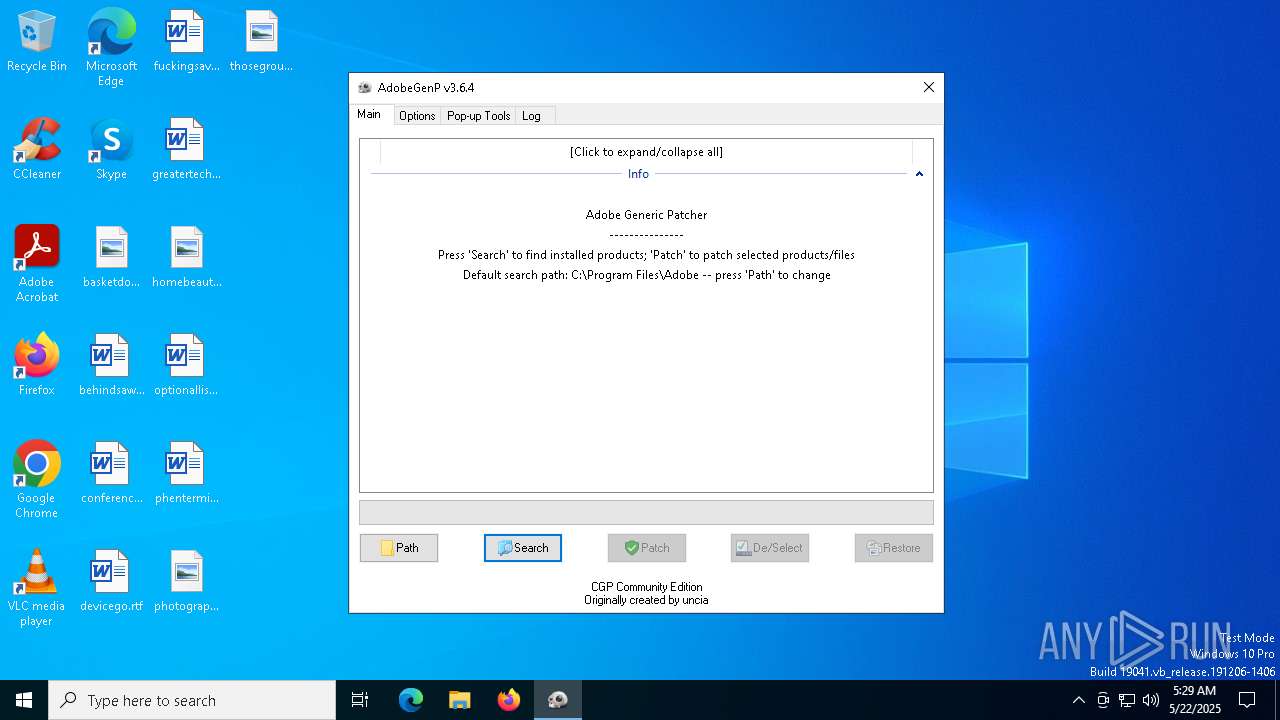
| File name: | GenP 3.6.4.exe |
| Full analysis: | https://app.any.run/tasks/5928217f-2a3e-4fed-944f-fe501796a26e |
| Verdict: | Malicious activity |
| Analysis date: | May 22, 2025, 05:29:20 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32+ executable (GUI) x86-64, for MS Windows, 6 sections |
| MD5: | 859E24EAF9E2B231CF7FADF25D8DB232 |
| SHA1: | EE1782596BC1574459B69B1DE675FFF66931E25B |
| SHA256: | B92860632A6DDAE2532206833CC0C4A18548D469136271ACDBD760E4986E260B |
| SSDEEP: | 98304:a9rem5Oid1RME3XUVZ6z2Mn85M7LRKUDmkSQXkkzvuPVca+fl3VgvtfvXW9AALqE:cZul |
MALICIOUS
GENERIC has been found (auto)
- GenP 3.6.4.exe (PID: 5960)
SUSPICIOUS
ADOBEGENP mutex has been found
- GenP 3.6.4.exe (PID: 5960)
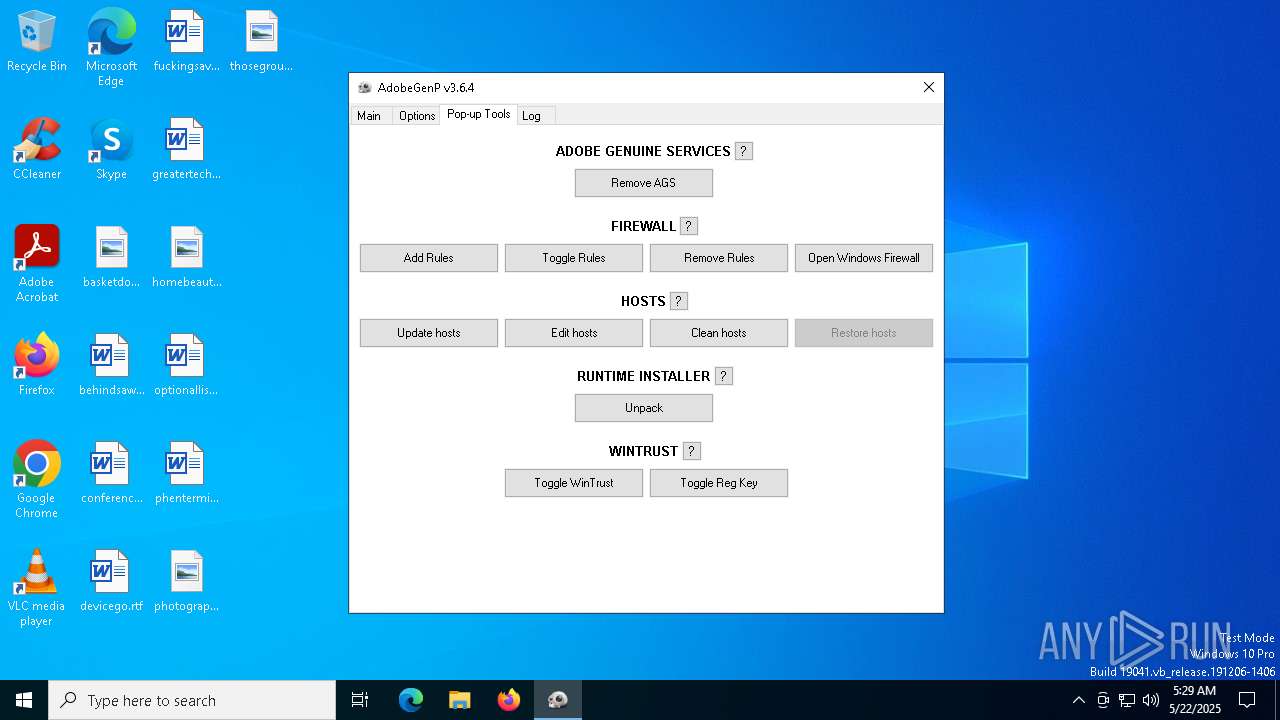
Creates files in the driver directory
- GenP 3.6.4.exe (PID: 5960)
Reads security settings of Internet Explorer
- GenP 3.6.4.exe (PID: 5960)
Starts CMD.EXE for commands execution
- GenP 3.6.4.exe (PID: 5960)
Process uses IPCONFIG to discover network configuration
- cmd.exe (PID: 3096)
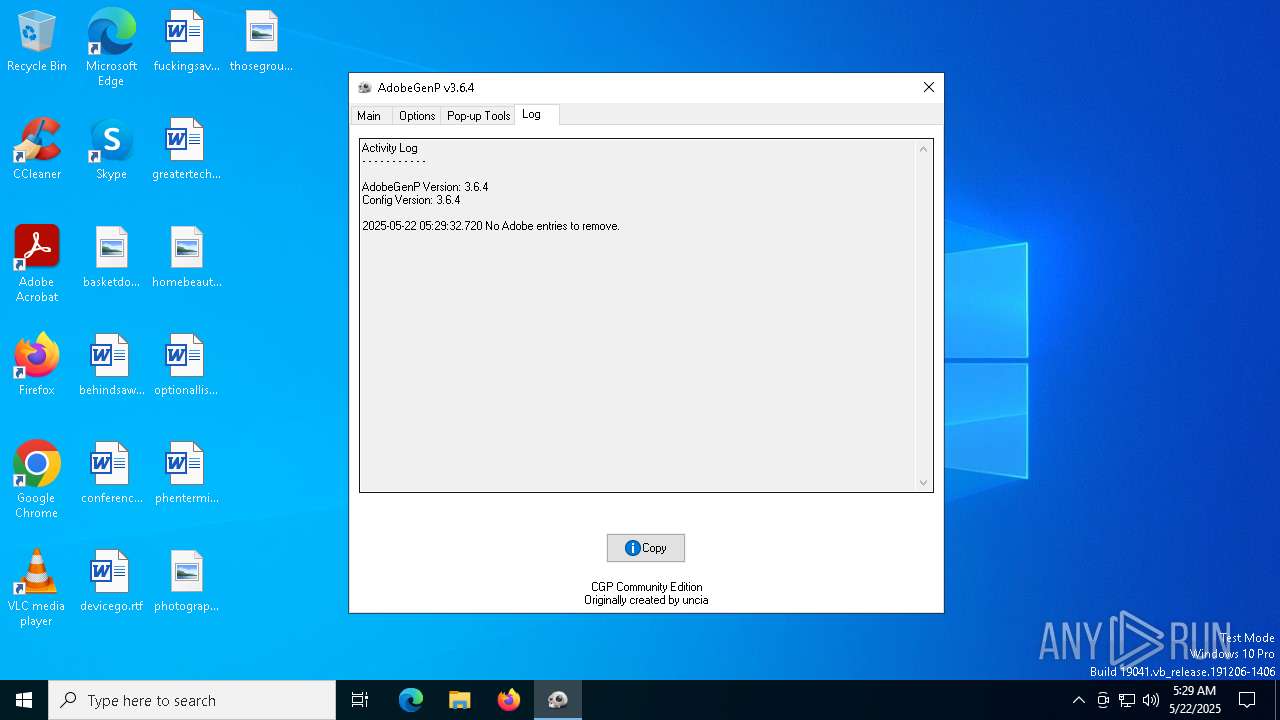
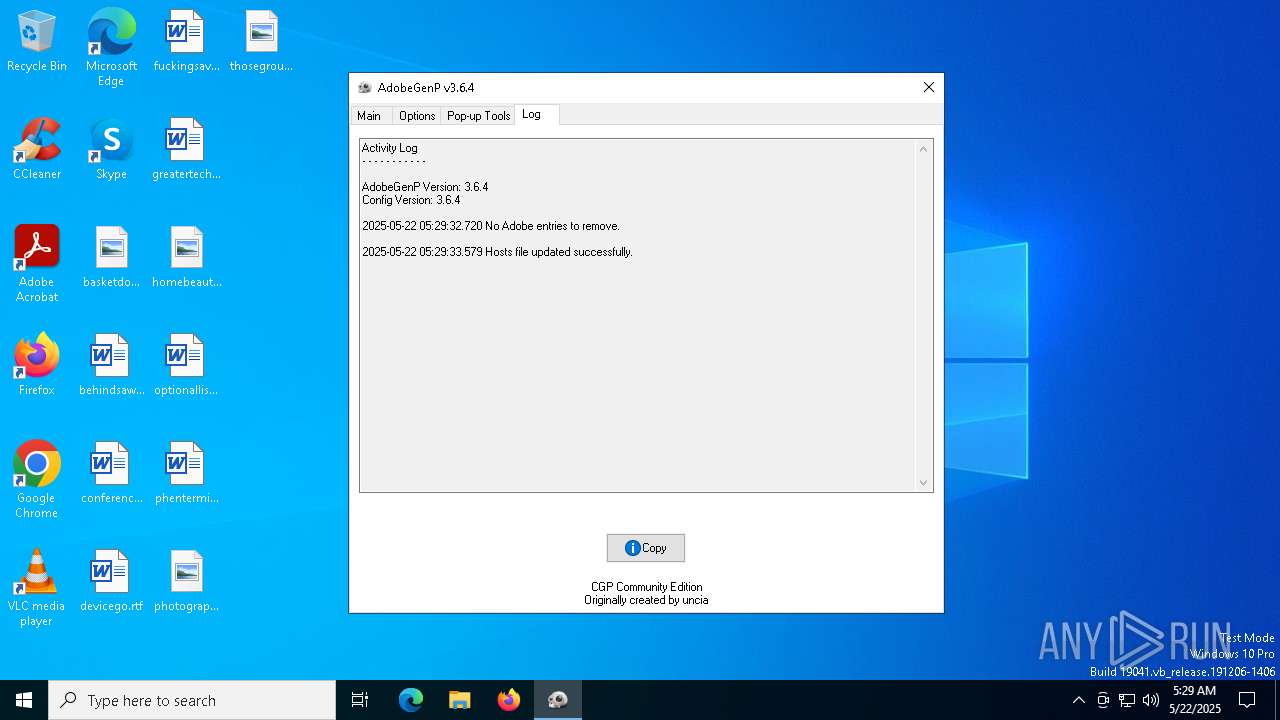
Modifies hosts file to alter network resolution
- GenP 3.6.4.exe (PID: 5960)
INFO
Reads mouse settings
- GenP 3.6.4.exe (PID: 5960)
The sample compiled with english language support
- GenP 3.6.4.exe (PID: 5960)
Checks supported languages
- GenP 3.6.4.exe (PID: 5960)
Reads the computer name
- GenP 3.6.4.exe (PID: 5960)
Create files in a temporary directory
- GenP 3.6.4.exe (PID: 5960)
Reads the machine GUID from the registry
- GenP 3.6.4.exe (PID: 5960)
Reads the software policy settings
- GenP 3.6.4.exe (PID: 5960)
Creates files or folders in the user directory
- GenP 3.6.4.exe (PID: 5960)
Checks proxy server information
- GenP 3.6.4.exe (PID: 5960)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Generic Win/DOS Executable (50) |
|---|---|---|
| .exe | | | DOS Executable Generic (49.9) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2025:04:23 18:29:11+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 14.16 |
| CodeSize: | 734208 |
| InitializedDataSize: | 2232320 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x2549c |
| OSVersion: | 5.2 |
| ImageVersion: | - |
| SubsystemVersion: | 5.2 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 3.6.4.0 |
| ProductVersionNumber: | 3.6.4.0 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Unknown |
| FileSubtype: | - |
| LanguageCode: | English (British) |
| CharacterSet: | Unicode |
| FileVersion: | 3.6.4.0 |
| Comments: | AdobeGenP |
| FileDescription: | Adobe Generic Patcher |
| ProductName: | AdobeGenP |
| ProductVersion: | 3.6.4 |
| CompanyName: | AdobeGenp |
| LegalCopyright: | AdobeGenP 2025 |
| LegalTradeMarks: | AdobeGenP 2025 |
Total processes
134
Monitored processes
7
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 668 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | SppExtComObj.Exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1180 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2320 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2616 | "C:\Users\admin\Downloads\GenP 3.6.4.exe" | C:\Users\admin\Downloads\GenP 3.6.4.exe | — | explorer.exe | |||||||||||
User: admin Company: AdobeGenp Integrity Level: MEDIUM Description: Adobe Generic Patcher Exit code: 3221226540 Version: 3.6.4.0 Modules
| |||||||||||||||
| 3096 | C:\WINDOWS\system32\cmd.exe /c ipconfig /displaydns > C:\Users\admin\AppData\Local\Temp\dns_cache.txt | C:\Windows\System32\cmd.exe | — | GenP 3.6.4.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5960 | "C:\Users\admin\Downloads\GenP 3.6.4.exe" | C:\Users\admin\Downloads\GenP 3.6.4.exe | explorer.exe | ||||||||||||
User: admin Company: AdobeGenp Integrity Level: HIGH Description: Adobe Generic Patcher Version: 3.6.4.0 Modules
| |||||||||||||||
| 6560 | ipconfig /displaydns | C:\Windows\System32\ipconfig.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: IP Configuration Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
1 163
Read events
1 160
Write events
3
Delete events
0
Modification events
| (PID) Process: | (5960) GenP 3.6.4.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (5960) GenP 3.6.4.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (5960) GenP 3.6.4.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
Executable files
1
Suspicious files
5
Text files
5
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5960 | GenP 3.6.4.exe | C:\Windows\System32\drivers\etc\hosts.bak | text | |
MD5:C40F0E533A52F202035621D27E732F5A | SHA256:408442168118E82FAF7D419AA4F0D8FA04F45A5E6D0E7065A9CDC723782C5AE3 | |||
| 5960 | GenP 3.6.4.exe | C:\Users\admin\AppData\Local\Temp\autB97E.tmp | binary | |
MD5:FC28D09F35A6D32EAE8D4CAF9BFF09D1 | SHA256:5B3003EE371F41596FBB89A40B0126BA3980E8D8FAF1DBE4B7388E462BF44442 | |||
| 5960 | GenP 3.6.4.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\RR3E01RZ\list[1].txt | text | |
MD5:9D883BAD02FADF2C8D4F6DD8EE1D68C6 | SHA256:484D5F0513D807637D22EDAEE6E0C6880DFE703862517B1E8A204F043B0EA80F | |||
| 5960 | GenP 3.6.4.exe | C:\Users\admin\Downloads\config.ini | text | |
MD5:FABC1F7F0E77C6882B9A16851E7D7E77 | SHA256:5E9A06AB44D12EC8AAAF3918859E8ED807E76CC58B7FEEB9B25741DE8AC4C56D | |||
| 5960 | GenP 3.6.4.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\8B2B9A00839EED1DFDCCC3BFC2F5DF12 | binary | |
MD5:9D8C2585F118E2994B90683836BB4C1C | SHA256:0BDDF2BF4DFBF873E547D93A3344AA944344371723F06619AA667A6AE5667162 | |||
| 5960 | GenP 3.6.4.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\B46811C17859FFB409CF0E904A4AA8F8 | binary | |
MD5:BF2E8E53A9B1DBAC0E2D2700D76BF56B | SHA256:4786DB866DF71EC1A0ADBE2BC88125D8E882FD0F1ABE5952DF7B9050C1BB8AA6 | |||
| 5960 | GenP 3.6.4.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\B46811C17859FFB409CF0E904A4AA8F8 | binary | |
MD5:1FBB37F79B317A9A248E7C4CE4F5BAC5 | SHA256:9BF639C595FE335B6F694EE35990BEFD2123F5E07FD1973FF619E3FC88F5F49F | |||
| 5960 | GenP 3.6.4.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\8B2B9A00839EED1DFDCCC3BFC2F5DF12 | binary | |
MD5:4A90329071AE30B759D279CCA342B0A6 | SHA256:4F544379EDA8E2653F71472AB968AEFD6B5D1F4B3CE28A5EDB14196184ED3B60 | |||
| 3096 | cmd.exe | C:\Users\admin\AppData\Local\Temp\dns_cache.txt | text | |
MD5:9DC473911DD76F3F8E25CF682A03DC72 | SHA256:11F2A16A72486638CA70488F3BA7D2E2D54EAAD4B6FAB5A22B4A486873CADDF8 | |||
| 5960 | GenP 3.6.4.exe | C:\Windows\System32\drivers\etc\hosts | text | |
MD5:2C952F8DEB0C82BD1A4F97FDB4252266 | SHA256:D8C0DB494C606B035F40F66E10D52090EB4326991208358E73F544CD919CBDCF | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
9
TCP/UDP connections
24
DNS requests
15
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.216.77.6:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.216.77.6:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5960 | GenP 3.6.4.exe | GET | 200 | 142.250.181.227:80 | http://c.pki.goog/r/gsr1.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5960 | GenP 3.6.4.exe | GET | 200 | 142.250.181.227:80 | http://c.pki.goog/r/r4.crl | unknown | — | — | whitelisted |
1812 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
1812 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2104 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.216.77.6:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 23.216.77.6:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5496 | MoUsoCoreWorker.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
— | — | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
3216 | svchost.exe | 172.211.123.250:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 20.190.160.20:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
a.dove.isdumb.one |
| unknown |
c.pki.goog |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |