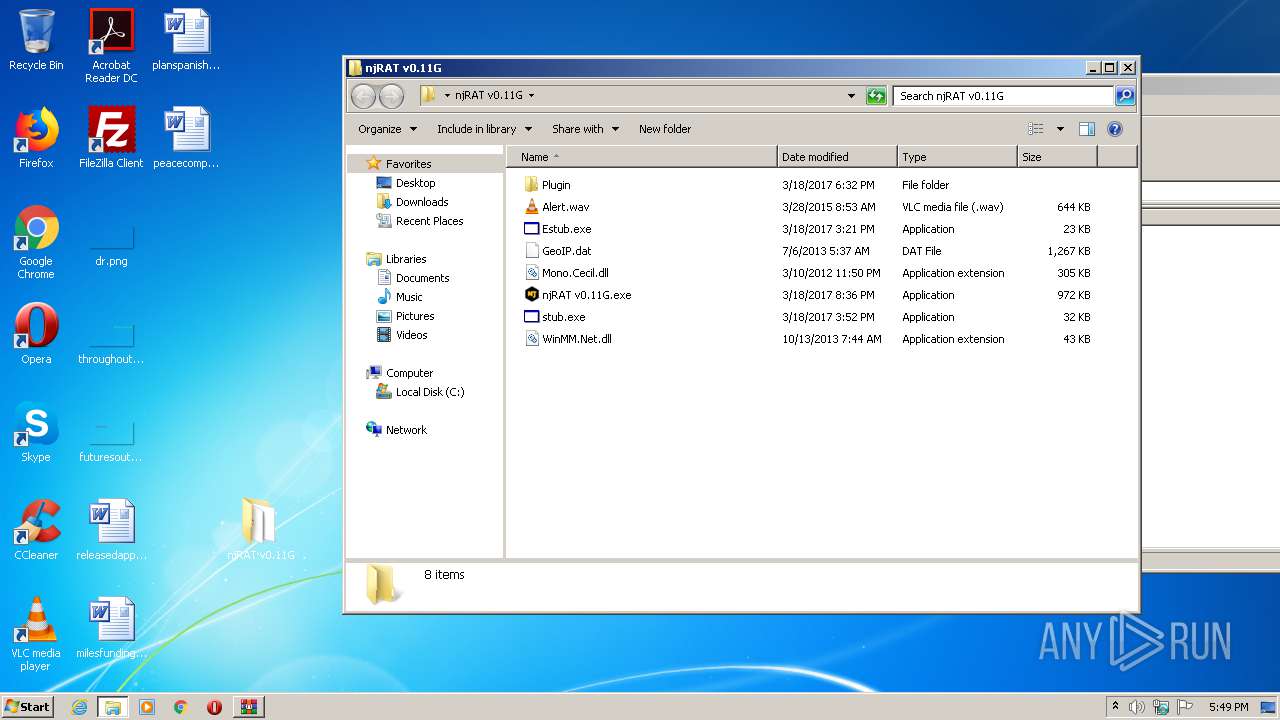
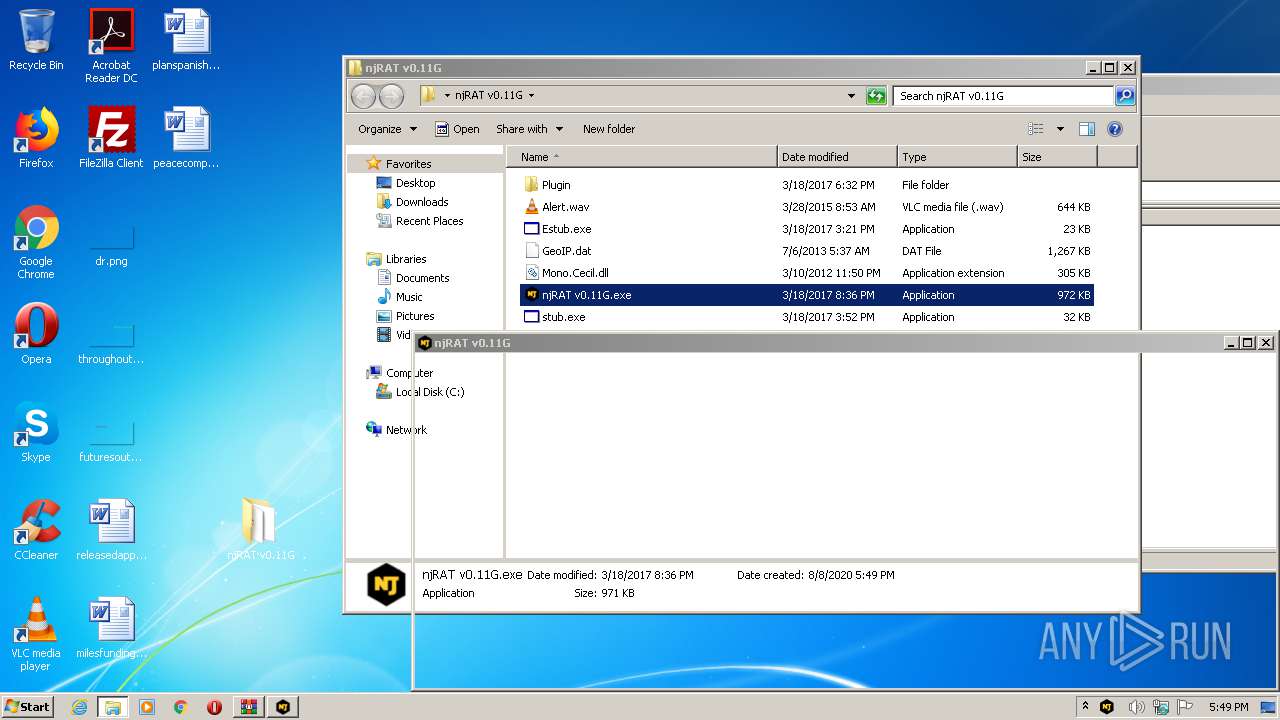
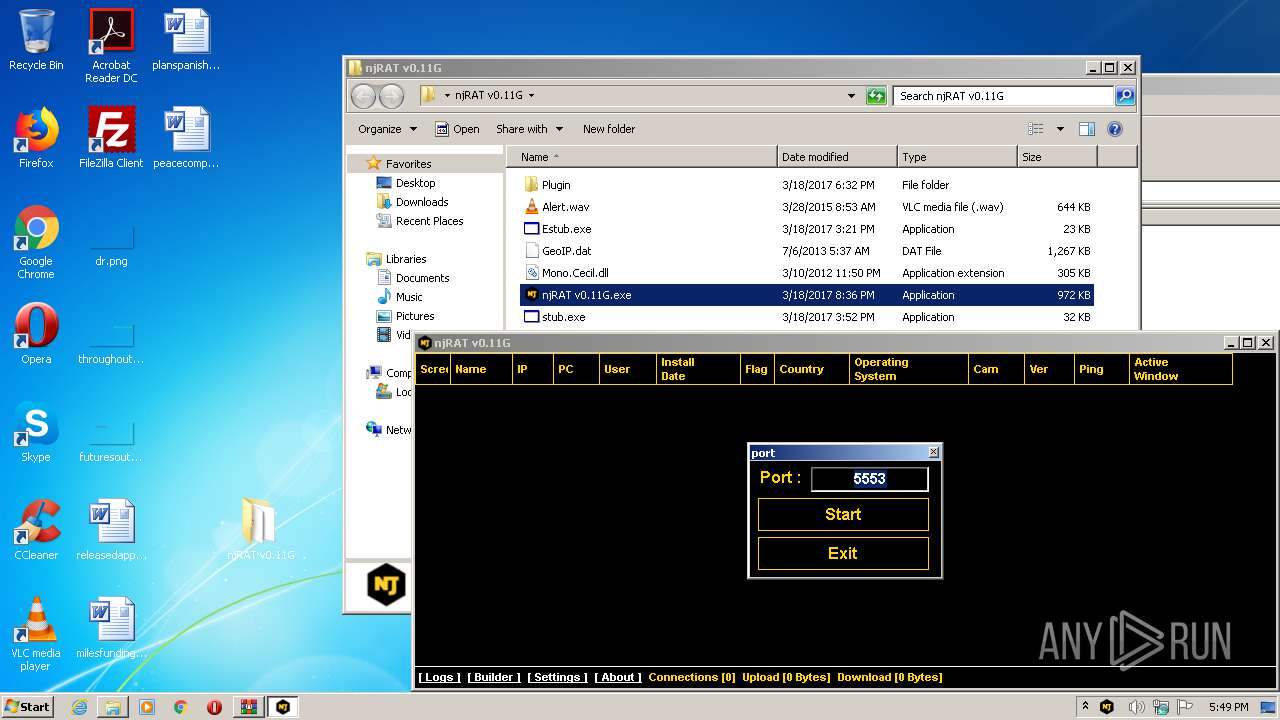
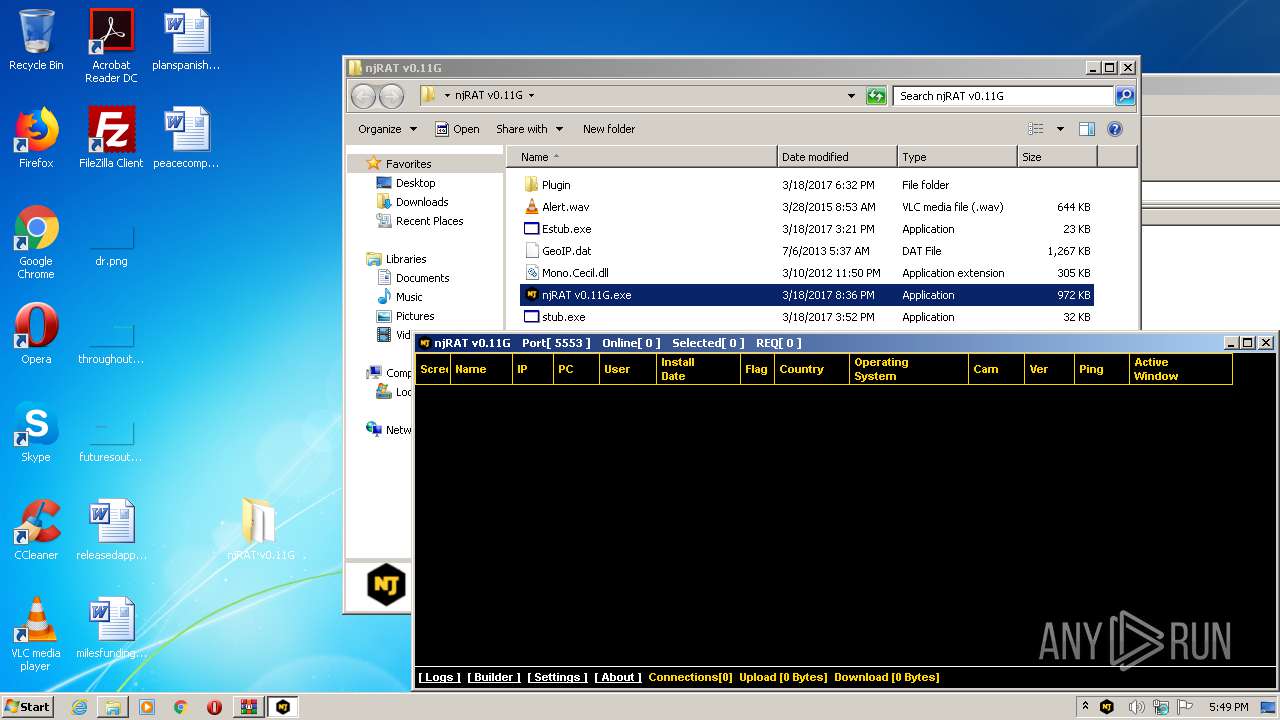
| File name: | njRAT-v0.11G.zip |
| Full analysis: | https://app.any.run/tasks/39137450-2d9c-4256-9704-522380822516 |
| Verdict: | Malicious activity |
| Threats: | Trojans are a group of malicious programs distinguished by their ability to masquerade as benign software. Depending on their type, trojans possess a variety of capabilities, ranging from maintaining full remote control over the victim’s machine to stealing data and files, as well as dropping other malware. At the same time, the main functionality of each trojan family can differ significantly depending on its type. The most common trojan infection chain starts with a phishing email. |
| Analysis date: | August 08, 2020, 16:48:47 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v1.0 to extract |
| MD5: | FD684E46300F02F015FD8267E3072161 |
| SHA1: | 6DC4DC44AAD01D0A24D0DF2A2A84D71BB8D2555C |
| SHA256: | B85CCA32882A0BA5C5D515BCC54DFD6CEE110FE94DC3FC94B4A8DC6B4614291E |
| SSDEEP: | 49152:BTcJPyzeCS++OHKxtH7gv0uAexaB7fFzB9vq0ukDAypBovNE0:dqMPl+XS0v/zLq/kDT0NL |
MALICIOUS
Loads dropped or rewritten executable
- SearchProtocolHost.exe (PID: 3484)
- njRAT v0.11G.exe (PID: 2204)
Application was dropped or rewritten from another process
- njRAT v0.11G.exe (PID: 2204)
SUSPICIOUS
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2872)
INFO
Manual execution by user
- njRAT v0.11G.exe (PID: 2204)
Reads settings of System Certificates
- njRAT v0.11G.exe (PID: 2204)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 10 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2017:03:18 23:36:04 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | njRAT v0.11G/ |
Total processes
40
Monitored processes
3
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2204 | "C:\Users\admin\Desktop\njRAT v0.11G\njRAT v0.11G.exe" | C:\Users\admin\Desktop\njRAT v0.11G\njRAT v0.11G.exe | explorer.exe | ||||||||||||
User: admin Company: njq8, Dx523 Integrity Level: MEDIUM Description: njRAT Exit code: 0 Version: 0.11.0.0 Modules
| |||||||||||||||
| 2872 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\njRAT-v0.11G.zip" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 3484 | "C:\Windows\system32\SearchProtocolHost.exe" Global\UsGthrFltPipeMssGthrPipe5_ Global\UsGthrCtrlFltPipeMssGthrPipe5 1 -2147483646 "Software\Microsoft\Windows Search" "Mozilla/4.0 (compatible; MSIE 6.0; Windows NT; MS Search 4.0 Robot)" "C:\ProgramData\Microsoft\Search\Data\Temp\usgthrsvc" "DownLevelDaemon" | C:\Windows\System32\SearchProtocolHost.exe | — | SearchIndexer.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft Windows Search Protocol Host Exit code: 0 Version: 7.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
857
Read events
820
Write events
37
Delete events
0
Modification events
| (PID) Process: | (2872) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2872) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2872) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\136\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2872) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\136\52C64B7E |
| Operation: | write | Name: | @C:\Windows\system32\NetworkExplorer.dll,-1 |
Value: Network | |||
| (PID) Process: | (2872) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\njRAT-v0.11G.zip | |||
| (PID) Process: | (2872) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2872) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2872) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2872) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2204) njRAT v0.11G.exe | Key: | HKEY_CURRENT_USER\Software\njRAT v0.11G |
| Operation: | write | Name: | p |
Value: 5553 | |||
Executable files
13
Suspicious files
1
Text files
0
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2872 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2872.18963\njRAT v0.11G\Plugin\pw.dll | executable | |
MD5:DB87DAF76C15F3808CEC149F639AA64F | SHA256:A3E4BEE1B6944AA9266BD58DE3F534A4C1896DF621881A5252A0D355A6E67C70 | |||
| 2872 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2872.18963\njRAT v0.11G\Plugin\sc2.dll | executable | |
MD5:19967E886EDCD2F22F8D4A58C8EA3773 | SHA256:3E5141C75B7746C0EB2B332082A165DEACB943CEF26BD84668E6B79B47BDFD93 | |||
| 2872 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2872.18963\njRAT v0.11G\Plugin\mic.dll | executable | |
MD5:D4C5DDC00F27162FC0947830E0E762B7 | SHA256:B6FB6B66821E70A27A4750B0CD0393E4EE2603A47FEAC48D6A3D66D1C1CB56D5 | |||
| 2872 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2872.18963\njRAT v0.11G\Estub.exe | executable | |
MD5:A269C8915FE8754A7AE451B879415477 | SHA256:142E61B92C40934E121C6204AD4A9CD2893CB3566E982A15D6DF55454FE782AF | |||
| 2872 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2872.18963\njRAT v0.11G\Plugin\inf.dll | executable | |
MD5:CEF141D894400BC2E0096D1ED0C8F95B | SHA256:9648FFD2EB53744C5F78DC8442A8BCBBE9831DB1E198BE370A62CBF9F51CD896 | |||
| 2872 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2872.18963\njRAT v0.11G\Plugin\plg.dll | executable | |
MD5:80F3036110C00A57B09BBA7343C16696 | SHA256:FC96E837E9902D3941210EEEE94D79F9D268F9715FB966945BDB20CB93C9E497 | |||
| 2872 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2872.18963\njRAT v0.11G\Alert.wav | wav | |
MD5:562FB3B4B1B1EAFD2CF107F2E92E0670 | SHA256:5FF592B183B2C990448F1DCD842A29CFE17A3EAA9956E0135C945C578676344A | |||
| 2872 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2872.18963\njRAT v0.11G\Mono.Cecil.dll | executable | |
MD5:851EC9D84343FBD089520D420348A902 | SHA256:CDADC26C09F869E21053EE1A0ACF3B2D11DF8EDD599FE9C377BD4D3CE1C9CDA9 | |||
| 2872 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2872.18963\njRAT v0.11G\Plugin\cam.dll | executable | |
MD5:A73EDB60B80A2DFA86735D821BEA7B19 | SHA256:7A4977B024D048B71BCC8F1CC65FB06E4353821323F852DC6740B79B9AB75C98 | |||
| 2872 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2872.18963\njRAT v0.11G\GeoIP.dat | binary | |
MD5:797B96CC417D0CDE72E5C25D0898E95E | SHA256:8A0675001B5BC63D8389FC7ED80B4A7B0F9538C744350F00162533519E106426 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
2
DNS requests
1
Threats
3
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2204 | njRAT v0.11G.exe | GET | 301 | 104.23.99.190:80 | http://pastebin.com/raw/jPBSDMAg | US | — | — | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2204 | njRAT v0.11G.exe | 104.23.99.190:80 | pastebin.com | Cloudflare Inc | US | malicious |
— | — | 104.23.99.190:443 | pastebin.com | Cloudflare Inc | US | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
pastebin.com |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2204 | njRAT v0.11G.exe | Misc activity | SUSPICIOUS [PTsecurity] Minimal HTTP Header for Request to Pastebin |
2 ETPRO signatures available at the full report