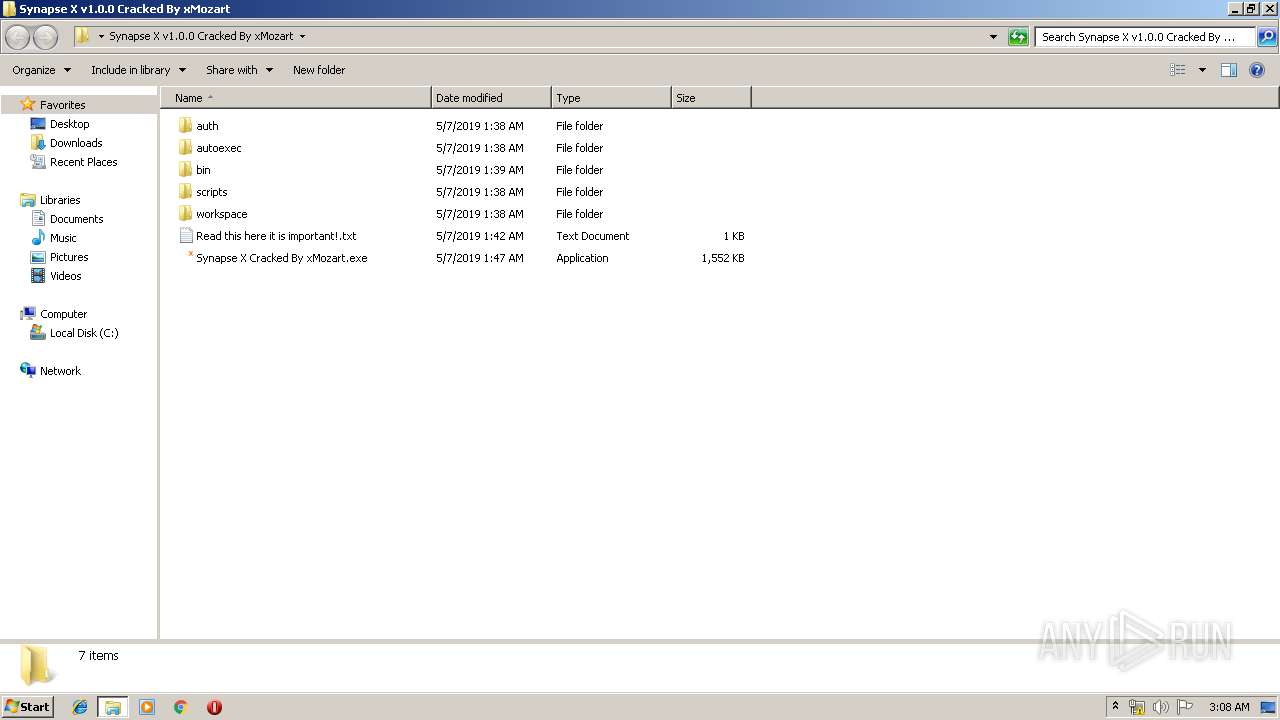
| File name: | Synapse X v1.0.0 Cracked By xMozart.rar |
| Full analysis: | https://app.any.run/tasks/63ad0310-bf43-4cd3-a954-88d2156eaf84 |
| Verdict: | Malicious activity |
| Analysis date: | May 07, 2019, 02:08:09 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | 2EB178B33A483718FCC874A3B14B2973 |
| SHA1: | 3A01A4CE1B5341C831470E427A0BAEC69FBF970B |
| SHA256: | B9109089BB2834A5DF70B0B509919F35FD294D42D0448D7ADB9BA04DD1ED337B |
| SSDEEP: | 196608:FXJBUbADlmrLl4GoUfTNcJTWJ90py6WkZOsRD68stUfn0wk:FXJd4Hl4LA8T40rvZOsRD6eVk |
MALICIOUS
Application was dropped or rewritten from another process
- Synapse.exe (PID: 3900)
- ROBLOX.exe (PID: 3540)
- svchost.exe (PID: 2480)
- C7FB8689DFEAC65B.bin (PID: 1524)
- Server.exe (PID: 2576)
- Server.exe (PID: 3740)
- ROBLOX.exe (PID: 3312)
- Synapse.exe (PID: 2468)
- C7FB8689DFEAC65B.bin (PID: 2448)
Writes to a start menu file
- svchost.exe (PID: 2480)
Changes the autorun value in the registry
- svchost.exe (PID: 2480)
Loads the Task Scheduler COM API
- schtasks.exe (PID: 4016)
Uses Task Scheduler to run other applications
- svchost.exe (PID: 2480)
Loads dropped or rewritten executable
- SearchProtocolHost.exe (PID: 2564)
SUSPICIOUS
Executable content was dropped or overwritten
- Synapse.exe (PID: 3900)
- Synapse X Cracked By xMozart.exe (PID: 2852)
- ROBLOX.exe (PID: 3540)
- svchost.exe (PID: 2480)
- Synapse.exe (PID: 2468)
Creates files in the user directory
- ROBLOX.exe (PID: 3540)
- svchost.exe (PID: 2480)
Creates executable files which already exist in Windows
- ROBLOX.exe (PID: 3540)
Starts application with an unusual extension
- Synapse.exe (PID: 3900)
- Synapse.exe (PID: 2468)
Starts itself from another location
- ROBLOX.exe (PID: 3540)
INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
51
Monitored processes
14
Malicious processes
6
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1524 | "bin\C7FB8689DFEAC65B.bin" | C:\Users\admin\Desktop\Synapse X v1.0.0 Cracked By xMozart\bin\C7FB8689DFEAC65B.bin | — | Synapse.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 4294967295 Version: 1.0.0.0 Modules
| |||||||||||||||
| 2128 | "C:\Windows\explorer.exe" | C:\Windows\explorer.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2448 | "bin\C7FB8689DFEAC65B.bin" | C:\Users\admin\AppData\Local\Temp\bin\C7FB8689DFEAC65B.bin | — | Synapse.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 2468 | "C:\Users\admin\AppData\Local\Temp\Synapse.exe" | C:\Users\admin\AppData\Local\Temp\Synapse.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: Synapse Bootstrapper Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 2480 | "C:\Users\admin\AppData\Roaming\svchost.exe" | C:\Users\admin\AppData\Roaming\svchost.exe | ROBLOX.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2564 | "C:\Windows\system32\SearchProtocolHost.exe" Global\UsGthrFltPipeMssGthrPipe4_ Global\UsGthrCtrlFltPipeMssGthrPipe4 1 -2147483646 "Software\Microsoft\Windows Search" "Mozilla/4.0 (compatible; MSIE 6.0; Windows NT; MS Search 4.0 Robot)" "C:\ProgramData\Microsoft\Search\Data\Temp\usgthrsvc" "DownLevelDaemon" | C:\Windows\System32\SearchProtocolHost.exe | — | SearchIndexer.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft Windows Search Protocol Host Exit code: 0 Version: 7.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2576 | "C:\Users\admin\AppData\Local\Temp\Server.exe" | C:\Users\admin\AppData\Local\Temp\Server.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2852 | "C:\Users\admin\Desktop\Synapse X v1.0.0 Cracked By xMozart\Synapse X Cracked By xMozart.exe" | C:\Users\admin\Desktop\Synapse X v1.0.0 Cracked By xMozart\Synapse X Cracked By xMozart.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: Stub Exit code: 4294967295 Version: 1.0.0.0 Modules
| |||||||||||||||
| 3312 | "C:\Users\admin\AppData\Local\Temp\ROBLOX.exe" | C:\Users\admin\AppData\Local\Temp\ROBLOX.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 3540 | "C:\Users\admin\AppData\Local\Temp\ROBLOX.exe" | C:\Users\admin\AppData\Local\Temp\ROBLOX.exe | Synapse X Cracked By xMozart.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
Total events
1 681
Read events
1 593
Write events
88
Delete events
0
Modification events
| (PID) Process: | (3556) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3556) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3556) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\62\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3556) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Synapse X v1.0.0 Cracked By xMozart.rar | |||
| (PID) Process: | (3556) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3556) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3556) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3556) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3556) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF42000000420000000204000037020000 | |||
| (PID) Process: | (3556) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\General |
| Operation: | write | Name: | LastFolder |
Value: C:\Users\admin\AppData\Local\Temp | |||
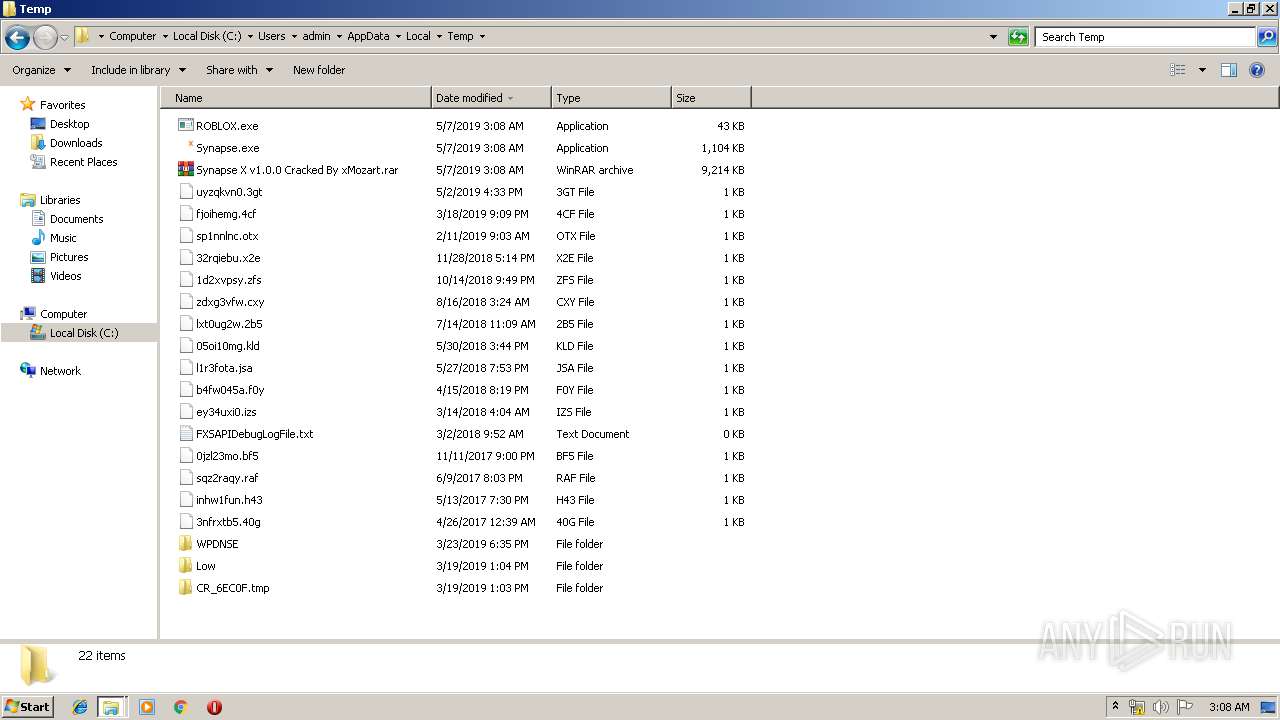
Executable files
8
Suspicious files
0
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3556 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3556.42632\Synapse X v1.0.0 Cracked By xMozart\bin\08C2E5CC124C3633.bin | — | |
MD5:— | SHA256:— | |||
| 3556 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3556.42632\Synapse X v1.0.0 Cracked By xMozart\bin\SynapseInjector.dll | — | |
MD5:— | SHA256:— | |||
| 3556 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3556.42632\Synapse X v1.0.0 Cracked By xMozart\Read this here it is important!.txt | — | |
MD5:— | SHA256:— | |||
| 3556 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3556.42632\Synapse X v1.0.0 Cracked By xMozart\Synapse X Cracked By xMozart.exe | — | |
MD5:— | SHA256:— | |||
| 2852 | Synapse X Cracked By xMozart.exe | C:\Users\admin\AppData\Local\Temp\ROBLOX.exe | executable | |
MD5:— | SHA256:— | |||
| 2480 | svchost.exe | C:\Users\admin\AppData\Local\Temp\Server.exe | executable | |
MD5:— | SHA256:— | |||
| 2480 | svchost.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\Java update.exe | executable | |
MD5:— | SHA256:— | |||
| 3540 | ROBLOX.exe | C:\Users\admin\AppData\Roaming\svchost.exe | executable | |
MD5:— | SHA256:— | |||
| 2852 | Synapse X Cracked By xMozart.exe | C:\Users\admin\AppData\Local\Temp\Synapse.exe | executable | |
MD5:— | SHA256:— | |||
| 3900 | Synapse.exe | C:\Users\admin\Desktop\Synapse X v1.0.0 Cracked By xMozart\bin\C7FB8689DFEAC65B.bin | executable | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
5
DNS requests
3
Threats
1
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3900 | Synapse.exe | 104.20.166.135:443 | synapse.to | Cloudflare Inc | US | shared |
2480 | svchost.exe | 141.255.157.116:1177 | stuckhunter.duckdns.org | Lost Oasis SARL | NL | unknown |
3900 | Synapse.exe | 104.20.165.135:443 | synapse.to | Cloudflare Inc | US | shared |
2468 | Synapse.exe | 104.20.165.135:443 | synapse.to | Cloudflare Inc | US | shared |
2468 | Synapse.exe | 104.20.166.135:443 | synapse.to | Cloudflare Inc | US | shared |
DNS requests
Domain | IP | Reputation |
|---|---|---|
synapse.to |
| whitelisted |
cdn.synapse.to |
| suspicious |
stuckhunter.duckdns.org |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1056 | svchost.exe | Misc activity | ET INFO DYNAMIC_DNS Query to *.duckdns. Domain |