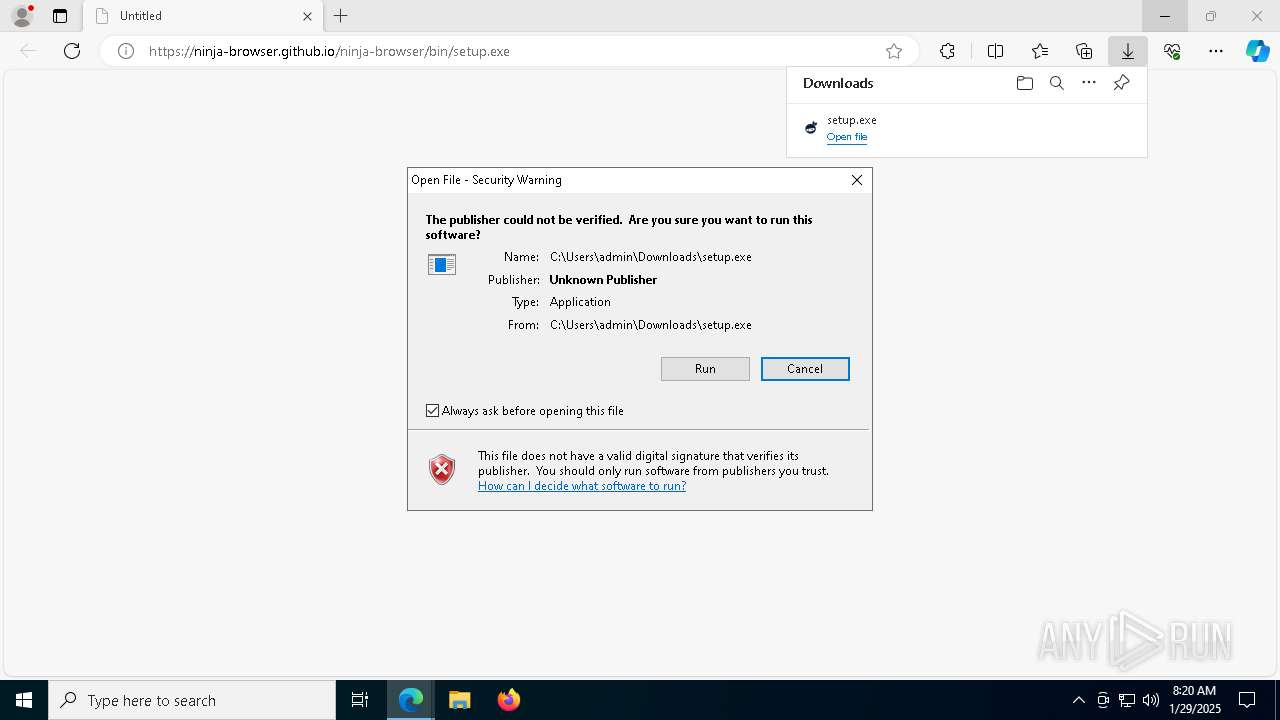
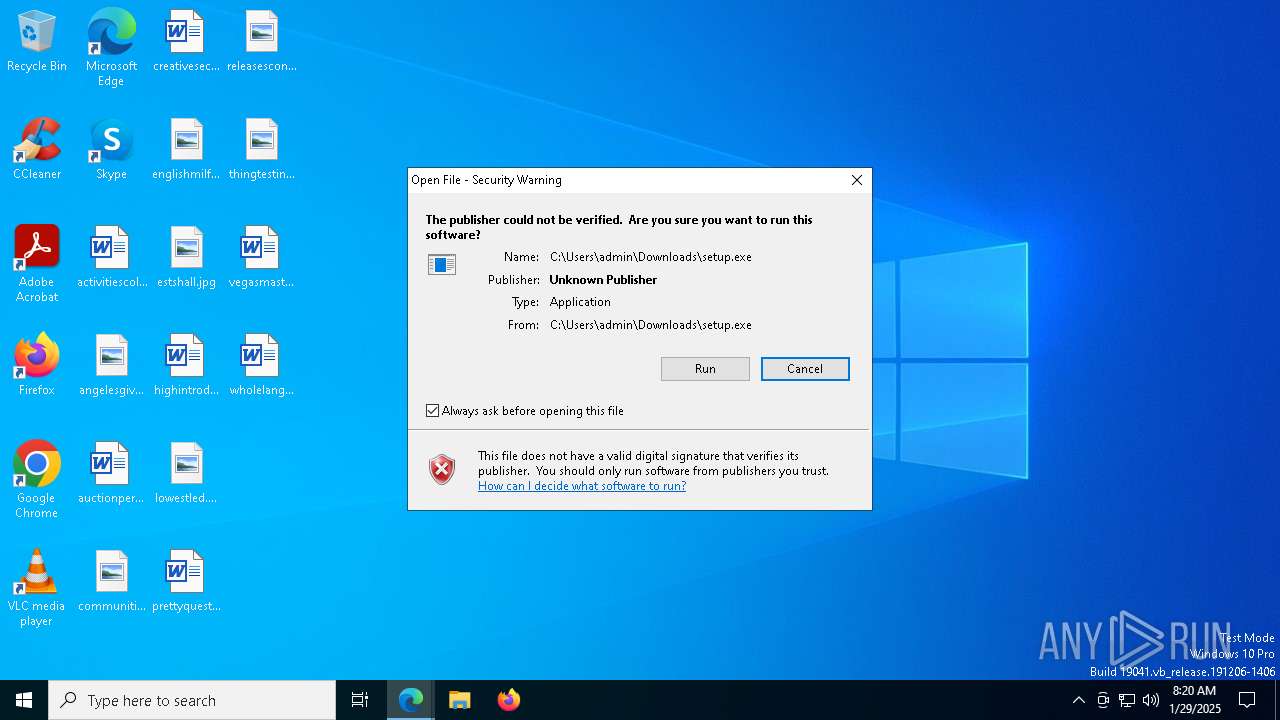
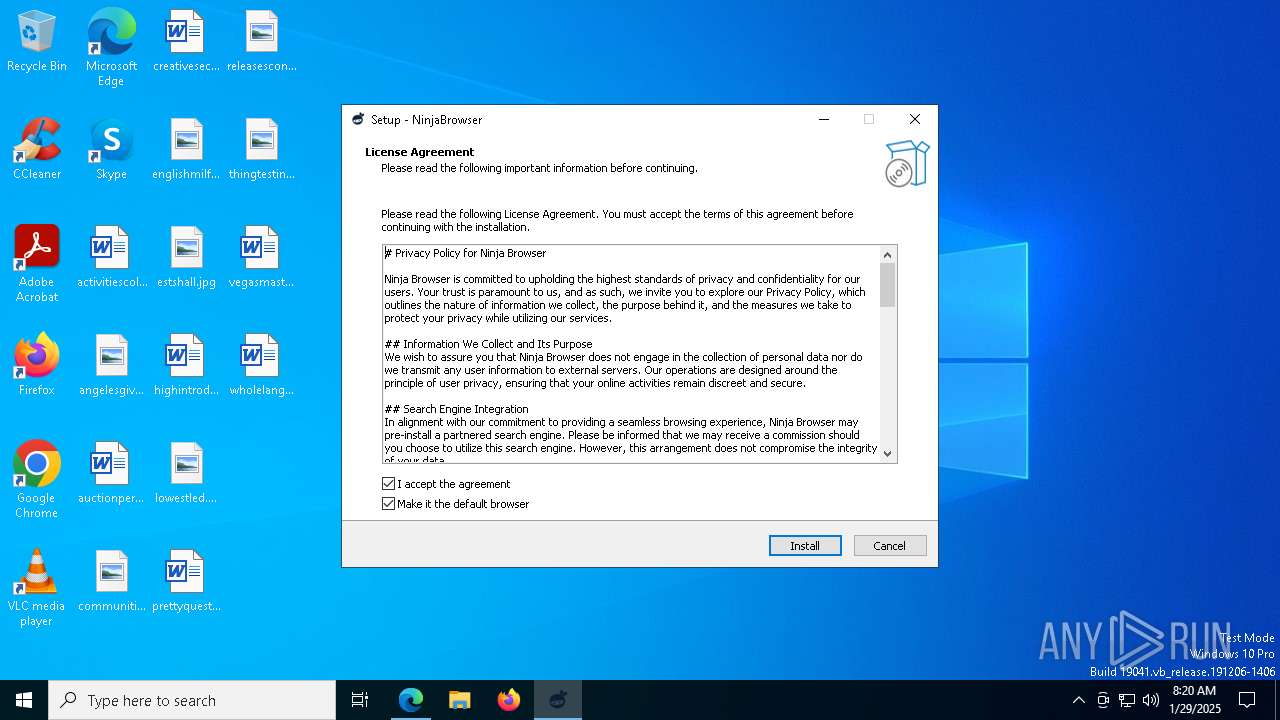
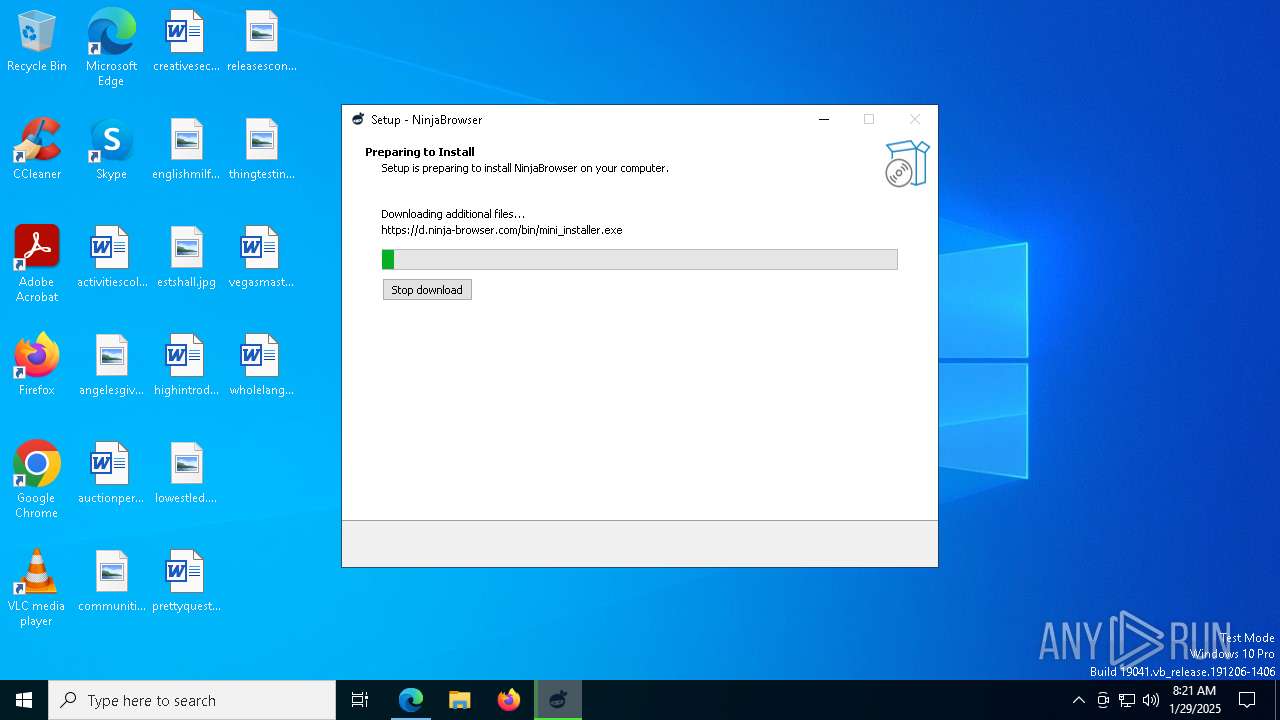
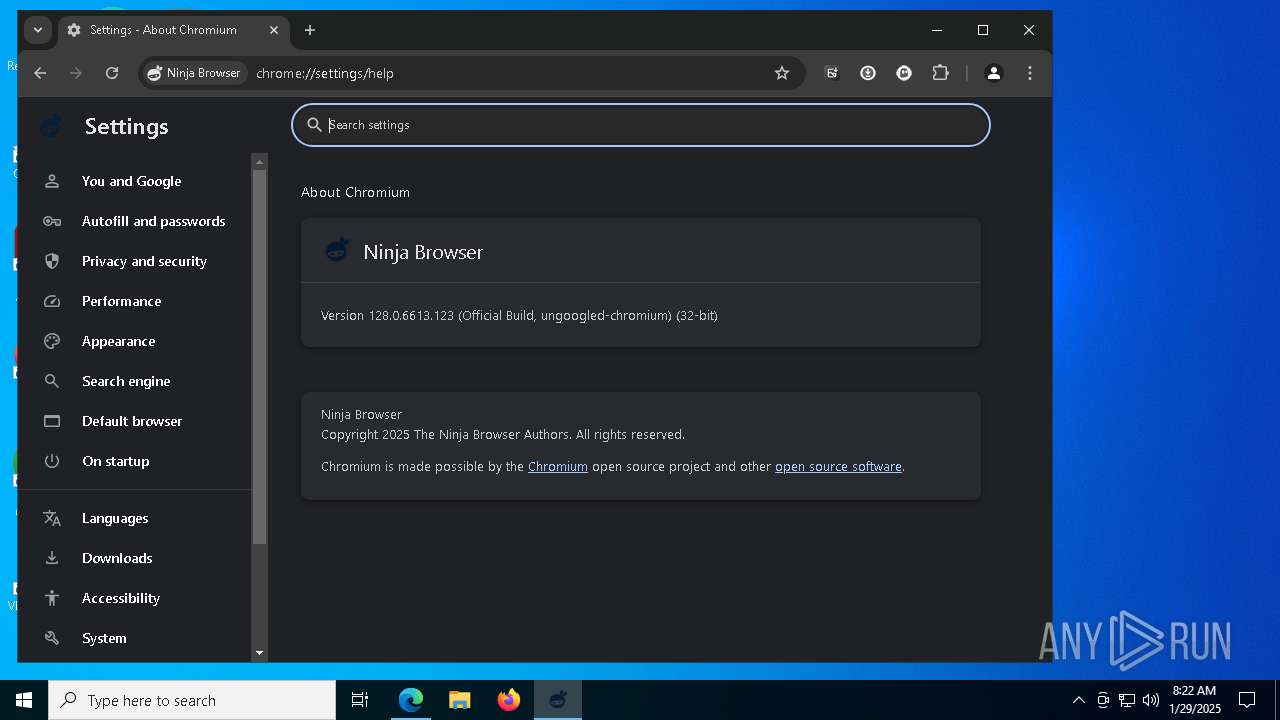
| URL: | https://ninja-browser.github.io/ninja-browser/bin/setup.exe |
| Full analysis: | https://app.any.run/tasks/ce77e5d6-fa10-4d8d-b436-72da4221115c |
| Verdict: | Malicious activity |
| Analysis date: | January 29, 2025, 08:20:35 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 8E1D9598284DBEFBB35C63FC38DCCD75 |
| SHA1: | CF3E8B8A5428B47723D96EB1A9DCF68E64CEE2AE |
| SHA256: | B8926B7C222A2786E4471BD47342F6892B05C21DA8EBC3F459AC84AF648053DE |
| SSDEEP: | 3:N8CX2MErBzX9+H2VL4A:2CmMEBz0SL4A |
MALICIOUS
PHISHING has been detected (SURICATA)
- svchost.exe (PID: 2192)
Changes the autorun value in the registry
- setup.exe (PID: 7260)
Bypass execution policy to execute commands
- powershell.exe (PID: 4264)
Changes powershell execution policy (Bypass)
- setup.tmp (PID: 2072)
Uses Task Scheduler to run other applications
- setup.tmp (PID: 2072)
Starts Visual C# compiler
- powershell.exe (PID: 4264)
SUSPICIOUS
Executable content was dropped or overwritten
- setup.exe (PID: 4628)
- setup.exe (PID: 5320)
- setup.tmp (PID: 2072)
- installer.exe (PID: 8188)
- setup.exe (PID: 7260)
- installer.exe (PID: 4872)
- setup.exe (PID: 3984)
- csc.exe (PID: 3144)
- csc.exe (PID: 4976)
Reads security settings of Internet Explorer
- setup.tmp (PID: 624)
- chrmstp.exe (PID: 5472)
Reads the Windows owner or organization settings
- setup.tmp (PID: 2072)
Creates file in the systems drive root
- msedge.exe (PID: 6336)
- installer.exe (PID: 8188)
- setup.exe (PID: 7260)
- installer.exe (PID: 4872)
Creates a software uninstall entry
- setup.exe (PID: 7260)
Application launched itself
- setup.exe (PID: 7260)
- NinjaBrowser.exe (PID: 1544)
- chrmstp.exe (PID: 1868)
Searches for installed software
- setup.exe (PID: 7260)
- setup.exe (PID: 5488)
- setup.exe (PID: 3984)
- chrmstp.exe (PID: 5472)
The process executes Powershell scripts
- setup.tmp (PID: 2072)
Gets path to any of the special folders (POWERSHELL)
- powershell.exe (PID: 4264)
Starts POWERSHELL.EXE for commands execution
- setup.tmp (PID: 2072)
