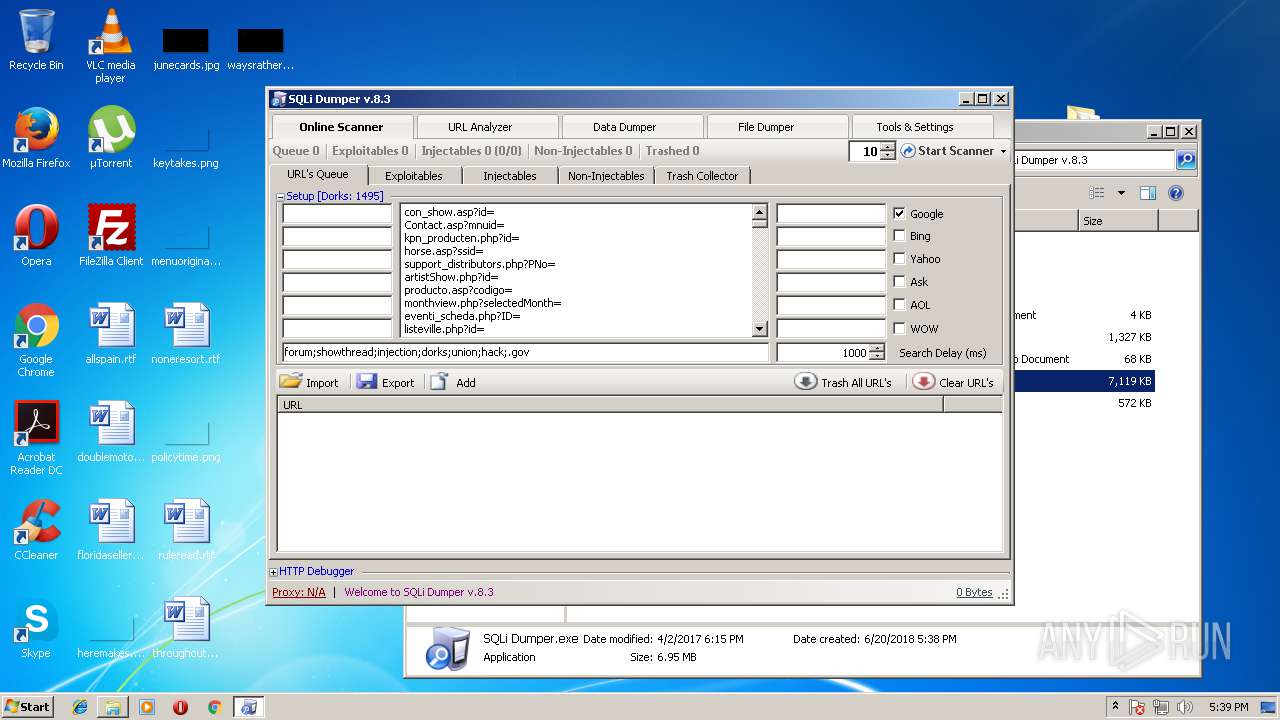
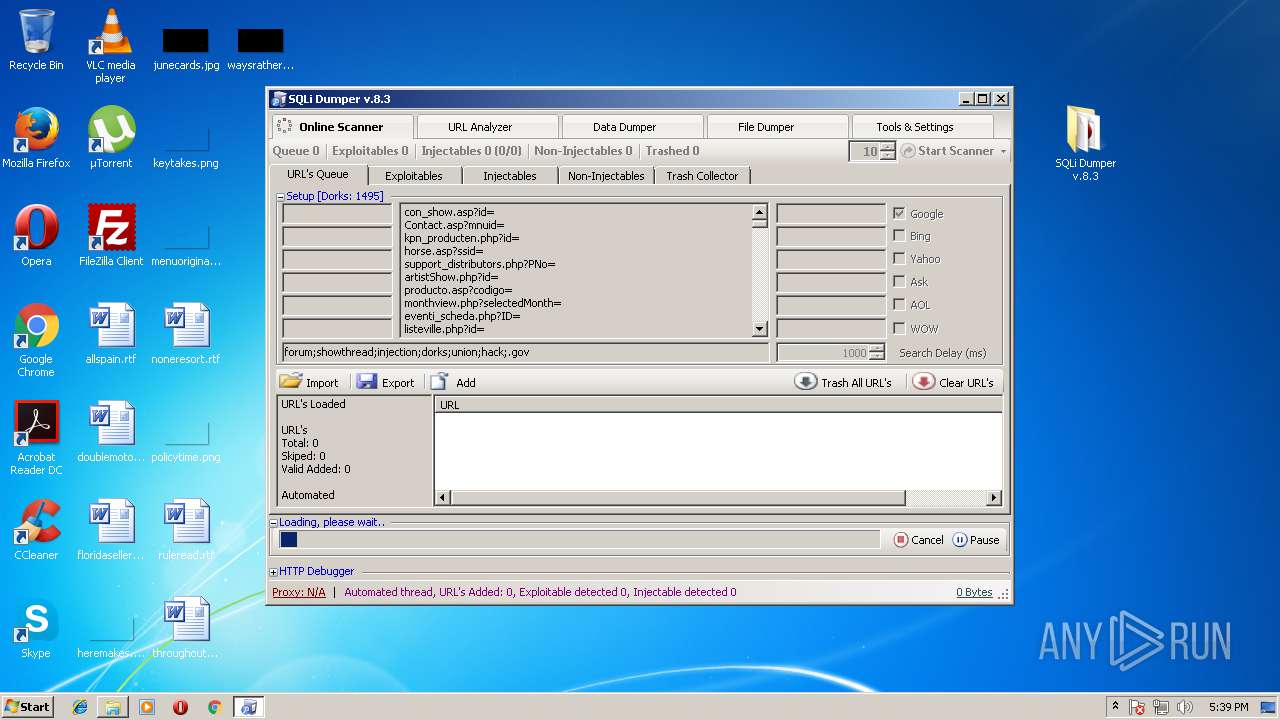
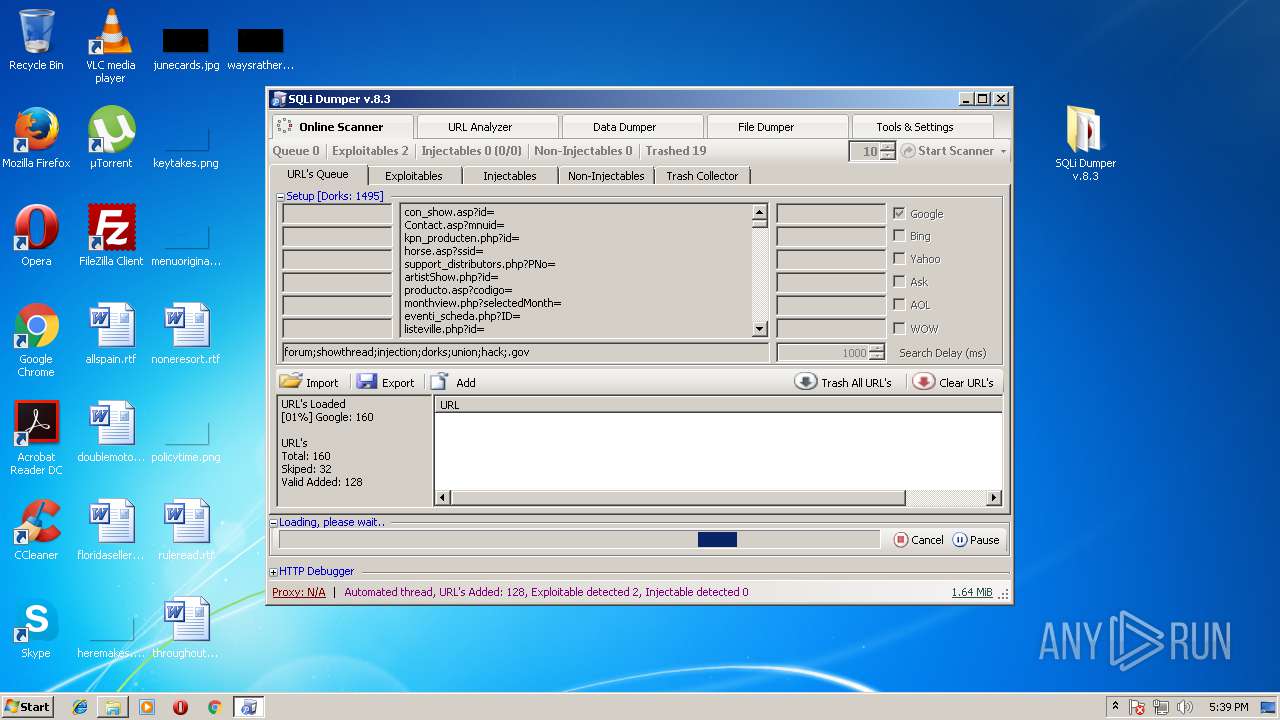
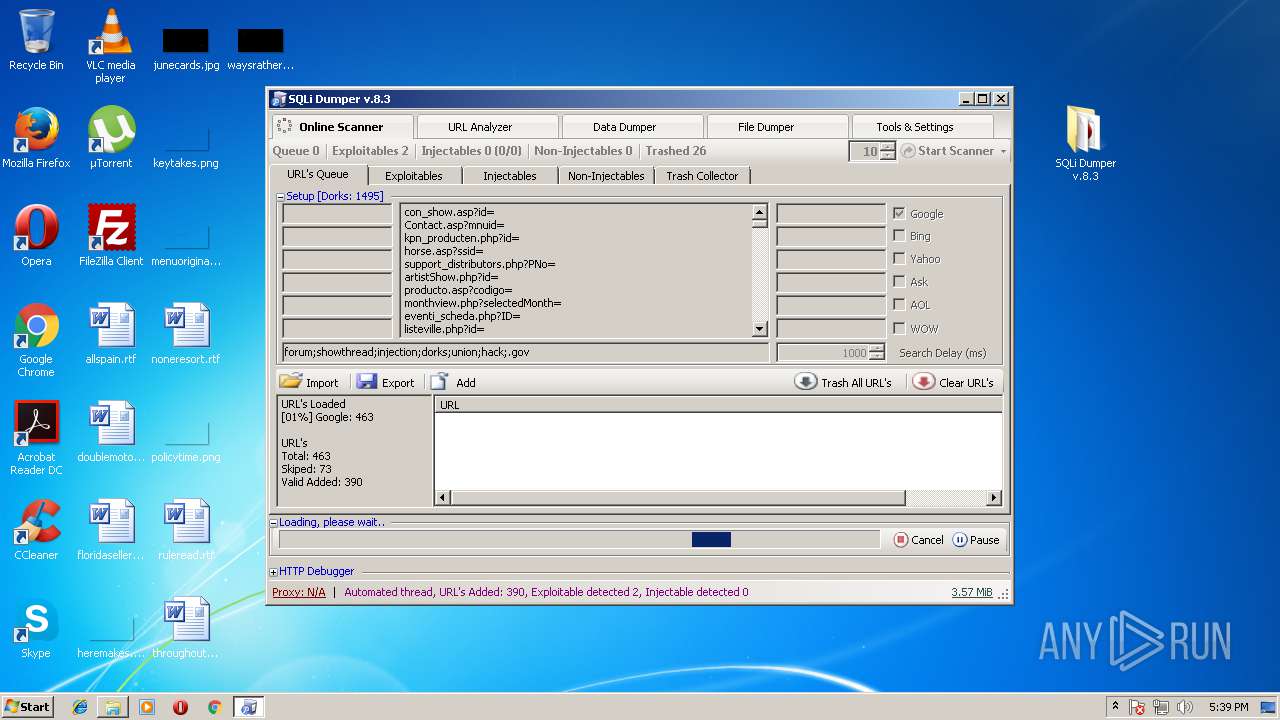
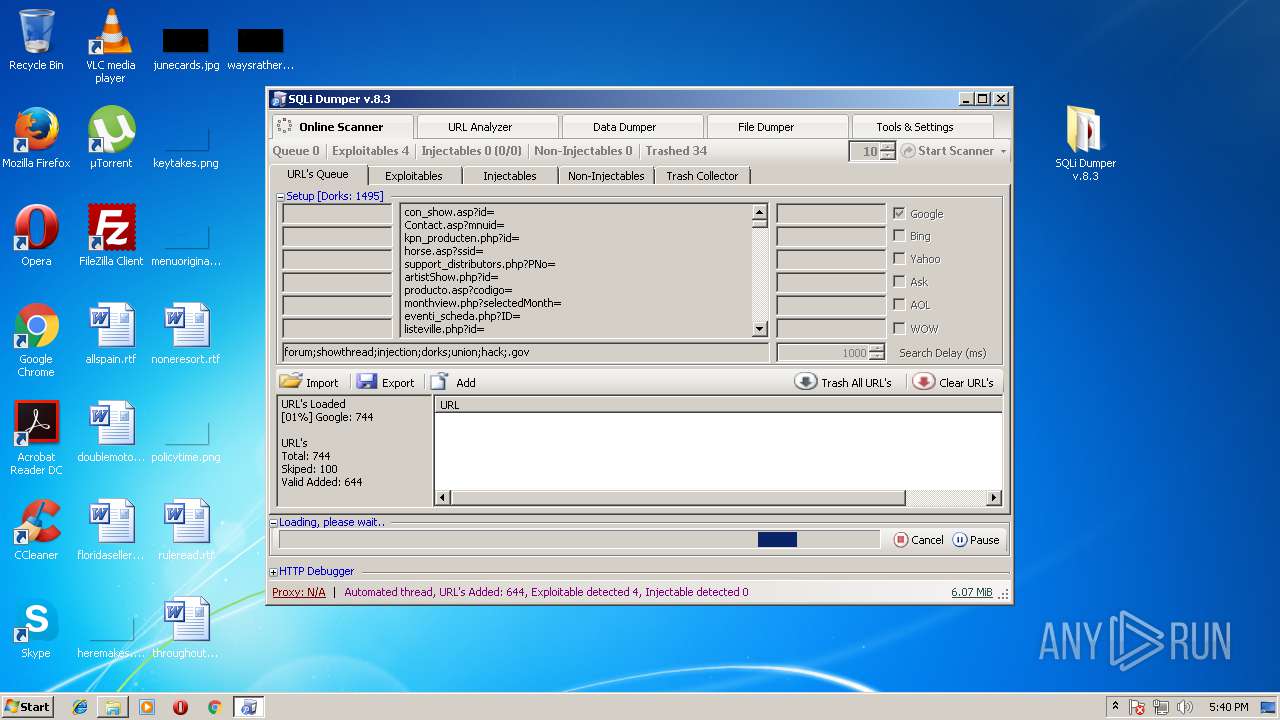
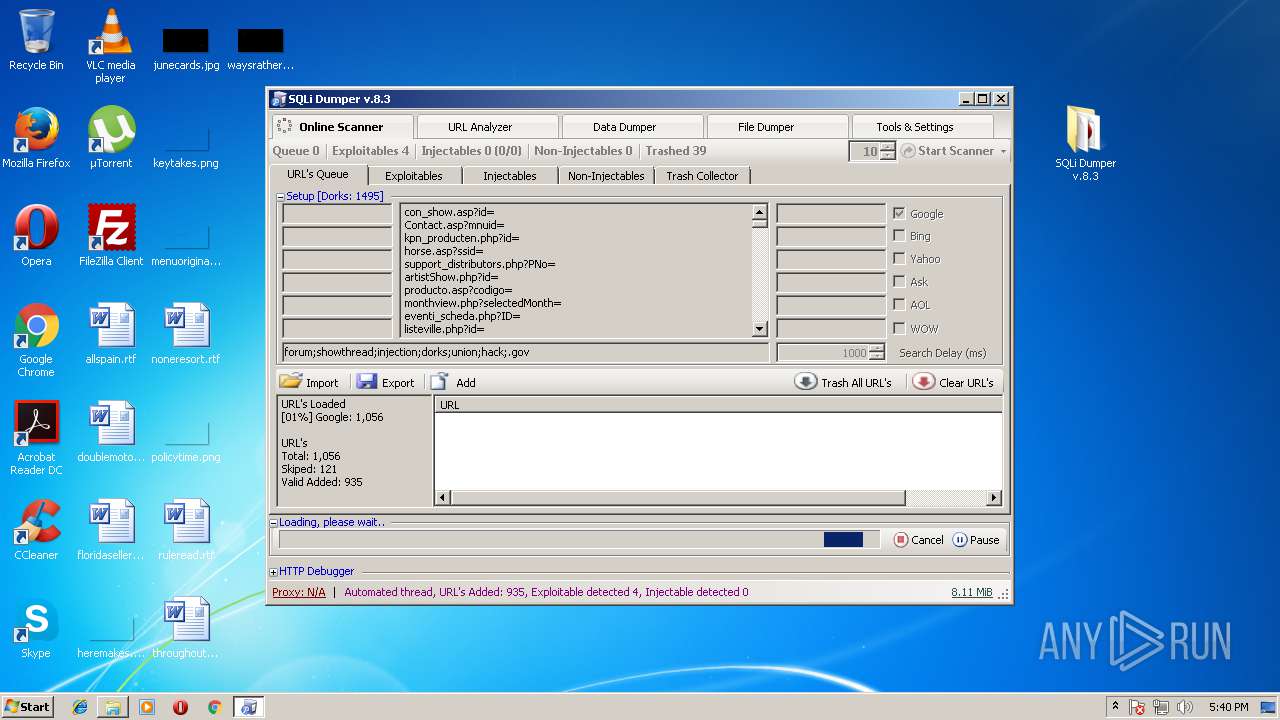
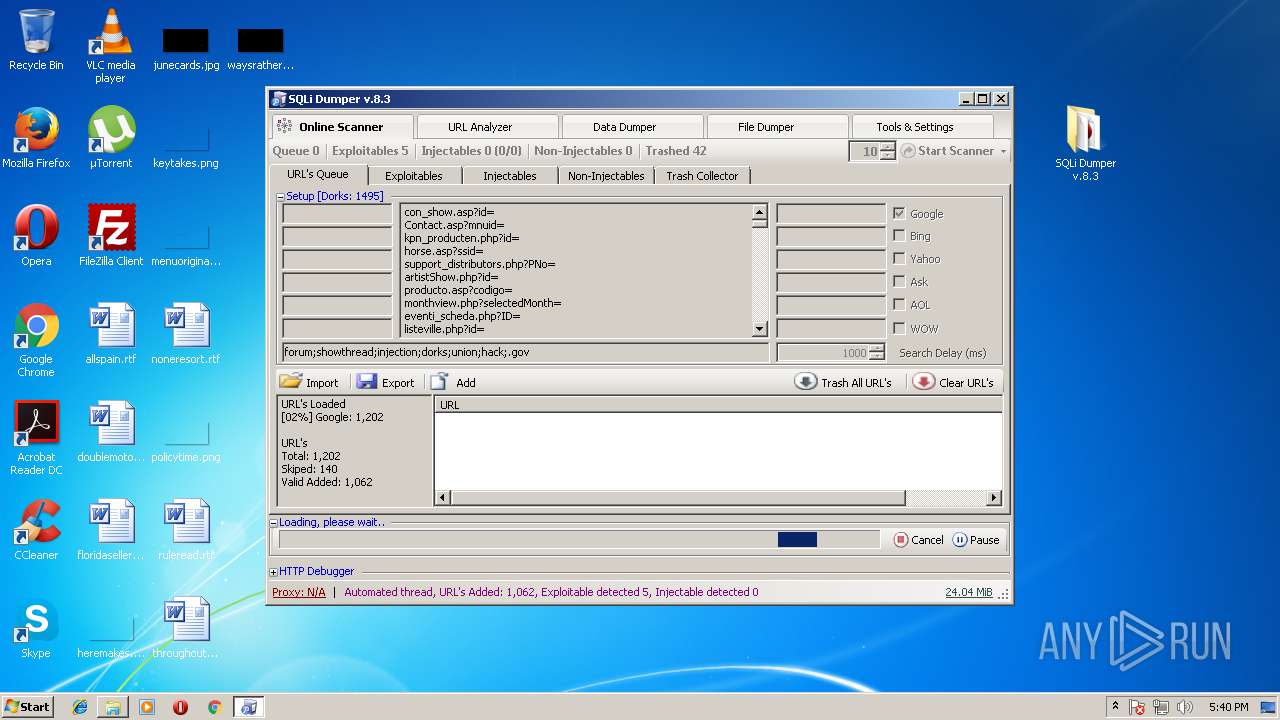
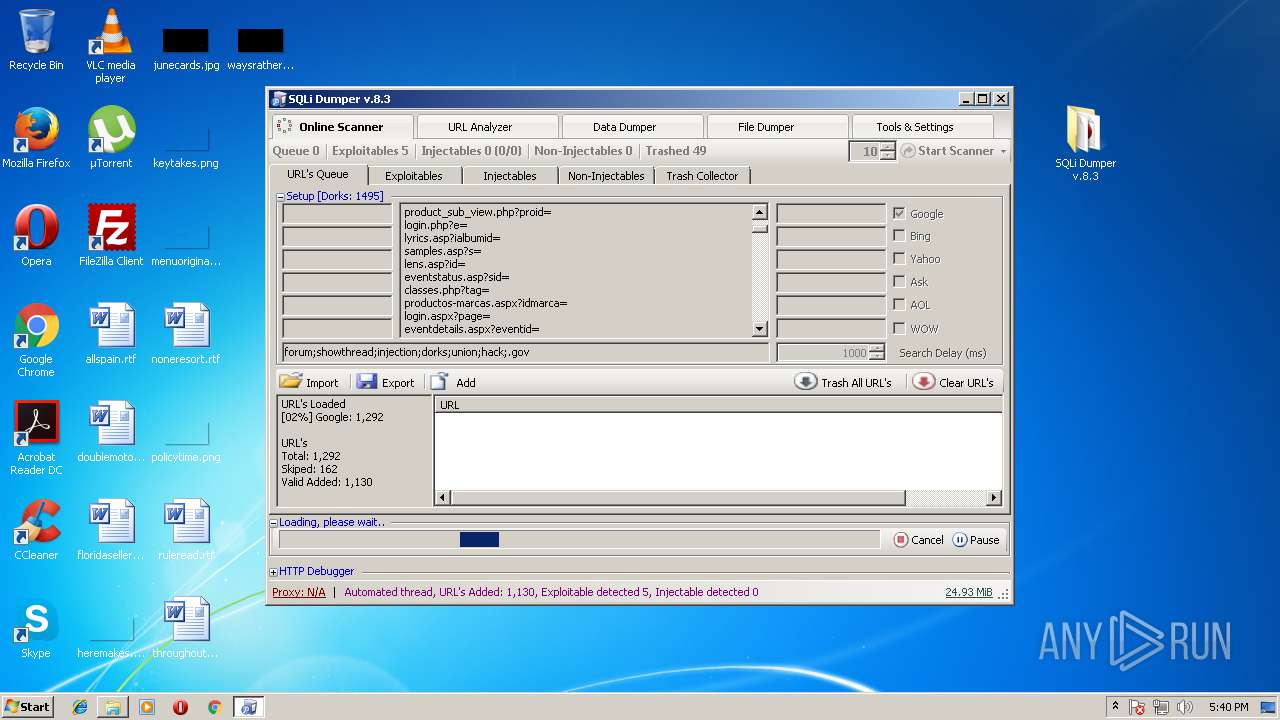
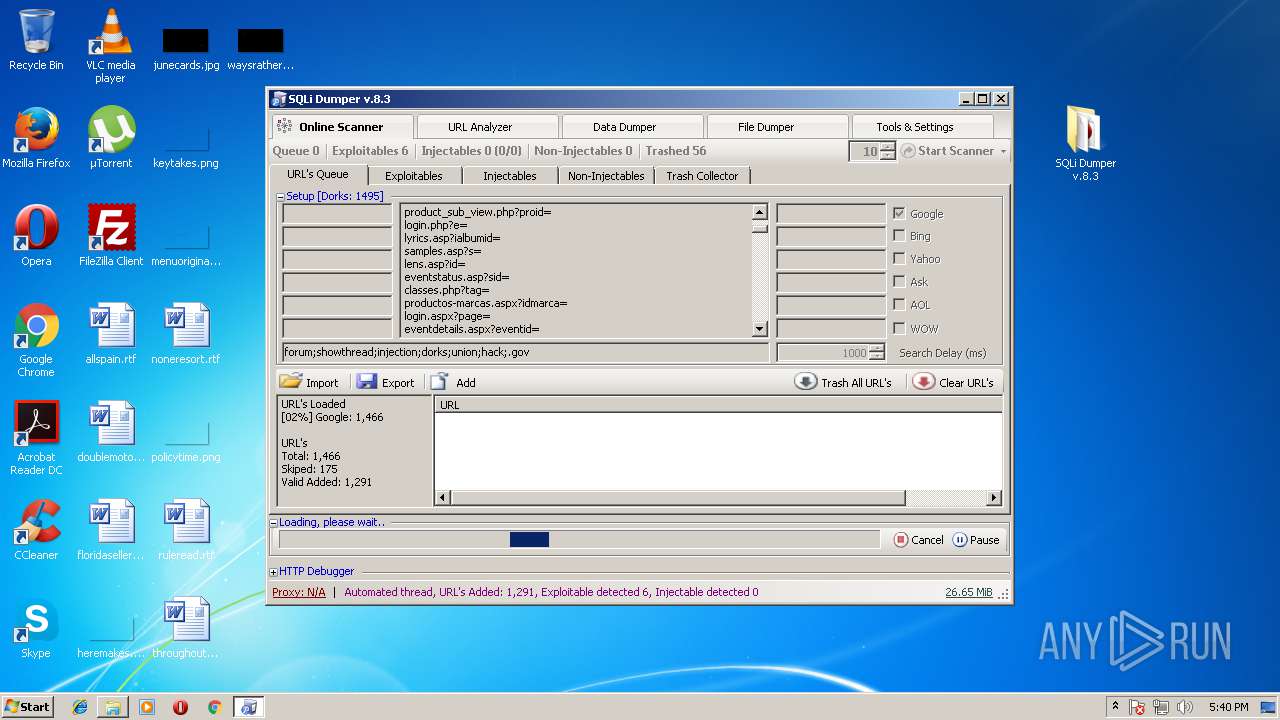
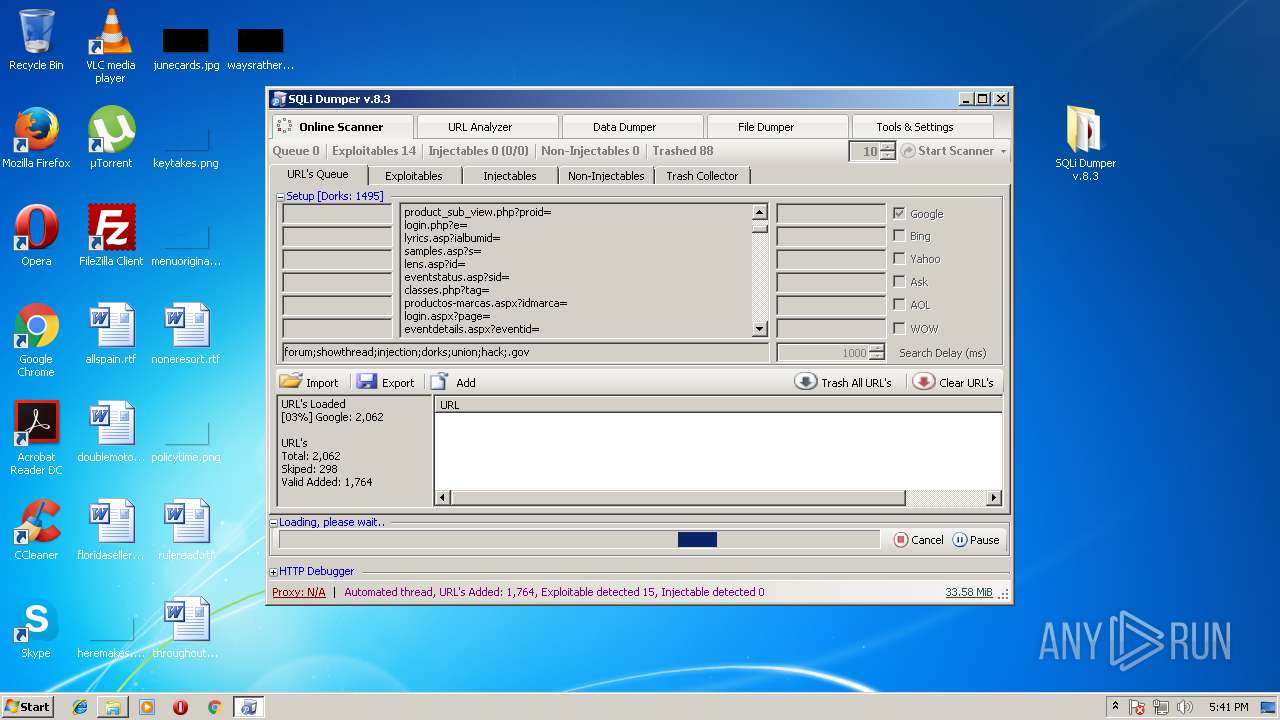
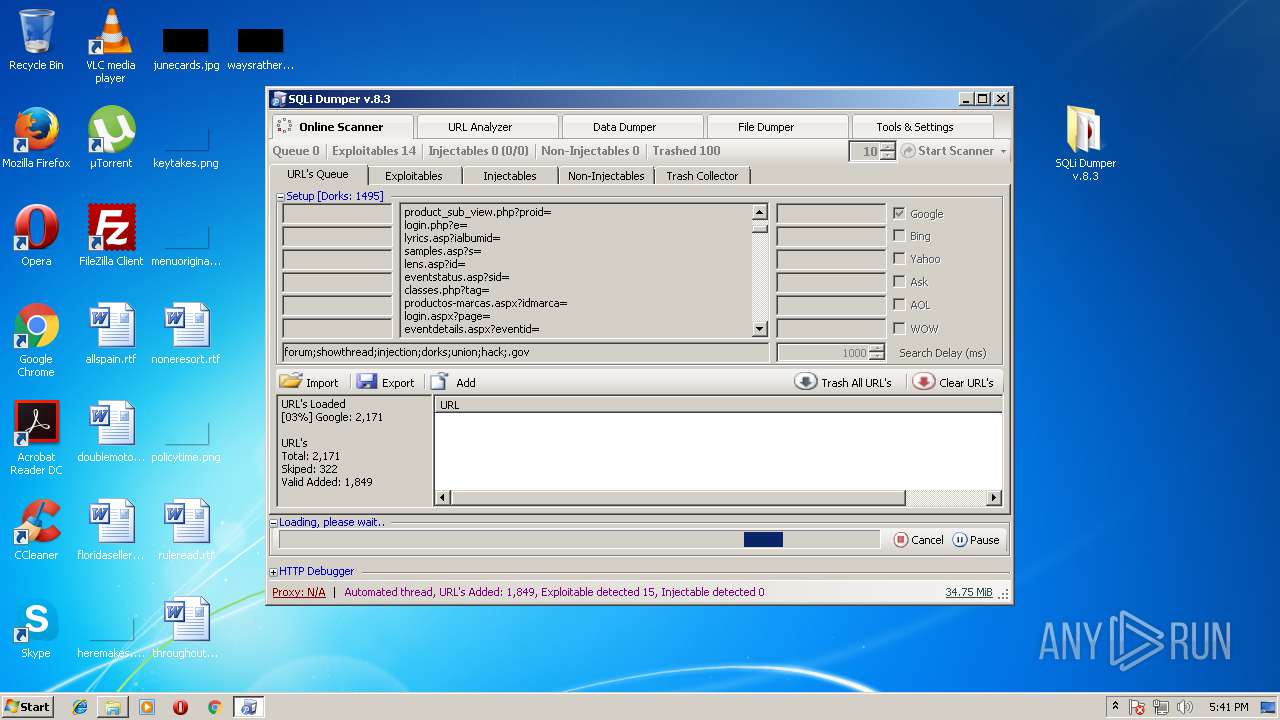
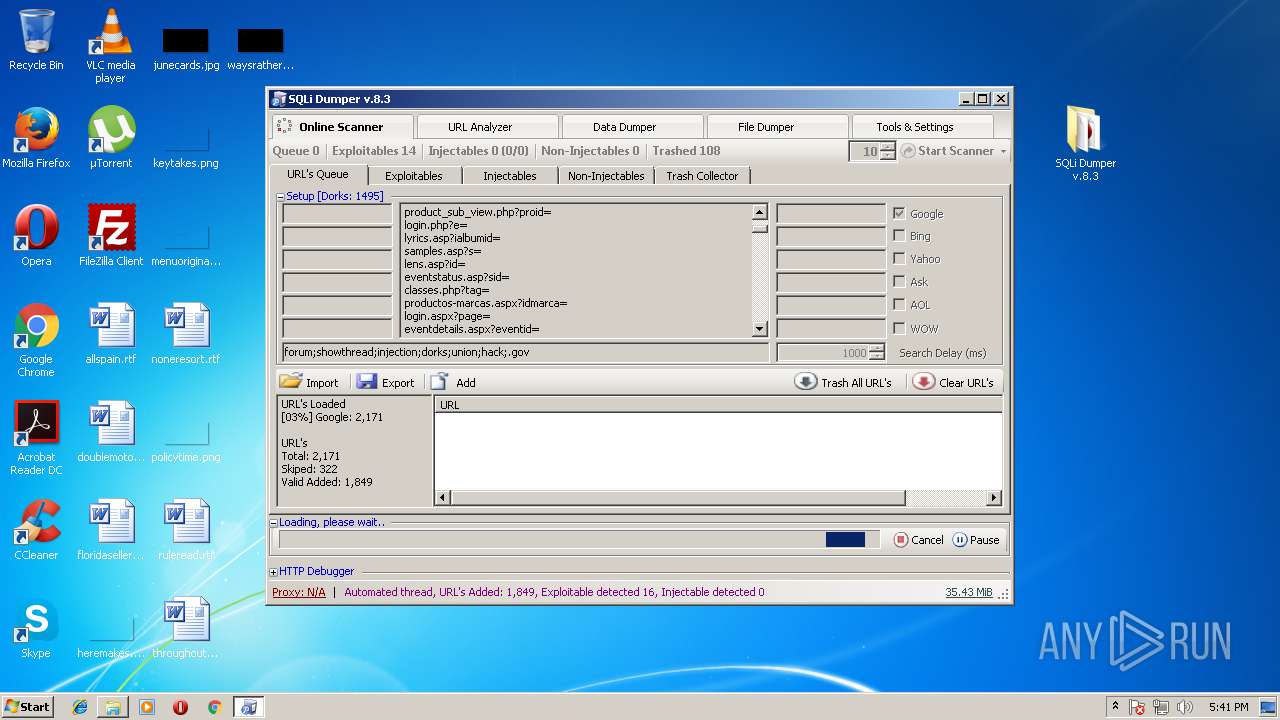
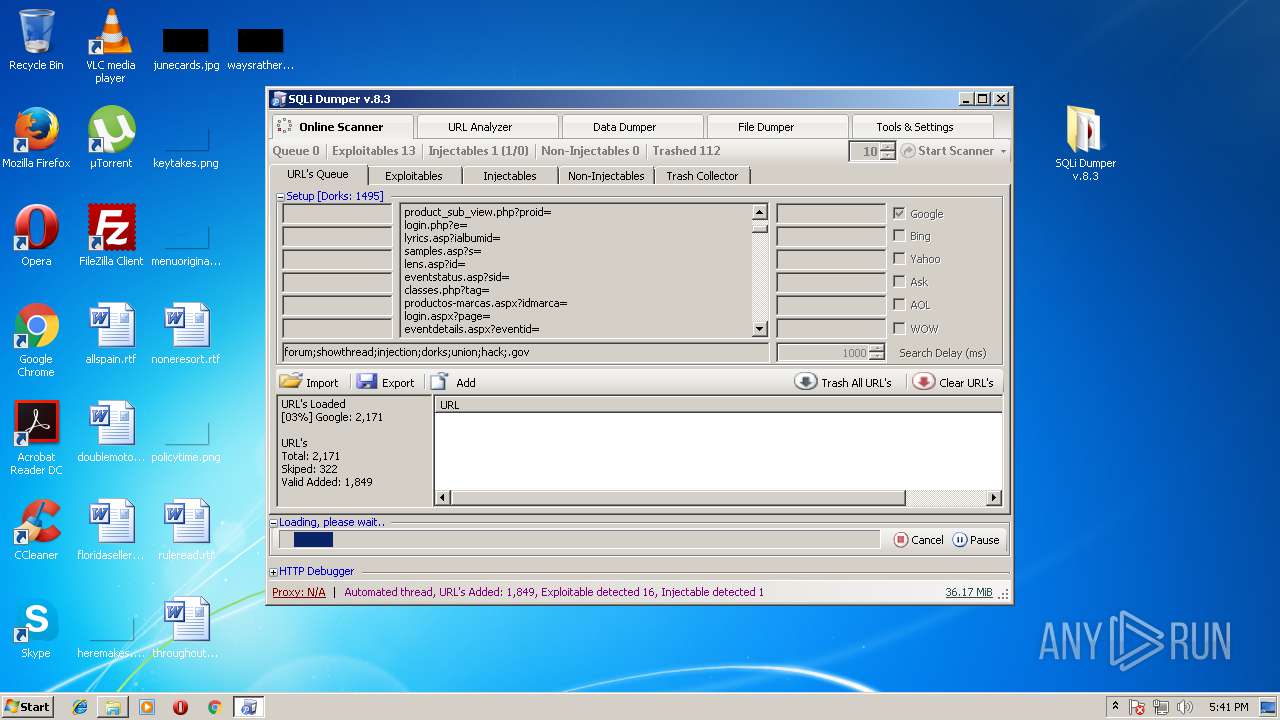
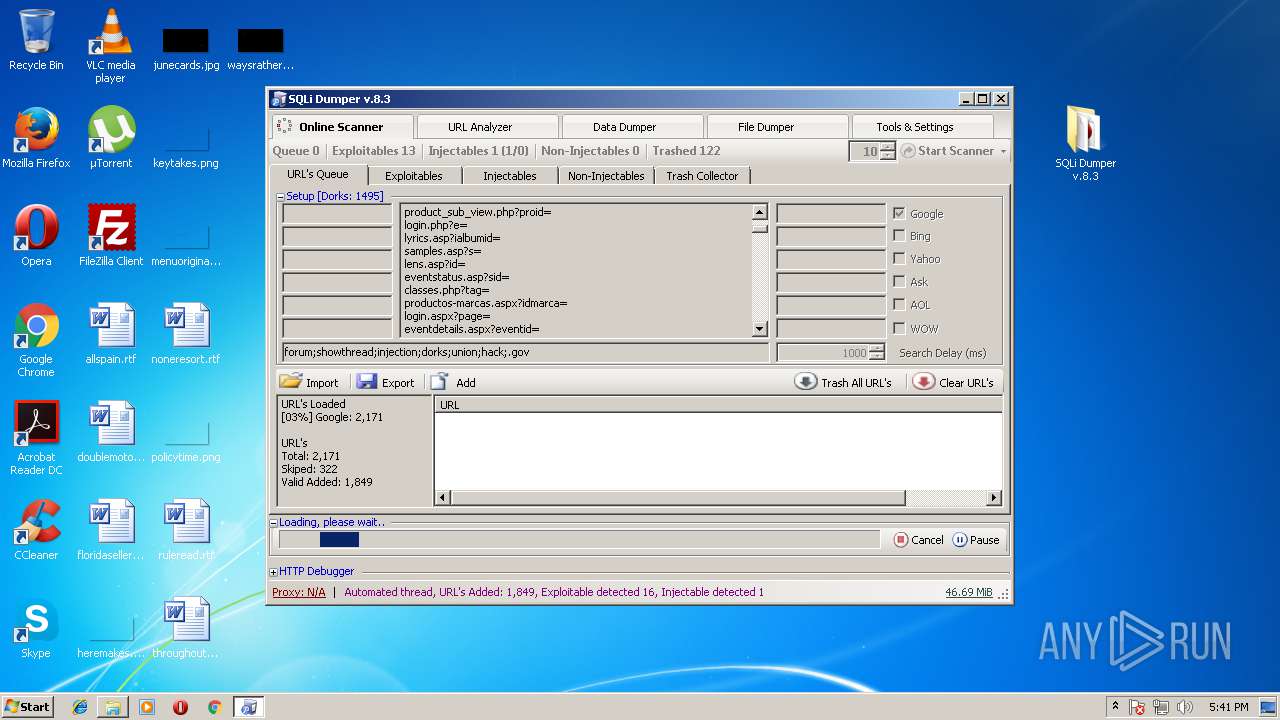
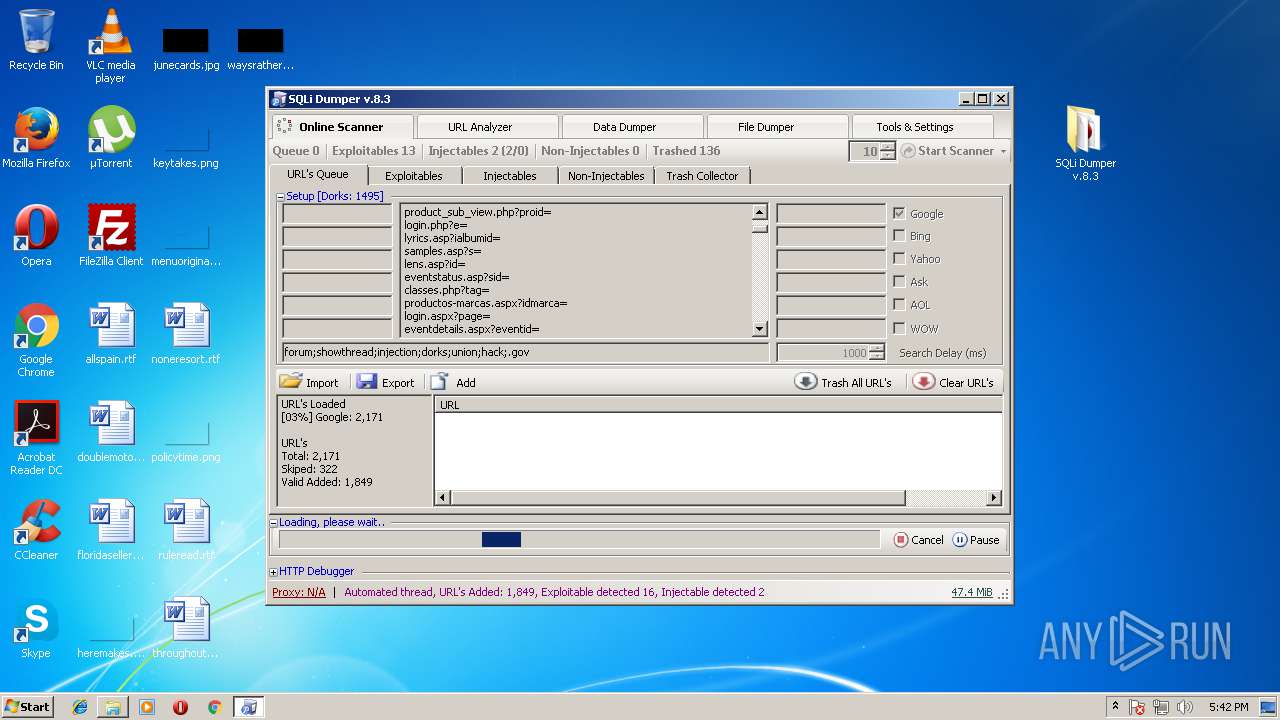
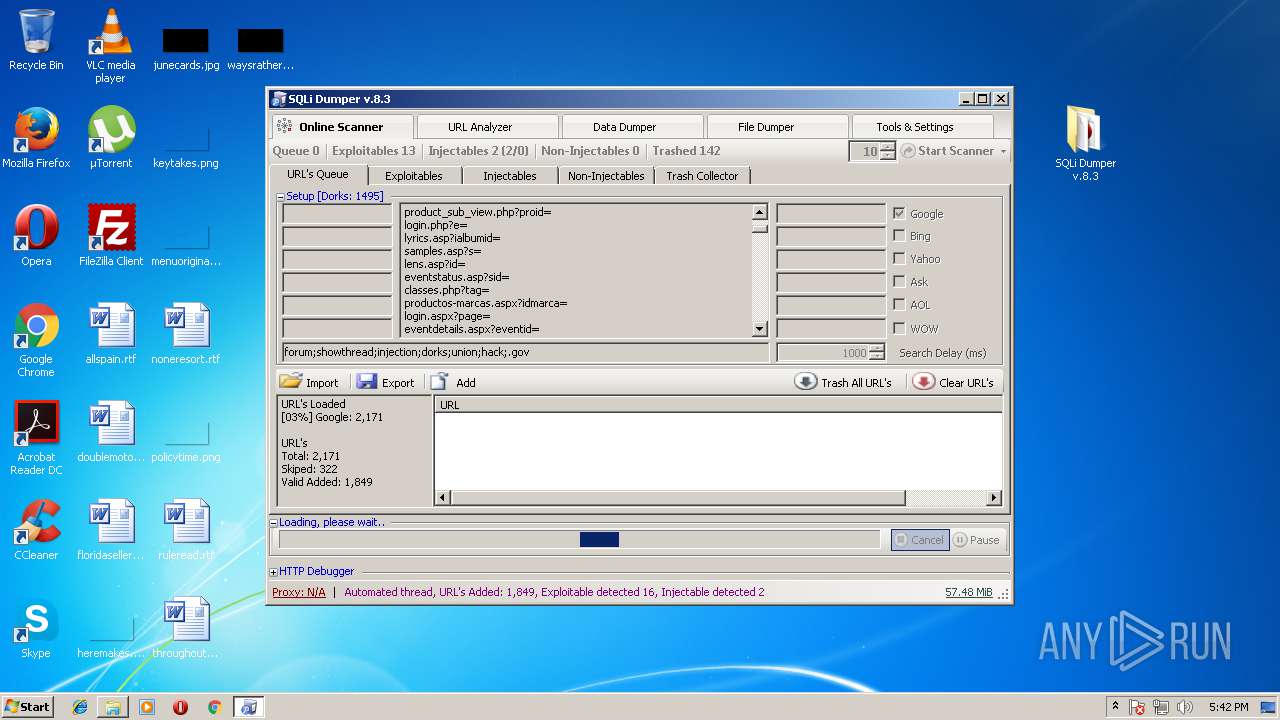
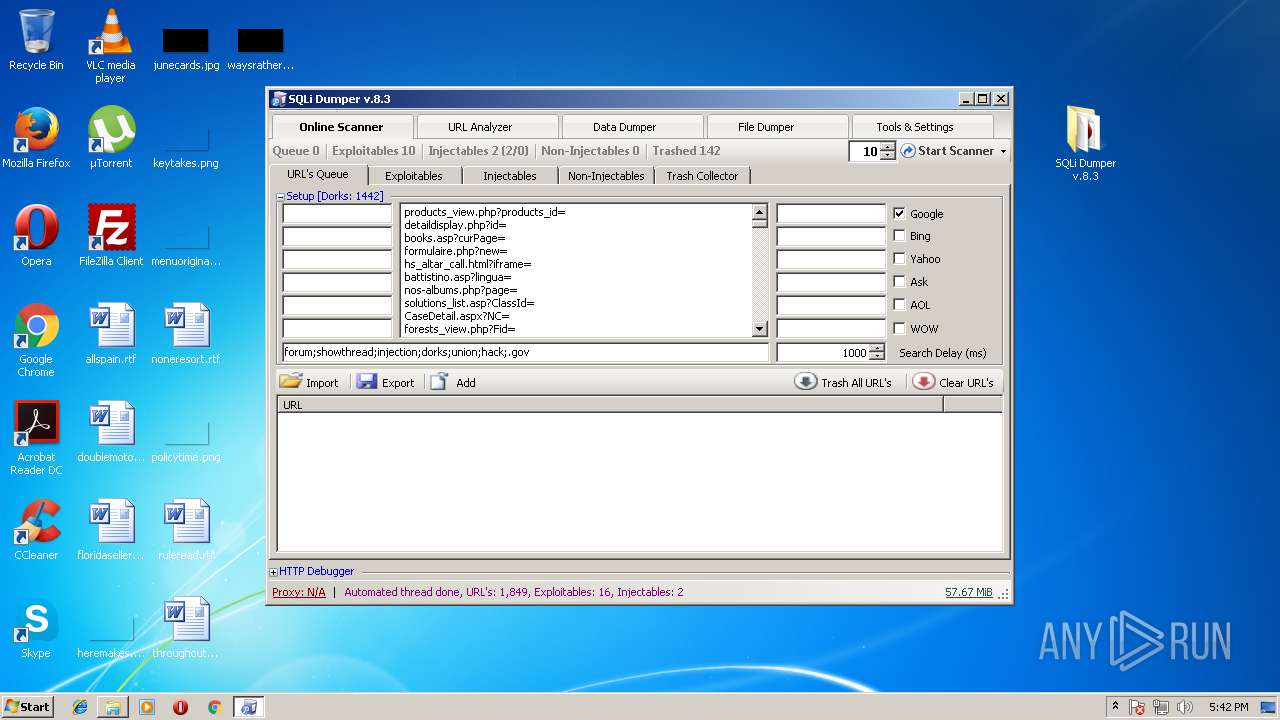
| File name: | sqli-dumper-v.8.3.rar |
| Full analysis: | https://app.any.run/tasks/90658826-aebf-4837-b5f0-2acf5018f109 |
| Verdict: | Malicious activity |
| Analysis date: | June 20, 2018, 16:38:26 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v4, os: Win32 |
| MD5: | CAC7FA52FBD5BE913470100316C4BEBF |
| SHA1: | FA426E910CC7E6DAB7516CE71719EE44E0BF59D3 |
| SHA256: | B8429037612C27F914E67DB778CC3E1236F877B04BFE81ACD93734964BED26DD |
| SSDEEP: | 98304:9CQzcNvBuKDHeIgWsw/hPOX1uBH6U07OlNdxg1N9yucwvXUaI4LkRggAnCrsmXA:9CQIXe5Wl2FuH6UZ29y1ZR44hvrsmQ |
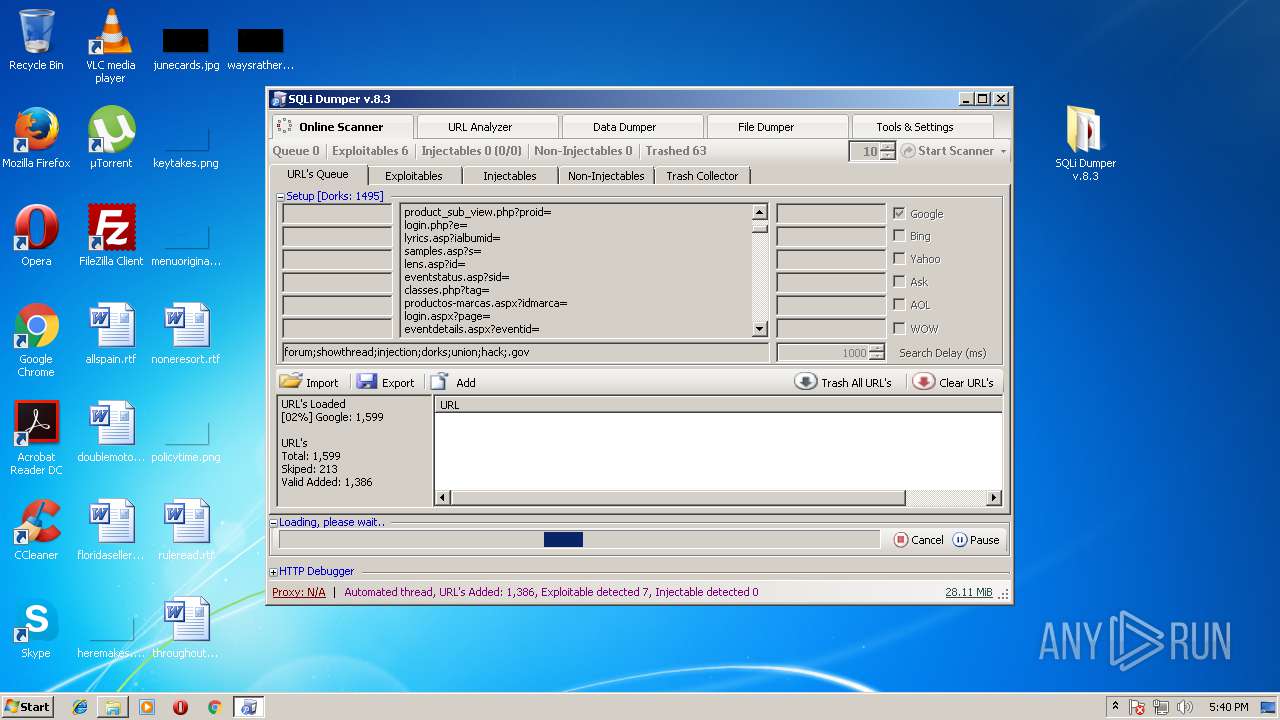
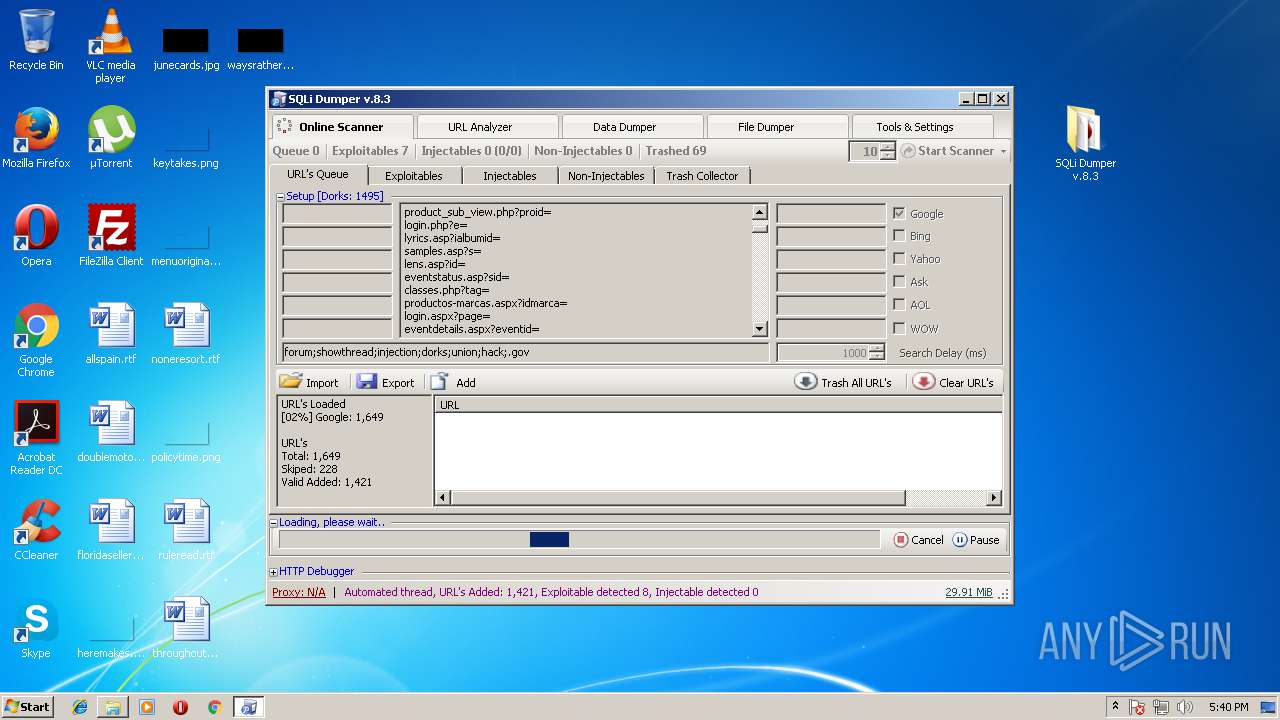
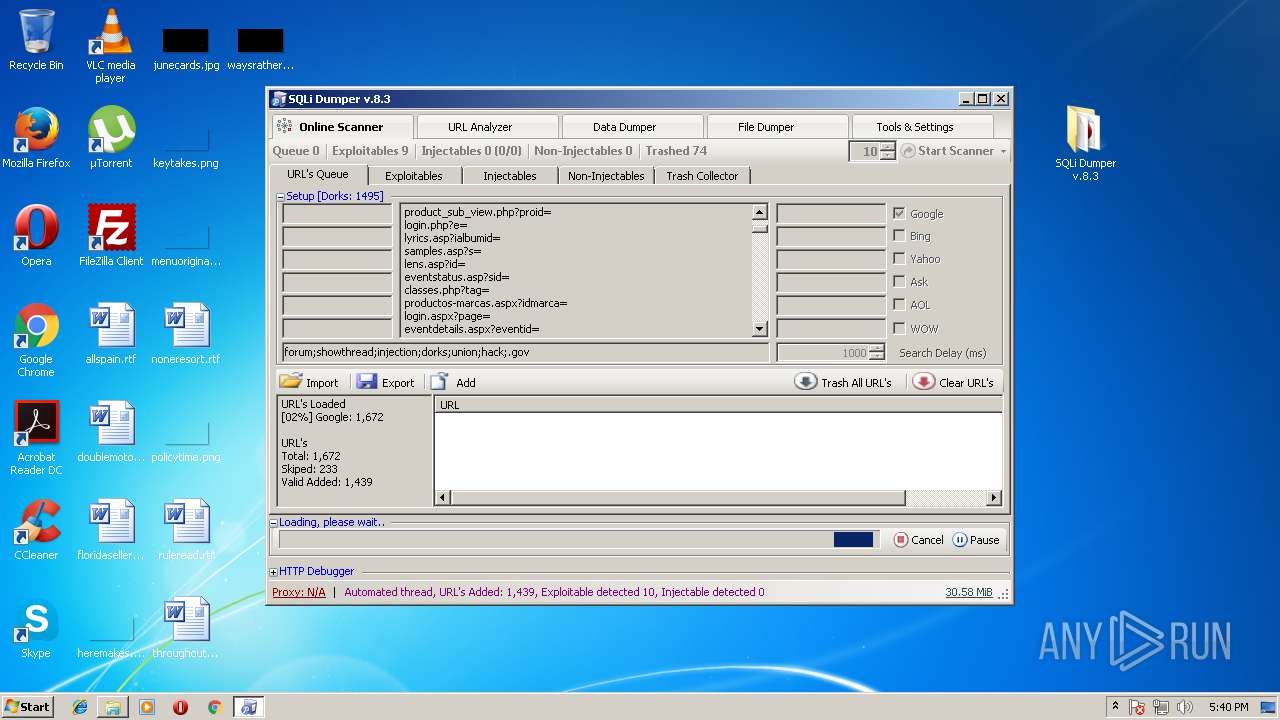
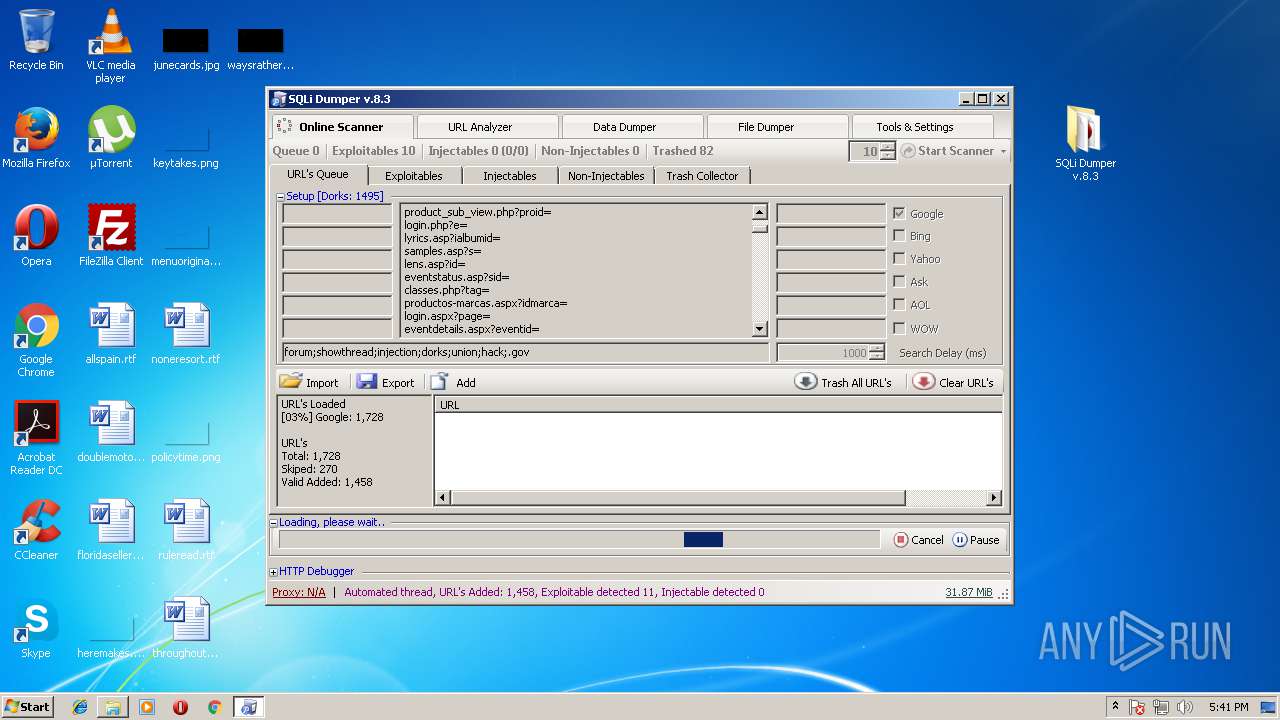
MALICIOUS
Application was dropped or rewritten from another process
- SQLi Dumper.exe (PID: 4008)
Loads dropped or rewritten executable
- SQLi Dumper.exe (PID: 4008)
SUSPICIOUS
Executable content was dropped or overwritten
- 7zFM.exe (PID: 980)
- SQLi Dumper.exe (PID: 4008)
Reads internet explorer settings
- SQLi Dumper.exe (PID: 4008)
INFO
Dropped object may contain URL's
- SQLi Dumper.exe (PID: 4008)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v-4.x) (58.3) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (41.6) |
EXIF
ZIP
| CompressedSize: | 1293 |
|---|---|
| UncompressedSize: | 4378 |
| OperatingSystem: | Win32 |
| ModifyDate: | 2018:05:24 11:54:19 |
| PackingMethod: | Normal |
| ArchivedFileName: | SQLi Dumper v.8.3\DIC\dic_admin.txt |
Total processes
39
Monitored processes
2
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 980 | "C:\Program Files\7-Zip\7zFM.exe" "C:\Users\admin\AppData\Local\Temp\sqli-dumper-v.8.3.rar" | C:\Program Files\7-Zip\7zFM.exe | explorer.exe | ||||||||||||
User: admin Company: Igor Pavlov Integrity Level: MEDIUM Description: 7-Zip File Manager Exit code: 0 Version: 16.04 Modules
| |||||||||||||||
| 4008 | "C:\Users\admin\Desktop\SQLi Dumper v.8.3\SQLi Dumper.exe" | C:\Users\admin\Desktop\SQLi Dumper v.8.3\SQLi Dumper.exe | explorer.exe | ||||||||||||
User: admin Company: c4rl0s@jabber.ru Integrity Level: MEDIUM Description: SQLi Dumper Exit code: 0 Version: 8.3.0.0 Modules
| |||||||||||||||
Total events
143
Read events
117
Write events
26
Delete events
0
Modification events
| (PID) Process: | (980) 7zFM.exe | Key: | HKEY_CURRENT_USER\Software\7-Zip\FM |
| Operation: | write | Name: | FolderShortcuts |
Value: | |||
| (PID) Process: | (980) 7zFM.exe | Key: | HKEY_CURRENT_USER\Software\7-Zip\FM |
| Operation: | write | Name: | FolderHistory |
Value: 43003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C004C006F00630061006C005C00540065006D0070005C00730071006C0069002D00640075006D007000650072002D0076002E0038002E0033002E007200610072005C000000 | |||
| (PID) Process: | (980) 7zFM.exe | Key: | HKEY_CURRENT_USER\Software\7-Zip\FM |
| Operation: | write | Name: | PanelPath0 |
Value: C:\Users\admin\AppData\Local\Temp\ | |||
| (PID) Process: | (980) 7zFM.exe | Key: | HKEY_CURRENT_USER\Software\7-Zip\FM |
| Operation: | write | Name: | FlatViewArc0 |
Value: 0 | |||
| (PID) Process: | (980) 7zFM.exe | Key: | HKEY_CURRENT_USER\Software\7-Zip\FM |
| Operation: | write | Name: | PanelPath1 |
Value: | |||
| (PID) Process: | (980) 7zFM.exe | Key: | HKEY_CURRENT_USER\Software\7-Zip\FM |
| Operation: | write | Name: | FlatViewArc1 |
