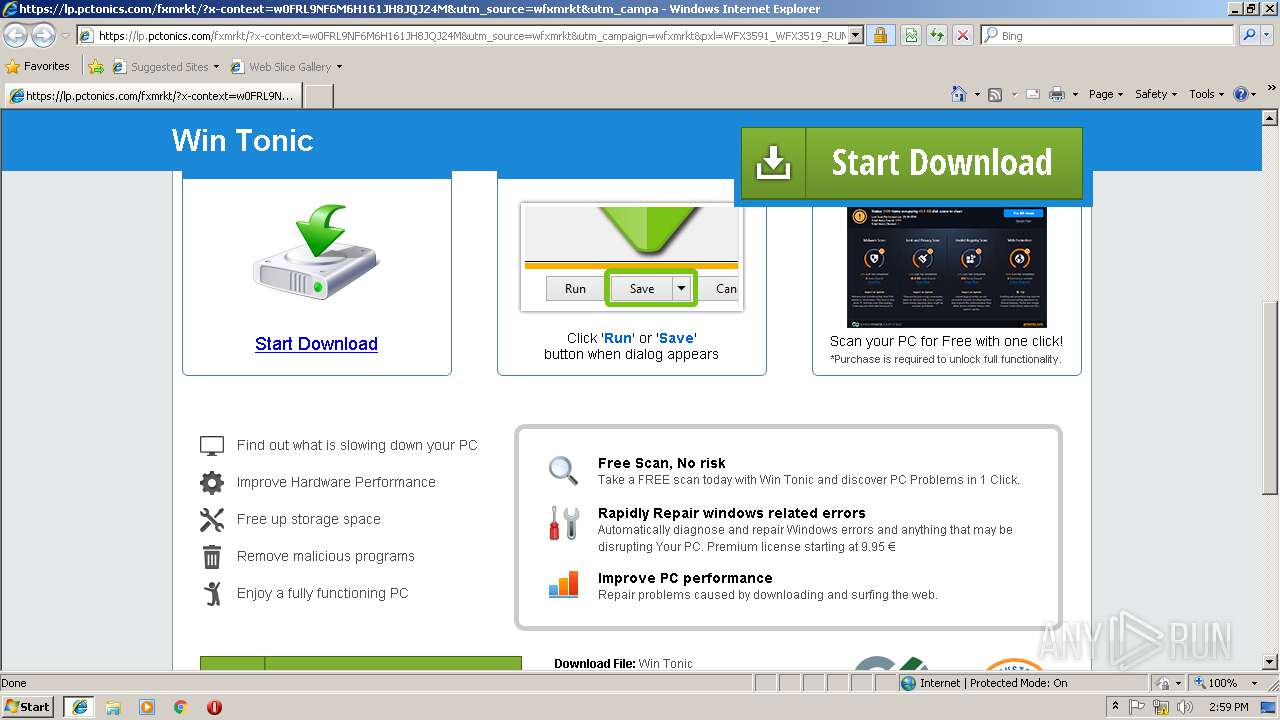
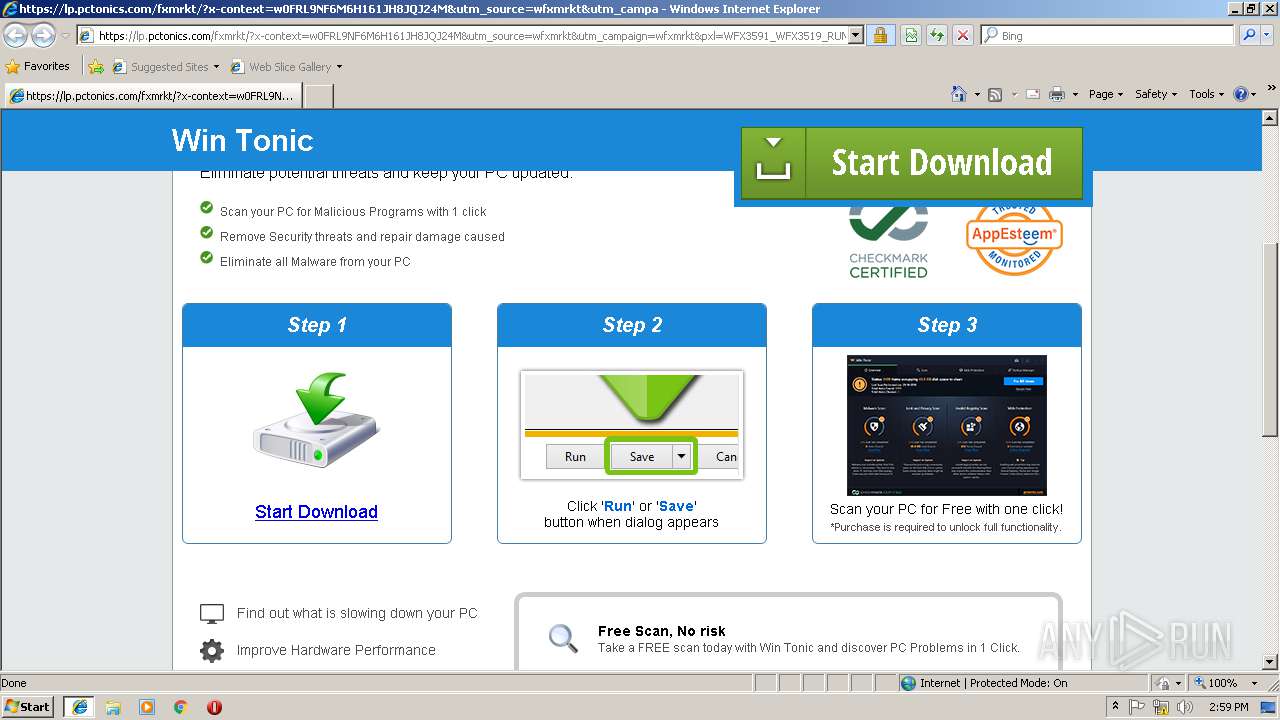
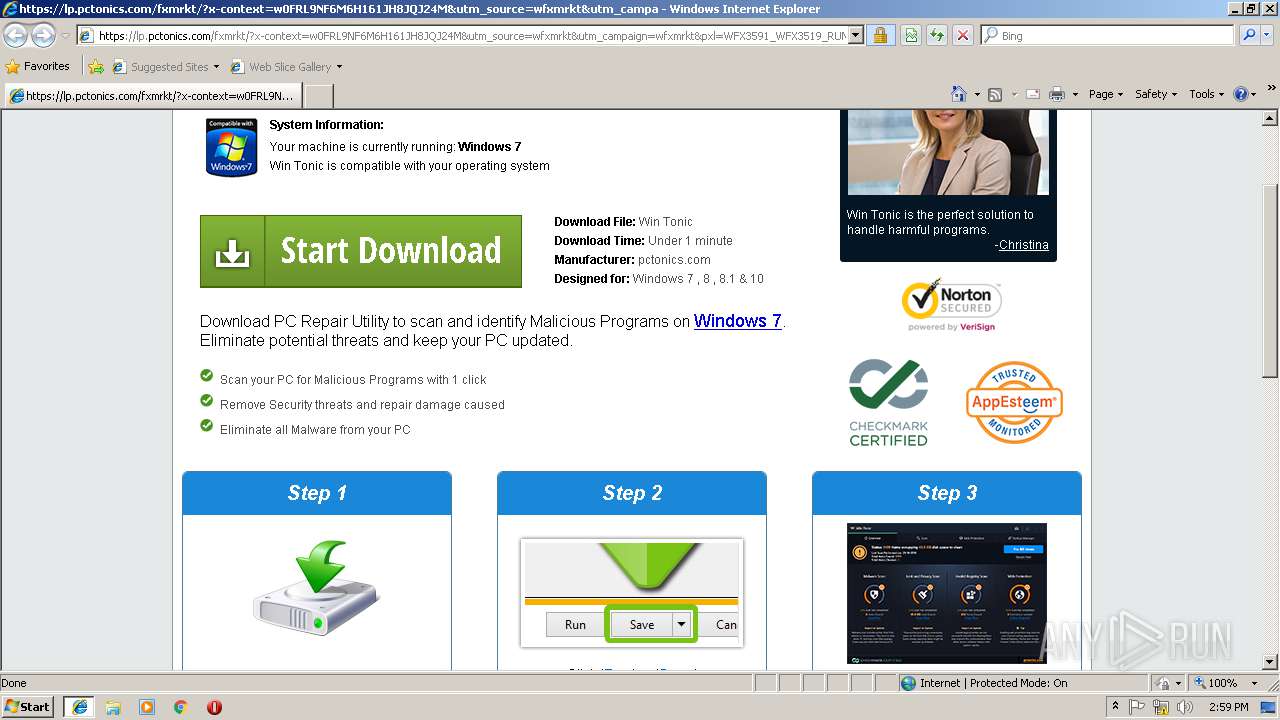
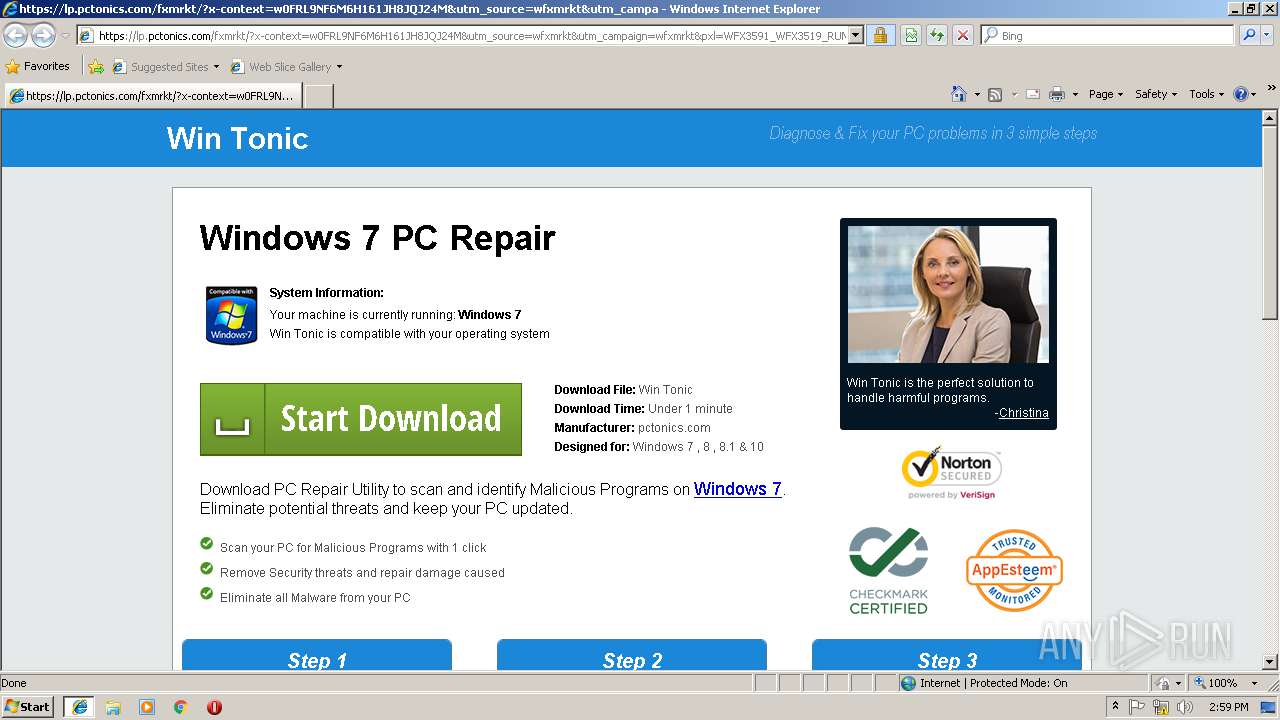
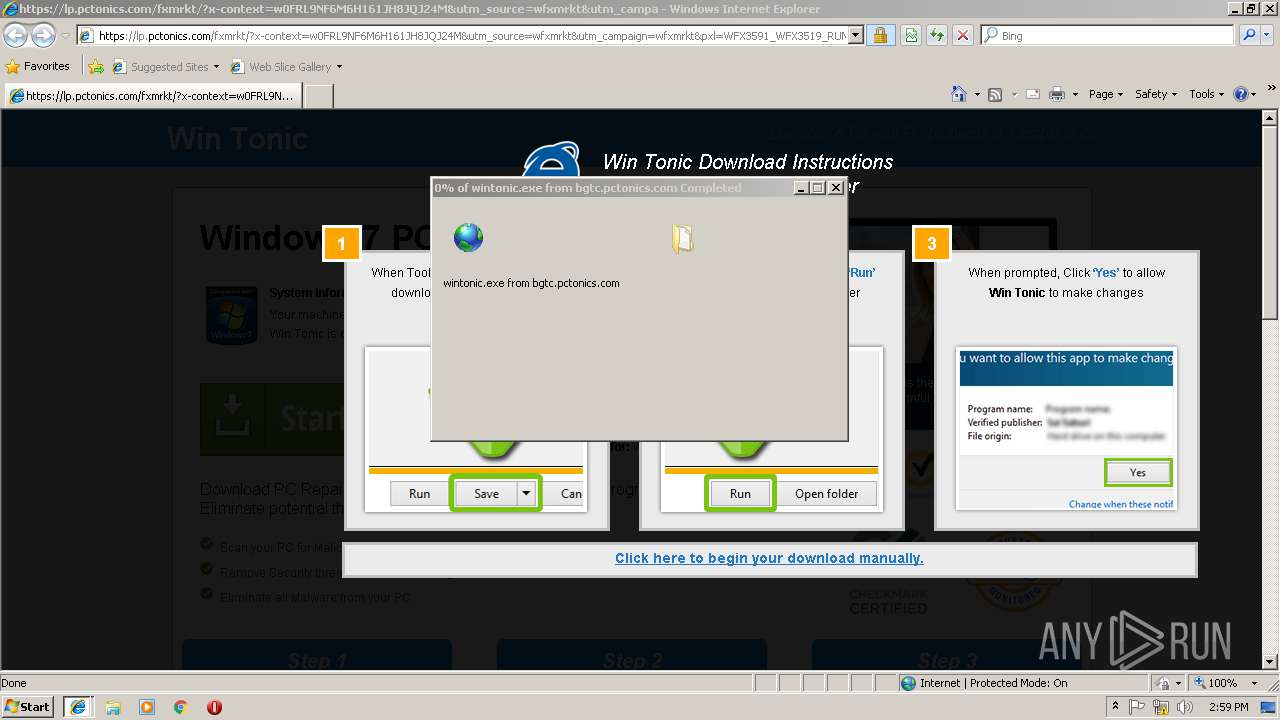
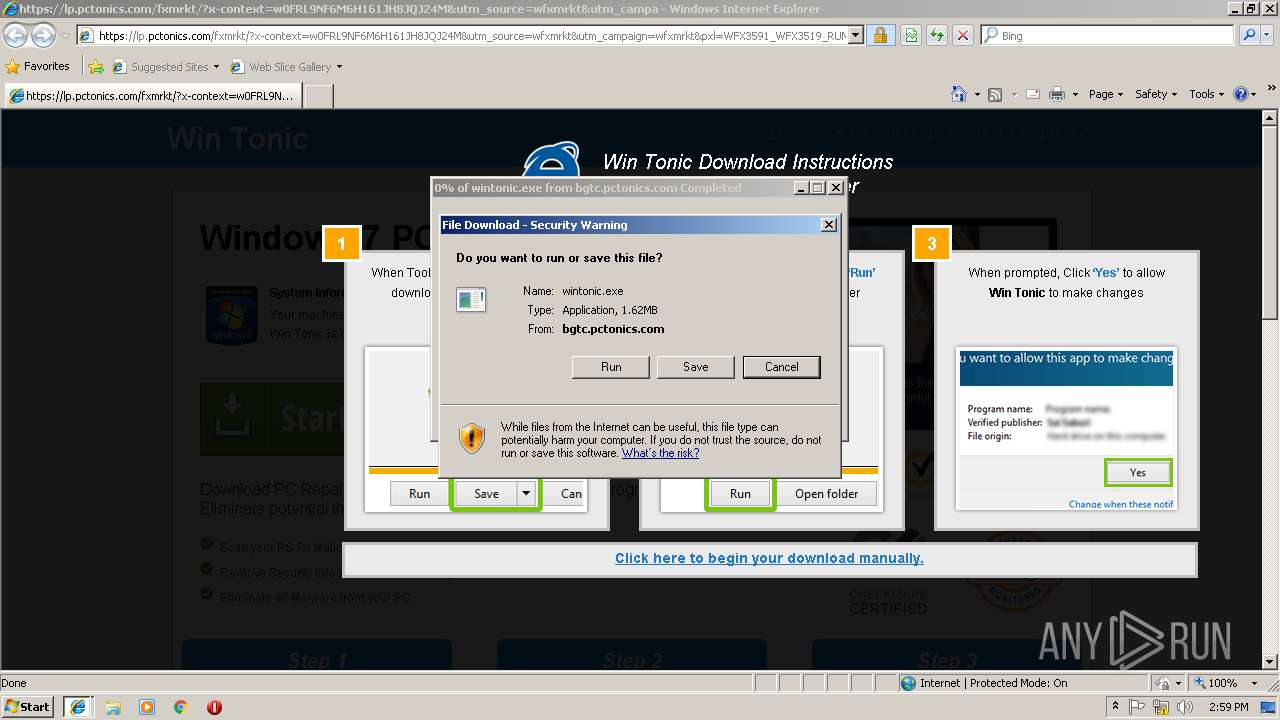
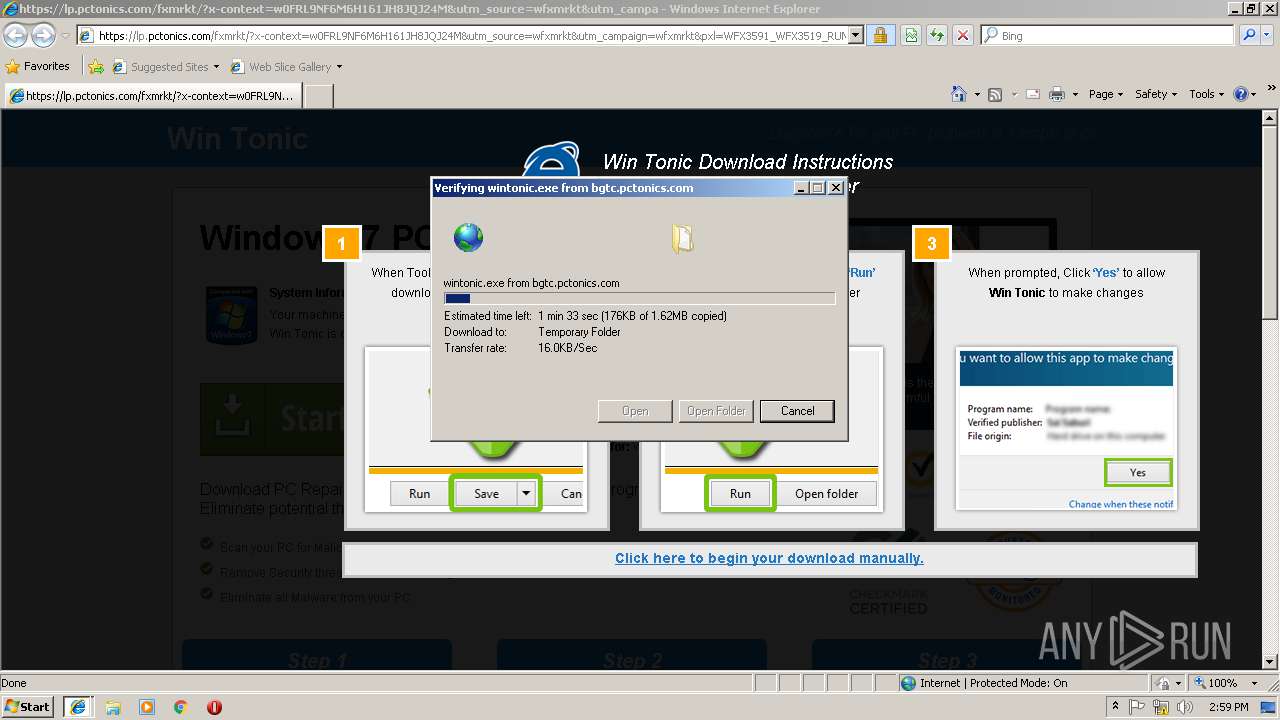
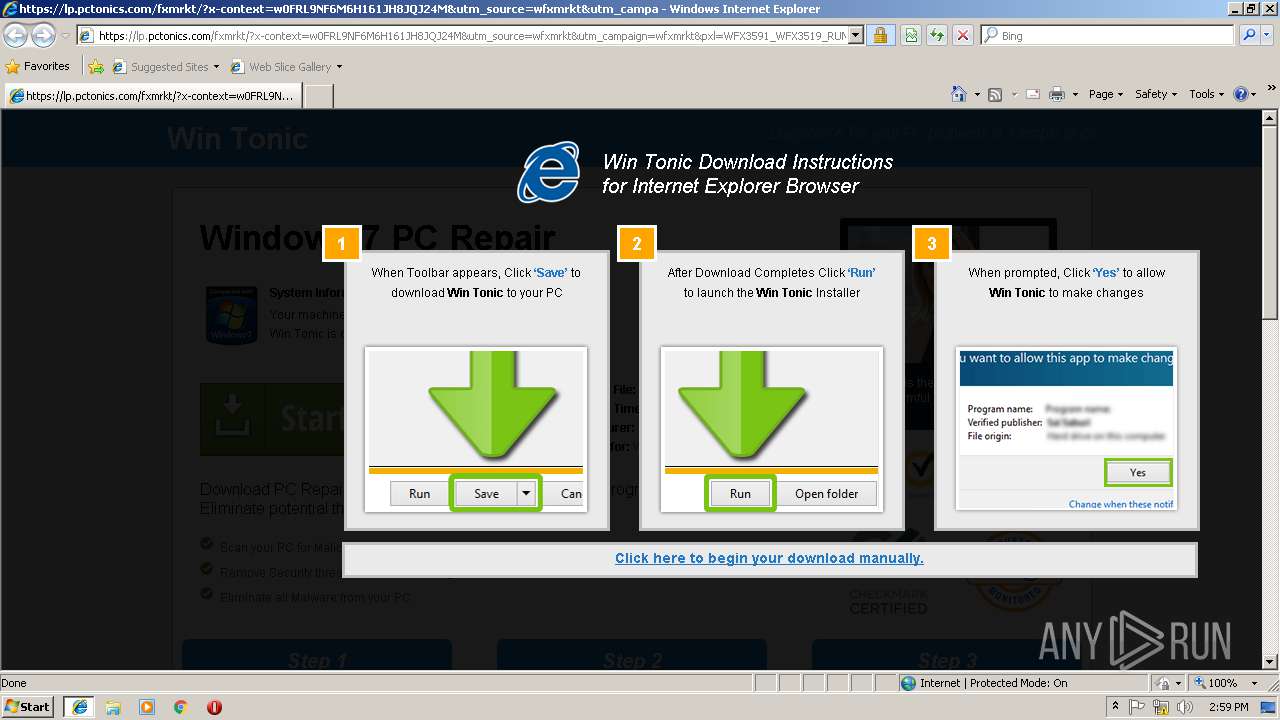
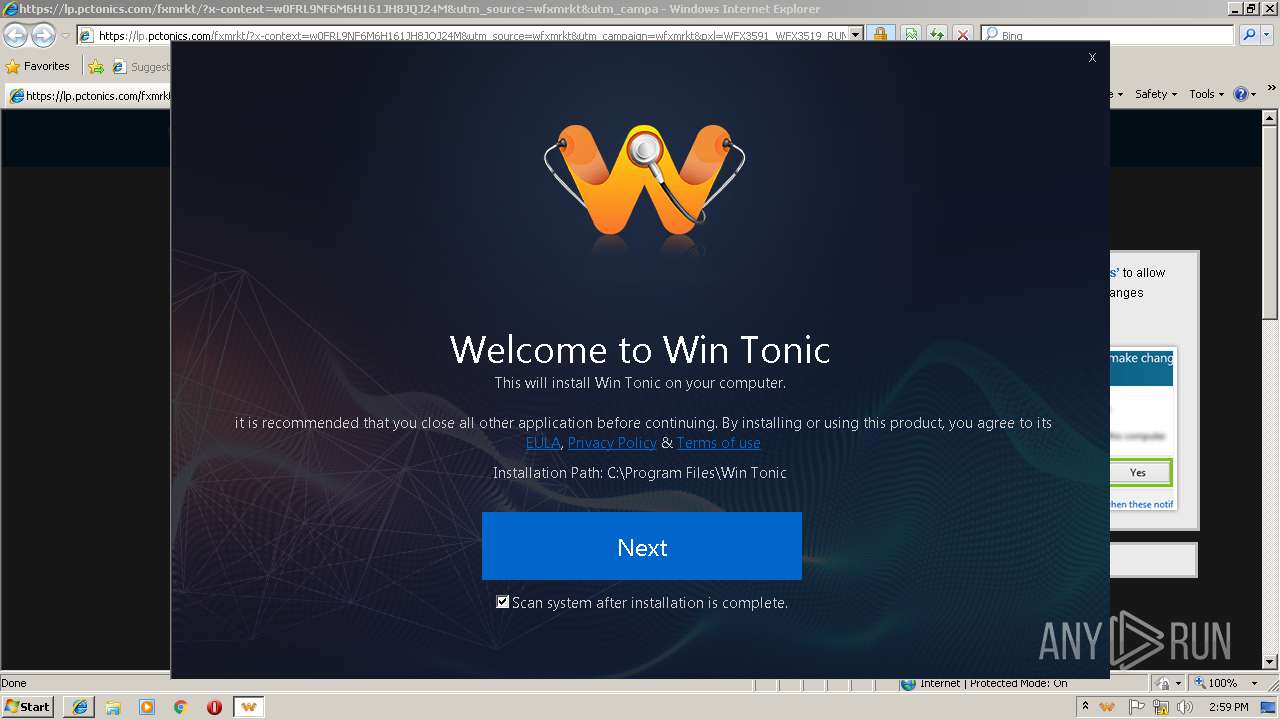
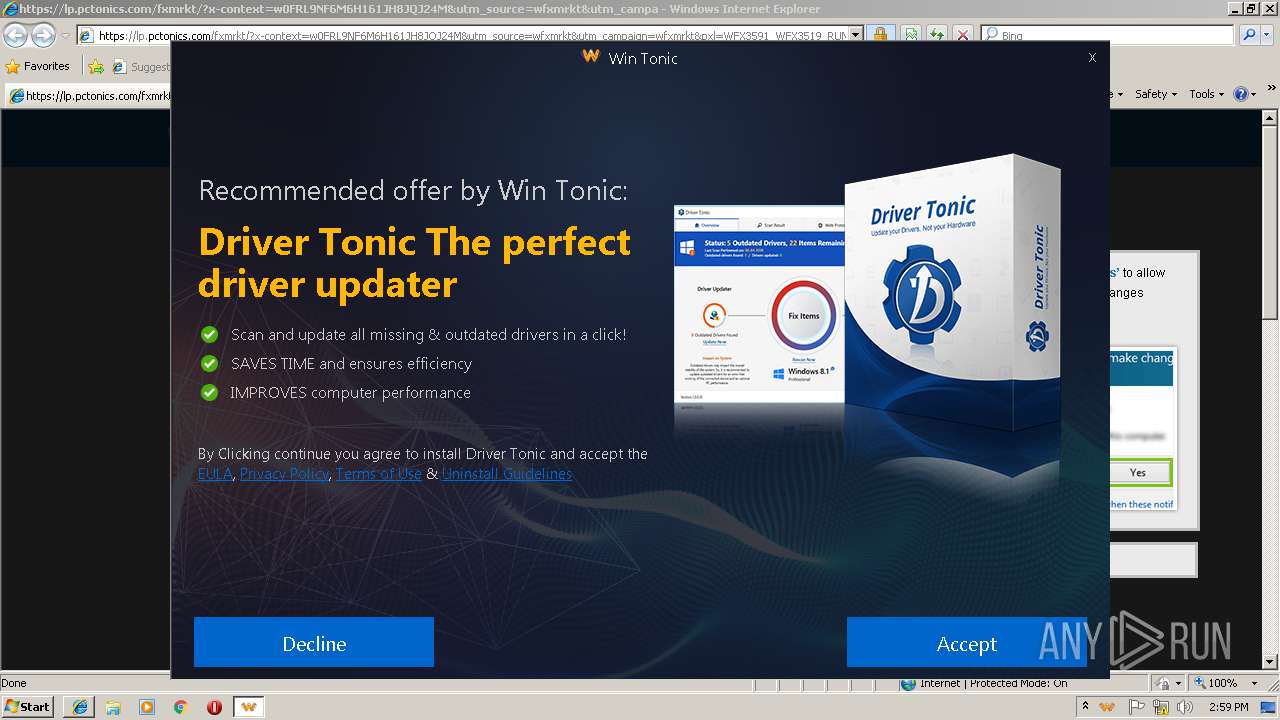
| URL: | http://ericsoon.com/5g |
| Full analysis: | https://app.any.run/tasks/ef2cf6fc-9f10-4ad3-b064-1d7407976b26 |
| Verdict: | Malicious activity |
| Analysis date: | December 18, 2018, 14:56:00 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | F7866FFC9365C10914C04145F41F607E |
| SHA1: | 4E12358BFC2ED80323261120ECC619BEAA082FC7 |
| SHA256: | B8AC81C94D1526343203D8EED8E7C7C9E96EC2496219E309AD72EF927B95226D |
| SSDEEP: | 3:N1Kb9Zin:Czi |
MALICIOUS
Application was dropped or rewritten from another process
- wintonic[1].exe (PID: 3776)
- wintonic[1].exe (PID: 2684)
- wntsetup.exe (PID: 2336)
- wtc.exe (PID: 3060)
Changes settings of System certificates
- wintonic[1].exe (PID: 2684)
- wtc.exe (PID: 3060)
Loads the Task Scheduler COM API
- schtasks.exe (PID: 3004)
Uses Task Scheduler to run other applications
- wntsetup.tmp (PID: 2488)
Loads dropped or rewritten executable
- wtc.exe (PID: 3060)
SUSPICIOUS
Executable content was dropped or overwritten
- iexplore.exe (PID: 3148)
- iexplore.exe (PID: 2852)
- wntsetup.exe (PID: 2336)
- wntsetup.tmp (PID: 2488)
- wintonic[1].exe (PID: 2684)
- wtc.exe (PID: 3060)
Reads internet explorer settings
- wintonic[1].exe (PID: 2684)
Uses RUNDLL32.EXE to load library
- wintonic[1].exe (PID: 2684)
Reads Internet Cache Settings
- rundll32.exe (PID: 3004)
- rundll32.exe (PID: 2980)
- wtc.exe (PID: 3060)
Adds / modifies Windows certificates
- wintonic[1].exe (PID: 2684)
Uses TASKKILL.EXE to kill process
- wntsetup.tmp (PID: 2488)
Reads Windows owner or organization settings
- wntsetup.tmp (PID: 2488)
Reads the Windows organization settings
- wntsetup.tmp (PID: 2488)
