| File name: | CheraxLoader.exe |
| Full analysis: | https://app.any.run/tasks/f9605696-77fd-44ad-973e-5dbc6d951774 |
| Verdict: | Malicious activity |
| Analysis date: | June 16, 2025, 15:33:48 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32+ executable (GUI) x86-64, for MS Windows, 9 sections |
| MD5: | 1FC9C12C797276A2DC7CE7ADCB0D15A5 |
| SHA1: | F20AE20E61DBC947CCA32DAF2B57FD84A4BACB58 |
| SHA256: | B8E6348BE5899627251A955C60010050E60A71341810C5A08BC4326A3E0EC0E5 |
| SSDEEP: | 98304:alku/J4yn6eIfWES8VlpCKHwFvEbbS0+/EH9UTI9iZdSIBu40xQ0Bbvfd4hesSvm:aN/J+LBIBG9Y |
MALICIOUS
No malicious indicators.SUSPICIOUS
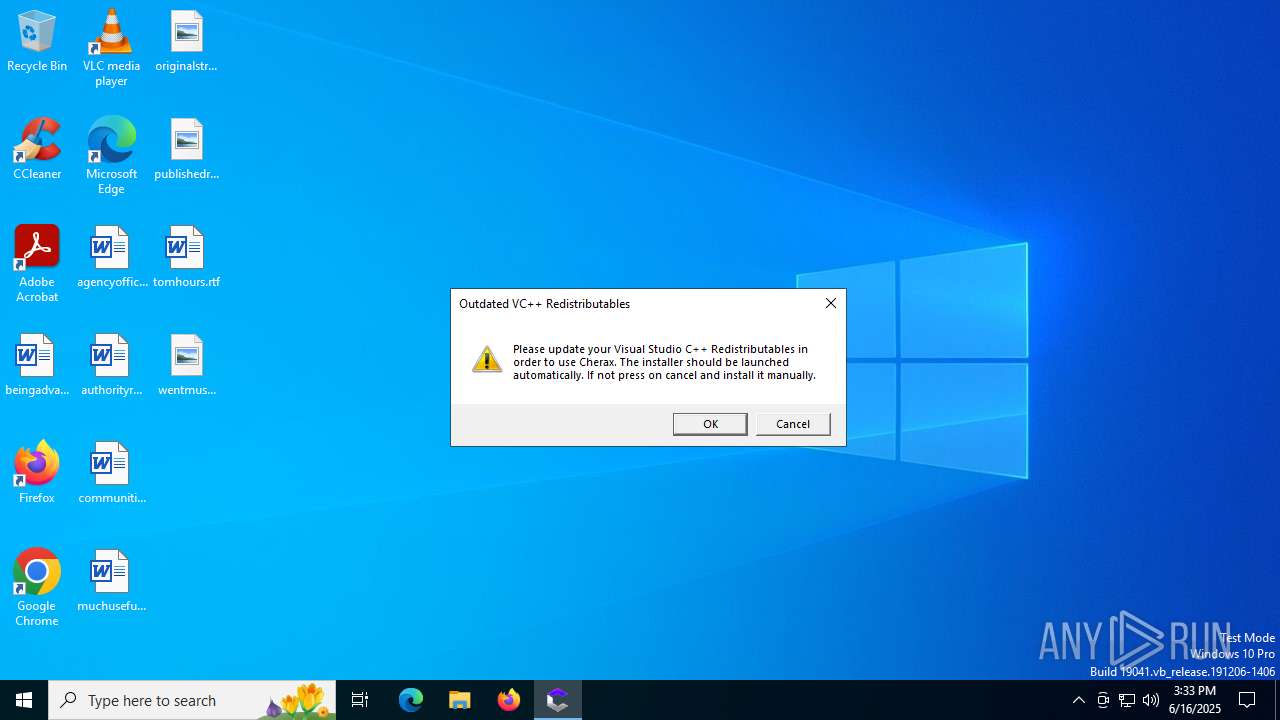
Process drops legitimate windows executable
- CheraxLoader.exe (PID: 1156)
- vc_redist.x64.exe (PID: 1712)
- vc_redist.x64.exe (PID: 6472)
- VC_redist.x64.exe (PID: 6652)
- msiexec.exe (PID: 2276)
- VC_redist.x64.exe (PID: 7120)
Starts a Microsoft application from unusual location
- vc_redist.x64.exe (PID: 6472)
- VC_redist.x64.exe (PID: 6652)
Executable content was dropped or overwritten
- vc_redist.x64.exe (PID: 1712)
- CheraxLoader.exe (PID: 1156)
- vc_redist.x64.exe (PID: 6472)
- VC_redist.x64.exe (PID: 6652)
- VC_redist.x64.exe (PID: 6868)
- VC_redist.x64.exe (PID: 7120)
Reads security settings of Internet Explorer
- vc_redist.x64.exe (PID: 6472)
Searches for installed software
- vc_redist.x64.exe (PID: 6472)
- dllhost.exe (PID: 6688)
Starts itself from another location
- vc_redist.x64.exe (PID: 6472)
The process drops C-runtime libraries
- msiexec.exe (PID: 2276)
Application launched itself
- VC_redist.x64.exe (PID: 4680)
- VC_redist.x64.exe (PID: 6868)
- updater.exe (PID: 4164)
Executes as Windows Service
- VSSVC.exe (PID: 5008)
The process executes via Task Scheduler
- updater.exe (PID: 4164)
- PLUGScheduler.exe (PID: 4156)
INFO
The sample compiled with english language support
- CheraxLoader.exe (PID: 1156)
- vc_redist.x64.exe (PID: 1712)
- vc_redist.x64.exe (PID: 6472)
- VC_redist.x64.exe (PID: 6652)
- msiexec.exe (PID: 2276)
- VC_redist.x64.exe (PID: 7120)
- VC_redist.x64.exe (PID: 6868)
Checks supported languages
- CheraxLoader.exe (PID: 1156)
- vc_redist.x64.exe (PID: 1712)
- VC_redist.x64.exe (PID: 6652)
- vc_redist.x64.exe (PID: 6472)
Reads the computer name
- CheraxLoader.exe (PID: 1156)
- vc_redist.x64.exe (PID: 6472)
- VC_redist.x64.exe (PID: 6652)
- vc_redist.x64.exe (PID: 1712)
Process checks computer location settings
- vc_redist.x64.exe (PID: 6472)
Create files in a temporary directory
- vc_redist.x64.exe (PID: 6472)
Manages system restore points
- SrTasks.exe (PID: 6148)
Executable content was dropped or overwritten
- msiexec.exe (PID: 2276)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Generic Win/DOS Executable (50) |
|---|---|---|
| .exe | | | DOS Executable Generic (49.9) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2025:05:06 12:40:55+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 14.43 |
| CodeSize: | 2911744 |
| InitializedDataSize: | 1962496 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x428ffa |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.0.0.3518 |
| ProductVersionNumber: | 1.0.0.3518 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Windows NT 32-bit |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| CompanyName: | Cherax |
| FileDescription: | Cherax Loader |
| FileVersion: | 1.0.0.3518 |
| InternalName: | Cherax.exe |
| LegalCopyright: | Copyright (C) 2019 - 2023 |
| OriginalFileName: | Cherax.exe |
| ProductName: | Cherax Loader |
| ProductVersion: | 1.0.0.3518 |
Total processes
313
Monitored processes
16
Malicious processes
3
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1156 | "C:\Users\admin\AppData\Local\Temp\CheraxLoader.exe" | C:\Users\admin\AppData\Local\Temp\CheraxLoader.exe | explorer.exe | ||||||||||||
User: admin Company: Cherax Integrity Level: HIGH Description: Cherax Loader Exit code: 1337 Version: 1.0.0.3518 Modules
| |||||||||||||||
| 1712 | "C:\Users\admin\Documents\Cherax\Cache\Downloads\vc_redist.x64.exe" | C:\Users\admin\Documents\Cherax\Cache\Downloads\vc_redist.x64.exe | CheraxLoader.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft Visual C++ 2015-2022 Redistributable (x64) - 14.44.35208 Exit code: 3010 Version: 14.44.35208.0 Modules
| |||||||||||||||
| 2276 | C:\WINDOWS\system32\msiexec.exe /V | C:\Windows\System32\msiexec.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Exit code: 0 Version: 5.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3620 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | SrTasks.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3756 | "C:\Users\admin\AppData\Local\Temp\CheraxLoader.exe" | C:\Users\admin\AppData\Local\Temp\CheraxLoader.exe | — | explorer.exe | |||||||||||
User: admin Company: Cherax Integrity Level: MEDIUM Description: Cherax Loader Exit code: 3221226540 Version: 1.0.0.3518 Modules
| |||||||||||||||
| 4156 | "C:\Program Files\RUXIM\PLUGscheduler.exe" | C:\Program Files\RUXIM\PLUGScheduler.exe | — | svchost.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Update LifeCycle Component Scheduler Exit code: 0 Version: 10.0.19041.3623 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4164 | "C:\Program Files (x86)\Google\GoogleUpdater\134.0.6985.0\updater.exe" --wake --system | C:\Program Files (x86)\Google\GoogleUpdater\134.0.6985.0\updater.exe | — | svchost.exe | |||||||||||
User: SYSTEM Company: Google LLC Integrity Level: SYSTEM Description: Google Updater Exit code: 0 Version: 134.0.6985.0 Modules
| |||||||||||||||
| 4680 | "C:\ProgramData\Package Cache\{8bdfe669-9705-4184-9368-db9ce581e0e7}\VC_redist.x64.exe" -uninstall -quiet -burn.related.upgrade -burn.ancestors={9387bec2-2f2b-48d1-a0ce-692c5df7042d} -burn.filehandle.self=1104 -burn.embedded BurnPipe.{EB829D4A-D9F4-4588-8604-31CCE65AD61D} {56F7093C-09DC-4E60-A4CC-6B00B158B4BD} 6652 | C:\ProgramData\Package Cache\{8bdfe669-9705-4184-9368-db9ce581e0e7}\VC_redist.x64.exe | — | VC_redist.x64.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft Visual C++ 2015-2022 Redistributable (x64) - 14.36.32532 Exit code: 0 Version: 14.36.32532.0 Modules
| |||||||||||||||
| 5008 | C:\WINDOWS\system32\vssvc.exe | C:\Windows\System32\VSSVC.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Volume Shadow Copy Service Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5020 | "C:\Program Files (x86)\Google\GoogleUpdater\134.0.6985.0\updater.exe" --crash-handler --system "--database=C:\Program Files (x86)\Google\GoogleUpdater\134.0.6985.0\Crashpad" --url=https://clients2.google.com/cr/report --annotation=prod=Update4 --annotation=ver=134.0.6985.0 "--attachment=C:\Program Files (x86)\Google\GoogleUpdater\updater.log" --initial-client-data=0x298,0x29c,0x2a0,0x278,0x2a4,0x85c460,0x85c46c,0x85c478 | C:\Program Files (x86)\Google\GoogleUpdater\134.0.6985.0\updater.exe | — | updater.exe | |||||||||||
User: SYSTEM Company: Google LLC Integrity Level: SYSTEM Description: Google Updater Exit code: 0 Version: 134.0.6985.0 Modules
| |||||||||||||||
Total events
12 551
Read events
11 583
Write events
600
Delete events
368
Modification events
| (PID) Process: | (6652) VC_redist.x64.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SystemRestore |
| Operation: | write | Name: | SrCreateRp (Enter) |
Value: 400000000000000021D63716D4DEDB01FC190000F0050000D5070000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (6688) dllhost.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGetSnapshots (Enter) |
Value: 480000000000000021D63716D4DEDB01201A0000101A0000D20700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (6688) dllhost.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGetSnapshots (Leave) |
Value: 480000000000000085D95616D4DEDB01201A0000101A0000D20700000100000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (6688) dllhost.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppEnumGroups (Enter) |
Value: 480000000000000085D95616D4DEDB01201A0000101A0000D10700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (6688) dllhost.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppEnumGroups (Leave) |
Value: 480000000000000085D95616D4DEDB01201A0000101A0000D10700000100000000000000010000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (6688) dllhost.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppCreate (Enter) |
Value: 480000000000000027F15D16D4DEDB01201A0000101A0000D00700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (6688) dllhost.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGatherWriterMetadata (Enter) |
Value: 4800000000000000D0A48D16D4DEDB01201A0000101A0000D30700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (5008) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\COM+ REGDB Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 480000000000000067999916D4DEDB019013000058030000E80300000100000001000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (5008) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\Registry Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 480000000000000067999916D4DEDB0190130000181B0000E80300000100000001000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (5008) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\ASR Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 4800000000000000F2FB9B16D4DEDB019013000010170000E80300000100000001000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
Executable files
68
Suspicious files
35
Text files
69
Unknown types
66
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6472 | vc_redist.x64.exe | C:\Windows\Temp\{401D4A6C-3B9E-478C-8159-9E17B088868E}\.ba\thm.xml | xml | |
MD5:F62729C6D2540015E072514226C121C7 | SHA256:F13BAE0EC08C91B4A315BB2D86EE48FADE597E7A5440DCE6F751F98A3A4D6916 | |||
| 1156 | CheraxLoader.exe | C:\Users\admin\Documents\Cherax\Cache\Downloads\vc_redist.x64.exe | executable | |
MD5:DE118D5E2AB7AAA7E1A08A0ECF84E8C9 | SHA256:D62841375B90782B1829483AC75695CCEF680A8F13E7DE569B992EF33C6CD14A | |||
| 1156 | CheraxLoader.exe | C:\Users\admin\Documents\Cherax\Loader.log | text | |
MD5:DF628FBBD487314F72725710B6EE903C | SHA256:7118933B01820BBB5A9E667614BE6161519EEAC4843F354B0E1165481E400589 | |||
| 6472 | vc_redist.x64.exe | C:\Windows\Temp\{401D4A6C-3B9E-478C-8159-9E17B088868E}\.ba\thm.wxl | xml | |
MD5:FBFCBC4DACC566A3C426F43CE10907B6 | SHA256:70400F181D00E1769774FF36BCD8B1AB5FBC431418067D31B876D18CC04EF4CE | |||
| 1712 | vc_redist.x64.exe | C:\Windows\Temp\{20224DD9-4F72-4953-98A0-9D99B8C3CAFC}\.cr\vc_redist.x64.exe | executable | |
MD5:DB2FEF85F5046E85EC2FC24089FE500A | SHA256:3814F726440521E12762A4F1D83DFDCF4C62B2CF71873987D87ECD54330095B5 | |||
| 6472 | vc_redist.x64.exe | C:\Windows\Temp\{401D4A6C-3B9E-478C-8159-9E17B088868E}\.ba\logo.png | image | |
MD5:D6BD210F227442B3362493D046CEA233 | SHA256:335A256D4779EC5DCF283D007FB56FD8211BBCAF47DCD70FE60DED6A112744EF | |||
| 6472 | vc_redist.x64.exe | C:\Windows\Temp\{401D4A6C-3B9E-478C-8159-9E17B088868E}\.ba\wixstdba.dll | executable | |
MD5:F68F43F809840328F4E993A54B0D5E62 | SHA256:E921F69B9FB4B5AD4691809D06896C5F1D655AB75E0CE94A372319C243C56D4E | |||
| 6472 | vc_redist.x64.exe | C:\Windows\Temp\{401D4A6C-3B9E-478C-8159-9E17B088868E}\.ba\license.rtf | text | |
MD5:04B33F0A9081C10E85D0E495A1294F83 | SHA256:8099DC3CF9502C335DA829E5C755948A12E3E6DE490EB492A99DEB673D883D8B | |||
| 6472 | vc_redist.x64.exe | C:\Windows\Temp\{401D4A6C-3B9E-478C-8159-9E17B088868E}\.ba\1029\thm.wxl | xml | |
MD5:16343005D29EC431891B02F048C7F581 | SHA256:07FB3EC174F25DFBE532D9D739234D9DFDA8E9D34F01FE660C5B4D56989FA779 | |||
| 6472 | vc_redist.x64.exe | C:\Windows\Temp\{401D4A6C-3B9E-478C-8159-9E17B088868E}\.ba\1028\license.rtf | text | |
MD5:2B063D92663595DFE4781AE687A03D86 | SHA256:44C76290F7A2E45940E8338912FEB49BCF4E071CFA85D2D34762857743ACBC8D | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
18
TCP/UDP connections
83
DNS requests
43
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
764 | lsass.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
5436 | SearchApp.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
2484 | msedge.exe | GET | 200 | 150.171.27.11:80 | http://edge.microsoft.com/browsernetworktime/time/1/current?cup2key=2:3ufK0RWnDcXZEOXrqNo_s1vbiS8e-hgBat-_ruPOCzw&cup2hreq=e3b0c44298fc1c149afbf4c8996fb92427ae41e4649b934ca495991b7852b855 | unknown | — | — | whitelisted |
1028 | backgroundTaskHost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA77flR%2B3w%2FxBpruV2lte6A%3D | unknown | — | — | whitelisted |
2716 | svchost.exe | GET | 200 | 23.209.209.135:80 | http://x1.c.lencr.org/ | unknown | — | — | whitelisted |
5436 | SearchApp.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
3832 | backgroundTaskHost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA77flR%2B3w%2FxBpruV2lte6A%3D | unknown | — | — | whitelisted |
764 | lsass.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEApDqVCbATUviZV57HIIulA%3D | unknown | — | — | whitelisted |
4944 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
2276 | msiexec.exe | GET | 200 | 23.216.77.6:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
5944 | MoUsoCoreWorker.exe | 51.104.136.2:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1268 | svchost.exe | 51.104.136.2:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3676 | RUXIMICS.exe | 51.104.136.2:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1156 | CheraxLoader.exe | 2.20.153.252:443 | aka.ms | Telkom-Internet | ZA | whitelisted |
764 | lsass.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
1156 | CheraxLoader.exe | 23.50.131.82:443 | download.visualstudio.microsoft.com | Akamai International B.V. | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4944 | svchost.exe | 20.190.160.4:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4944 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
aka.ms |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
download.visualstudio.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |
Threats
Process | Message |
|---|---|
msiexec.exe | Failed to release Service
|