Value: 0 | |||
| (PID) Process: | (980) 7zFM.exe | Key: | HKEY_CURRENT_USER\Software\7-Zip\FM |
| Operation: | write | Name: | ListMode |
Value: 771 | |||
| (PID) Process: | (980) 7zFM.exe | Key: | HKEY_CURRENT_USER\Software\7-Zip\FM |
| Operation: | write | Name: | Position |
Value: 1600000016000000D60300000B02000000000000 | |||
| (PID) Process: | (980) 7zFM.exe | Key: | HKEY_CURRENT_USER\Software\7-Zip\FM |
| Operation: | write | Name: | Panels |
Value: 0100000000000000DA010000 | |||
| (PID) Process: | (980) 7zFM.exe | Key: | HKEY_CURRENT_USER\Software\7-Zip\FM\Columns |
| Operation: | write | Name: | 7-Zip.Rar |
Value: 0100000004000000010000000400000001000000A00000000700000001000000640000000800000001000000640000000C00000001000000640000000A00000001000000640000000B00000001000000640000000900000001000000640000000F00000001000000640000000D00000001000000640000000E00000001000000640000001000000001000000640000001100000001000000640000001300000001000000640000001700000001000000640000001600000001000000640000002100000001000000640000001F0000000100000064000000200000000100000064000000 | |||
Executable files
2
Suspicious files
1
Text files
10
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 980 | 7zFM.exe | C:\Users\admin\AppData\Local\Temp\7zE4D3772BA\SQLi Dumper v.8.3\Settings.xml | xml | |
MD5:— | SHA256:— | |||
| 980 | 7zFM.exe | C:\Users\admin\AppData\Local\Temp\7zE4D3772BA\SQLi Dumper v.8.3\ErrLog.log | text | |
MD5:— | SHA256:— | |||
| 4008 | SQLi Dumper.exe | C:\Users\admin\Desktop\SQLi Dumper v.8.3\TXT\URL Exploitables.xml | xml | |
MD5:— | SHA256:— | |||
| 980 | 7zFM.exe | C:\Users\admin\AppData\Local\Temp\7zE4D3772BA\SQLi Dumper v.8.3\DIC\dic_file_dump.txt | text | |
MD5:351CACFFC2884FCD4E69BB1FB04DDEB5 | SHA256:C67BCC0B4ED5E5EF72AA1134C0838D9201A97C2BF462FDFF0AC9052A53B286A2 | |||
| 980 | 7zFM.exe | C:\Users\admin\AppData\Local\Temp\7zE4D3772BA\SQLi Dumper v.8.3\GeoIP.dat | binary | |
MD5:CB9AD69965F9F4CFF8572983F60BE67C | SHA256:56C7079DC309168D9C41DD4A7A61033ACD264A120CA8D2E2182ABB5B9AE6B0A3 | |||
| 980 | 7zFM.exe | C:\Users\admin\AppData\Local\Temp\7zE4D3772BA\SQLi Dumper v.8.3\SQLi Dumper.pdb | pdb | |
MD5:A6A9112EA988AED102B2A4949C98E943 | SHA256:C94BADABDA58F4F9C839BBDE39D7FC4C120EDF5305E6E8F2AD0F67B727B93337 | |||
| 980 | 7zFM.exe | C:\Users\admin\AppData\Local\Temp\7zE4D3772BA\SQLi Dumper v.8.3\SQLi Dumper.exe | executable | |
MD5:D3C358F1785594FB5619CDA521B9FF04 | SHA256:4879007515FC16FD0B22156852F2AF0424C947F8CF543F5F4CCCF1AED52BC97D | |||
| 980 | 7zFM.exe | C:\Users\admin\AppData\Local\Temp\7zE4D3772BA\SQLi Dumper v.8.3\DIC\dic_admin.txt | text | |
MD5:A0E54634DDD435DF5B82E20EA20C7EFE | SHA256:963E3A1E46D5F4C35B85464DB61B7C346C5C44669E64A5C016192DDE078F997A | |||
| 4008 | SQLi Dumper.exe | C:\Users\admin\Desktop\SQLi Dumper v.8.3\TXT\URL Injectables.xml | xml | |
MD5:— | SHA256:— | |||
| 4008 | SQLi Dumper.exe | C:\Users\admin\Desktop\SQLi Dumper v.8.3\TXT\URL Trash.txt | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
643
TCP/UDP connections
1 244
DNS requests
210
Threats
5
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4008 | SQLi Dumper.exe | GET | 301 | 136.243.123.133:80 | http://www.ma-kasse.dk/ft14/udwea.php?hsr=angular-number-picker | DE | — | — | unknown |
4008 | SQLi Dumper.exe | GET | — | 12.9.136.42:80 | http://www.cognoise.com/index.php?topic=32029.0 | US | — | — | unknown |
4008 | SQLi Dumper.exe | GET | 200 | 157.97.107.125:80 | http://community.egroupware.org/index.php?wikipage=ManualCalendarPlanner | DE | html | 6.34 Kb | unknown |
4008 | SQLi Dumper.exe | GET | 200 | 88.208.233.77:80 | http://www.jesushouse.org.uk/products/powerWeb/site/calendarEvents/monthView.php?order=sell_price&sort=desc&page=3&selectedMonth=6&selectedYear=2013&PHPSESSID=61i959p9v8dg0247rqpqnkhfb7 | GB | html | 8.42 Kb | unknown |
4008 | SQLi Dumper.exe | GET | 200 | 164.132.50.204:80 | http://www.saluzzoturistica.it/eventi_scheda.php?id=8919'A=0 | FR | html | 7.79 Kb | unknown |
4008 | SQLi Dumper.exe | GET | 200 | 164.132.50.204:80 | http://www.saluzzoturistica.it/eventi_scheda.php?id=8919 | FR | html | 8.43 Kb | unknown |
4008 | SQLi Dumper.exe | GET | 200 | 77.72.24.71:80 | http://www.spiritojazz.it/it/eventi_scheda.php?ID=109 | IT | html | 2.79 Kb | unknown |
4008 | SQLi Dumper.exe | GET | 200 | 81.29.212.3:80 | http://www.grandigiardini.it/eventi-scheda.php?id=2151 | IT | html | 27.9 Kb | unknown |
4008 | SQLi Dumper.exe | GET | 404 | 136.243.123.133:80 | http://ma-kasse.dk/ft14/udwea.php?hsr=angular-number-picker | DE | html | 73.5 Kb | unknown |
4008 | SQLi Dumper.exe | GET | 404 | 185.24.69.149:80 | http://www.centroglobo.it/eventi-scheda.php?ID=52 | IT | html | 6.29 Kb | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4008 | SQLi Dumper.exe | 12.9.136.42:80 | www.cognoise.com | Avnet Inc. | US | unknown |
4008 | SQLi Dumper.exe | 88.208.233.77:80 | www.jesushouse.org.uk | 1&1 Internet SE | GB | unknown |
4008 | SQLi Dumper.exe | 157.97.107.125:80 | community.egroupware.org | Profitbricks GmbH | DE | unknown |
4008 | SQLi Dumper.exe | 164.132.50.204:80 | www.saluzzoturistica.it | OVH SAS | FR | unknown |
4008 | SQLi Dumper.exe | 216.58.206.9:443 | www.blogger.com | Google Inc. | US | whitelisted |
4008 | SQLi Dumper.exe | 83.166.138.100:443 | www.libreria-locarnese.ch | Infomaniak Network SA | CH | malicious |
4008 | SQLi Dumper.exe | 81.29.212.3:80 | www.grandigiardini.it | Telecitygroup International Limited | IT | unknown |
4008 | SQLi Dumper.exe | 54.38.68.27:443 | www.diabolik.it | OVH SAS | FR | unknown |
4008 | SQLi Dumper.exe | 172.217.18.13:443 | accounts.google.com | Google Inc. | US | whitelisted |
4008 | SQLi Dumper.exe | 185.2.4.96:80 | www.turboalgor.it | Simply Transit Ltd | IT | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.google.com |
| malicious |
www.blogger.com |
| shared |
www.jesushouse.org.uk |
| unknown |
www.ma-kasse.dk |
| unknown |
www.cognoise.com |
| unknown |
community.egroupware.org |
| unknown |
accounts.google.com |
| shared |
www.saluzzoturistica.it |
| unknown |
www.libreria-locarnese.ch |
| malicious |
www.diabolik.it |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
4008 | SQLi Dumper.exe | Misc activity | [PT SUSPICIOUS] JS obfuscation (obfuscator.io) |
4008 | SQLi Dumper.exe | Web Application Attack | ET WEB_CLIENT Possible HTTP 500 XSS Attempt (External Source) |
4008 | SQLi Dumper.exe | Web Application Attack | ET WEB_CLIENT Possible HTTP 500 XSS Attempt (External Source) |
4008 | SQLi Dumper.exe | Web Application Attack | ET WEB_CLIENT Possible HTTP 500 XSS Attempt (External Source) |
4008 | SQLi Dumper.exe | Web Application Attack | ET WEB_CLIENT Possible HTTP 500 XSS Attempt (External Source) |