Converts a specified value to an integer (POWERSHELL)
- powershell.exe (PID: 4264)
Uses base64 encoding (POWERSHELL)
- powershell.exe (PID: 4264)
Uses .NET C# to load dll
- powershell.exe (PID: 4264)
CSC.EXE is used to compile C# code
- csc.exe (PID: 3144)
- csc.exe (PID: 4976)
INFO
Executable content was dropped or overwritten
- msedge.exe (PID: 6664)
- msedge.exe (PID: 6336)
Reads the computer name
- setup.tmp (PID: 624)
- setup.tmp (PID: 2072)
- identity_helper.exe (PID: 7896)
- installer.exe (PID: 8188)
- setup.exe (PID: 7260)
- setup.exe (PID: 5488)
- NinjaBrowser.exe (PID: 1544)
- installer.exe (PID: 4872)
- chrmstp.exe (PID: 5472)
- NinjaBrowser.exe (PID: 4264)
Process checks computer location settings
- setup.tmp (PID: 624)
- NinjaBrowser.exe (PID: 7208)
- NinjaBrowser.exe (PID: 1544)
- NinjaBrowser.exe (PID: 7432)
- NinjaBrowser.exe (PID: 5916)
- NinjaBrowser.exe (PID: 5400)
- NinjaBrowser.exe (PID: 520)
- NinjaBrowser.exe (PID: 7384)
- NinjaBrowser.exe (PID: 7692)
- NinjaBrowser.exe (PID: 2904)
Checks supported languages
- setup.exe (PID: 5320)
- setup.exe (PID: 4628)
- setup.tmp (PID: 2072)
- identity_helper.exe (PID: 7896)
- setup.tmp (PID: 624)
- installer.exe (PID: 8188)
- setup.exe (PID: 7260)
- setup.exe (PID: 5488)
- installer.exe (PID: 4872)
- setup.exe (PID: 3984)
- csc.exe (PID: 4976)
- csc.exe (PID: 3144)
- NinjaBrowser.exe (PID: 1544)
- NinjaBrowser.exe (PID: 7432)
- NinjaBrowser.exe (PID: 7208)
- NinjaBrowser.exe (PID: 7812)
- NinjaBrowser.exe (PID: 7196)
- NinjaBrowser.exe (PID: 3564)
- NinjaBrowser.exe (PID: 1220)
- NinjaBrowser.exe (PID: 6672)
- NinjaBrowser.exe (PID: 1328)
- NinjaBrowser.exe (PID: 7256)
- NinjaBrowser.exe (PID: 4864)
- NinjaBrowser.exe (PID: 3820)
- NinjaBrowser.exe (PID: 4244)
- NinjaBrowser.exe (PID: 4052)
- NinjaBrowser.exe (PID: 5936)
- NinjaBrowser.exe (PID: 7908)
- NinjaBrowser.exe (PID: 1916)
- NinjaBrowser.exe (PID: 2976)
- NinjaBrowser.exe (PID: 7296)
- NinjaBrowser.exe (PID: 6440)
- NinjaBrowser.exe (PID: 7156)
- NinjaBrowser.exe (PID: 540)
- NinjaBrowser.exe (PID: 7452)
- NinjaBrowser.exe (PID: 1512)
- NinjaBrowser.exe (PID: 7648)
- NinjaBrowser.exe (PID: 5880)
- NinjaBrowser.exe (PID: 6280)
- NinjaBrowser.exe (PID: 624)
- NinjaBrowser.exe (PID: 1304)
- NinjaBrowser.exe (PID: 6252)
- NinjaBrowser.exe (PID: 5400)
- NinjaBrowser.exe (PID: 7048)
- NinjaBrowser.exe (PID: 7640)
- NinjaBrowser.exe (PID: 5788)
- NinjaBrowser.exe (PID: 5916)
- NinjaBrowser.exe (PID: 1488)
- NinjaBrowser.exe (PID: 2356)
- NinjaBrowser.exe (PID: 7404)
- NinjaBrowser.exe (PID: 7644)
- NinjaBrowser.exe (PID: 6592)
- NinjaBrowser.exe (PID: 8116)
- NinjaBrowser.exe (PID: 5936)
- NinjaBrowser.exe (PID: 8000)
- NinjaBrowser.exe (PID: 4264)
- NinjaBrowser.exe (PID: 8044)
- NinjaBrowser.exe (PID: 6436)
- NinjaBrowser.exe (PID: 520)
- NinjaBrowser.exe (PID: 7384)
- chrmstp.exe (PID: 5472)
- NinjaBrowser.exe (PID: 1016)
- NinjaBrowser.exe (PID: 7692)
- NinjaBrowser.exe (PID: 2904)
- NinjaBrowser.exe (PID: 7604)
Create files in a temporary directory
- setup.exe (PID: 4628)
- setup.exe (PID: 5320)
- setup.tmp (PID: 2072)
- installer.exe (PID: 8188)
- installer.exe (PID: 4872)
- csc.exe (PID: 3144)
- cvtres.exe (PID: 7760)
- cvtres.exe (PID: 1512)
- csc.exe (PID: 4976)
- NinjaBrowser.exe (PID: 1544)
Reads Environment values
- identity_helper.exe (PID: 7896)
Application launched itself
- msedge.exe (PID: 6336)
Detects InnoSetup installer (YARA)
- setup.exe (PID: 5320)
- setup.exe (PID: 4628)
- setup.tmp (PID: 2072)
- setup.tmp (PID: 624)
Checks proxy server information
- setup.tmp (PID: 2072)
- NinjaBrowser.exe (PID: 1544)
Compiled with Borland Delphi (YARA)
- setup.exe (PID: 5320)
- setup.tmp (PID: 624)
- setup.exe (PID: 4628)
- setup.tmp (PID: 2072)
Reads the software policy settings
- setup.tmp (PID: 2072)
Creates files in the program directory
- setup.tmp (PID: 2072)
- setup.exe (PID: 7260)
- setup.exe (PID: 5488)
- setup.exe (PID: 3984)
The sample compiled with english language support
- installer.exe (PID: 8188)
- setup.exe (PID: 7260)
- setup.exe (PID: 3984)
- installer.exe (PID: 4872)
Creates files or folders in the user directory
- setup.exe (PID: 5488)
- NinjaBrowser.exe (PID: 1544)
- NinjaBrowser.exe (PID: 8072)
- chrmstp.exe (PID: 5472)
Converts byte array into Unicode string (POWERSHELL)
- powershell.exe (PID: 4264)
Gets data length (POWERSHELL)
- powershell.exe (PID: 4264)
Reads the machine GUID from the registry
- csc.exe (PID: 4976)
- csc.exe (PID: 3144)
- NinjaBrowser.exe (PID: 1544)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
258
Monitored processes
124
Malicious processes
13
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 520 | "C:\Program Files (x86)\NinjaBrowser\NinjaBrowser\Application\NinjaBrowser.exe" --type=renderer --extension-process --disable-gpu-compositing --video-capture-use-gpu-memory-buffer --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=63 --field-trial-handle=6348,i,17544050084098114097,8399006958837570068,262144 --variations-seed-version --mojo-platform-channel-handle=8716 /prefetch:2 | C:\Program Files (x86)\NinjaBrowser\NinjaBrowser\Application\NinjaBrowser.exe | — | NinjaBrowser.exe | |||||||||||
User: admin Company: The Ninja Browser Authors Integrity Level: LOW Description: Ninja Browser Version: 128.0.6613.123 Modules
| |||||||||||||||
| 540 | "C:\Program Files (x86)\NinjaBrowser\NinjaBrowser\Application\NinjaBrowser.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --field-trial-handle=6480,i,17544050084098114097,8399006958837570068,262144 --variations-seed-version --mojo-platform-channel-handle=9524 /prefetch:8 | C:\Program Files (x86)\NinjaBrowser\NinjaBrowser\Application\NinjaBrowser.exe | — | NinjaBrowser.exe | |||||||||||
User: admin Company: The Ninja Browser Authors Integrity Level: LOW Description: Ninja Browser Exit code: 0 Version: 128.0.6613.123 Modules
| |||||||||||||||
| 624 | "C:\Users\admin\AppData\Local\Temp\is-4VHPP.tmp\setup.tmp" /SL5="$901E8,826227,820736,C:\Users\admin\Downloads\setup.exe" | C:\Users\admin\AppData\Local\Temp\is-4VHPP.tmp\setup.tmp | — | setup.exe | |||||||||||
User: admin Company: NinjaBrowser Integrity Level: MEDIUM Description: Setup/Uninstall Exit code: 0 Version: 51.1052.0.0 Modules
| |||||||||||||||
| 624 | "C:\Program Files (x86)\NinjaBrowser\NinjaBrowser\Application\NinjaBrowser.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --field-trial-handle=5548,i,17544050084098114097,8399006958837570068,262144 --variations-seed-version --mojo-platform-channel-handle=5940 /prefetch:8 | C:\Program Files (x86)\NinjaBrowser\NinjaBrowser\Application\NinjaBrowser.exe | — | NinjaBrowser.exe | |||||||||||
User: admin Company: The Ninja Browser Authors Integrity Level: LOW Description: Ninja Browser Exit code: 0 Version: 128.0.6613.123 Modules
| |||||||||||||||
| 1016 | "C:\Program Files (x86)\NinjaBrowser\NinjaBrowser\Application\NinjaBrowser.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --field-trial-handle=8404,i,17544050084098114097,8399006958837570068,262144 --variations-seed-version --mojo-platform-channel-handle=3436 /prefetch:8 | C:\Program Files (x86)\NinjaBrowser\NinjaBrowser\Application\NinjaBrowser.exe | — | NinjaBrowser.exe | |||||||||||
User: admin Company: The Ninja Browser Authors Integrity Level: LOW Description: Ninja Browser Exit code: 0 Version: 128.0.6613.123 Modules
| |||||||||||||||
| 1200 | "C:\Program Files (x86)\NinjaBrowser\NinjaBrowser\Application\NinjaBrowser.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --field-trial-handle=3960,i,17544050084098114097,8399006958837570068,262144 --variations-seed-version --mojo-platform-channel-handle=5048 /prefetch:8 | C:\Program Files (x86)\NinjaBrowser\NinjaBrowser\Application\NinjaBrowser.exe | — | NinjaBrowser.exe | |||||||||||
User: admin Company: The Ninja Browser Authors Integrity Level: LOW Description: Ninja Browser Exit code: 0 Version: 128.0.6613.123 Modules
| |||||||||||||||
| 1220 | "C:\Program Files (x86)\NinjaBrowser\NinjaBrowser\Application\NinjaBrowser.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --field-trial-handle=6064,i,17544050084098114097,8399006958837570068,262144 --variations-seed-version --mojo-platform-channel-handle=6088 /prefetch:8 | C:\Program Files (x86)\NinjaBrowser\NinjaBrowser\Application\NinjaBrowser.exe | — | NinjaBrowser.exe | |||||||||||
User: admin Company: The Ninja Browser Authors Integrity Level: LOW Description: Ninja Browser Exit code: 0 Version: 128.0.6613.123 Modules
| |||||||||||||||
| 1304 | "C:\Program Files (x86)\NinjaBrowser\NinjaBrowser\Application\NinjaBrowser.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --field-trial-handle=9180,i,17544050084098114097,8399006958837570068,262144 --variations-seed-version --mojo-platform-channel-handle=10292 /prefetch:8 | C:\Program Files (x86)\NinjaBrowser\NinjaBrowser\Application\NinjaBrowser.exe | — | NinjaBrowser.exe | |||||||||||
User: admin Company: The Ninja Browser Authors Integrity Level: LOW Description: Ninja Browser Exit code: 0 Version: 128.0.6613.123 Modules
| |||||||||||||||
| 1328 | "C:\Program Files (x86)\NinjaBrowser\NinjaBrowser\Application\NinjaBrowser.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --field-trial-handle=4804,i,17544050084098114097,8399006958837570068,262144 --variations-seed-version --mojo-platform-channel-handle=6792 /prefetch:8 | C:\Program Files (x86)\NinjaBrowser\NinjaBrowser\Application\NinjaBrowser.exe | — | NinjaBrowser.exe | |||||||||||
User: admin Company: The Ninja Browser Authors Integrity Level: LOW Description: Ninja Browser Exit code: 0 Version: 128.0.6613.123 Modules
| |||||||||||||||
| 1400 | "C:\Program Files (x86)\NinjaBrowser\NinjaBrowser\Application\NinjaBrowser.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --field-trial-handle=5088,i,17544050084098114097,8399006958837570068,262144 --variations-seed-version --mojo-platform-channel-handle=5224 /prefetch:8 | C:\Program Files (x86)\NinjaBrowser\NinjaBrowser\Application\NinjaBrowser.exe | — | NinjaBrowser.exe | |||||||||||
User: admin Company: The Ninja Browser Authors Integrity Level: LOW Description: Ninja Browser Exit code: 0 Version: 128.0.6613.123 Modules
| |||||||||||||||
Total events
18 075
Read events
17 888
Write events
178
Delete events
9
Modification events
| (PID) Process: | (6336) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (6336) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (6336) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (6336) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (6336) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\LastWasDefault |
| Operation: | write | Name: | S-1-5-21-1693682860-607145093-2874071422-1001 |
Value: FB9DD0446A8B2F00 | |||
| (PID) Process: | (6336) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\LastWasDefault |
| Operation: | write | Name: | S-1-5-21-1693682860-607145093-2874071422-1001 |
Value: 541EE0446A8B2F00 | |||
| (PID) Process: | (6336) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\328416 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {2827711A-3F5B-4702-A109-B721E06D8D4F} | |||
| (PID) Process: | (6336) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\328416 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {57193FD4-B920-4A13-A0D4-CA288FCD1076} | |||
| (PID) Process: | (6336) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\LastWasDefault |
| Operation: | write | Name: | S-1-5-21-1693682860-607145093-2874071422-1001 |
Value: 257D2F456A8B2F00 | |||
| (PID) Process: | (7660) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Shell Extensions\Cached |
| Operation: | write | Name: | {2781761E-28E0-4109-99FE-B9D127C57AFE} {56FFCC30-D398-11D0-B2AE-00A0C908FA49} 0xFFFF |
Value: 010000000000000083C72EB42672DB01 | |||
Executable files
31
Suspicious files
938
Text files
951
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6336 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old~RF136053.TMP | — | |
MD5:— | SHA256:— | |||
| 6336 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6336 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old~RF136063.TMP | — | |
MD5:— | SHA256:— | |||
| 6336 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6336 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old~RF136063.TMP | — | |
MD5:— | SHA256:— | |||
| 6336 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6336 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old~RF136063.TMP | — | |
MD5:— | SHA256:— | |||
| 6336 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6336 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old~RF136063.TMP | — | |
MD5:— | SHA256:— | |||
| 6336 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
23
TCP/UDP connections
59
DNS requests
66
Threats
4
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4712 | MoUsoCoreWorker.exe | GET | 200 | 95.101.54.128:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
7688 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
7688 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
4548 | svchost.exe | HEAD | 200 | 199.232.210.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/9b9f8fb4-8a65-41e4-bda3-5416858f0aeb?P1=1738717720&P2=404&P3=2&P4=eCrGy3XBwmoCCx20j6fN5sQ7mrheeklQYStpmkdCFN2iLB02fR8Zb6y9PZiIw%2fjBtDJobEVpnnWX9Pk85LXitg%3d%3d | unknown | — | — | whitelisted |
5308 | backgroundTaskHost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
4548 | svchost.exe | GET | 206 | 199.232.210.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/9b9f8fb4-8a65-41e4-bda3-5416858f0aeb?P1=1738717720&P2=404&P3=2&P4=eCrGy3XBwmoCCx20j6fN5sQ7mrheeklQYStpmkdCFN2iLB02fR8Zb6y9PZiIw%2fjBtDJobEVpnnWX9Pk85LXitg%3d%3d | unknown | — | — | whitelisted |
4548 | svchost.exe | GET | 206 | 199.232.210.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/9b9f8fb4-8a65-41e4-bda3-5416858f0aeb?P1=1738717720&P2=404&P3=2&P4=eCrGy3XBwmoCCx20j6fN5sQ7mrheeklQYStpmkdCFN2iLB02fR8Zb6y9PZiIw%2fjBtDJobEVpnnWX9Pk85LXitg%3d%3d | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 2.23.77.188:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | 95.101.54.128:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
— | — | 40.127.240.158:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
1176 | svchost.exe | 20.190.159.73:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1176 | svchost.exe | 2.23.77.188:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
1076 | svchost.exe | 184.28.89.167:443 | go.microsoft.com | AKAMAI-AS | US | whitelisted |
6336 | msedge.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
6664 | msedge.exe | 13.107.42.16:443 | config.edge.skype.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
ocsp.digicert.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
config.edge.skype.com |
| whitelisted |
ninja-browser.github.io |
| unknown |
edge.microsoft.com |
| whitelisted |
business.bing.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2192 | svchost.exe | Possible Social Engineering Attempted | PHISHING [ANY.RUN] Suspected Phishing domain by CrossDomain ( .ninja-browser .com) |
8072 | NinjaBrowser.exe | Not Suspicious Traffic | INFO [ANY.RUN] Requests to a free CDN for open source projects (jsdelivr .net) |
8072 | NinjaBrowser.exe | Not Suspicious Traffic | INFO [ANY.RUN] Requests to a free CDN for open source projects (jsdelivr .net) |
8072 | NinjaBrowser.exe | Not Suspicious Traffic | INFO [ANY.RUN] Requests to a free CDN for open source projects (jsdelivr .net) |