Creates files in the user directory
- wntsetup.tmp (PID: 2488)
- wtc.exe (PID: 3060)
INFO
Application launched itself
- iexplore.exe (PID: 2852)
Changes internet zones settings
- iexplore.exe (PID: 2852)
Reads Internet Cache Settings
- iexplore.exe (PID: 2852)
- iexplore.exe (PID: 3148)
Reads internet explorer settings
- iexplore.exe (PID: 3148)
Reads settings of System Certificates
- iexplore.exe (PID: 2852)
- wintonic[1].exe (PID: 2684)
Creates files in the user directory
- FlashUtil32_26_0_0_131_ActiveX.exe (PID: 3592)
- iexplore.exe (PID: 3148)
Adds / modifies Windows certificates
- iexplore.exe (PID: 2852)
Changes settings of System certificates
- iexplore.exe (PID: 2852)
Creates files in the program directory
- wntsetup.tmp (PID: 2488)
Application was dropped or rewritten from another process
- wntsetup.tmp (PID: 2488)
Loads dropped or rewritten executable
- wntsetup.tmp (PID: 2488)
Creates a software uninstall entry
- wntsetup.tmp (PID: 2488)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
51
Monitored processes
12
Malicious processes
5
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1936 | "C:\Windows\System32\taskkill.exe" /f /im "wtc.exe" | C:\Windows\System32\taskkill.exe | — | wntsetup.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Terminates Processes Exit code: 128 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
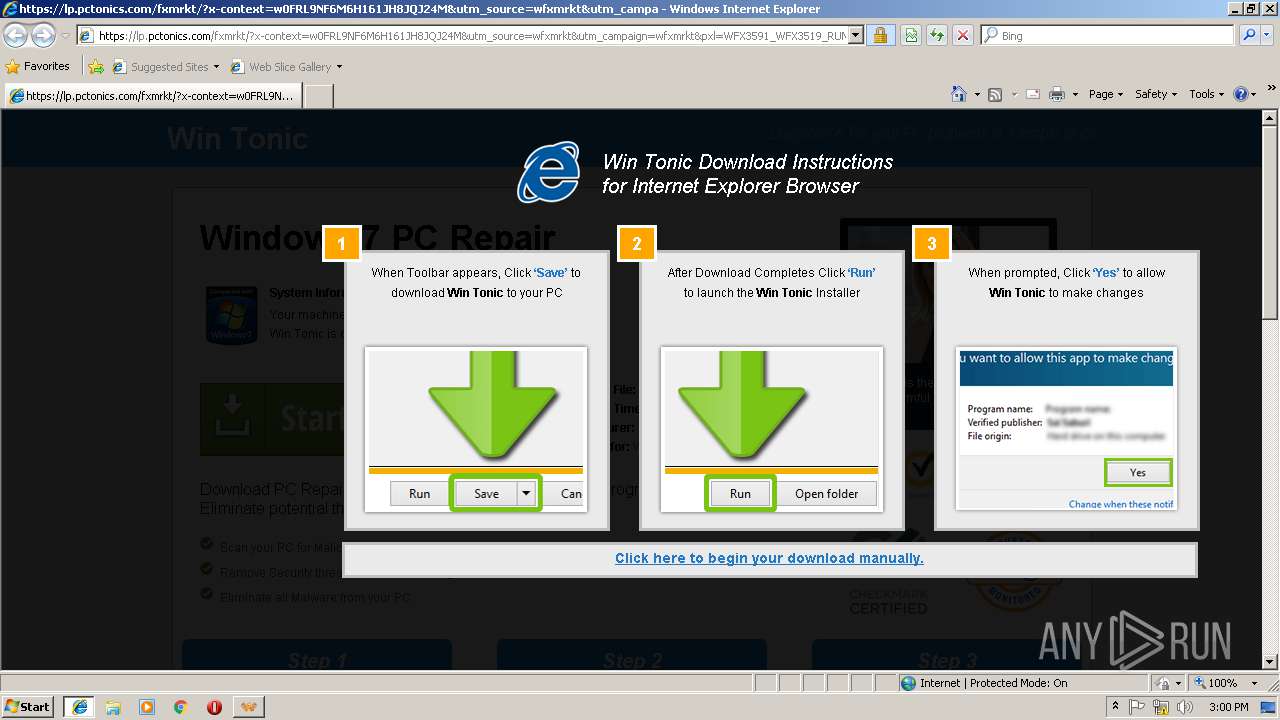
| 2336 | C:\Users\admin\AppData\Local\Temp\~tlljpxz.tmp\wntsetup.exe /verysilent /insdu | C:\Users\admin\AppData\Local\Temp\~tlljpxz.tmp\wntsetup.exe | wintonic[1].exe | ||||||||||||
User: admin Company: pctonics.com Integrity Level: HIGH Description: Win Tonic Setup Exit code: 0 Version: 1.0.0.13 Modules
| |||||||||||||||
| 2488 | "C:\Users\admin\AppData\Local\Temp\is-G5KU9.tmp\wntsetup.tmp" /SL5="$50222,7504259,148992,C:\Users\admin\AppData\Local\Temp\~tlljpxz.tmp\wntsetup.exe" /verysilent /insdu | C:\Users\admin\AppData\Local\Temp\is-G5KU9.tmp\wntsetup.tmp | wntsetup.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Setup/Uninstall Exit code: 0 Version: 51.1052.0.0 Modules
| |||||||||||||||
| 2684 | "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\R9ZEWH8D\wintonic[1].exe" | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\R9ZEWH8D\wintonic[1].exe | iexplore.exe | ||||||||||||
User: admin Company: pctonics.com Integrity Level: HIGH Description: Win Tonic Setup Exit code: 0 Version: 1.0.0.13 Modules
| |||||||||||||||
| 2852 | "C:\Program Files\Internet Explorer\iexplore.exe" -nohome | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2980 | "C:\Windows\system32\rundll32.exe" "C:\Windows\system32\WININET.dll",DispatchAPICall 1 | C:\Windows\system32\rundll32.exe | — | wintonic[1].exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3004 | "C:\Windows\system32\rundll32.exe" "C:\Windows\system32\WININET.dll",DispatchAPICall 1 | C:\Windows\system32\rundll32.exe | — | wintonic[1].exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3004 | "C:\Windows\System32\schtasks.exe" /delete /tn "Win Tonic_launcher" /f | C:\Windows\System32\schtasks.exe | — | wntsetup.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Manages scheduled tasks Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3060 | "C:\Program Files\Win Tonic\wtc.exe" getdetails | C:\Program Files\Win Tonic\wtc.exe | wntsetup.tmp | ||||||||||||
User: admin Company: pctonics.com Integrity Level: HIGH Description: Win Tonic Exit code: 0 Version: 1.0.0.13 Modules
| |||||||||||||||
| 3148 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:2852 CREDAT:71937 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
1 404
Read events
1 183
Write events
215
Delete events
6
Modification events
| (PID) Process: | (2852) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (2852) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (2852) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (2852) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Zones |
| Operation: | write | Name: | SecuritySafe |
Value: 1 | |||
| (PID) Process: | (2852) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (2852) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 4600000069000000010000000000000000000000000000000000000000000000C0E333BBEAB1D301000000000000000000000000020000001700000000000000FE800000000000007D6CB050D9C573F70B000000000000006D00330032005C004D00530049004D004700330032002E0064006C000100000004AA400014AA4000040000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000002000000C0A8016400000000000000000000000000000000000000000800000000000000805D3F00983740000008000002000000000000600000002060040000B8A94000020000008802000060040000B8A9400004000000F8010000B284000088B64000B84B400043003A000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2852) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Recovery\Active |
| Operation: | write | Name: | {1760C701-02D5-11E9-BAD8-5254004A04AF} |
Value: 0 | |||
| (PID) Process: | (2852) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{2670000A-7350-4F3C-8081-5663EE0C6C49}\iexplore |
| Operation: | write | Name: | Type |
Value: 4 | |||
| (PID) Process: | (2852) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{2670000A-7350-4F3C-8081-5663EE0C6C49}\iexplore |
| Operation: | write | Name: | Count |
Value: 3 | |||
| (PID) Process: | (2852) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{2670000A-7350-4F3C-8081-5663EE0C6C49}\iexplore |
| Operation: | write | Name: | Time |
Value: E2070C00020012000E0038001B003000 | |||
Executable files
38
Suspicious files
20
Text files
89
Unknown types
14
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2852 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\RB73MZ6Y\favicon[1].ico | — | |
MD5:— | SHA256:— | |||
| 2852 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\Services\search_{0633EE93-D776-472f-A0FF-E1416B8B2E3A}.ico | — | |
MD5:— | SHA256:— | |||
| 3148 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\admin@mybestmv[1].txt | — | |
MD5:— | SHA256:— | |||
| 3148 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\CabBAC1.tmp | — | |
MD5:— | SHA256:— | |||
| 3148 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\TarBAC2.tmp | — | |
MD5:— | SHA256:— | |||
| 3148 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\CabBAE2.tmp | — | |
MD5:— | SHA256:— | |||
| 3148 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\TarBAE3.tmp | — | |
MD5:— | SHA256:— | |||
| 3148 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\CabBB80.tmp | — | |
MD5:— | SHA256:— | |||
| 3148 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\TarBB81.tmp | — | |
MD5:— | SHA256:— | |||
| 3148 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\admin@lp.pctonics[2].txt | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
18
TCP/UDP connections
36
DNS requests
26
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2684 | wintonic[1].exe | GET | 200 | 216.245.208.194:80 | http://www.winactiv.com/mtrack/?metd=trackBlog&utm_source=wtninstlr&utm_campaign=wtninstlr&pxl=WTN2631_WTN2573_RUNT&x-fetch=1 | US | — | — | malicious |
3148 | iexplore.exe | GET | 302 | 108.168.193.189:80 | http://mybestmv.com/aS/feedclick?s=yytAuj_c3efSrSIi1CQOo63dDnCBF-q5ZHDKZGtRZ0YH0A88-gtuC6d73pnnDH6ohvzYfNFjJsIjeRAqbTvnp39VQ1WDsBX4gvjSx48oQmVg6RfU48Vyi6YZ_8dAZcE4MLekFlfWsTpfBjRhq2gpKFKUZ1W8pDiXxXHyM723-XJcSR5VscbDD-A8cJKrn3eoTMLXzdyCk6w0YvkDo2w1bbwkueIpEfbrPPB5QXnxCJnTJdtF0FOG52EZNfOdEfrqm0Stm87Dehj0XczhdPgzfAxYLQJlA6AdI8zBVm7CLKsYpwe7FJ8U9sxCWoFgZnU3QgHE_ADrcYET59b5H4ABP-BwOAusydB7aMw9kf3Q7WUsK-KyPeLtw0E60J1thegEDs1KkpwizIONxe921dax5gL7-qli9f0u4REv6cueBFLrtGILh46O8EEz9p_dzN2qppmEYGHEpbI7M5IsSMyry4DY8GkP8LkljcraP653I1h7fYyz4nV6TgglzHkQMy51lSXtdxiQ5NsvHNKls5gu_zA_4RrwlH-LQIpEXAzTdzKuTo1EEtXt1mKAuioWlk1NjYeCldHCV01FhrsH_YFO96NoqgfayOufX-4j2HaYavCo-0lVQgWWao1A_Oy-YoJRgE6y61F-l4bmhCIE4olKgVcAcKGTPLfJ94PSzH08SX6Fi0krfrDcnMEi4p_qQYwulWIXFY7Pbuyu3pXFP_20YSL4-tfwdwSohsCsflWRAUaH3WwB5kYnN_6MEkuUl-xygQwZrSjSsGGFUFk7SB2euQ0uDtmuFc9ISoU3O3fwhzCAXjwUBfCbrFtMeq2ceQUPCHpImeQceId2FKGXEZYMFESvs19ePKv7Jnafg4zsE5hlq9a5XjilKgcCYnoJcgTTd27OVL8lU4ryy2ugQQRCmrizOwAO_7JwMN9Ql0tMp6G_0Dp5RXCD1i33OPVbnIqZ5m5znWyhW44i5EOxelb9ftCtzdlG7ZSZ6LOXG4z6rYwL18iG0zeaBfMlt3vmHU5eVCmV5Z-9CTOUcetgOamKG0pCrC_Pq4DA6tBTf_fCnR_iJ3dopc6SfWxSLtP0jVcVzRqlr-dSWB_BqpL9w-751Toibwg-lPQaoblk4PzTY2SPj4-suADJRnvjUD-ieftCeR7UZWfo0eCchxPX96b1dyQPtXcJTecQHYnF_uGKIhdpqhpekI-YEw-YHz9wjN_a1iSnaG39La5KXFpr4jnsmj1yRaKza98liONbHPwQZsO8YmaKOcu1_CHqzSk-KRg7Hh1Ks9EDqy402f8tgGtHKXoQBFlUUAsN62zf_3xM1EzY519alF2DU8ma27xqJzjTjYfrT0TkyaLnMDgCYKw_zW5VKObqgy2Ue8yETgMdE27l7_yFLjmCLn6-41xWTjNYVizBVEQQ2Z5toTkcPX6zURAfwEFmHutHThS_zYdsP057uO7DPCiDGW_mE6U66cwqaM0swxNkiW6YXVVUf0QPFd2bqkHtxqQPKo8iO1JoiW9ytZY5qgqGhw6WvqfIg96vCoAN_22zkXdxREC8vdmwb22VXE0y3wuXLJHIL8yvwhRuuLMfUDT6n5cYL73NcRS2oikebNLrD9B2dzKtS9icSgMOu-BzdDgwdrm_ccF9cB6eJ04bw6ekIh44QXQMSG8ajTvLAWjnNWyAHki7oSet2XFEQLy92bBv3W1GV8cpqri6ZwgJdGYaHBEgmeh4brRO9EOBv62nc2X8UbfPZDllnG2epDSGEpB11KOS4FTG_CLdbUZXxymquKkc16KWdVhql6LEptcXKyJUX8w5y5YYMM1ChNUa0Z7NSSQeS1G6U-o-6lDa6sitqCU7ugF2M-yurttxDkCRSzKtK6Mz5FaVqw | US | — | — | suspicious |
3148 | iexplore.exe | GET | 302 | 108.168.193.189:80 | http://p238000.mybestmv.com/adServe/domainClick?ai=k1rIm1Xu0SnhGf0HCi4Z4N8ecLmJCpIXqsmJbRsC1AIcmWdW5gasRvDjQQu8g48YHjhBdAxIbxoOmJXbaQnOeMHqawRSqy3iSM2cJjXHyR2zX6GIO2tD51TnXZ0xChEfzQeUGEmV2rK3l70Jp2tIot7uyrqp8mCM7FPzlMKFAR8pboxl453J5r2Q8GLkctPB22093hIRLkRvTGlATFPocyEWv4AX6X80NlvZceNveDSNh_0QqYMZBQW2EPX3lzlhOP4Y9yygj9tfb5FQeZl75NtmHa-sXA6BXP6n_paJdUeYDMm3vSUGcJ63Auzq9ETFjWCJrE7_AWbZBTo5Q_lXiXsmXgeLf7LqVtI4n5UgcdZB9i_JnmT88Zc9r3PL9gX26ZahH6XlbypVlUIwcWsqjqsO6YAE-TQFqUzaeYhSjwo4wze4caGpDvAdDxfNZOFVxWfBO_Pgkf9Lj9hxf0SJk0tVfUbfcXAUJnPWw0bavLxuFSFLz0EJSRe7zzBJbLAQvEGFQ0jWJkN4bvlPQArirXHpAiEoSXb7bgejlzf67IHJhBqnpFAYj8fGfgQ5mocZZfpLVgo8NH4tpk9xaCpH8hhZILtDpse8xN4a6q1MZBM&ui=yytAuj_c3efSrSIi1CQOo3CjzROHtxynsVIujLziilCMZZ3afVWzZWPNdyuYtzYOuzNPM99h_4xuuLMfUDT6n5cYL73NcRS2oikebNLrD9B2dzKtS9icSjlVvvXd1Zgg&si=1&oref=a3330799f2d8709c40a7b20bd5df5482&rb=2Vb288azLYM&rb=0 | US | — | — | malicious |
3148 | iexplore.exe | GET | 302 | 140.82.32.36:80 | http://www.microsoft.com-repair-windows.live/tonic2/?campid=6eb1faf6-de75-4354-9c92-8497c0008423&model=Desktop&os=Windows%207&city=Amsterdam&zn=357627343&sc=090fd18d-e753-47df-9bb5-c2bb855eabc0&ip=85.203.44.11&ua=Mozilla%2F4.0%20%28compatible%3B%20MSIE%208.0%3B%20Windows%20NT%206.1%3B%20Trident%2F4.0%3B%20SLCC2%3B%20.NET%20CLR%202.0.50727%3B%20.NET%20CLR%203.5.30729%3B%20.NET%20CLR%203.0.30729%3B%20Media%20Center%20PC%206.0%3B%20.NET4.0C%3B%20.NET4.0E%29&browser=Internet%20Explorer&browserversion=Internet%20Explorer%208&lang=en&connection=BROADBAND&isp=Falco%20Networks%20B.V.&carrier=&cep=_l__JcS7BJGXPbQb8hbS0bk1FoyG-ng6c6k21iUllvwDuPyEwVwwMffeAReauWGDFEwnNvEmhiCkA3F6ZCKCktviU6TpTRmqwLm7cGsTXCQypMZ-v1bxgIN2TucUeIktxOKCCWTZIrgNr_JCxOKKghDdPHLz6W8TZbu8bFbHQk1dfa_QprCX08eEP7G1s4Z_23mO1nBvtXmCipO51iyxXiw3hK1fqPFKEgioFinFjEdopH-4-H7sx8JN5NJcEHUGSuy5u5ofvUADvVLc8tXNhfw4VmdKHtWyGemuyYjE141YIWcUvh-1zVuHIBCr47aKqxCQY6-c1r3KtqA9aoD2ZpumWqTRCpmWhqip4lYhARhOV97pBzp8_GnFU-CVLRgnSBUoldIKcUPh_fNHX08MJDG6EAvBaPxonfa546LeNqVdd2t9qkPVhDnC8k7M56hm7sSCyz3DOGXzFVKB5EKHXacjQJDg0ixhaU1MrCNkTZrISlTABX_9pTr13LAQwvvA15RjvABwQZvt3diW3EzrX_7aKNLDncpPFDIDejVULbk&source=357627343&keyword=ericsoon.com%20KW%20%20Wireless%20ericsoon.com%20Mobile%20Phones%20Mobile%20Apps%20&%20Add-Ons%20Internet%20%20Telecom%20Mobile%20&%20Wireless%20Accessories%20Mobile%20ericsson.com&geo=NL&campaignname=Global%20-%20WINTONIC%2010%20C&device=Computer&bid=0.0007&clickid=357627343069101536386 | US | — | — | whitelisted |
3148 | iexplore.exe | GET | 302 | 18.184.38.55:80 | http://tracking.marketing/bfa3dd87-cad5-454b-abdf-56fda85b6d57?sc=090fd18d-e753-47df-9bb5-c2bb855eabc0&zn=357627343&campid=6eb1faf6-de75-4354-9c92-8497c0008423 | US | — | — | shared |
3060 | wtc.exe | GET | 200 | 93.184.220.29:80 | http://crl3.digicert.com/sha2-ev-server-g1.crl | US | binary | 85.3 Kb | whitelisted |
3148 | iexplore.exe | GET | 200 | 93.184.221.240:80 | http://www.download.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab | US | compressed | 55.2 Kb | whitelisted |
3060 | wtc.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTfqhLjKLEJQZPin0KCzkdAQpVYowQUsT7DaQP4v0cB1JgmGggC72NkK8MCEAx5qUSwjBGVIJJhX%2BJrHYM%3D | US | der | 471 b | whitelisted |
3060 | wtc.exe | POST | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/ | US | html | 46 b | whitelisted |
3060 | wtc.exe | GET | — | 216.245.208.194:80 | http://www.winactiv.com/getip/ | US | — | — | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3148 | iexplore.exe | 72.52.179.174:80 | ericsoon.com | Liquid Web, L.L.C | US | malicious |
2852 | iexplore.exe | 204.79.197.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
3148 | iexplore.exe | 108.168.193.189:80 | mybestmv.com | SoftLayer Technologies Inc. | US | suspicious |
3148 | iexplore.exe | 18.195.174.160:443 | tracking.marketing | Amazon.com, Inc. | DE | malicious |
3148 | iexplore.exe | 140.82.32.36:80 | www.microsoft.com-repair-windows.live | — | US | suspicious |
3148 | iexplore.exe | 18.184.38.55:80 | tracking.marketing | — | US | shared |
3148 | iexplore.exe | 18.195.174.160:80 | tracking.marketing | Amazon.com, Inc. | DE | malicious |
3148 | iexplore.exe | 93.184.221.240:80 | www.download.windowsupdate.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
3148 | iexplore.exe | 52.85.182.39:80 | x.ss2.us | Amazon.com, Inc. | US | suspicious |
3148 | iexplore.exe | 216.58.215.232:443 | ssl.google-analytics.com | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.bing.com |
| whitelisted |
ericsoon.com |
| malicious |
mybestmv.com |
| unknown |
p238000.mybestmv.com |
| malicious |
tracking.marketing |
| shared |
www.microsoft.com-repair-windows.live |
| whitelisted |
lp.pctonics.com |
| unknown |
www.download.windowsupdate.com |
| whitelisted |
img.pctonics.com |
| whitelisted |
fonts.googleapis.com |
| whitelisted |
Threats
Process | Message |
|---|---|
wtc.exe | 18-12-2018-03:00:46::GeneralSettings|LoadProxySettings|oProxy|null
|
wtc.exe | 18-12-2018-03:00:46::SetCountryCodeAndPhoneFromWeb| country code from web nl
|
wtc.exe | 18-12-2018-03:00:46::GeneralSettings|LoadProxySettings|oProxy|null
|