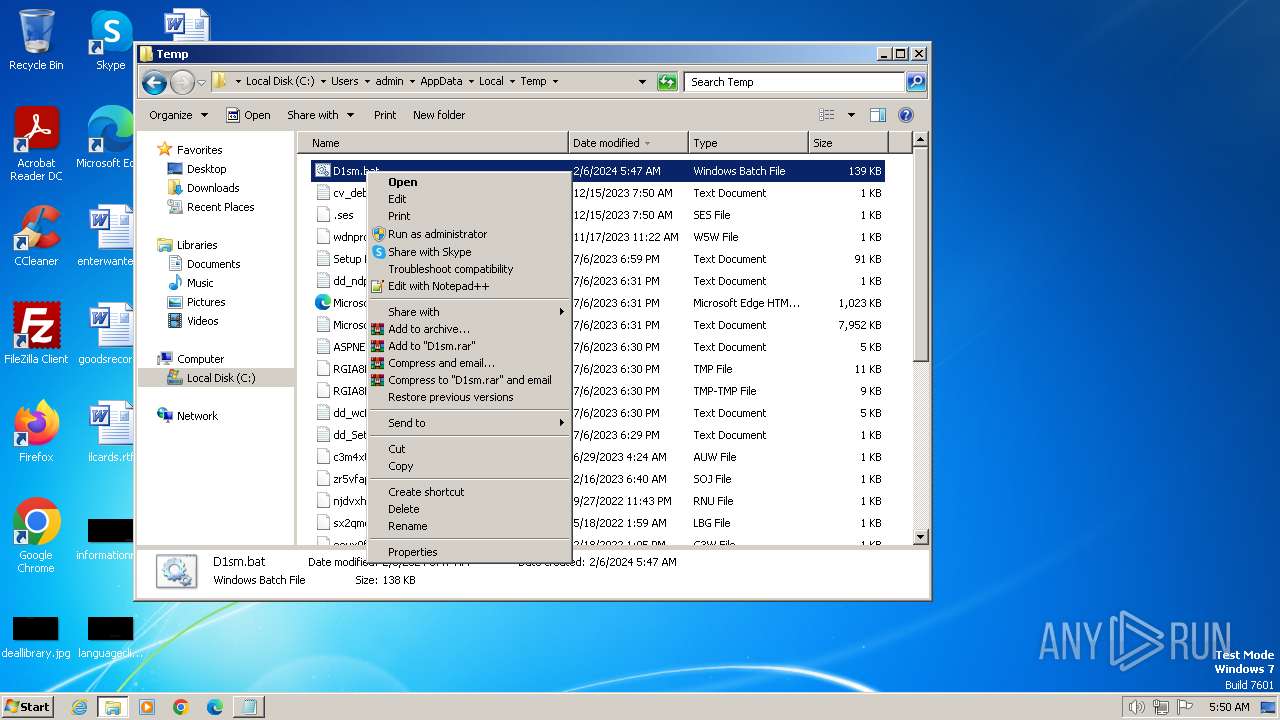
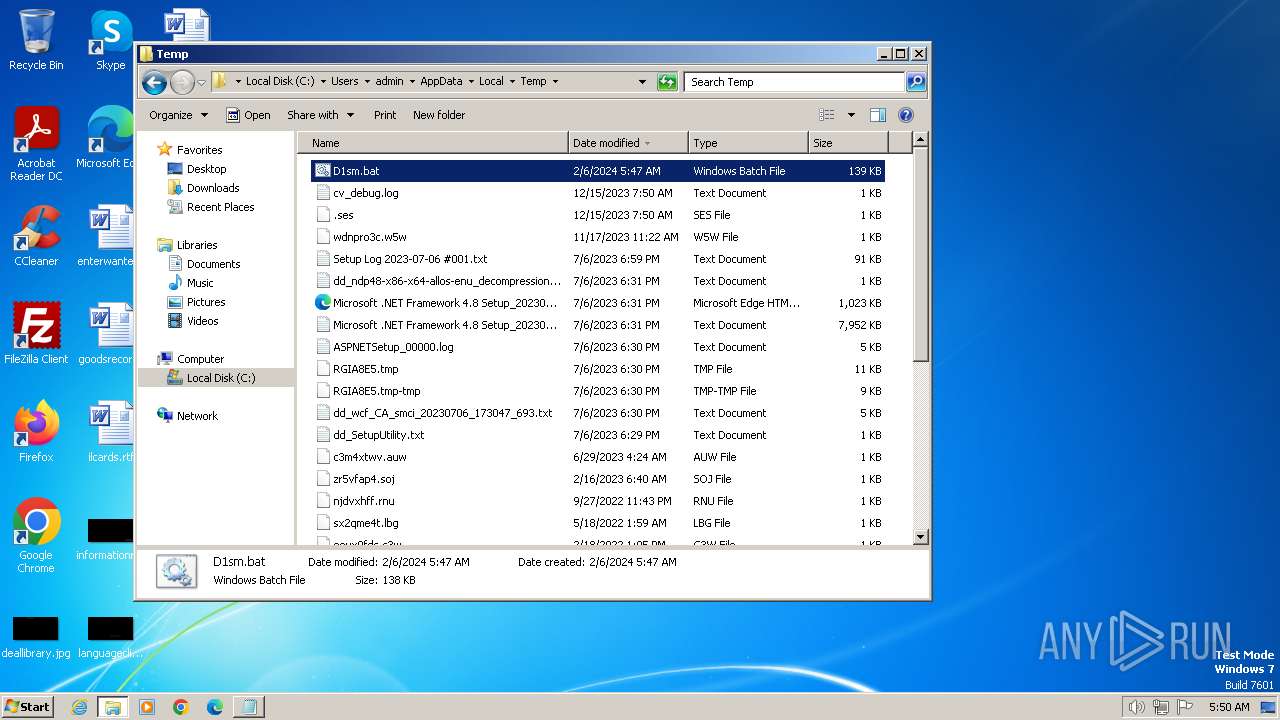
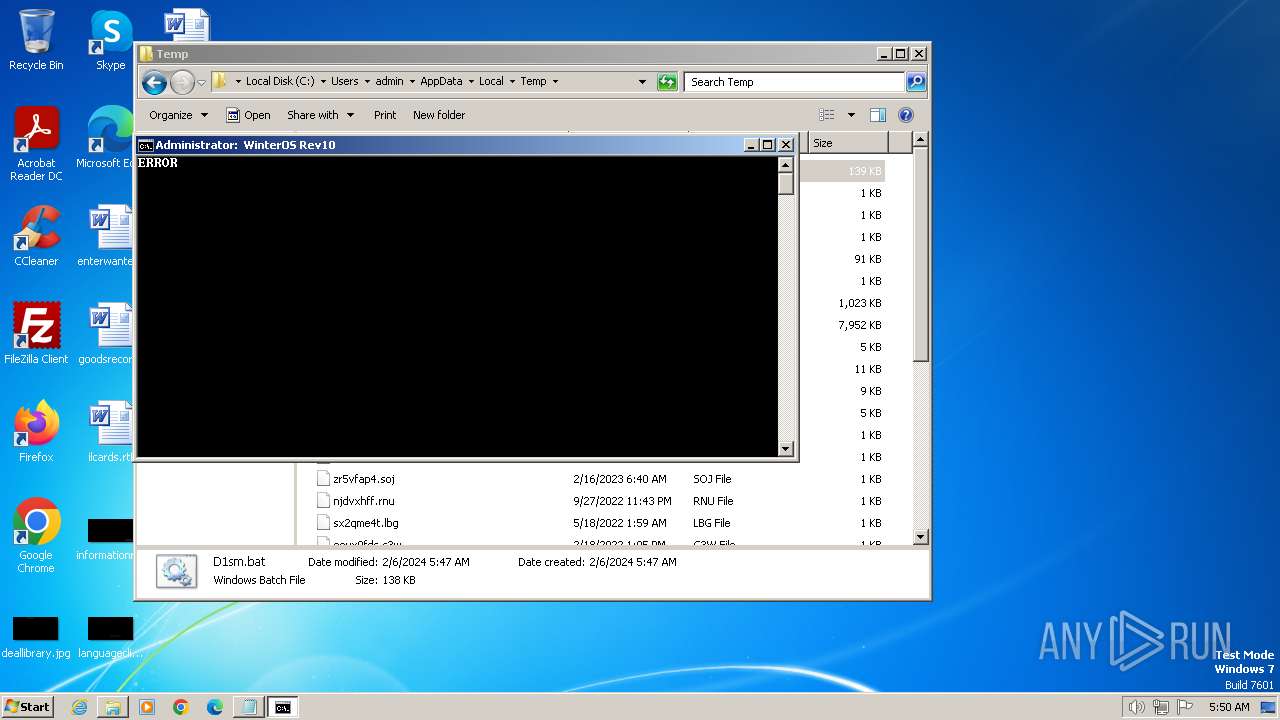
| File name: | D1sm.bat |
| Full analysis: | https://app.any.run/tasks/ab0b5453-62a9-4754-a4c8-f959b99232a4 |
| Verdict: | Malicious activity |
| Analysis date: | February 06, 2024, 05:47:48 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | text/plain |
| File info: | Little-endian UTF-16 Unicode text, with very long lines, with no line terminators |
| MD5: | D2CAAE5B89EC9681F9BFC0042EED33B3 |
| SHA1: | A7D592B29A854FE266DD8EB019BC40A8830AE7CB |
| SHA256: | B874845DD6798B0A358CF5C6494BC1B32C060C1511716B8B3A91A8FAB89394AB |
| SSDEEP: | 384:B+1MT/lJ0oYZff6M0lOzI7zGQ+J1vksJNETtPshnjI2i/2bb2tmB2:B+6lJ7xOzI/5+J1Tz2tkhjRi42tmB2 |
MALICIOUS
Uses sleep, probably for evasion detection (SCRIPT)
- wscript.exe (PID: 980)
SUSPICIOUS
Application launched itself
- cmd.exe (PID: 3212)
- cmd.exe (PID: 3684)
- cmd.exe (PID: 2984)
Starts CMD.EXE for commands execution
- cmd.exe (PID: 3212)
- cscript.exe (PID: 3940)
- cmd.exe (PID: 3684)
- cmd.exe (PID: 2984)
- cscript.exe (PID: 952)
Reads the Internet Settings
- cscript.exe (PID: 3940)
- cscript.exe (PID: 952)
Executing commands from a ".bat" file
- cscript.exe (PID: 3940)
- cscript.exe (PID: 952)
Runs shell command (SCRIPT)
- cscript.exe (PID: 3940)
- cscript.exe (PID: 952)
The process executes VB scripts
- cmd.exe (PID: 3276)
- cmd.exe (PID: 4068)
INFO
Manual execution by a user
- explorer.exe (PID: 3412)
- cmd.exe (PID: 3212)
- cmd.exe (PID: 3276)
- wscript.exe (PID: 980)
- cmd.exe (PID: 4068)
Reads security settings of Internet Explorer
- cscript.exe (PID: 3940)
- cscript.exe (PID: 952)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .txt | | | Text - UTF-16 (LE) encoded (66.6) |
|---|---|---|
| .mp3 | | | MP3 audio (33.3) |
Total processes
69
Monitored processes
16
Malicious processes
2
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 952 | cscript.exe //b "C:\Users\admin\AppData\Local\Temp\tmp.vbs" | C:\Windows\System32\cscript.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Console Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 980 | "C:\Windows\System32\WScript.exe" "C:\Users\admin\AppData\Local\Temp\Space.vbs" | C:\Windows\System32\wscript.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 1380 | "C:\Windows\system32\NOTEPAD.EXE" "C:\Users\admin\AppData\Local\Temp\D1sm.bat.txt" | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1956 | reg query "HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\OEMInformation" /v "Model" | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2124 | C:\Windows\system32\cmd.exe /c reg query "HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\OEMInformation" /v "Model" 2>NUL | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2984 | "C:\Windows\System32\cmd.exe" /c "C:\Users\admin\AppData\Local\Temp\D1sm.bat" | C:\Windows\System32\cmd.exe | cscript.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 3221225786 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 3212 | "C:\Windows\System32\cmd.exe" /C "C:\Users\admin\AppData\Local\Temp\D1sm.bat" | C:\Windows\System32\cmd.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 3221225786 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 3276 | C:\Windows\system32\cmd.exe /c ""C:\Users\admin\AppData\Local\Temp\D1sm.bat" " | C:\Windows\System32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 3412 | "C:\Windows\explorer.exe" | C:\Windows\explorer.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3484 | C:\Windows\system32\cmd.exe /c reg query "HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\OEMInformation" /v "Model" 2>NUL | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
Total events
633
Read events
617
Write events
16
Delete events
0
Modification events
| (PID) Process: | (3940) cscript.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (3940) cscript.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (3940) cscript.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (3940) cscript.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (952) cscript.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (952) cscript.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (952) cscript.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (952) cscript.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
Executable files
0
Suspicious files
0
Text files
5
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3212 | cmd.exe | C:\Users\admin\AppData\Local\Temp\Space.vbs | text | |
MD5:B778C0DC1BE72A073AF8D2B071B7FFE6 | SHA256:3947ACBF485BFDA0B12BE11262A8795D4EB27687B1D698C124861D72A1A7795B | |||
| 4068 | cmd.exe | C:\Users\admin\AppData\Local\Temp\tmp.vbs | text | |
MD5:95768B3B2A6BF7199DA4E01EB3867B11 | SHA256:6FF5990E97ABA90B7A295BCB4F5659E54A8F4A1D6D7C801B894F28C1AC317B31 | |||
| 3276 | cmd.exe | C:\Users\admin\AppData\Local\Temp\tmp.vbs | text | |
MD5:95768B3B2A6BF7199DA4E01EB3867B11 | SHA256:6FF5990E97ABA90B7A295BCB4F5659E54A8F4A1D6D7C801B894F28C1AC317B31 | |||
| 3684 | cmd.exe | C:\Users\admin\AppData\Local\Temp\Space.vbs | text | |
MD5:B778C0DC1BE72A073AF8D2B071B7FFE6 | SHA256:3947ACBF485BFDA0B12BE11262A8795D4EB27687B1D698C124861D72A1A7795B | |||
| 2984 | cmd.exe | C:\Users\admin\AppData\Local\Temp\Space.vbs | text | |
MD5:B778C0DC1BE72A073AF8D2B071B7FFE6 | SHA256:3947ACBF485BFDA0B12BE11262A8795D4EB27687B1D698C124861D72A1A7795B | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
5
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 224.0.0.252:5355 | — | — | — | unknown |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |