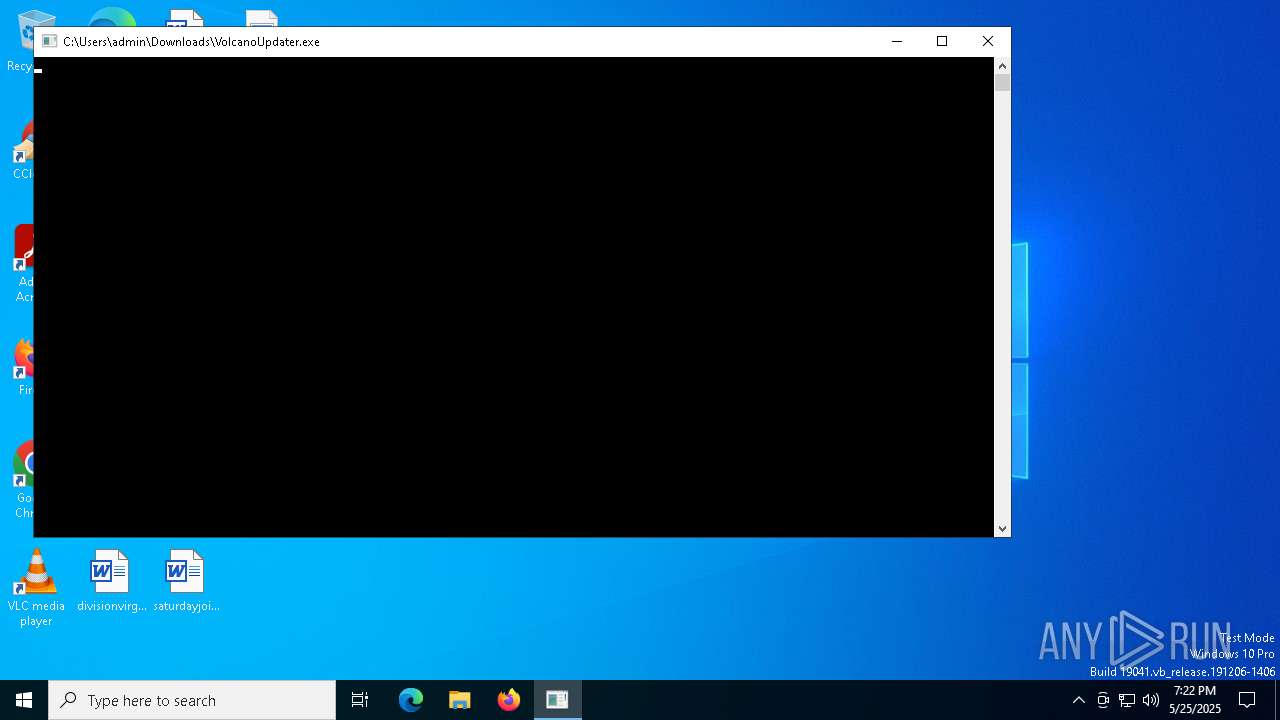
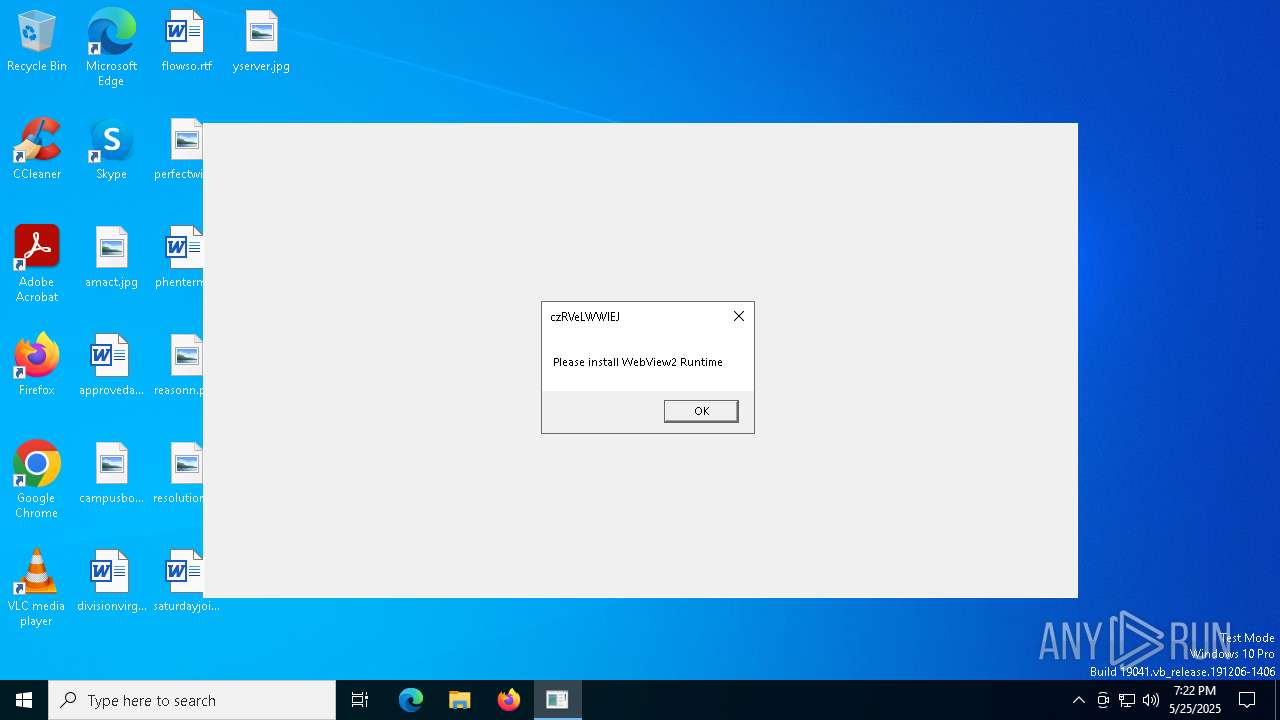
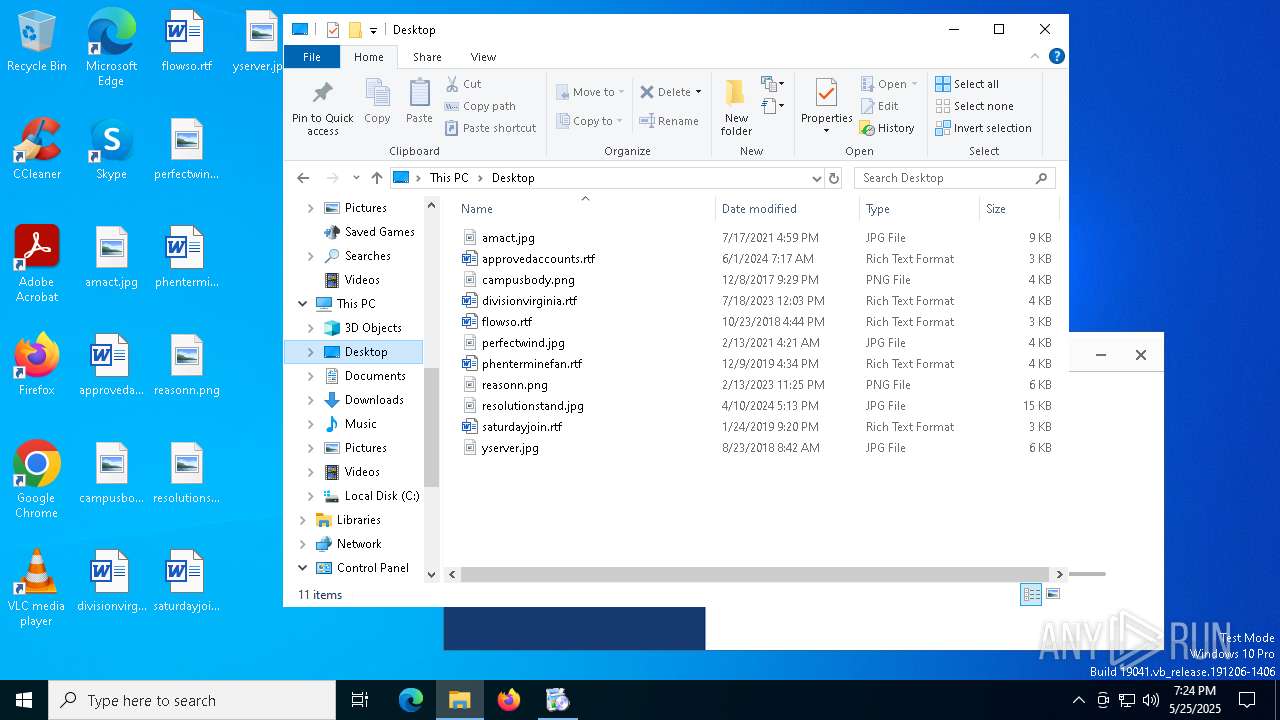
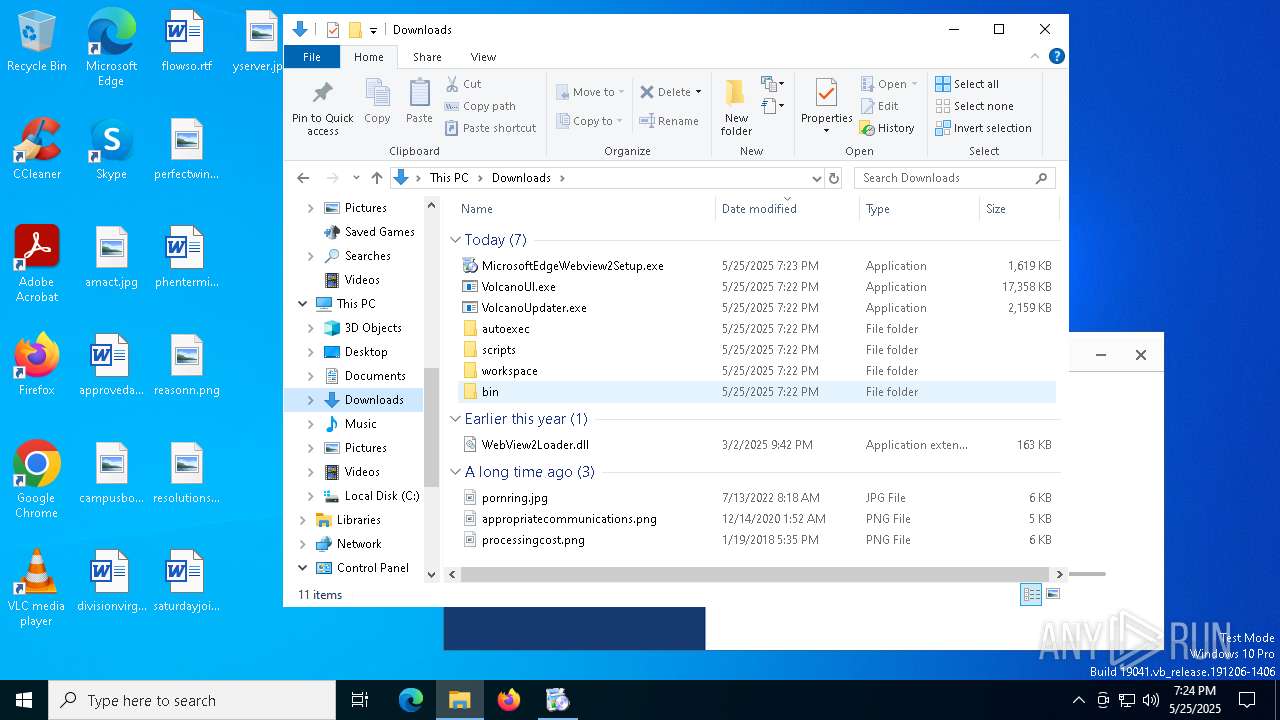
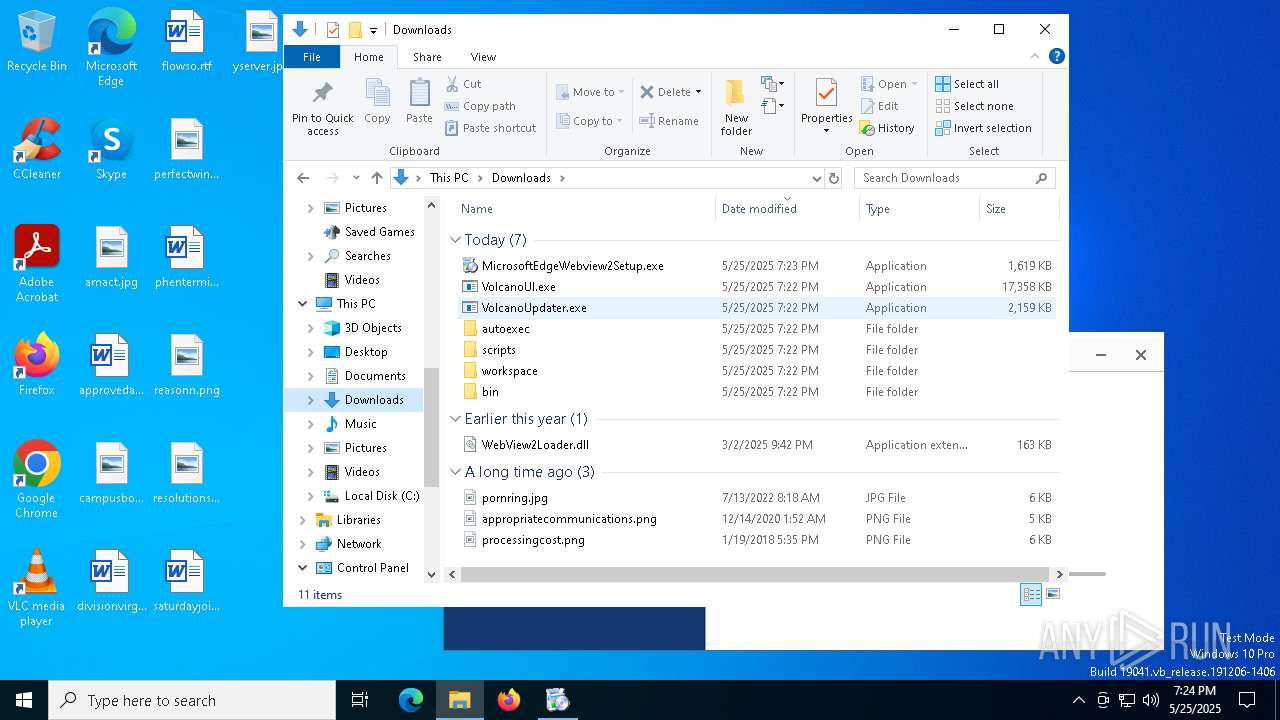
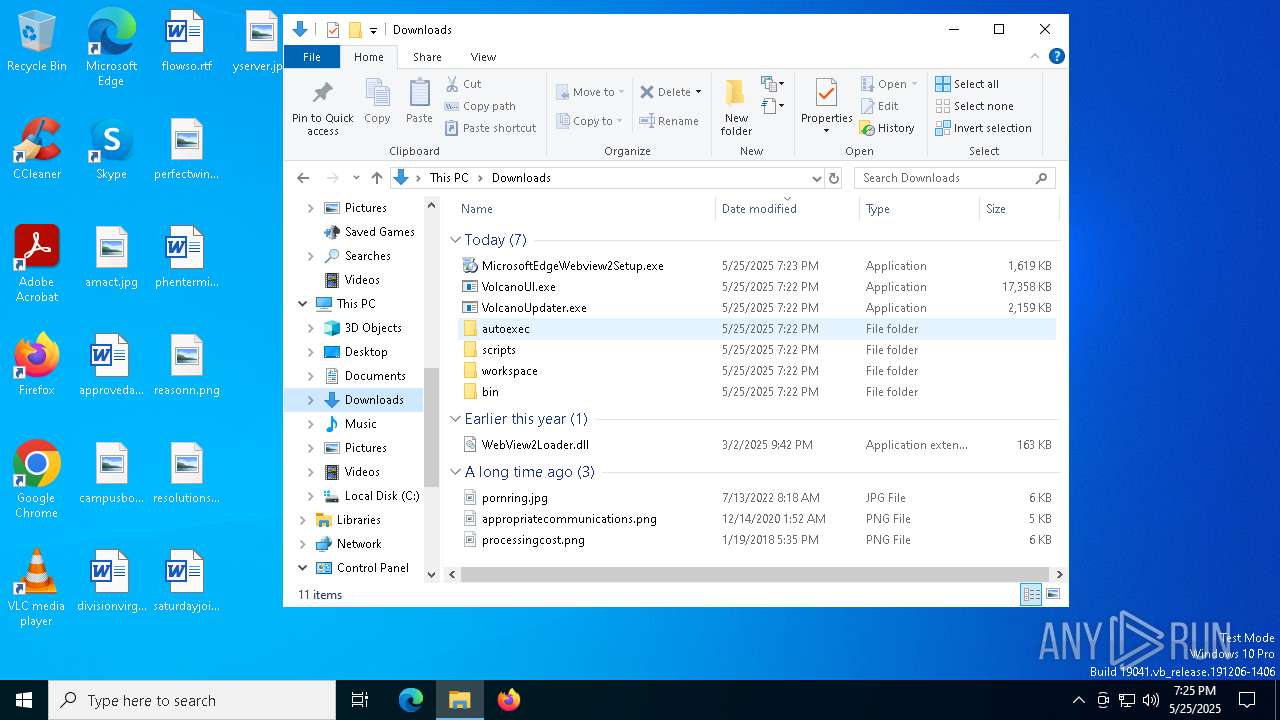
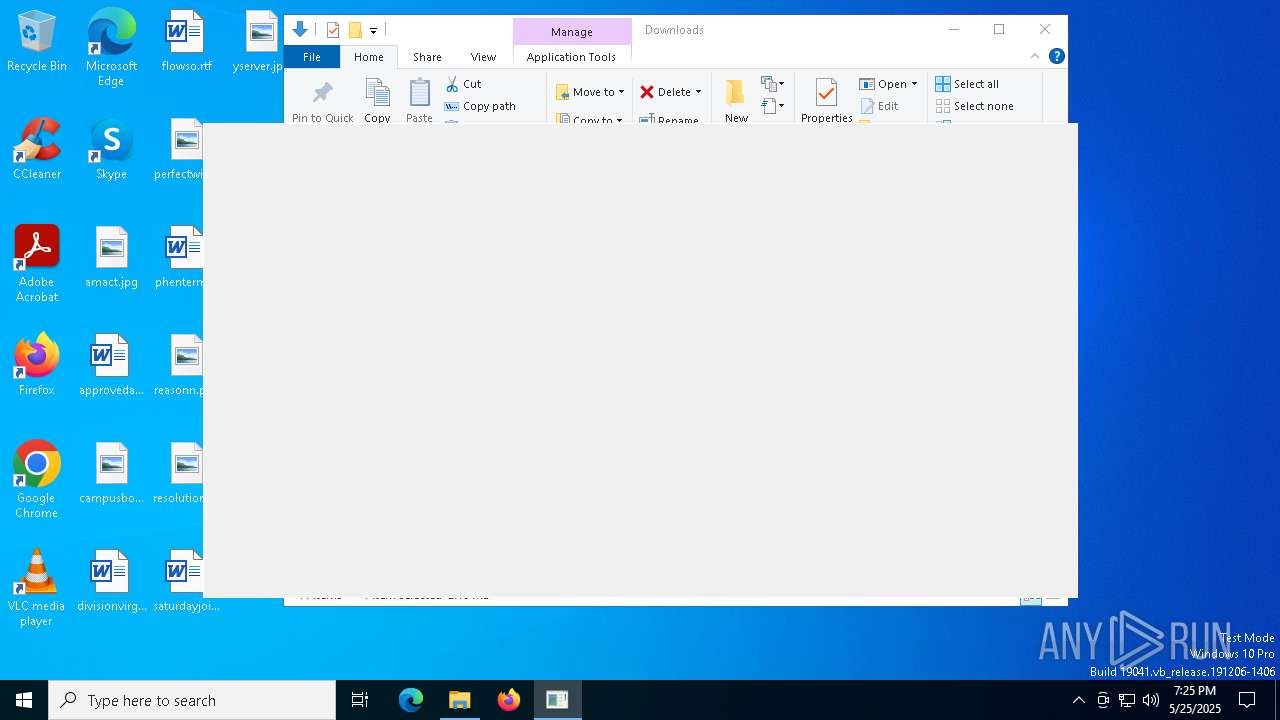
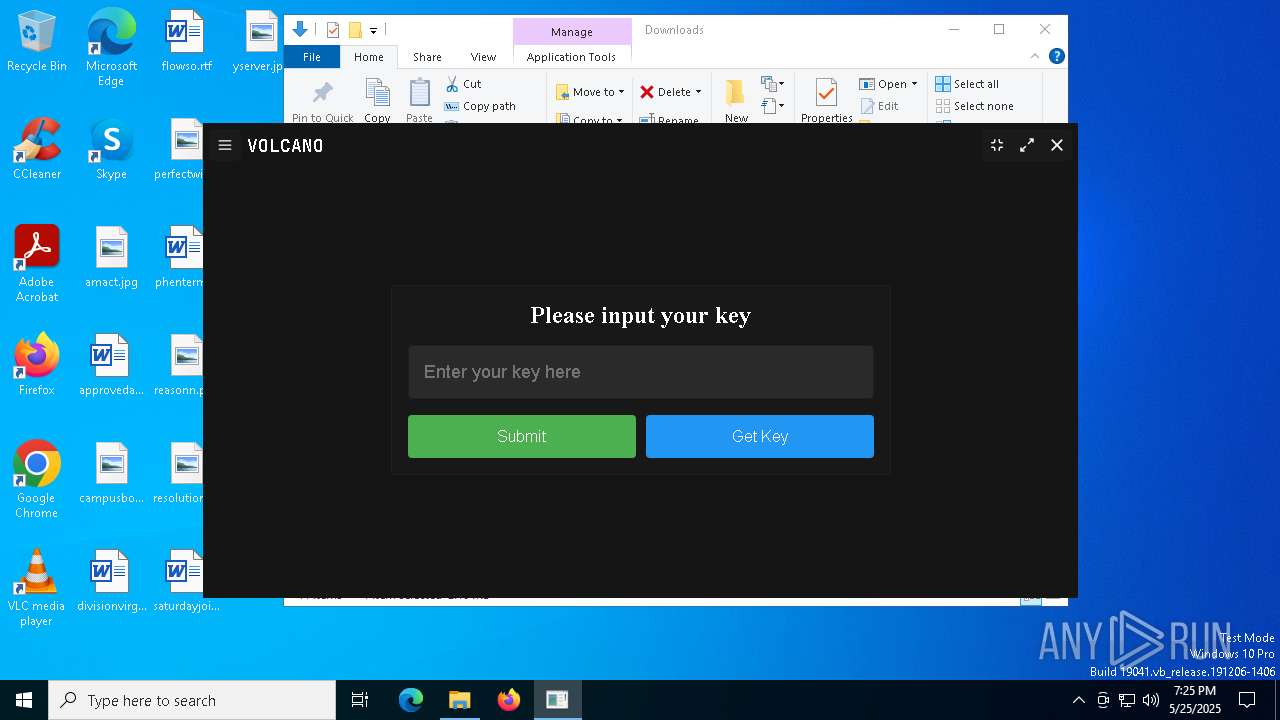
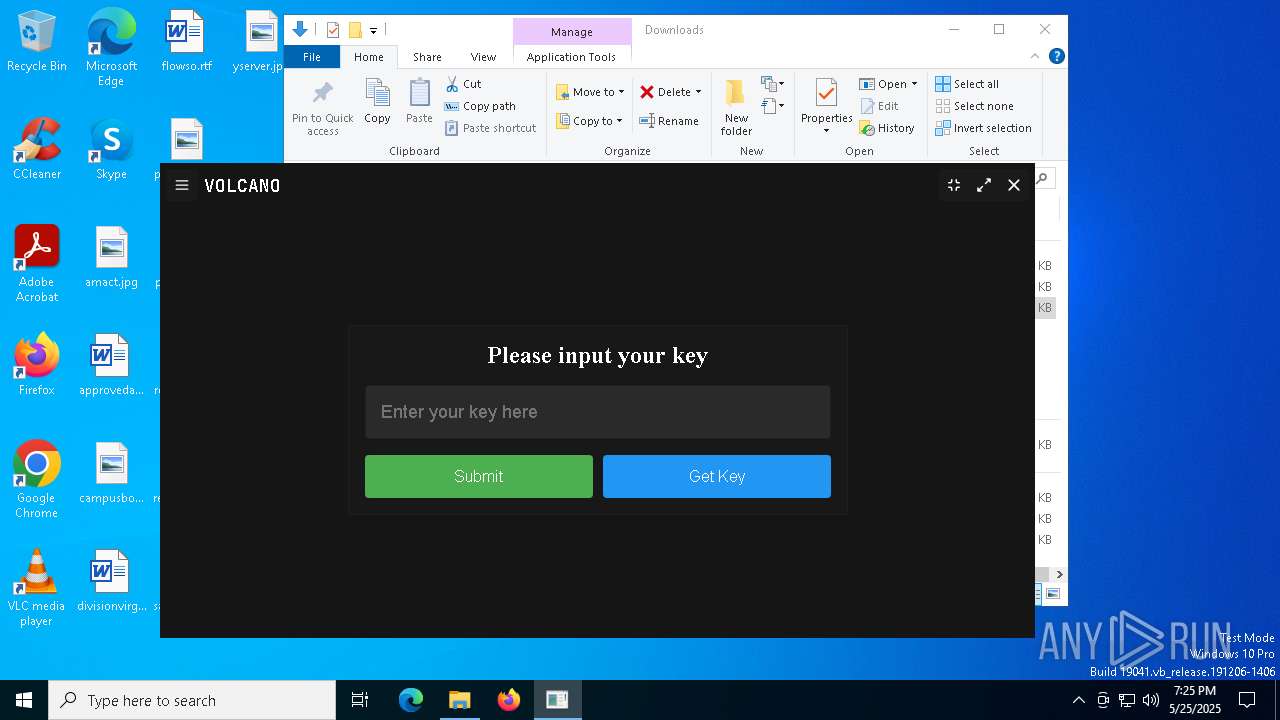
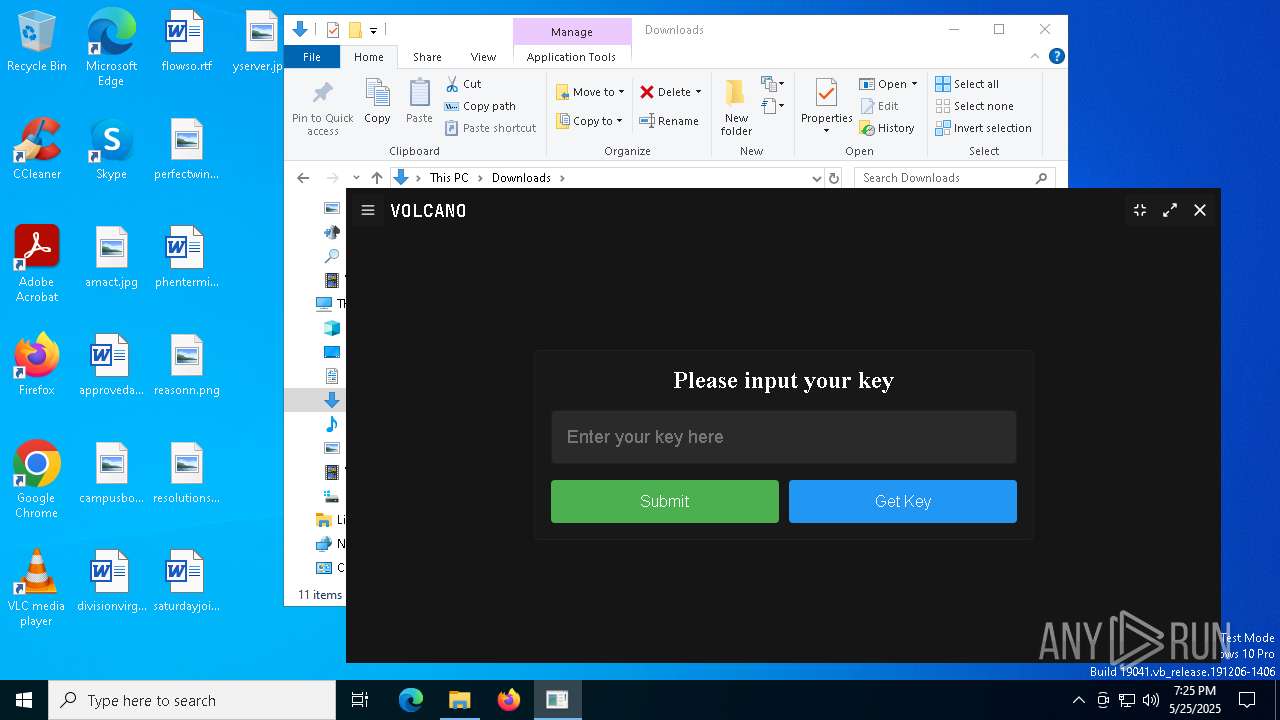
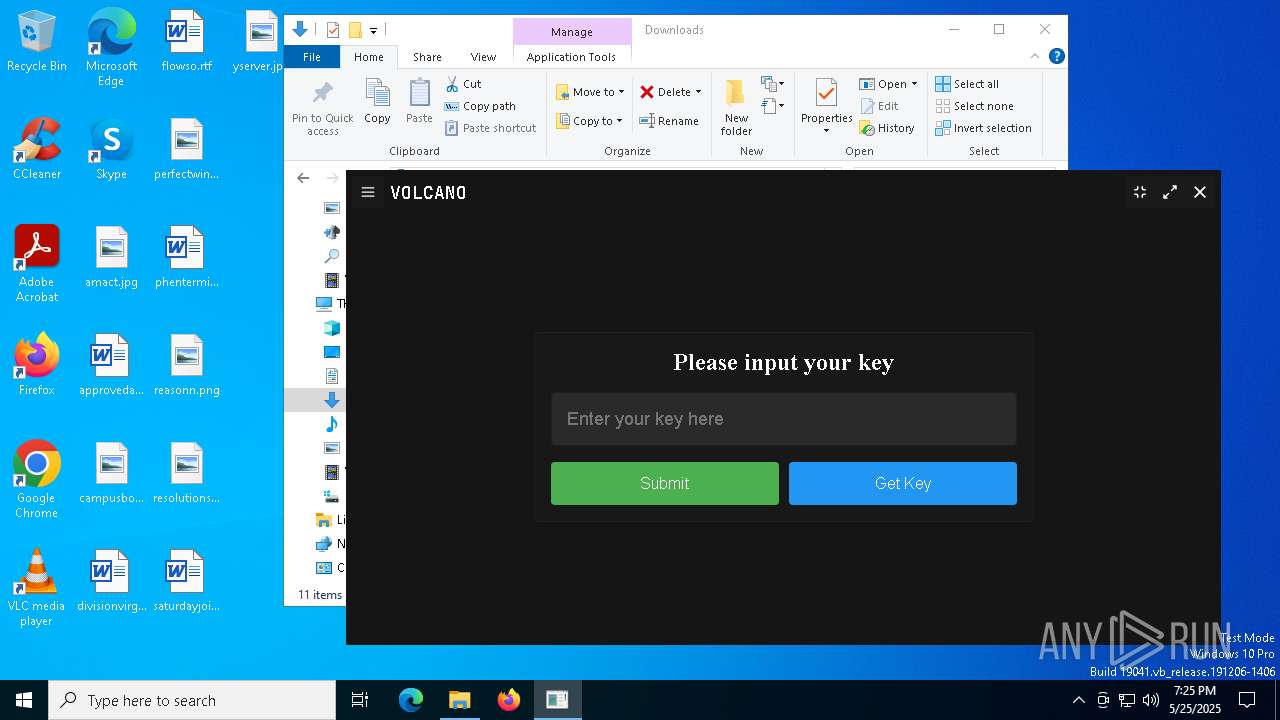
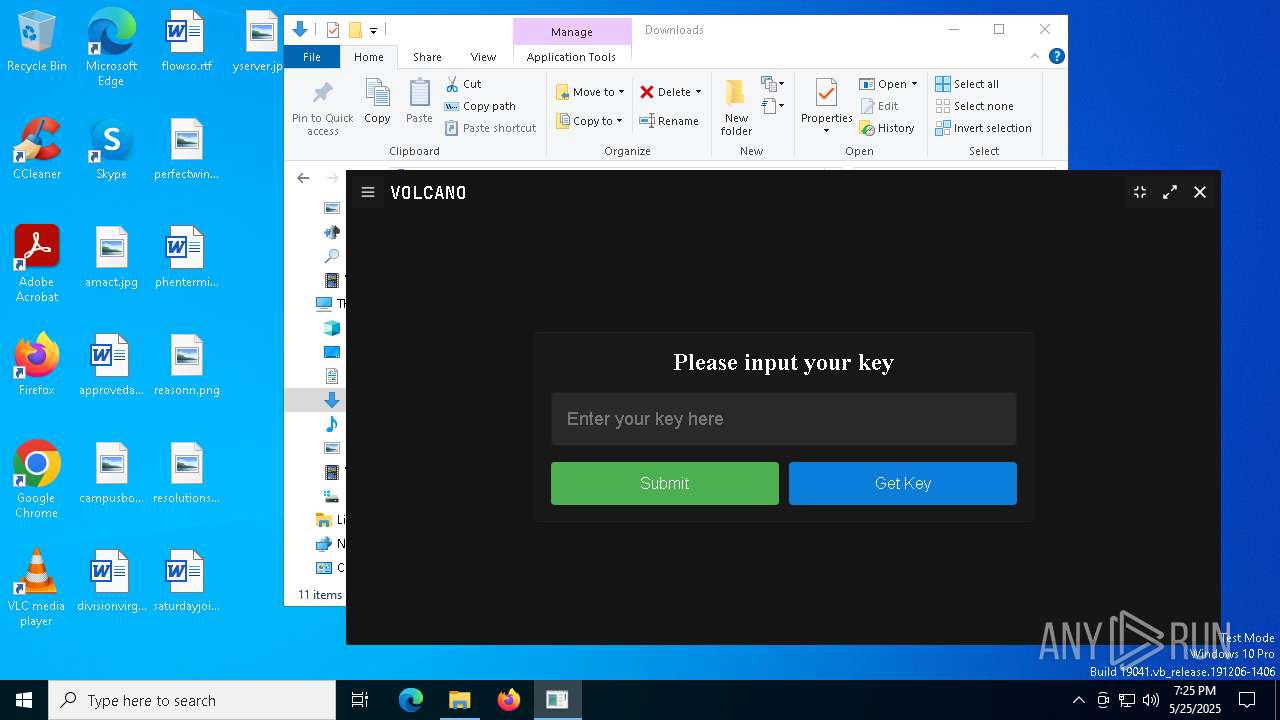
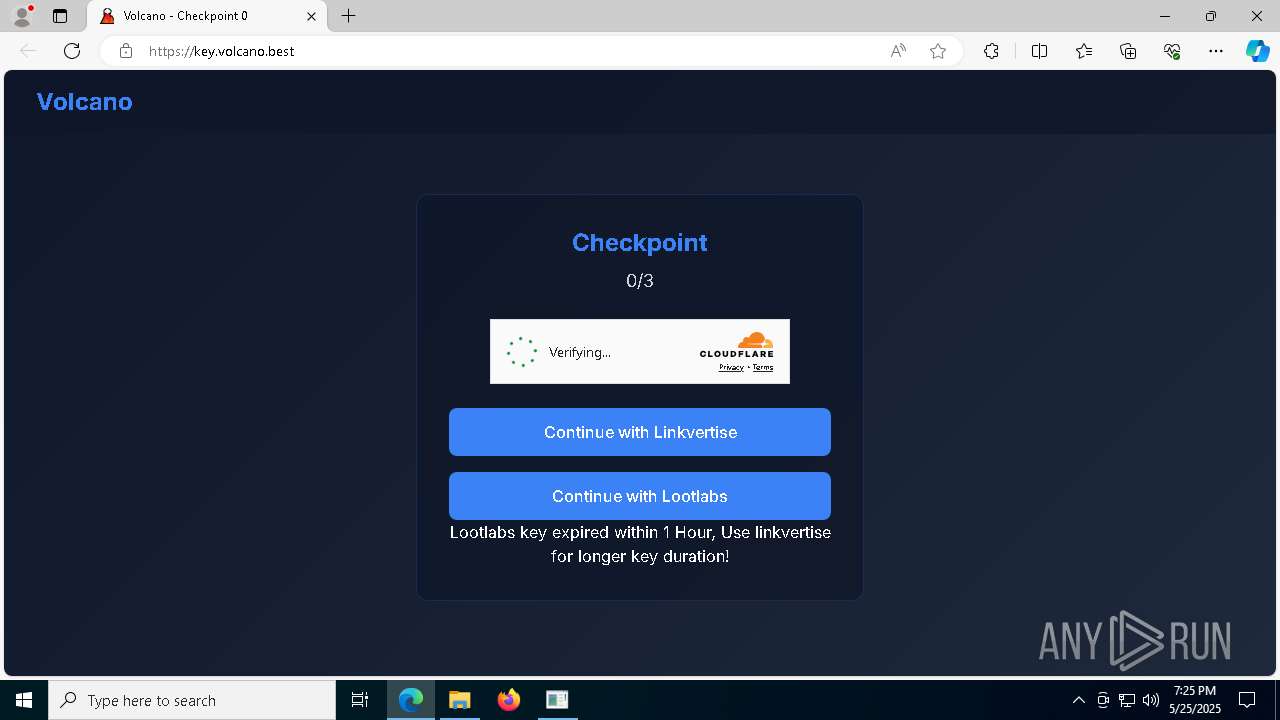
| File name: | VolcanoUpdater.exe |
| Full analysis: | https://app.any.run/tasks/f6a9fedd-d4d0-46a0-9188-0a4c7871fc88 |
| Verdict: | Malicious activity |
| Analysis date: | May 25, 2025, 19:22:39 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32+ executable (console) x86-64, for MS Windows, 8 sections |
| MD5: | 68EC393FCAA470A36055026FC029E0FD |
| SHA1: | 1BB4020B2EC2A9EEC6E186FD6F5A358D42D9FC91 |
| SHA256: | B85D05A566C6CCCFC46BF8A59926F13998B21258F854F66F8A26B21255CB8947 |
| SSDEEP: | 98304:Ak2TmcPuBdFdfWLchV20tmeqJerNo82b9k+YZX/VZHrH9N/mgLOqirBwTpKiDNIQ:YFcpHb/uY |
MALICIOUS
Changes the autorun value in the registry
- MicrosoftEdgeUpdate.exe (PID: 300)
SUSPICIOUS
Executable content was dropped or overwritten
- VolcanoUpdater.exe (PID: 1324)
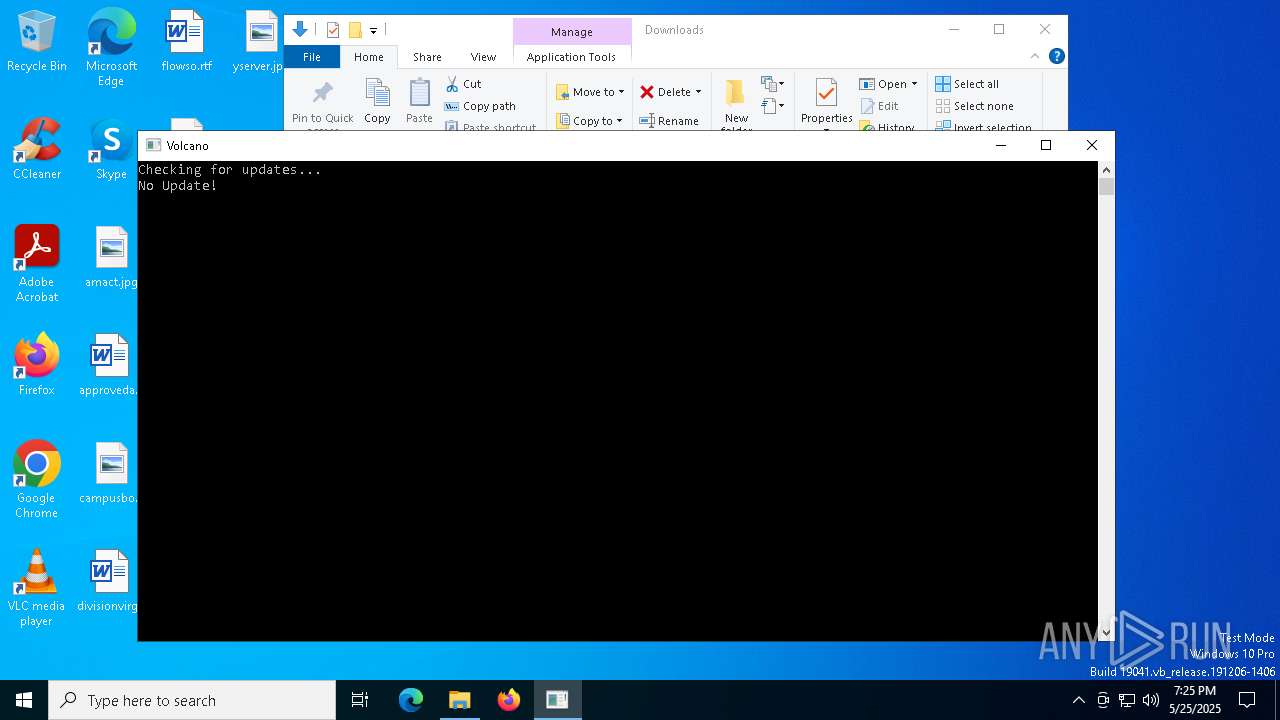
- VolcanoUI.exe (PID: 1056)
- MicrosoftEdgeWebview2Setup.exe (PID: 6368)
- MicrosoftEdgeUpdate.exe (PID: 300)
- MicrosoftEdge_X64_136.0.3240.92.exe (PID: 6488)
- setup.exe (PID: 7188)
Reads the date of Windows installation
- VolcanoUpdater.exe (PID: 1324)
Reads security settings of Internet Explorer
- VolcanoUpdater.exe (PID: 1324)
- MicrosoftEdgeUpdate.exe (PID: 300)
Reads the BIOS version
- VolcanoUI.exe (PID: 1056)
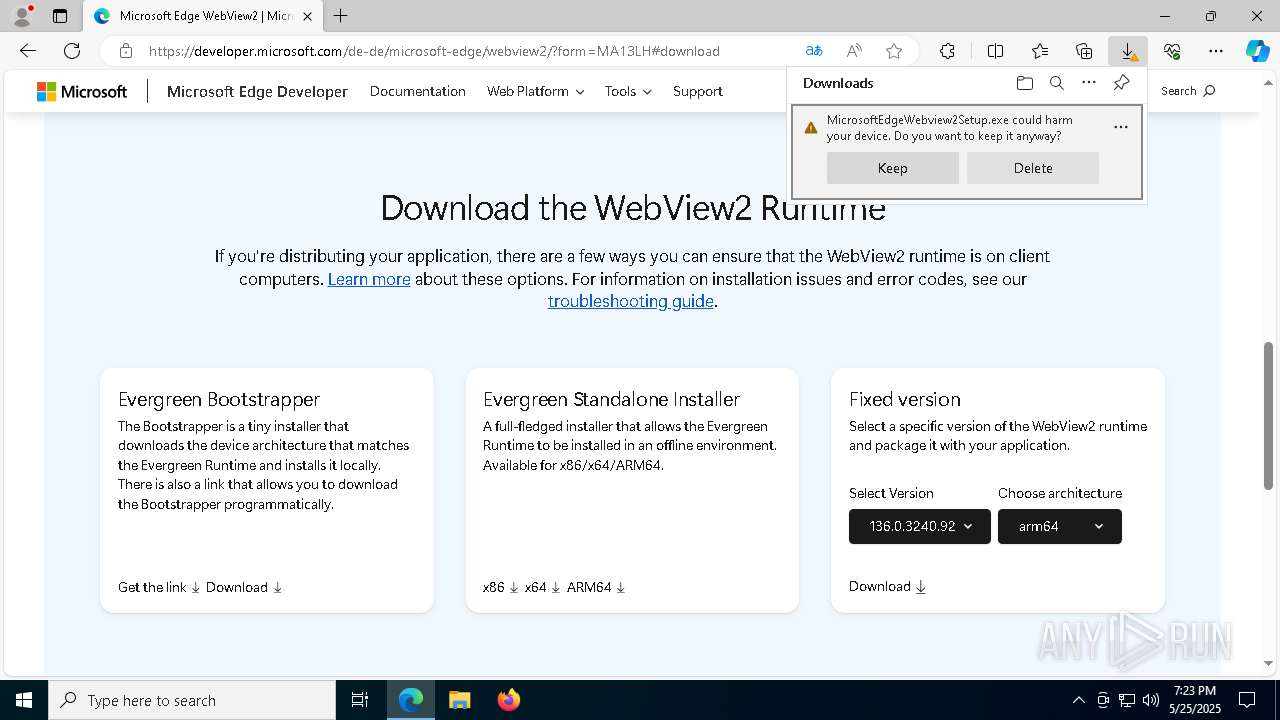
Process drops legitimate windows executable
