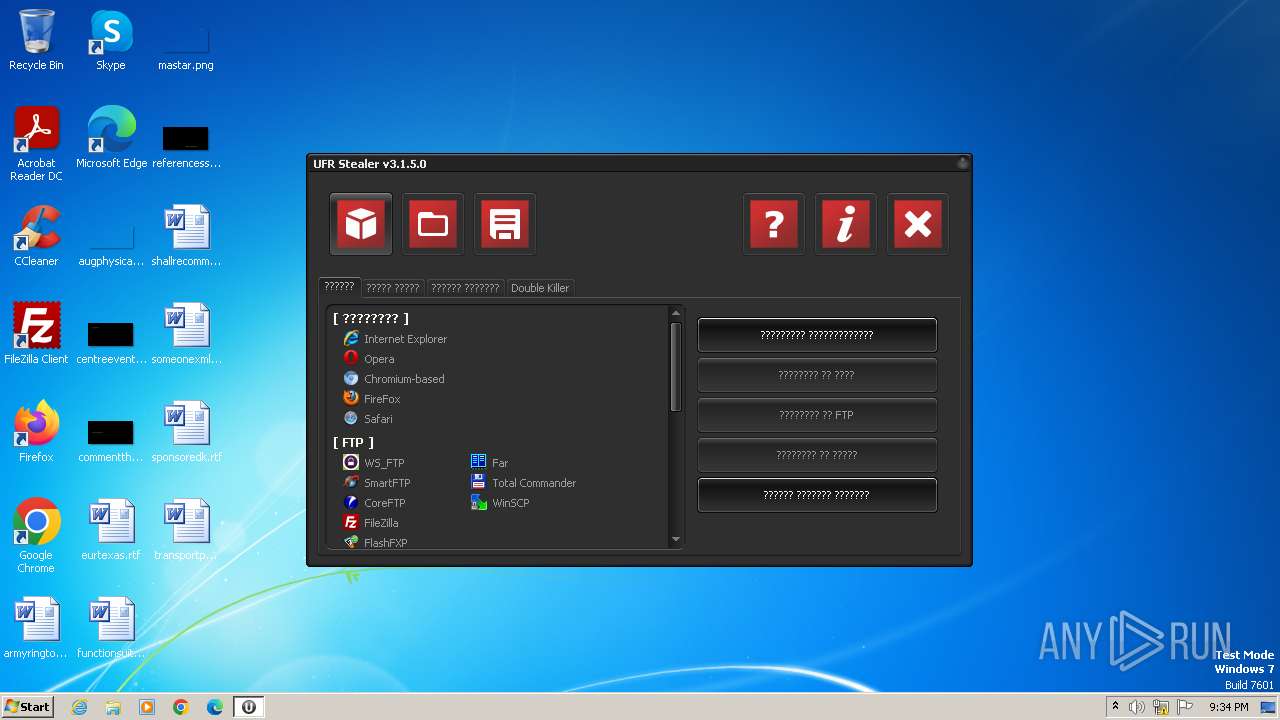
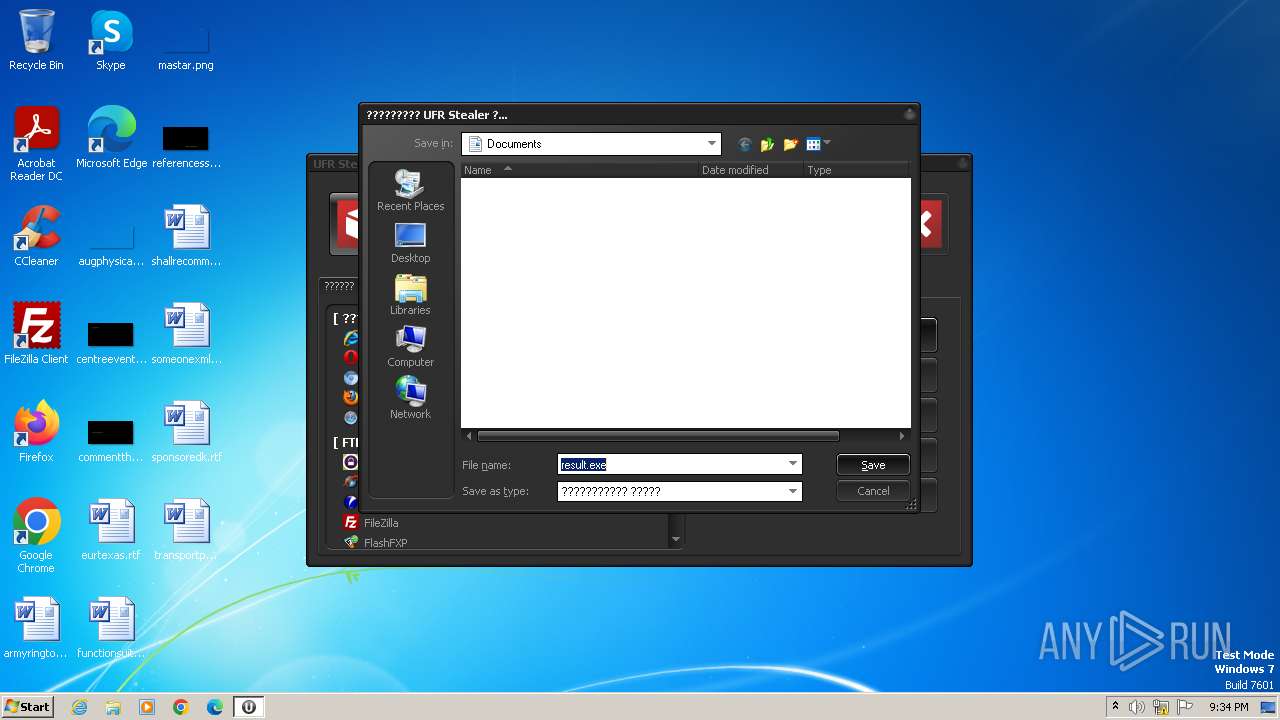
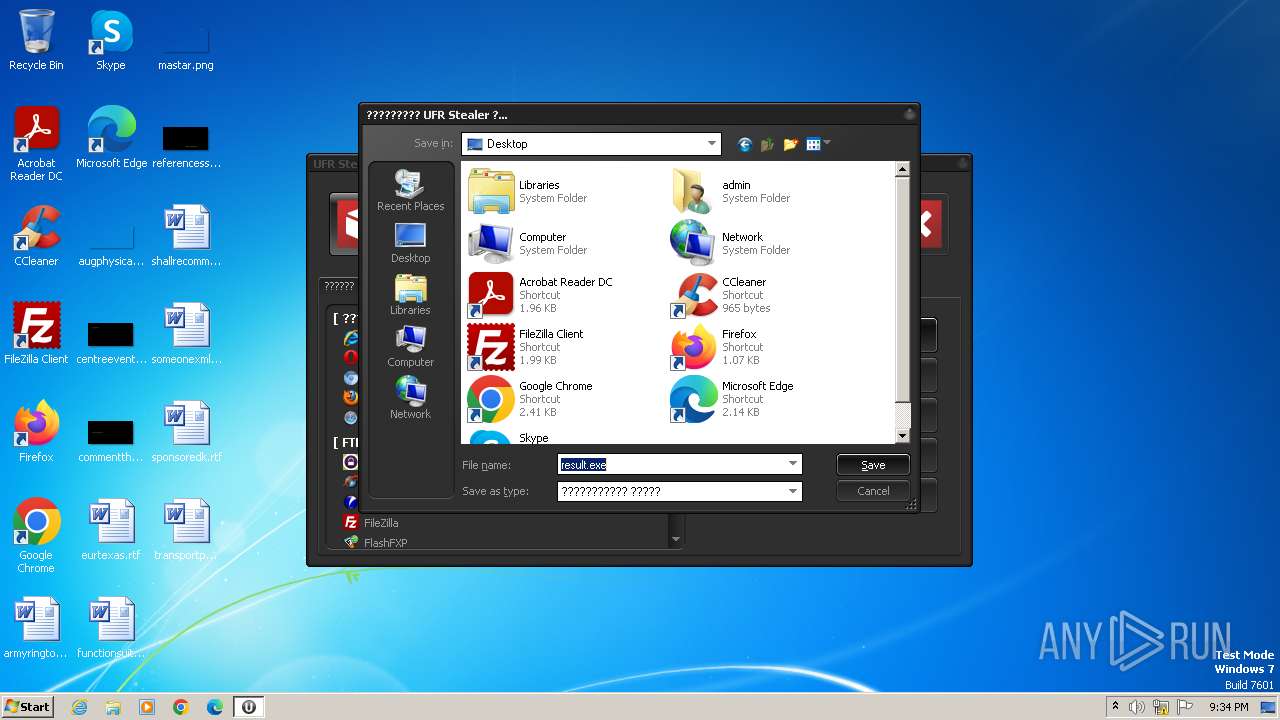
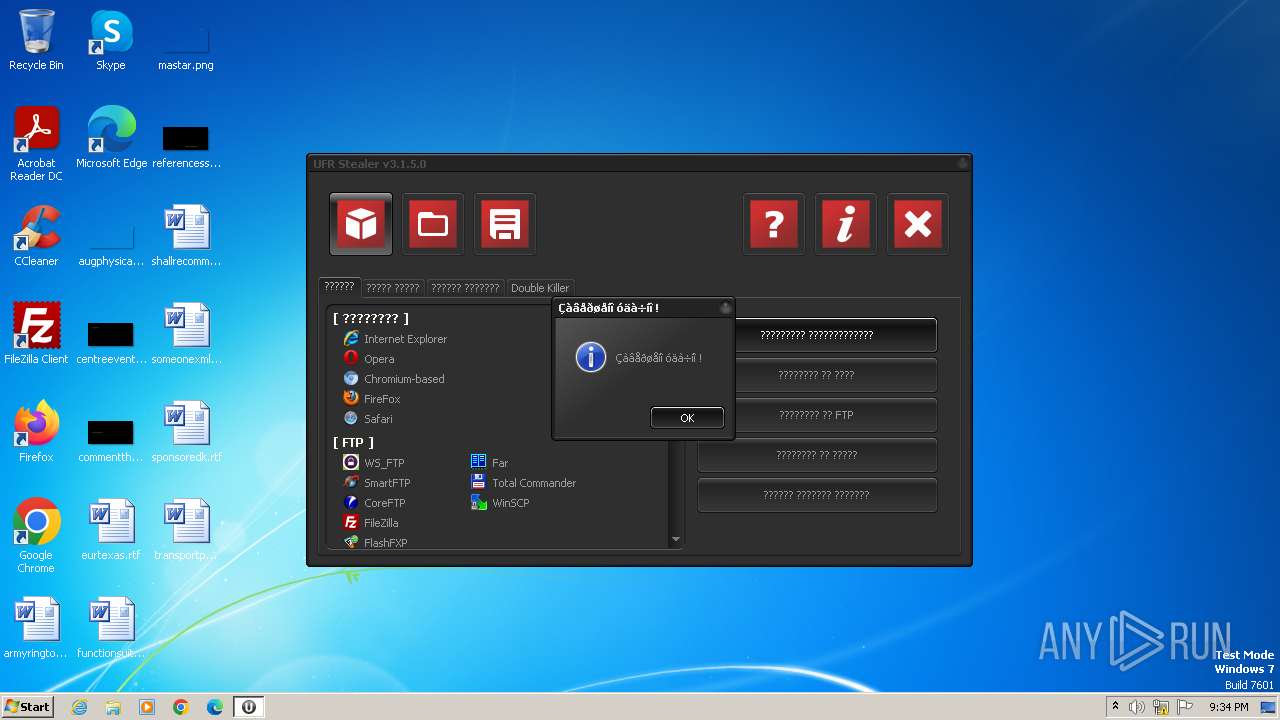
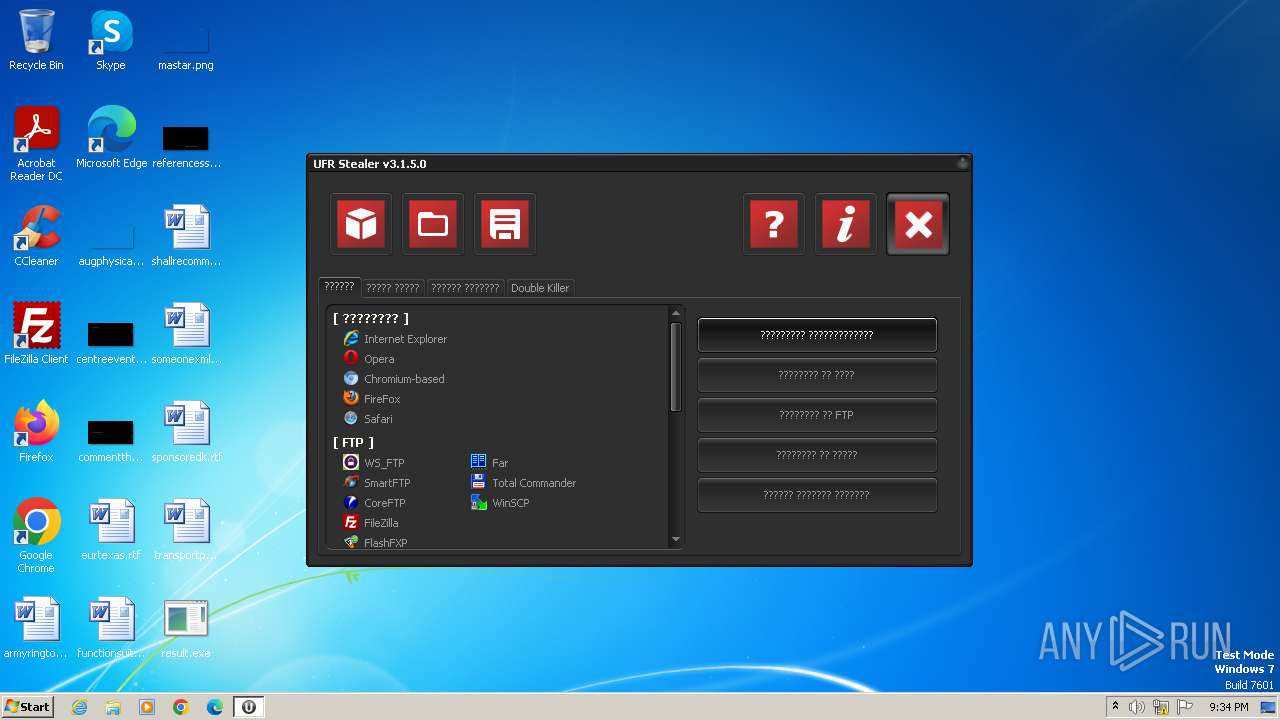
| File name: | UFR.exe |
| Full analysis: | https://app.any.run/tasks/795e8aa7-90e9-4e33-aa54-27f73e07d878 |
| Verdict: | Malicious activity |
| Analysis date: | December 02, 2023, 21:33:37 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, UPX compressed |
| MD5: | EB40B0FB8931A46620F4A42258969213 |
| SHA1: | BFD6E0931826144B4B24B83C4ABE244EEBD330C2 |
| SHA256: | B935A9835A07AD642FE157E5B57E75092124FEB750DA2E383EE16593760B747E |
| SSDEEP: | 49152:uX3QPpBIeSWELDyOspRzEh0Xn5WL8Hjv/tvuixnbYOc8z2PqgWA0Il55qy/qPj6R:uX3QPpBIenEfy/03L8HD/tvugbBcDyJC |
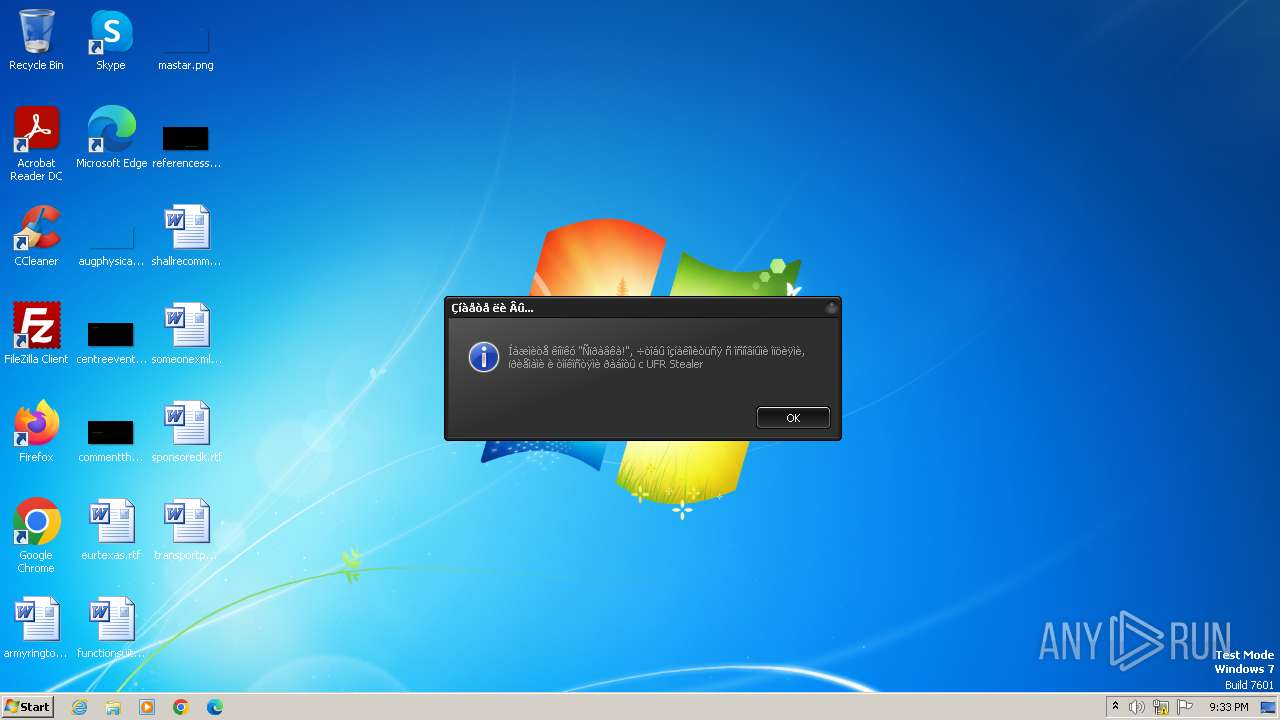
MALICIOUS
Drops the executable file immediately after the start
- UFR.exe (PID: 844)
- upx.exe (PID: 280)
- result.exe (PID: 3784)
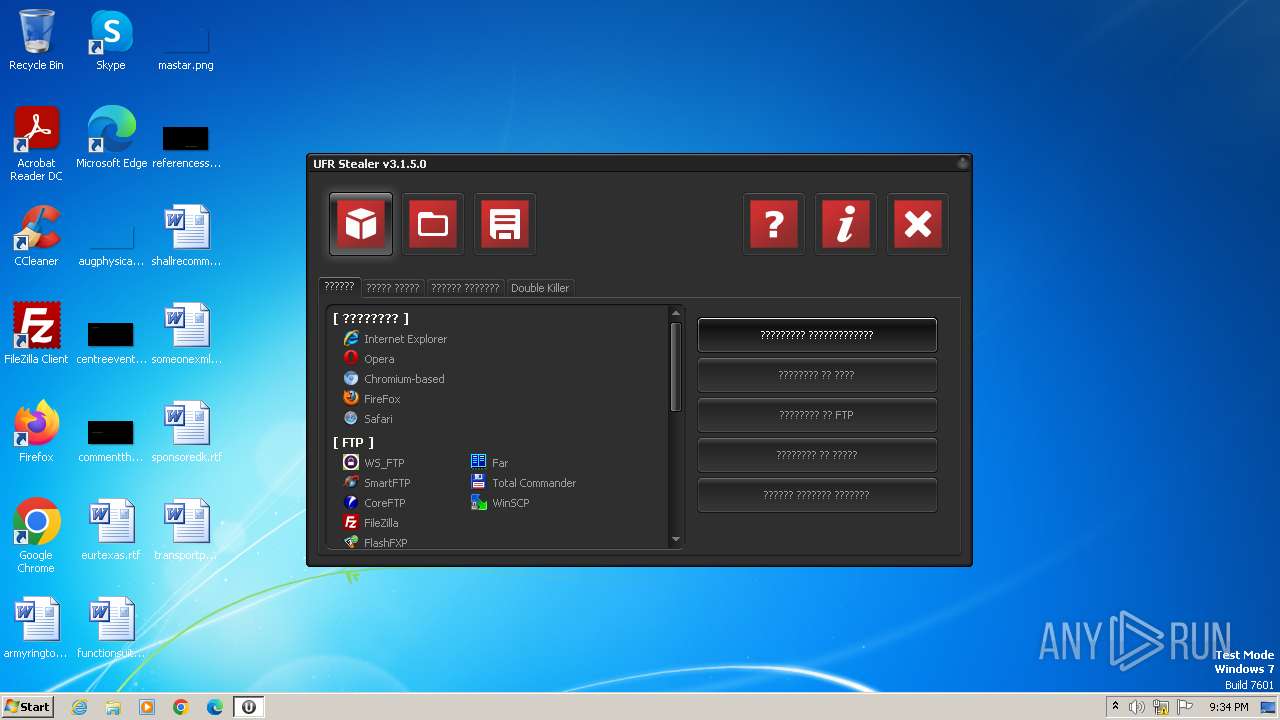
Steals credentials from Web Browsers
- result.exe (PID: 2084)
Actions looks like stealing of personal data
- result.exe (PID: 2084)
