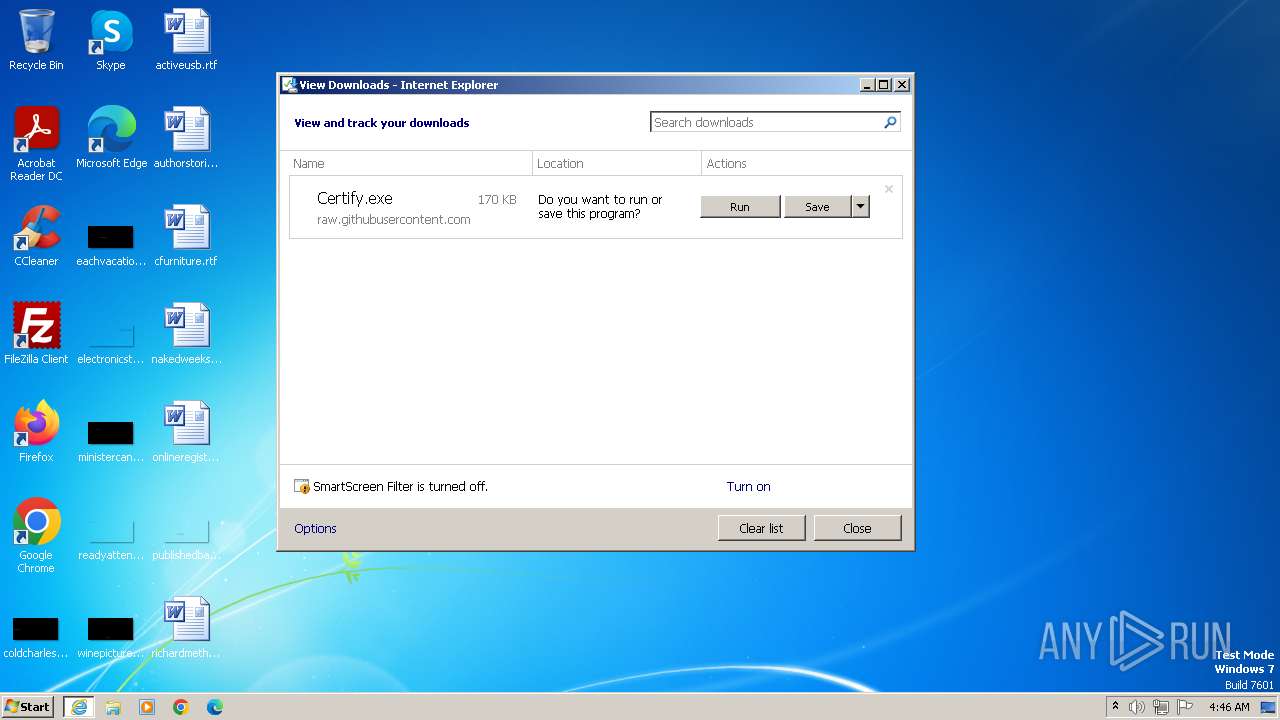
| URL: | https://github.com/r3motecontrol/Ghostpack-CompiledBinaries/raw/master/Certify.exe |
| Full analysis: | https://app.any.run/tasks/56ecefbe-7fbf-4a82-b9ad-9b2e38ebbe8a |
| Verdict: | Malicious activity |
| Analysis date: | October 25, 2023, 03:46:37 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| SHA1: | CB8566F3281FEE781C9F9F40387E742E9D21BE1A |
| SHA256: | B8DFA56C0C5F2549A1246FF791764FEEFF3A61D9B763D3C762412DAA9B98F779 |
| SSDEEP: | 3:N8tEdnWIjiuG6QFSlfLNn:2uQ/3UBn |
MALICIOUS
Application was dropped or rewritten from another process
- Certify.exe (PID: 2956)
SUSPICIOUS
No suspicious indicators.INFO
Drops the executable file immediately after the start
- iexplore.exe (PID: 3996)
- iexplore.exe (PID: 2752)
Application launched itself
- iexplore.exe (PID: 2752)
The process uses the downloaded file
- iexplore.exe (PID: 2752)
Checks supported languages
- Certify.exe (PID: 2956)
Reads the computer name
- Certify.exe (PID: 2956)
Manual execution by a user
- taskmgr.exe (PID: 3520)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
41
Monitored processes
4
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2752 | "C:\Program Files\Internet Explorer\iexplore.exe" "https://github.com/r3motecontrol/Ghostpack-CompiledBinaries/raw/master/Certify.exe" | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2956 | "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\Certify.exe" | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\Certify.exe | — | iexplore.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Certify Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 3520 | "C:\Windows\system32\taskmgr.exe" | C:\Windows\System32\taskmgr.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Task Manager Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3996 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:2752 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
Total events
16 861
Read events
16 805
Write events
56
Delete events
0
Modification events
| (PID) Process: | (2752) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 0 | |||
| (PID) Process: | (2752) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 30847387 | |||
| (PID) Process: | (2752) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30847437 | |||
| (PID) Process: | (2752) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (2752) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (2752) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (2752) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (2752) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 4600000056010000090000000000000000000000000000000400000000000000C0E333BBEAB1D3010000000000000000000000000100000002000000C0A8016B000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2752) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (2752) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
Executable files
3
Suspicious files
13
Text files
3
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3996 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | compressed | |
MD5:1BFE591A4FE3D91B03CDF26EAACD8F89 | SHA256:9CF94355051BF0F4A45724CA20D1CC02F76371B963AB7D1E38BD8997737B13D8 | |||
| 3996 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\50CD3D75D026C82E2E718570BD6F44D0_D222662A57BAA60D2F5EA0D2CC7B2F1C | binary | |
MD5:8484B9F6429D1A4EFAD167318360305F | SHA256:45A60CD4F41EDD66569C5695E67BD6E042208887E79FEDBF5057E12660BAC314 | |||
| 3996 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\B398B80134F72209547439DB21AB308D_ADE4E4D3A3BCBCA5C39C54D362D88565 | binary | |
MD5:167B3838B95C5C1694673E39777F0F55 | SHA256:C45B408EB6242D01313C8337A00FCA0FFE643F2D59D82C0E3E1ADBB28F42F685 | |||
| 3996 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\50CD3D75D026C82E2E718570BD6F44D0_D222662A57BAA60D2F5EA0D2CC7B2F1C | binary | |
MD5:73D4D8CD8EC9C39312A79B34856B7A04 | SHA256:889923FD3CD229E3AAB7E82CBED7ADBF07E8005DE0D7640EDF3CAA1A2EBB2002 | |||
| 2752 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\Recovery\Active\{1C9E456B-72E9-11EE-B150-12A9866C77DE}.dat | binary | |
MD5:92BC5C8E53B5500F443775CB8F938B99 | SHA256:2F8B19E5AE596DC08C1F94DA2E8832A4C423C27ACCB251F29A9FBE415C78479A | |||
| 3996 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\Certify[1].exe | executable | |
MD5:308A9CC8C7B647CDA04D50207805C970 | SHA256:33395DE7242393ED2CAF3F18B4C12A963C8100924AAF3DD378F8D74D0E0140C8 | |||
| 3996 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\B398B80134F72209547439DB21AB308D_A4CF52CCA82D7458083F7280801A3A04 | binary | |
MD5:1EABDCA26DCA1D490C0707A59952D447 | SHA256:A5DB5A4589E4A90D16950AC51E51C2BF0C07C62D834BD8E7952271C7A0E8AB13 | |||
| 2752 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\Certify.exe.nxtap83.partial:Zone.Identifier | text | |
MD5:FBCCF14D504B7B2DBCB5A5BDA75BD93B | SHA256:EACD09517CE90D34BA562171D15AC40D302F0E691B439F91BE1B6406E25F5913 | |||
| 3996 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\B398B80134F72209547439DB21AB308D_A4CF52CCA82D7458083F7280801A3A04 | binary | |
MD5:7F3D187A61AF0831C9F03A9C0BD808B5 | SHA256:6B830AD5DF7BD10FD41FA9ABD3F73A16678ACC46E5E11D51C2CEA28B714FE603 | |||
| 2752 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DF6EB7F1FF75B439E9.TMP | binary | |
MD5:2A1C27E398BEE40C712E8CA4A28CD5EA | SHA256:AB962B9AADC8DEA08A2701816026A196B702E631EB8F940E86F7B133FBC4850C | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
14
DNS requests
6
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3996 | iexplore.exe | GET | 200 | 209.197.3.8:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?49bc7857dc93f557 | unknown | compressed | 4.66 Kb | unknown |
3996 | iexplore.exe | GET | 200 | 209.197.3.8:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?8f869686e34b7eef | unknown | compressed | 4.66 Kb | unknown |
3996 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQrHR6YzPN2BNbByL0VoiTIBBMAOAQUCrwIKReMpTlteg7OM8cus%2B37w3oCEAzQqL7GMs%2FmReygqbCE%2Bxw%3D | unknown | der | 312 b | unknown |
3996 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAfy81yHqHeveu%2FpR5k1Jb0%3D | unknown | der | 471 b | unknown |
3996 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAbY2QTVWENG9oovp1QifsQ%3D | unknown | der | 471 b | unknown |
2752 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | binary | 471 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3996 | iexplore.exe | 140.82.121.3:443 | — | GITHUB | US | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
3996 | iexplore.exe | 209.197.3.8:80 | ctldl.windowsupdate.com | STACKPATH-CDN | US | whitelisted |
3996 | iexplore.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
3996 | iexplore.exe | 185.199.108.133:443 | raw.githubusercontent.com | FASTLY | US | unknown |
2656 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2752 | iexplore.exe | 152.199.19.161:443 | iecvlist.microsoft.com | EDGECAST | US | whitelisted |
2752 | iexplore.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
ctldl.windowsupdate.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
raw.githubusercontent.com |
| shared |
iecvlist.microsoft.com |
| whitelisted |
r20swj13mr.microsoft.com |
| whitelisted |