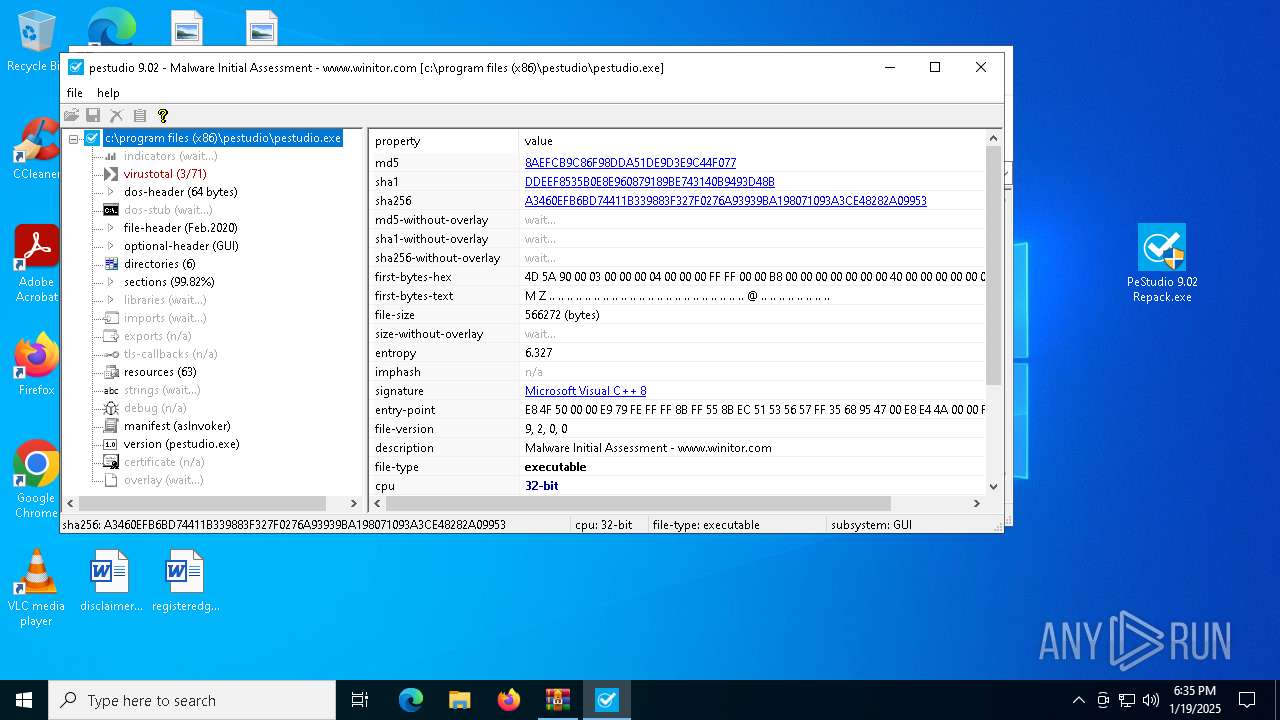
| File name: | PeStudio 9.02 Repack pcprogsnet.rar |
| Full analysis: | https://app.any.run/tasks/c4ea747e-6501-481c-86ab-110ecc9b393b |
| Verdict: | Malicious activity |
| Analysis date: | January 19, 2025, 18:34:08 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
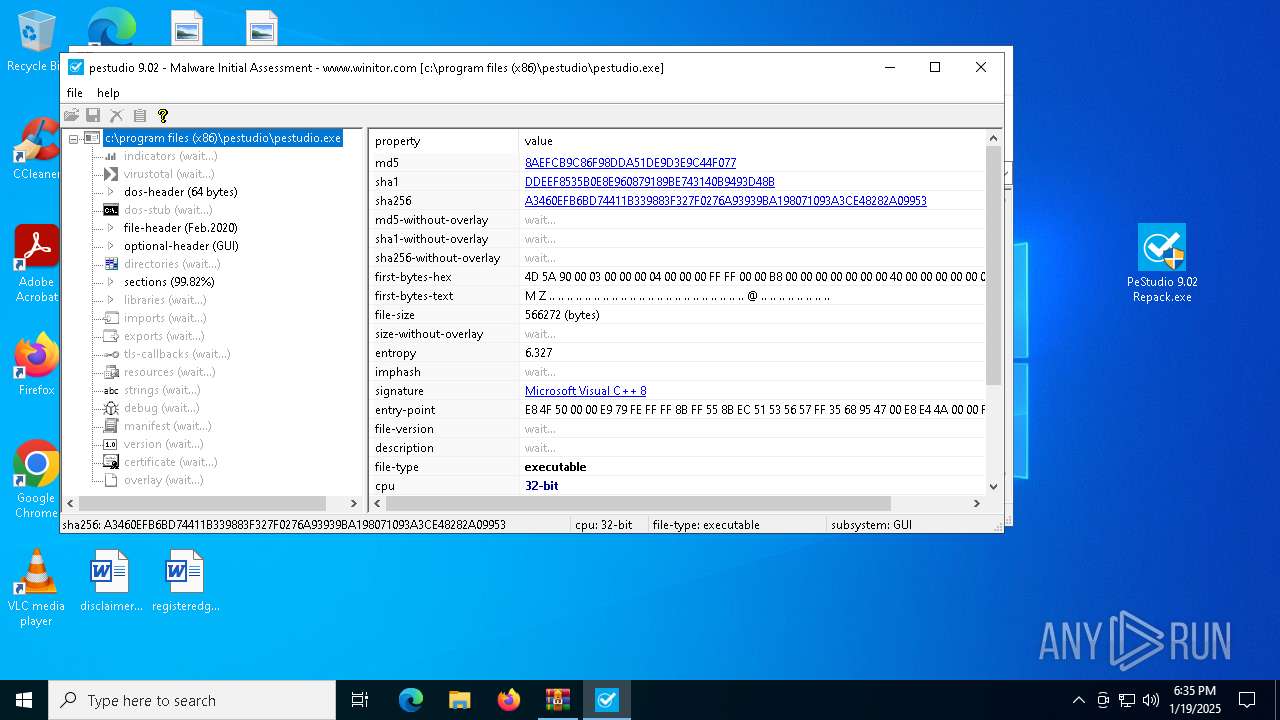
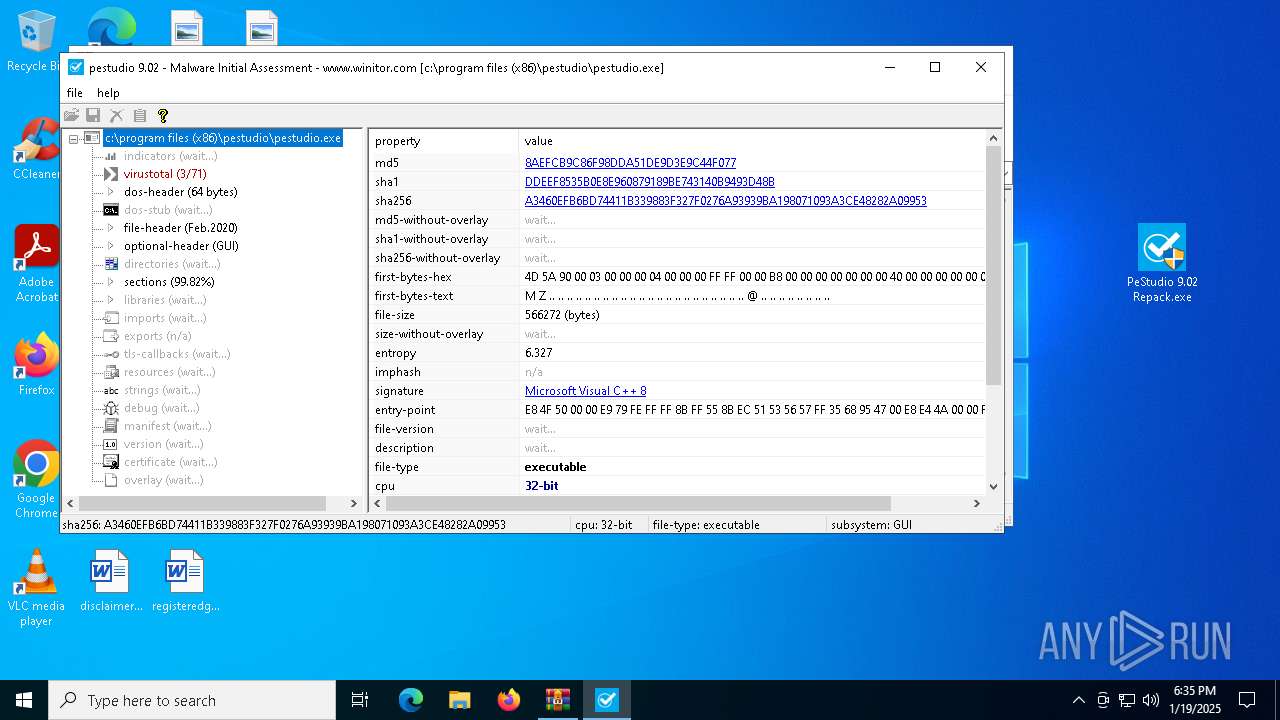
| MD5: | D04A12857432E47CFF69D8BF05A625E3 |
| SHA1: | FB3DE448B730BD60345984A0C359538018C3C79A |
| SHA256: | B928D39A7833DCADFD0A86C2842A10D2B7E9CDAD649743459942882445776218 |
| SSDEEP: | 98304:prAJHQD3eDBZkRVUDJYnCXm9TxpyqugE1ii2BcmjDkQZOpVDsLbcA9JqqV5CG7M3:lzv5ECQ |
MALICIOUS
ALINA has been detected (YARA)
- pestudio.exe (PID: 5872)
SUSPICIOUS
Executable content was dropped or overwritten
- PeStudio 9.02 Repack.exe (PID: 6836)
- PeStudio 9.02 Repack.tmp (PID: 6860)
Process drops legitimate windows executable
- PeStudio 9.02 Repack.tmp (PID: 6860)
Creates file in the systems drive root
- pestudio.exe (PID: 5872)
Reads security settings of Internet Explorer
- pestudio.exe (PID: 5872)
There is functionality for taking screenshot (YARA)
- pestudio.exe (PID: 5872)
Reads Microsoft Outlook installation path
- pestudio.exe (PID: 5872)
Reads the Windows owner or organization settings
- PeStudio 9.02 Repack.tmp (PID: 6860)
INFO
The process uses the downloaded file
- WinRAR.exe (PID: 2088)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2088)
Manual execution by a user
- PeStudio 9.02 Repack.exe (PID: 6784)
- PeStudio 9.02 Repack.exe (PID: 6836)
Reads the computer name
- PeStudio 9.02 Repack.tmp (PID: 6860)
- pestudio.exe (PID: 5872)
has been detected (YARA)
- PeStudio 9.02 Repack.exe (PID: 6836)
- PeStudio 9.02 Repack.tmp (PID: 6860)
Checks supported languages
- PeStudio 9.02 Repack.tmp (PID: 6860)
- PeStudio 9.02 Repack.exe (PID: 6836)
- pestudio.exe (PID: 5872)
Create files in a temporary directory
- PeStudio 9.02 Repack.tmp (PID: 6860)
- PeStudio 9.02 Repack.exe (PID: 6836)
Compiled with Borland Delphi (YARA)
- PeStudio 9.02 Repack.tmp (PID: 6860)
- PeStudio 9.02 Repack.exe (PID: 6836)
The sample compiled with english language support
- PeStudio 9.02 Repack.tmp (PID: 6860)
Reads the software policy settings
- pestudio.exe (PID: 5872)
Creates a software uninstall entry
- PeStudio 9.02 Repack.tmp (PID: 6860)
Reads the machine GUID from the registry
- pestudio.exe (PID: 5872)
The sample compiled with chinese language support
- PeStudio 9.02 Repack.tmp (PID: 6860)
Creates files in the program directory
- PeStudio 9.02 Repack.tmp (PID: 6860)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
EXIF
ZIP
| FileVersion: | RAR v5 |
|---|
Total processes
136
Monitored processes
5
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2088 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\PeStudio 9.02 Repack pcprogsnet.rar" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 5872 | "C:\Program Files (x86)\pestudio\pestudio.exe" | C:\Program Files (x86)\pestudio\pestudio.exe | PeStudio 9.02 Repack.tmp | ||||||||||||
User: admin Company: www.winitor.com Integrity Level: HIGH Description: Malware Initial Assessment - www.winitor.com Version: 9, 2, 0, 0 Modules
| |||||||||||||||
| 6784 | "C:\Users\admin\Desktop\PeStudio 9.02 Repack.exe" | C:\Users\admin\Desktop\PeStudio 9.02 Repack.exe | — | explorer.exe | |||||||||||
User: admin Company: pestudio Integrity Level: MEDIUM Description: pestudio 9.02 Exit code: 3221226540 Version: 9.02 Modules
| |||||||||||||||
| 6836 | "C:\Users\admin\Desktop\PeStudio 9.02 Repack.exe" | C:\Users\admin\Desktop\PeStudio 9.02 Repack.exe | explorer.exe | ||||||||||||
User: admin Company: pestudio Integrity Level: HIGH Description: pestudio 9.02 Exit code: 0 Version: 9.02 Modules
| |||||||||||||||
| 6860 | "C:\Users\admin\AppData\Local\Temp\is-8SJ20.tmp\PeStudio 9.02 Repack.tmp" /SL5="$7035E,2441214,151552,C:\Users\admin\Desktop\PeStudio 9.02 Repack.exe" | C:\Users\admin\AppData\Local\Temp\is-8SJ20.tmp\PeStudio 9.02 Repack.tmp | PeStudio 9.02 Repack.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Setup/Uninstall Exit code: 0 Version: 51.1052.0.0 Modules
| |||||||||||||||
Total events
6 205
Read events
6 129
Write events
74
Delete events
2
Modification events
| (PID) Process: | (2088) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
| (PID) Process: | (2088) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (2088) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (2088) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (2088) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\PeStudio 9.02 Repack pcprogsnet.rar | |||
| (PID) Process: | (2088) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2088) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2088) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2088) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (6860) PeStudio 9.02 Repack.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\*\shell\pestudio |
| Operation: | write | Name: | Icon |
Value: "C:\Program Files (x86)\pestudio\pestudio.exe",0 | |||
Executable files
16
Suspicious files
6
Text files
26
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2088 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb2088.47270\PeStudio 9.02 Repack.exe | executable | |
MD5:989AE536D6F2E7956E3CFB7E0CDD639F | SHA256:FBE1D21F381A13543938ABA036003F8AD9AEF9822081E83B4DE5FE3C7891454E | |||
| 6860 | PeStudio 9.02 Repack.tmp | C:\Users\admin\AppData\Local\Temp\is-9DAGV.tmp\_isetup\_shfoldr.dll | executable | |
MD5:92DC6EF532FBB4A5C3201469A5B5EB63 | SHA256:9884E9D1B4F8A873CCBD81F8AD0AE257776D2348D027D811A56475E028360D87 | |||
| 6860 | PeStudio 9.02 Repack.tmp | C:\Program Files (x86)\pestudio\is-NKTI1.tmp | executable | |
MD5:B0CA93CEB050A2FEFF0B19E65072BBB5 | SHA256:0E93313F42084D804B9AC4BE53D844E549CFCAF19E6F276A3B0F82F01B9B2246 | |||
| 6860 | PeStudio 9.02 Repack.tmp | C:\Program Files (x86)\pestudio\is-U8ABE.tmp | image | |
MD5:8CDB0587C493E7FF881490BA00D78594 | SHA256:A3556B122C91AF0C5F9ED26BB135EBB8014EDF56FB79AB5C37F74851C44BF57A | |||
| 6860 | PeStudio 9.02 Repack.tmp | C:\Users\admin\AppData\Local\Temp\is-9DAGV.tmp\VclStylesInno.dll | executable | |
MD5:B0CA93CEB050A2FEFF0B19E65072BBB5 | SHA256:0E93313F42084D804B9AC4BE53D844E549CFCAF19E6F276A3B0F82F01B9B2246 | |||
| 6860 | PeStudio 9.02 Repack.tmp | C:\Program Files (x86)\pestudio\is-DOG1P.tmp | executable | |
MD5:79AA22672B9E87BC087DA01B167C919B | SHA256:445EBF83C488C4431084383AD21D7BAB2D381CBF86ACD89BC06DDF93B38D98C1 | |||
| 6860 | PeStudio 9.02 Repack.tmp | C:\Program Files (x86)\pestudio\Desktop.ini | text | |
MD5:BB8C258FD3738746551917584E925B9A | SHA256:4F97F67205D881D35AF8483E8A640521403023C7590B193745B9A2505F66C4F0 | |||
| 6860 | PeStudio 9.02 Repack.tmp | C:\Program Files (x86)\pestudio\VclStylesinno.dll | executable | |
MD5:B0CA93CEB050A2FEFF0B19E65072BBB5 | SHA256:0E93313F42084D804B9AC4BE53D844E549CFCAF19E6F276A3B0F82F01B9B2246 | |||
| 6860 | PeStudio 9.02 Repack.tmp | C:\Program Files (x86)\pestudio\is-JK4T2.tmp | text | |
MD5:BB8C258FD3738746551917584E925B9A | SHA256:4F97F67205D881D35AF8483E8A640521403023C7590B193745B9A2505F66C4F0 | |||
| 6860 | PeStudio 9.02 Repack.tmp | C:\Program Files (x86)\pestudio\unins000.exe | executable | |
MD5:79AA22672B9E87BC087DA01B167C919B | SHA256:445EBF83C488C4431084383AD21D7BAB2D381CBF86ACD89BC06DDF93B38D98C1 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
8
TCP/UDP connections
35
DNS requests
20
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 23.48.23.145:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6992 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
5872 | pestudio.exe | GET | 301 | 34.54.88.138:80 | http://www.virustotal.com/vtapi/v2/file/report?apikey=03488030fb57e825ca7f652571f12f15dbb069220773190978b85793c9ecfead&resource=8aefcb9c86f98dda51de9d3e9c44f077 | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6992 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
6288 | backgroundTaskHost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
5064 | SearchApp.exe | 104.126.37.131:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
— | — | 23.48.23.145:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 51.104.136.2:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2632 | svchost.exe | 51.104.136.2:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1176 | svchost.exe | 20.190.159.0:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1176 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |