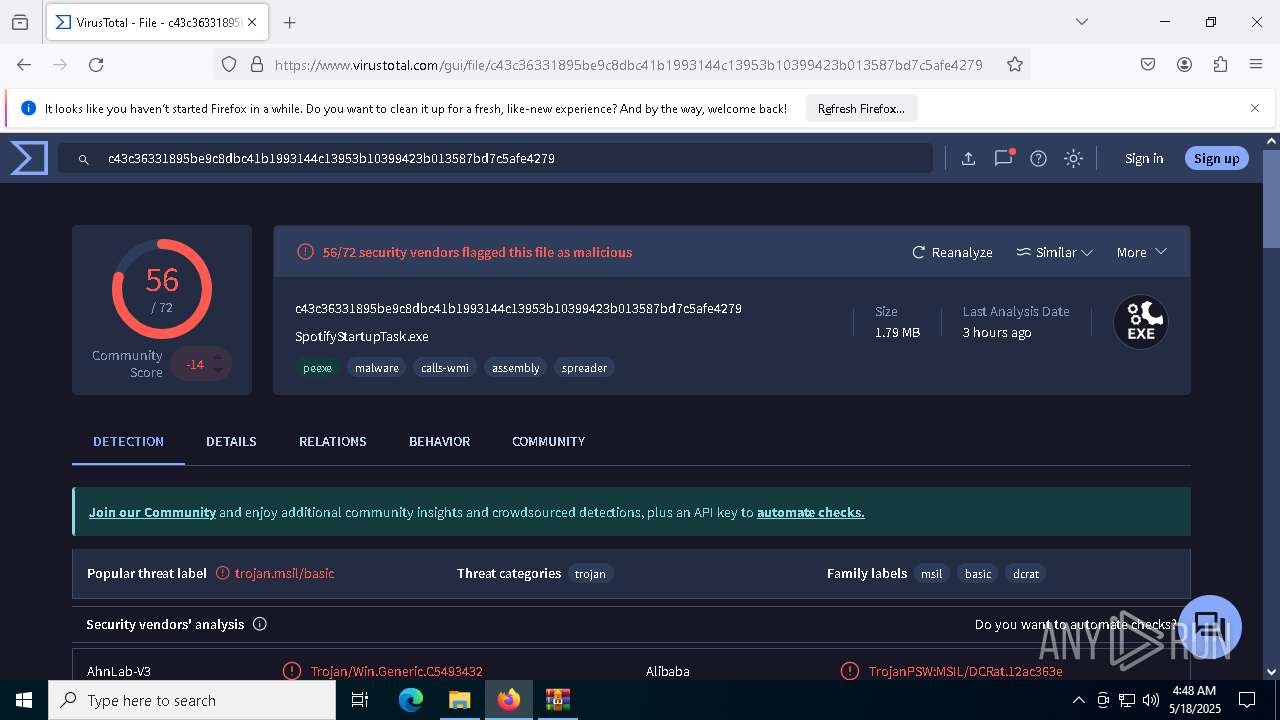
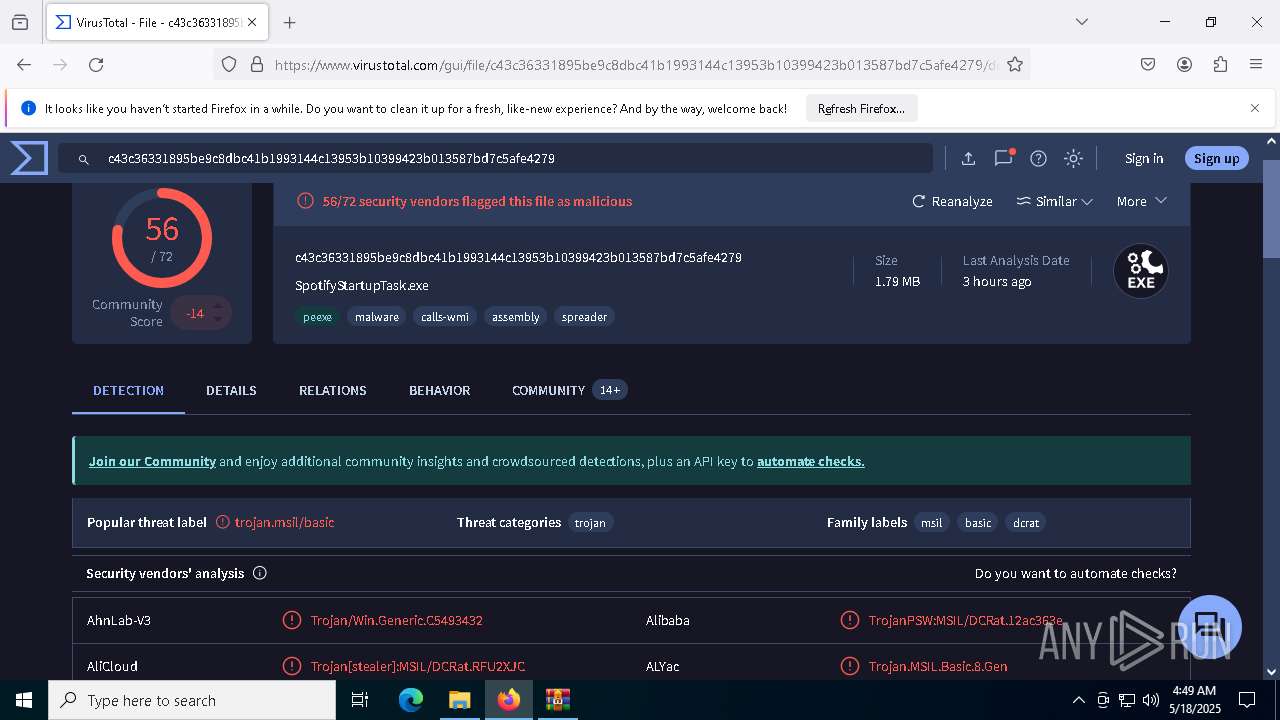
| File name: | c43c36331895be9c8dbc41b1993144c13953b10399423b013587bd7c5afe4279.zip |
| Full analysis: | https://app.any.run/tasks/858cc421-2800-4c1a-87c6-0899b202cd06 |
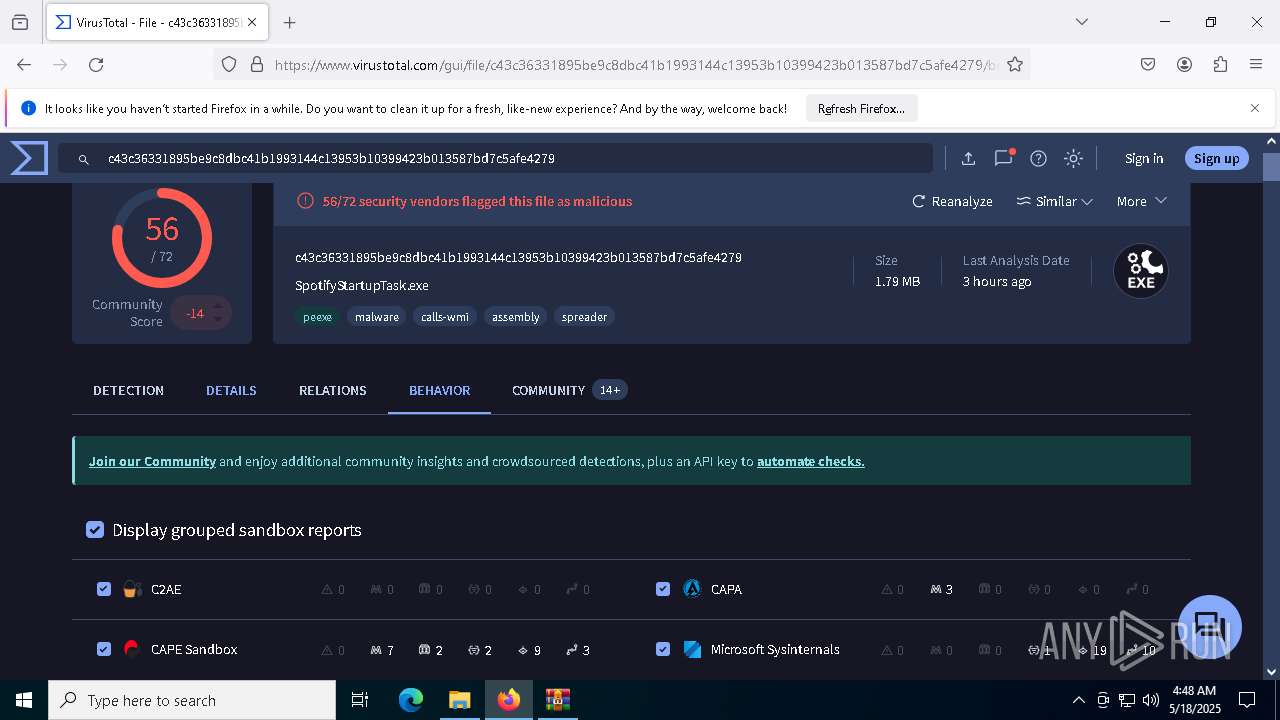
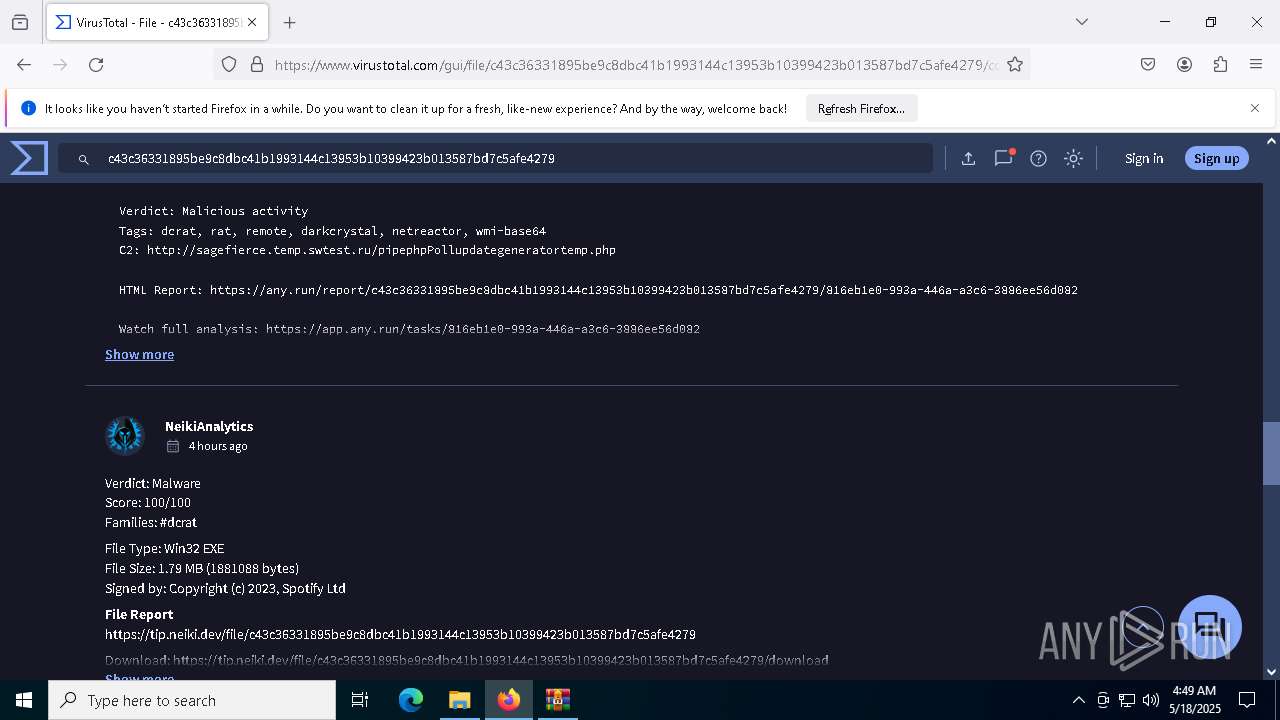
| Verdict: | Malicious activity |
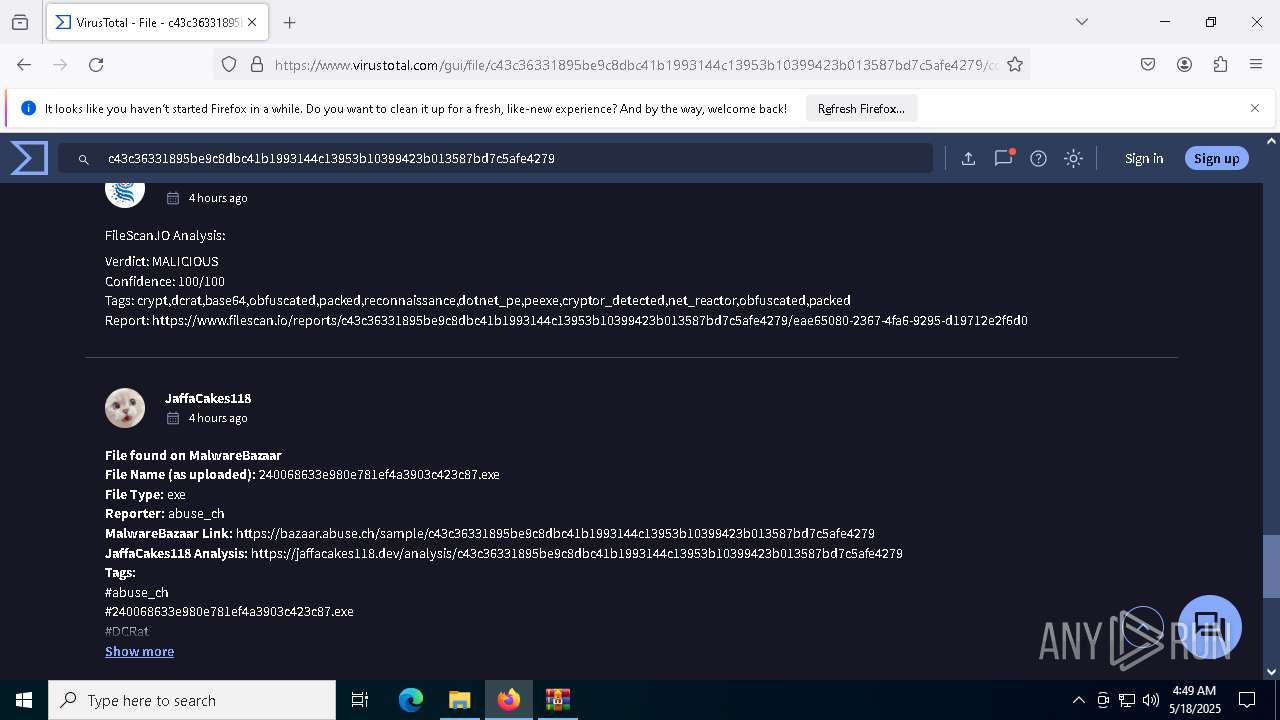
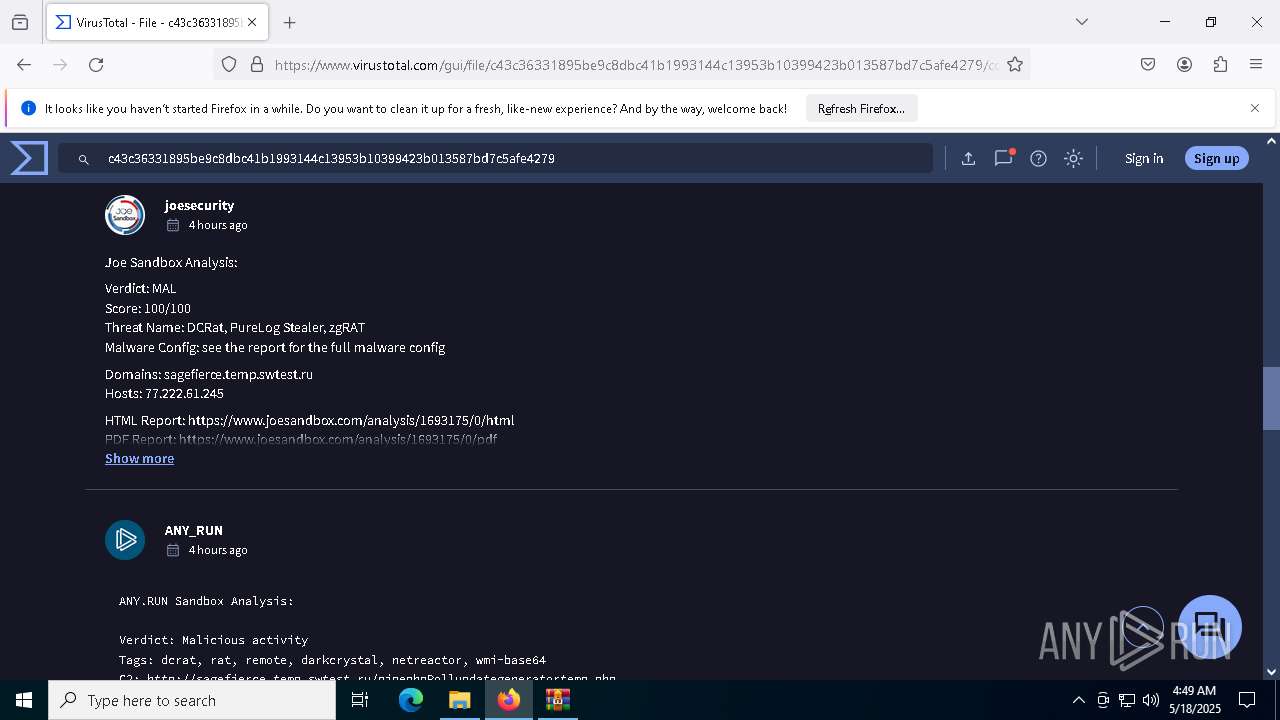
| Threats: | DCrat, also known as Dark Crystal RAT, is a remote access trojan (RAT), which was first introduced in 2018. It is a modular malware that can be customized to perform different tasks. For instance, it can steal passwords, crypto wallet information, hijack Telegram and Steam accounts, and more. Attackers may use a variety of methods to distribute DCrat, but phishing email campaigns are the most common. |
| Analysis date: | May 18, 2025, 04:44:30 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
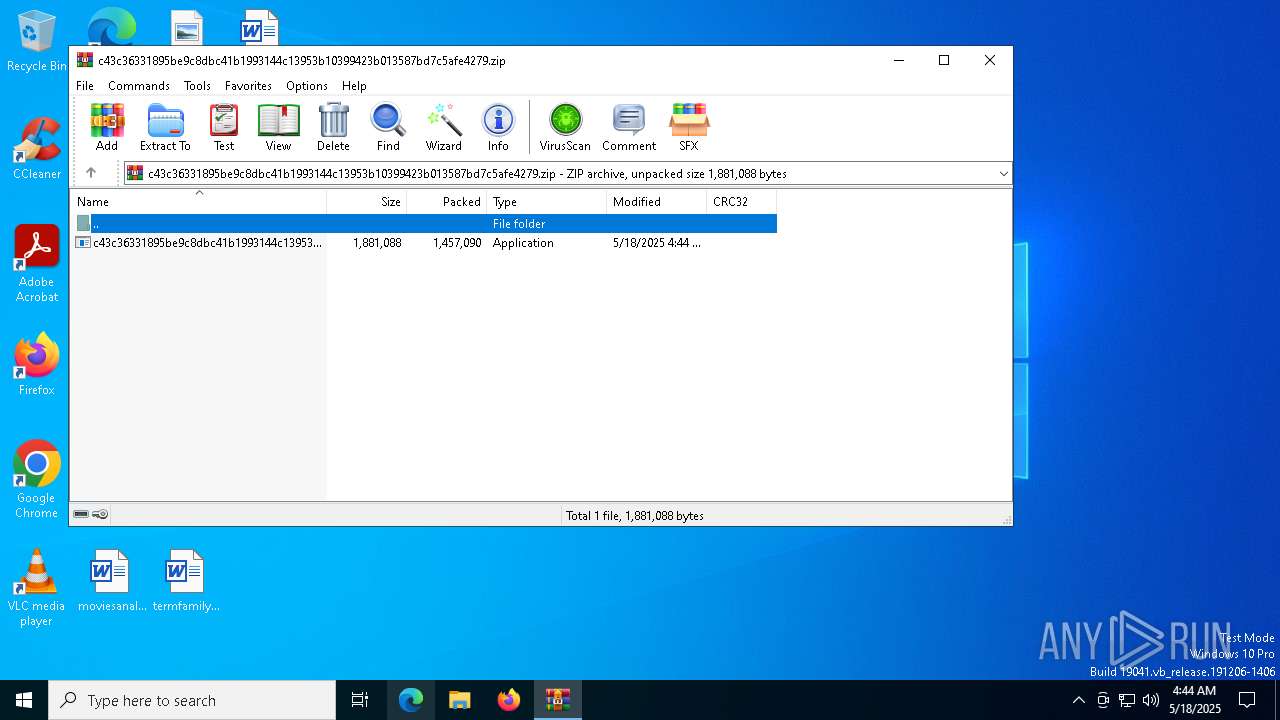
| File info: | Zip archive data, at least v5.1 to extract, compression method=AES Encrypted |
| MD5: | C207D76B4ABA6E209D22B91B3E612FEF |
| SHA1: | 415B856725C1222DECEF00195A14C78AA8A1E6B1 |
| SHA256: | B8A356BE3DD2A723443CDFB09EB53AE3998FD6FAFF9781B085DFC120931C3EDF |
| SSDEEP: | 49152:Z57SSrLSEusdzf1p74SIMv/ibsHxq0KV4dVml+YCeqp+/OvlsVLCf6latPS03oG8:Z573rmAdp74SD/ioHxXKV4ElCtVsUtP+ |
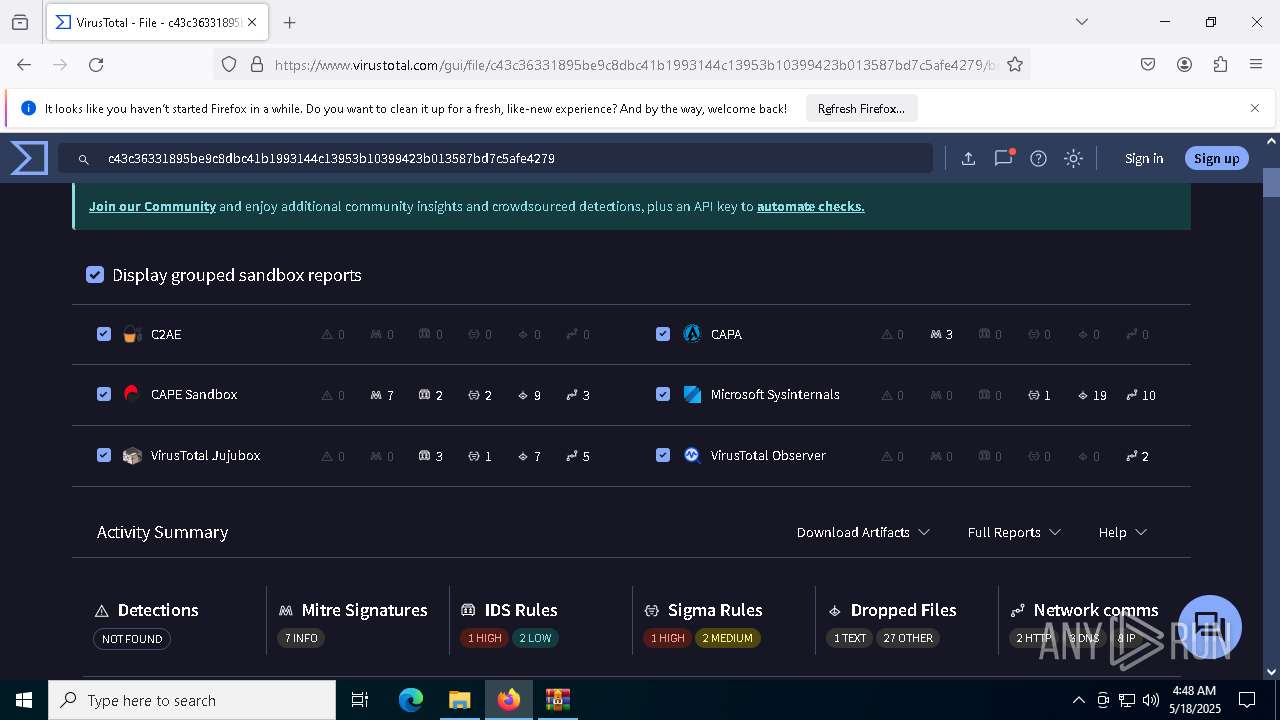
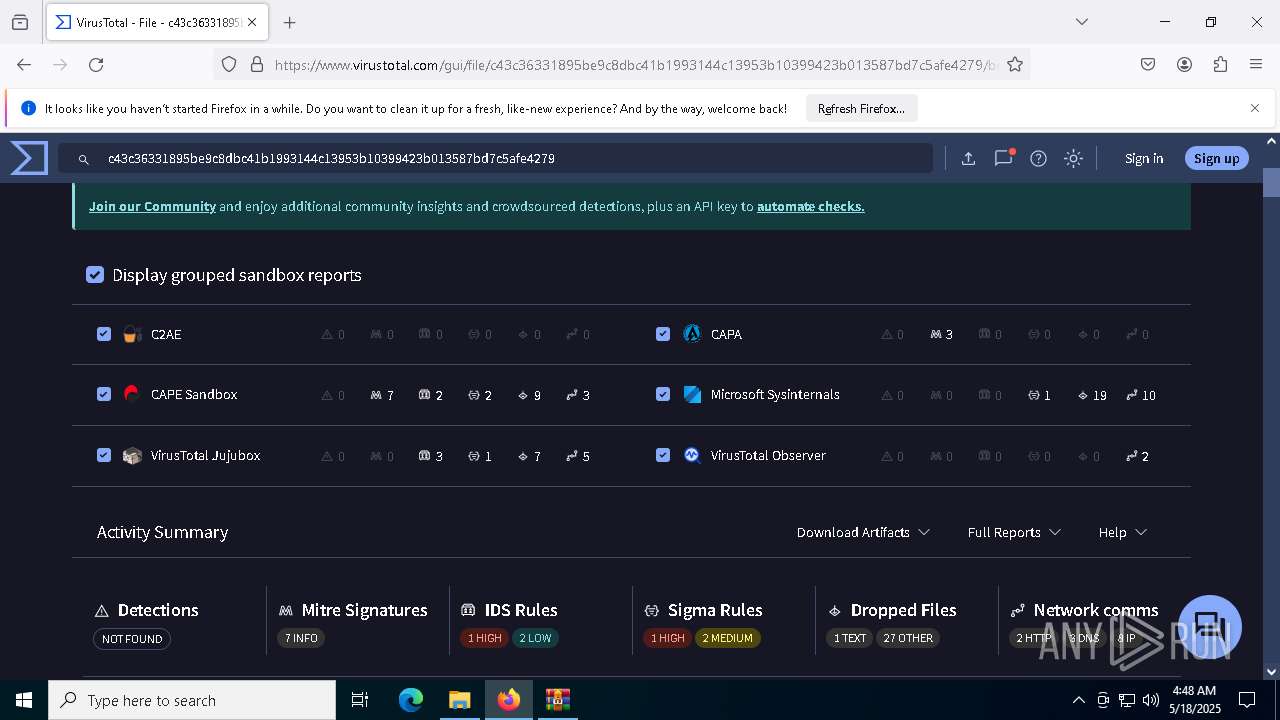
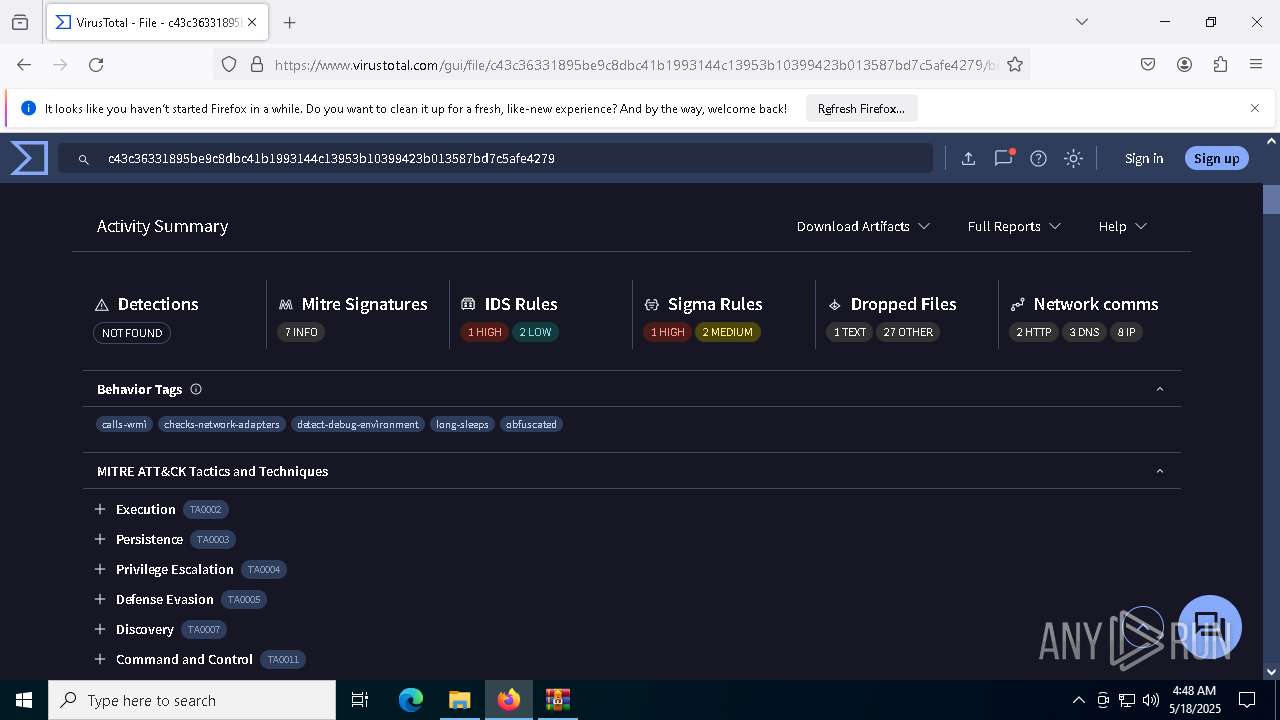
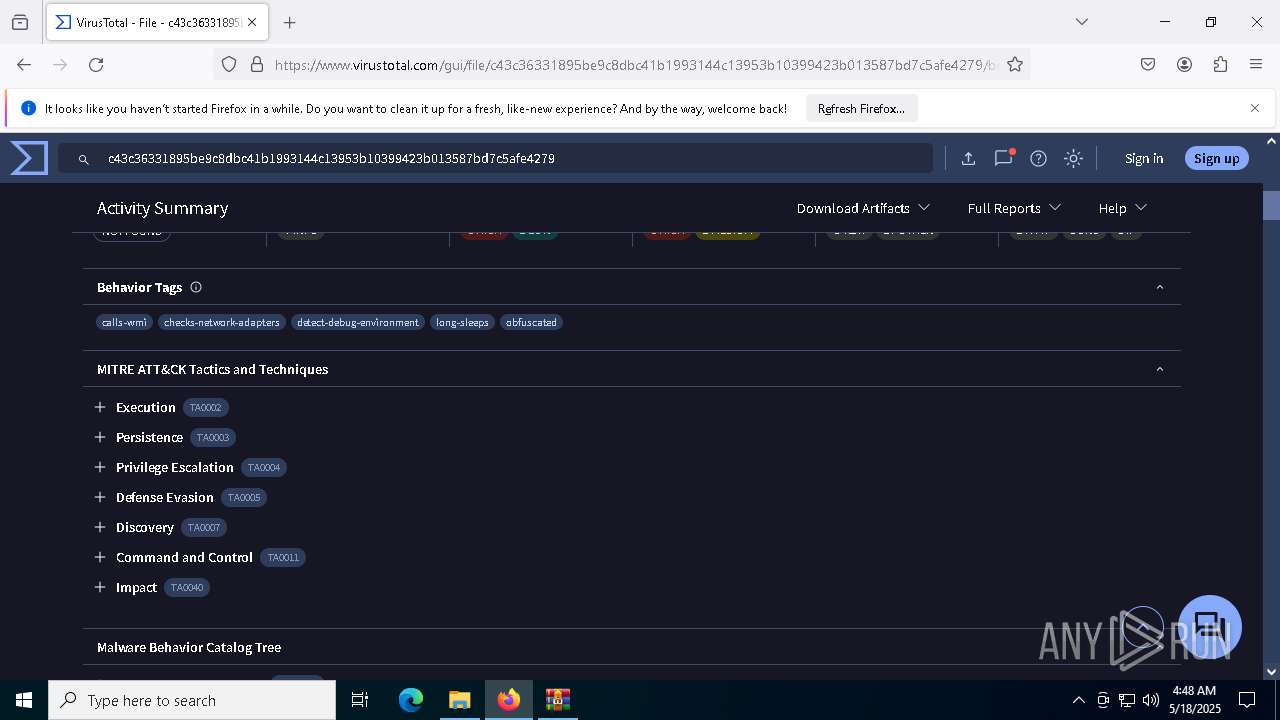
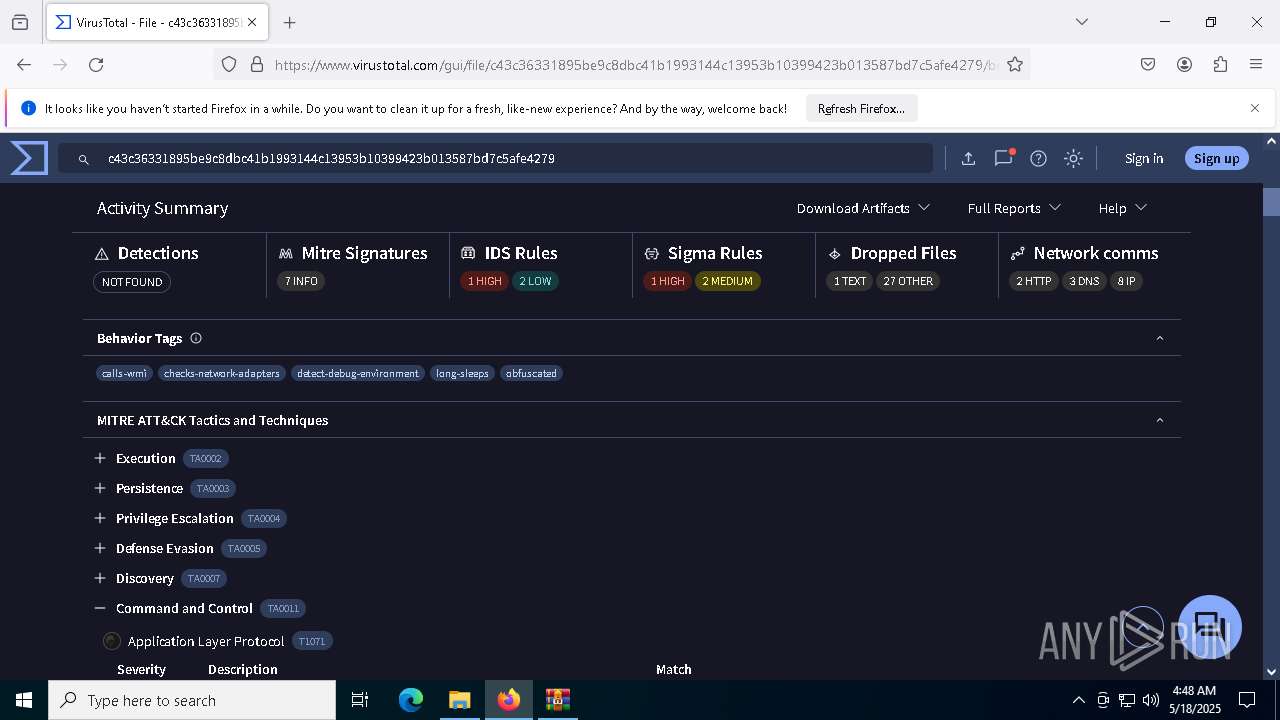
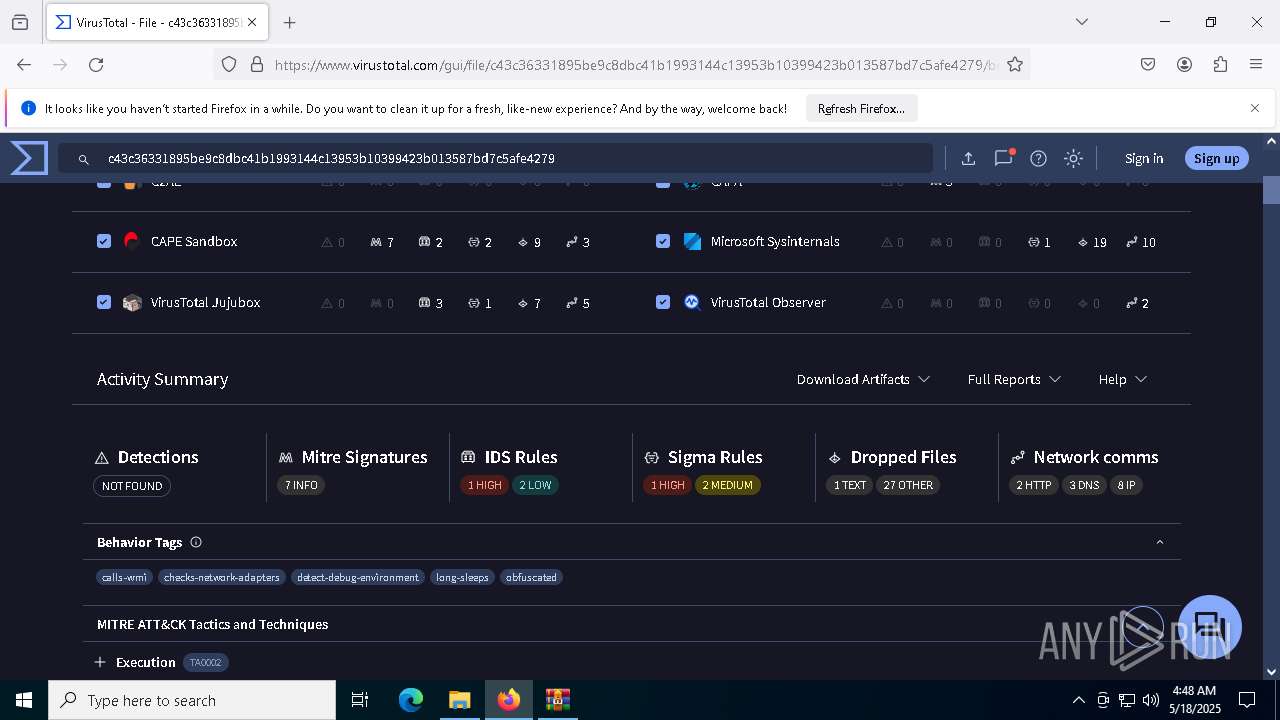
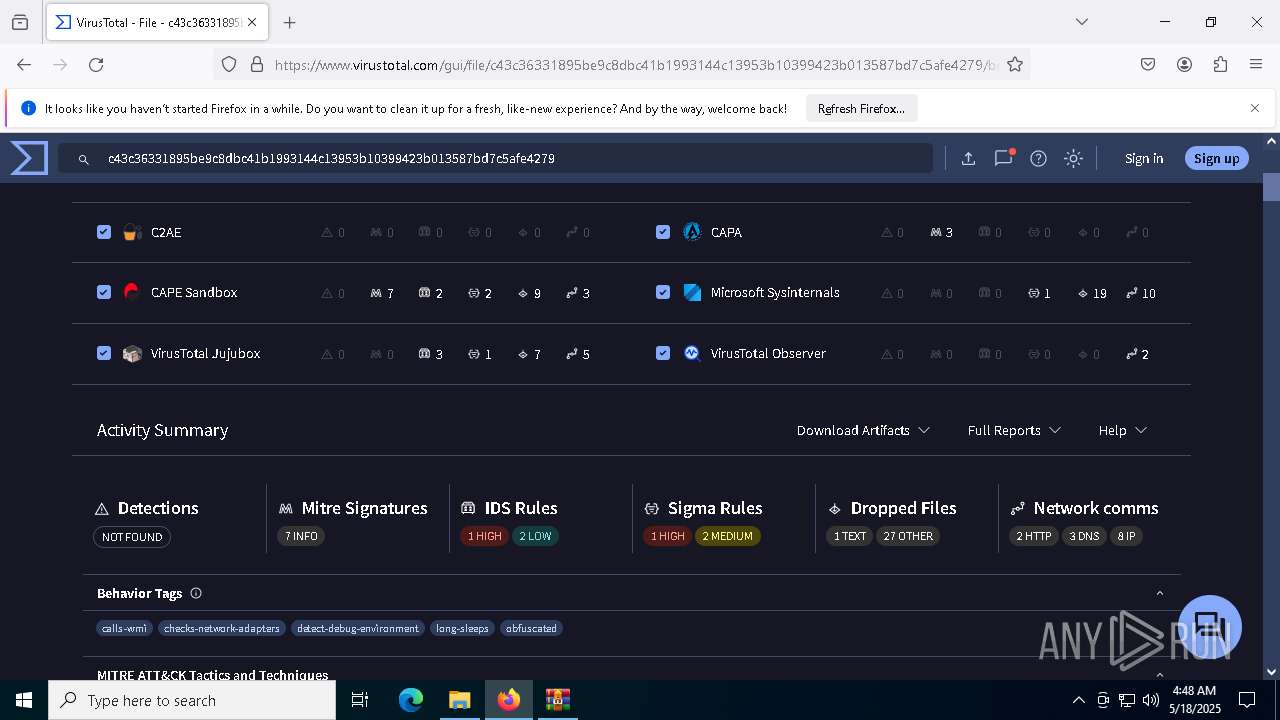
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 6800)
DCRAT mutex has been found
- winlogon.exe (PID: 7888)
- c43c36331895be9c8dbc41b1993144c13953b10399423b013587bd7c5afe4279.exe (PID: 7648)
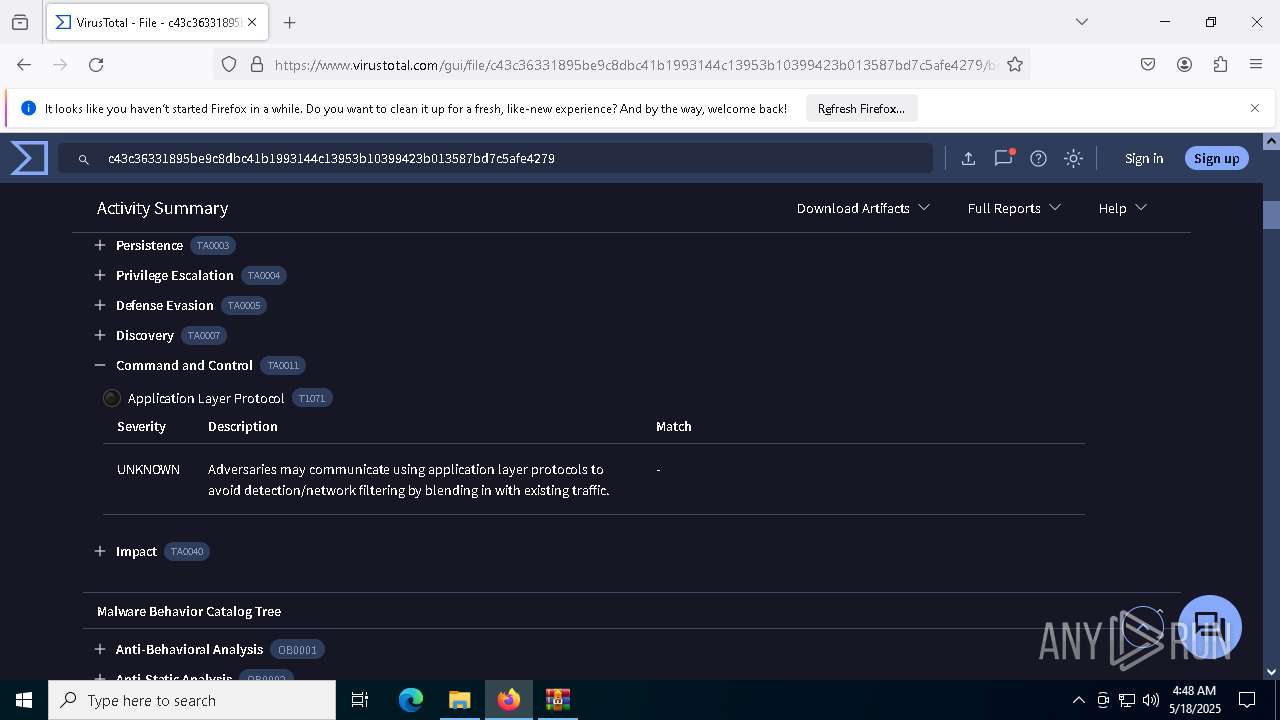
DARKCRYSTAL has been detected (SURICATA)
- winlogon.exe (PID: 7888)
Connects to the CnC server
- winlogon.exe (PID: 7888)
DCRAT has been detected (YARA)
- winlogon.exe (PID: 7888)
SUSPICIOUS
The process creates files with name similar to system file names
- c43c36331895be9c8dbc41b1993144c13953b10399423b013587bd7c5afe4279.exe (PID: 7648)
Starts CMD.EXE for commands execution
- c43c36331895be9c8dbc41b1993144c13953b10399423b013587bd7c5afe4279.exe (PID: 7648)
Reads security settings of Internet Explorer
- c43c36331895be9c8dbc41b1993144c13953b10399423b013587bd7c5afe4279.exe (PID: 7648)
Executing commands from a ".bat" file
- c43c36331895be9c8dbc41b1993144c13953b10399423b013587bd7c5afe4279.exe (PID: 7648)
Starts application with an unusual extension
- cmd.exe (PID: 7724)
Reads the date of Windows installation
- c43c36331895be9c8dbc41b1993144c13953b10399423b013587bd7c5afe4279.exe (PID: 7648)
Probably delay the execution using 'w32tm.exe'
- cmd.exe (PID: 7724)
The executable file from the user directory is run by the CMD process
- winlogon.exe (PID: 7888)
Executable content was dropped or overwritten
- winlogon.exe (PID: 7888)
- c43c36331895be9c8dbc41b1993144c13953b10399423b013587bd7c5afe4279.exe (PID: 7648)
There is functionality for taking screenshot (YARA)
- winlogon.exe (PID: 7888)
INFO
Create files in a temporary directory
- c43c36331895be9c8dbc41b1993144c13953b10399423b013587bd7c5afe4279.exe (PID: 7648)
Process checks computer location settings
- c43c36331895be9c8dbc41b1993144c13953b10399423b013587bd7c5afe4279.exe (PID: 7648)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 6800)
Checks supported languages
- c43c36331895be9c8dbc41b1993144c13953b10399423b013587bd7c5afe4279.exe (PID: 7648)
- chcp.com (PID: 7780)
- winlogon.exe (PID: 7888)
Manual execution by a user
- c43c36331895be9c8dbc41b1993144c13953b10399423b013587bd7c5afe4279.exe (PID: 7648)
- firefox.exe (PID: 3100)
Reads Environment values
- c43c36331895be9c8dbc41b1993144c13953b10399423b013587bd7c5afe4279.exe (PID: 7648)
- winlogon.exe (PID: 7888)
Changes the display of characters in the console
- cmd.exe (PID: 7724)
Reads the machine GUID from the registry
- winlogon.exe (PID: 7888)
- c43c36331895be9c8dbc41b1993144c13953b10399423b013587bd7c5afe4279.exe (PID: 7648)
Reads the computer name
- winlogon.exe (PID: 7888)
- c43c36331895be9c8dbc41b1993144c13953b10399423b013587bd7c5afe4279.exe (PID: 7648)
Disables trace logs
- winlogon.exe (PID: 7888)
Checks proxy server information
- winlogon.exe (PID: 7888)
- slui.exe (PID: 8172)
.NET Reactor protector has been detected
- winlogon.exe (PID: 7888)
Found Base64 encoded reference to WMI classes (YARA)
- winlogon.exe (PID: 7888)
Reads the software policy settings
- slui.exe (PID: 7224)
- slui.exe (PID: 8172)
Application launched itself
- firefox.exe (PID: 3100)
- firefox.exe (PID: 6744)
Failed to create an executable file in Windows directory
- c43c36331895be9c8dbc41b1993144c13953b10399423b013587bd7c5afe4279.exe (PID: 7648)
Creates files in the program directory
- c43c36331895be9c8dbc41b1993144c13953b10399423b013587bd7c5afe4279.exe (PID: 7648)
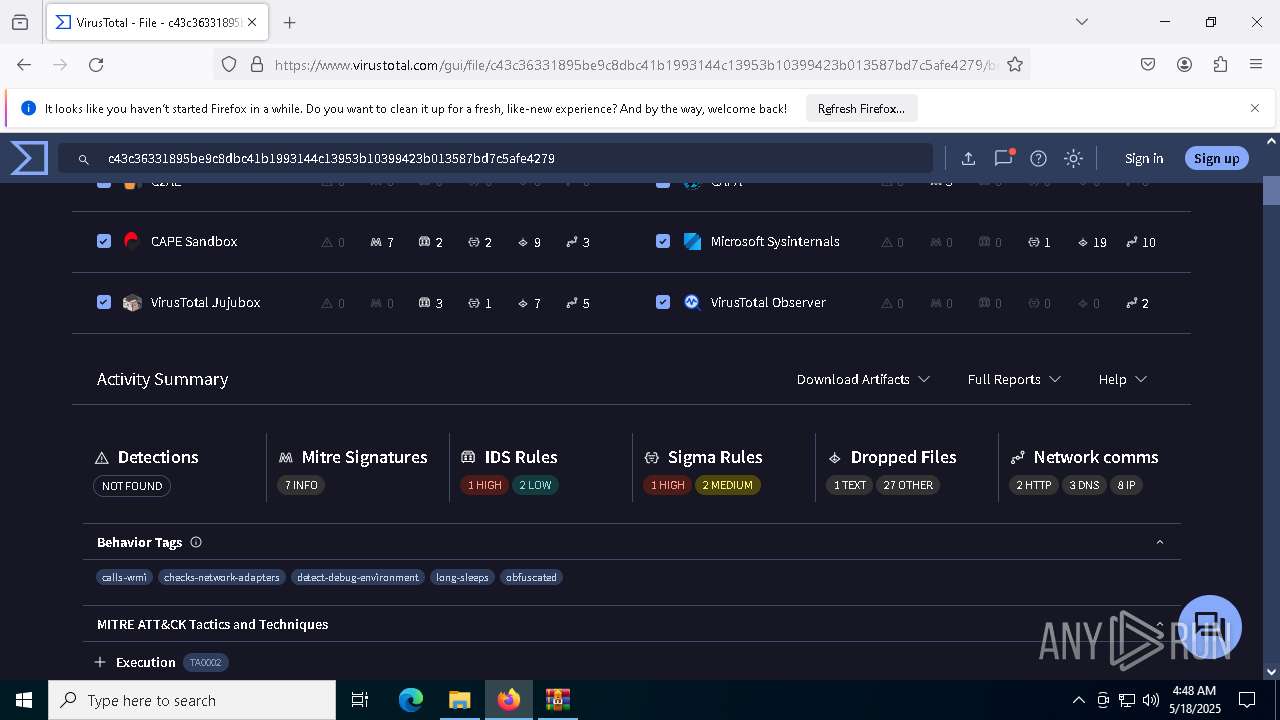
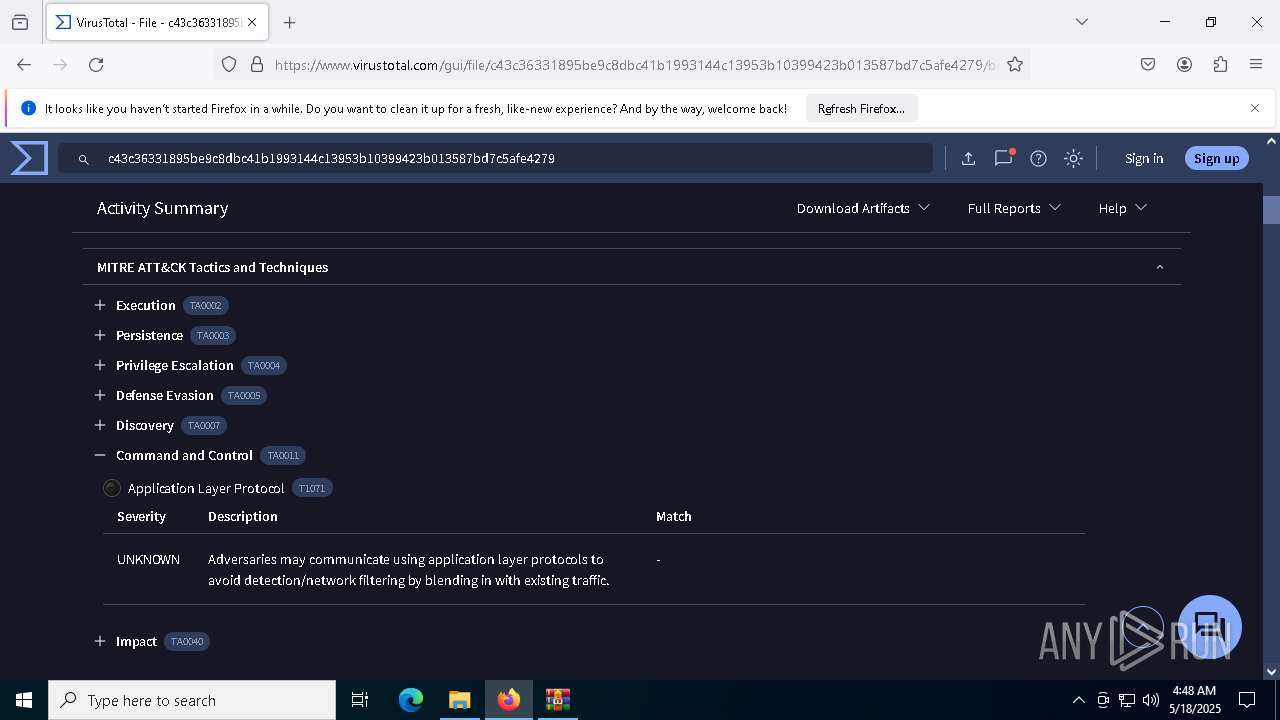
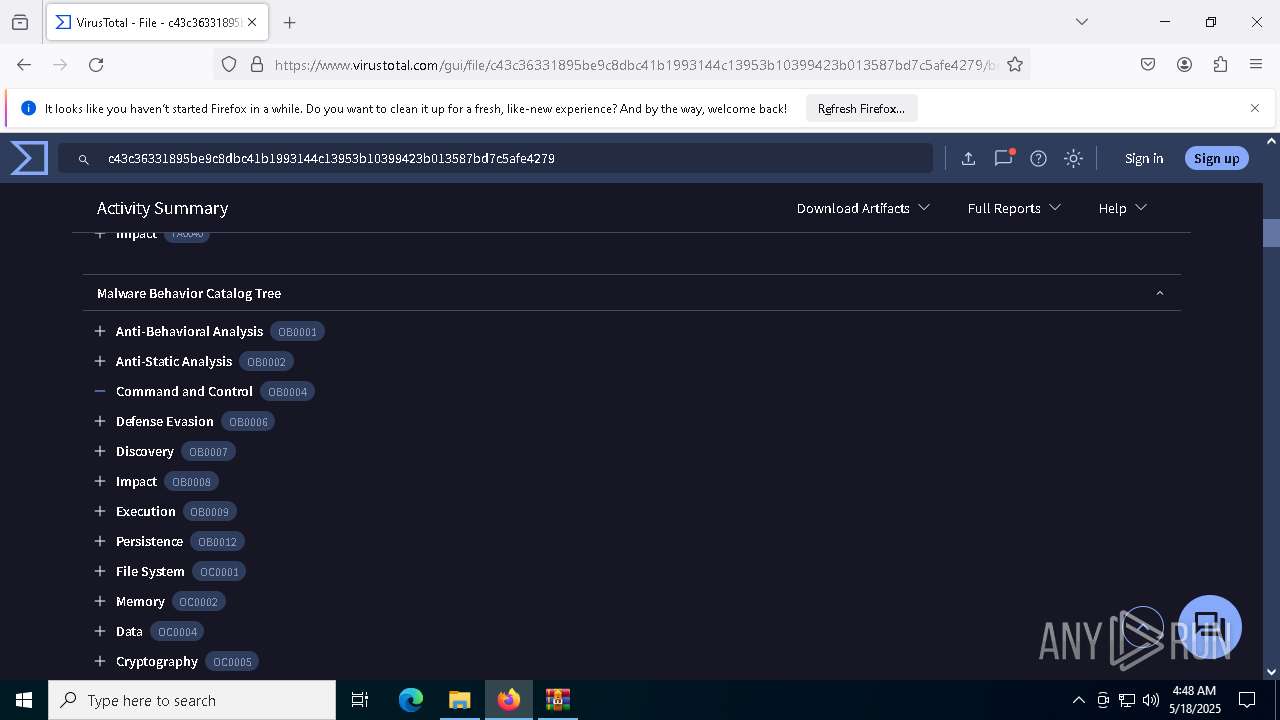
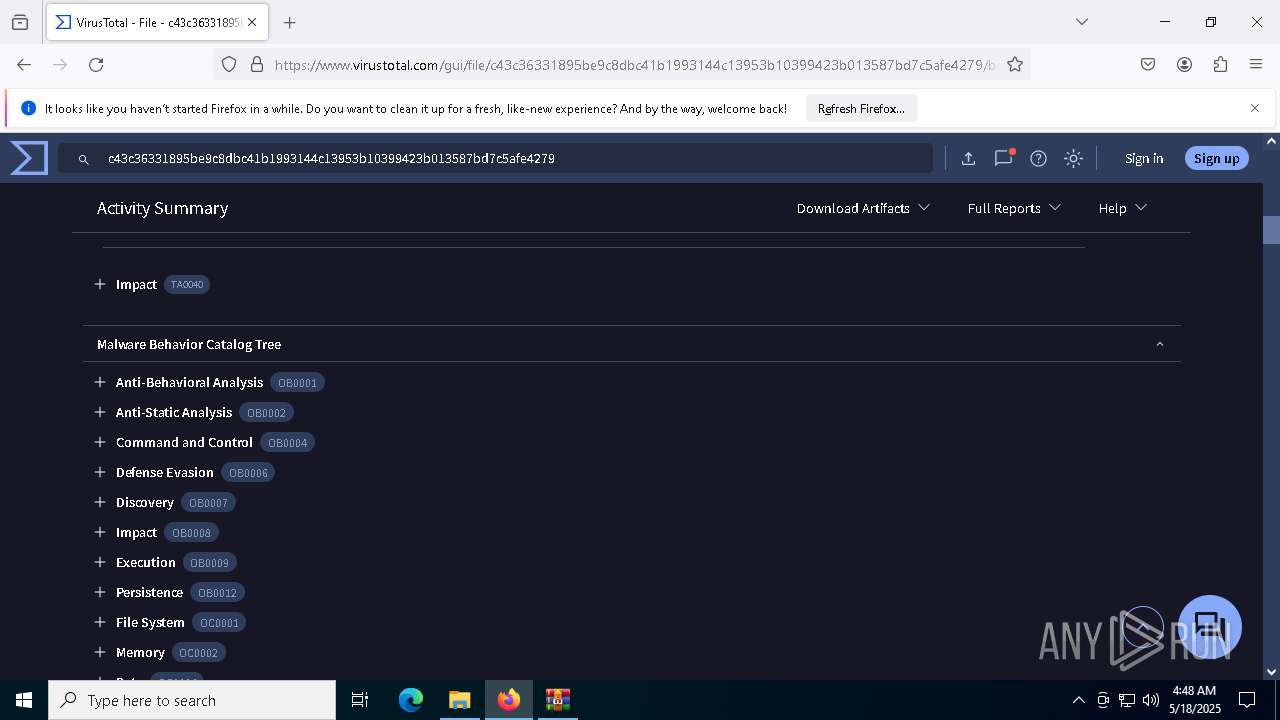
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
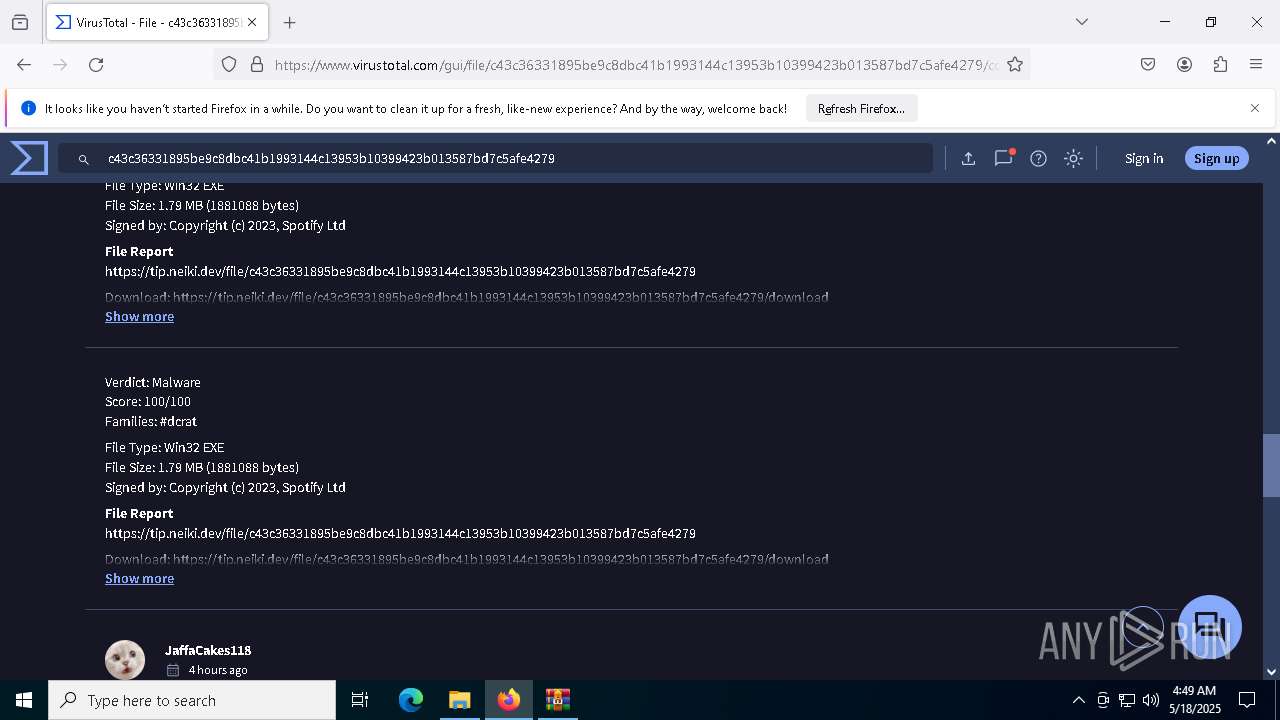
DcRat
(PID) Process(7888) winlogon.exe
C2 (1)http://sagefierce.temp.swtest.ru/pipephpPollupdategeneratortemp.php
Options
Version5.0.1
C2 (1)http://sagefierce.temp.swtest.ru/pipephpPollupdategeneratortemp.php
Options
Version5.0.1
Plugins (2)TVqQAAMAAAAEAAAA//8AALgAAAAAAAAAQAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAgAAAAA4fug4AtAnNIbgBTM0hVGhpcyBwcm9ncmFtIGNhbm5vdCBiZSBydW4gaW4gRE9TIG1vZGUuDQ0KJAAAAAAAAABQRQAATAEDALI7+mQAAAAAAAAAAOAAIiALAQgAAAgBAAAGAAAAAAAAricBAAAgAAAAQAEAAABAAAAgAAAAAgAABAAAAAAAAAAEAAAAAAAAAACAAQAAAgAArNABAAMAQIUA...
TVqQAAMAAAAEAAAA//8AALgAAAAAAAAAQAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAgAAAAA4fug4AtAnNIbgBTM0hVGhpcyBwcm9ncmFtIGNhbm5vdCBiZSBydW4gaW4gRE9TIG1vZGUuDQ0KJAAAAAAAAABQRQAATAEDAAKX/2QAAAAAAAAAAOAAIiALAQgAAEYBAAAGAAAAAAAA7mUBAAAgAAAAgAEAAABAAAAgAAAAAgAABAAAAAAAAAAEAAAAAAAAAADAAQAAAgAAm0ACAAMAQIUA...
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 51 |
|---|---|
| ZipBitFlag: | 0x0003 |
| ZipCompression: | Unknown (99) |
| ZipModifyDate: | 2025:05:18 04:44:24 |
| ZipCRC: | 0x2ef19503 |
| ZipCompressedSize: | 1457090 |
| ZipUncompressedSize: | 1881088 |
| ZipFileName: | c43c36331895be9c8dbc41b1993144c13953b10399423b013587bd7c5afe4279.exe |
Total processes
155
Monitored processes
25
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2096 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=2156 -parentBuildID 20240213221259 -prefsHandle 2144 -prefMapHandle 2132 -prefsLen 31031 -prefMapSize 244583 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {769982de-d8c4-41ff-8887-fc016c6b9566} 6744 "\\.\pipe\gecko-crash-server-pipe.6744" 111a0f81310 socket | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Version: 123.0 Modules
| |||||||||||||||
| 2196 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2392 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=1912 -parentBuildID 20240213221259 -prefsHandle 1840 -prefMapHandle 1832 -prefsLen 31031 -prefMapSize 244583 -appDir "C:\Program Files\Mozilla Firefox\browser" - {4fd639f9-d264-49e9-825c-59577e1307e2} 6744 "\\.\pipe\gecko-crash-server-pipe.6744" 111addeb710 gpu | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Version: 123.0 Modules
| |||||||||||||||
| 2432 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=4996 -childID 3 -isForBrowser -prefsHandle 4988 -prefMapHandle 4984 -prefsLen 31243 -prefMapSize 244583 -jsInitHandle 1544 -jsInitLen 235124 -parentBuildID 20240213221259 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {64f1a78e-dd8b-4010-aed6-a3f5433d8483} 6744 "\\.\pipe\gecko-crash-server-pipe.6744" 111b5c66850 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Version: 123.0 Modules
| |||||||||||||||
| 2984 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=4292 -childID 2 -isForBrowser -prefsHandle 4284 -prefMapHandle 4280 -prefsLen 36588 -prefMapSize 244583 -jsInitHandle 1544 -jsInitLen 235124 -parentBuildID 20240213221259 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {b85c4fcf-610f-41ee-bdcc-d798f1bc39eb} 6744 "\\.\pipe\gecko-crash-server-pipe.6744" 111b511b4d0 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Version: 123.0 Modules
| |||||||||||||||
| 3100 | "C:\Program Files\Mozilla Firefox\firefox.exe" | C:\Program Files\Mozilla Firefox\firefox.exe | — | explorer.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 0 Version: 123.0 Modules
| |||||||||||||||
| 5324 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=5756 -childID 6 -isForBrowser -prefsHandle 5928 -prefMapHandle 5900 -prefsLen 31324 -prefMapSize 244583 -jsInitHandle 1544 -jsInitLen 235124 -parentBuildID 20240213221259 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {364608ac-27ba-4076-9c53-afe8d703d640} 6744 "\\.\pipe\gecko-crash-server-pipe.6744" 111b5f31310 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Version: 123.0 Modules
| |||||||||||||||
| 6468 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=4924 -parentBuildID 20240213221259 -sandboxingKind 0 -prefsHandle 4772 -prefMapHandle 4908 -prefsLen 38183 -prefMapSize 244583 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {55323cf7-3453-4597-8bdb-5da5fea992b1} 6744 "\\.\pipe\gecko-crash-server-pipe.6744" 111b6a4a510 utility | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Version: 123.0 Modules
| |||||||||||||||
| 6724 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=4100 -childID 8 -isForBrowser -prefsHandle 5976 -prefMapHandle 2288 -prefsLen 31324 -prefMapSize 244583 -jsInitHandle 1544 -jsInitLen 235124 -parentBuildID 20240213221259 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {64f21f5b-3aa6-4092-8968-64740481b46e} 6744 "\\.\pipe\gecko-crash-server-pipe.6744" 111b24ba4d0 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Version: 123.0 Modules
| |||||||||||||||
| 6744 | "C:\Program Files\Mozilla Firefox\firefox.exe" | C:\Program Files\Mozilla Firefox\firefox.exe | firefox.exe | ||||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Version: 123.0 Modules
| |||||||||||||||
Total events
25 002
Read events
24 812
Write events
170
Delete events
20
Modification events
| (PID) Process: | (6800) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (6800) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (6800) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (6800) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\c43c36331895be9c8dbc41b1993144c13953b10399423b013587bd7c5afe4279.zip | |||
| (PID) Process: | (6800) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6800) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6800) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6800) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (6800) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 15 |
Value: | |||
| (PID) Process: | (6800) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 14 |
Value: | |||
Executable files
12
Suspicious files
183
Text files
30
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6800 | WinRAR.exe | C:\Users\admin\Downloads\c43c36331895be9c8dbc41b1993144c13953b10399423b013587bd7c5afe4279.exe | executable | |
MD5:240068633E980E781EF4A3903C423C87 | SHA256:C43C36331895BE9C8DBC41B1993144C13953B10399423B013587BD7C5AFE4279 | |||
| 7648 | c43c36331895be9c8dbc41b1993144c13953b10399423b013587bd7c5afe4279.exe | C:\Users\admin\Desktop\AIwEkujz.log | executable | |
MD5:E9CE850DB4350471A62CC24ACB83E859 | SHA256:7C95D3B38114E7E4126CB63AADAF80085ED5461AB0868D2365DD6A18C946EA3A | |||
| 7648 | c43c36331895be9c8dbc41b1993144c13953b10399423b013587bd7c5afe4279.exe | C:\Users\admin\winlogon.exe | executable | |
MD5:240068633E980E781EF4A3903C423C87 | SHA256:C43C36331895BE9C8DBC41B1993144C13953B10399423B013587BD7C5AFE4279 | |||
| 6744 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\9kie7cg6.default-release\startupCache\scriptCache-current.bin | — | |
MD5:— | SHA256:— | |||
| 7648 | c43c36331895be9c8dbc41b1993144c13953b10399423b013587bd7c5afe4279.exe | C:\Users\admin\Downloads\25880f70f4f0ef | text | |
MD5:1CDCAE4A986380EAF9288940FF267C56 | SHA256:BD82020FE8C6807691E3CC72C85324E6C2659F7D2074A3C8E6BC4E069B4429EB | |||
| 7648 | c43c36331895be9c8dbc41b1993144c13953b10399423b013587bd7c5afe4279.exe | C:\Users\admin\csrss.exe | executable | |
MD5:240068633E980E781EF4A3903C423C87 | SHA256:C43C36331895BE9C8DBC41B1993144C13953B10399423B013587BD7C5AFE4279 | |||
| 7648 | c43c36331895be9c8dbc41b1993144c13953b10399423b013587bd7c5afe4279.exe | C:\Users\admin\Desktop\rfoPABUS.log | executable | |
MD5:F4B38D0F95B7E844DD288B441EBC9AAF | SHA256:AAB95596475CA74CEDE5BA50F642D92FA029F6F74F6FAEAE82A9A07285A5FB97 | |||
| 7648 | c43c36331895be9c8dbc41b1993144c13953b10399423b013587bd7c5afe4279.exe | C:\Users\admin\886983d96e3d3e | text | |
MD5:20D5712E1B88DD61AA91620B3C1D4F05 | SHA256:95970C7736A90976F19219B3CE9562AD407FC402655A4CA7C4C06EA22647E8DE | |||
| 7648 | c43c36331895be9c8dbc41b1993144c13953b10399423b013587bd7c5afe4279.exe | C:\Users\Default\Links\ee2ad38f3d4382 | text | |
MD5:75965AC2B8A7E2E716AF67CF44604EFC | SHA256:D7E4F866203DEE16E885B112176558EBC2DB347AFDAD220F77D26D912C777DB0 | |||
| 7648 | c43c36331895be9c8dbc41b1993144c13953b10399423b013587bd7c5afe4279.exe | C:\ProgramData\9e8d7a4ca61bd9 | text | |
MD5:84DCFFAF8C3972FF5F1055315E27DD61 | SHA256:F5C70837597D7ACBDDCB54DF8453F3345E83F58AC78B33E142DD9F5D00A8953E | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
189
TCP/UDP connections
139
DNS requests
143
Threats
7
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.216.77.20:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
7888 | winlogon.exe | POST | 200 | 77.222.61.245:80 | http://sagefierce.temp.swtest.ru/pipephpPollupdategeneratortemp.php | unknown | — | — | malicious |
7940 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
7888 | winlogon.exe | POST | 200 | 77.222.61.245:80 | http://sagefierce.temp.swtest.ru/pipephpPollupdategeneratortemp.php | unknown | — | — | malicious |
7888 | winlogon.exe | POST | 200 | 77.222.61.245:80 | http://sagefierce.temp.swtest.ru/pipephpPollupdategeneratortemp.php | unknown | — | — | malicious |
7940 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
7888 | winlogon.exe | POST | 200 | 77.222.61.245:80 | http://sagefierce.temp.swtest.ru/pipephpPollupdategeneratortemp.php | unknown | — | — | malicious |
7888 | winlogon.exe | POST | 200 | 77.222.61.245:80 | http://sagefierce.temp.swtest.ru/pipephpPollupdategeneratortemp.php | unknown | — | — | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2104 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 23.216.77.20:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
2112 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3216 | svchost.exe | 172.211.123.249:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 20.190.160.4:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
sagefierce.temp.swtest.ru |
| malicious |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2196 | svchost.exe | Potentially Bad Traffic | ET TA_ABUSED_SERVICES Commonly Abused Domain Service Domain in DNS Lookup (temp .swtest .ru) |
7888 | winlogon.exe | A Network Trojan was detected | REMOTE [ANY.RUN] DarkCrystal Rat Check-in (POST) |
7888 | winlogon.exe | A Network Trojan was detected | ET MALWARE [ANY.RUN] DarkCrystal Rat Check-in (POST) |
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Google Tag Manager analytics (googletagmanager .com) |
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Google Tag Manager analytics (googletagmanager .com) |
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Google Tag Manager analytics (googletagmanager .com) |
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Google Tag Manager analytics (googletagmanager .com) |