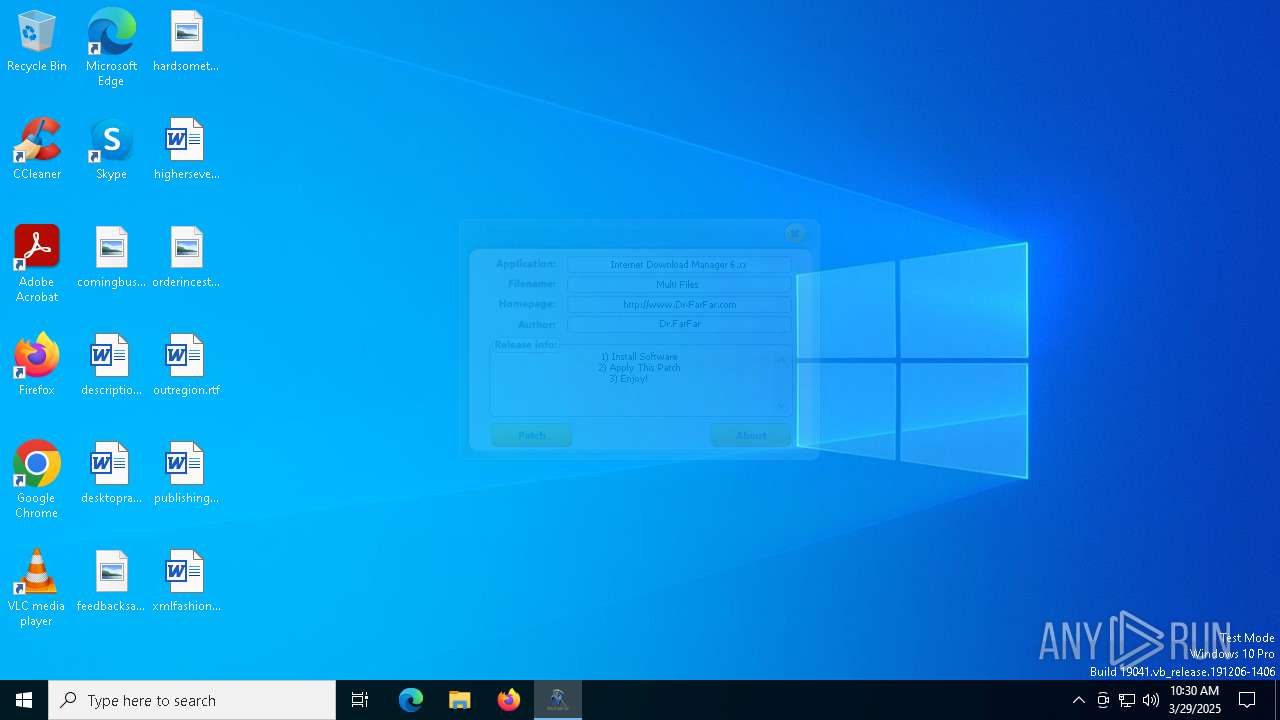
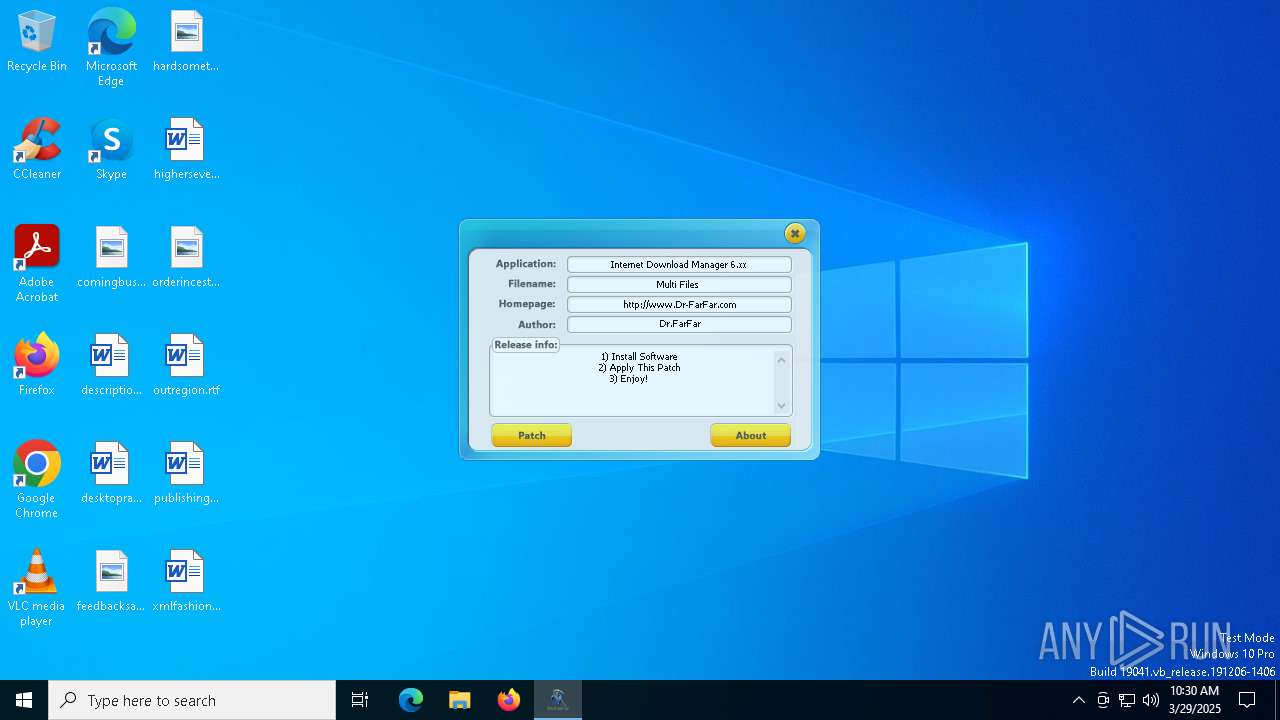
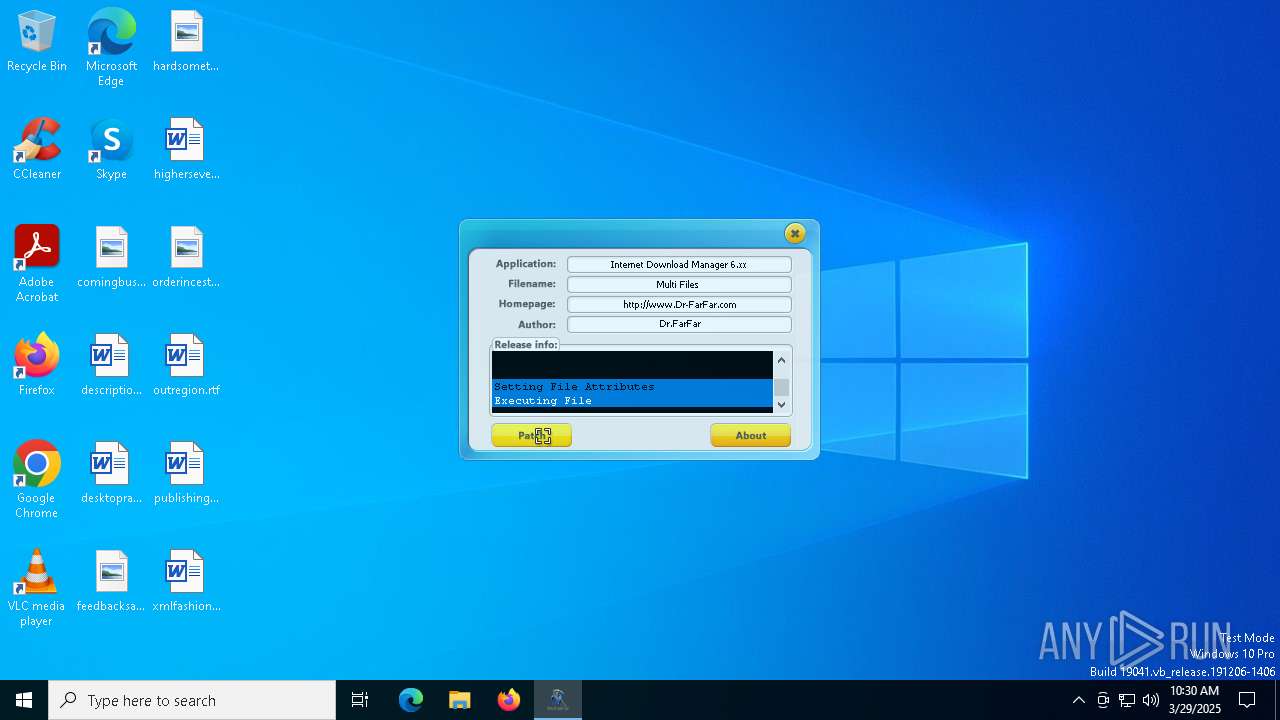
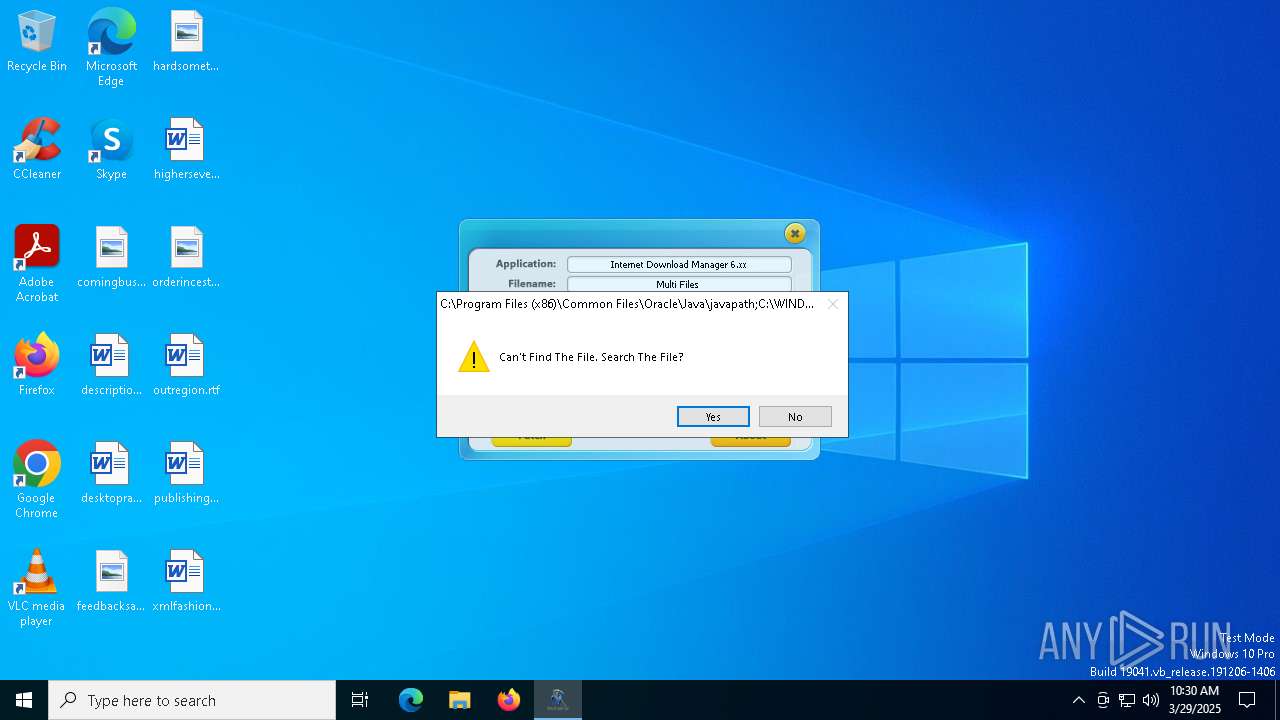
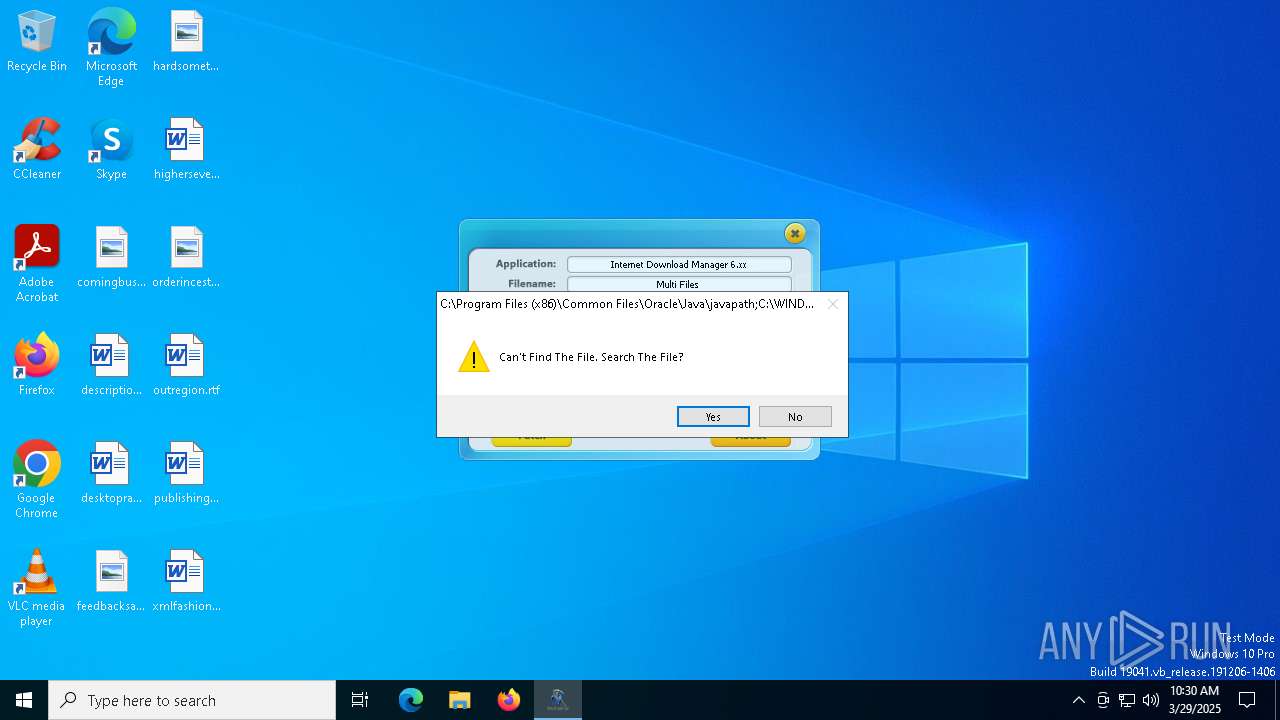
| File name: | IDM 6.x Patch - No Update v10.9.exe |
| Full analysis: | https://app.any.run/tasks/7babed89-e7d5-4c3a-9d6f-fe1452d45862 |
| Verdict: | Malicious activity |
| Analysis date: | March 29, 2025, 10:30:22 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 5 sections |
| MD5: | 2D2B364D2FD203F6D9F7B8D7E2DC3C8B |
| SHA1: | C1A2AA36DEDCF9A1161582D1EAEF961537236F44 |
| SHA256: | B8C108891BF770128E0BAF7BF28F72E6A63BA6FB8DACF98A846237DCFEFAB65F |
| SSDEEP: | 24576:vBQibW+3Pk5jsg8YAuYTKsQd35EV7nA6O9mj09XbDC4yRvZ4Ecj39IO2WkZ8XPwb:vBQibW+3Pk5jsg8YDYTKsQd35EV7nA6r |
MALICIOUS
No malicious indicators.SUSPICIOUS
Reads security settings of Internet Explorer
- IDM 6.x Patch - No Update v10.9.exe (PID: 896)
- IDM-Kill.exe (PID: 6272)
Uses REG/REGEDIT.EXE to modify registry
- IDM 6.x Patch - No Update v10.9.exe (PID: 896)
Executable content was dropped or overwritten
- IDM 6.x Patch - No Update v10.9.exe (PID: 896)
Executing commands from a ".bat" file
- IDM-Kill.exe (PID: 6272)
Uses TASKKILL.EXE to kill process
- cmd.exe (PID: 2136)
Starts CMD.EXE for commands execution
- IDM-Kill.exe (PID: 6272)
There is functionality for taking screenshot (YARA)
- IDM 6.x Patch - No Update v10.9.exe (PID: 896)
Searches for installed software
- explorer.exe (PID: 6512)
INFO
Create files in a temporary directory
- IDM 6.x Patch - No Update v10.9.exe (PID: 896)
- IDM-Kill.exe (PID: 6272)
The sample compiled with english language support
- IDM 6.x Patch - No Update v10.9.exe (PID: 896)
Checks supported languages
- IDM 6.x Patch - No Update v10.9.exe (PID: 896)
- IDM-Kill.exe (PID: 6272)
Reads the computer name
- IDM 6.x Patch - No Update v10.9.exe (PID: 896)
- IDM-Kill.exe (PID: 6272)
Process checks computer location settings
- IDM 6.x Patch - No Update v10.9.exe (PID: 896)
- IDM-Kill.exe (PID: 6272)
Reads security settings of Internet Explorer
- explorer.exe (PID: 6512)
UPX packer has been detected
- IDM 6.x Patch - No Update v10.9.exe (PID: 896)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (64.6) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (15.4) |
| .exe | | | Win32 Executable (generic) (10.5) |
| .exe | | | Generic Win/DOS Executable (4.6) |
| .exe | | | DOS Executable Generic (4.6) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2012:12:21 20:59:46+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 10 |
| CodeSize: | 512 |
| InitializedDataSize: | 743424 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x102b |
| OSVersion: | 5 |
| ImageVersion: | - |
| SubsystemVersion: | 5 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 10.9.0.0 |
| ProductVersionNumber: | 10.9.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Windows NT 32-bit |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| Email: | inFo@Dr-FarFar.CoM |
| Website: | https://www.Dr-FarFar.com |
| Comments: | www.Dr-FarFar.com |
| CompanyName: | Dr.FarFar | www.Dr-FarFar.com |
| FileDescription: | IDM 6.x Patch - No Update |
| FileVersion: | 10.9.0.0 |
| InternalName: | IDM 6.x Patch - No Update.exe |
| LegalCopyright: | Copyright © Dr.FarFar |
| LegalTrademarks: | www.Dr-FarFar.com |
| OriginalFileName: | IDM 6.x Patch - No Update.exe |
| ProductName: | IDM 6.x Patch - No Update |
| ProductVersion: | 10.9.0.0 |
| AssemblyVersion: | 10.9.0.0 |
Total processes
146
Monitored processes
12
Malicious processes
1
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 896 | "C:\Users\admin\AppData\Local\Temp\IDM 6.x Patch - No Update v10.9.exe" | C:\Users\admin\AppData\Local\Temp\IDM 6.x Patch - No Update v10.9.exe | explorer.exe | ||||||||||||
User: admin Company: Dr.FarFar | www.Dr-FarFar.com Integrity Level: HIGH Description: IDM 6.x Patch - No Update Version: 10.9.0.0 Modules
| |||||||||||||||
| 1056 | taskkill /T /F /IM "IDMan.exe" | C:\Windows\SysWOW64\taskkill.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Terminates Processes Exit code: 128 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2136 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\AppData\Local\Temp\CD35.tmp\Kill.bat" "C:\WINDOWS\IDM-Kill.exe"" | C:\Windows\SysWOW64\cmd.exe | — | IDM-Kill.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 128 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3240 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | — | SppExtComObj.Exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4300 | "C:\Users\admin\AppData\Local\Temp\IDM 6.x Patch - No Update v10.9.exe" | C:\Users\admin\AppData\Local\Temp\IDM 6.x Patch - No Update v10.9.exe | — | explorer.exe | |||||||||||
User: admin Company: Dr.FarFar | www.Dr-FarFar.com Integrity Level: MEDIUM Description: IDM 6.x Patch - No Update Exit code: 3221226540 Version: 10.9.0.0 Modules
| |||||||||||||||
| 5244 | taskkill /T /F /IM "IEMonitor.exe" | C:\Windows\SysWOW64\taskkill.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Terminates Processes Exit code: 128 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5556 | "C:\Windows\System32\regedit.exe" /s "C:\Users\admin\AppData\Local\Temp\\regpatch.reg" | C:\Windows\SysWOW64\regedit.exe | — | IDM 6.x Patch - No Update v10.9.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Editor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5668 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6272 | "C:\WINDOWS\IDM-Kill.exe" | C:\Windows\IDM-Kill.exe | — | IDM 6.x Patch - No Update v10.9.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 6512 | C:\WINDOWS\explorer.exe /factory,{5BD95610-9434-43C2-886C-57852CC8A120} -Embedding | C:\Windows\explorer.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Version: 10.0.19041.3758 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
15 645
Read events
15 622
Write events
11
Delete events
12
Modification events
| (PID) Process: | (5556) regedit.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Internet Download Manager |
| Operation: | delete value | Name: | FName |
Value: | |||
| (PID) Process: | (5556) regedit.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Internet Download Manager |
| Operation: | delete value | Name: | LName |
Value: | |||
| (PID) Process: | (5556) regedit.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Internet Download Manager |
| Operation: | delete value | Name: | |
Value: | |||
| (PID) Process: | (5556) regedit.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Internet Download Manager |
| Operation: | delete value | Name: | Serial |
Value: | |||
| (PID) Process: | (5556) regedit.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\DownloadManager |
| Operation: | delete value | Name: | FName |
Value: | |||
| (PID) Process: | (5556) regedit.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\DownloadManager |
| Operation: | delete value | Name: | LName |
Value: | |||
| (PID) Process: | (5556) regedit.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\DownloadManager |
| Operation: | delete value | Name: | |
Value: | |||
| (PID) Process: | (5556) regedit.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\DownloadManager |
| Operation: | delete value | Name: | Serial |
Value: | |||
| (PID) Process: | (6512) explorer.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | NodeSlots |
Value: 02020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202 | |||
| (PID) Process: | (6512) explorer.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | MRUListEx |
Value: 0000000004000000030000000E000000100000000F0000000C0000000D0000000B000000050000000A000000090000000800000001000000070000000600000002000000FFFFFFFF | |||
Executable files
3
Suspicious files
0
Text files
2
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 896 | IDM 6.x Patch - No Update v10.9.exe | C:\Users\admin\AppData\Local\Temp\regpatch.reg | text | |
MD5:00E363D22614EA923F7830FED69727E9 | SHA256:FF98F2F735B5CC4F137989C609A7B19930EC68D24EF3F99FB4EDC65F66EC412B | |||
| 896 | IDM 6.x Patch - No Update v10.9.exe | C:\Users\admin\AppData\Local\Temp\bassmod.dll | executable | |
MD5:E4EC57E8508C5C4040383EBE6D367928 | SHA256:8AD9E47693E292F381DA42DDC13724A3063040E51C26F4CA8E1F8E2F1DDD547F | |||
| 896 | IDM 6.x Patch - No Update v10.9.exe | C:\Windows\IDM-Kill.exe | executable | |
MD5:E24E55FD8BD1E163E5588997DF3F966B | SHA256:2D6854DC437486BCCD6B86D955229835A6BAB1ED0EBA3327F79D7AF4E1878B69 | |||
| 896 | IDM 6.x Patch - No Update v10.9.exe | C:\Users\admin\AppData\Local\Temp\dup2patcher.dll | executable | |
MD5:C71F41C656285E66A848F516ECCE99C8 | SHA256:65B0DE5A994B8E729D1419653C605D19121BC53F8A5F9EED705A3CCD18ECAB47 | |||
| 6272 | IDM-Kill.exe | C:\Users\admin\AppData\Local\Temp\CD35.tmp\Kill.bat | text | |
MD5:218CC35BBB8DC5BBB73985C5D3484019 | SHA256:54667FEEEB952ACE354163B9198BD910A960436C9CA9D67C77DFC364565AFDD7 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
28
DNS requests
16
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 2.16.241.12:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
2924 | SearchApp.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
2924 | SearchApp.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
7320 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
7320 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | 2.16.241.12:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3216 | svchost.exe | 20.198.162.76:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | SG | whitelisted |
6544 | svchost.exe | 20.190.159.130:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6544 | svchost.exe | 184.30.131.245:80 | ocsp.digicert.com | AKAMAI-AS | US | whitelisted |
2104 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2924 | SearchApp.exe | 2.23.227.208:443 | www.bing.com | Ooredoo Q.S.C. | QA | whitelisted |
2924 | SearchApp.exe | 204.79.197.222:443 | fp.msedge.net | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
www.bing.com |
| whitelisted |
fp.msedge.net |
| whitelisted |
th.bing.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |