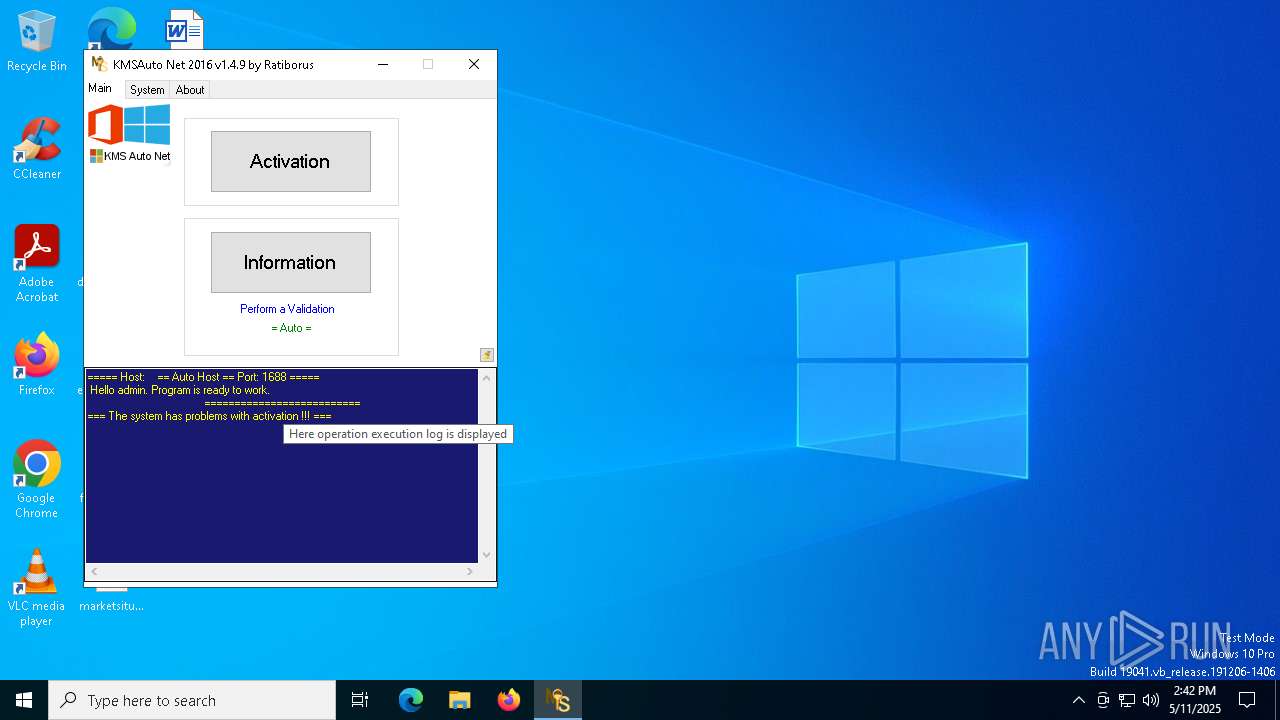
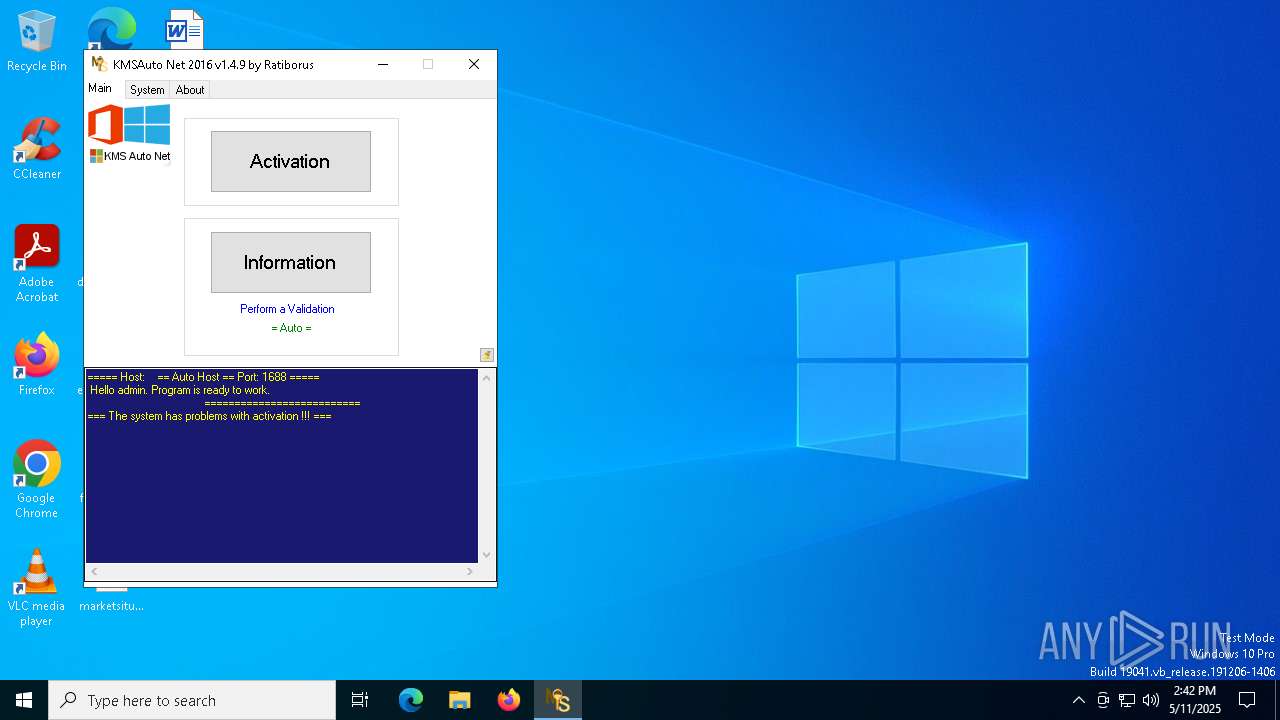
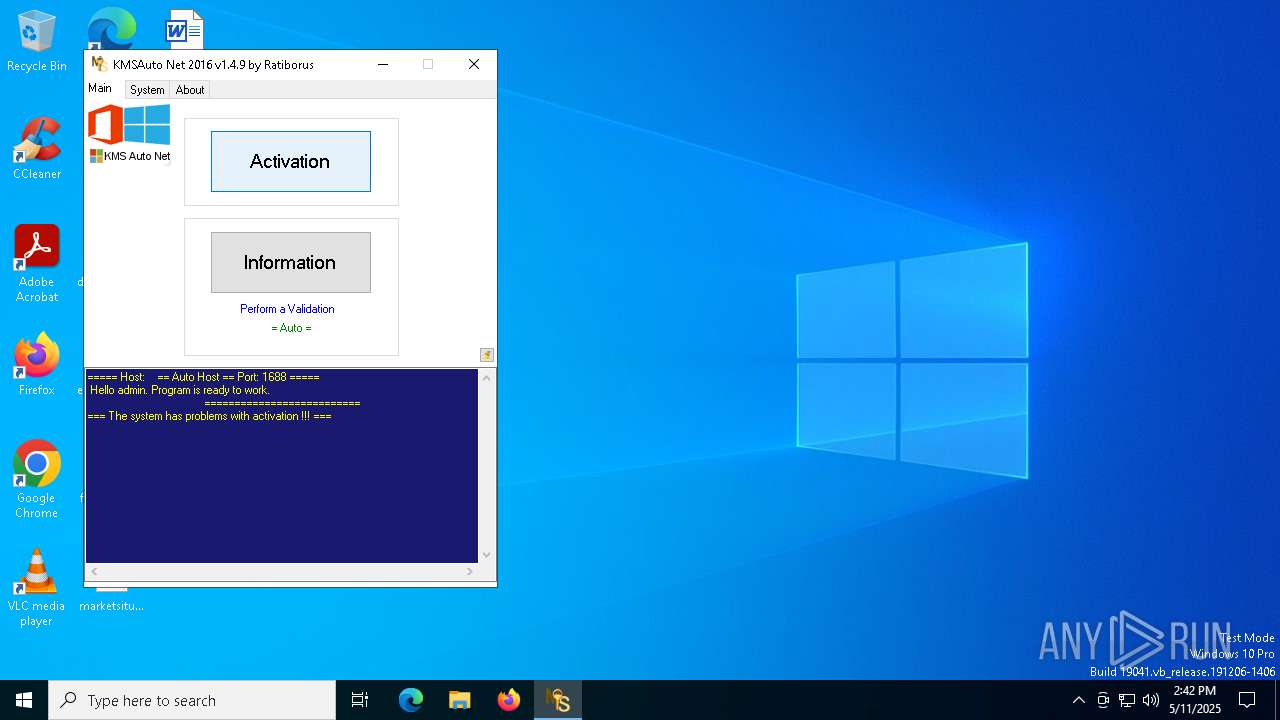
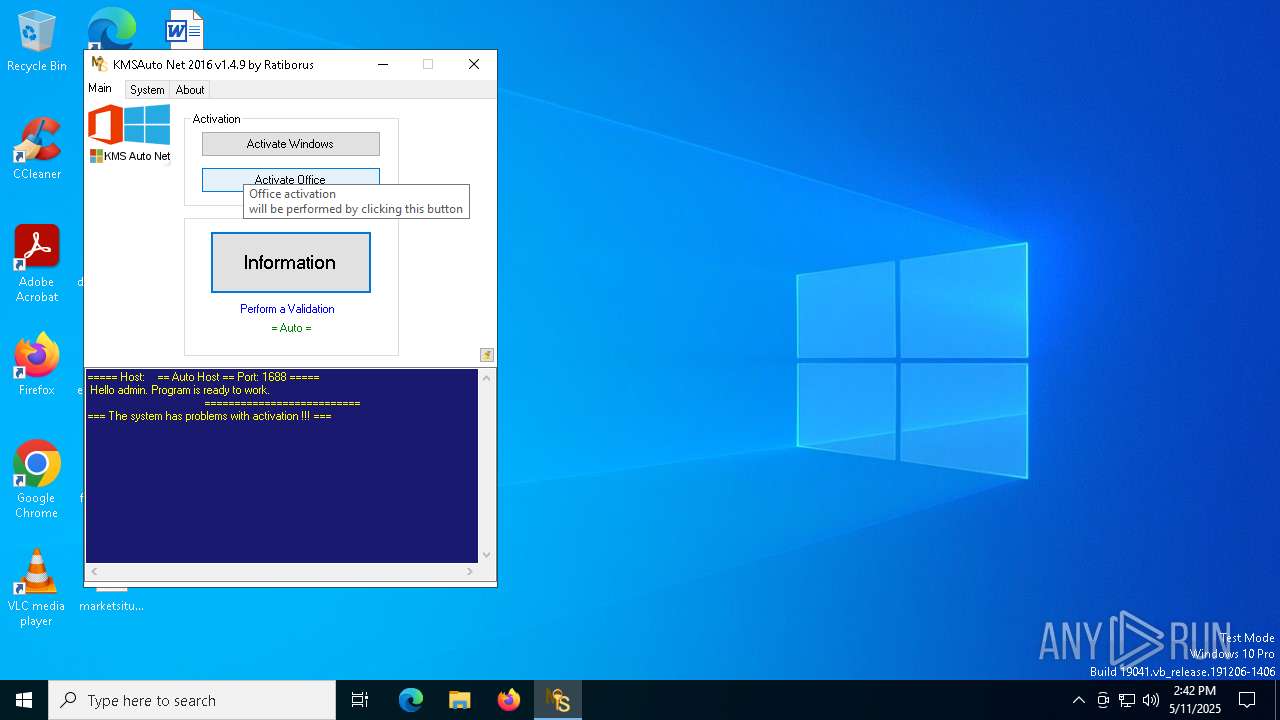
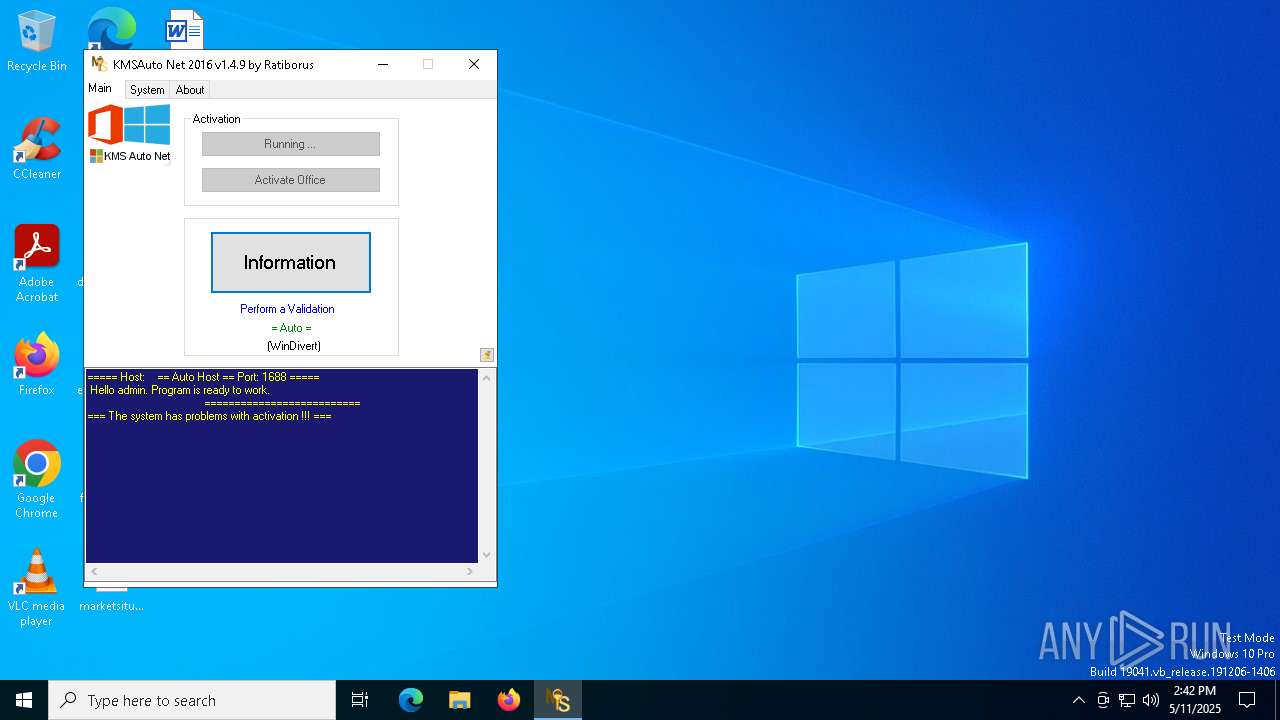
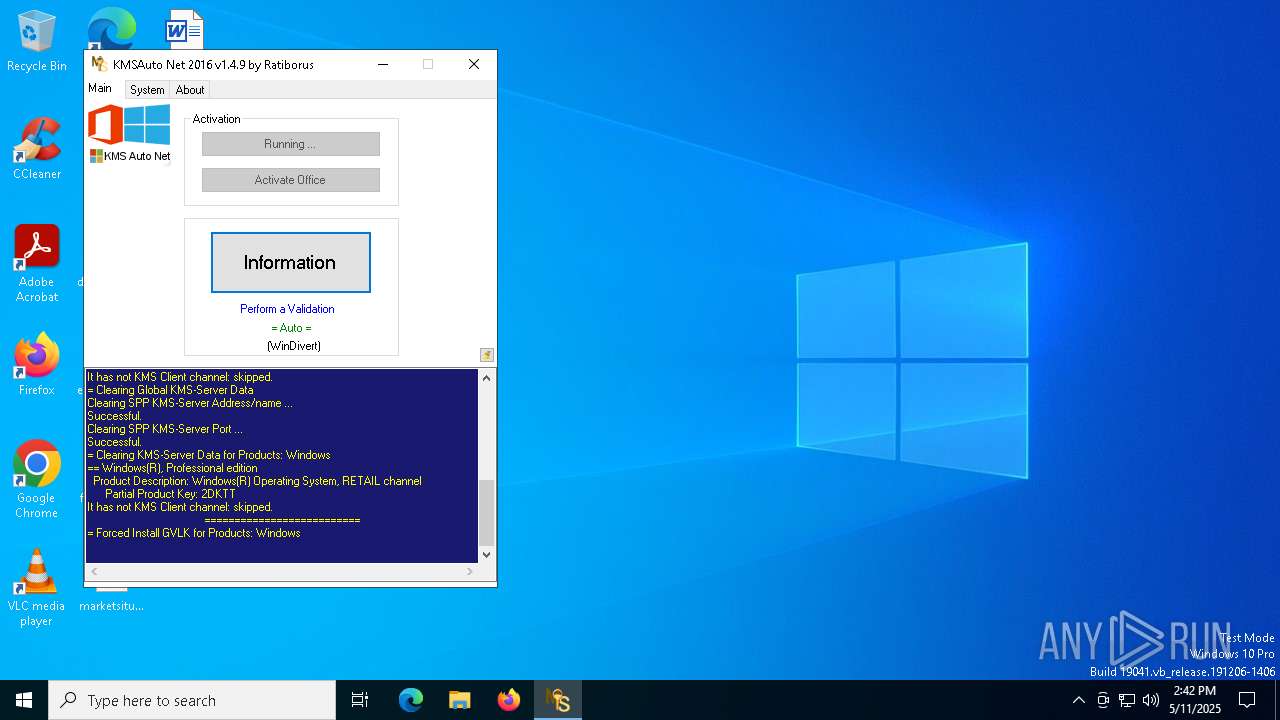
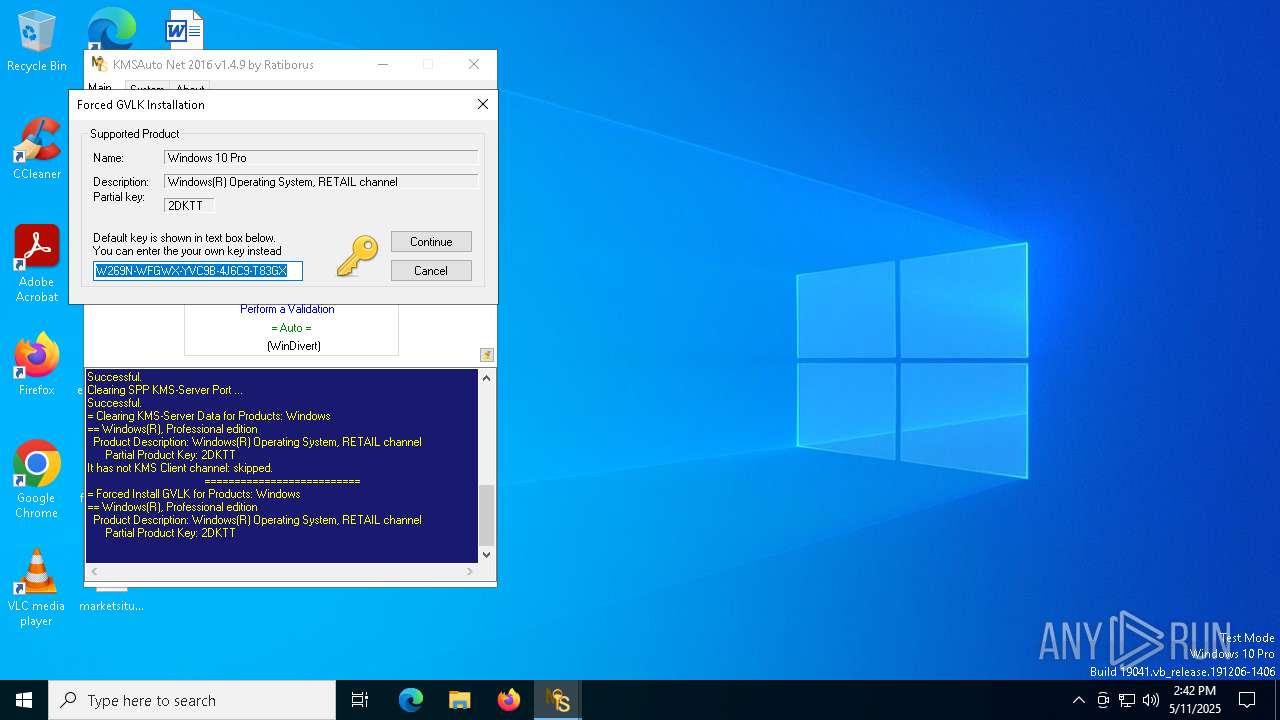
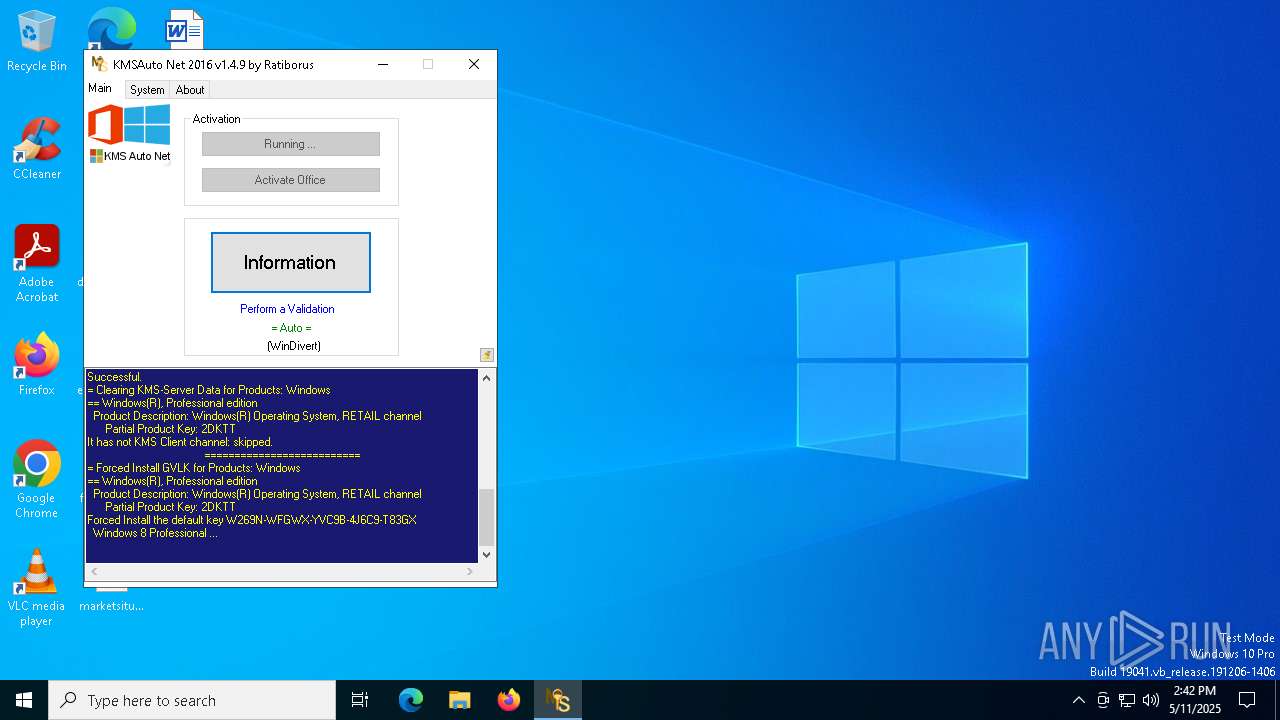
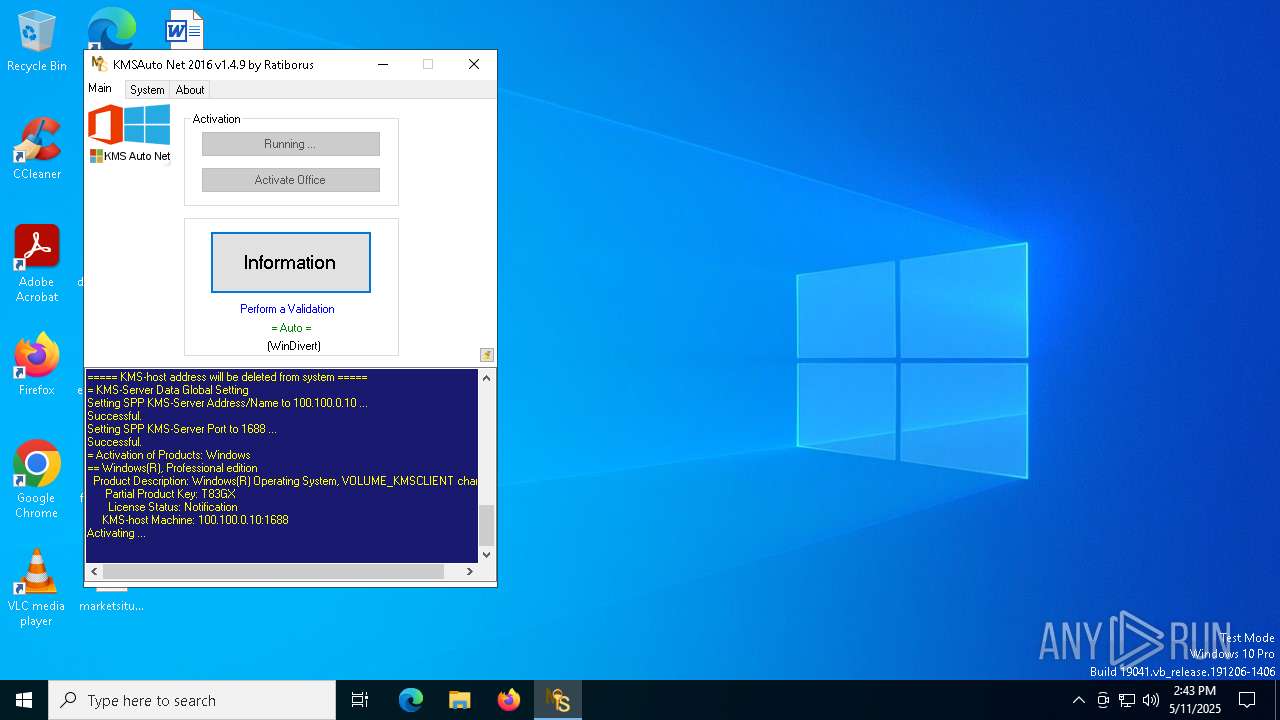
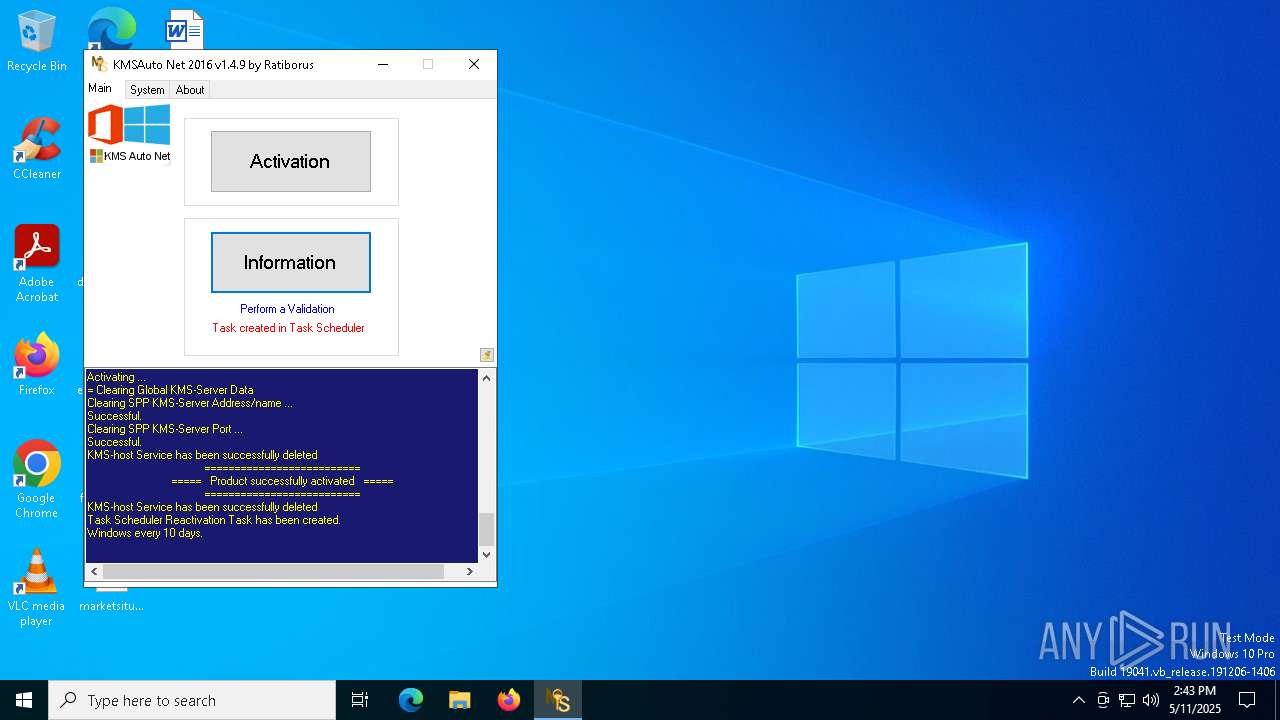
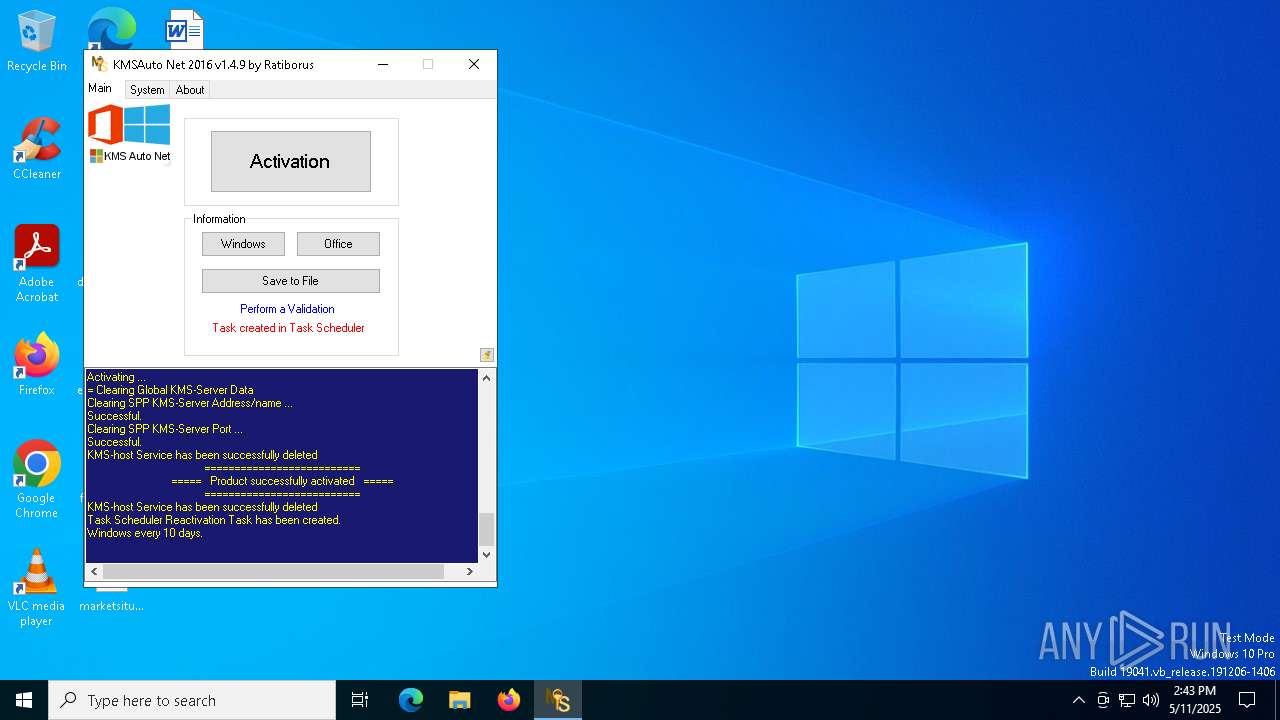
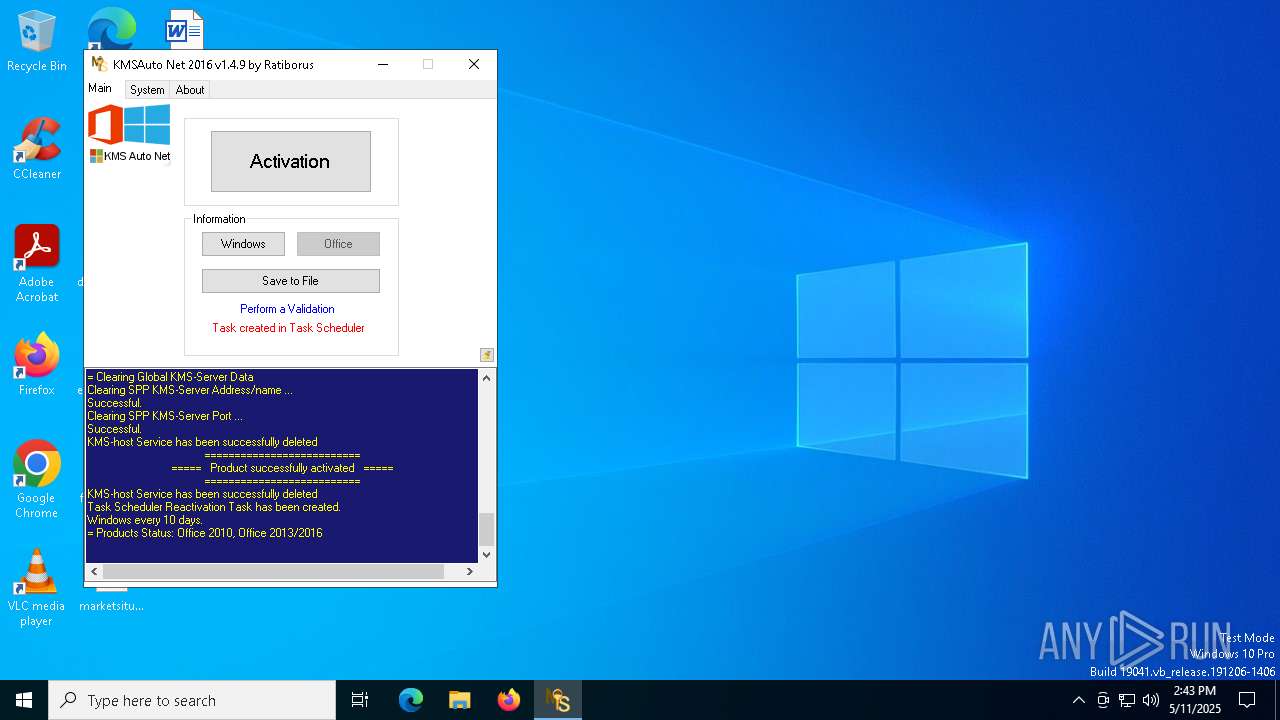
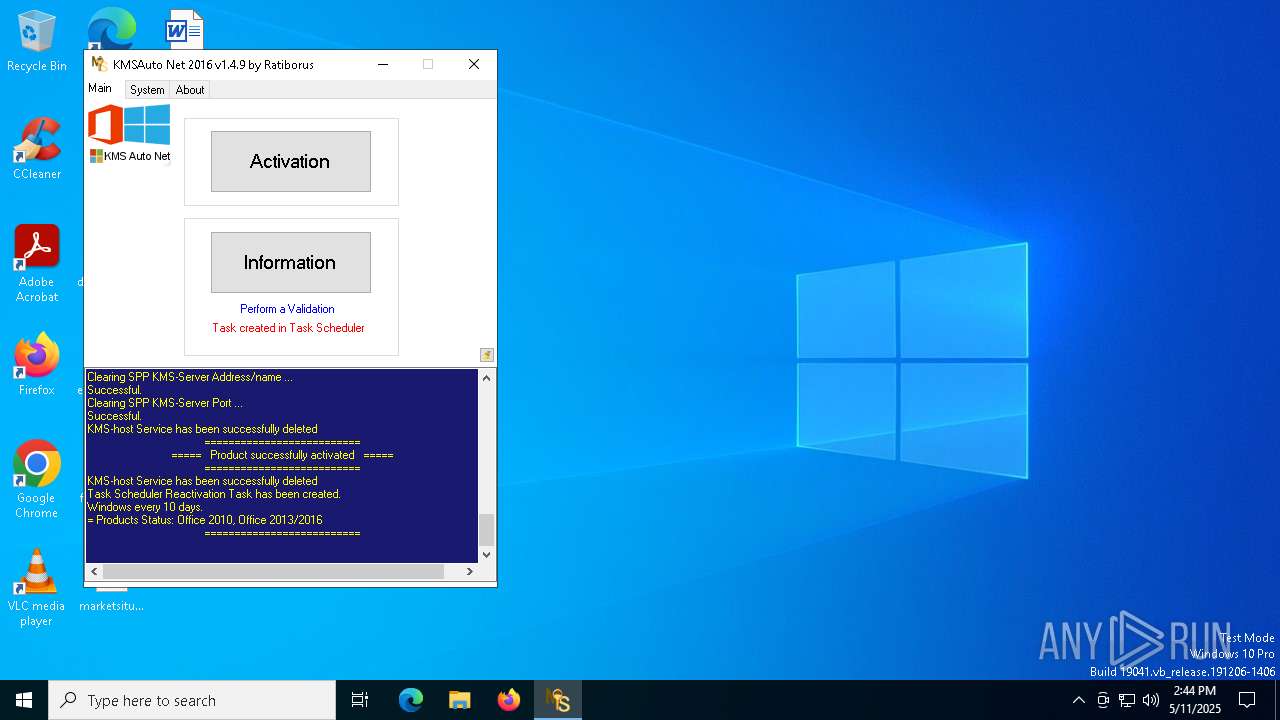
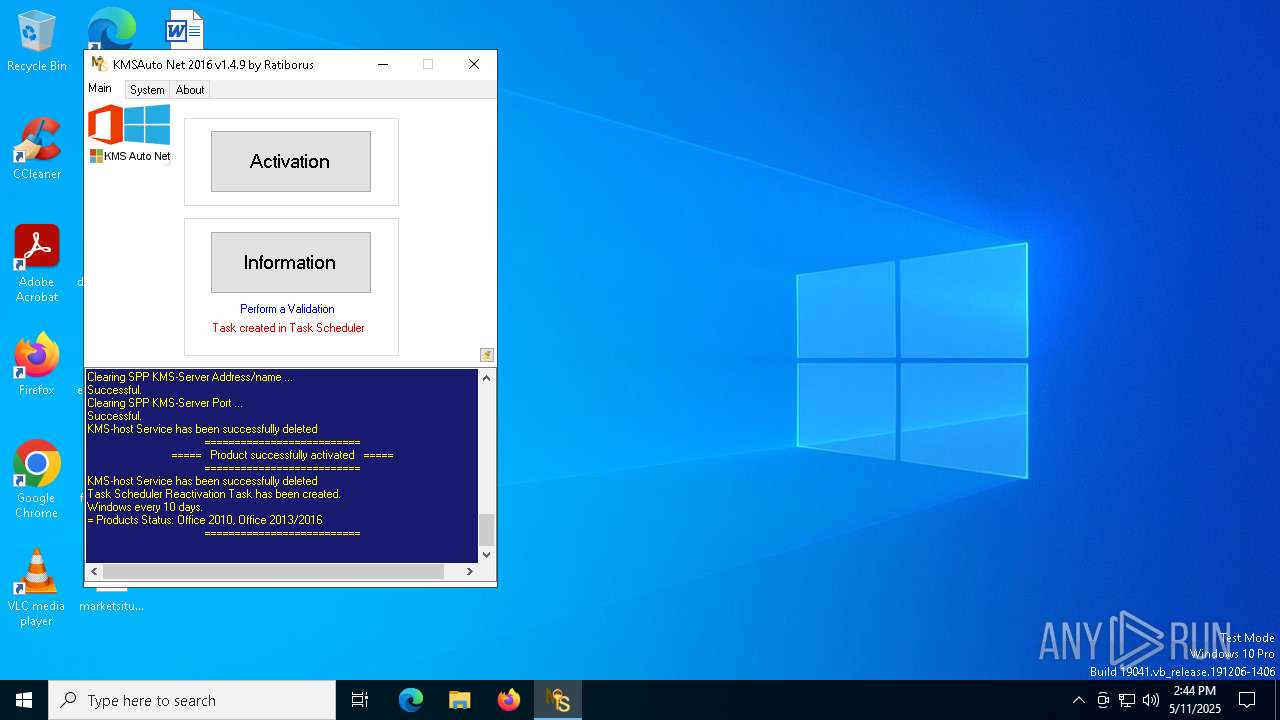
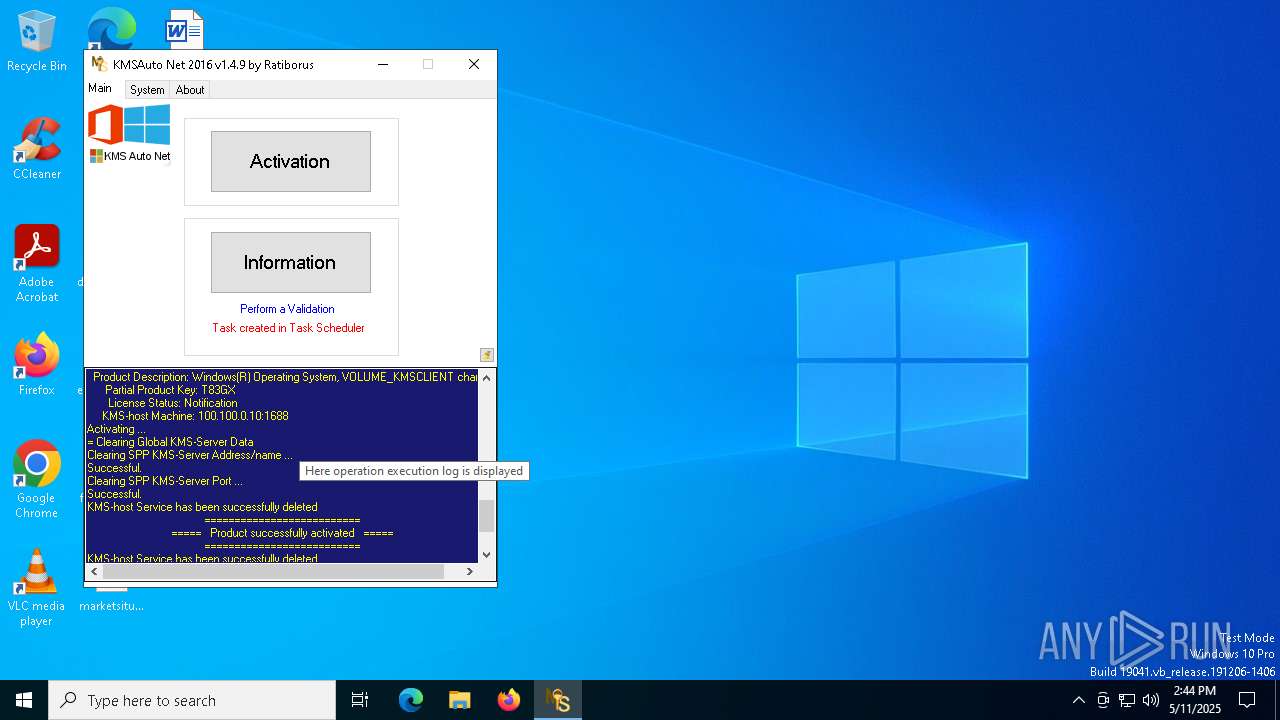
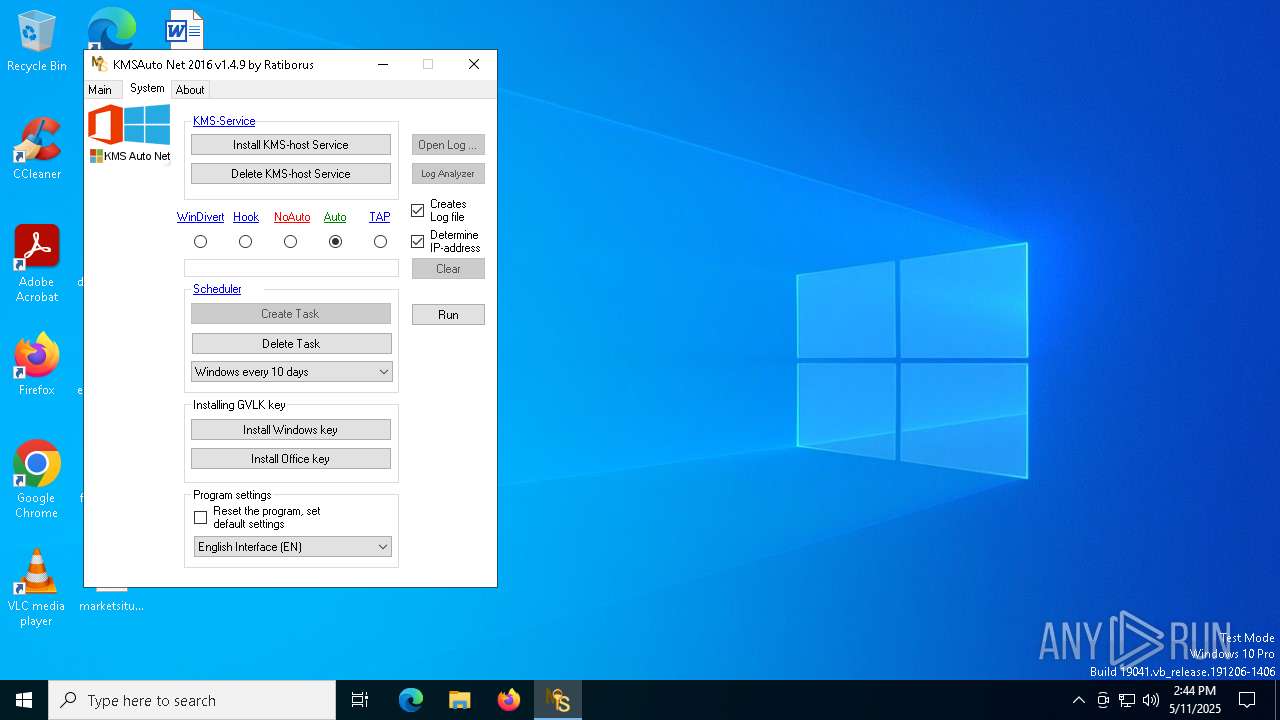
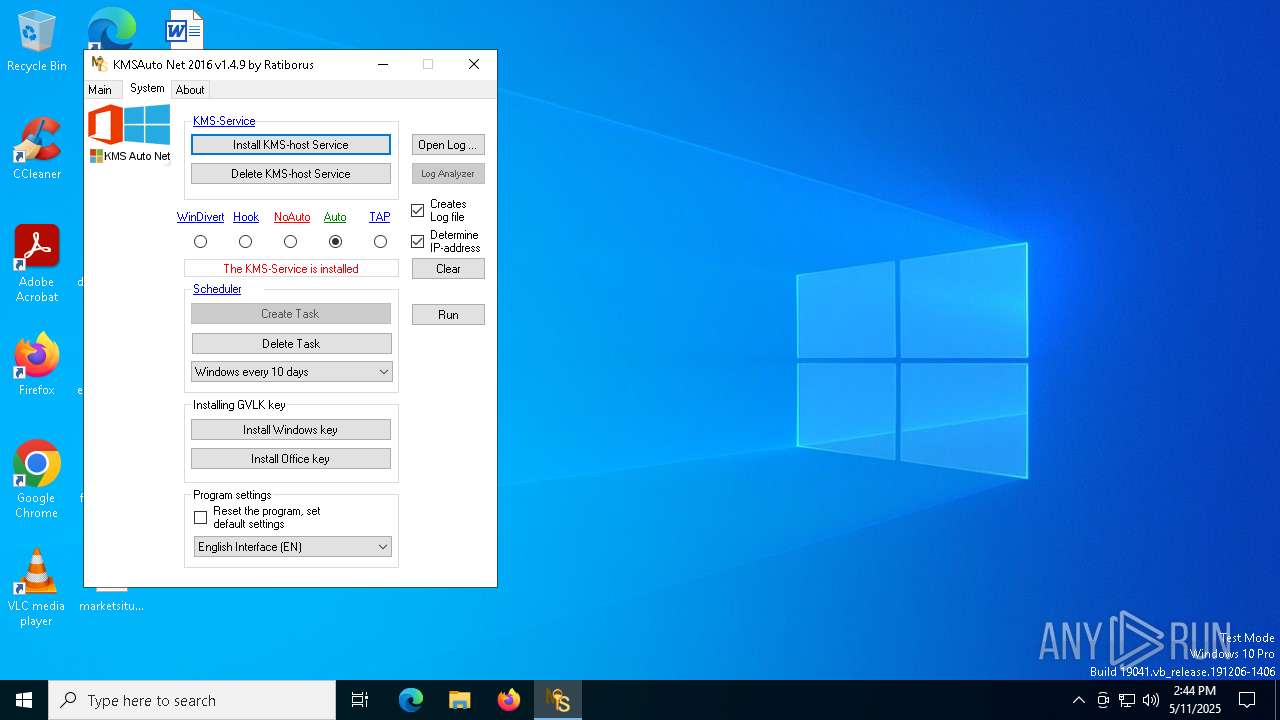
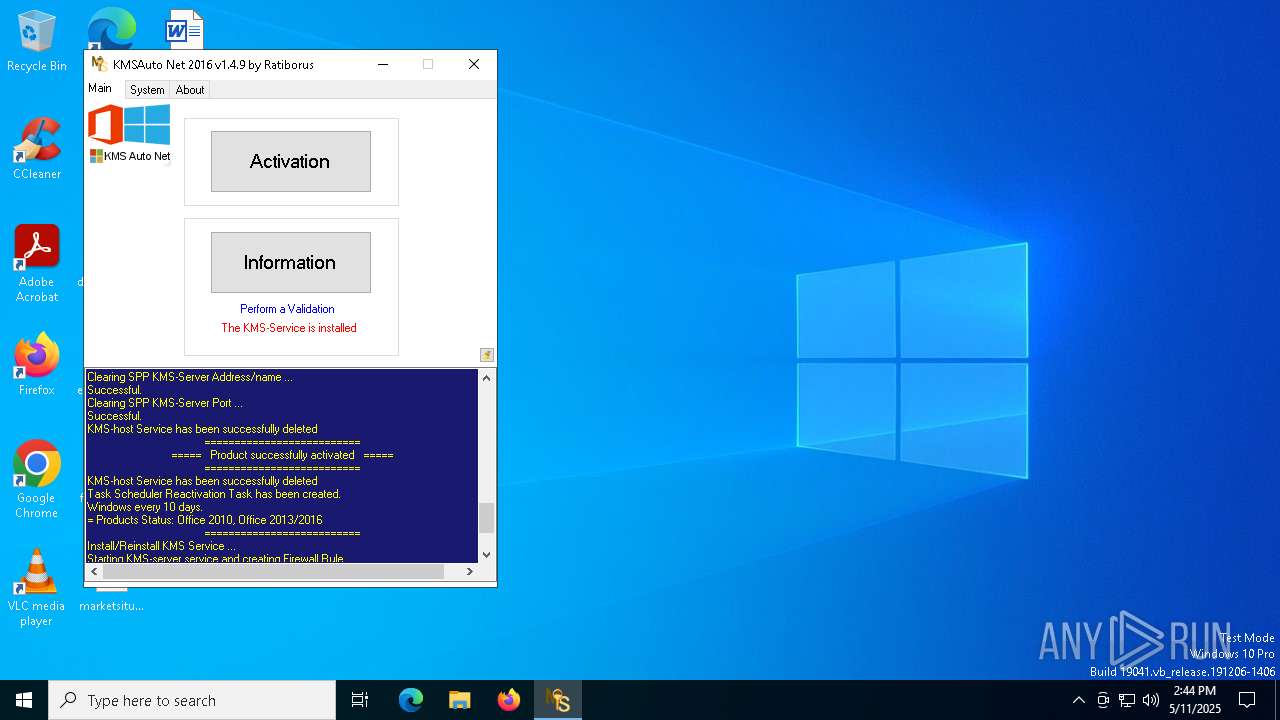
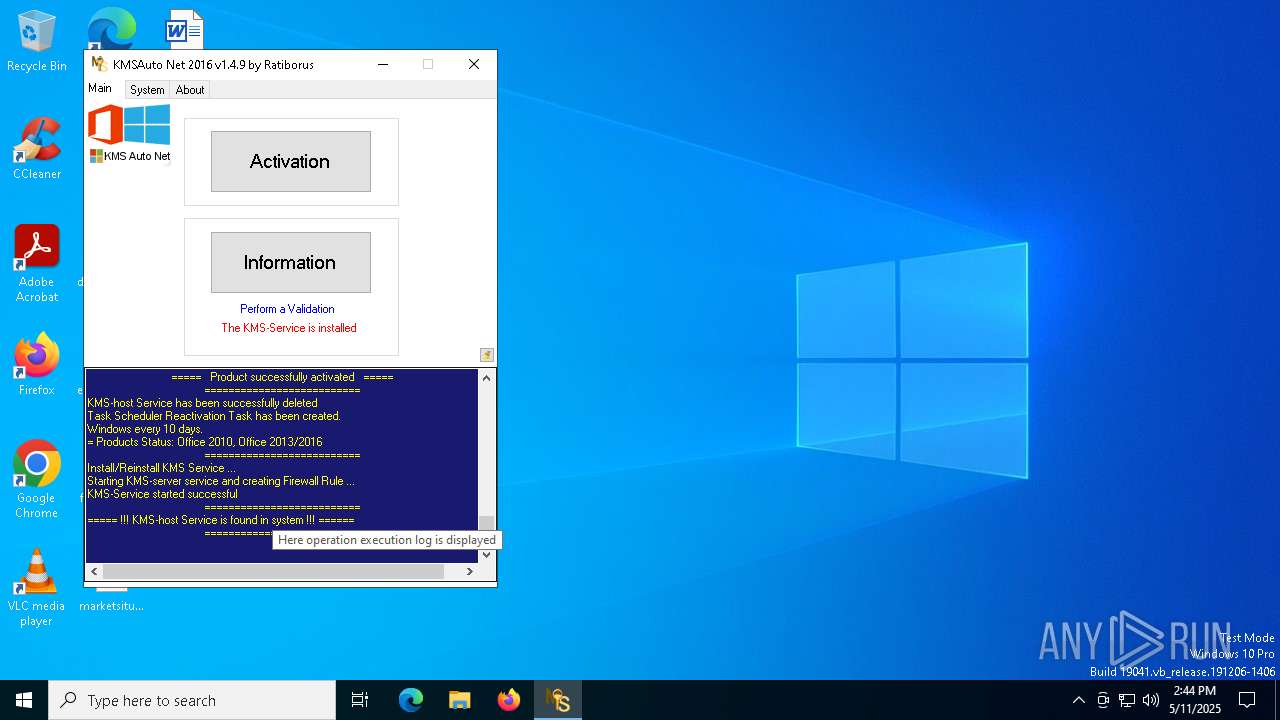
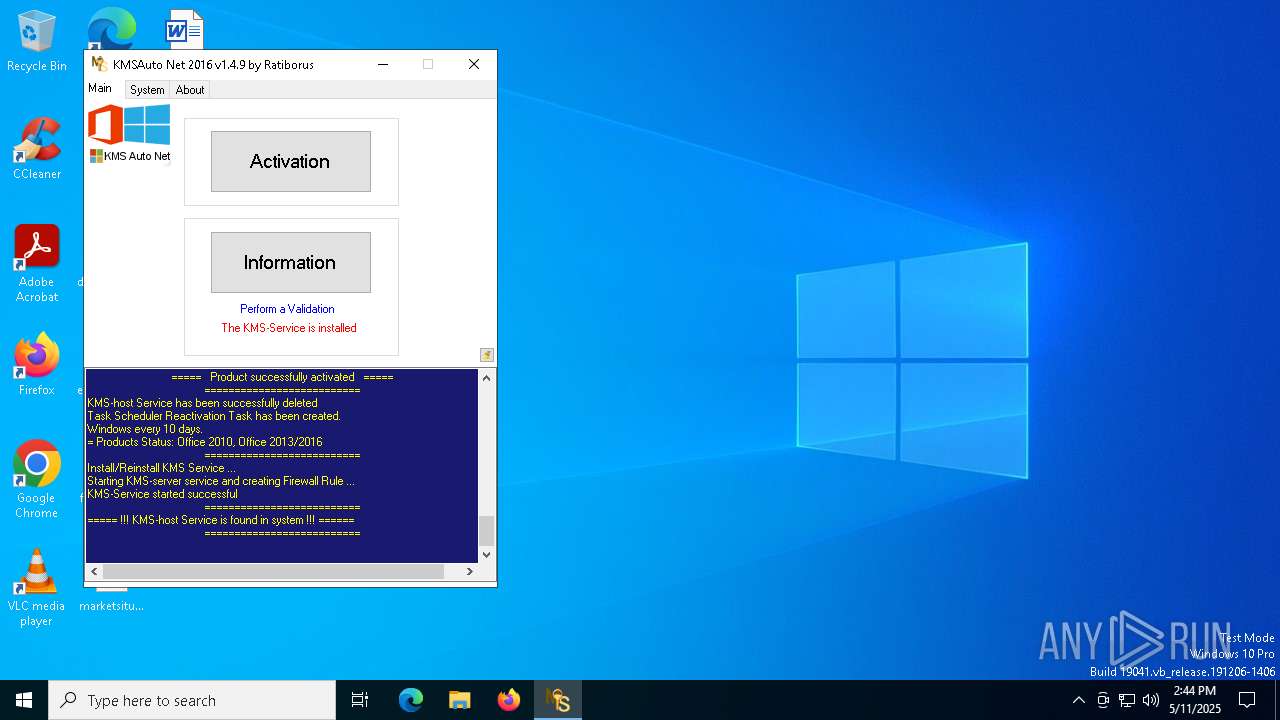
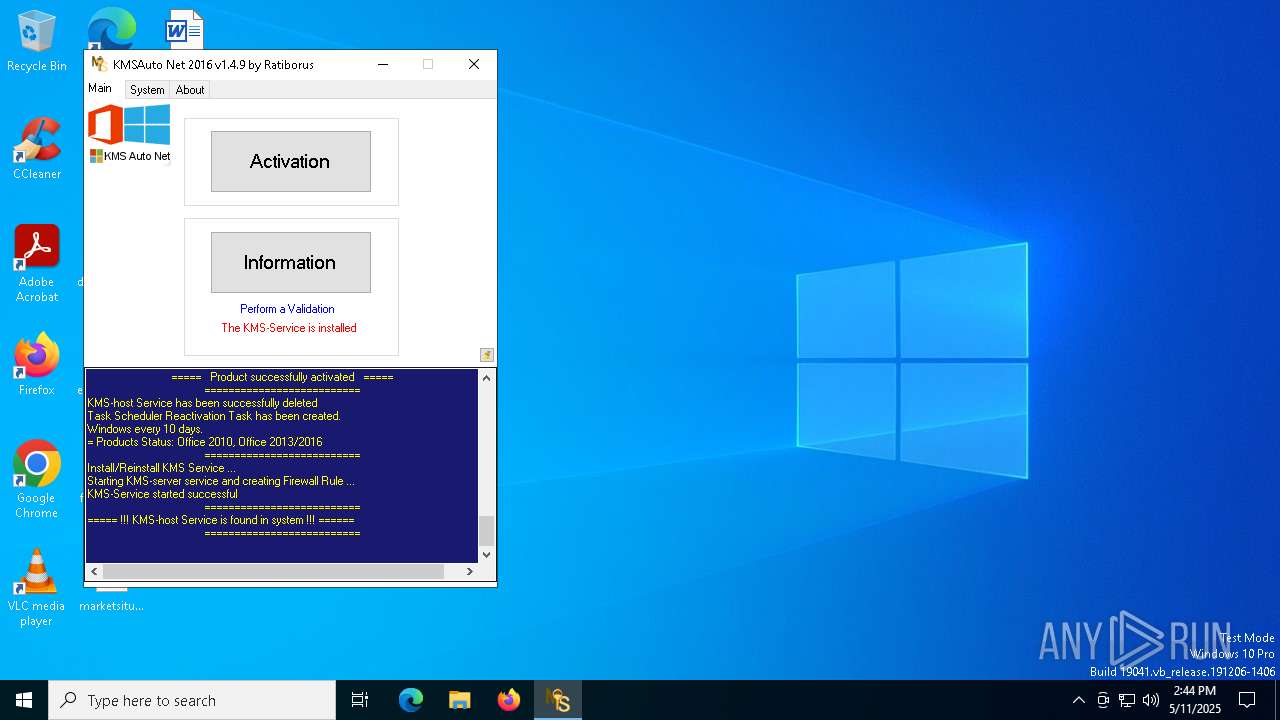
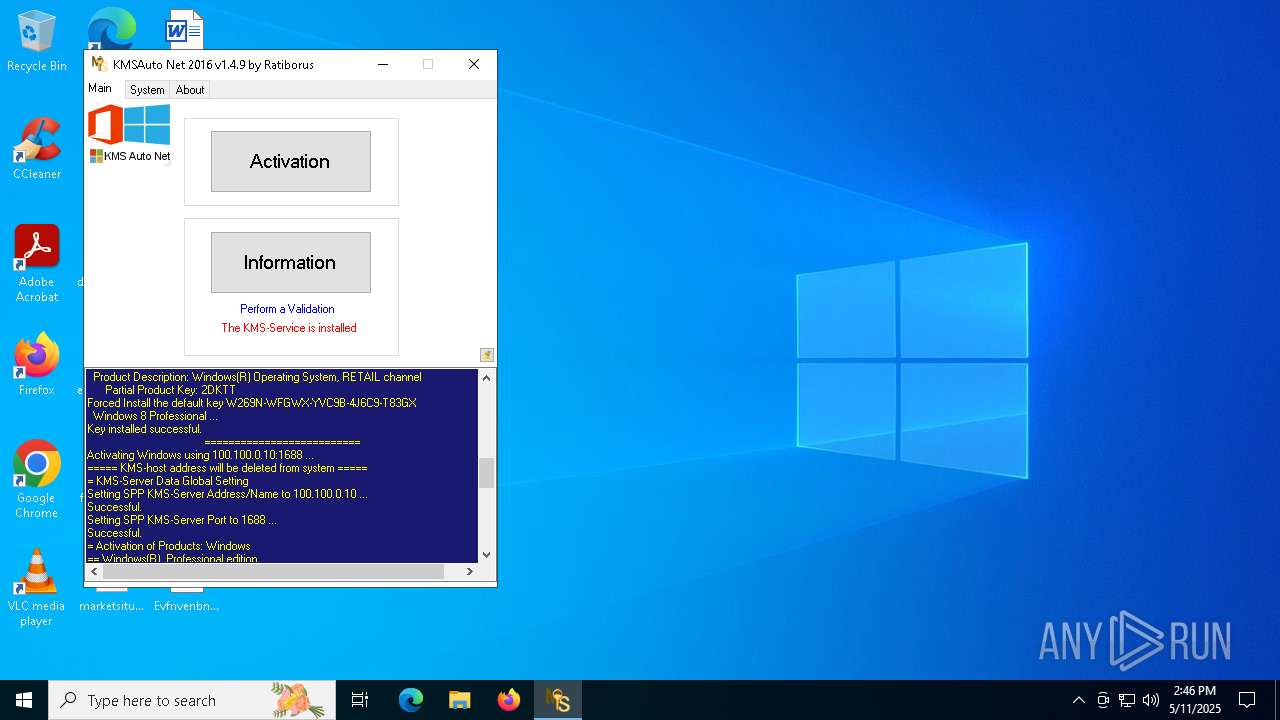
| File name: | KMSAuto Net.exe |
| Full analysis: | https://app.any.run/tasks/3e21b647-8fef-4221-b7d4-1d33612a292b |
| Verdict: | Malicious activity |
| Analysis date: | May 11, 2025, 14:42:04 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386 Mono/.Net assembly, for MS Windows, 3 sections |
| MD5: | 2FB86BE791B4BB4389E55DF0FEC04EB7 |
| SHA1: | 375DC8189059602F9EB571B473D723FAD3AD3D8C |
| SHA256: | B8AEC57F7E9C193FCD9796CF22997605624B8B5F9BF5F0C6190E1090D426EE31 |
| SSDEEP: | 196608:wokKDywCAfywOweBzcyw3ywsywDywPbywgsywZywRywxywBywEyw4ywwywmIBywI:FywCAqwUBzBwiwxwGwPewgxwUwswMw84 |
MALICIOUS
Executing a file with an untrusted certificate
- KMSAuto Net.exe (PID: 1672)
- KMSSS.exe (PID: 5308)
- FakeClient.exe (PID: 2616)
- KMSSS.exe (PID: 6480)
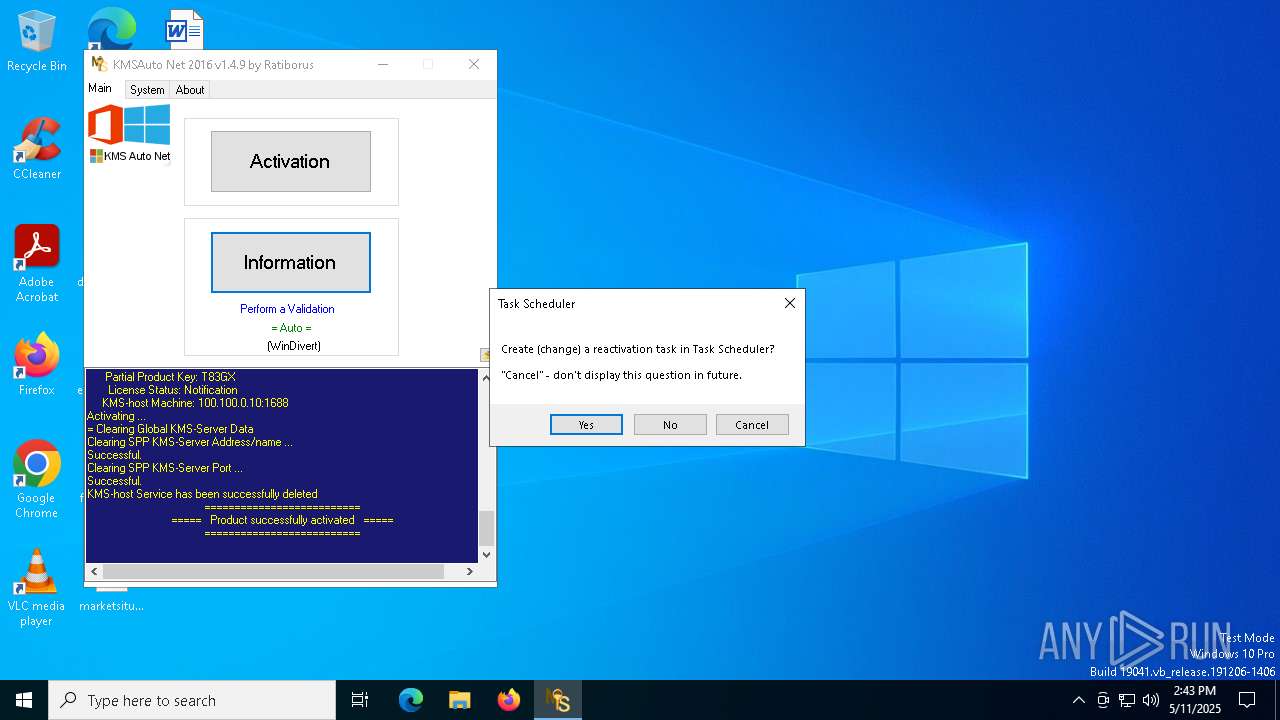
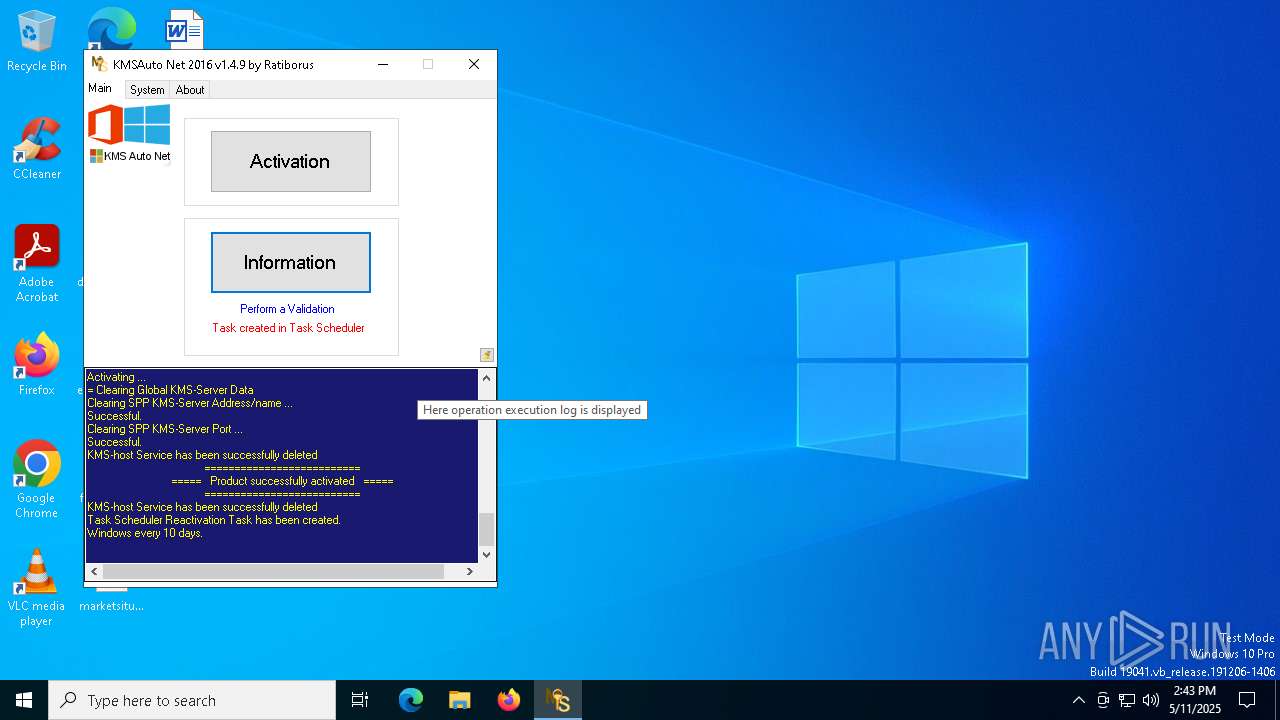
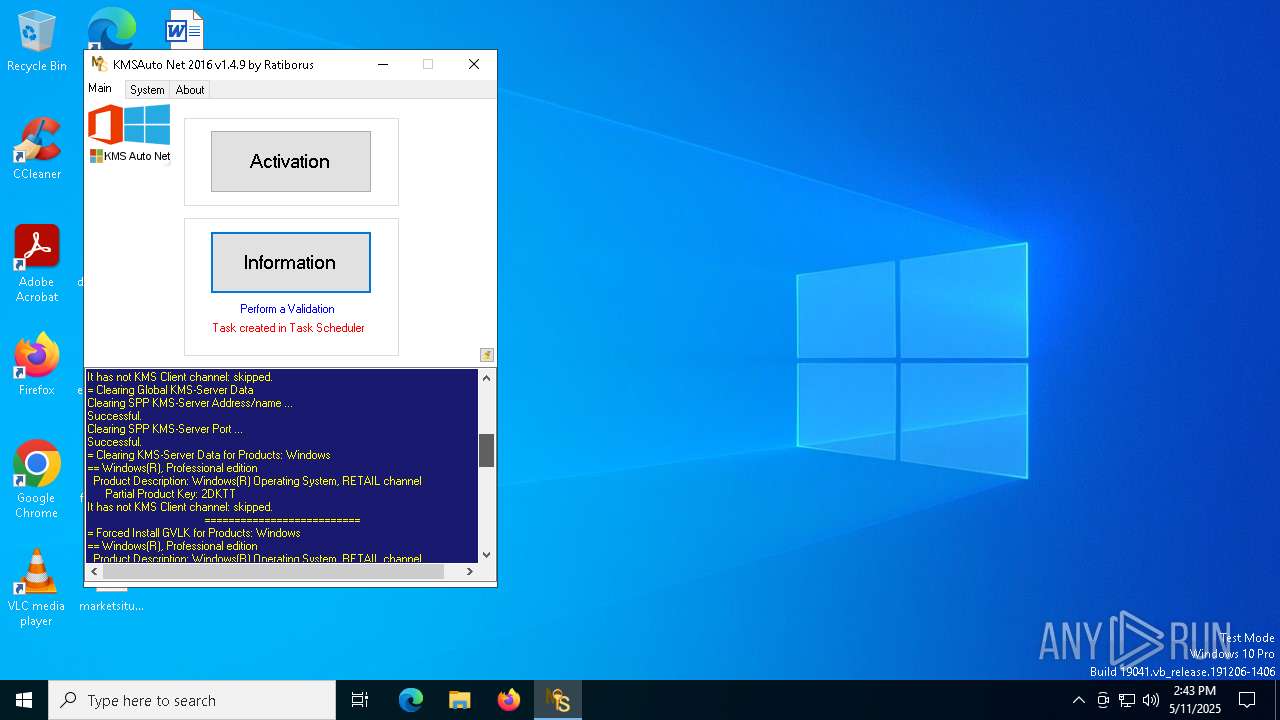
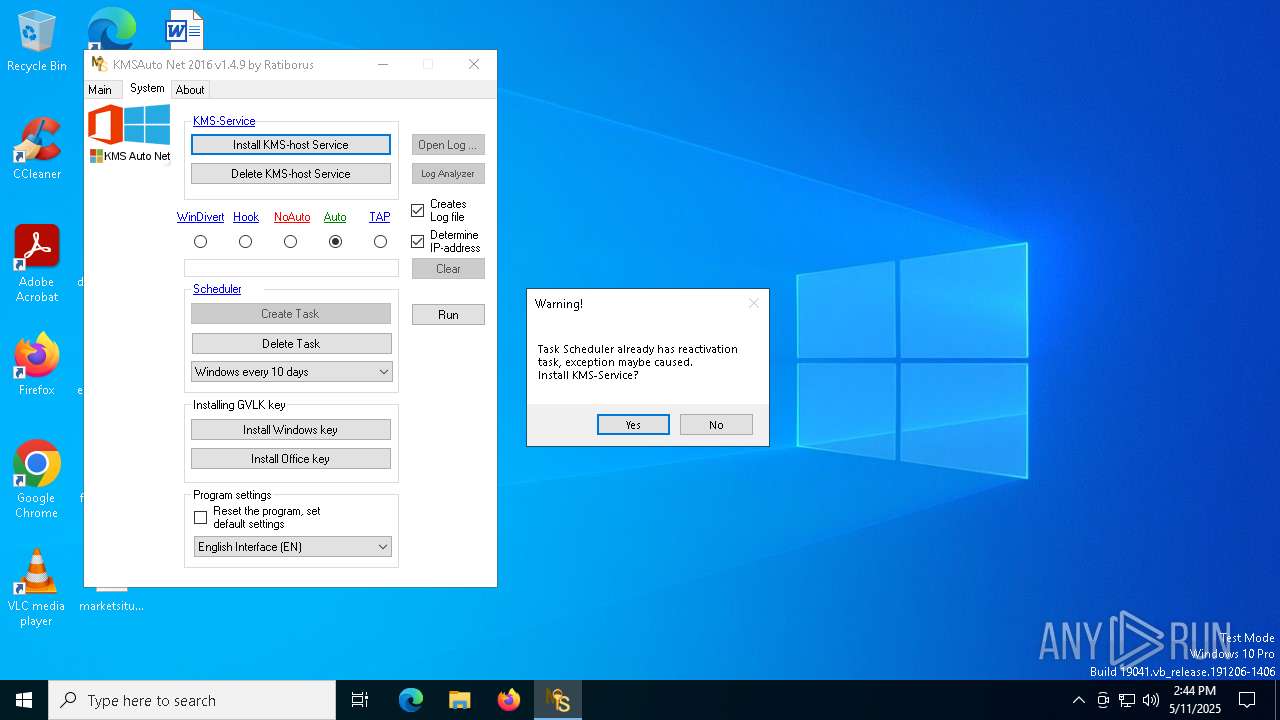
Uses Task Scheduler to run other applications
- cmd.exe (PID: 1748)
SUSPICIOUS
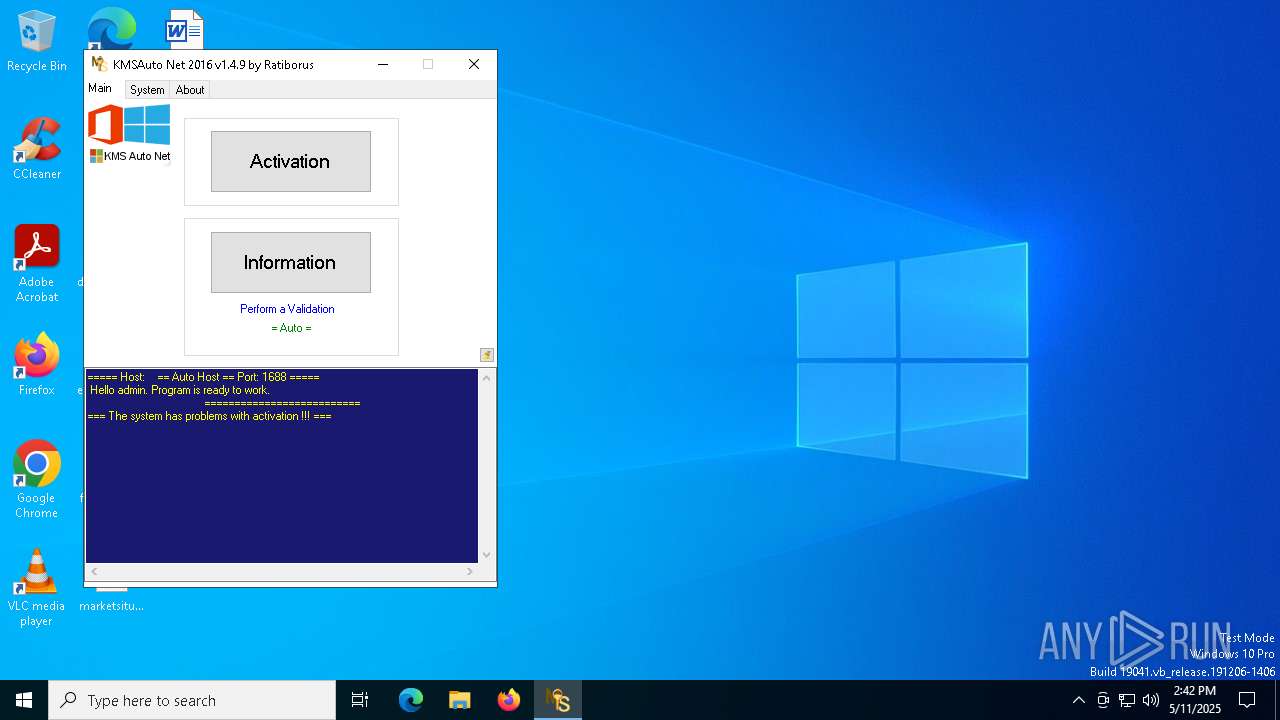
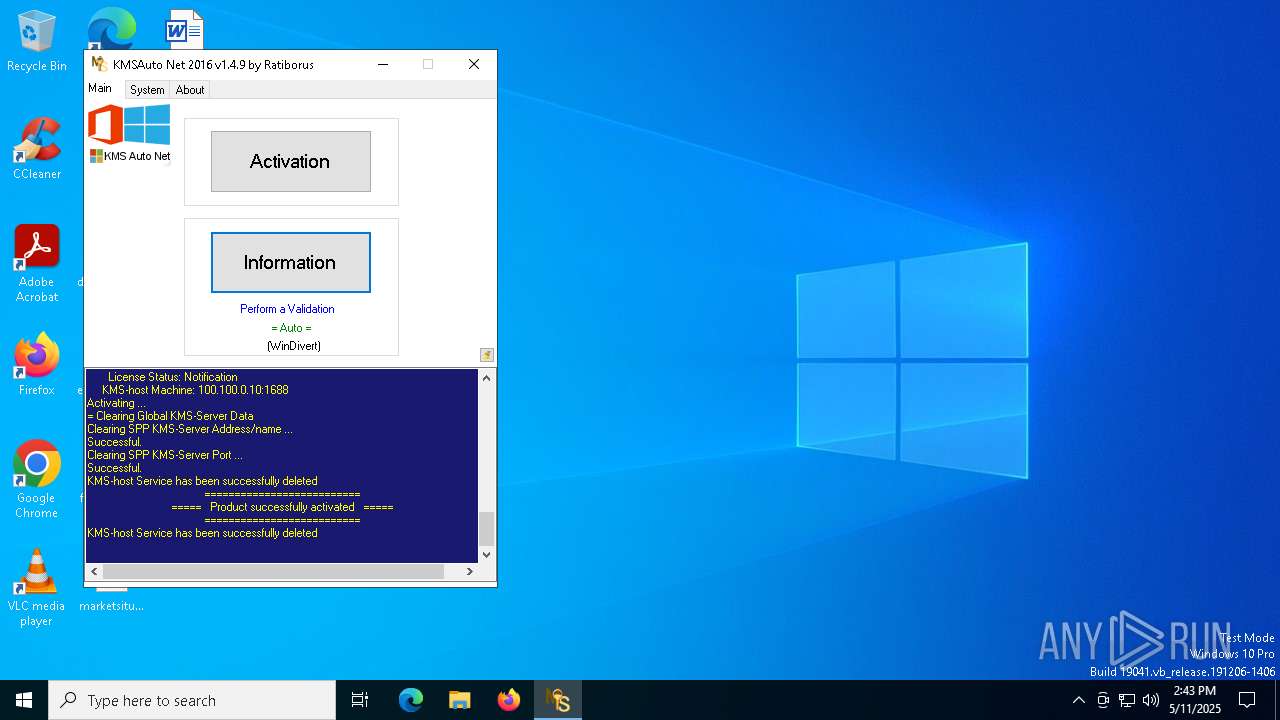
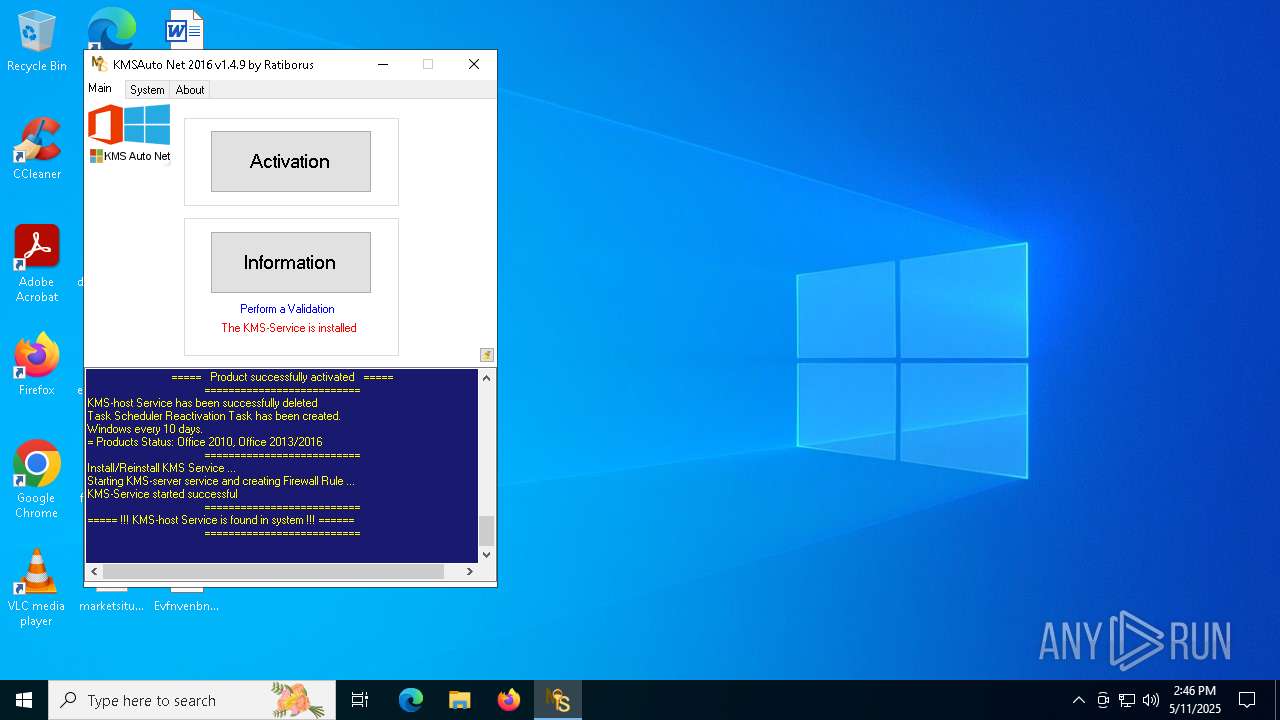
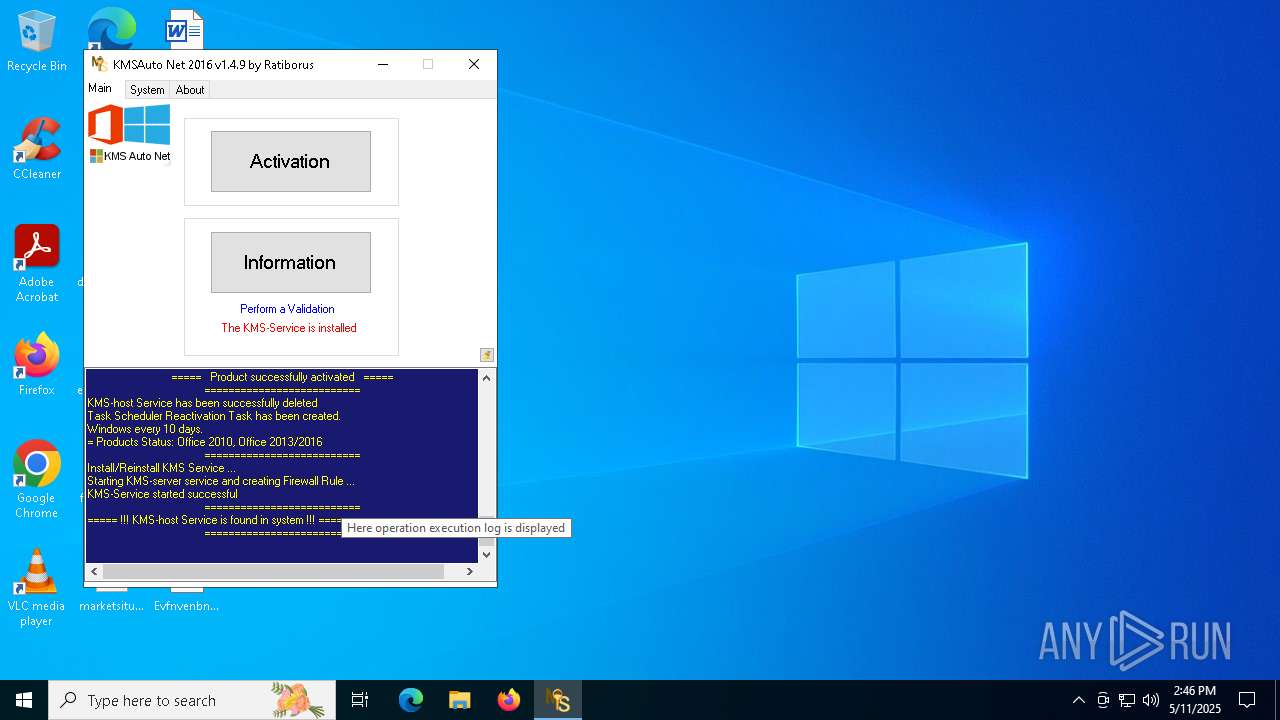
KMS tool has been detected
- KMSAuto Net.exe (PID: 1672)
- KMSAuto Net.exe (PID: 5072)
- KMSAuto Net.exe (PID: 5072)
There is functionality for taking screenshot (YARA)
- KMSAuto Net.exe (PID: 5072)
Drops 7-zip archiver for unpacking
- KMSAuto Net.exe (PID: 5072)
Starts CMD.EXE for commands execution
- KMSAuto Net.exe (PID: 5072)
- cmd.exe (PID: 1388)
- cmd.exe (PID: 5244)
Reads Internet Explorer settings
- KMSAuto Net.exe (PID: 5072)
Starts application with an unusual extension
- cmd.exe (PID: 2268)
- cmd.exe (PID: 3332)
- cmd.exe (PID: 5600)
- cmd.exe (PID: 4448)
- cmd.exe (PID: 1168)
- cmd.exe (PID: 744)
Executable content was dropped or overwritten
- AESDecoder.exe (PID: 4452)
- KMSAuto Net.exe (PID: 5072)
- bin_x64.dat (PID: 6828)
- bin.dat (PID: 5008)
- AESDecoder.exe (PID: 1164)
- bin_x64.dat (PID: 5404)
- bin.dat (PID: 5260)
- bin_x64.dat (PID: 4304)
- AESDecoder.exe (PID: 2800)
- bin.dat (PID: 6244)
Drops a system driver (possible attempt to evade defenses)
- bin_x64.dat (PID: 6828)
- bin_x64.dat (PID: 5404)
- bin_x64.dat (PID: 4304)
Process drops legitimate windows executable
- bin_x64.dat (PID: 6828)
- bin_x64.dat (PID: 5404)
- bin_x64.dat (PID: 4304)
Application launched itself
- cmd.exe (PID: 1388)
- cmd.exe (PID: 5244)
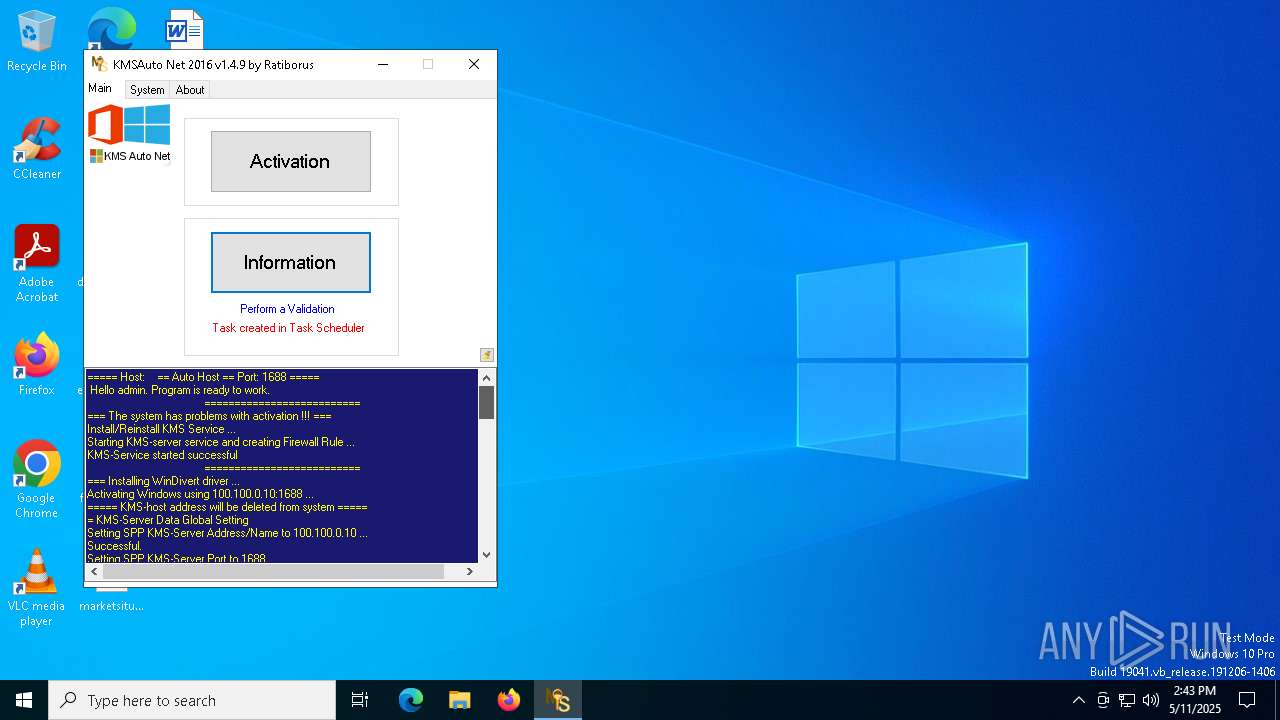
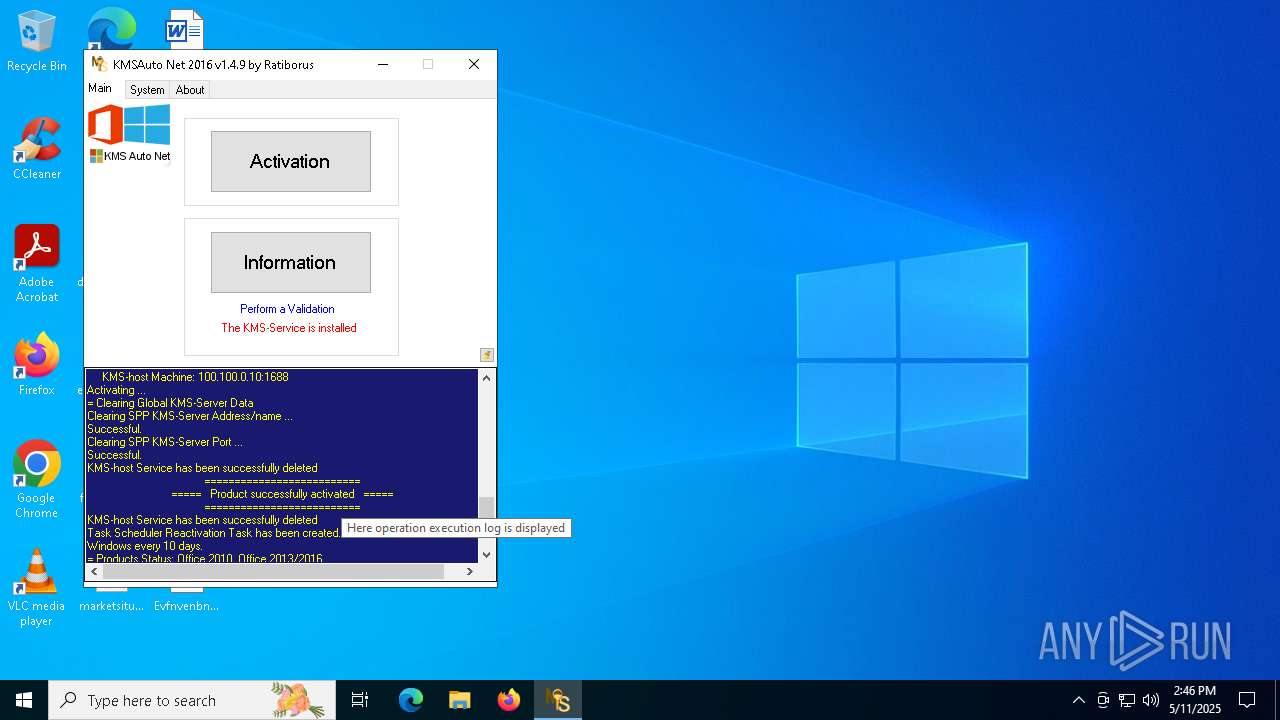
Uses NETSH.EXE to delete a firewall rule or allowed programs
- KMSAuto Net.exe (PID: 5072)
Uses NETSH.EXE to add a firewall rule or allowed programs
- KMSAuto Net.exe (PID: 5072)
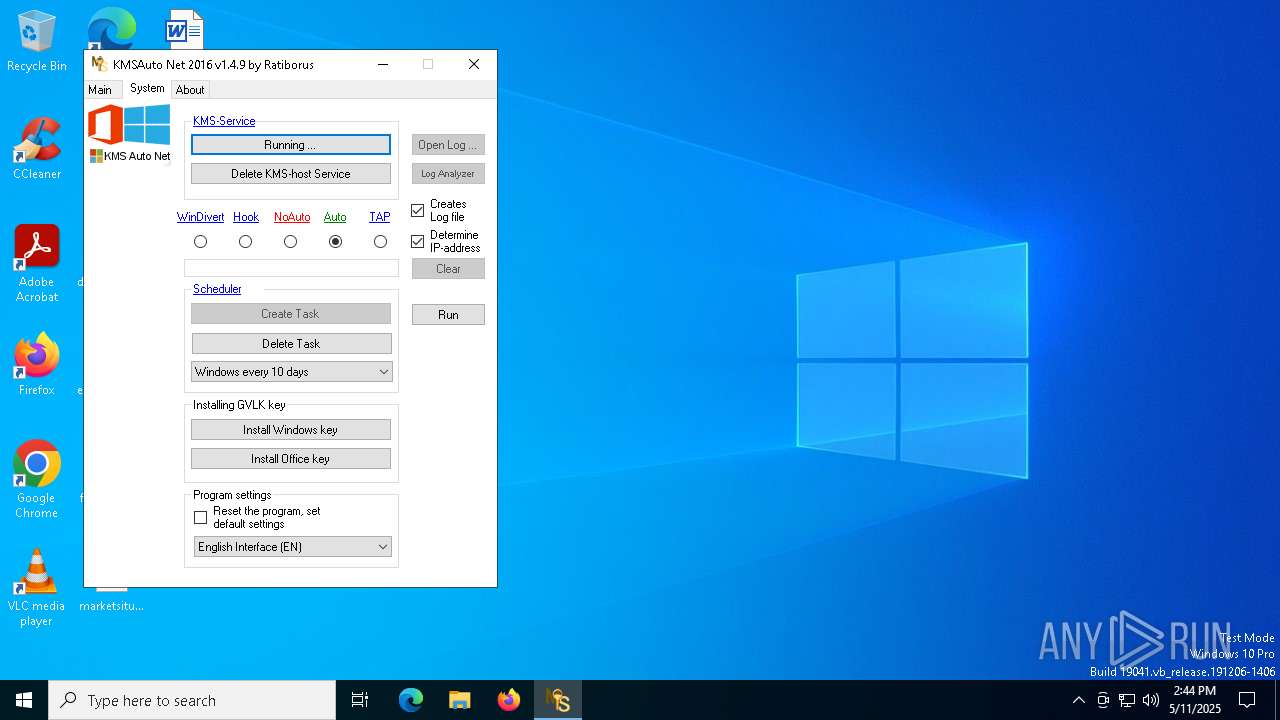
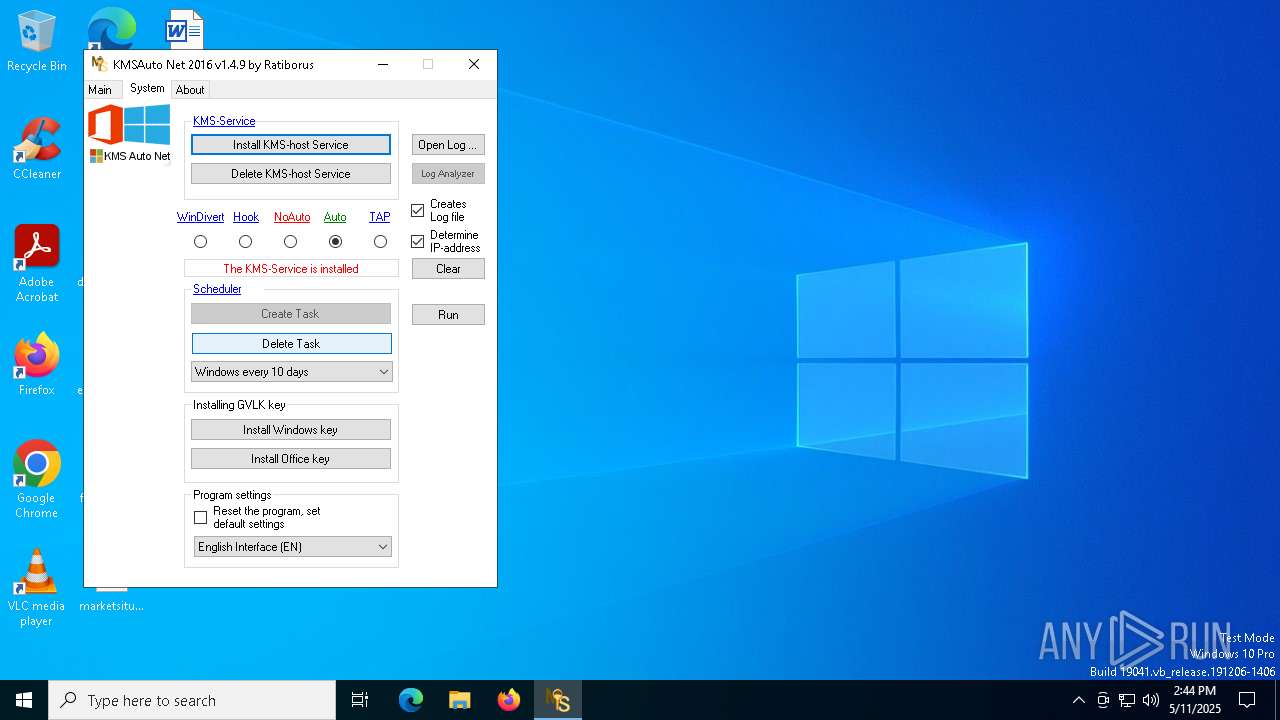
Creates a new Windows service
- sc.exe (PID: 5156)
- sc.exe (PID: 1040)
Creates or modifies Windows services
- KMSAuto Net.exe (PID: 5072)
Executes as Windows Service
- KMSSS.exe (PID: 5308)
- KMSSS.exe (PID: 6480)
Uses REG/REGEDIT.EXE to modify registry
- KMSAuto Net.exe (PID: 5072)
- cmd.exe (PID: 2288)
Uses ROUTE.EXE to modify routing table
- cmd.exe (PID: 5600)
Uses ROUTE.EXE to obtain the routing table information
- cmd.exe (PID: 5232)
Uses TASKKILL.EXE to kill process
- cmd.exe (PID: 6148)
Stops a currently running service
- sc.exe (PID: 3240)
- sc.exe (PID: 4728)
Windows service management via SC.EXE
- sc.exe (PID: 2980)
- sc.exe (PID: 4696)
- sc.exe (PID: 5720)
- sc.exe (PID: 856)
- sc.exe (PID: 6132)
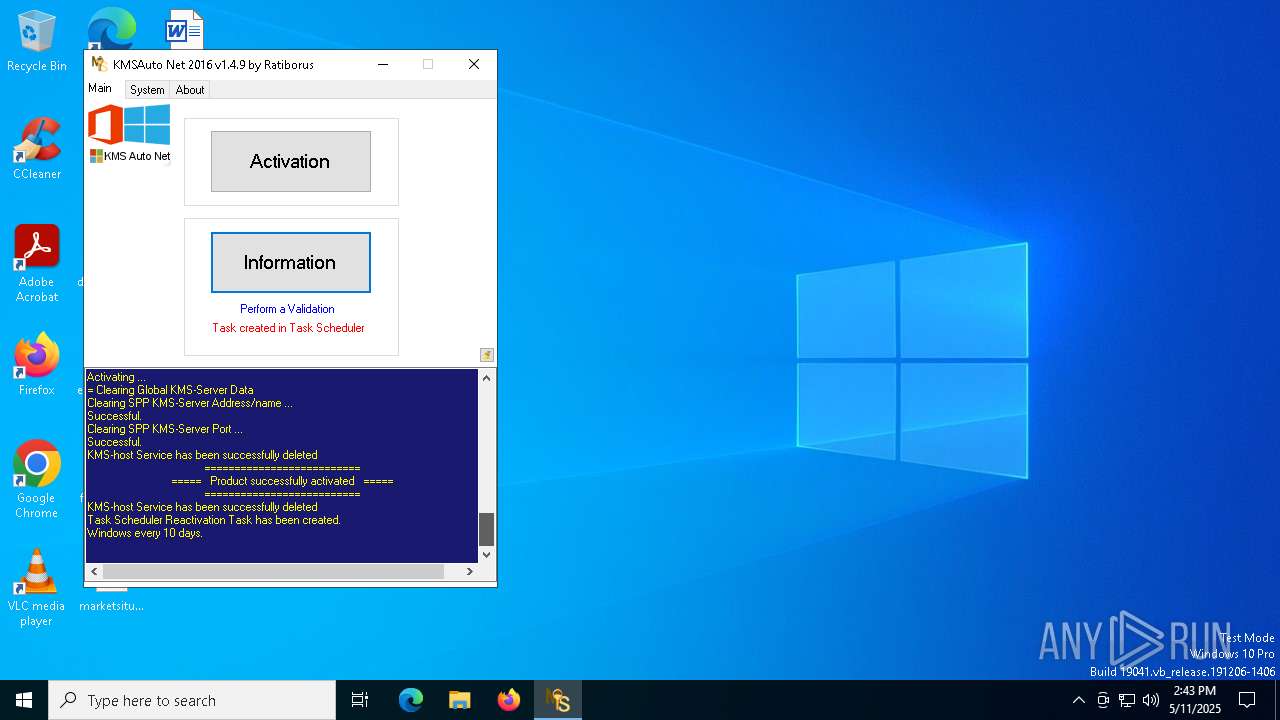
Deletes scheduled task without confirmation
- schtasks.exe (PID: 6660)
Modifies existing scheduled task
- schtasks.exe (PID: 456)
Starts SC.EXE for service management
- KMSAuto Net.exe (PID: 5072)
INFO
Reads the computer name
- KMSAuto Net.exe (PID: 5072)
- KMSSS.exe (PID: 5308)
- FakeClient.exe (PID: 2616)
- KMSSS.exe (PID: 6480)
Checks supported languages
- KMSAuto Net.exe (PID: 5072)
- bin.dat (PID: 5260)
- bin_x64.dat (PID: 6828)
- KMSSS.exe (PID: 5308)
- FakeClient.exe (PID: 2616)
- AESDecoder.exe (PID: 1164)
- bin.dat (PID: 5008)
- bin_x64.dat (PID: 5404)
- bin.dat (PID: 6244)
- AESDecoder.exe (PID: 4452)
- bin_x64.dat (PID: 4304)
- KMSSS.exe (PID: 6480)
- AESDecoder.exe (PID: 2800)
Reads the machine GUID from the registry
- KMSAuto Net.exe (PID: 5072)
- KMSSS.exe (PID: 5308)
- KMSSS.exe (PID: 6480)
Reads product name
- KMSAuto Net.exe (PID: 5072)
Creates files or folders in the user directory
- KMSAuto Net.exe (PID: 5072)
Reads Environment values
- KMSAuto Net.exe (PID: 5072)
Creates files in the program directory
- KMSAuto Net.exe (PID: 5072)
- cmd.exe (PID: 4448)
- bin.dat (PID: 5260)
- AESDecoder.exe (PID: 4452)
- bin_x64.dat (PID: 6828)
- KMSSS.exe (PID: 5308)
- cmd.exe (PID: 2064)
- bin.dat (PID: 5008)
- AESDecoder.exe (PID: 1164)
- bin_x64.dat (PID: 5404)
- cmd.exe (PID: 2656)
- bin.dat (PID: 6244)
- bin_x64.dat (PID: 4304)
- AESDecoder.exe (PID: 2800)
- KMSSS.exe (PID: 6480)
The sample compiled with english language support
- KMSAuto Net.exe (PID: 5072)
- bin_x64.dat (PID: 6828)
- bin_x64.dat (PID: 5404)
- bin_x64.dat (PID: 4304)
Creates a new folder
- cmd.exe (PID: 6728)
- cmd.exe (PID: 4448)
- cmd.exe (PID: 2656)
- cmd.exe (PID: 2064)
Adds a route via ROUTE.EXE
- ROUTE.EXE (PID: 2096)
Reads the software policy settings
- slui.exe (PID: 6184)
Deletes a route via ROUTE.EXE
- ROUTE.EXE (PID: 208)
Create files in a temporary directory
- KMSAuto Net.exe (PID: 5072)
Manual execution by a user
- WINWORD.EXE (PID: 4696)
- WINWORD.EXE (PID: 5136)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (16) |
|---|---|---|
| .scr | | | Windows screen saver (7.6) |
| .dll | | | Win32 Dynamic Link Library (generic) (3.8) |
| .exe | | | Win32 Executable (generic) (2.6) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2016:12:06 11:38:59+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32 |
| LinkerVersion: | 80 |
| CodeSize: | 8713728 |
| InitializedDataSize: | 49152 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x851422 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.4.9.0 |
| ProductVersionNumber: | 1.4.9.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | - |
| CompanyName: | MSFree Inc. |
| FileDescription: | KMSAuto Net |
| FileVersion: | 1.4.9 |
| InternalName: | KMSAuto Net.exe |
| LegalCopyright: | - |
| LegalTrademarks: | - |
| OriginalFileName: | KMSAuto Net.exe |
| ProductName: | KMSAuto Net |
| ProductVersion: | 1.4.9 |
| AssemblyVersion: | 1.4.9.0 |
Total processes
316
Monitored processes
173
Malicious processes
7
Suspicious processes
4
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 132 | netstat -ano | C:\Windows\System32\NETSTAT.EXE | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: TCP/IP Netstat Command Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 208 | route delete 100.100.0.10 0.0.0.0 | C:\Windows\System32\ROUTE.EXE | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: TCP/IP Route Command Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 300 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 456 | schtasks.exe /change /TN KMSAutoNet /RI 14400 | C:\Windows\System32\schtasks.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Task Scheduler Configuration Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 616 | netstat -ano | C:\Windows\System32\NETSTAT.EXE | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: TCP/IP Netstat Command Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 668 | cmd /c echo test>>"C:\Users\admin\Desktop\test.test" | C:\Windows\SysWOW64\cmd.exe | — | KMSAuto Net.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 720 | C:\WINDOWS\Sysnative\cmd.exe /D /c FakeClient.exe 100.100.0.10 | C:\Windows\System32\cmd.exe | — | KMSAuto Net.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 720 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | sc.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 736 | C:\WINDOWS\Sysnative\cmd.exe /D /c del /F /Q "bin.dat" | C:\Windows\System32\cmd.exe | — | KMSAuto Net.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 736 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | netsh.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
33 829
Read events
32 160
Write events
1 538
Delete events
131
Modification events
| (PID) Process: | (616) NETSTAT.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\RFC1156Agent\CurrentVersion\Parameters |
| Operation: | write | Name: | TrapPollTimeMilliSecs |
Value: 15000 | |||
| (PID) Process: | (5072) KMSAuto Net.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\KMSEmulator |
| Operation: | write | Name: | ImagePath |
Value: "C:\ProgramData\KMSAuto\bin\KMSSS.exe" -Port 1688 -PWin RandomKMSPID -PO14 RandomKMSPID -PO15 RandomKMSPID -PO16 RandomKMSPID -AI 43200 -RI 43200 -Log -IP | |||
| (PID) Process: | (5072) KMSAuto Net.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\KMSEmulator |
| Operation: | write | Name: | Description |
Value: KMS-host for all Microsoft VL Products | |||
| (PID) Process: | (5072) KMSAuto Net.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\KMSEmulator |
| Operation: | write | Name: | DisplayName |
Value: KMS-host Service | |||
| (PID) Process: | (5608) SppExtComObj.Exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows NT\CurrentVersion\SoftwareProtectionPlatform\55c92734-d682-4d71-983e-d6ec3f16059f\2de67392-b7a7-462a-b1ca-108dd189f588 |
| Operation: | write | Name: | DiscoveredKeyManagementServiceIpAddress |
Value: 100.100.0.10 | |||
| (PID) Process: | (3024) reg.exe | Key: | HKEY_USERS\S-1-5-20\SOFTWARE\Microsoft\Windows NT\CurrentVersion\SoftwareProtectionPlatform\55c92734-d682-4d71-983e-d6ec3f16059f\2de67392-b7a7-462a-b1ca-108dd189f588 |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (3024) reg.exe | Key: | HKEY_USERS\S-1-5-20\SOFTWARE\Microsoft\Windows NT\CurrentVersion\SoftwareProtectionPlatform\55c92734-d682-4d71-983e-d6ec3f16059f |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (132) NETSTAT.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\RFC1156Agent\CurrentVersion\Parameters |
| Operation: | write | Name: | TrapPollTimeMilliSecs |
Value: 15000 | |||
| (PID) Process: | (4696) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\Common\ClientTelemetry\Sampling |
| Operation: | write | Name: | 0 |
Value: 017012000000001000B24E9A3E02000000000000000600000000000000 | |||
| (PID) Process: | (4696) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\Common\CrashPersistence\WINWORD\4696 |
| Operation: | write | Name: | 0 |
Value: 0B0E107F6C42D99BB6F64A97370E6BEFEB2F8F23004684CE8E9CB4D0F0ED016A04102400449A7D64B29D01008500A907556E6B6E6F776EC906022222CA0DC2190000C91003783634C511D824D2120B770069006E0077006F00720064002E00650078006500C51620C517808004C91808323231322D44656300 | |||
Executable files
79
Suspicious files
186
Text files
76
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 668 | cmd.exe | C:\Users\admin\Desktop\test.test | text | |
MD5:9F06243ABCB89C70E0C331C61D871FA7 | SHA256:837CCB607E312B170FAC7383D7CCFD61FA5072793F19A25E75FBACB56539B86B | |||
| 5072 | KMSAuto Net.exe | C:\Users\admin\AppData\Local\MSfree Inc\kmsauto.ini | text | |
MD5:AF6A20FD7DFADCD582CCF2B1BFAAF82B | SHA256:0BEE97833A70AA9BA271E93226DACE849836C64919FBFE15543D694E219D4AF2 | |||
| 4452 | AESDecoder.exe | C:\ProgramData\KMSAuto\bin\KMSSS.exe | executable | |
MD5:ADD80E5D9FAD482705C3807BACFE1993 | SHA256:BB3830B14DF80838FB201C611ABF0C1F3714C6B8B103ED084EAFC170036631BE | |||
| 5260 | bin.dat | C:\ProgramData\KMSAuto\bin\TunMirror2.exe.aes | binary | |
MD5:A1A5AFA53B578DB6ABF400A88548F487 | SHA256:A9E76D637E0C0A65036D7F2D5C3D7B1C53218B94716554F4D9F6630DCFF8C75A | |||
| 5260 | bin.dat | C:\ProgramData\KMSAuto\bin\AESDecoder.exe | executable | |
MD5:B90ED3E4DBB23A464723706F12C86065 | SHA256:8391D5B724D235BA52531D9A6D85E466382CE15CBD6BA97C4AD1278ED1F03BD7 | |||
| 6828 | bin_x64.dat | C:\ProgramData\KMSAuto\bin\driver\x64TAP1\ptun0901.cat | binary | |
MD5:28B3A205C15D9D722319D270B3500BD0 | SHA256:438B3CDB66A5E1CE7B659744B81A570EB7CB0C8B403738A17DD2629625B0C765 | |||
| 6828 | bin_x64.dat | C:\ProgramData\KMSAuto\bin\driver\oas_sert.cer | binary | |
MD5:0041584E5F66762B1FA9BE8910D0B92B | SHA256:BB27684B569CBB72DEC63EA6FDEF8E5F410CDAEB73717EEE1B36478DBCFF94CC | |||
| 6828 | bin_x64.dat | C:\ProgramData\KMSAuto\bin\driver\x64TAP1\OemVista.inf | binary | |