- VolcanoUI.exe (PID: 1056)
- MicrosoftEdgeWebview2Setup.exe (PID: 6368)
- msedge.exe (PID: 1012)
- MicrosoftEdgeUpdate.exe (PID: 300)
- msedge.exe (PID: 1696)
Starts a Microsoft application from unusual location
- MicrosoftEdgeUpdate.exe (PID: 300)
Starts itself from another location
- MicrosoftEdgeUpdate.exe (PID: 300)
Creates/Modifies COM task schedule object
- MicrosoftEdgeUpdateComRegisterShell64.exe (PID: 7620)
- MicrosoftEdgeUpdateComRegisterShell64.exe (PID: 2552)
- MicrosoftEdgeUpdate.exe (PID: 900)
- MicrosoftEdgeUpdateComRegisterShell64.exe (PID: 6944)
Application launched itself
- MicrosoftEdgeUpdate.exe (PID: 7484)
- setup.exe (PID: 7188)
- msedgewebview2.exe (PID: 5236)
INFO
Checks supported languages
- VolcanoUpdater.exe (PID: 1324)
- VolcanoUI.exe (PID: 1056)
- identity_helper.exe (PID: 8036)
- MicrosoftEdgeWebview2Setup.exe (PID: 6368)
- MicrosoftEdgeUpdate.exe (PID: 300)
- MicrosoftEdgeUpdate.exe (PID: 900)
- MicrosoftEdgeUpdateComRegisterShell64.exe (PID: 2552)
- MicrosoftEdgeUpdateComRegisterShell64.exe (PID: 6944)
- MicrosoftEdgeUpdateComRegisterShell64.exe (PID: 7620)
- MicrosoftEdgeUpdate.exe (PID: 5056)
- MicrosoftEdgeUpdate.exe (PID: 7484)
- identity_helper.exe (PID: 5048)
- MicrosoftEdgeUpdate.exe (PID: 6840)
Process checks computer location settings
- VolcanoUpdater.exe (PID: 1324)
- MicrosoftEdgeUpdate.exe (PID: 300)
Reads the computer name
- VolcanoUpdater.exe (PID: 1324)
- VolcanoUI.exe (PID: 1056)
- identity_helper.exe (PID: 8036)
- MicrosoftEdgeUpdate.exe (PID: 300)
- MicrosoftEdgeUpdateComRegisterShell64.exe (PID: 2552)
- MicrosoftEdgeUpdate.exe (PID: 900)
- MicrosoftEdgeUpdateComRegisterShell64.exe (PID: 6944)
- MicrosoftEdgeUpdate.exe (PID: 5056)
- MicrosoftEdgeUpdateComRegisterShell64.exe (PID: 7620)
- MicrosoftEdgeUpdate.exe (PID: 6840)
- MicrosoftEdgeUpdate.exe (PID: 7484)
- identity_helper.exe (PID: 5048)
The sample compiled with english language support
- VolcanoUI.exe (PID: 1056)
- msedge.exe (PID: 1696)
- MicrosoftEdgeWebview2Setup.exe (PID: 6368)
- msedge.exe (PID: 1012)
- MicrosoftEdgeUpdate.exe (PID: 300)
Manual execution by a user
- msedge.exe (PID: 1012)
- VolcanoUpdater.exe (PID: 5576)
Application launched itself
- msedge.exe (PID: 1012)
- msedge.exe (PID: 5260)
Reads Environment values
- identity_helper.exe (PID: 8036)
- MicrosoftEdgeUpdate.exe (PID: 5056)
- identity_helper.exe (PID: 5048)
Executable content was dropped or overwritten
- msedge.exe (PID: 1012)
- msedge.exe (PID: 1696)
Create files in a temporary directory
- MicrosoftEdgeWebview2Setup.exe (PID: 6368)
- MicrosoftEdgeUpdate.exe (PID: 300)
Creates files or folders in the user directory
- MicrosoftEdgeUpdate.exe (PID: 300)
Checks proxy server information
- MicrosoftEdgeUpdate.exe (PID: 7484)
- MicrosoftEdgeUpdate.exe (PID: 5056)
Reads the software policy settings
- MicrosoftEdgeUpdate.exe (PID: 5056)
- MicrosoftEdgeUpdate.exe (PID: 7484)
- slui.exe (PID: 2660)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (87.3) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (6.3) |
| .exe | | | DOS Executable Generic (6.3) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2025:05:06 11:33:46+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 14.38 |
| CodeSize: | 799744 |
| InitializedDataSize: | 262144 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x84b90 |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows command line |
Total processes
244
Monitored processes
107
Malicious processes
4
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 300 | C:\Users\admin\AppData\Local\Temp\EUD500.tmp\MicrosoftEdgeUpdate.exe /installsource taggedmi /install "appguid={F3017226-FE2A-4295-8BDF-00C3A9A7E4C5}&appname=Microsoft%20Edge%20Webview2%20Runtime&needsadmin=prefers" | C:\Users\admin\AppData\Local\Temp\EUD500.tmp\MicrosoftEdgeUpdate.exe | MicrosoftEdgeWebview2Setup.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Update Exit code: 0 Version: 1.3.195.61 Modules
| |||||||||||||||
| 664 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --no-appcompat-clear --disable-gpu-compositing --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=31 --mojo-platform-channel-handle=7384 --field-trial-handle=2292,i,12520877682851872010,12758843426488310366,262144 --variations-seed-version /prefetch:1 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 772 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=5244 --field-trial-handle=2424,i,16534194379772514162,15029697938749614639,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 776 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --lang=en-US --service-sandbox-type=none --no-appcompat-clear --mojo-platform-channel-handle=1504 --field-trial-handle=2292,i,12520877682851872010,12758843426488310366,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 780 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=5256 --field-trial-handle=2424,i,16534194379772514162,15029697938749614639,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 900 | "C:\Users\admin\AppData\Local\Microsoft\EdgeUpdate\MicrosoftEdgeUpdate.exe" /regserver | C:\Users\admin\AppData\Local\Microsoft\EdgeUpdate\MicrosoftEdgeUpdate.exe | — | MicrosoftEdgeUpdate.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Update Exit code: 0 Version: 1.3.195.61 Modules
| |||||||||||||||
| 1012 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --profile-directory=Default | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1056 | "C:\Users\admin\Downloads\VolcanoUI.exe" | C:\Users\admin\Downloads\VolcanoUI.exe | VolcanoUpdater.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 1268 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=gpu-process --no-appcompat-clear --gpu-preferences=WAAAAAAAAADgAAAMAAAAAAAAAAAAAAAAAABgAAAAAAA4AAAAAAAAAAAAAAAEAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAGAAAAAAAAAAYAAAAAAAAAAgAAAAAAAAACAAAAAAAAAAIAAAAAAAAAA== --mojo-platform-channel-handle=2288 --field-trial-handle=2292,i,12520877682851872010,12758843426488310366,262144 --variations-seed-version /prefetch:2 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1324 | "C:\Users\admin\Downloads\VolcanoUpdater.exe" | C:\Users\admin\Downloads\VolcanoUpdater.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
Total events
26 659
Read events
24 804
Write events
1 787
Delete events
68
Modification events
| (PID) Process: | (1012) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (1012) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (1012) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (1012) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (1012) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\LastWasDefault |
| Operation: | write | Name: | S-1-5-21-1693682860-607145093-2874071422-1001 |
Value: 978E130B91942F00 | |||
| (PID) Process: | (1012) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\524950 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {05E0028A-05D0-4017-B648-CFD82288BD8D} | |||
| (PID) Process: | (1012) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\LastWasDefault |
| Operation: | write | Name: | S-1-5-21-1693682860-607145093-2874071422-1001 |
Value: 62FA170B91942F00 | |||
| (PID) Process: | (1012) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\524950 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {3239C7A9-AEDF-4093-ADFE-7AF703E1242D} | |||
| (PID) Process: | (1012) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\524950 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {0D6F36B4-9D7D-4A05-B36D-8AE865D68039} | |||
| (PID) Process: | (1012) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\524950 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {94FA1287-187F-4293-A5CD-BE76573C4F5E} | |||
Executable files
262
Suspicious files
801
Text files
246
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1324 | VolcanoUpdater.exe | C:\Users\admin\Downloads\bin\luau-lifter.exe | executable | |
MD5:F1246A49C8183FCFAC4D7669A6C50881 | SHA256:F5AD37B2293814CE33149CA8D8BF1D673AE0C8F3CB025D7B83954EB0E68E631D | |||
| 1324 | VolcanoUpdater.exe | C:\Users\admin\Downloads\bin\page\assets\azcli-BaLxmfj-.js | text | |
MD5:9F8FD789940B11DD714CB454CFF5B730 | SHA256:D47DC669F95028FDC21BD700095C951072088DDD87B458CAD21466794155C0B5 | |||
| 1324 | VolcanoUpdater.exe | C:\Users\admin\Downloads\bin\page\assets\bat-CFOPXBzS.js | text | |
MD5:4133D4FC714DDF40B53FB1F2F3B15579 | SHA256:471438AB5BC0B324A6B828AC8FA79CD86214FC4C84F4C2E9AAF55CAF56043D92 | |||
| 1324 | VolcanoUpdater.exe | C:\Users\admin\Downloads\bin\version.txt | text | |
MD5:F4F08DCDA80BEBA3E9D2E98C8C8E6854 | SHA256:2097CDEB0DCADAC588E3D8C174ACAE6F3EEE98AF7B0C49FE623B0D19A9D86F72 | |||
| 1324 | VolcanoUpdater.exe | C:\Users\admin\Downloads\bin\page\assets\apex-DyP6w7ZV.js | text | |
MD5:EEA817DCF104C3F416EB86054E4AB065 | SHA256:9E6D5B433394FC90B3A7C58514AB58C6BB49E740EF03E146928A3FD0095AEB68 | |||
| 1324 | VolcanoUpdater.exe | C:\Users\admin\Downloads\bin\page\assets\csp-5Rap-vPy.js | text | |
MD5:8CB672DB7B68FE7F3F7DFCB05AE388A5 | SHA256:C413FA2B83B1A0B1AF76E822721C4A429163B7BCD477B4DEEBD41F7C4E4C8A20 | |||
| 1324 | VolcanoUpdater.exe | C:\Users\admin\Downloads\bin\page\assets\cpp-CLLBncYj.js | text | |
MD5:0F3FCC7CA8691D6CF4FF68B8347D18DD | SHA256:A5FB8F0E4EBFC61B3865C092BD6434A36D24EE6E62477D4ADD55A1D796CD88B4 | |||
| 1324 | VolcanoUpdater.exe | C:\Users\admin\Downloads\bin\page\assets\codicon-DCmgc-ay.ttf | binary | |
MD5:CB7F0A51C106A33FB4ABAB8C454373D8 | SHA256:0F1D5219934E96E83B8DB162D60B4D8C09B5DE1E7D38031CBAFE4A3C0F2889C9 | |||
| 1324 | VolcanoUpdater.exe | C:\Users\admin\Downloads\bin\page\assets\cssMode-wuhyQlOf.js | binary | |
MD5:B63088DC9449EDE74B283708F401FC0F | SHA256:019BE82D233F42BEE2CFA76DD31E3AA42D73C2F6276C7A576677BC7B005D7A38 | |||
| 1324 | VolcanoUpdater.exe | C:\Users\admin\Downloads\bin\page\assets\csharp-dUCx_-0o.js | text | |
MD5:5616EF1623A707EDDFB5641341DB735E | SHA256:DE87D1D2BDCEC69C9A9AB2CE355B9BC638BAC7E4078D303DF89DADCB85F58846 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
17
TCP/UDP connections
195
DNS requests
209
Threats
17
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.48.23.153:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
756 | lsass.exe | GET | 200 | 172.217.16.131:80 | http://c.pki.goog/r/r4.crl | unknown | — | — | whitelisted |
756 | lsass.exe | GET | 200 | 172.217.16.131:80 | http://c.pki.goog/r/gsr1.crl | unknown | — | — | whitelisted |
872 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
872 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
1012 | msedge.exe | GET | 200 | 23.219.150.101:80 | http://www.microsoft.com/pkiops/crl/MicCodSigPCA2011_2011-07-08.crl | unknown | — | — | whitelisted |
7544 | svchost.exe | HEAD | 200 | 2.19.126.157:80 | http://msedge.f.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/3e2fb3dd-6316-4a11-801b-c8c0d21312e9?P1=1748805843&P2=404&P3=2&P4=AmYOFJjeRAQEe%2f%2bBsWvsN1YnZHp2nBIAa18FUX42E3qut374AUu8o1sTHbjvP2ET2ncaHrg6lnD8h2hW2dHqsQ%3d%3d | unknown | — | — | whitelisted |
1012 | msedge.exe | GET | 200 | 2.16.168.124:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
5796 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1040 | RUXIMICS.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.48.23.153:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5496 | MoUsoCoreWorker.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
2112 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1324 | VolcanoUpdater.exe | 104.21.48.1:443 | file.volcano.best | CLOUDFLARENET | — | malicious |
756 | lsass.exe | 172.217.16.131:80 | c.pki.goog | GOOGLE | US | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
file.volcano.best |
| malicious |
c.pki.goog |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
config.edge.skype.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1696 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Azure Front Door domain observed in TLS SNI ( .azurefd .net) |
1696 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Azure Front Door domain observed in TLS SNI ( .azurefd .net) |
1696 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Azure Front Door domain observed in TLS SNI ( .azurefd .net) |
1696 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Azure Front Door domain observed in TLS SNI ( .azurefd .net) |
1696 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Azure Front Door domain observed in TLS SNI ( .azurefd .net) |
1696 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Azure Front Door domain observed in TLS SNI ( .azurefd .net) |
1696 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Azure Front Door domain observed in TLS SNI ( .azurefd .net) |
1696 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Azure Front Door domain observed in TLS SNI ( .azurefd .net) |
7544 | svchost.exe | Misc activity | ET INFO Packed Executable Download |
7384 | msedgewebview2.exe | Generic Protocol Command Decode | SURICATA QUIC failed decrypt |