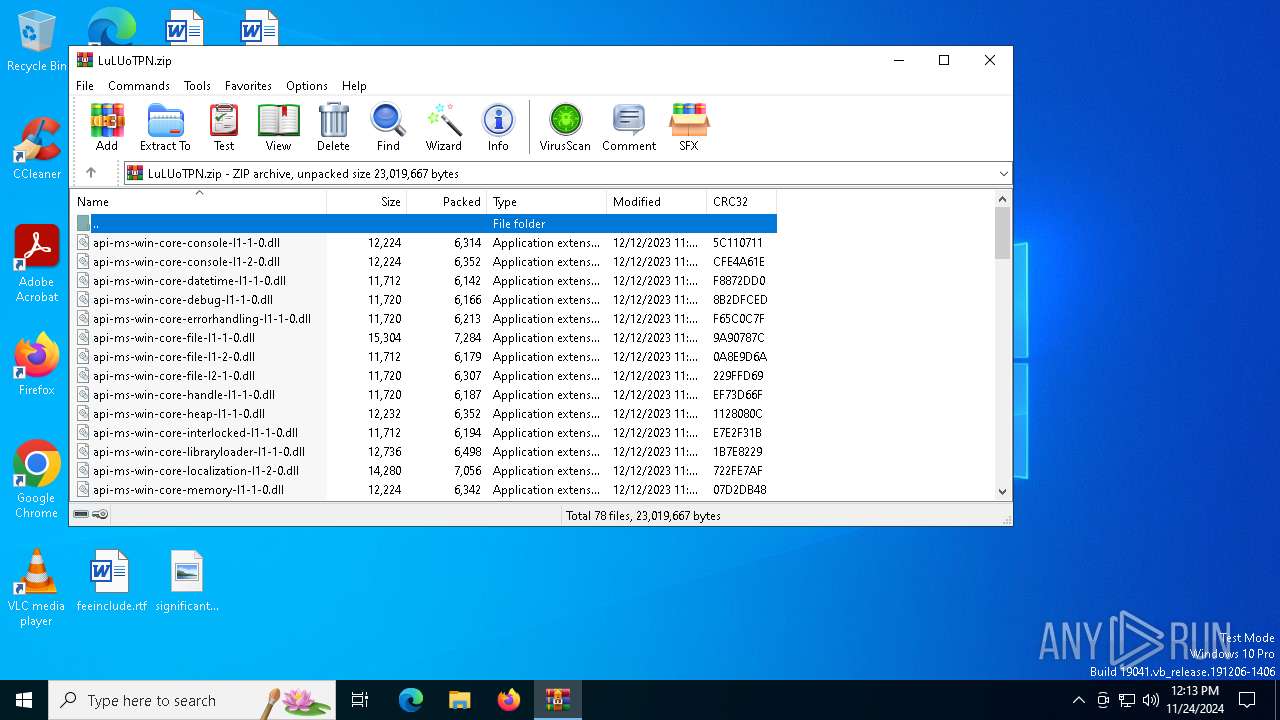
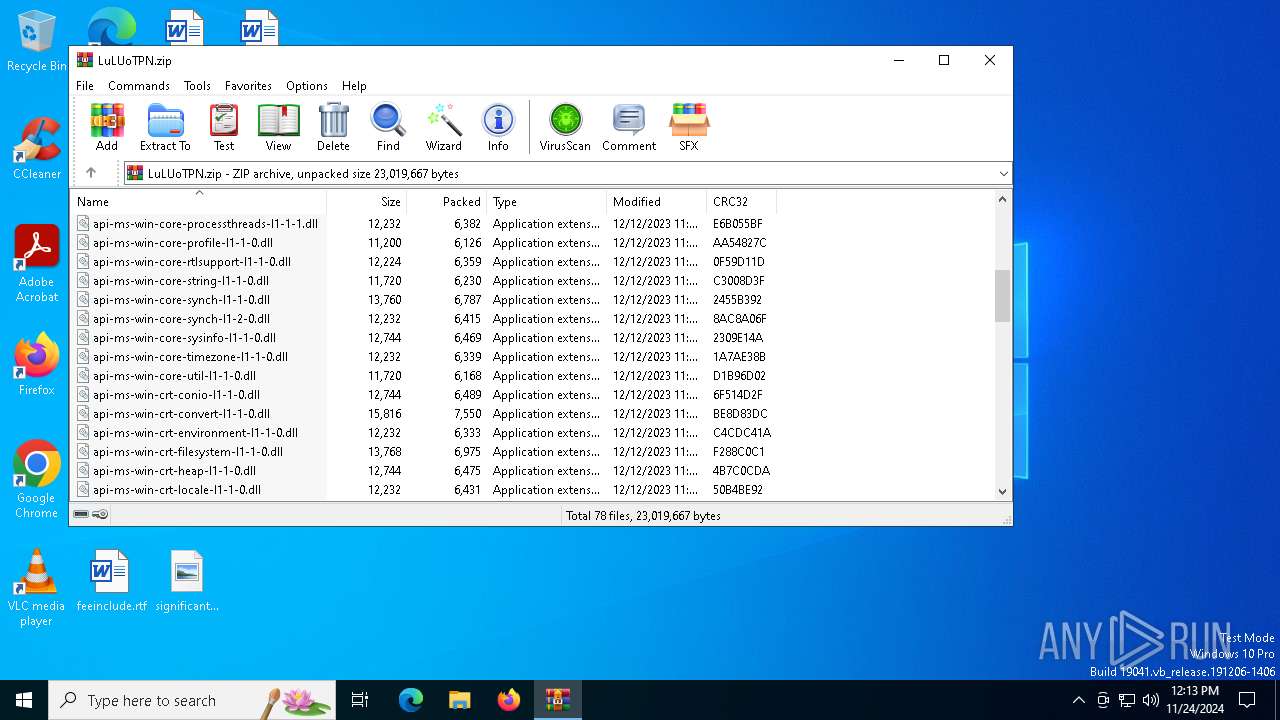
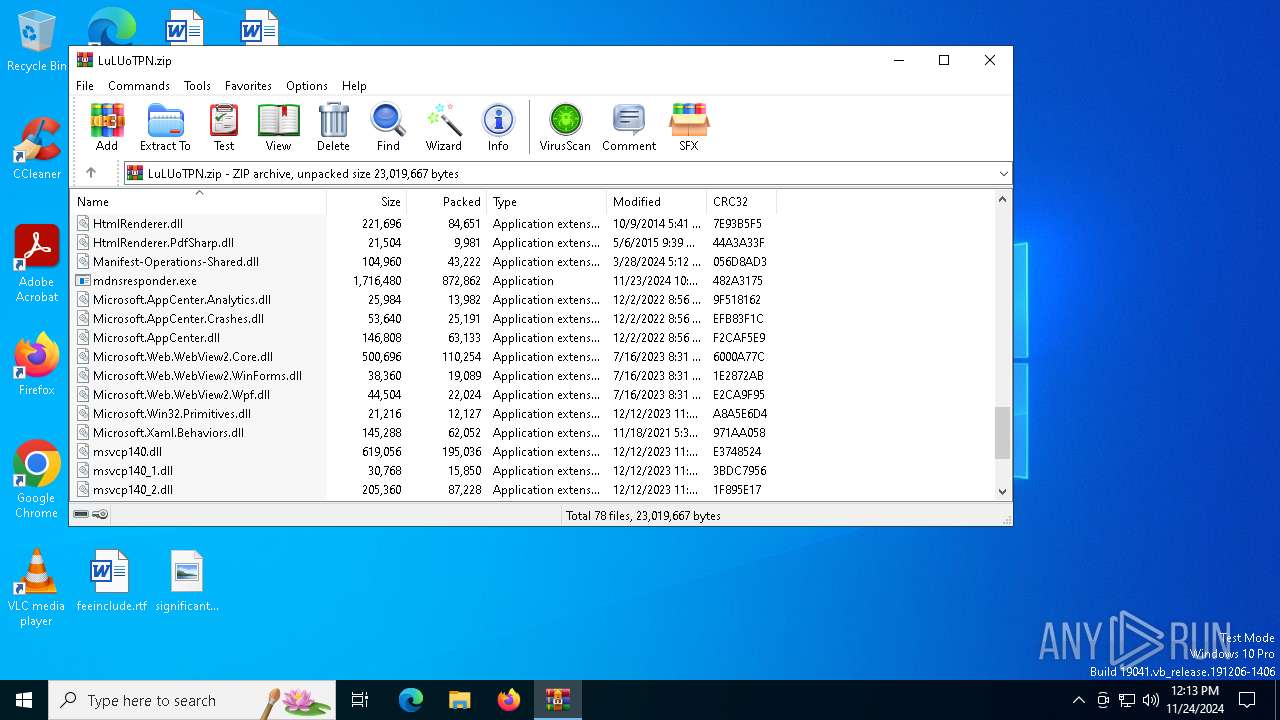
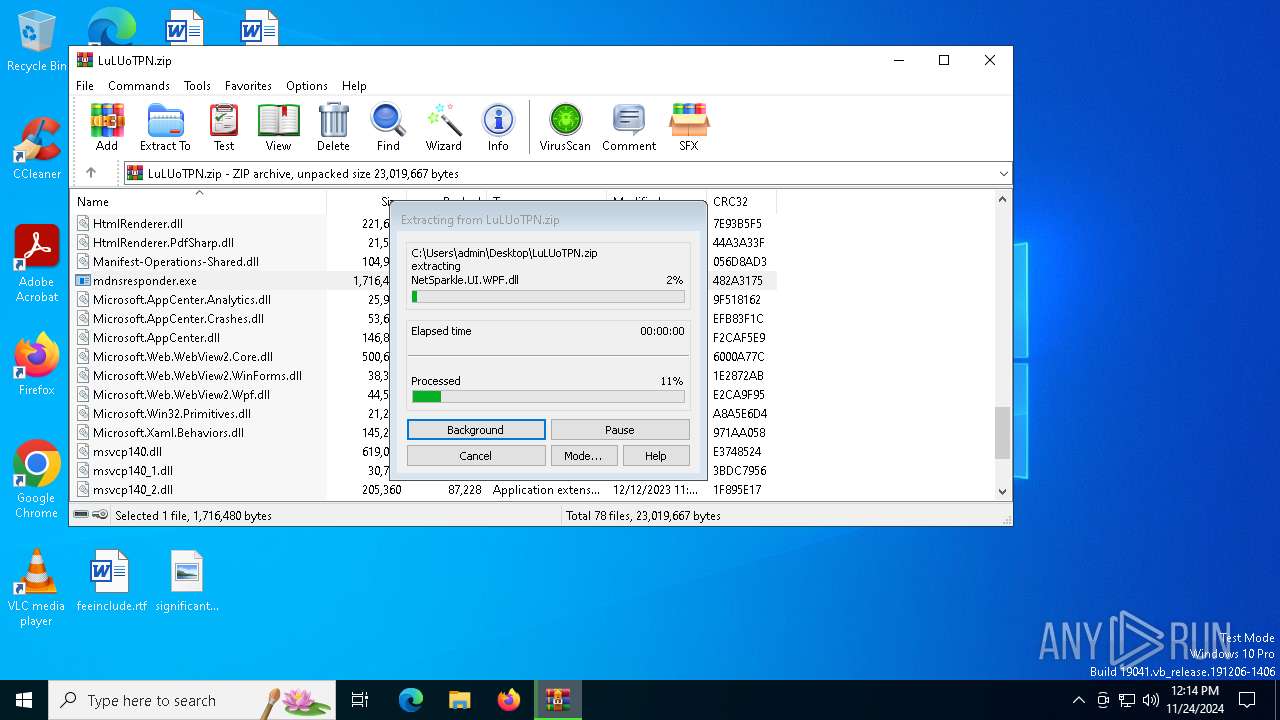
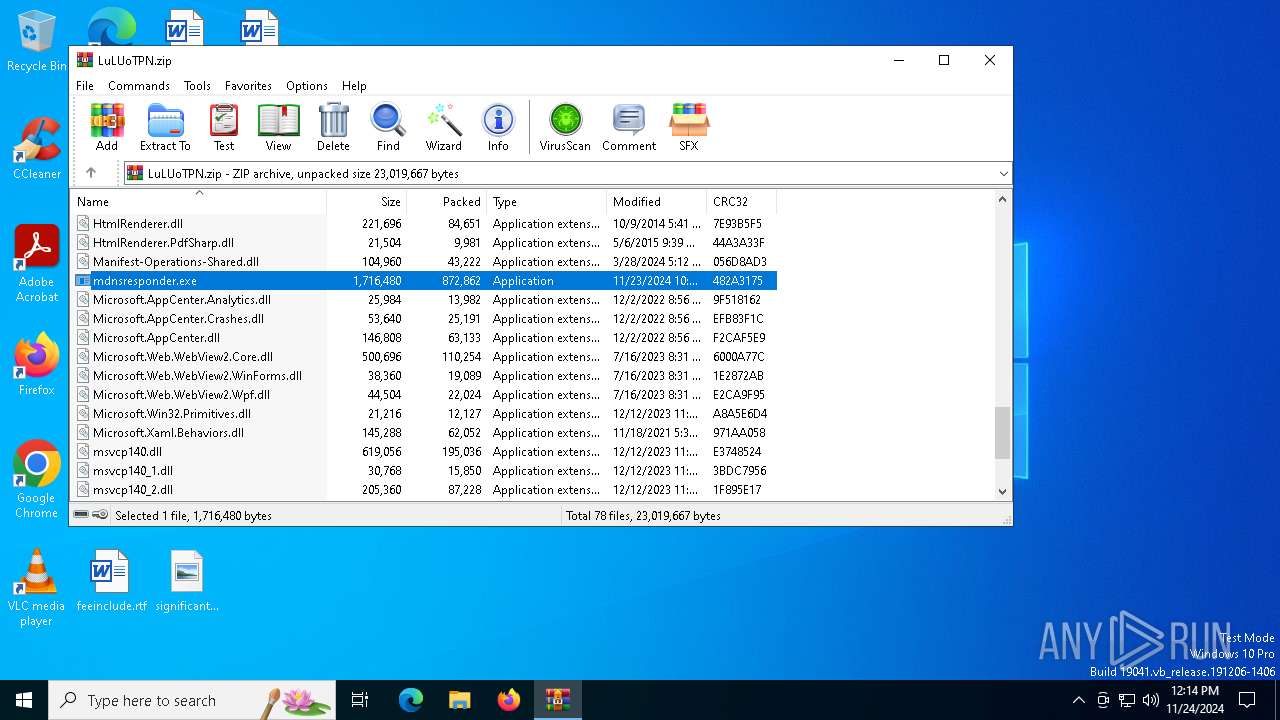
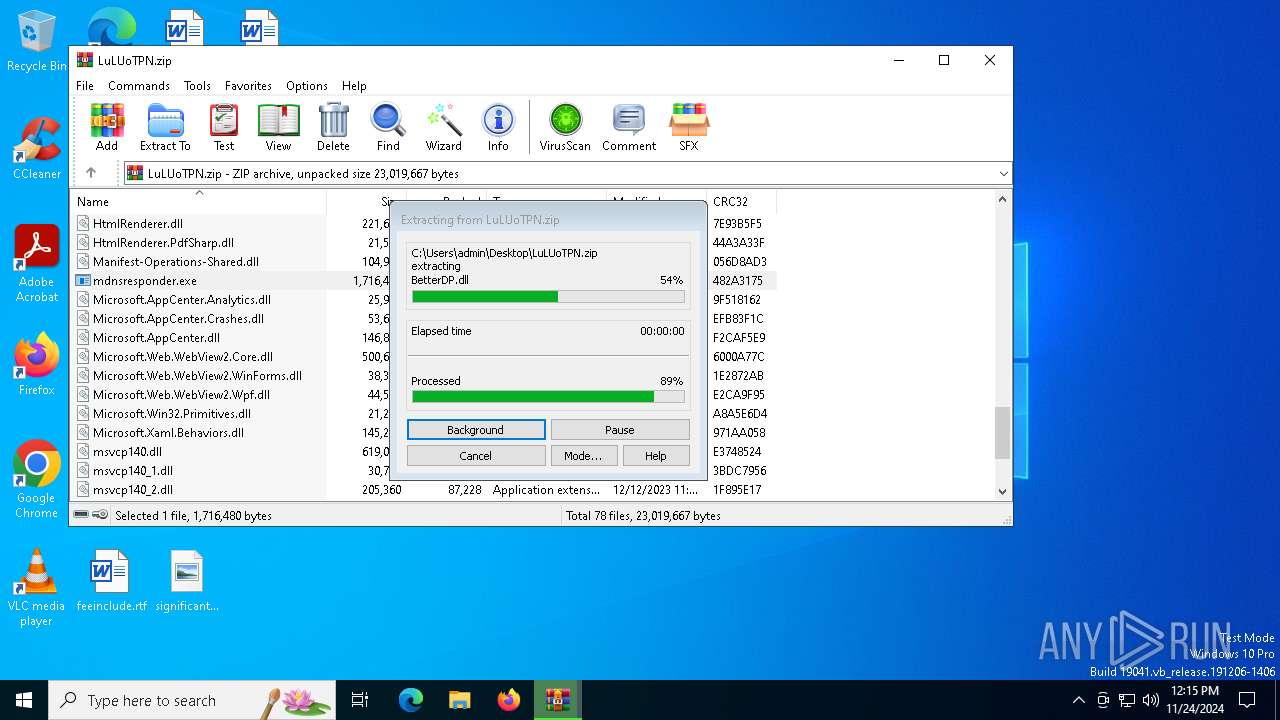
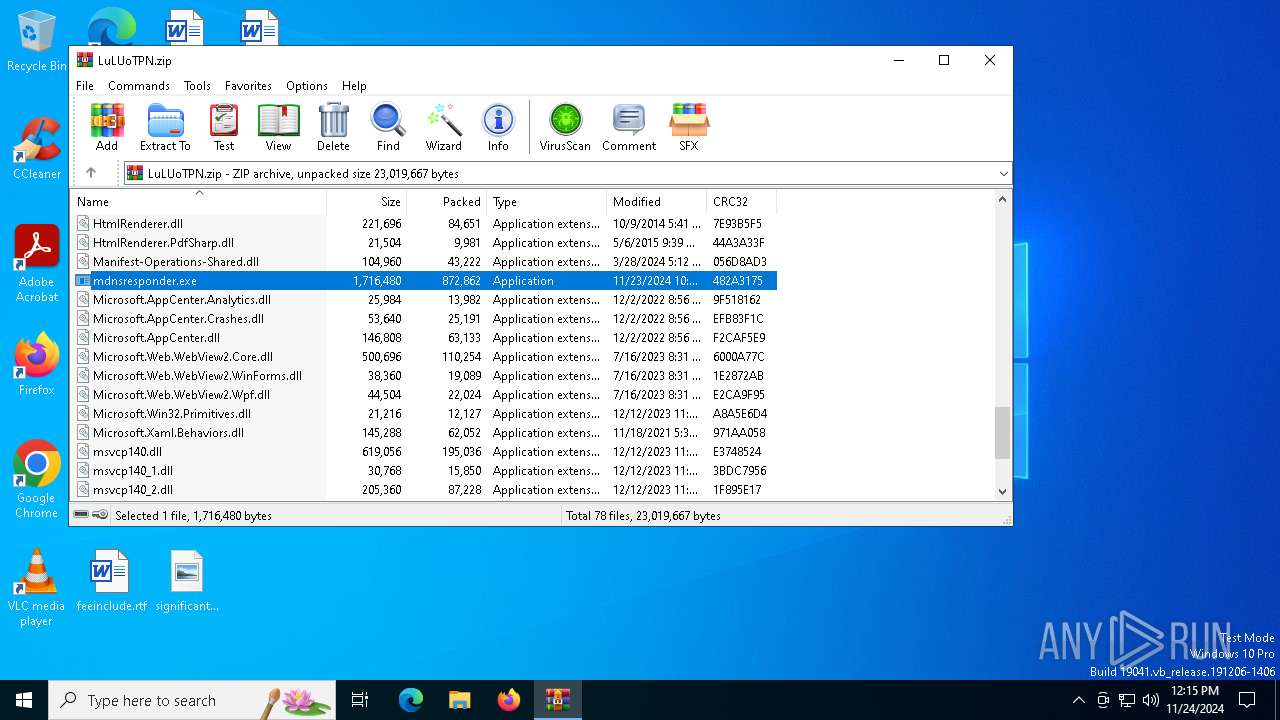
| File name: | LuLUoTPN.zip |
| Full analysis: | https://app.any.run/tasks/7bc33bdb-e3b1-4d7e-a51d-889a496290fd |
| Verdict: | Malicious activity |
| Analysis date: | November 24, 2024, 12:13:14 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | 336AE4F91BDAAB9FD548A0BB96E85BF3 |
| SHA1: | 9E30716EC6E7C9D1F099E4AE685FC9E4ECB51606 |
| SHA256: | B9068030CEDBF08F1149951AD6AFDDE65025383E3D27E2123ECE23F6363DDE51 |
| SSDEEP: | 98304:2hsXk7/vms4XL0ZqdCZN8x4AImf0AMliFaeBFAvQa5CwDXP9XIdqDdv9AjGwE7SJ:CJNdlss8UTuhWHuFa+qk2m0oJyfcPoCn |
MALICIOUS
No malicious indicators.SUSPICIOUS
Process drops SQLite DLL files
- mdnsresponder.exe (PID: 2164)
- WinRAR.exe (PID: 5548)
Executable content was dropped or overwritten
- mdnsresponder.exe (PID: 2164)
Starts application with an unusual extension
- mdnsresponder.exe (PID: 2164)
- mdnsresponder.exe (PID: 420)
Process drops legitimate windows executable
- WinRAR.exe (PID: 5548)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 5548)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2023:12:12 03:55:22 |
| ZipCRC: | 0x421f0eab |
| ZipCompressedSize: | 100323 |
| ZipUncompressedSize: | 234528 |
| ZipFileName: | HEIC_DLL_v142.dll |
Total processes
128
Monitored processes
8
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 420 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa5548.34876\mdnsresponder.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa5548.34876\mdnsresponder.exe | — | WinRAR.exe | |||||||||||
User: admin Company: iTop Inc. Integrity Level: MEDIUM Description: iTop Data Recovery Service Exit code: 1 Version: 4.0.0.168 Modules
| |||||||||||||||
| 1944 | C:\WINDOWS\SysWOW64\more.com | C:\Windows\SysWOW64\more.com | — | mdnsresponder.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: More Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2164 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa5548.25023\mdnsresponder.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa5548.25023\mdnsresponder.exe | WinRAR.exe | ||||||||||||
User: admin Company: iTop Inc. Integrity Level: MEDIUM Description: iTop Data Recovery Service Exit code: 1 Version: 4.0.0.168 Modules
| |||||||||||||||
| 2380 | C:\WINDOWS\SysWOW64\more.com | C:\Windows\SysWOW64\more.com | — | mdnsresponder.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: More Utility Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2612 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | more.com | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4444 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | more.com | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5548 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\Desktop\LuLUoTPN.zip | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 6056 | C:\WINDOWS\SysWOW64\msiexec.exe | C:\Windows\SysWOW64\msiexec.exe | more.com | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
4 979
Read events
4 971
Write events
8
Delete events
0
Modification events
| (PID) Process: | (5548) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (5548) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (5548) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (5548) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\LuLUoTPN.zip | |||
| (PID) Process: | (5548) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (5548) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (5548) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (5548) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
Executable files
154
Suspicious files
8
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5548 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa5548.25023\HEIC_SWIG_DLL_v142.dll | executable | |
MD5:0EDD60513A12689189309B50261E8979 | SHA256:54F9E01DF5A6061A4D84BDC0FC0D263A70F4FA2BAE307146BAE9D00B90226DAB | |||
| 5548 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa5548.25023\HtmlRenderer.PdfSharp.dll | executable | |
MD5:F8730360B74E1FBFD46B6EC8E4209ACC | SHA256:BDDC95E5EED0A68A54FCF2DFA99548642966DFDBF9B91940FF028E1EBF0ACDBD | |||
| 5548 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa5548.25023\Microsoft.AppCenter.Analytics.dll | executable | |
MD5:06C46082C5D357EABCA5698946BDDF19 | SHA256:52591E162196D5EB495E9530A0334A72D940EFA977881B31EF4A399BB275E13B | |||
| 5548 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa5548.25023\Microsoft.Web.WebView2.Core.dll | executable | |
MD5:28C6A96591A4890D33DEAA7DBABEBF10 | SHA256:6E7B8869B538417CC361C97A37F7CEEC92DDC8AD84E0585BCF7021DABBF6F985 | |||
| 5548 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa5548.25023\mdnsresponder.exe | executable | |
MD5:EC539C4A9C60B3690FBD891E19333362 | SHA256:1D60149CE640F4E07BCEEB8940950441025277F1EBA4F501F8AFE558030B34FE | |||
| 5548 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa5548.25023\Microsoft.Web.WebView2.Wpf.dll | executable | |
MD5:39069FA58D5BA0B2B4C6F55864DADCB6 | SHA256:D41B57A535EB6B4D78264DCEDAE2C635B1640B43EC05B82091A7DE9937C340D1 | |||
| 5548 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa5548.25023\Microsoft.Xaml.Behaviors.dll | executable | |
MD5:EC5A1ABEE150ABE698689211B07CD1EC | SHA256:B864DA9D88414877CEA9B1A016146265A5FB9D0E12F4DBB1DCCC0CC998119A54 | |||
| 5548 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa5548.25023\Microsoft.Web.WebView2.WinForms.dll | executable | |
MD5:46128473A0B3ECAA7C8980B1F8DB78DA | SHA256:9BAC64579FB676AA77D79CB469FFD4F9F69A64EF0838F52DD1AF87931924F913 | |||
| 5548 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa5548.25023\NetSparkle.dll | executable | |
MD5:624692A10058C03151F76A0D25BE332C | SHA256:98032257BF7C8F78D6FD472EDC847D6A114CC0C10B7FD92A23AB255EABDFF0A4 | |||
| 5548 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa5548.25023\msvcp140_1.dll | executable | |
MD5:474B780BEC21ACEE1C90A3859B70B3D6 | SHA256:03EFF40BCD7386B4026D142B3C854824A9FA9401711BC50749697AB33C449C62 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
12
TCP/UDP connections
26
DNS requests
8
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5892 | RUXIMICS.exe | GET | 200 | 23.53.40.178:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5892 | RUXIMICS.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 23.53.40.178:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | POST | 200 | 104.21.20.178:443 | https://sturdy-operated.cyou/api | unknown | text | 48 b | unknown |
— | — | POST | 200 | 172.67.193.71:443 | https://sturdy-operated.cyou/api | unknown | text | 2 b | unknown |
— | — | POST | 200 | 104.21.20.178:443 | https://sturdy-operated.cyou/api | unknown | text | 15 b | unknown |
— | — | POST | 200 | 104.21.20.178:443 | https://sturdy-operated.cyou/api | unknown | text | 17.1 Kb | unknown |
— | — | POST | 200 | 104.21.20.178:443 | https://sturdy-operated.cyou/api | unknown | text | 15 b | unknown |
— | — | POST | 200 | 172.67.193.71:443 | https://sturdy-operated.cyou/api | unknown | text | 15 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5892 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 104.126.37.176:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5892 | RUXIMICS.exe | 23.53.40.178:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 23.53.40.178:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2324 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
sturdy-operated.cyou |
| unknown |
self.events.data.microsoft.com |
| whitelisted |