| File name: | 010.dll.patched |
| Full analysis: | https://app.any.run/tasks/facaa918-fa77-42c4-a4a9-eaed66bcba1a |
| Verdict: | Malicious activity |
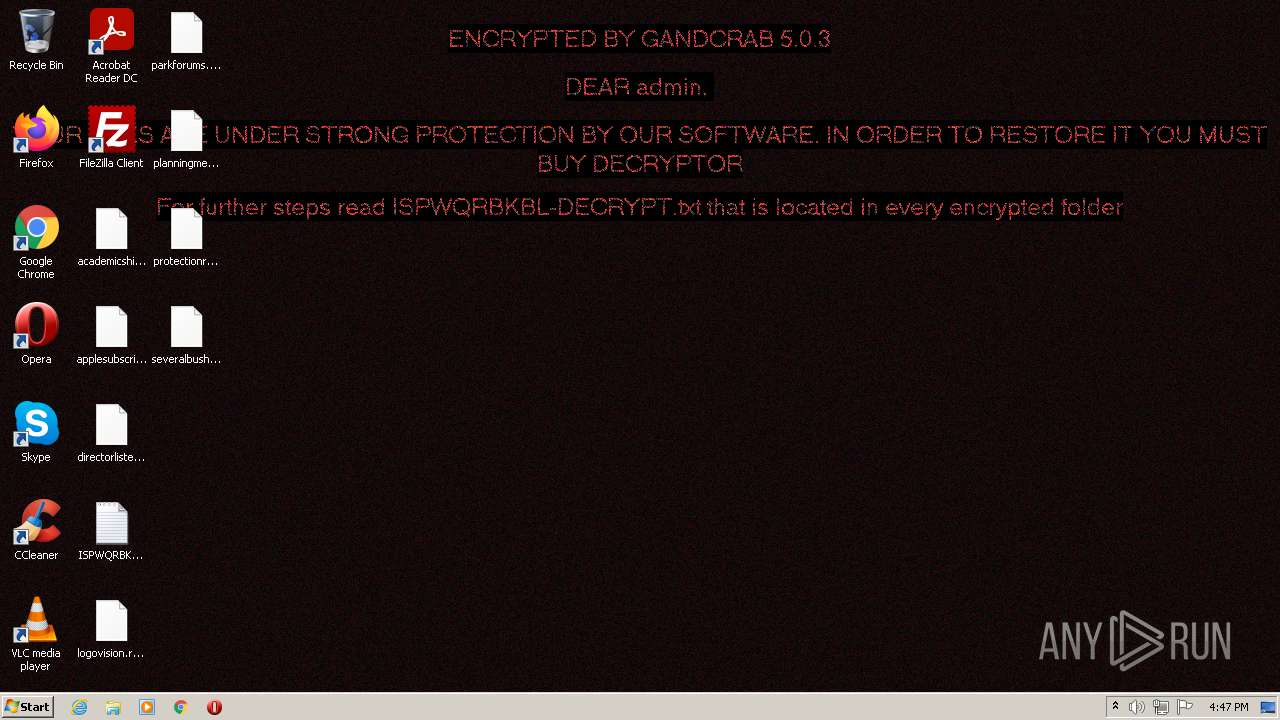
| Threats: | GandCrab is probably one of the most famous Ransomware. A Ransomware is a malware that asks the victim to pay money in order to restore access to encrypted files. If the user does not cooperate the files are forever lost. |
| Analysis date: | August 19, 2021, 15:46:40 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (DLL) (console) Intel 80386, for MS Windows |
| MD5: | E6714BCE3D8D9D0749572BD20ADA0D96 |
| SHA1: | 4F2DEDC17145CE8EBDEE9EFF605AA5AD1E87717E |
| SHA256: | B8B50AC7B9BFC4BE19C9DD9B4FDC469773D8E1EEE72194F2779C522F953E6ADB |
| SSDEEP: | 12288:KW285kea6pRwcA6Vbpzms7B9+lf+u+i0Qw:gvRt6Vvdu+i0Qw |
MALICIOUS
GandCrab keys found
- wermgr.exe (PID: 1248)
Writes file to Word startup folder
- wermgr.exe (PID: 1248)
Actions looks like stealing of personal data
- wermgr.exe (PID: 1248)
Steals credentials from Web Browsers
- wermgr.exe (PID: 1248)
Deletes shadow copies
- wermgr.exe (PID: 1248)
Renames files like Ransomware
- wermgr.exe (PID: 1248)
GANDCRAB detected
- wermgr.exe (PID: 1248)
SUSPICIOUS
Uses RUNDLL32.EXE to load library
- rundll32.exe (PID: 3928)
Reads Environment values
- wermgr.exe (PID: 1248)
Application launched itself
- rundll32.exe (PID: 3928)
Reads the cookies of Mozilla Firefox
- wermgr.exe (PID: 1248)
Creates files like Ransomware instruction
- wermgr.exe (PID: 1248)
Drops a file with a compile date too recent
- wermgr.exe (PID: 1248)
Checks supported languages
- wmic.exe (PID: 2792)
Reads the computer name
- wmic.exe (PID: 2792)
Creates files in the user directory
- wermgr.exe (PID: 1248)
INFO
Loads main object executable
- rundll32.exe (PID: 3928)
Checks supported languages
- rundll32.exe (PID: 3928)
- rundll32.exe (PID: 2292)
- wermgr.exe (PID: 1248)
Reads the computer name
- wermgr.exe (PID: 1248)
Reads CPU info
- wermgr.exe (PID: 1248)
Dropped object may contain Bitcoin addresses
- wermgr.exe (PID: 1248)
Checks Windows Trust Settings
- wermgr.exe (PID: 1248)
Reads settings of System Certificates
- wermgr.exe (PID: 1248)
Dropped object may contain TOR URL's
- wermgr.exe (PID: 1248)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (42.2) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (37.3) |
| .dll | | | Win32 Dynamic Link Library (generic) (8.8) |
| .exe | | | Win32 Executable (generic) (6) |
| .exe | | | Generic Win/DOS Executable (2.7) |
EXIF
EXE
| Subsystem: | Windows command line |
|---|---|
| SubsystemVersion: | 6.2 |
| ImageVersion: | 6.2 |
| OSVersion: | 6.2 |
| EntryPoint: | 0x1b70 |
| UninitializedDataSize: | - |
| InitializedDataSize: | 652800 |
| CodeSize: | 4608 |
| LinkerVersion: | 10.1 |
| PEType: | PE32 |
| TimeStamp: | 2012:07:26 04:42:02+02:00 |
| MachineType: | Intel 386 or later, and compatibles |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_CUI |
| Compilation Date: | 26-Jul-2012 02:42:02 |
| Detected languages: |
|
| Debug artifacts: |
|
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0090 |
| Pages in file: | 0x0003 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x0000 |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x0000 |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x000000F8 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 5 |
| Time date stamp: | 26-Jul-2012 02:42:02 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.text | 0x00001000 | 0x000011F8 | 0x00001200 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 6.13854 |
.rdata | 0x00003000 | 0x000103DA | 0x00010400 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 5.44455 |
.data | 0x00014000 | 0x00000A6C | 0x00000400 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 1.27607 |
.rsrc | 0x00015000 | 0x0008D820 | 0x0008DA00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 5.00894 |
.reloc | 0x000A3000 | 0x00000A5E | 0x00000C00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_DISCARDABLE, IMAGE_SCN_MEM_READ | 1.69342 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
2 | 5.04378 | 548 | UNKNOWN | English - United States | RT_MANIFEST |
101 | 5.00185 | 578904 | UNKNOWN | Portuguese - Brazil | UNKNOWN |
Imports
KERNEL32.dll |
MSVCR110.dll |
Exports
Title | Ordinal | Address |
|---|---|---|
A_SHAFinal | 1 | 0x00001200 |
A_SHAInit | 2 | 0x00001200 |
A_SHAUpdate | 3 | 0x00001200 |
AlpcAdjustCompletionListConcurrencyCount | 4 | 0x00001200 |
AlpcFreeCompletionListMessage | 5 | 0x00001200 |
AlpcGetCompletionListLastMessageInformation | 6 | 0x00001200 |
AlpcGetCompletionListMessageAttributes | 7 | 0x00001200 |
AlpcGetHeaderSize | 8 | 0x00001200 |
AlpcGetMessageAttribute | 9 | 0x00001200 |
AlpcGetMessageFromCompletionList | 10 | 0x00001200 |
Total processes
42
Monitored processes
4
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1248 | "C:\Windows\System32\wermgr.exe" | C:\Windows\System32\wermgr.exe | rundll32.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Problem Reporting Exit code: 0 Version: 6.1.7601.24521 (win7sp1_ldr_escrow.190909-1704) Modules
| |||||||||||||||
| 2292 | "C:\Windows\System32\rundll32.exe" | C:\Windows\System32\rundll32.exe | — | rundll32.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2792 | "C:\Windows\system32\wbem\wmic.exe" shadowcopy delete | C:\Windows\system32\wbem\wmic.exe | — | wermgr.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: WMI Commandline Utility Exit code: 2147749908 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3928 | "C:\Windows\System32\rundll32.exe" "C:\Users\admin\AppData\Local\Temp\010.dll.patched.exe", A_SHAFinal | C:\Windows\System32\rundll32.exe | — | Explorer.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
19 879
Read events
19 836
Write events
43
Delete events
0
Modification events
| (PID) Process: | (1248) wermgr.exe | Key: | HKEY_CURRENT_USER\Software\ex_data\data |
| Operation: | write | Name: | ext |
Value: 2E0069007300700077007100720062006B0062006C000000 | |||
| (PID) Process: | (1248) wermgr.exe | Key: | HKEY_CURRENT_USER\Software\keys_data\data |
| Operation: | write | Name: | public |
Value: 0602000000A40000525341310008000001000100F3D628C9F27502FAEA17CE17B0A35A5A11B979951AAB4DAFB6548C536C3A9F43508AAFD36C1E93C2026AFB131DACFC2C872DFD1635BC9B27437A1210CD97F4732BBC417311C06D9D3021170D2D6F36DA493E20DE287395B9528A1EA09522C5193BDA681C956BD1D2BADEC316B5AFE35523177C7C06490EAF6A1963D4E5342B0E1EB7C0CF5CC774262D33B1F9810341BECC6FC134B57CD129E0B74C0FD76FE30AE4889F2B8369AF7720C7C0C399E94C39503E03D374C1E74AB66DC99040A0FF33A4819F9DEEDF0C44C07D948AB9F35D1138241DBE2873ABB1315EB8AD853C642290EF6C1E28DF33DAA30C390A64883092527DD4BEA642D8AF496185321CAA01CF | |||
| (PID) Process: | (1248) wermgr.exe | Key: | HKEY_CURRENT_USER\Software\keys_data\data |
| Operation: | write | Name: | private |
Value: 94040000591EB4C83662CAA684A44A483C3A2EDC9B9F4D534AA396F9D48169F477088D8950DACE4A90FB288233DFC9799EEC5A650B8F56075E9E8EECDFED7D3F49EECAED782E17C78EFD1B675ECFDE17DFF728077D3C5B69D2251965B92CC2B7014D051F67747B38E6968765005BE356242BD1A0D10018D44047F2EC789A5C841F5F57D06F4F7D496DA15F42CC0075B7AE77F7BEB8F6D272E8F124C3FE491C9C5721F6A556445A20150CA3D4262909CAF9C56EDB8B671012E17539018400195C8D9EE72EC4E0D944307E94964502A8EFEFE56D4D77F8A77542FE4B994AF55C4B5D4D95C226869E8488666C426DA89576289B4211A03C65A0AA22F1AE1BF566FC7257128647694313287D6FCB3DD73B3ACD83D637D55DBED625C8C2CD080DBCC0AE0B3CFA4D8EB9A72057E60A24C4D6309B59D5ADB868907FF6998C5081FDA237500BB2D83AE71C4B5BD904EDAE4AF9B6172CF22A1B02ED4EF4FCEA59287EE8F99F16009E747FDD8AB23196F1CA7BE63360C905DB5FA0156713AF3CA17B818E7EDBB9C492993CEA9F8E024E26416343D1CEFA235120923E0AD3203EB15A3041CEC8604C5F942241DB0C19EB6682927BA9CDF8BAC789DDD1204985DFCB591BC000A4970188000BB3C7CBF5F2A78F3B087ACC5B7ED6EF7AA97C55174FBBA97628831E141F1CD4CF1870975891E40F066A5AC11AD120CBB427FE5950EB73E6AEBF1785DB522F7D3D58E57536039D55519FE3099F65B03E49EEEFA8A247ADCF456EEF02965FC8B74A405B1DCAF28B0BAA4DC1E7C443DFBF8F4551807AAA00C24684514010C43BB35E450D944A871AD8BD891E121B409485B672A9F9F1F32230F6E682A1B0F423B64B45747BE8C26B621B34F9F63DCB8456B0BB05F435A8F8729A9100C97008EDD661E4BB3D63AABF8AC88602054EE19B151470DD37A4EAA8940AC14E5CD5A8A9A206B5F8CA700336599902D1F14A136AE06F2AEC85317FCBB1F1EA03ECE1E5BF622B2436CE8AFC65AC3D3EAA5BB0899CD476BD7B3D4565F456B7412160C943EACB2BCAA7FB6907F69AB4C070E2B63DF04752AA79D0CB4920019E9C9F56802F522757268D498F81ED8247AE77312662ED80731E22E744B84732F2BAD7045F1AF1BC5DCF98A72F9995904833D74CA3DA132FAC27CCF14E1F03E28E1998F06AC911D07A76266F82AB162E05BD2050E13FAD92503E24F3B6B2C14A76E7217AB903EB8716E017F44F0573E6A1D93A994076F6FE6490A72396F98043833C713B17B95F48E259364D315C5BDD26F5A849F98875BC903434501FDD29574B86D360B3914BE5121F662EFAFEC067349D821FB7C61B41B8937546B0C13A29E2E7BAEA4668ADD628AE3F75AFAF0F42AB912614B06CA4BC972114E8E866FA2D0888F7CBDC6F96AD399E8474F88A06B5E591FA9B6177A1CEE069F75F88240F275C8B3610BF4EE7B2EE586772971463B54A525DFD32461C8D29BC7C0BAB15AB78A78F932593E61FE9A8FEA64864D0DAF0DE7B556B829C4B98BE8145CD4F357E13610AB3F7A8AA7F390719ACD8B6166E9655017EE41335306C312506AF1C043067ED7DA2C0385C86E90C24EA025A75987883592716CB0862E46AE3CFFD7D278B8D68E6C69153C66D84EF2456CF4AFDB28A62A42AE8CEEF7B92BB82AF6A2DAE3A16E791604EBD66A9D1E9AF9992CF292959EC69EDD1423FC865178D6A1DA2B9C155C86F8EAEFFFB2597F90206DA49D016F528B7CF5A897DB425A88490E86FFE840EDD5CA59102A36F96C7BBC5113FAA2A517FD935A2D2569C54923C2CEF77B06EE3910305EC8A90715C8F829A2F34DC9E43C11EDFA6BD57AC5F7F6046B3CB73900F039966FB7562E1DDCBADC2CD5F1EC1887F815182A26F097FBDD59B9B8714B1EB74F3856977AEB6A3A9E607E0157169AC9F50741501BA0D3095FED83999B4537F58FBB0DED504DB240B01705BE073CA54A7706C13DFF6455620D029A069D429C0F20DC74B2738A4B73D148A259615CD206F63F23AB8DC69EDD9F29FE632B9C1F138029F192154104835B0E64EB23A9F6DADDFED2D0D59E021DC7D930EACB76608BDE7069CF70B0AF1220909A3CFD38345596945F798FD5FACC17A4DC4277118B136B16BB2205C592300C228AD66D90C69B774F449FBC6C74411D86FD9C326FFF42CBC36C7AB5FF90C576F4042B1EB1128B9232EE56C81F089A74E578E8513BBD2477347FC1C980D0B6A93E214D04C93AB3B3C2BA6A3A9B4B45ECAA7992277196E5EA43ECF1C0370E10F89DFBB6D7332FEEBEB72601F0F2E2901D90BE012899EBC3E9B030CED67152680F56E24AA44532264887B53561BE9ADBE17196E7B1033385FD9038B2FAB76247134E074807A4FE77FB861FA0E8EBD9859A538 | |||
| (PID) Process: | (1248) wermgr.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (1248) wermgr.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (1248) wermgr.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (1248) wermgr.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (1248) wermgr.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (1248) wermgr.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (1248) wermgr.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
Executable files
0
Suspicious files
705
Text files
241
Unknown types
13
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2292 | rundll32.exe | C:\Users\admin\AppData\Local\Temp\Liebert.bmp | — | |
MD5:— | SHA256:— | |||
| 1248 | wermgr.exe | C:\Users\admin\AppData\ISPWQRBKBL-DECRYPT.txt | text | |
MD5:— | SHA256:— | |||
| 1248 | wermgr.exe | C:\Users\admin\ISPWQRBKBL-DECRYPT.txt | text | |
MD5:— | SHA256:— | |||
| 1248 | wermgr.exe | C:\MSOCache\ISPWQRBKBL-DECRYPT.txt | text | |
MD5:— | SHA256:— | |||
| 1248 | wermgr.exe | C:\Users\admin\AppData\Roaming\Adobe\ISPWQRBKBL-DECRYPT.txt | text | |
MD5:— | SHA256:— | |||
| 1248 | wermgr.exe | C:\Users\admin\AppData\Roaming\Adobe\Acrobat\DC\JSCache\GlobData.ispwqrbkbl | binary | |
MD5:— | SHA256:— | |||
| 1248 | wermgr.exe | C:\Users\admin\.oracle_jre_usage\90737d32e3abaa4.timestamp.ispwqrbkbl | binary | |
MD5:— | SHA256:— | |||
| 1248 | wermgr.exe | C:\Users\admin\AppData\Roaming\Adobe\Acrobat\ISPWQRBKBL-DECRYPT.txt | text | |
MD5:— | SHA256:— | |||
| 1248 | wermgr.exe | C:\Users\admin\AppData\Roaming\Adobe\Acrobat\DC\ISPWQRBKBL-DECRYPT.txt | text | |
MD5:— | SHA256:— | |||
| 1248 | wermgr.exe | C:\Users\admin\AppData\Roaming\Adobe\Acrobat\DC\JSCache\ISPWQRBKBL-DECRYPT.txt | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
7
DNS requests
6
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1248 | wermgr.exe | GET | 200 | 95.101.89.66:80 | http://crl.identrust.com/DSTROOTCAX3CRL.crl | unknown | der | 1.16 Kb | whitelisted |
1248 | wermgr.exe | GET | 200 | 104.90.178.254:80 | http://x1.c.lencr.org/ | NL | der | 717 b | whitelisted |
1248 | wermgr.exe | GET | 200 | 95.101.89.24:80 | http://r3.o.lencr.org/MFMwUTBPME0wSzAJBgUrDgMCGgUABBRI2smg%2ByvTLU%2Fw3mjS9We3NfmzxAQUFC6zF7dYVsuuUAlA5h%2BvnYsUwsYCEgOnfMZUsgKL%2BI5SAfRsy2dNqg%3D%3D | unknown | der | 503 b | shared |
1248 | wermgr.exe | GET | 200 | 95.101.89.105:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?f91bb3fb3cb5b1e5 | unknown | compressed | 4.70 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1248 | wermgr.exe | 77.75.249.22:443 | www.2mmotorsport.biz | Profihost AG | DE | malicious |
1248 | wermgr.exe | 95.101.89.105:80 | ctldl.windowsupdate.com | Akamai International B.V. | — | unknown |
1248 | wermgr.exe | 95.101.89.24:80 | r3.o.lencr.org | Akamai International B.V. | — | unknown |
— | — | 217.26.63.20:443 | www.haargenau.biz | Hostpoint AG | CH | malicious |
1248 | wermgr.exe | 217.26.63.20:443 | www.haargenau.biz | Hostpoint AG | CH | malicious |
1248 | wermgr.exe | 104.90.178.254:80 | x1.c.lencr.org | Akamai Technologies, Inc. | NL | unknown |
1248 | wermgr.exe | 95.101.89.66:80 | crl.identrust.com | Akamai International B.V. | — | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.2mmotorsport.biz |
| unknown |
ctldl.windowsupdate.com |
| whitelisted |
crl.identrust.com |
| whitelisted |
x1.c.lencr.org |
| whitelisted |
r3.o.lencr.org |
| shared |
www.haargenau.biz |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Potentially Bad Traffic | ET INFO Observed DNS Query to .biz TLD |
— | — | Potentially Bad Traffic | ET INFO Observed DNS Query to .biz TLD |