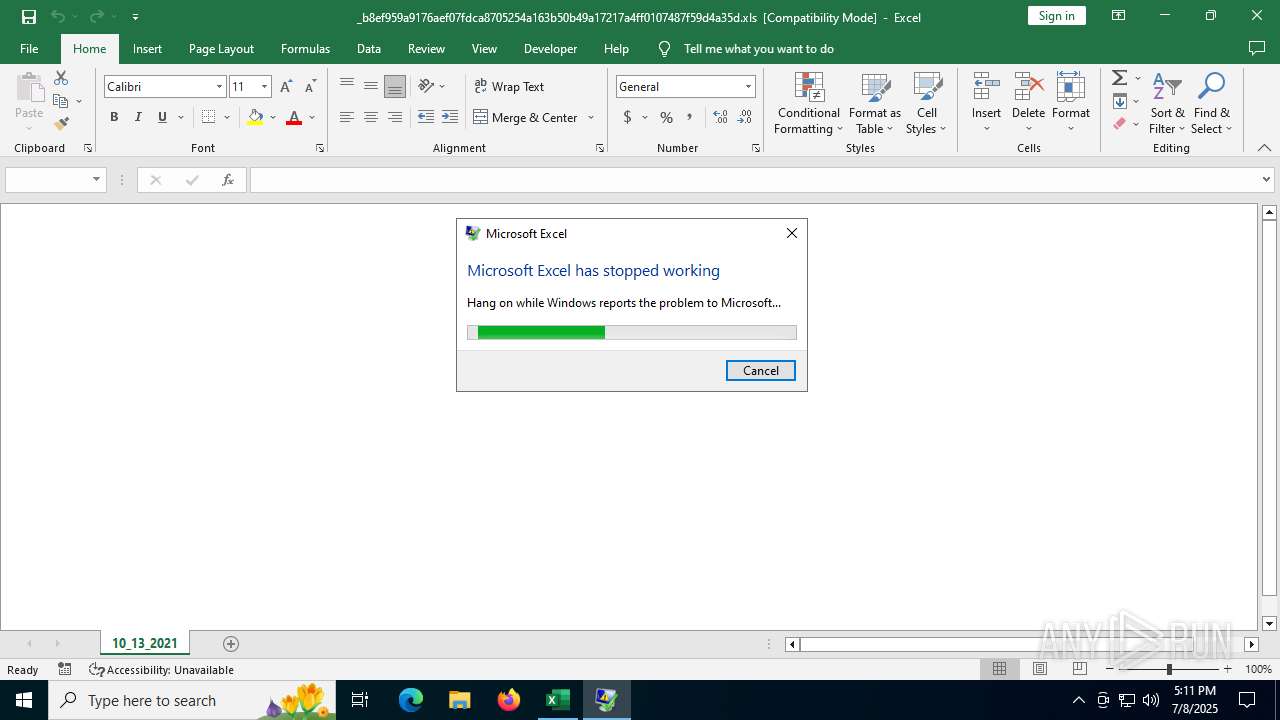
| File name: | _b8ef959a9176aef07fdca8705254a163b50b49a17217a4ff0107487f59d4a35d.xls |
| Full analysis: | https://app.any.run/tasks/1673014c-8545-4431-9af6-00fbfb043568 |
| Verdict: | Malicious activity |
| Analysis date: | July 08, 2025, 17:10:43 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| MIME: | application/vnd.ms-excel |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 10.0, Code page: 1252, Author: Inc. Intuit, Create Time/Date: Wed Oct 13 10:08:56 2021, Last Saved Time/Date: Wed Oct 13 10:08:59 2021, Security: 0 |
| MD5: | E63DEAEA51F7CC2064FF808E11E1AD55 |
| SHA1: | 4D58EC4C978988F16468CDA2323103AE62B2BAEA |
| SHA256: | B8EF959A9176AEF07FDCA8705254A163B50B49A17217A4FF0107487F59D4A35D |
| SSDEEP: | 1536:LFk3hbdlylKsgqopeJBWhZFGkE+cL2NdAA5eSUPIbjB59ZYiosYvvXvTWbxgXTPE:LFk3hbdlylKsgqopeJBWhZFGkE+cL2NZ |
MALICIOUS
Calls Win API functions (MACROS)
- EXCEL.EXE (PID: 2976)
Unusual execution from MS Office
- EXCEL.EXE (PID: 2976)
SUSPICIOUS
No suspicious indicators.INFO
Creates files in the program directory
- DWWIN.EXE (PID: 7020)
Reads Microsoft Office registry keys
- DWWIN.EXE (PID: 7020)
Checks proxy server information
- DWWIN.EXE (PID: 7020)
- slui.exe (PID: 4084)
Reads the software policy settings
- DWWIN.EXE (PID: 7020)
- slui.exe (PID: 4084)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .xls | | | Microsoft Excel sheet (48) |
|---|---|---|
| .xls | | | Microsoft Excel sheet (alternate) (39.2) |
EXIF
FlashPix
| Author: | Inc. Intuit |
|---|---|
| LastModifiedBy: | - |
| CreateDate: | 2021:10:13 10:08:56 |
| ModifyDate: | 2021:10:13 10:08:59 |
| Security: | None |
| CodePage: | Windows Latin 1 (Western European) |
| Company: | - |
| AppVersion: | 16 |
| ScaleCrop: | No |
| LinksUpToDate: | No |
| SharedDoc: | No |
| HyperlinksChanged: | No |
| TitleOfParts: | 10_13_2021 |
| HeadingPairs: |
|
| CompObjUserTypeLen: | 32 |
| CompObjUserType: | Microsoft Excel 2003 Worksheet |
Total processes
141
Monitored processes
3
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2976 | "C:\Program Files\Microsoft Office\Root\Office16\EXCEL.EXE" C:\Users\admin\Desktop\_b8ef959a9176aef07fdca8705254a163b50b49a17217a4ff0107487f59d4a35d.xls | C:\Program Files\Microsoft Office\root\Office16\EXCEL.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Excel Exit code: 4 Version: 16.0.16026.20146 Modules
| |||||||||||||||
| 4084 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7020 | C:\WINDOWS\system32\dwwin.exe -x -s 952 | C:\Windows\System32\DWWIN.EXE | EXCEL.EXE | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Error Reporting Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
18 868
Read events
18 599
Write events
253
Delete events
16
Modification events
| (PID) Process: | (2976) EXCEL.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\Common\ClientTelemetry\Sampling |
| Operation: | write | Name: | 1 |
Value: 01D014000000001000B24E9A3E02000000000000000600000000000000 | |||
| (PID) Process: | (2976) EXCEL.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Excel\Resiliency\StartupItems |
| Operation: | write | Name: | wm. |
Value: 776D2E00A00B00000100000000000000B66DB2452BF0DB0100000000 | |||
| (PID) Process: | (2976) EXCEL.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Excel |
| Operation: | write | Name: | FontInfoCache |
Value: 6000000060000000F5FFFFFF0000000000000000000000009001000000000000000000205400610068006F006D00610000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000050000001B000000000000000D0000000B000000020000000200000000000000330000000000000000000000F5FFFFFF0000000000000000000000009001000000000000000000205300650067006F006500200055004900000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000060000001C000000000000000D0000000B000000020000000200000000000000330000000000000000000000F5FFFFFF000000000000000000000000BC02000000000000000000205400610068006F006D006100000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000600000020000000000000000D0000000B000000020000000200000000000000330000000000000000000000F3FFFFFF0000000000000000000000009001000000000000000000005400610068006F006D00610000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000060000002000000000000000100000000D000000030000000300000000000000330000000000000000000000F3FFFFFF000000000000000000000000E803000000000000000000005400610068006F006D00610000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000070000002600000000000000100000000D000000030000000300000000000000330000000000000000000000F1FFFFFF000000000000000000000000900100000000000000000000430061006C0069006200720069000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000080000001A00000000000000120000000E000000040000000300000000000000330000000000000000000000F3FFFFFF0000000000000000000000009001000000000000000000005300650067006F006500200055004900000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000070000002100000000000000110000000E000000030000000400000000000000330000000000000000000000F3FFFFFF000000000000000000000000BC02000000000000000000005300650067006F006500200055004900000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000080000002100000000000000110000000E000000030000000400000000000000330000000000000000000000F3FFFFFF0000000000000000000000009001000000000000000000205300650067006F006500200055004900000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000070000002100000000000000110000000E000000030000000400000000000000330000000000000000000000F3FFFFFF000000000000000000000000BC02000000000000000000205300650067006F006500200055004900000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000080000002100000000000000110000000E000000030000000400000000000000330000000000000000000000F5FFFFFF0000000000000000000000009001000000000000000000205300650067006F006500200055004900000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000060000001C000000000000000D0000000B000000020000000200000000000000330000000000000000000000F1FFFFFF000000000000000000000000900100000000000000000000430061006C0069006200720069000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000080000001A00000000000000120000000E000000040000000300000000000000330000000000000000000000F5FFFFFF0000000000000000000000009001000000000000000000205300650067006F006500200055004900000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000060000001C000000000000000D0000000B000000020000000200000000000000330000000000000000000000F5FFFFFF0000000000000000000000009001000000000000000000205400610068006F006D00610000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000050000001B000000000000000D0000000B000000020000000200000000000000330000000000000000000000F5FFFFFF000000000000000000000000BC02000000000000000000205300650067006F006500200055004900000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000060000001C000000000000000D0000000B000000020000000200000000000000330000000000000000000000F1FFFFFF000000000000000000000000900100000000000000000000430061006C0069006200720069000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000080000001A00000000000000120000000E000000040000000300000000000000330000000000000000000000F3FFFFFF000000000000000000000000BC02000000000000000000005300650067006F006500200055004900000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000080000002100000000000000110000000E000000030000000400000000000000330000000000000000000000 | |||
| (PID) Process: | (2976) EXCEL.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\Roaming |
| Operation: | write | Name: | RoamingConfigurableSettings |
Value: DC00000000000000803A0900E90707000200080011000A003A00F801000000000000000000000000201C0000201C00008051010080510100805101008051010080F4030080F4030080F403002C01000084030000805101000000000084030000805101000A0000001E0000001E000000000000000000000080510100010000000100000000000000000000000000000000000000008D2700008D2700008D2700010000000A000000805101000000300000003000000030000000000084030000805101001E0000008403000080510100050000000500000005000000 | |||
| (PID) Process: | (2976) EXCEL.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Excel\Resiliency\StartupItems |
| Operation: | delete value | Name: | wm. |
Value: 海. | |||
| (PID) Process: | (2976) EXCEL.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Excel\Resiliency\StartupItems |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (2976) EXCEL.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Excel\Resiliency |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (2976) EXCEL.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Excel\Resiliency\StartupItems |
| Operation: | write | Name: | ko. |
Value: 6B6F2E00A00B000000000040010000005C7B03462BF0DB01CA00000002000000BA0000000400000063003A005C00750073006500720073005C00610064006D0069006E005C006400650073006B0074006F0070005C005F0062003800650066003900350039006100390031003700360061006500660030003700660064006300610038003700300035003200350034006100310036003300620035003000620034003900610031003700320031003700610034006600660030003100300037003400380037006600350039006400340061003300350064002E0078006C007300000000000000 | |||
| (PID) Process: | (2976) EXCEL.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Excel\Resiliency\DocumentRecovery\17736C |
| Operation: | write | Name: | 17736C |
Value: 04000000A00B00005C00000043003A005C00550073006500720073005C00610064006D0069006E005C004400650073006B0074006F0070005C005F0062003800650066003900350039006100390031003700360061006500660030003700660064006300610038003700300035003200350034006100310036003300620035003000620034003900610031003700320031003700610034006600660030003100300037003400380037006600350039006400340061003300350064002E0078006C007300000000001700000043003A005C00550073006500720073005C00610064006D0069006E005C004400650073006B0074006F0070005C000100000000000000506803462BF0DB016C7317006C73170000000000E0020000001000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2976) EXCEL.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Excel\Resiliency\DocumentRecovery\17736C |
| Operation: | write | Name: | 17736C |
Value: 04000000A00B00005C00000043003A005C00550073006500720073005C00610064006D0069006E005C004400650073006B0074006F0070005C005F0062003800650066003900350039006100390031003700360061006500660030003700660064006300610038003700300035003200350034006100310036003300620035003000620034003900610031003700320031003700610034006600660030003100300037003400380037006600350039006400340061003300350064002E0078006C007300000000001700000043003A005C00550073006500720073005C00610064006D0069006E005C004400650073006B0074006F0070005C000100000000000000506803462BF0DB016C7317006C73170000000000E0020000001800000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
Executable files
0
Suspicious files
13
Text files
5
Unknown types
7
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7020 | DWWIN.EXE | C:\ProgramData\Microsoft\Windows\WER\ReportQueue\AppCrash_EXCEL.EXE_f0ba593678c823b3c7333937273fe7d2c1fa42_00000000_93fe19da-3dac-49fa-8b97-b320d8e38e4a\Report.wer | — | |
MD5:— | SHA256:— | |||
| 2976 | EXCEL.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\WebServiceCache\AllUsers\officeclient.microsoft.com\5FB1A747-D35D-4756-A330-EBAC9CDB1196 | xml | |
MD5:FF2821D3FA97E613907847F3EB7883CB | SHA256:FD596F2DC92E0A6DC7815FA2D1D962B72BC05F8BBEB7281D368722477E2A5D6A | |||
| 2976 | EXCEL.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Office\Recent\_b8ef959a9176aef07fdca8705254a163b50b49a17217a4ff0107487f59d4a35d.xls.LNK | lnk | |
MD5:26134BAF7443A45FA5A89C64F752E220 | SHA256:3E6CAEC0177F4335380141916C99F445C6D0A1293AE87D534E1AFDC4F6F874D9 | |||
| 2976 | EXCEL.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Office\Recent\index.dat | ini | |
MD5:061474CF6E04677907E918F093A23733 | SHA256:E62DBD0723B6176FB74A90A3E620E3D875D9F4B539D0E306BCD8CA93E4AC6023 | |||
| 2976 | EXCEL.EXE | C:\Users\admin\AppData\Local\Microsoft\TokenBroker\Cache\56a61aeb75d8f5be186c26607f4bb213abe7c5ec.tbres | binary | |
MD5:871D2F0FA06EC89120BD71E59AFEC19C | SHA256:5F6CA707D5915602C6A7C5C77013CD1548191591BB97413679E6D96A793C6186 | |||
| 2976 | EXCEL.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\Personalization\Governance\Anonymous\floodgatecampaigns.json.tmp | tss | |
MD5:308B5A1F5138608A5E231269DB621E72 | SHA256:33DEBAC7B1F51E23B1440FE356846C902ADC89F986B2A94E250F1DC25B4A1180 | |||
| 2976 | EXCEL.EXE | C:\Users\admin\AppData\Local\Microsoft\TokenBroker\Cache\089d66ba04a8cec4bdc5267f42f39cf84278bb67.tbres | binary | |
MD5:DD3828FB8020BEDE8DF966474043FE7B | SHA256:4104710F094184026A309282F5AFA6C5FB179EC75519CB21526DB09CBF920E72 | |||
| 2976 | EXCEL.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\UsageMetricsStore\FileActivityStoreV3\Excel\1380790193167760279.C4 | gmc | |
MD5:BB7DF04E1B0A2570657527A7E108AE23 | SHA256:C35020473AED1B4642CD726CAD727B63FFF2824AD68CEDD7FFB73C7CBD890479 | |||
| 7020 | DWWIN.EXE | C:\ProgramData\Microsoft\Windows\WER\Temp\WER86F3.tmp.WERInternalMetadata.xml | xml | |
MD5:0A1E4DFB3259FF99A2798AEBFFA3F6A4 | SHA256:18BF421ED43665844CD68E9363E02C6DB3DE89C9699EADCD23BF83054837EBBF | |||
| 2976 | EXCEL.EXE | C:\Users\admin\AppData\Local\Temp\~DF78EB5104C0CBFDB4.TMP | document | |
MD5:C9AC1DA214474EDE4F194221CDA83A5D | SHA256:EF9133F140CBA3DF6E65E9DAF059518D00DCB6CA7E4767DC186779232A299885 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
40
TCP/UDP connections
56
DNS requests
25
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2140 | RUXIMICS.exe | GET | 200 | 2.16.168.124:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 2.16.168.124:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | GET | 200 | 2.16.168.124:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
2140 | RUXIMICS.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 52.109.28.46:443 | https://officeclient.microsoft.com/config16/?lcid=1033&syslcid=1033&uilcid=1033&build=16.0.16026&crev=3 | unknown | — | 181 Kb | whitelisted |
— | — | GET | 200 | 52.123.129.14:443 | https://ecs.office.com/config/v2/Office/excel/16.0.16026.20146/Production/CC?&Clientid=%7bD61AB268-C26A-439D-BB15-2A0DEDFCA6A3%7d&Application=excel&Platform=win32&Version=16.0.16026.20146&MsoVersion=16.0.16026.20002&SDX=fa000000002.2.0.1907.31003&SDX=fa000000005.1.0.1909.30011&SDX=fa000000006.1.0.1909.13002&SDX=fa000000008.1.0.1908.16006&SDX=fa000000009.1.0.1908.6002&SDX=fa000000016.1.0.1810.13001&SDX=fa000000029.1.0.1906.25001&SDX=fa000000033.1.0.1908.24001&SDX=wa104381125.1.0.1810.9001&ProcessName=excel.exe&Audience=Production&Build=ship&Architecture=x64&Language=en-US&SubscriptionLicense=false&PerpetualLicense=2019&LicenseCategory=6&LicenseSKU=Professional2019Retail&OsVersion=10.0&OsBuild=19045&Channel=CC&InstallType=C2R&SessionId=%7b60B99F60-B07A-47BA-BA57-B6CD6A096086%7d&LabMachine=false | unknown | binary | 389 Kb | whitelisted |
— | — | GET | 200 | 23.197.142.186:443 | https://fs.microsoft.com/fs/4.41/flatFontAssets.pkg | unknown | compressed | 496 Kb | whitelisted |
— | — | POST | 200 | 40.126.32.138:443 | https://login.live.com/RST2.srf | unknown | xml | 1.24 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1268 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2140 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1268 | svchost.exe | 2.16.168.124:80 | crl.microsoft.com | Akamai International B.V. | RU | whitelisted |
2140 | RUXIMICS.exe | 2.16.168.124:80 | crl.microsoft.com | Akamai International B.V. | RU | whitelisted |
5944 | MoUsoCoreWorker.exe | 2.16.168.124:80 | crl.microsoft.com | Akamai International B.V. | RU | whitelisted |
1268 | svchost.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
2140 | RUXIMICS.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
officeclient.microsoft.com |
| whitelisted |
ecs.office.com |
| whitelisted |
fs.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
messaging.engagement.office.com |
| whitelisted |
messaging.lifecycle.office.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Unknown Traffic | ET USER_AGENTS Microsoft Dr Watson User-Agent (MSDW) |