MD5:864625122184689B4854483B51BD4C09 | SHA256:4A4CC81DD6655906E817EBAEDE1692871A79B7000A5F9188B30082C06C71894B | |||
| 5260 | bin.dat | C:\ProgramData\KMSAuto\bin\KMSSS.exe.aes | binary | |
MD5:9192D6947F2A3ABF00084DEDA48A2C6F | SHA256:DED5E9E73B2BA3BD188C98A58335C65FE149D2082B88C3D91516ED25E5A379EE | |||
| 4452 | AESDecoder.exe | C:\ProgramData\KMSAuto\bin\TunMirror.exe | executable | |
MD5:FB5F055633E4F7890004972E108A07CD | SHA256:02145C3F60E704DF17919CD26CB79BD31A12B98D66B0B7FD1CF7EA894AD1F871 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
17
TCP/UDP connections
107
DNS requests
42
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 23.48.23.194:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6468 | SIHClient.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
6468 | SIHClient.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
2924 | SearchApp.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
5136 | WINWORD.EXE | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEApDqVCbATUviZV57HIIulA%3D | unknown | — | — | whitelisted |
5136 | WINWORD.EXE | GET | 200 | 23.48.23.143:80 | http://crl.microsoft.com/pki/crl/products/MicrosoftTimeStampPCA.crl | unknown | — | — | whitelisted |
5136 | WINWORD.EXE | GET | 200 | 23.48.23.143:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut_2010-06-23.crl | unknown | — | — | whitelisted |
5136 | WINWORD.EXE | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicCodSigPCA2011_2011-07-08.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 23.48.23.194:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3216 | svchost.exe | 172.211.123.249:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 40.126.31.128:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6544 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
2104 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
validation-v2.sls.microsoft.com |
| whitelisted |