SUSPICIOUS
Reads the Internet Settings
- UFR.exe (PID: 844)
- result.exe (PID: 2084)
Starts itself from another location
- result.exe (PID: 3784)
Searches for installed software
- result.exe (PID: 2084)
Loads DLL from Mozilla Firefox
- result.exe (PID: 2084)
Reads Mozilla Firefox installation path
- result.exe (PID: 2084)
INFO
Reads the machine GUID from the registry
- UFR.exe (PID: 844)
- result.exe (PID: 2084)
Reads the computer name
- UFR.exe (PID: 844)
- result.exe (PID: 2084)
Checks supported languages
- UFR.exe (PID: 844)
- result.exe (PID: 3784)
- upx.exe (PID: 280)
- result.exe (PID: 2084)
Manual execution by a user
- result.exe (PID: 3784)
Create files in a temporary directory
- upx.exe (PID: 280)
- UFR.exe (PID: 844)
- result.exe (PID: 3784)
- result.exe (PID: 2084)
Reads Windows Product ID
- result.exe (PID: 2084)
Reads CPU info
- result.exe (PID: 2084)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | UPX compressed Win32 Executable (38.2) |
|---|---|---|
| .exe | | | Win32 EXE Yoda's Crypter (37.5) |
| .dll | | | Win32 Dynamic Link Library (generic) (9.2) |
| .exe | | | Win32 Executable (generic) (6.3) |
| .exe | | | Win16/32 Executable Delphi generic (2.9) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 1992:06:20 00:22:17+02:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, Bytes reversed lo, 32-bit, Bytes reversed hi |
| PEType: | PE32 |
| LinkerVersion: | 2.25 |
| CodeSize: | 1015808 |
| InitializedDataSize: | 24576 |
| UninitializedDataSize: | 1511424 |
| EntryPoint: | 0x269c00 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 3.1.5.0 |
| ProductVersionNumber: | 3.1.5.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Russian |
| CharacterSet: | Windows, Cyrillic |
| CompanyName: | VaZoNeZ Corp. |
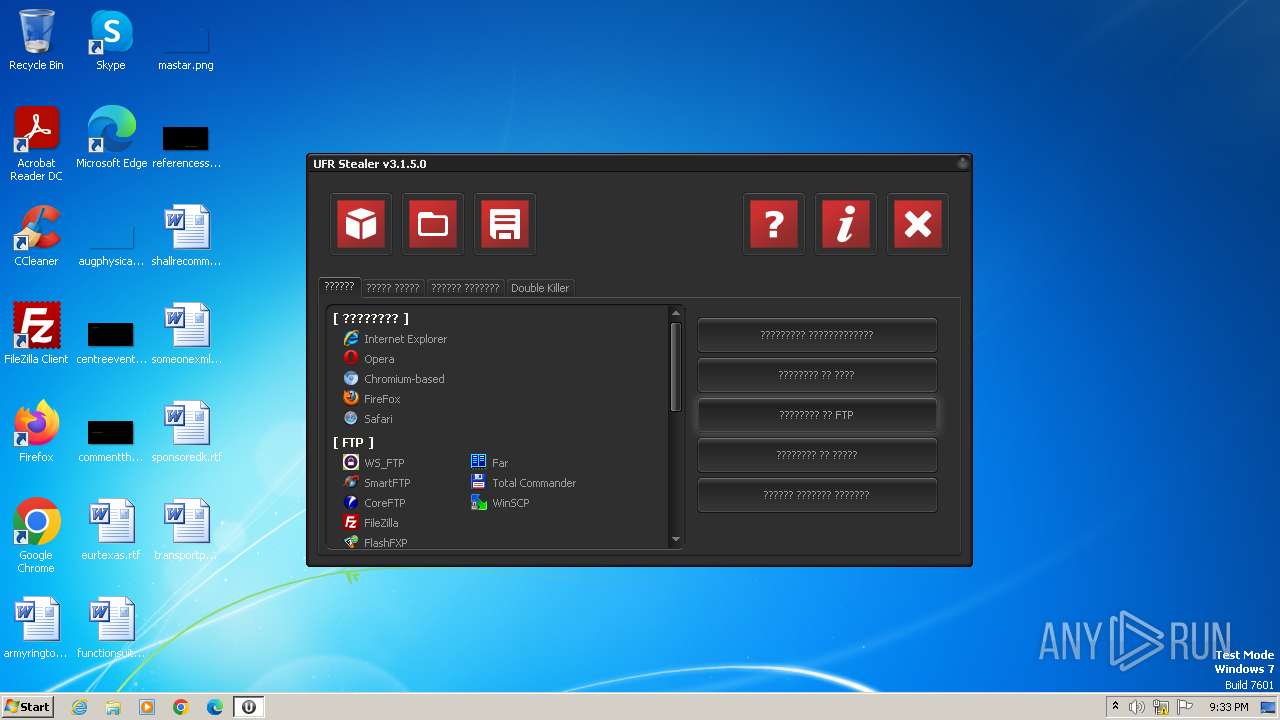
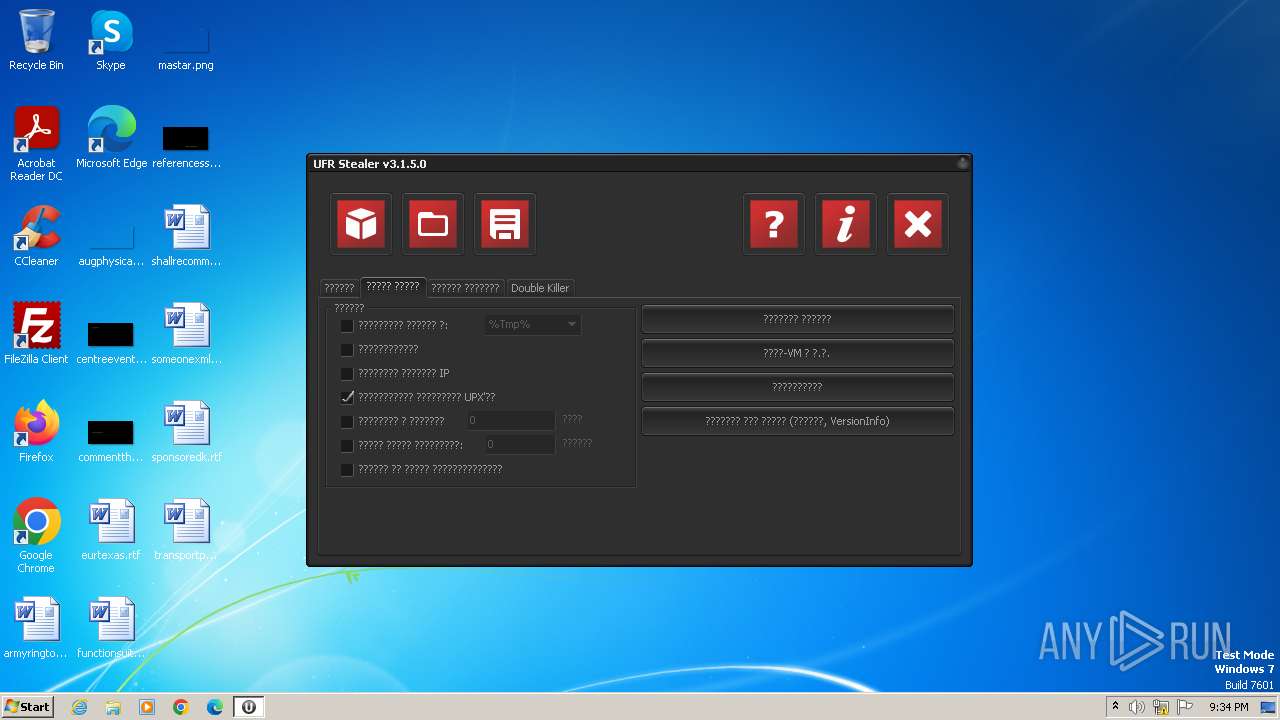
| FileDescription: | UFR Stealer |
| FileVersion: | 3.1.5.0 |
| InternalName: | UFR Stealer |
| LegalCopyright: | Copyrights doomed! |
| LegalTrademarks: | Fuck |
| OriginalFileName: | UFR Stealer |
| ProductName: | UFR Stealer |
| ProductVersion: | 3.1.5.0 |
Total processes
41
Monitored processes
4
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 280 | "C:\Users\admin\AppData\Local\Temp\upx.exe" -9 -opacked_ufr.exe "C:\Users\admin\Desktop\result.exe" | C:\Users\admin\AppData\Local\Temp\upx.exe | — | UFR.exe | |||||||||||
User: admin Company: The UPX Team http://upx.sf.net Integrity Level: MEDIUM Description: UPX executable packer Exit code: 0 Version: 3.08 (2011-12-12) Modules
| |||||||||||||||
| 844 | "C:\Users\admin\AppData\Local\Temp\UFR.exe" | C:\Users\admin\AppData\Local\Temp\UFR.exe | — | explorer.exe | |||||||||||
User: admin Company: VaZoNeZ Corp. Integrity Level: MEDIUM Description: UFR Stealer Exit code: 0 Version: 3.1.5.0 Modules
| |||||||||||||||
| 2084 | "C:\Users\admin\AppData\Local\Temp\result.exe" | C:\Users\admin\AppData\Local\Temp\result.exe | result.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 3784 | "C:\Users\admin\Desktop\result.exe" | C:\Users\admin\Desktop\result.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
Total events
2 746
Read events
2 698
Write events
47
Delete events
1
Modification events
| (PID) Process: | (844) UFR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\17F\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (844) UFR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | NodeSlots |
Value: 0202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202 | |||
| (PID) Process: | (844) UFR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | MRUListEx |
Value: 07000000020000000100000000000000060000000C0000000B0000000D0000000A0000000900000008000000030000000500000004000000FFFFFFFF | |||
| (PID) Process: | (844) UFR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | MRUListEx |
Value: 02000000070000000100000000000000060000000C0000000B0000000D0000000A0000000900000008000000030000000500000004000000FFFFFFFF | |||
| (PID) Process: | (844) UFR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\50\ComDlgLegacy |
| Operation: | write | Name: | TV_FolderType |
Value: {FBB3477E-C9E4-4B3B-A2BA-D3F5D3CD46F9} | |||
| (PID) Process: | (844) UFR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\50\ComDlgLegacy |
| Operation: | write | Name: | TV_TopViewID |
Value: {82BA0782-5B7A-4569-B5D7-EC83085F08CC} | |||
| (PID) Process: | (844) UFR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\50\ComDlgLegacy |
| Operation: | write | Name: | TV_TopViewVersion |
Value: 0 | |||
| (PID) Process: | (844) UFR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\AllFolders\ComDlgLegacy\{FBB3477E-C9E4-4B3B-A2BA-D3F5D3CD46F9}\{82BA0782-5B7A-4569-B5D7-EC83085F08CC} |
| Operation: | write | Name: | Mode |
Value: 4 | |||
| (PID) Process: | (844) UFR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\AllFolders\ComDlgLegacy\{FBB3477E-C9E4-4B3B-A2BA-D3F5D3CD46F9}\{82BA0782-5B7A-4569-B5D7-EC83085F08CC} |
| Operation: | write | Name: | LogicalViewMode |
Value: 1 | |||
| (PID) Process: | (844) UFR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\AllFolders\ComDlgLegacy\{FBB3477E-C9E4-4B3B-A2BA-D3F5D3CD46F9}\{82BA0782-5B7A-4569-B5D7-EC83085F08CC} |
| Operation: | write | Name: | FFlags |
Value: 1 | |||
Executable files
8
Suspicious files
4
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 844 | UFR.exe | C:\Users\admin\Desktop\RCXE5C0.tmp | executable | |
MD5:A459373F3C9EC0EAAF3725D4A253EAB3 | SHA256:AEAF0DC84FA3AB2D5F0D2F2D4B3DFF5CB6C7F1F21CD1C5759ADD1EE4AC2FFAE8 | |||
| 2084 | result.exe | C:\Users\admin\AppData\Local\Temp\report_02-12-2023_21-34-26-A39FF9DD32F770EC588100CE56A74336-IIIB.bin | binary | |
MD5:8E2E5EE3F5D9D83FB4B812233DB9A954 | SHA256:BF517AEDA24F7C0A17E7056E74AC1E409ACD9B98EA8E1D078E935481C552B9AC | |||
| 844 | UFR.exe | C:\Users\admin\Desktop\RCXE5C1.tmp | executable | |
MD5:61657CDAC975295C74F830EF569455CD | SHA256:0BC9E331BDDB81A75FEA4631F8779E3E1A05C3289EA2D73C64DBA745F6017FB1 | |||
| 3784 | result.exe | C:\Users\admin\AppData\Local\Temp\result.exe | executable | |
MD5:DAC8460D77767AB1696D2740D57B4908 | SHA256:92A238249F2291FFF54D80BC58F0139ADAD1726A6B81207BF1079DAC1DCB534B | |||
| 2084 | result.exe | C:\Users\admin\AppData\Local\Temp\NO_PWDS_report_02-12-2023_21-34-26-A39FF9DD32F770EC588100CE56A74336-IIIB.bin | binary | |
MD5:8E2E5EE3F5D9D83FB4B812233DB9A954 | SHA256:BF517AEDA24F7C0A17E7056E74AC1E409ACD9B98EA8E1D078E935481C552B9AC | |||
| 844 | UFR.exe | C:\Users\admin\AppData\Local\Temp\upx.exe | executable | |
MD5:FFA637ABD482B5E7D3FB75182F43F080 | SHA256:4D3D363B5B3DCD9FA516B481C92D62C02AED804318BDC4D5E97A68BB6E6D62DB | |||
| 844 | UFR.exe | C:\Users\admin\AppData\Local\Temp\ufr_build | binary | |
MD5:04DD44403C324911E8A9EF482D1C9429 | SHA256:5F2C7EF0E1EA2FCB760AEB1100842DE30BAA770A7F036C61C7C7151063EB379C | |||
| 2084 | result.exe | C:\Users\admin\AppData\Local\Temp\ufr_reports\NO_PWDS_report_02-12-2023_21-34-26-A39FF9DD32F770EC588100CE56A74336-IIIB.bin | binary | |
MD5:5CCC6F6705C79AEC24CF57E6DF1E1439 | SHA256:909337830E2BB951D82BCA64DD8CFF8EF285968A8D6701DEA5A59FACC612D924 | |||
| 844 | UFR.exe | C:\Users\admin\Desktop\result.exe | executable | |
MD5:CFA6664E8258848B1019F12B80BFD7AA | SHA256:8FDC0CF562B7D92F17A0830346341877A20FC4563B91960D5446A1BAF58000CD | |||
| 280 | upx.exe | C:\Users\admin\AppData\Local\Temp\packed_ufr.exe | executable | |
MD5:43513E2DEA64E8E8A508C9ABB82F665F | SHA256:00BA3257D750733156D50B02C4FA964C7EA1EBFEDBA4B67ABDC2F8E5B8E6DC59 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
4
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2588 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |