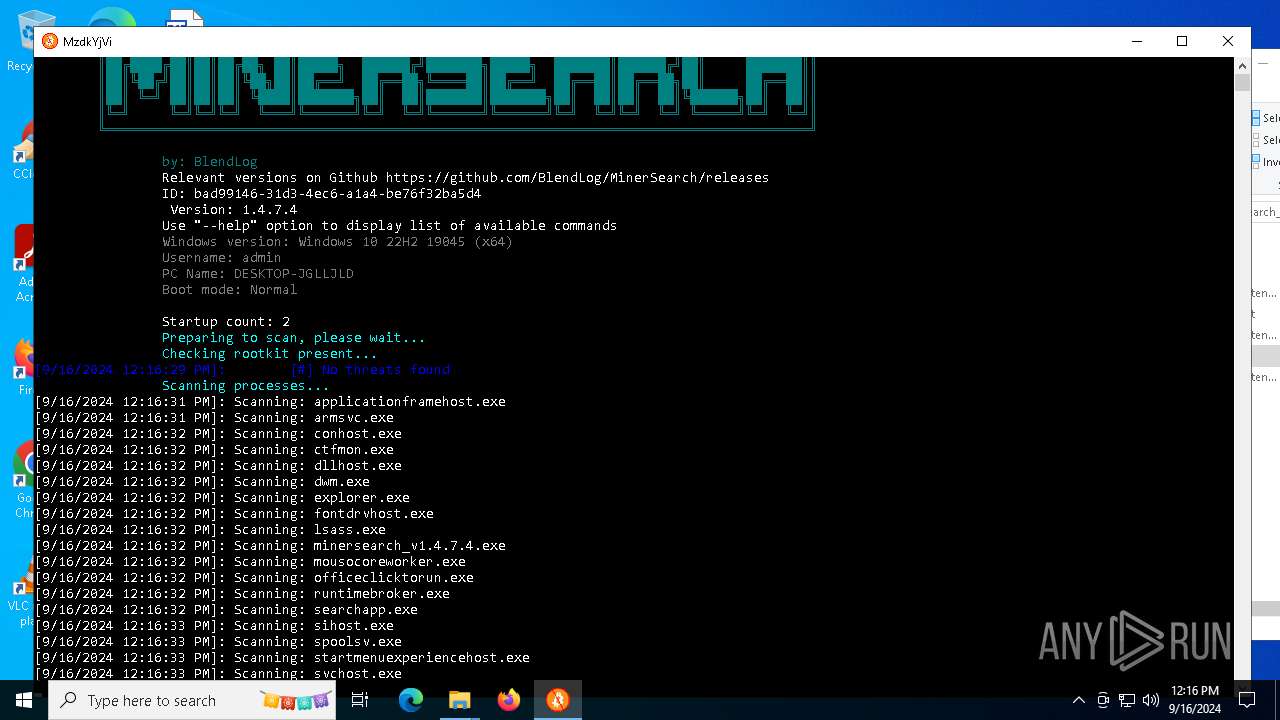
No malicious indicators.SUSPICIOUS
Reads security settings of Internet Explorer
- MinerSearch_v1.4.7.4.exe (PID: 2636)
The process verifies whether the antivirus software is installed
- MinerSearch_v1.4.7.4.exe (PID: 2636)
Adds/modifies Windows certificates
- MinerSearch_v1.4.7.4.exe (PID: 2636)
Checks Windows Trust Settings
- MinerSearch_v1.4.7.4.exe (PID: 2636)
INFO
The process uses the downloaded file
- WinRAR.exe (PID: 6812)
Reads mouse settings
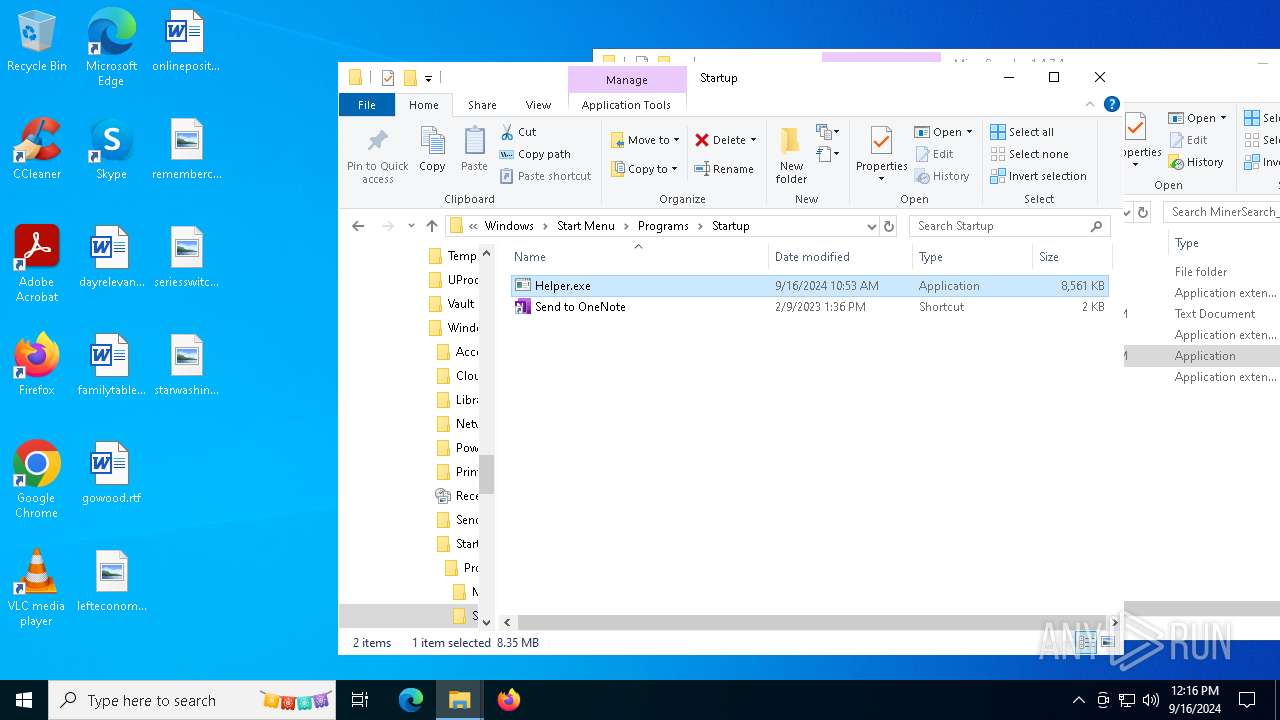
- Helper.exe (PID: 1616)
- Helper.exe (PID: 2228)
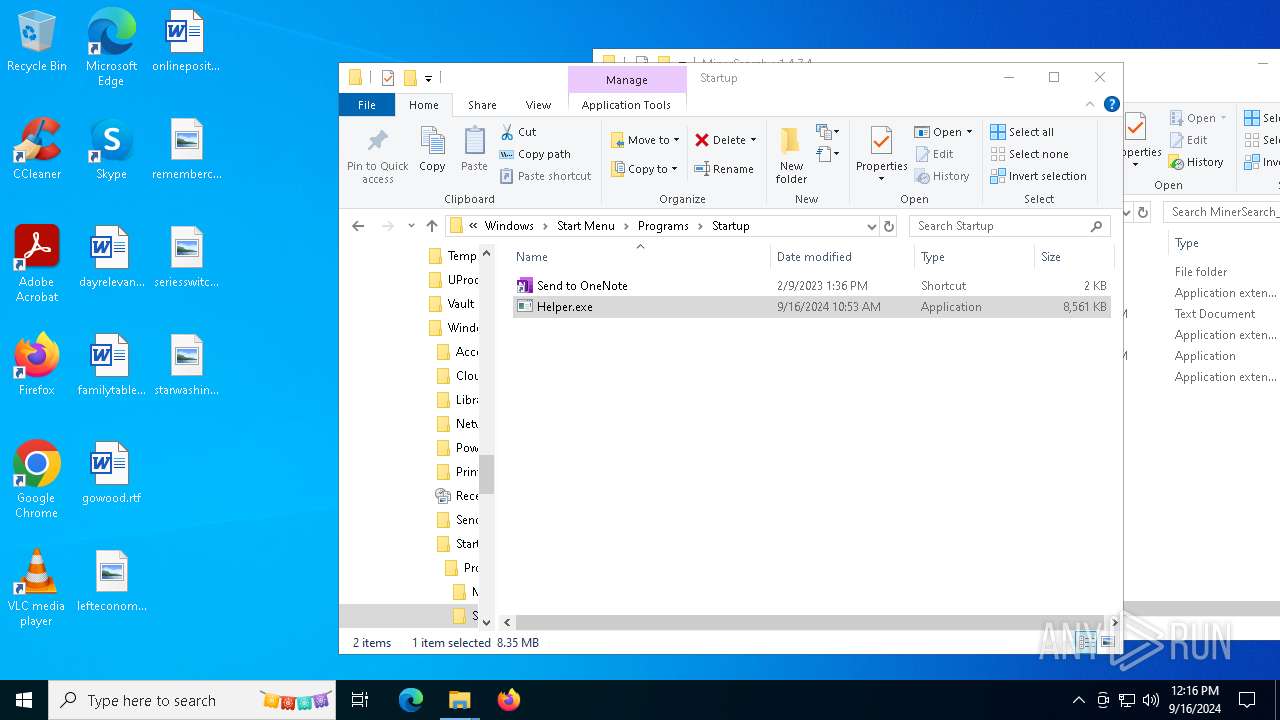
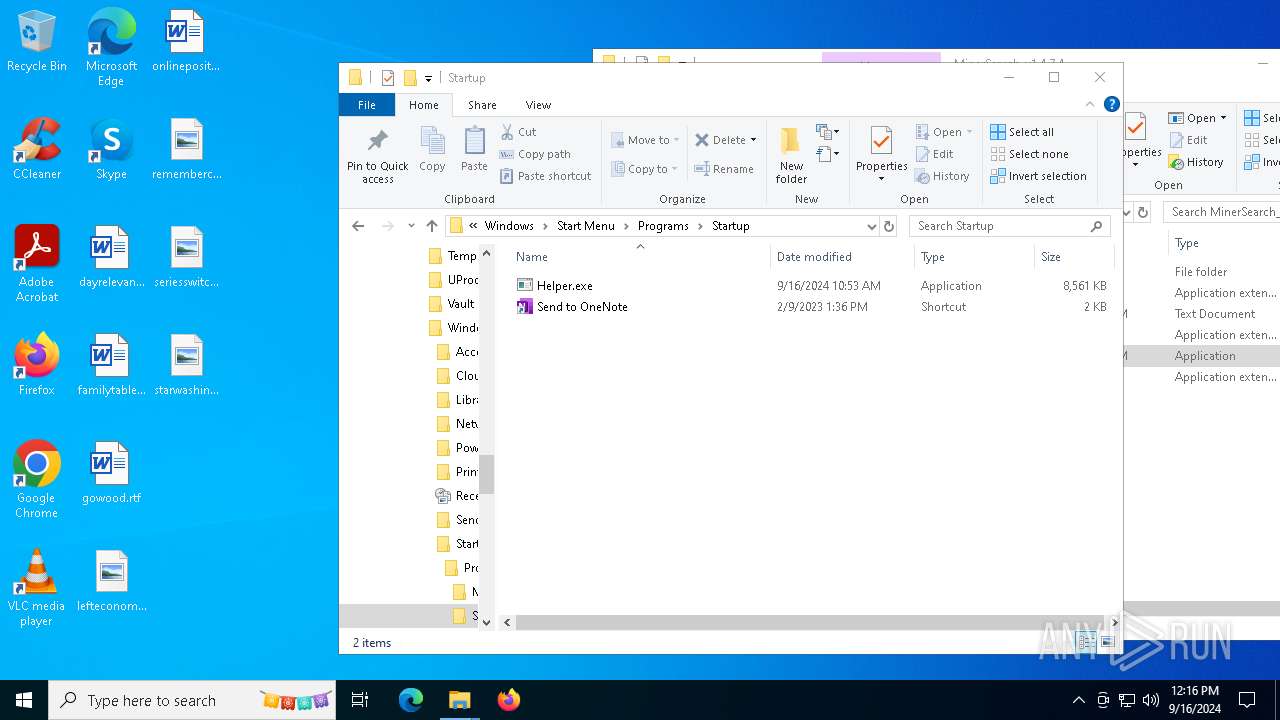
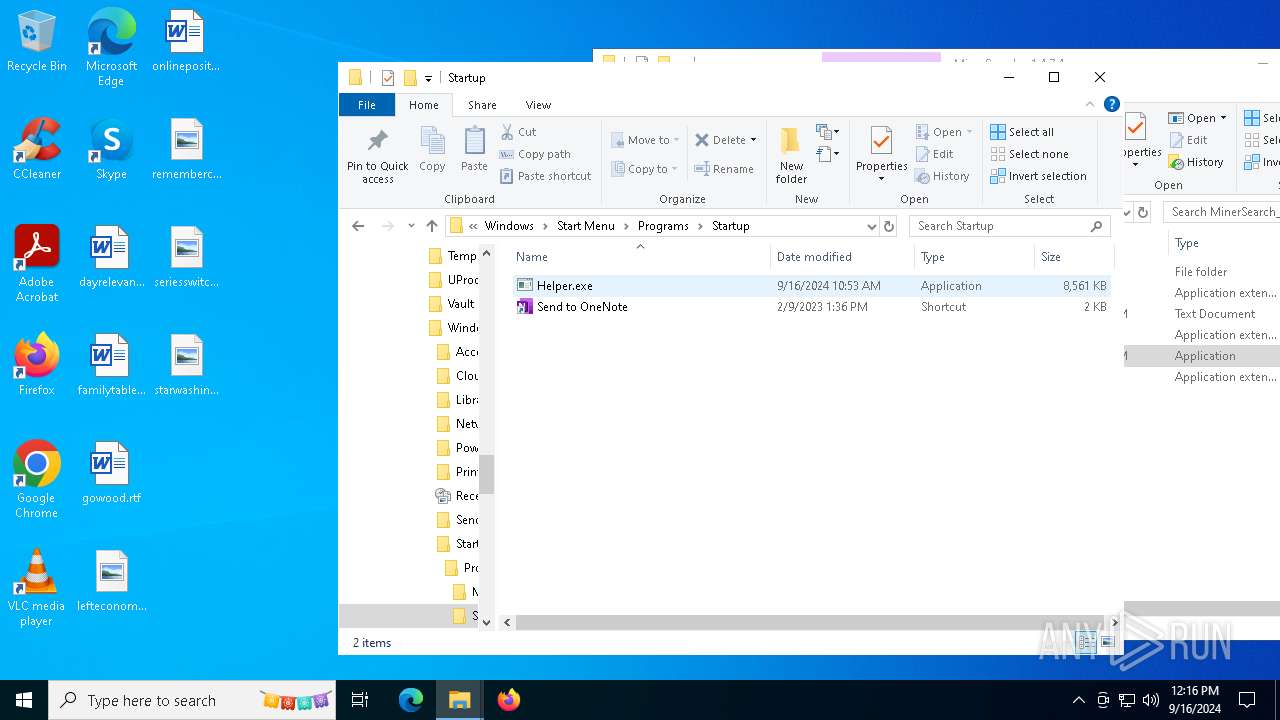
Executable content was dropped or overwritten
- WinRAR.exe (PID: 6812)
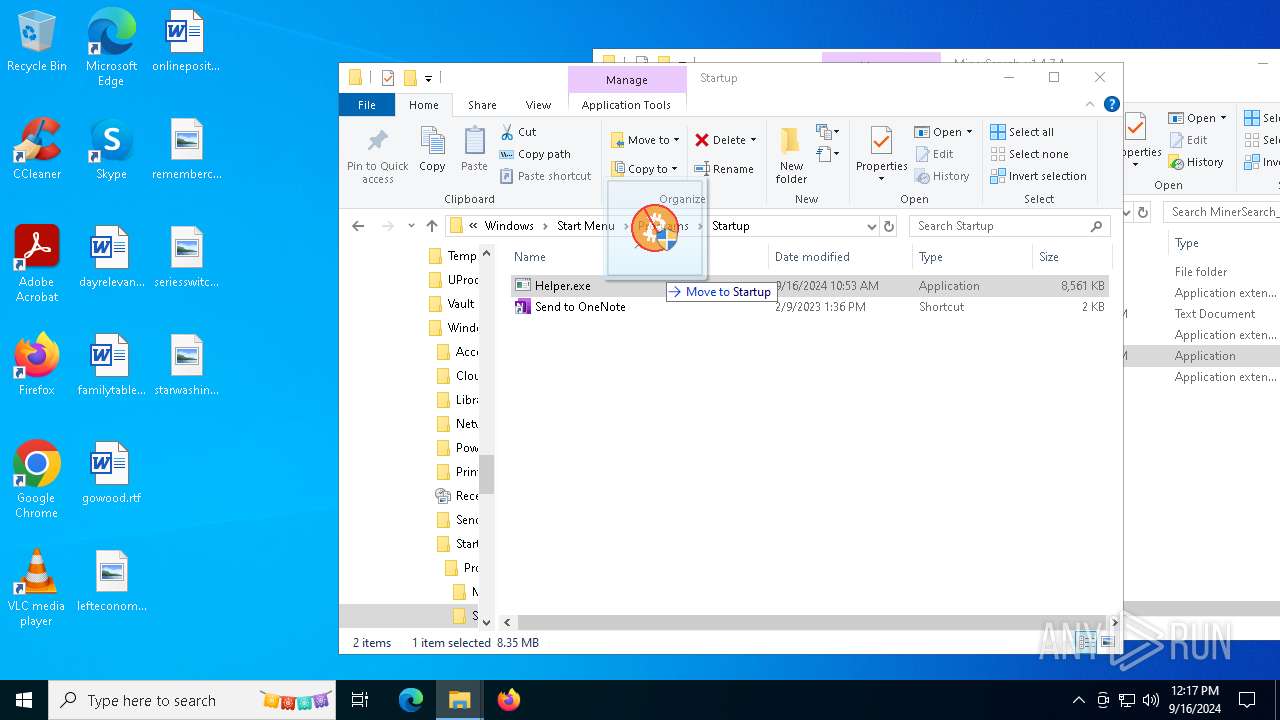
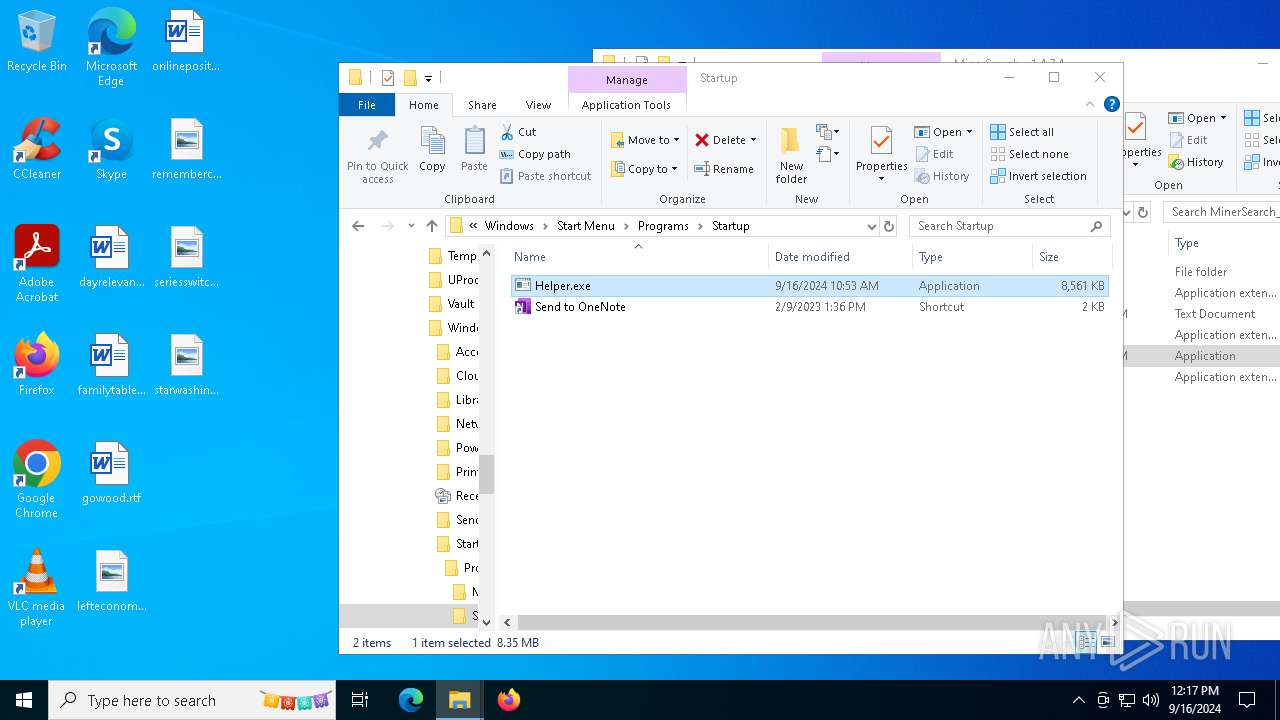
Manual execution by a user
- Helper.exe (PID: 2228)
- Helper.exe (PID: 1616)
- MinerSearch_v1.4.7.4.exe (PID: 6888)
- MinerSearch_v1.4.7.4.exe (PID: 2636)
- MinerSearch_v1.4.7.4.exe (PID: 4024)
- MinerSearch_v1.4.7.4.exe (PID: 7060)
- MinerSearch_v1.4.7.4.exe (PID: 6792)
- Helper.exe (PID: 6412)
- MinerSearch_v1.4.7.4.exe (PID: 1936)
Checks supported languages
- Helper.exe (PID: 1616)
- Helper.exe (PID: 2228)
- MinerSearch_v1.4.7.4.exe (PID: 2636)
Reads the computer name
- MinerSearch_v1.4.7.4.exe (PID: 2636)
Reads the machine GUID from the registry
- MinerSearch_v1.4.7.4.exe (PID: 2636)
Checks proxy server information
- MinerSearch_v1.4.7.4.exe (PID: 2636)
Creates files or folders in the user directory
- MinerSearch_v1.4.7.4.exe (PID: 2636)
Reads the software policy settings
- MinerSearch_v1.4.7.4.exe (PID: 2636)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
148
Monitored processes
14
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 884 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | MinerSearch_v1.4.7.4.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) | |||||||||||||||
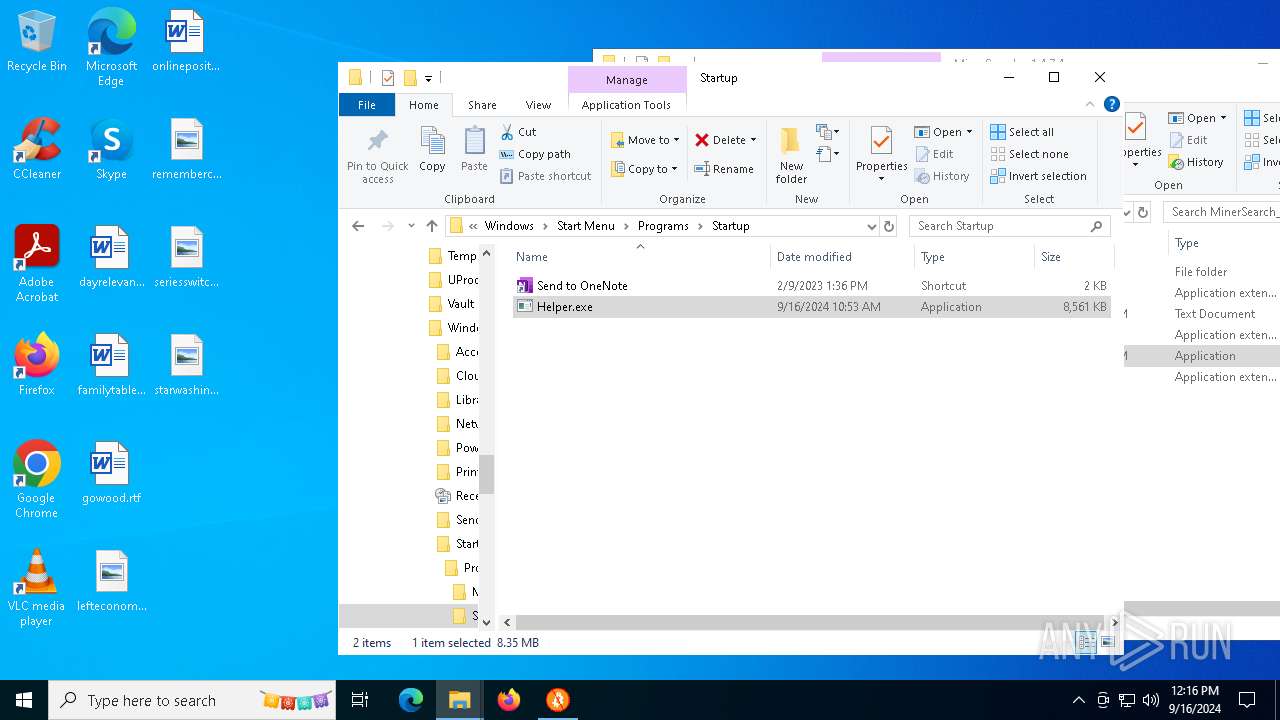
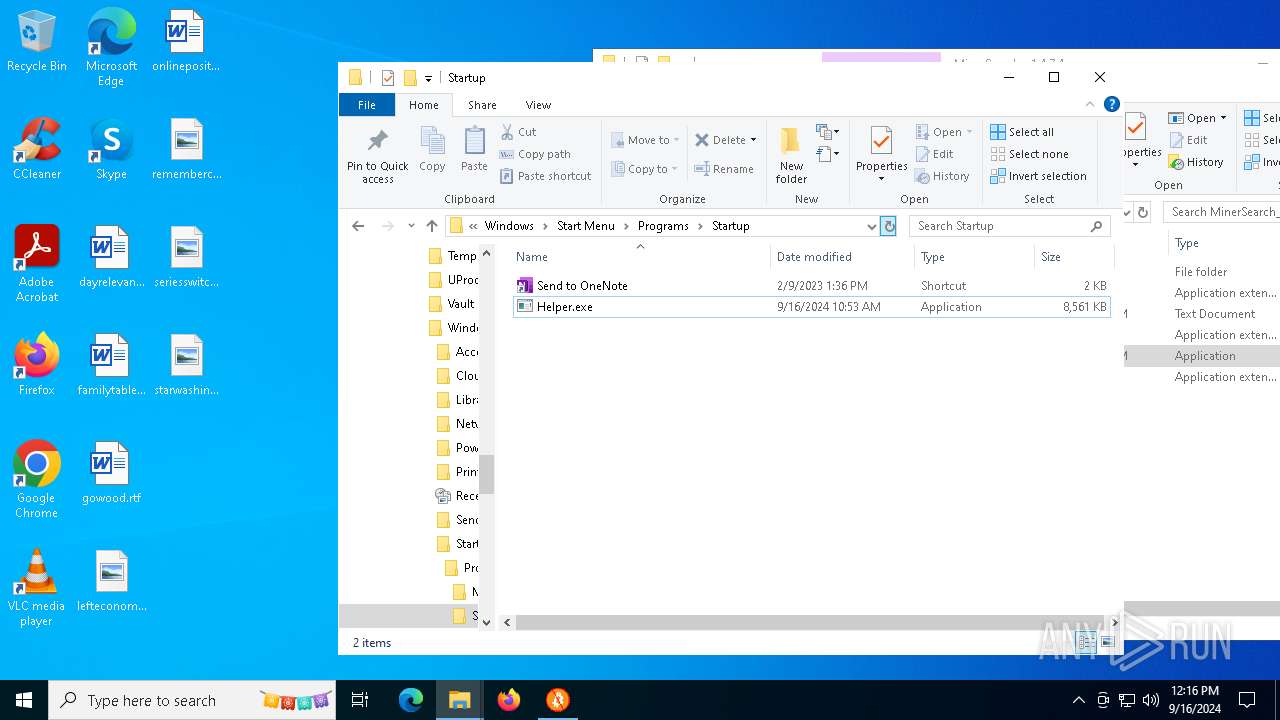
| 1616 | "C:\Users\admin\Desktop\MinerSearch_v1.4.7.4\Helper.exe" | C:\Users\admin\Desktop\MinerSearch_v1.4.7.4\Helper.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
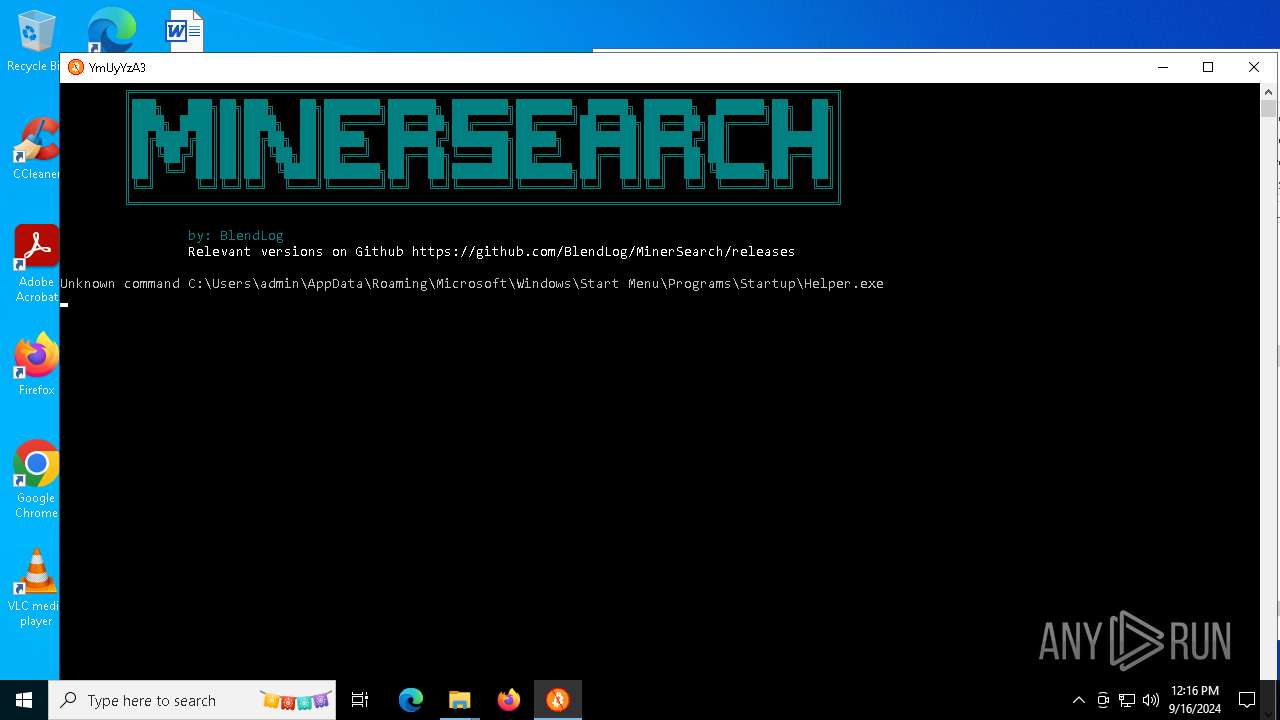
| 1936 | "C:\Users\admin\Desktop\MinerSearch_v1.4.7.4\MinerSearch_v1.4.7.4.exe" "C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\Helper.exe" | C:\Users\admin\Desktop\MinerSearch_v1.4.7.4\MinerSearch_v1.4.7.4.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Version: 1.4.7.4 | |||||||||||||||
| 2228 | "C:\Users\admin\Desktop\MinerSearch_v1.4.7.4\Helper.exe" | C:\Users\admin\Desktop\MinerSearch_v1.4.7.4\Helper.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 2636 | "C:\Users\admin\Desktop\MinerSearch_v1.4.7.4\MinerSearch_v1.4.7.4.exe" | C:\Users\admin\Desktop\MinerSearch_v1.4.7.4\MinerSearch_v1.4.7.4.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 3221225786 Version: 1.4.7.4 Modules
| |||||||||||||||
| 4024 | "C:\Users\admin\Desktop\MinerSearch_v1.4.7.4\MinerSearch_v1.4.7.4.exe" | C:\Users\admin\Desktop\MinerSearch_v1.4.7.4\MinerSearch_v1.4.7.4.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Version: 1.4.7.4 | |||||||||||||||
| 5940 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
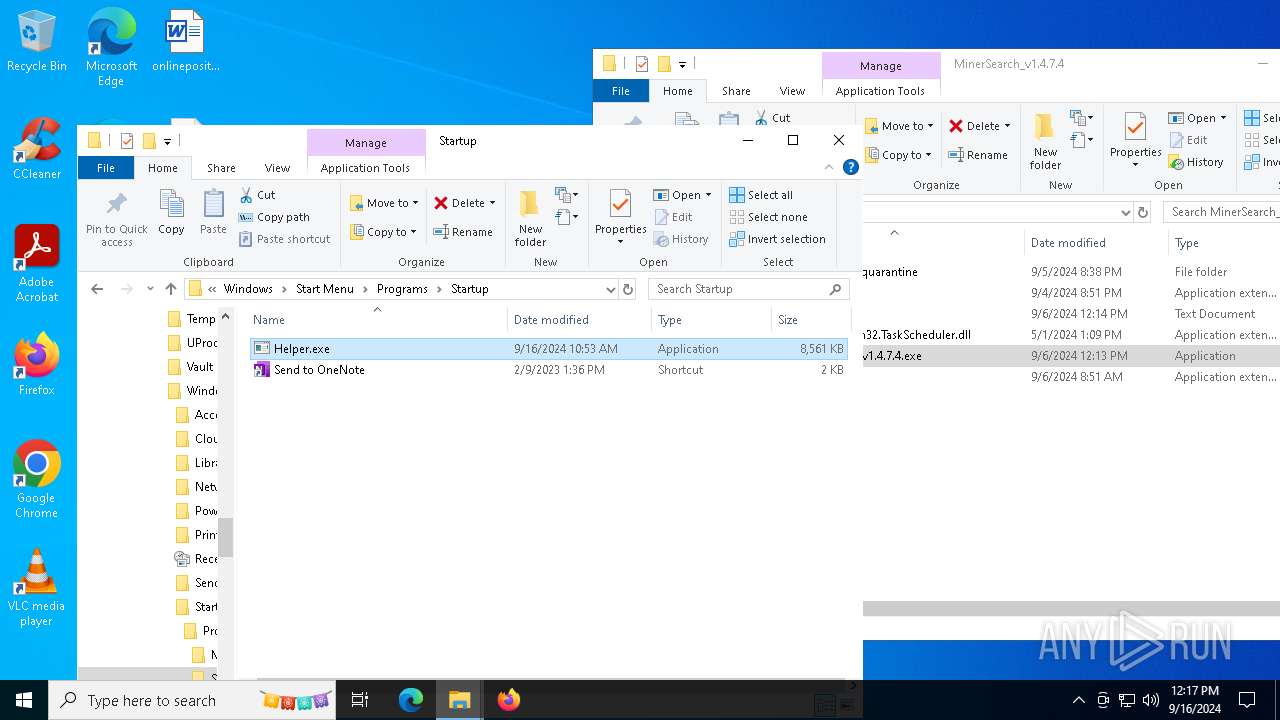
| 6412 | "C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\Helper.exe" C:\Users\admin\Desktop\MinerSearch_v1.4.7.4\MinerSearch_v1.4.7.4.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\Helper.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 | |||||||||||||||
| 6532 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | MinerSearch_v1.4.7.4.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6748 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | MinerSearch_v1.4.7.4.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) | |||||||||||||||
Total events
37 293
Read events
37 267
Write events
22
Delete events
4
Modification events
| (PID) Process: | (6812) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (6812) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\MinerSearch_v1.4.7.4.rar | |||
| (PID) Process: | (6812) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6812) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6812) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6812) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (6812) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF3D0000002D000000FD03000016020000 | |||
| (PID) Process: | (6812) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | name |
Value: 256 | |||
| (PID) Process: | (6812) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6812) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | psize |
Value: 80 | |||
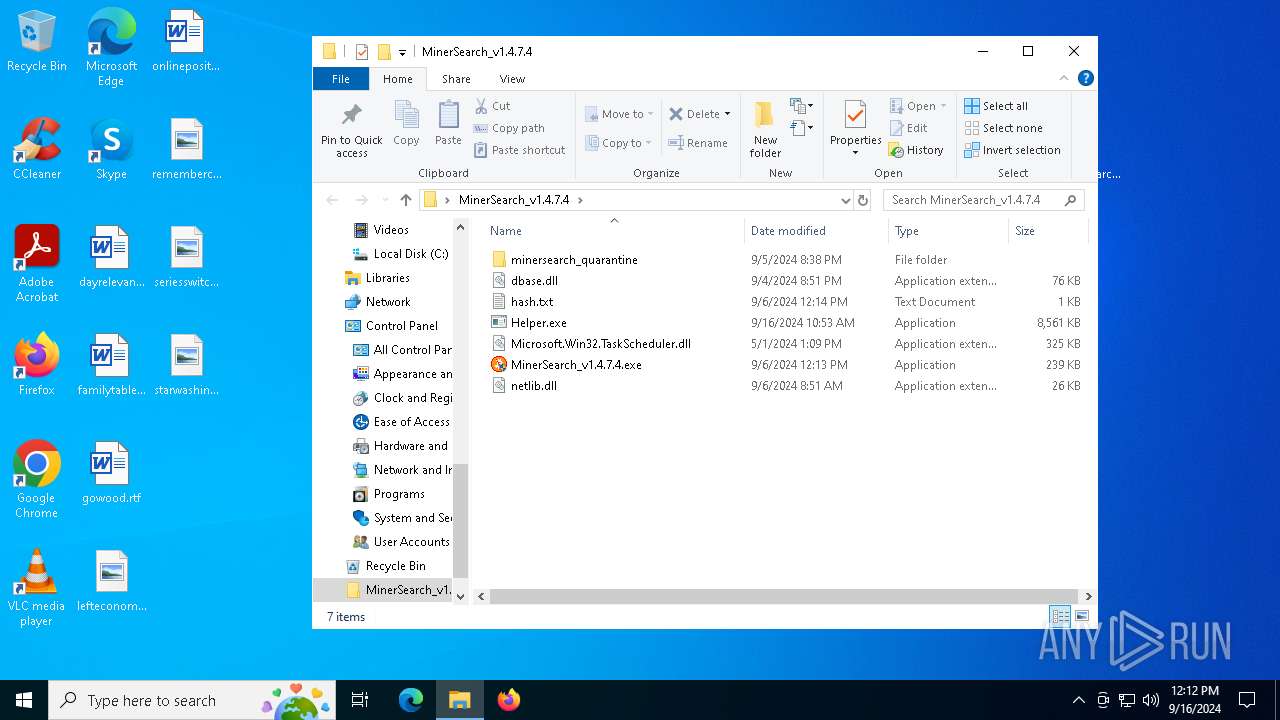
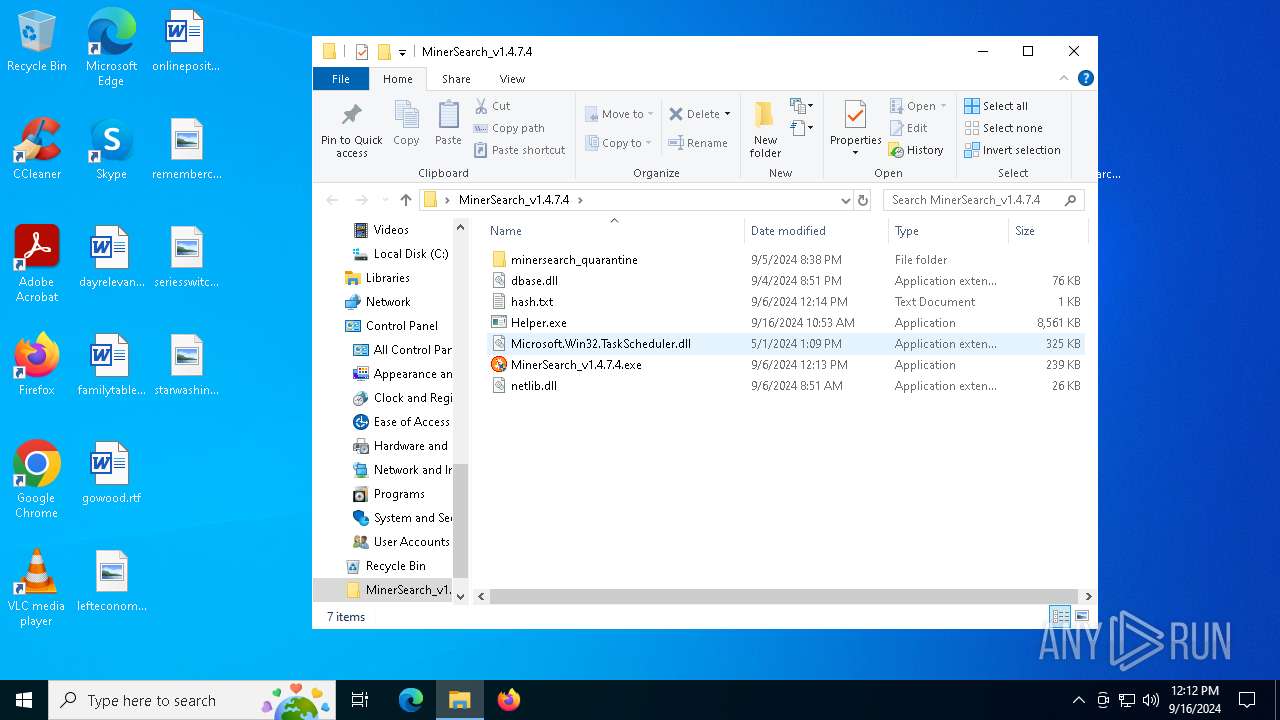
Executable files
5
Suspicious files
93
Text files
5
Unknown types
6
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
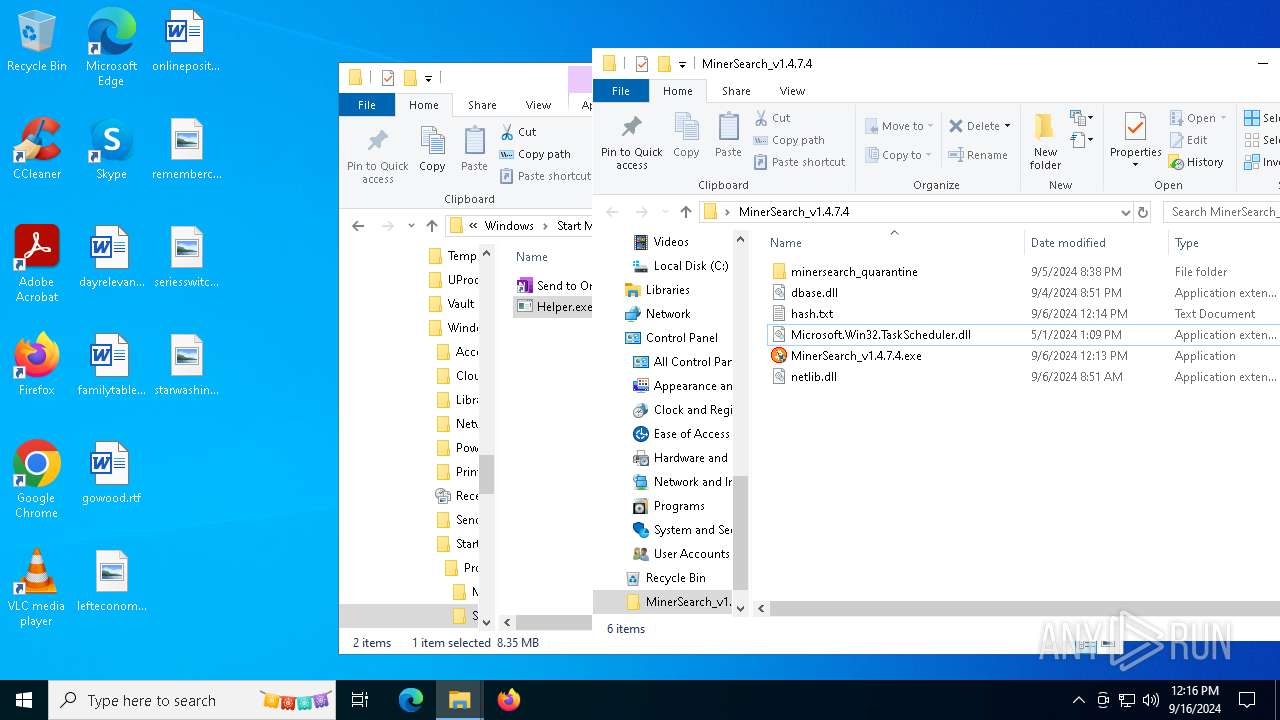
| 6812 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6812.7398\MinerSearch_v1.4.7.4\Helper.exe | executable | |
MD5:CFAC88EABC29939AD8FF9F63D4C83582 | SHA256:2A204312D040E59A12F75BB2558A69803F09FAF8CC50E8DBF71467CB728E8904 | |||
| 6812 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6812.7398\MinerSearch_v1.4.7.4\MinerSearch_v1.4.7.4.exe | executable | |
MD5:F7742D76E9EBCD8AEFB330D36F65C28F | SHA256:6D6922F898D93EBD76428E53BC01D0ED314F9D8F9E23A11B9708457C7BC6C15F | |||
| 6812 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6812.7398\MinerSearch_v1.4.7.4\netlib.dll | executable | |
MD5:E1F852BA7AD79847091EF8FF10B83421 | SHA256:B7427E4FD74BEEFE74C89B3DB66CDFCF674382DC80802C787E97FED23FD9259E | |||
| 6812 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6812.7398\MinerSearch_v1.4.7.4\Microsoft.Win32.TaskScheduler.dll | executable | |
MD5:0616EA42B68A8F5F2F01BCD985BDCBC7 | SHA256:EA27C65491119EEE5C8E87CE3D470783580DB8FC5BD141C496768D7D0CCE779A | |||
| 6812 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6812.7398\MinerSearch_v1.4.7.4\dbase.dll | executable | |
MD5:D3124D4AF1578F451BDA44BB6EE47E03 | SHA256:2BB837031E0A50E8F2BF82F1B2FD1DEE66DA1CD2D3BD21AEC5070C2E741293B7 | |||
| 2636 | MinerSearch_v1.4.7.4.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\2CD1F910DD5DC23C234E99A91DE345C0 | binary | |
MD5:B124797F4667D445AB9A6D6D768CDD38 | SHA256:DA8A12B2EAC6AB5647F35CD8541977C1C92C38D92468A36CA3A7EBC81D6847F4 | |||
| 6812 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6812.7398\MinerSearch_v1.4.7.4\hash.txt | text | |
MD5:0CF3D3E0FBB5AFD2CDCB07BAFEBC692B | SHA256:774094F9B7A937E33D65E75D50D29DB6AF3B6F3BE365236DE3DA2B4415844BEC | |||
| 2636 | MinerSearch_v1.4.7.4.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\A583E2A51BFBDC1E492A57B7C8325850 | der | |
MD5:C7D1234376F3389D6C220F0DCF24341B | SHA256:F67F7E62B47D1C4D9059F9F01FF40D52044EE81F594C5B8C8925C254381061E5 | |||
| 2636 | MinerSearch_v1.4.7.4.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\8EC9B1D0ABBD7F98B401D425828828CE_EB45B4DDD2CA201E87E40B2FB5245AEF | binary | |
MD5:E114BBAB17475825A5606C32D85D3080 | SHA256:B9A62AD7C8A58EEBC4328BCD1984F7AA5A74087C6B3572DA19137EBFE77A3EEE | |||
| 2636 | MinerSearch_v1.4.7.4.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\C8E534EE129F27D55460CE17FD628216_1130D9B25898B0DB0D4F04DC5B93F141 | binary | |
MD5:F03185BC64C23CAD1E0A66F8043CE11E | SHA256:BCE5DB3BFEB68CEE37FAAF580C4234ECA540055C547ACFB4327246C0EB70BEA5 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
62
TCP/UDP connections
63
DNS requests
34
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2636 | MinerSearch_v1.4.7.4.exe | GET | 200 | 23.48.23.143:80 | http://crl.microsoft.com/pki/crl/products/MicTimStaPCA_2010-07-01.crl | unknown | — | — | whitelisted |
2636 | MinerSearch_v1.4.7.4.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSRXerF0eFeSWRripTgTkcJWMm7iQQUaDfg67Y7%2BF8Rhvv%2BYXsIiGX0TkICEAV14ffsm9imej9hicY%2Bl7s%3D | unknown | — | — | whitelisted |
2636 | MinerSearch_v1.4.7.4.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTjzY2p9Pa8oibmj%2BNSMWsz63kmWgQUuhbZbU2FL3MpdpovdYxqII%2BeyG8CEAVEr%2FOUnQg5pr%2FbP1%2FlYRY%3D | unknown | — | — | whitelisted |
2636 | MinerSearch_v1.4.7.4.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSnR4FoxLLkI7vkvsUIFlZt%2BlGH3gQUWsS5eyoKo6XqcQPAYPkt9mV1DlgCEAkQWITrlZ07yLmU%2BRintu4%3D | unknown | — | — | whitelisted |
2636 | MinerSearch_v1.4.7.4.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBT3xL4LQLXDRDM9P665TW442vrsUQQUReuir%2FSSy4IxLVGLp6chnfNtyA8CEAQJGBtf1btmdVNDtW%2BVUAg%3D | unknown | — | — | whitelisted |
2636 | MinerSearch_v1.4.7.4.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBT3xL4LQLXDRDM9P665TW442vrsUQQUReuir%2FSSy4IxLVGLp6chnfNtyA8CEAqhJdbWMht%2BQeQF2jaXwhU%3D | unknown | — | — | whitelisted |
6012 | svchost.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6124 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
2036 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6124 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
6012 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6400 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2120 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
6012 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6012 | svchost.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
3260 | svchost.exe | 40.113.110.67:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2120 | MoUsoCoreWorker.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2036 | svchost.exe | 40.126.32.136:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
crl3.digicert.com |
| whitelisted |