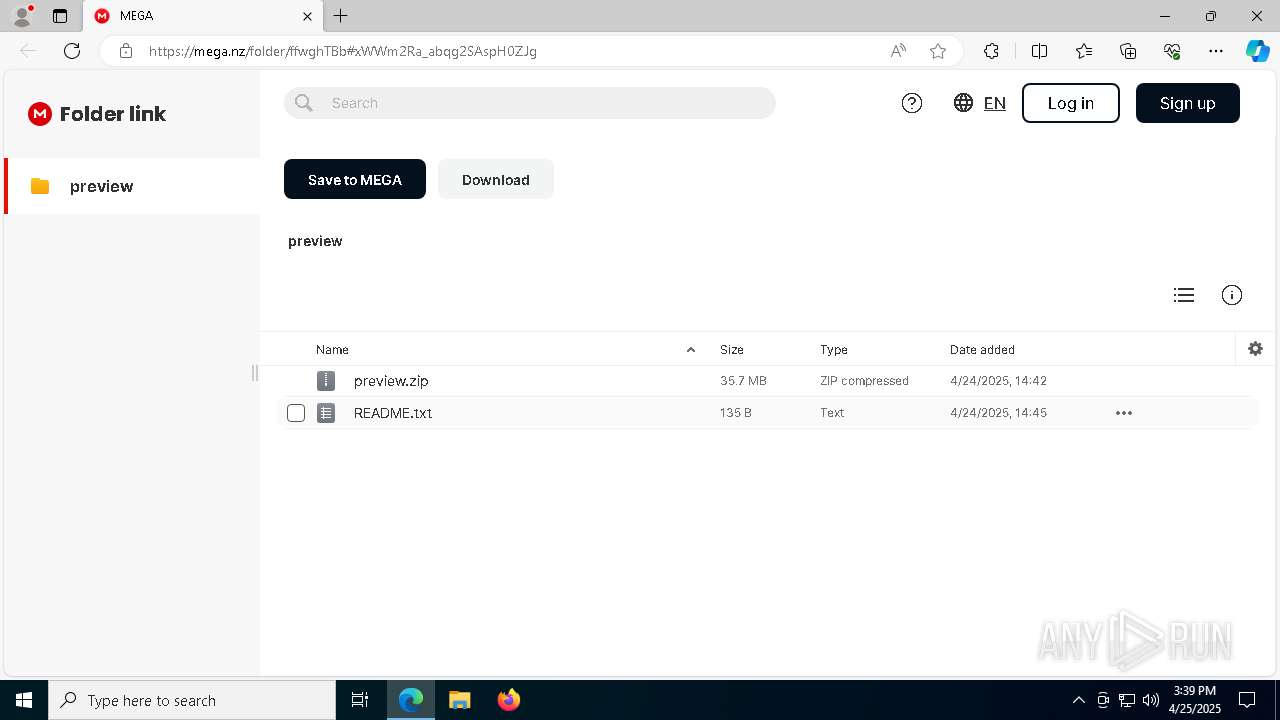
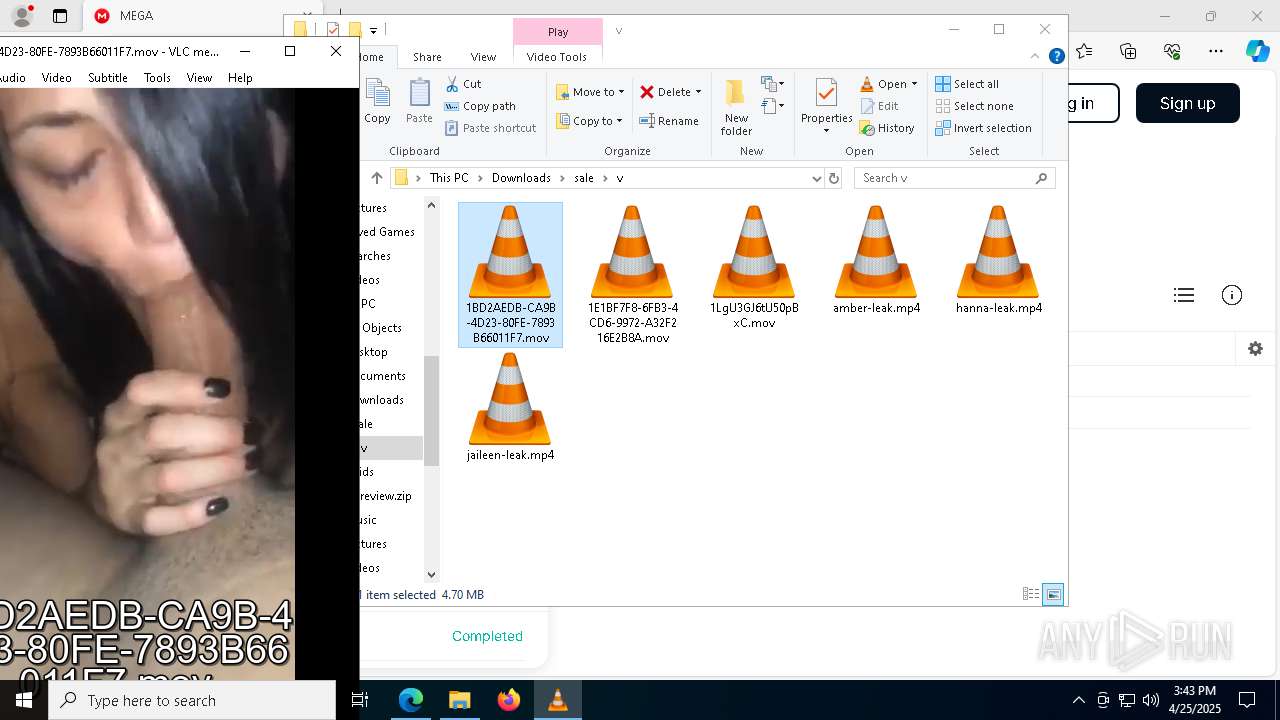
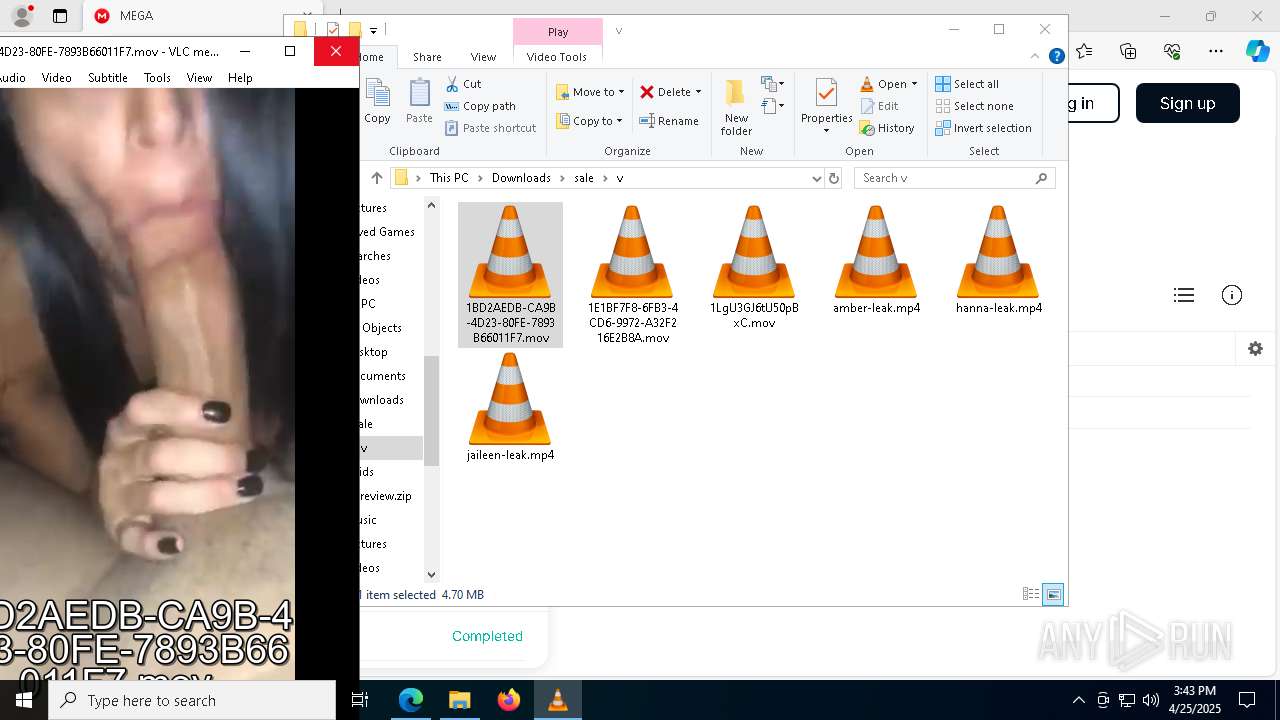
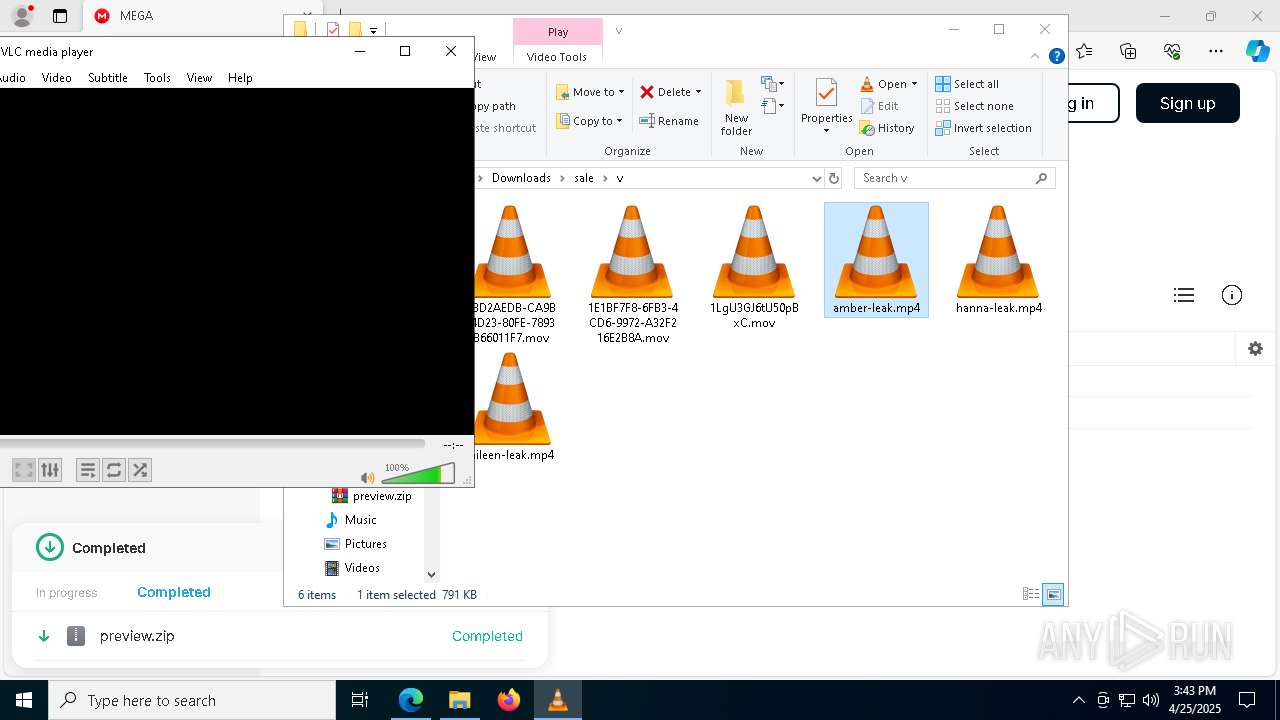
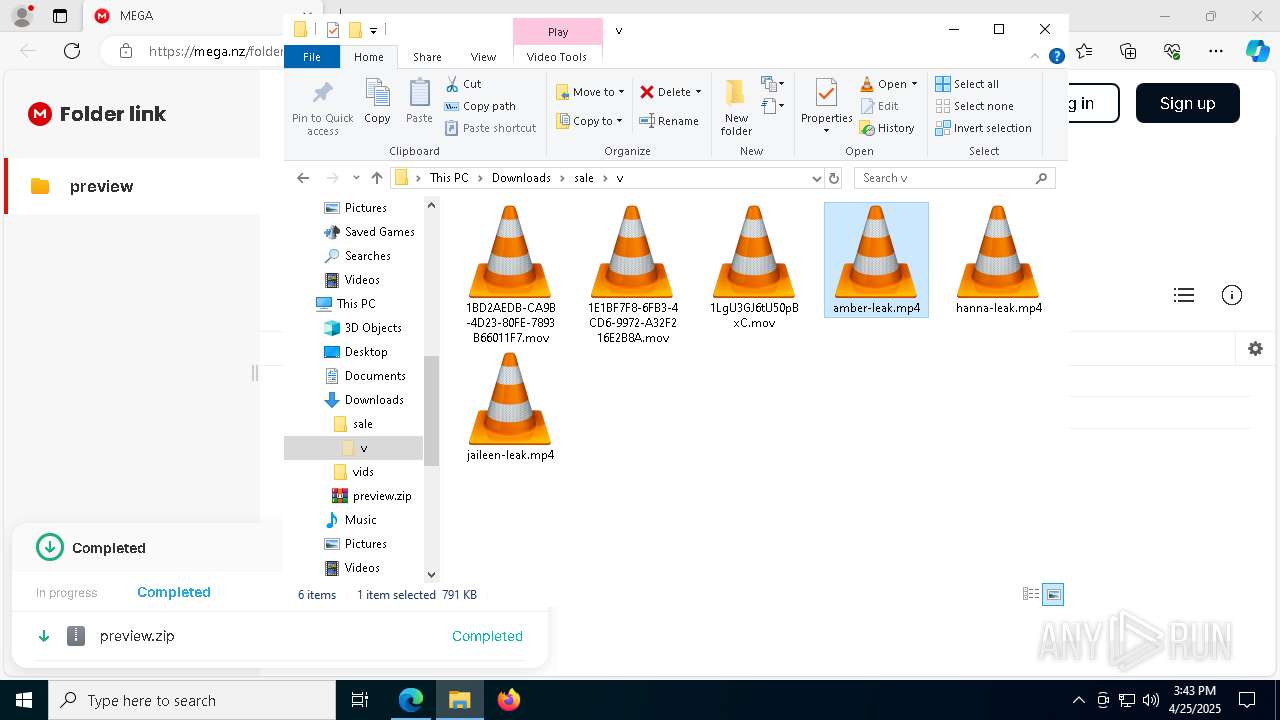
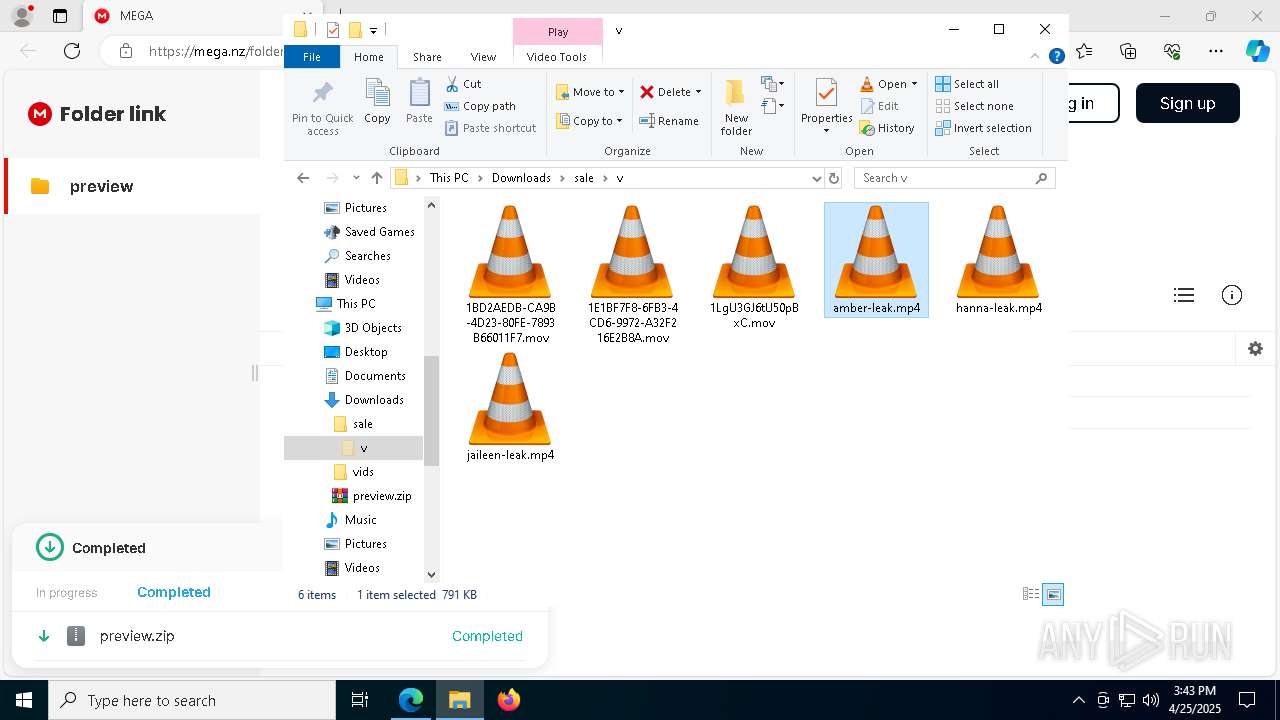
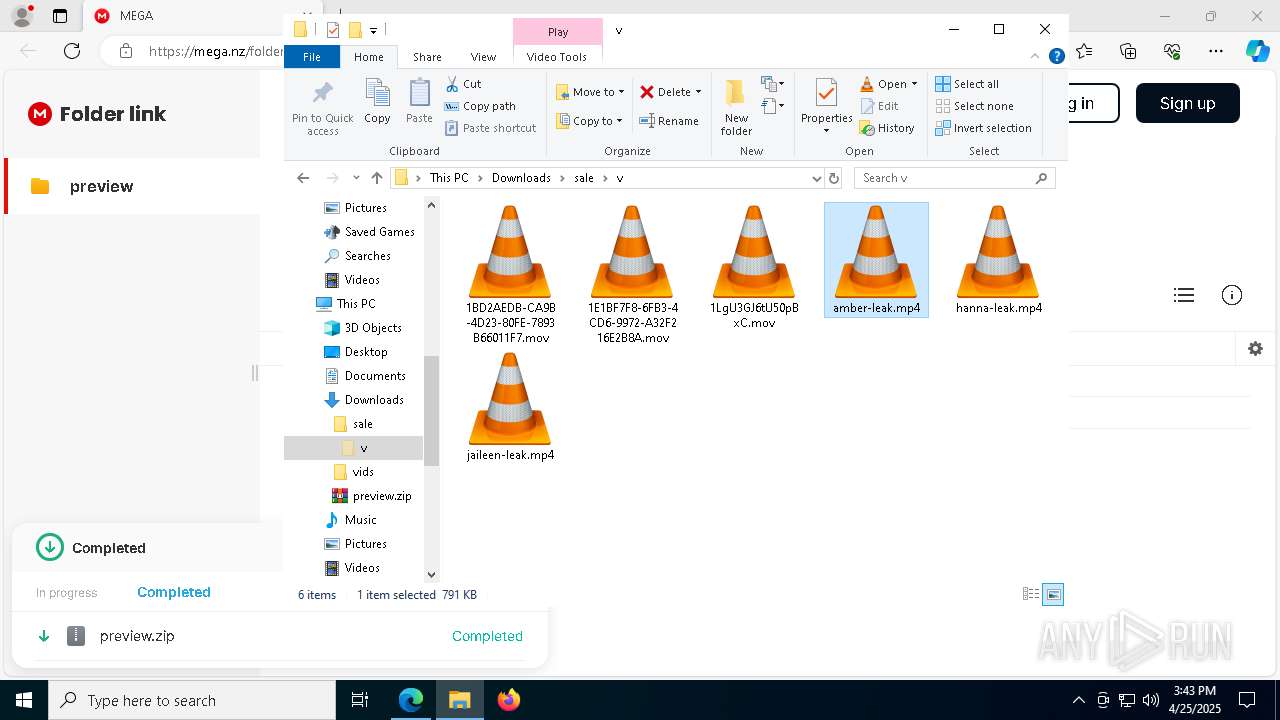
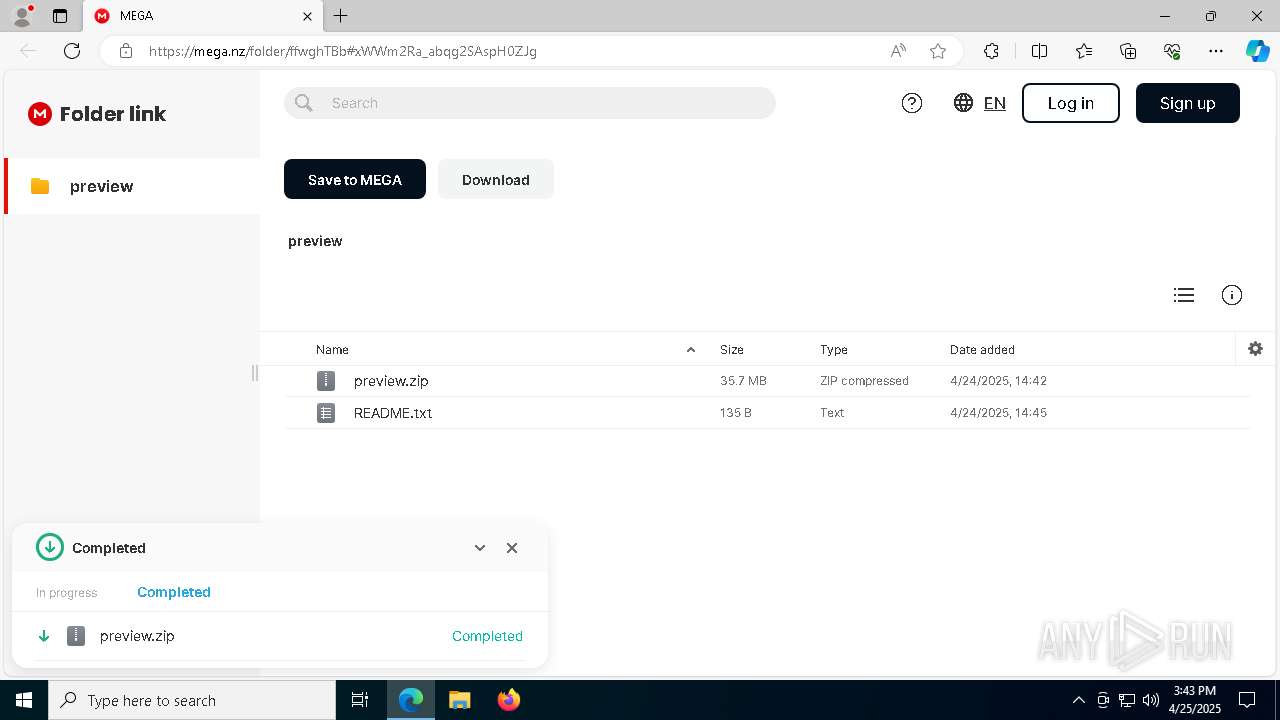
| URL: | https://mega.nz/folder/ffwghTBb#xWWm2Ra_abqg2SAspH0ZJg |
| Full analysis: | https://app.any.run/tasks/b65d387d-0565-48d9-a61c-212b9277853a |
| Verdict: | Malicious activity |
| Analysis date: | April 25, 2025, 15:39:30 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Indicators: | |
| MD5: | 9743E20B82B0CB2CF486FF653D08B5F6 |
| SHA1: | EB79D760D880CB1281EFB178A133E7C8C3D0F73A |
| SHA256: | B8835D9557A2FBC10D06B56E477B67C4360A8ACFECD8754721C7E1ED10C0140C |
| SSDEEP: | 3:N8X/iuyKjaITr1nC:26rArlC |
MALICIOUS
Changes powershell execution policy (Bypass)
- cmd.exe (PID: 7804)
- cmd.exe (PID: 7860)
- cmd.exe (PID: 4012)
Run PowerShell with an invisible window
- powershell.exe (PID: 5668)
- powershell.exe (PID: 7760)
- powershell.exe (PID: 7816)
Bypass execution policy to execute commands
- powershell.exe (PID: 5668)
- powershell.exe (PID: 7760)
- powershell.exe (PID: 7816)
SUSPICIOUS
The process executes Powershell scripts
- cmd.exe (PID: 7804)
- cmd.exe (PID: 7860)
- powershell.exe (PID: 5668)
- powershell.exe (PID: 7760)
- cmd.exe (PID: 4012)
Uses TIMEOUT.EXE to delay execution
- cmd.exe (PID: 7860)
- cmd.exe (PID: 7804)
- cmd.exe (PID: 4012)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 7804)
- cmd.exe (PID: 7860)
- powershell.exe (PID: 7760)
- powershell.exe (PID: 5668)
- cmd.exe (PID: 4012)
Executable content was dropped or overwritten
- powershell.exe (PID: 5668)
PowerShell delay command usage (probably sleep evasion)
- powershell.exe (PID: 4560)
- powershell.exe (PID: 5008)
Application launched itself
- powershell.exe (PID: 5668)
- powershell.exe (PID: 7760)
Executes application which crashes
- msedgewebview3.exe (PID: 6892)
Base64-obfuscated command line is found
- powershell.exe (PID: 5668)
- powershell.exe (PID: 7760)
Removes files via Powershell
- powershell.exe (PID: 5008)
- powershell.exe (PID: 4560)
INFO
Manual execution by a user
- cmd.exe (PID: 7860)
- cmd.exe (PID: 7804)
- WinRAR.exe (PID: 644)
- cmd.exe (PID: 4012)
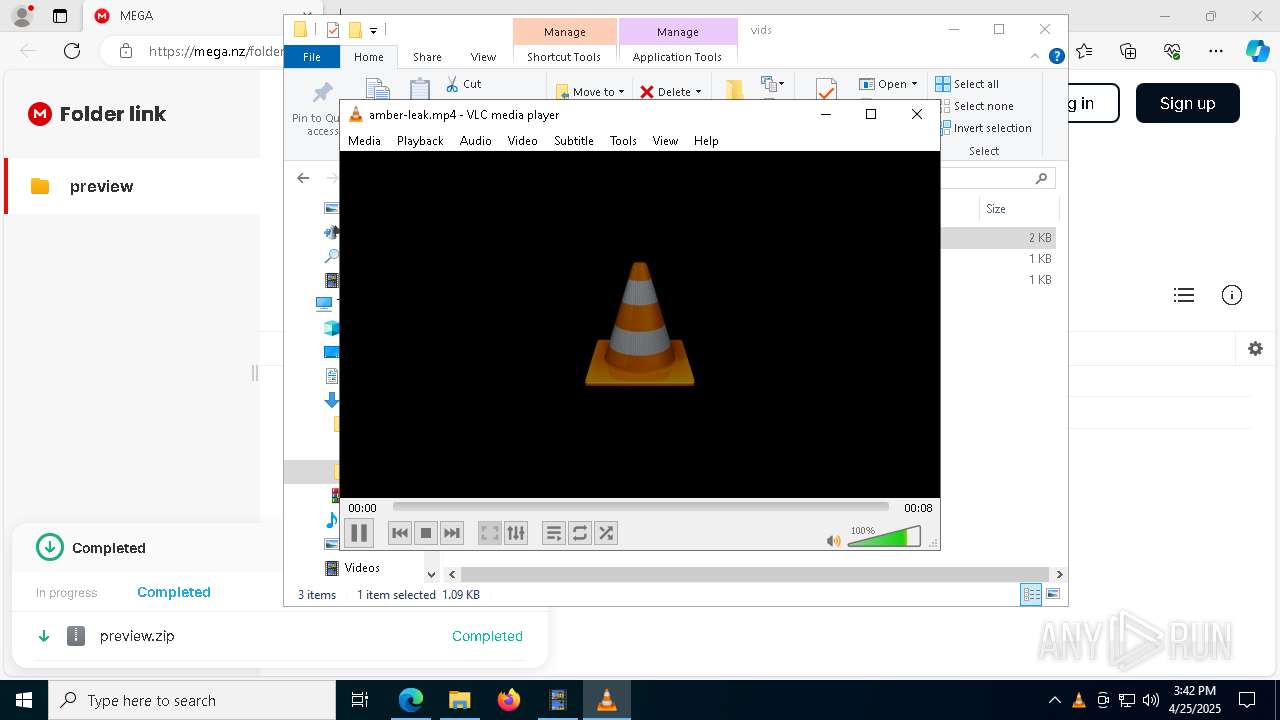
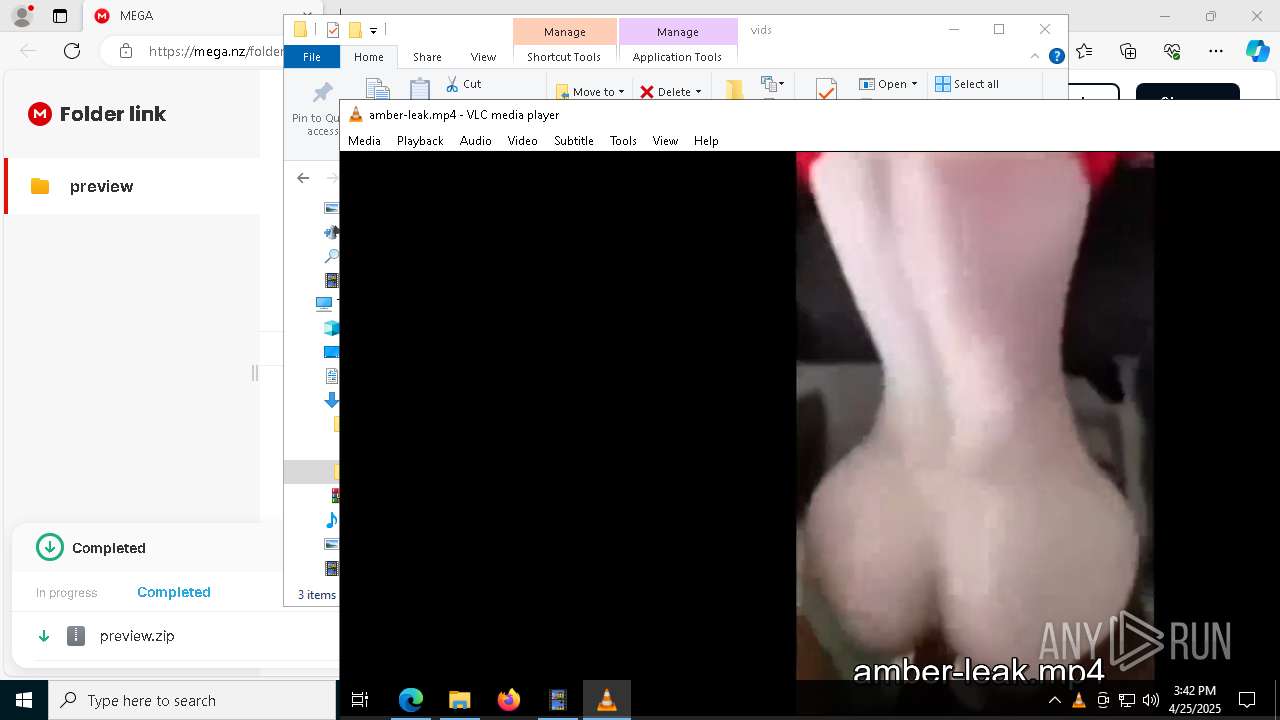
- vlc.exe (PID: 7812)
- vlc.exe (PID: 7904)
- vlc.exe (PID: 300)
- vlc.exe (PID: 3992)
- vlc.exe (PID: 6348)
Application launched itself
- msedge.exe (PID: 6480)
Reads Environment values
- identity_helper.exe (PID: 5404)
Execution of CURL command
- cmd.exe (PID: 7860)
- cmd.exe (PID: 7804)
- cmd.exe (PID: 4012)
Checks supported languages
- identity_helper.exe (PID: 5404)
Reads the software policy settings
- slui.exe (PID: 8156)
- slui.exe (PID: 8112)
Reads the computer name
- identity_helper.exe (PID: 5404)
Checks proxy server information
- slui.exe (PID: 8156)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
247
Monitored processes
106
Malicious processes
3
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
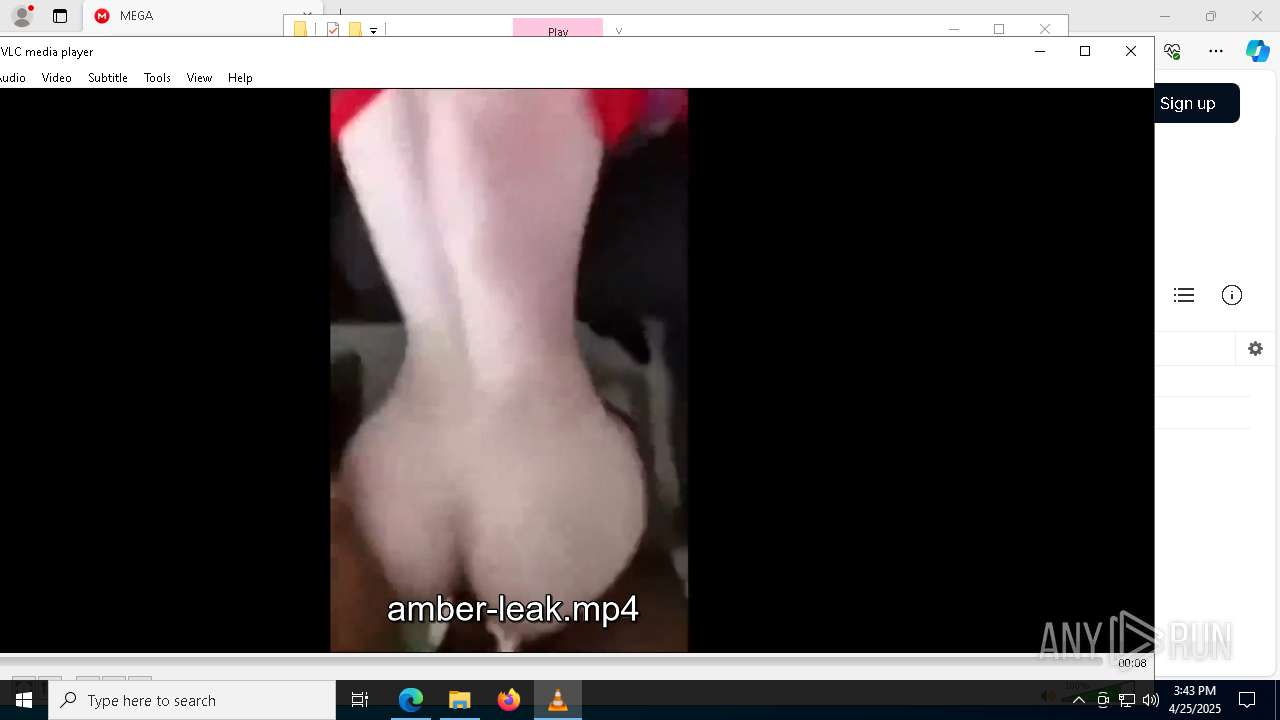
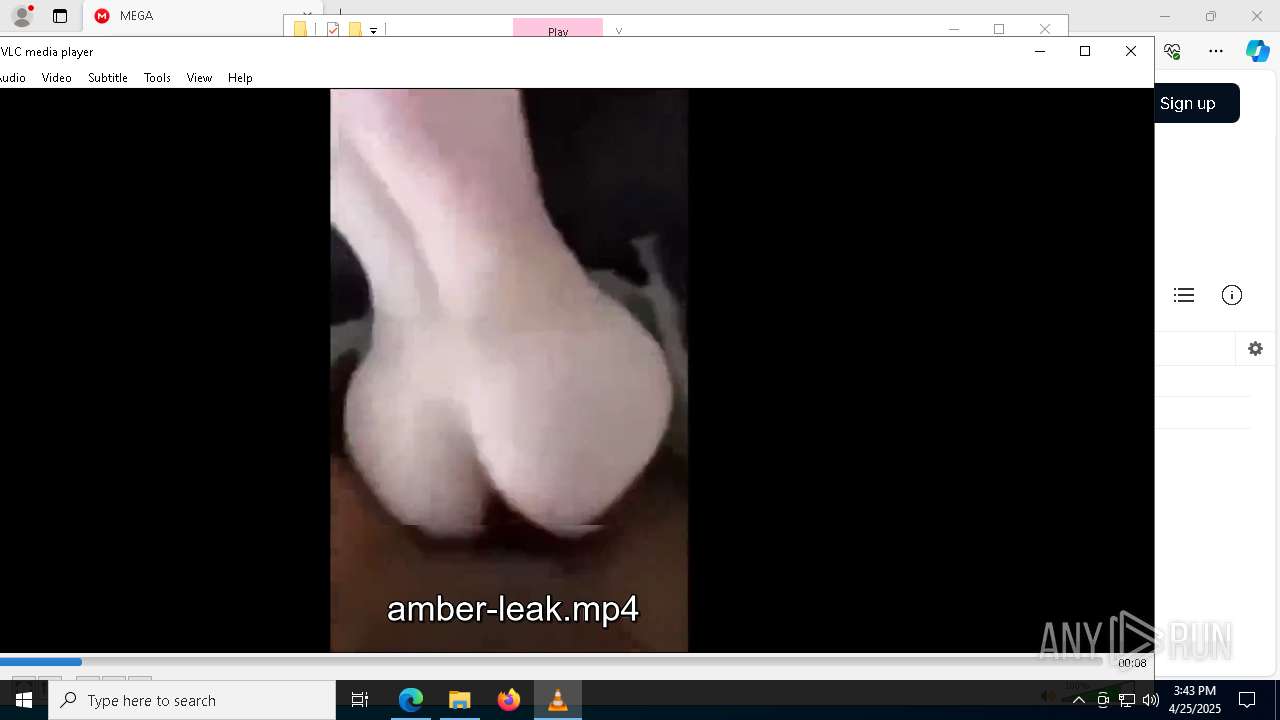
| 300 | "C:\Program Files\VideoLAN\VLC\vlc.exe" --started-from-file "C:\Users\admin\Downloads\sale\v\amber-leak.mp4" | C:\Program Files\VideoLAN\VLC\vlc.exe | — | explorer.exe | |||||||||||
User: admin Company: VideoLAN Integrity Level: MEDIUM Description: VLC media player Exit code: 0 Version: 3.0.11 Modules
| |||||||||||||||
| 616 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=edge_search_indexer.mojom.SearchIndexerInterfaceBroker --lang=en-US --service-sandbox-type=search_indexer --message-loop-type-ui --no-appcompat-clear --mojo-platform-channel-handle=1556 --field-trial-handle=2484,i,7627640511318947862,3069805829855342446,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 122.0.2365.59 Modules
| |||||||||||||||
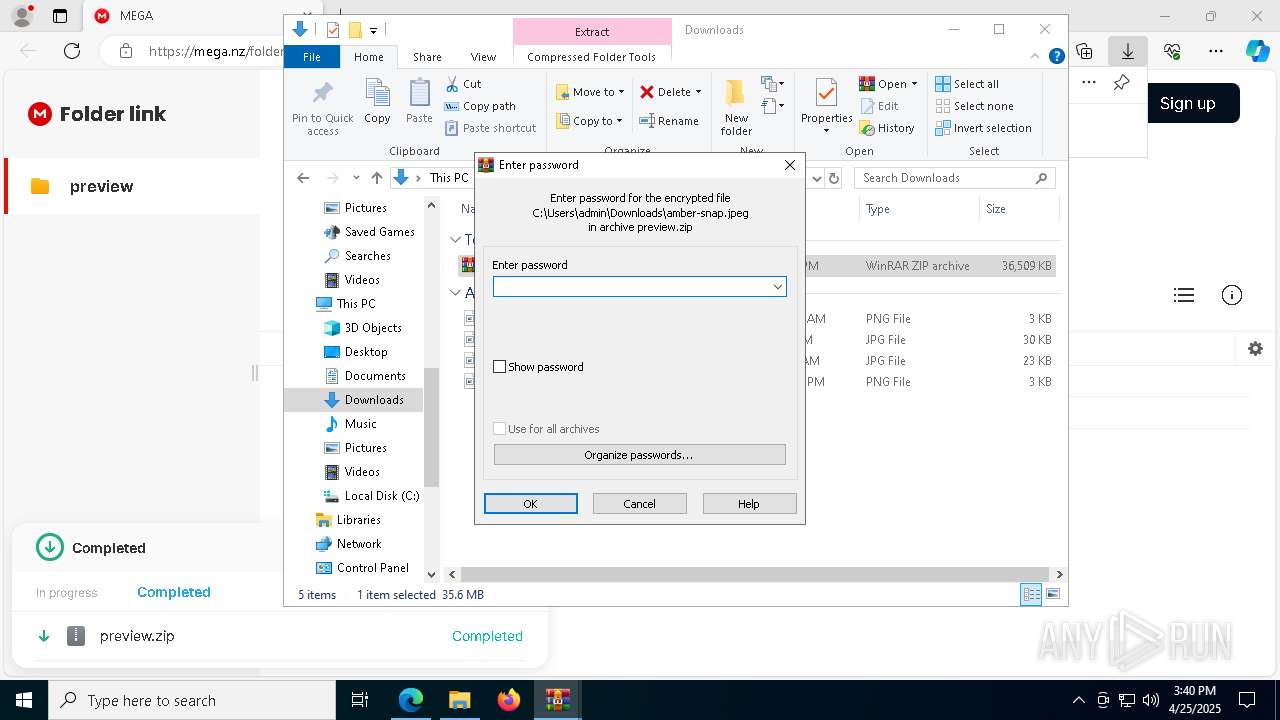
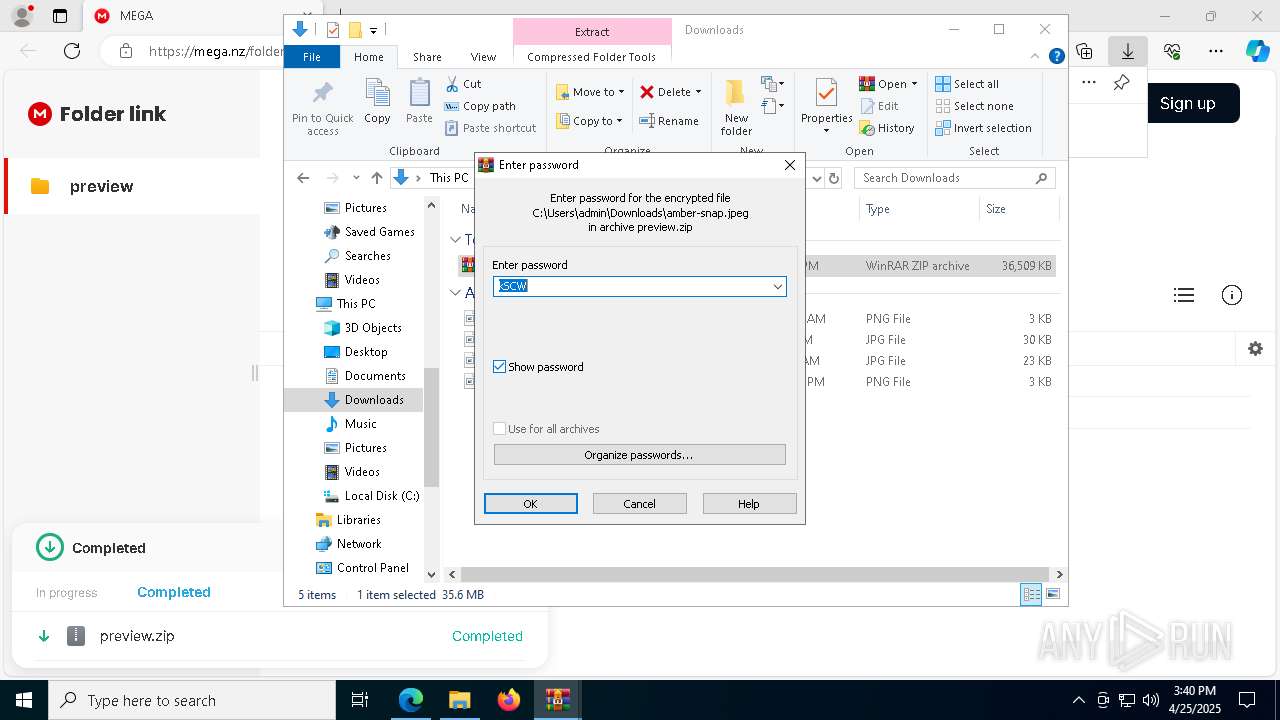
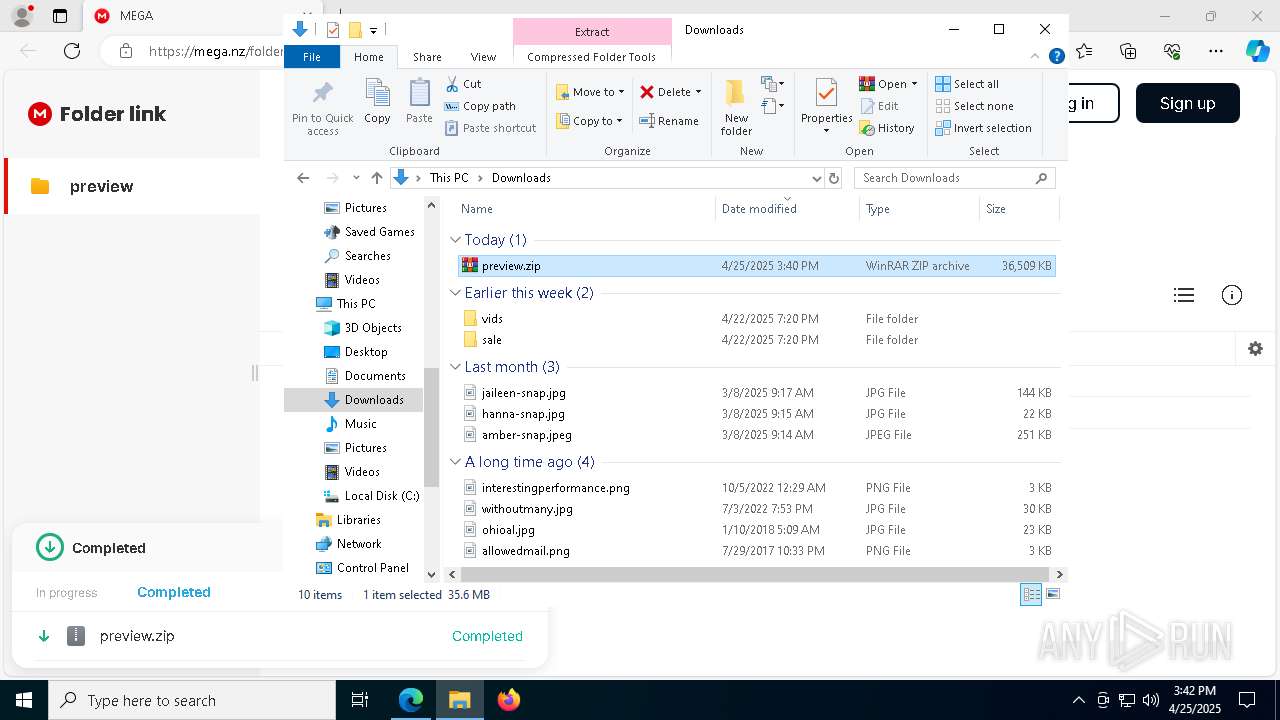
| 644 | "C:\Program Files\WinRAR\WinRAR.exe" x -iext -ow -ver -- "C:\Users\admin\Downloads\preview.zip" C:\Users\admin\Downloads\ | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 684 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=7636 --field-trial-handle=2484,i,7627640511318947862,3069805829855342446,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1072 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=1704 --field-trial-handle=2484,i,7627640511318947862,3069805829855342446,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1180 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=5688 --field-trial-handle=2484,i,7627640511318947862,3069805829855342446,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1240 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=8012 --field-trial-handle=2484,i,7627640511318947862,3069805829855342446,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1240 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=7492 --field-trial-handle=2484,i,7627640511318947862,3069805829855342446,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1812 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --lang=en-US --service-sandbox-type=none --no-appcompat-clear --mojo-platform-channel-handle=1496 --field-trial-handle=2484,i,7627640511318947862,3069805829855342446,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 2096 | "C:\Program Files\VideoLAN\VLC\vlc.exe" --started-from-file "C:\Users\admin\Downloads\sale\v\amber-leak.mp4" | C:\Program Files\VideoLAN\VLC\vlc.exe | — | cmd.exe | |||||||||||
User: admin Company: VideoLAN Integrity Level: MEDIUM Description: VLC media player Exit code: 0 Version: 3.0.11 Modules
| |||||||||||||||
Total events
48 391
Read events
48 279
Write events
112
Delete events
0
Modification events
| (PID) Process: | (6480) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\328516 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {78CFAA07-C8B4-4265-9E15-87E03712DE98} | |||
| (PID) Process: | (6480) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\328516 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {A4FDAC1A-8F95-4311-856B-808573F04CF5} | |||
| (PID) Process: | (6480) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (6480) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (6480) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (6480) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (6480) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\LastWasDefault |
| Operation: | write | Name: | S-1-5-21-1693682860-607145093-2874071422-1001 |
Value: 5D6BD16C32922F00 | |||
| (PID) Process: | (6480) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\LastWasDefault |
| Operation: | write | Name: | S-1-5-21-1693682860-607145093-2874071422-1001 |
Value: 8047D96C32922F00 | |||
| (PID) Process: | (6480) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\328516 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {1C5EDAFF-842A-4553-AD55-130B12DCBE43} | |||
| (PID) Process: | (6480) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\Profiles |
| Operation: | write | Name: | EnhancedLinkOpeningDefault |
Value: Default | |||
Executable files
78
Suspicious files
1 166
Text files
212
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6480 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old~RF10b94f.TMP | — | |
MD5:— | SHA256:— | |||
| 6480 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6480 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old~RF10b95f.TMP | — | |
MD5:— | SHA256:— | |||
| 6480 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6480 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old~RF10b96e.TMP | — | |
MD5:— | SHA256:— | |||
| 6480 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old~RF10b97e.TMP | — | |
MD5:— | SHA256:— | |||
| 6480 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6480 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old~RF10b99d.TMP | — | |
MD5:— | SHA256:— | |||
| 6480 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6480 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
46
TCP/UDP connections
177
DNS requests
152
Threats
20
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 2.19.11.105:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
1452 | svchost.exe | GET | 206 | 23.50.131.85:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/5d32607d-eea9-44fc-ac55-77800b9862a5?P1=1746050955&P2=404&P3=2&P4=DQSDNtRMlfeCo9NDYKa4mQFlPO5PCWZja3b6DPu5Iy58V%2b4GgI1q4chg%2f5JMEf8dh%2fUBwNo07B8c5Cwakx1kbw%3d%3d | unknown | — | — | whitelisted |
1452 | svchost.exe | GET | 206 | 23.50.131.85:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/5d32607d-eea9-44fc-ac55-77800b9862a5?P1=1746050955&P2=404&P3=2&P4=DQSDNtRMlfeCo9NDYKa4mQFlPO5PCWZja3b6DPu5Iy58V%2b4GgI1q4chg%2f5JMEf8dh%2fUBwNo07B8c5Cwakx1kbw%3d%3d | unknown | — | — | whitelisted |
1452 | svchost.exe | GET | 206 | 23.50.131.85:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/5d32607d-eea9-44fc-ac55-77800b9862a5?P1=1746050955&P2=404&P3=2&P4=DQSDNtRMlfeCo9NDYKa4mQFlPO5PCWZja3b6DPu5Iy58V%2b4GgI1q4chg%2f5JMEf8dh%2fUBwNo07B8c5Cwakx1kbw%3d%3d | unknown | — | — | whitelisted |
1452 | svchost.exe | GET | 206 | 23.50.131.85:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/5d32607d-eea9-44fc-ac55-77800b9862a5?P1=1746050955&P2=404&P3=2&P4=DQSDNtRMlfeCo9NDYKa4mQFlPO5PCWZja3b6DPu5Iy58V%2b4GgI1q4chg%2f5JMEf8dh%2fUBwNo07B8c5Cwakx1kbw%3d%3d | unknown | — | — | whitelisted |
1452 | svchost.exe | GET | 206 | 23.50.131.85:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/5d32607d-eea9-44fc-ac55-77800b9862a5?P1=1746050955&P2=404&P3=2&P4=DQSDNtRMlfeCo9NDYKa4mQFlPO5PCWZja3b6DPu5Iy58V%2b4GgI1q4chg%2f5JMEf8dh%2fUBwNo07B8c5Cwakx1kbw%3d%3d | unknown | — | — | whitelisted |
1452 | svchost.exe | GET | 200 | 23.50.131.85:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/bf8090eb-6e5c-4c51-9250-5bf9b46cf160?P1=1746050955&P2=404&P3=2&P4=nCAm115PiMamcTfGp2nOiJAQ4NBjpvhAQOMsocl2vgF2QtMR4wP0WWSQXhJdkfnCZwP63aZQEU1a3ud19uyn4Q%3d%3d | unknown | — | — | whitelisted |
1452 | svchost.exe | GET | 206 | 23.50.131.85:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/5d32607d-eea9-44fc-ac55-77800b9862a5?P1=1746050955&P2=404&P3=2&P4=DQSDNtRMlfeCo9NDYKa4mQFlPO5PCWZja3b6DPu5Iy58V%2b4GgI1q4chg%2f5JMEf8dh%2fUBwNo07B8c5Cwakx1kbw%3d%3d | unknown | — | — | whitelisted |
1452 | svchost.exe | GET | 206 | 23.50.131.85:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/5d32607d-eea9-44fc-ac55-77800b9862a5?P1=1746050955&P2=404&P3=2&P4=DQSDNtRMlfeCo9NDYKa4mQFlPO5PCWZja3b6DPu5Iy58V%2b4GgI1q4chg%2f5JMEf8dh%2fUBwNo07B8c5Cwakx1kbw%3d%3d | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 2.19.11.105:80 | crl.microsoft.com | Elisa Oyj | NL | whitelisted |
— | — | 2.23.246.101:80 | www.microsoft.com | Ooredoo Q.S.C. | QA | whitelisted |
2104 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6480 | msedge.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
7340 | msedge.exe | 31.216.144.5:443 | mega.nz | Datacenter Luxembourg S.A. | LU | whitelisted |
7340 | msedge.exe | 13.107.42.16:443 | config.edge.skype.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
7340 | msedge.exe | 150.171.28.11:443 | edge.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
config.edge.skype.com |
| whitelisted |
mega.nz |
| whitelisted |
edge.microsoft.com |
| whitelisted |
business.bing.com |
| whitelisted |
edge-mobile-static.azureedge.net |
| whitelisted |
www.bing.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
7340 | msedge.exe | Misc activity | ET FILE_SHARING File Sharing Related Domain in DNS Lookup (mega .nz) |
7340 | msedge.exe | Misc activity | ET FILE_SHARING File Sharing Related Domain in DNS Lookup (mega .nz) |
7340 | msedge.exe | Misc activity | ET FILE_SHARING Observed DNS Query to Filesharing Service (mega .co .nz) |
7340 | msedge.exe | Misc activity | ET FILE_SHARING Observed DNS Query to Filesharing Service (mega .co .nz) |
7340 | msedge.exe | Misc activity | ET FILE_SHARING File Sharing Domain Observed in TLS SNI (mega .nz) |
7340 | msedge.exe | Misc activity | ET FILE_SHARING File Sharing Domain Observed in TLS SNI (mega .nz) |
7340 | msedge.exe | Misc activity | ET FILE_SHARING File Sharing Related Domain in DNS Lookup (mega .nz) |
7340 | msedge.exe | Misc activity | ET FILE_SHARING Observed DNS Query to Filesharing Service (mega .co .nz) |
7340 | msedge.exe | Misc activity | ET FILE_SHARING File Sharing Related Domain in DNS Lookup (mega .nz) |
7340 | msedge.exe | Misc activity | ET FILE_SHARING File Sharing Domain Observed in TLS SNI (mega .nz) |