| File name: | b92c4f3b24c0772241f5ec985be12c3070858c0922155ff6d2c88410a593a5b0.exe |
| Full analysis: | https://app.any.run/tasks/4c833114-d633-413d-a8fb-faab497eee86 |
| Verdict: | Malicious activity |
| Analysis date: | July 13, 2024, 11:49:17 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32+ executable (console) x86-64, for MS Windows |
| MD5: | 9EF88513C03FE6F865123205CCC83097 |
| SHA1: | BE1D9D7F4AA6F4FE7BC111A72EDCF972F8A6360F |
| SHA256: | B92C4F3B24C0772241F5EC985BE12C3070858C0922155FF6D2C88410A593A5B0 |
| SSDEEP: | 6144:pG6vHVnWtVwq4H1H64RJrWTG1KlKrhBKS9ZckukOLXoK2AH:p1vtPbH6AruG1KlKrhYS9ikukOboK2A |
MALICIOUS
Drops the executable file immediately after the start
- b92c4f3b24c0772241f5ec985be12c3070858c0922155ff6d2c88410a593a5b0.exe (PID: 4600)
SUSPICIOUS
Reads the date of Windows installation
- b92c4f3b24c0772241f5ec985be12c3070858c0922155ff6d2c88410a593a5b0.exe (PID: 4600)
Reads security settings of Internet Explorer
- b92c4f3b24c0772241f5ec985be12c3070858c0922155ff6d2c88410a593a5b0.exe (PID: 4600)
Likely accesses (executes) a file from the Public directory
- WINWORD.EXE (PID: 4724)
Connects to the server without a host name
- b92c4f3b24c0772241f5ec985be12c3070858c0922155ff6d2c88410a593a5b0.exe (PID: 4600)
Connects to unusual port
- b92c4f3b24c0772241f5ec985be12c3070858c0922155ff6d2c88410a593a5b0.exe (PID: 4600)
INFO
Checks proxy server information
- b92c4f3b24c0772241f5ec985be12c3070858c0922155ff6d2c88410a593a5b0.exe (PID: 4600)
Process checks computer location settings
- b92c4f3b24c0772241f5ec985be12c3070858c0922155ff6d2c88410a593a5b0.exe (PID: 4600)
Reads Microsoft Office registry keys
- b92c4f3b24c0772241f5ec985be12c3070858c0922155ff6d2c88410a593a5b0.exe (PID: 4600)
Checks supported languages
- b92c4f3b24c0772241f5ec985be12c3070858c0922155ff6d2c88410a593a5b0.exe (PID: 4600)
Reads the computer name
- b92c4f3b24c0772241f5ec985be12c3070858c0922155ff6d2c88410a593a5b0.exe (PID: 4600)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (87.3) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (6.3) |
| .exe | | | DOS Executable Generic (6.3) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2024:07:09 09:25:46+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 14.16 |
| CodeSize: | 252928 |
| InitializedDataSize: | 303616 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x1c24c |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows command line |
Total processes
128
Monitored processes
3
Malicious processes
0
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2220 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | b92c4f3b24c0772241f5ec985be12c3070858c0922155ff6d2c88410a593a5b0.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4600 | "C:\Users\admin\Desktop\b92c4f3b24c0772241f5ec985be12c3070858c0922155ff6d2c88410a593a5b0.exe" | C:\Users\admin\Desktop\b92c4f3b24c0772241f5ec985be12c3070858c0922155ff6d2c88410a593a5b0.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 1 Modules
| |||||||||||||||
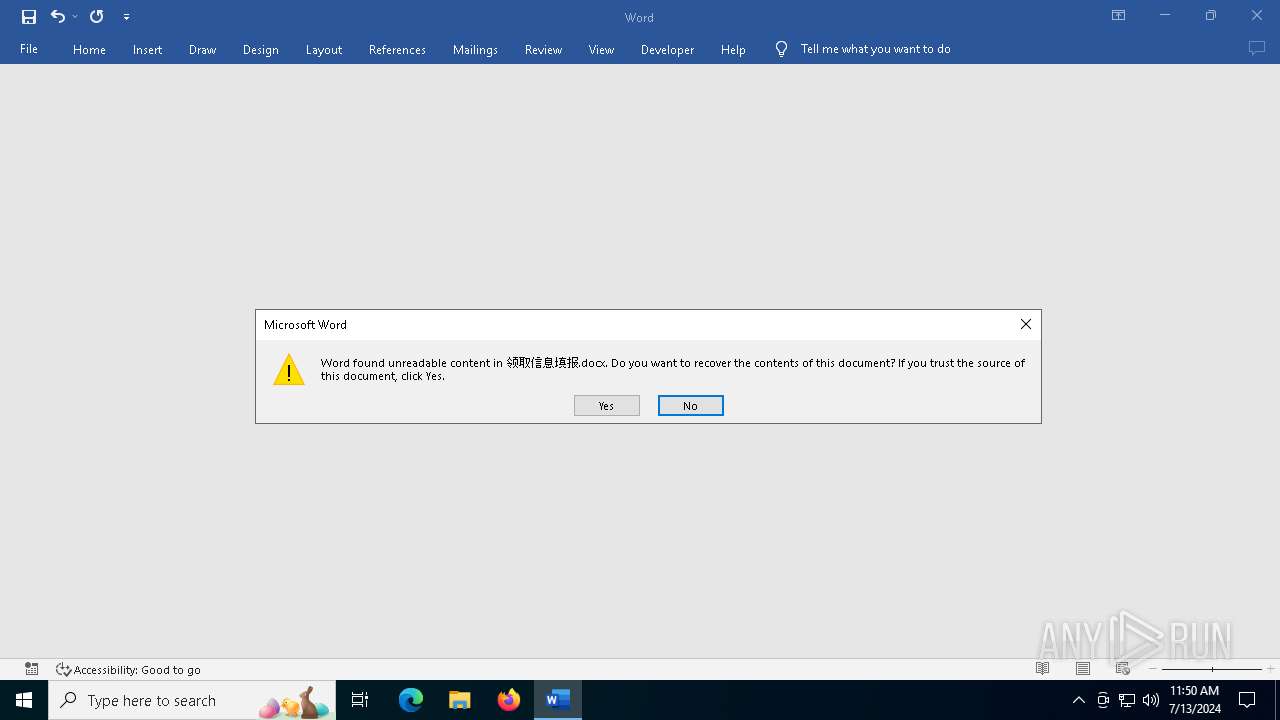
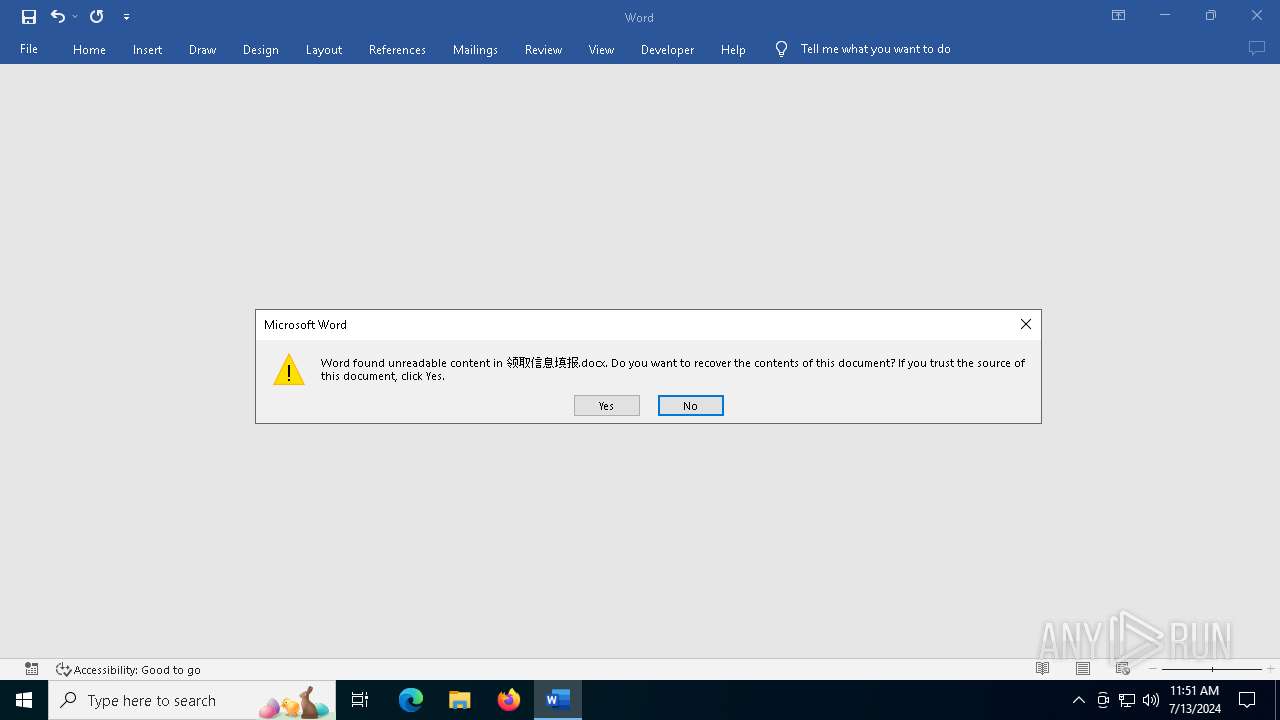
| 4724 | "C:\Program Files\Microsoft Office\Root\Office16\WINWORD.EXE" /n "C:\Users\Public\领取信息填报.docx" /o "" | C:\Program Files\Microsoft Office\root\Office16\WINWORD.EXE | b92c4f3b24c0772241f5ec985be12c3070858c0922155ff6d2c88410a593a5b0.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Version: 16.0.16026.20146 Modules
| |||||||||||||||
Total events
11 219
Read events
10 969
Write events
242
Delete events
8
Modification events
| (PID) Process: | (4600) b92c4f3b24c0772241f5ec985be12c3070858c0922155ff6d2c88410a593a5b0.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (4600) b92c4f3b24c0772241f5ec985be12c3070858c0922155ff6d2c88410a593a5b0.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (4600) b92c4f3b24c0772241f5ec985be12c3070858c0922155ff6d2c88410a593a5b0.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (4600) b92c4f3b24c0772241f5ec985be12c3070858c0922155ff6d2c88410a593a5b0.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (4600) b92c4f3b24c0772241f5ec985be12c3070858c0922155ff6d2c88410a593a5b0.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (4600) b92c4f3b24c0772241f5ec985be12c3070858c0922155ff6d2c88410a593a5b0.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (4600) b92c4f3b24c0772241f5ec985be12c3070858c0922155ff6d2c88410a593a5b0.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (4600) b92c4f3b24c0772241f5ec985be12c3070858c0922155ff6d2c88410a593a5b0.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.docx\OpenWithProgids |
| Operation: | write | Name: | Word.Document.12 |
Value: | |||
| (PID) Process: | (4600) b92c4f3b24c0772241f5ec985be12c3070858c0922155ff6d2c88410a593a5b0.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Shell Extensions\Cached |
| Operation: | write | Name: | {5985FC23-2588-4D9A-B38B-7E7AFFAB3155} {886D8EEB-8CF2-4446-8D02-CDBA1DBDCF99} 0xFFFF |
Value: 010000000000000023816CB61AD5DA01 | |||
| (PID) Process: | (4600) b92c4f3b24c0772241f5ec985be12c3070858c0922155ff6d2c88410a593a5b0.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\3c\52C64B7E |
| Operation: | write | Name: | @C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\Office16\oregres.dll,-205 |
Value: Word | |||
Executable files
0
Suspicious files
5
Text files
4
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4724 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\WebServiceCache\AllUsers\officeclient.microsoft.com\D1B7648C-9CEA-41D7-8AFB-D782F1FCB661 | xml | |
MD5:774FBCCCEEB2A6E85CA080E4BC9F22C3 | SHA256:24003B97AF0A31CBAA2097286F003698CCAF513A5276862A118A7EB0D3A9127D | |||
| 4724 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\TokenBroker\Cache\5475cb191e478c39370a215b2da98a37e9dc813d.tbres | binary | |
MD5:B6759229527F483BA820C53167AB9FD3 | SHA256:AED3875C67C0B5524622F3105F3D5030AEE2AA179FF1332A1646B6221214FDB5 | |||
| 4724 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\AddInClassifierCache\OfficeSharedEntitiesUpdated.bin | text | |
MD5:276D069E8256333107E94183C1DA16EB | SHA256:0B21FE96B90157B633FD6B0F2375E901550C7FABC7090B2A0F0DBD53C2AA4718 | |||
| 4724 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\TokenBroker\Cache\56a61aeb75d8f5be186c26607f4bb213abe7c5ec.tbres | binary | |
MD5:D462B9A51CC7DB77CE161CF7B10308E5 | SHA256:176CBADAD16E08692820391E18F3B48D9595B238D60F1106DA18BB17A6EBA295 | |||
| 4724 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\TokenBroker\Cache\089d66ba04a8cec4bdc5267f42f39cf84278bb67.tbres | binary | |
MD5:75B9CFDA139592C5C475A445274AE3C5 | SHA256:12FB8F0732359FB2E0A99D7EACC34B7101E57B45EE3B9EC15A9CA69A2F47ED68 | |||
| 4724 | WINWORD.EXE | C:\Users\Public\~$领取信息填报.docx | abr | |
MD5:CC5B233F667478BD72B6C20BD98AE375 | SHA256:4EC31ECADA1875A83315E9573A68EA1F015F628097689AEDF3B33D7EAD141311 | |||
| 4600 | b92c4f3b24c0772241f5ec985be12c3070858c0922155ff6d2c88410a593a5b0.exe | C:\Users\Public\领取信息填报.docx | html | |
MD5:0723E124F290EF0C356627361C46B792 | SHA256:7F8C7F918148B32820B0C39F8904DE975147F2A5D34A3F676298A691AE857284 | |||
| 4724 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$Normal.dotm | binary | |
MD5:A5343672C0BE98D43274DA4B95E277D8 | SHA256:608F9FA56798E71FBFAC95FE04DABD972281DBECC3BF90D8938828831F04B6DA | |||
| 4724 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\AddInClassifierCache\OfficeSharedEntities.bin | text | |
MD5:CC90D669144261B198DEAD45AA266572 | SHA256:89C701EEFF939A44F28921FD85365ECD87041935DCD0FE0BAF04957DA12C9899 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
11
TCP/UDP connections
26
DNS requests
11
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4600 | b92c4f3b24c0772241f5ec985be12c3070858c0922155ff6d2c88410a593a5b0.exe | GET | 404 | 103.43.9.193:80 | http://103.43.9.193/jkljkl.docx | unknown | — | — | unknown |
2072 | svchost.exe | GET | 200 | 23.48.23.143:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
2072 | svchost.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
4600 | b92c4f3b24c0772241f5ec985be12c3070858c0922155ff6d2c88410a593a5b0.exe | GET | 200 | 103.43.9.193:80 | http://103.43.9.193/szsz | unknown | — | — | unknown |
5328 | RUXIMICS.exe | GET | 200 | 23.48.23.143:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1792 | MoUsoCoreWorker.exe | GET | 200 | 23.48.23.143:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1792 | MoUsoCoreWorker.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 52.109.28.46:443 | https://officeclient.microsoft.com/config16/?lcid=1033&syslcid=1033&uilcid=1033&build=16.0.16026&crev=3 | unknown | xml | 170 Kb | unknown |
— | — | GET | 200 | 23.48.23.55:443 | https://omex.cdn.office.net/addinclassifier/officesharedentities | unknown | text | 314 Kb | unknown |
— | — | GET | 200 | 52.113.194.132:443 | https://ecs.office.com/config/v2/Office/word/16.0.16026.20146/Production/CC?&Clientid=%7bD61AB268-C26A-439D-BB15-2A0DEDFCA6A3%7d&Application=word&Platform=win32&Version=16.0.16026.20146&MsoVersion=16.0.16026.20002&SDX=fa000000002.2.0.1907.31003&SDX=fa000000005.1.0.1909.30011&SDX=fa000000006.1.0.1909.13002&SDX=fa000000008.1.0.1908.16006&SDX=fa000000009.1.0.1908.6002&SDX=fa000000016.1.0.1810.13001&SDX=fa000000029.1.0.1906.25001&SDX=fa000000033.1.0.1908.24001&SDX=wa104381125.1.0.1810.9001&ProcessName=winword.exe&Audience=Production&Build=ship&Architecture=x64&Language=en-US&SubscriptionLicense=false&PerpetualLicense=2019&LicenseCategory=6&LicenseSKU=Professional2019Retail&OsVersion=10.0&OsBuild=19045&Channel=CC&InstallType=C2R&SessionId=%7bDA58C712-3AD1-4D87-B673-01EE461E0666%7d&LabMachine=false | unknown | text | 374 Kb | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2072 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5328 | RUXIMICS.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1792 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4032 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4600 | b92c4f3b24c0772241f5ec985be12c3070858c0922155ff6d2c88410a593a5b0.exe | 103.43.9.193:80 | — | CNSERVERS | HK | unknown |
2072 | svchost.exe | 23.48.23.143:80 | crl.microsoft.com | Akamai International B.V. | DE | unknown |
5328 | RUXIMICS.exe | 23.48.23.143:80 | crl.microsoft.com | Akamai International B.V. | DE | unknown |
1792 | MoUsoCoreWorker.exe | 23.48.23.143:80 | crl.microsoft.com | Akamai International B.V. | DE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
officeclient.microsoft.com |
| whitelisted |
omex.cdn.office.net |
| whitelisted |
ecs.office.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
4600 | b92c4f3b24c0772241f5ec985be12c3070858c0922155ff6d2c88410a593a5b0.exe | Potentially Bad Traffic | ET INFO Dotted Quad Host DOCX Request |