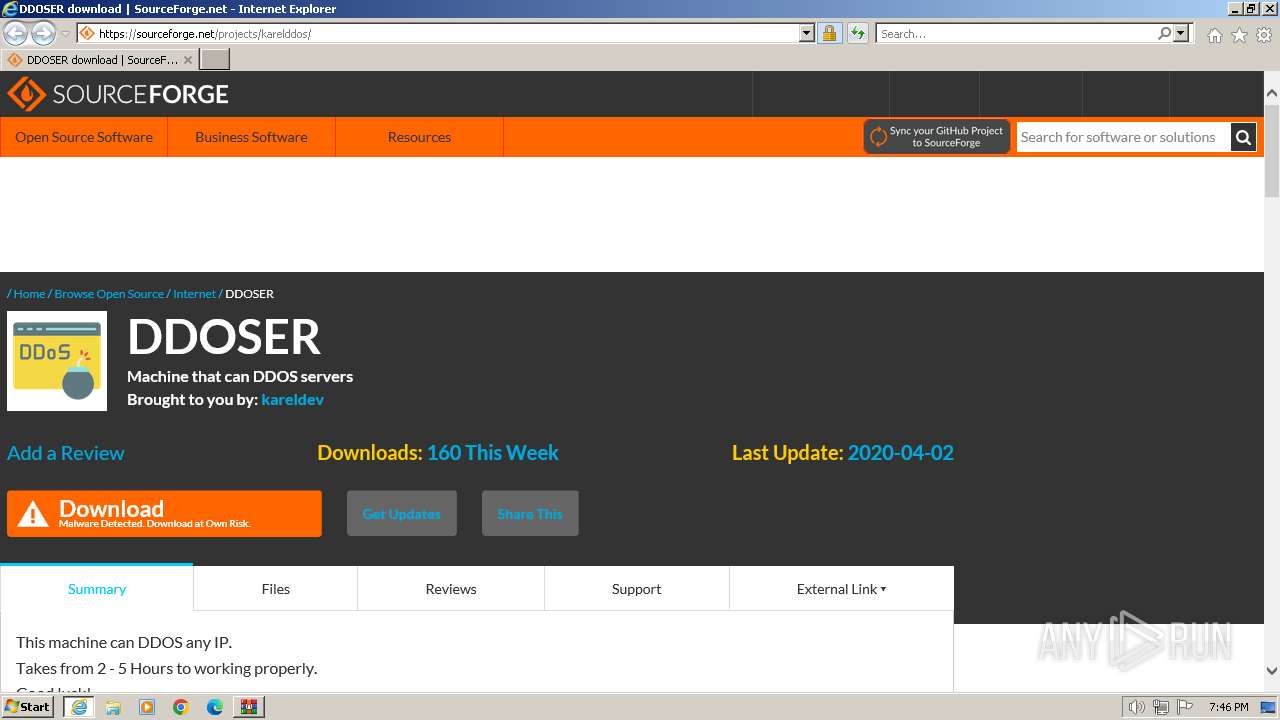
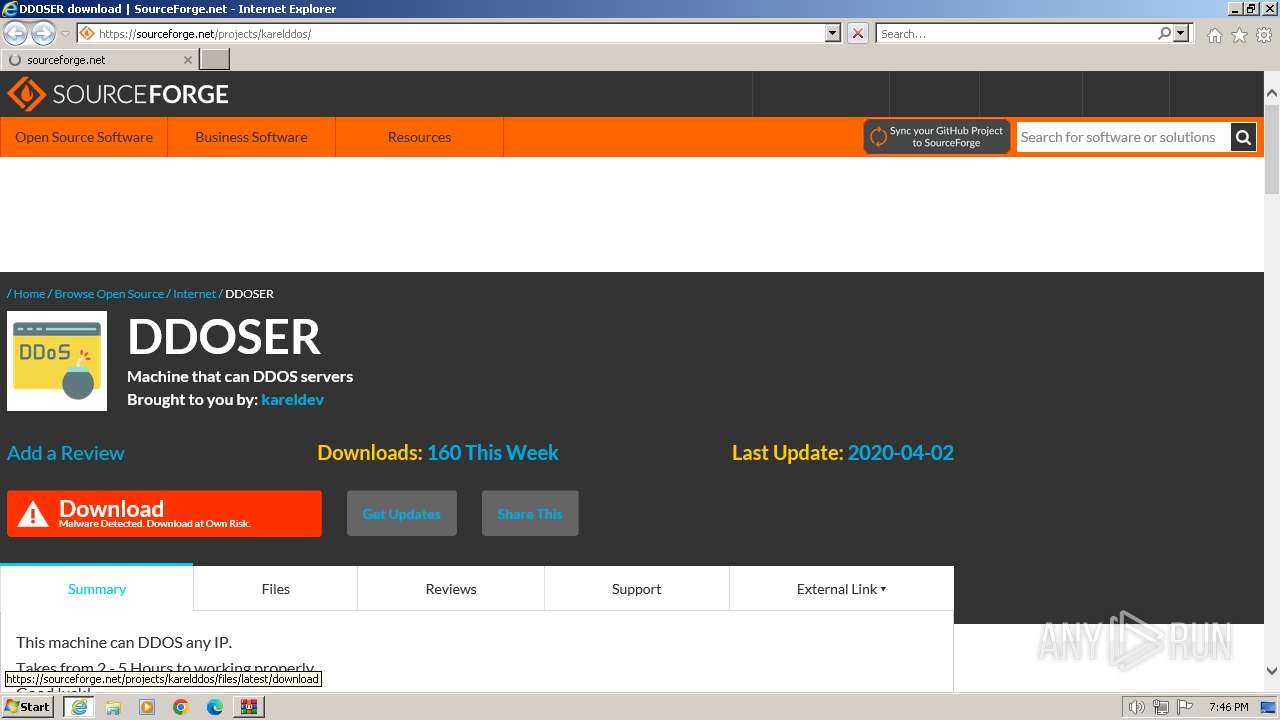
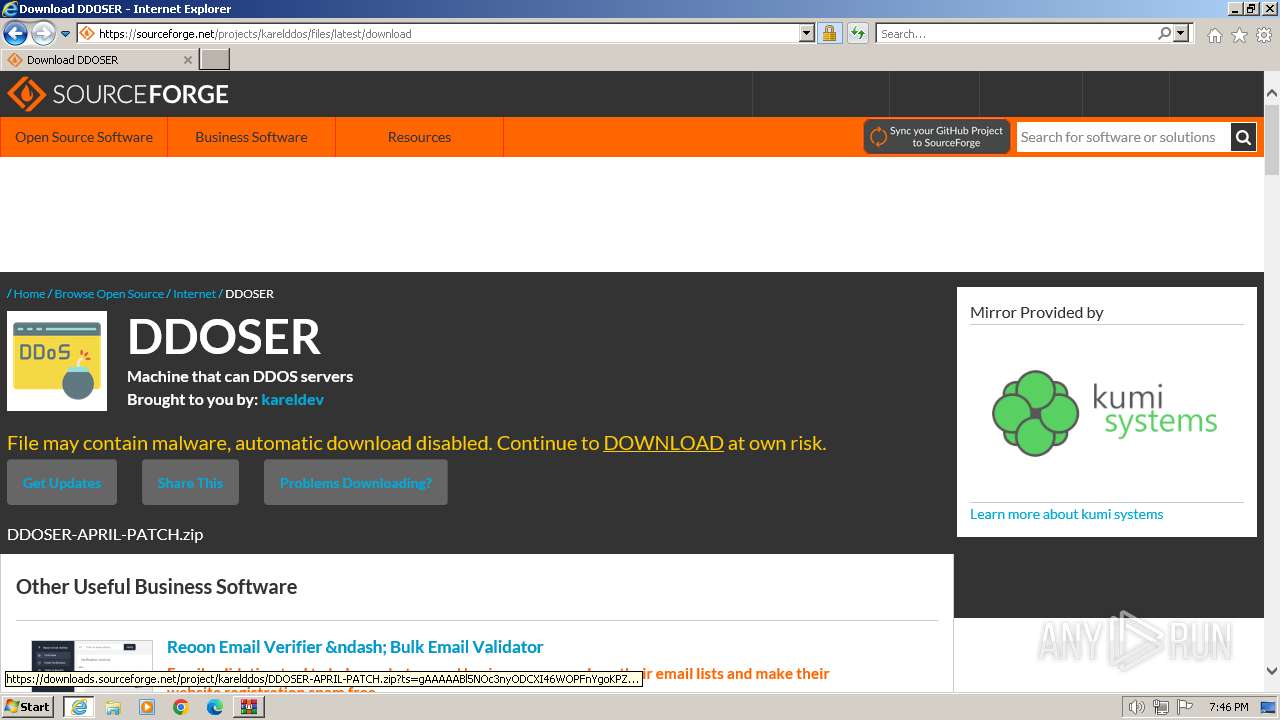
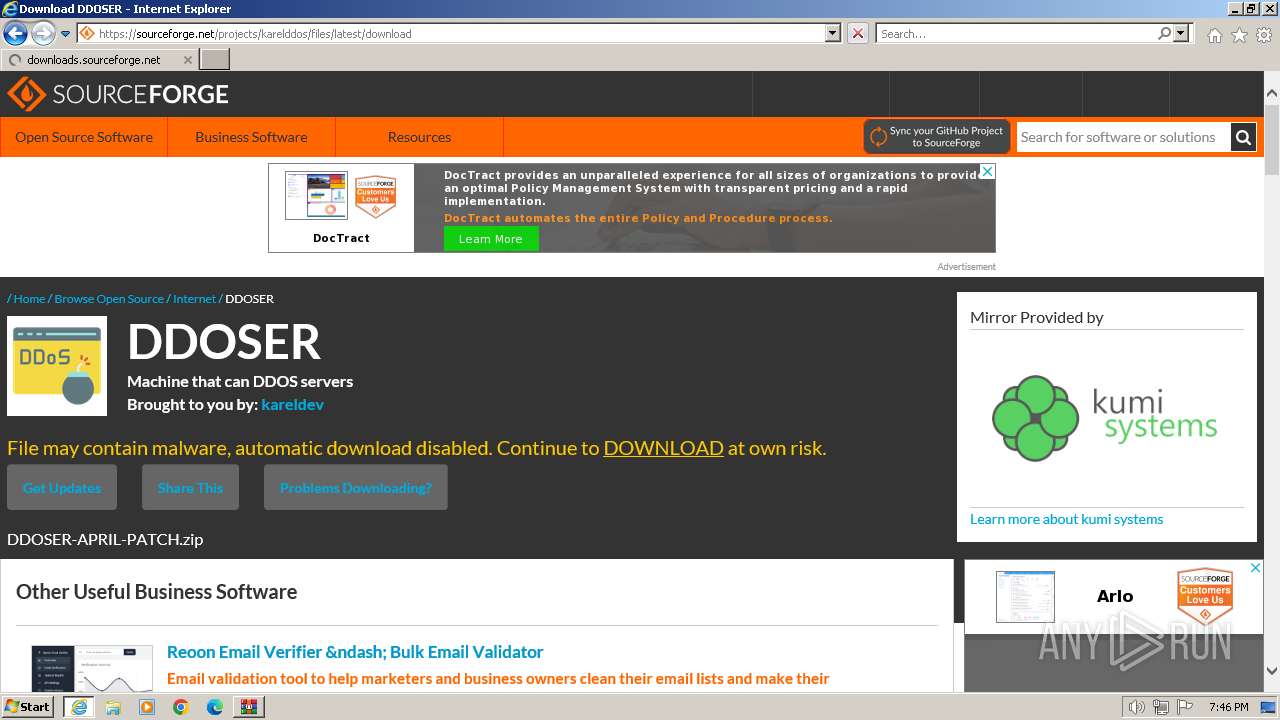
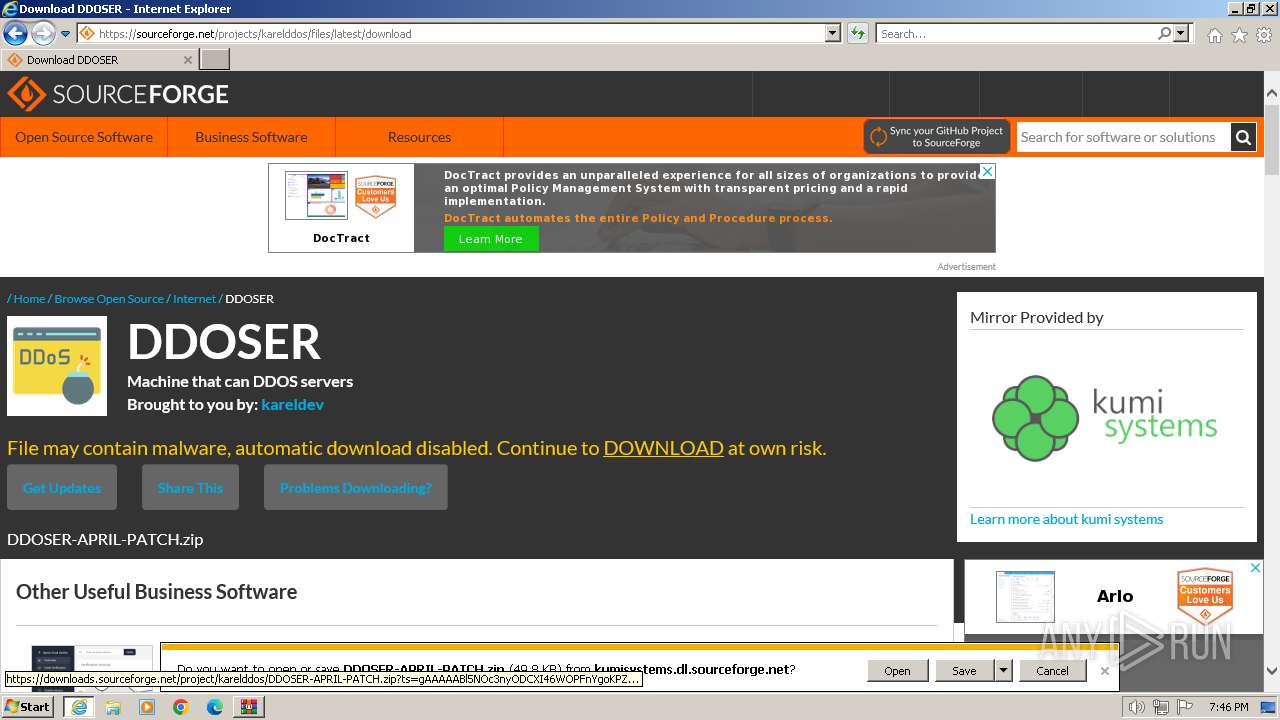
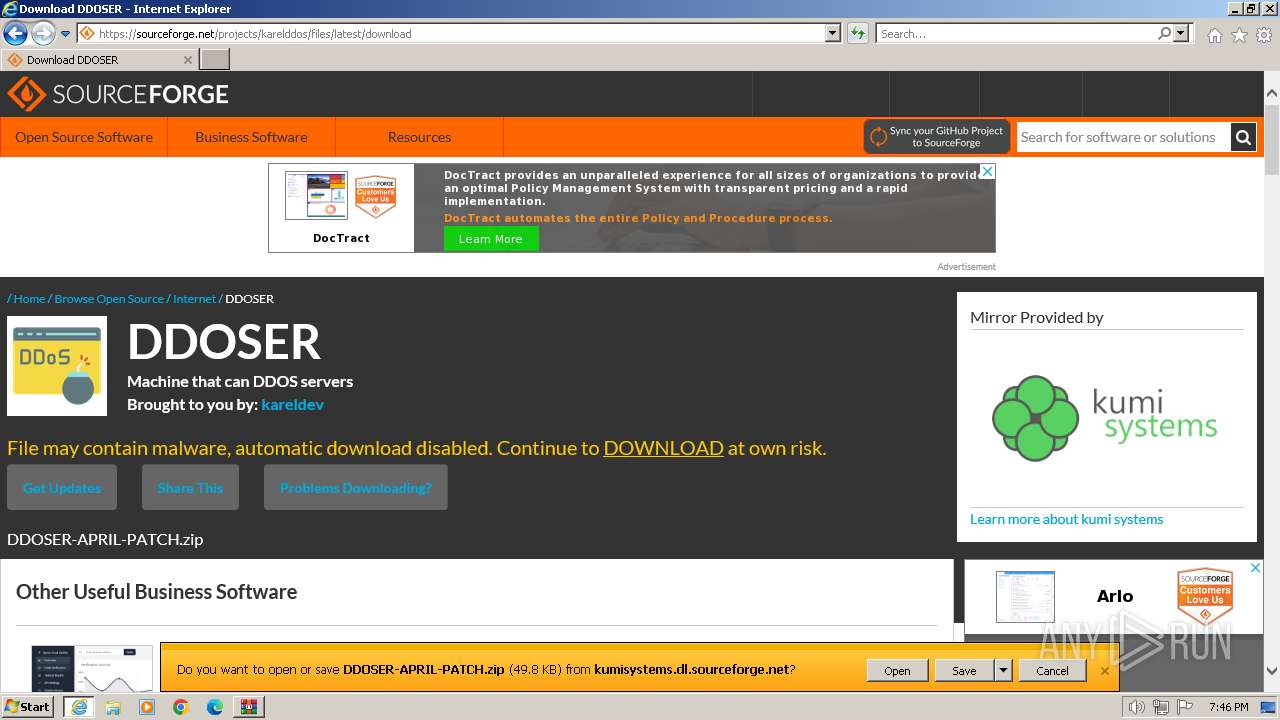
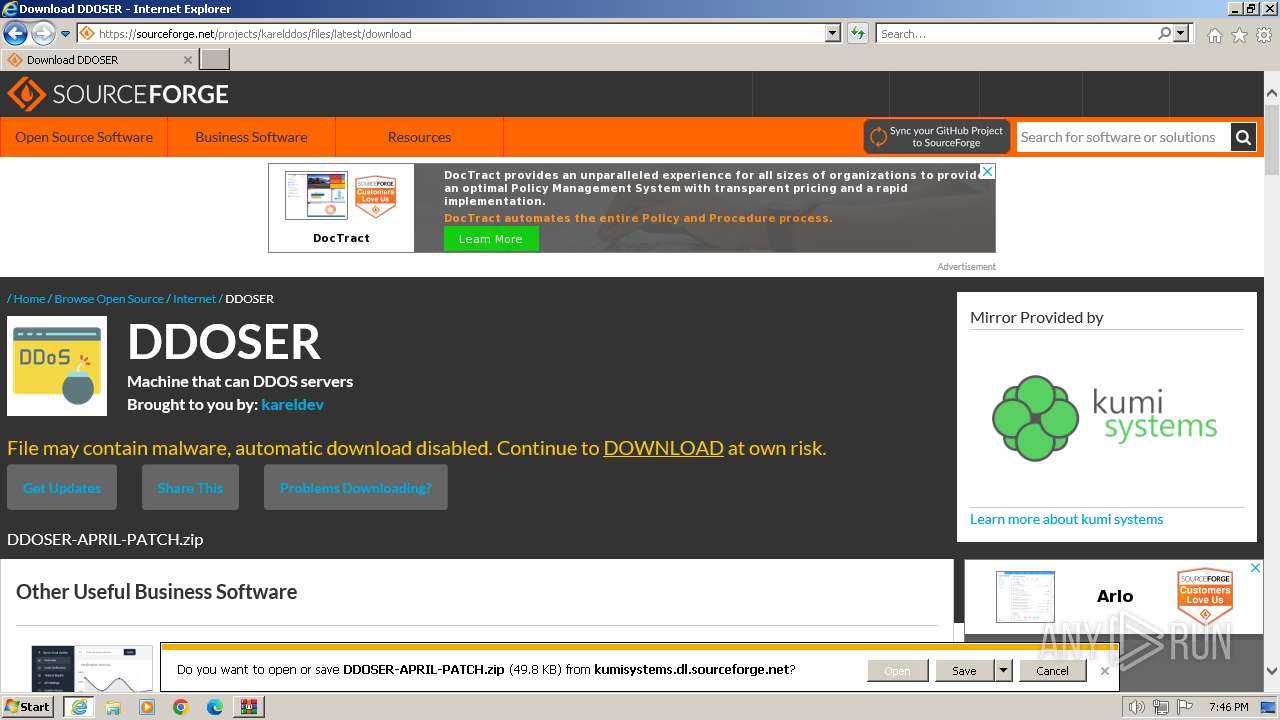
| File name: | AppNee.com.XOIC.v1.3.Final.7z |
| Full analysis: | https://app.any.run/tasks/6b882ea5-d56a-4617-8402-165fa92b7d04 |
| Verdict: | Malicious activity |
| Analysis date: | March 03, 2024, 19:46:00 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-7z-compressed |
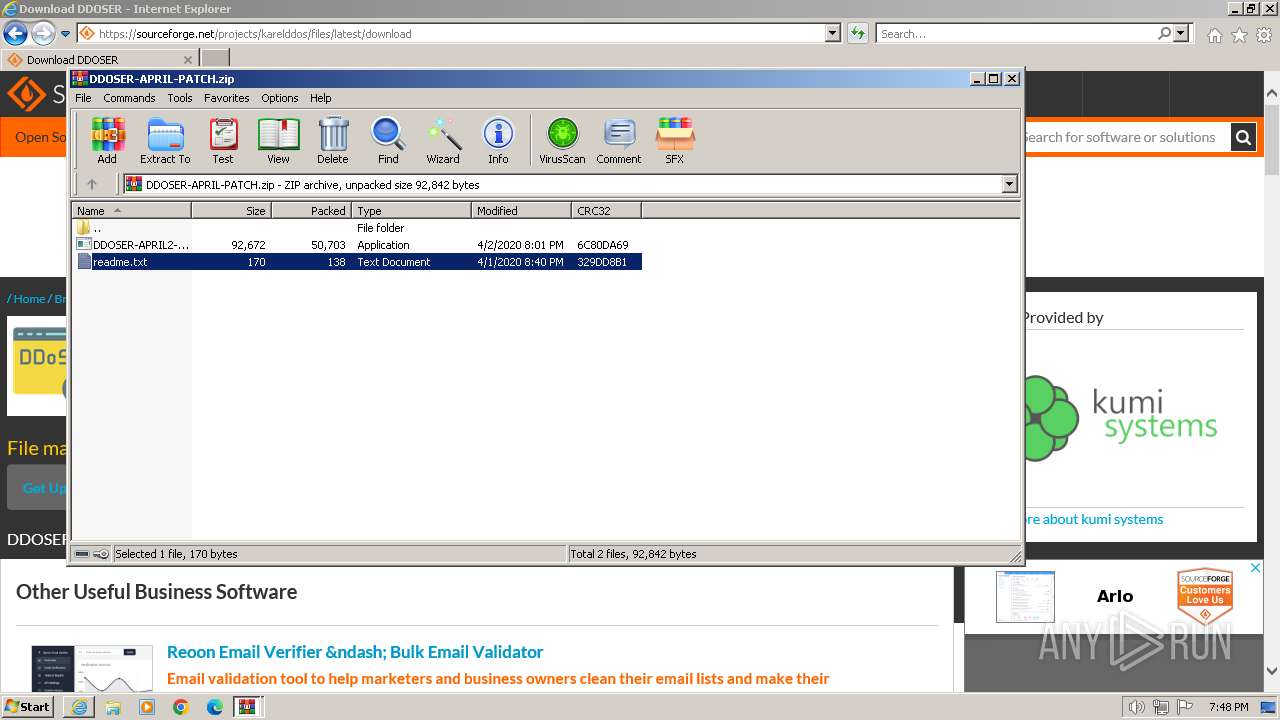
| File info: | 7-zip archive data, version 0.4 |
| MD5: | 5C25332FFEBFBC705D4774E7876F17A9 |
| SHA1: | CD0879E54D997430357B659AD83F1A2DD8271D1F |
| SHA256: | B835A76C4F5541B20BD5E659D836F84F6C1C00CA7C5D2DC93B0AE6027B861B9F |
| SSDEEP: | 12288:rP2sOAAYKiNXQI+mAJXwv+waA0UvIHNhItfkq35m:rP2sfAjiNQI+mAJXwvqA0UwHXItcq35m |
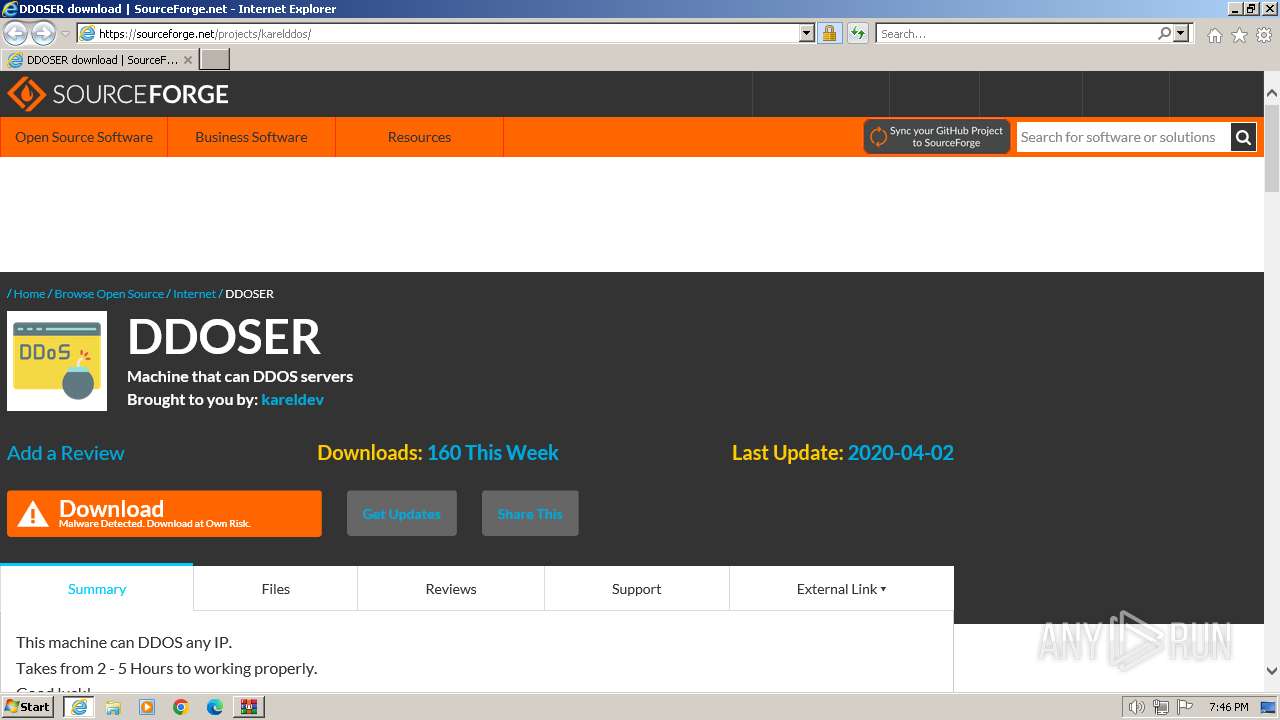
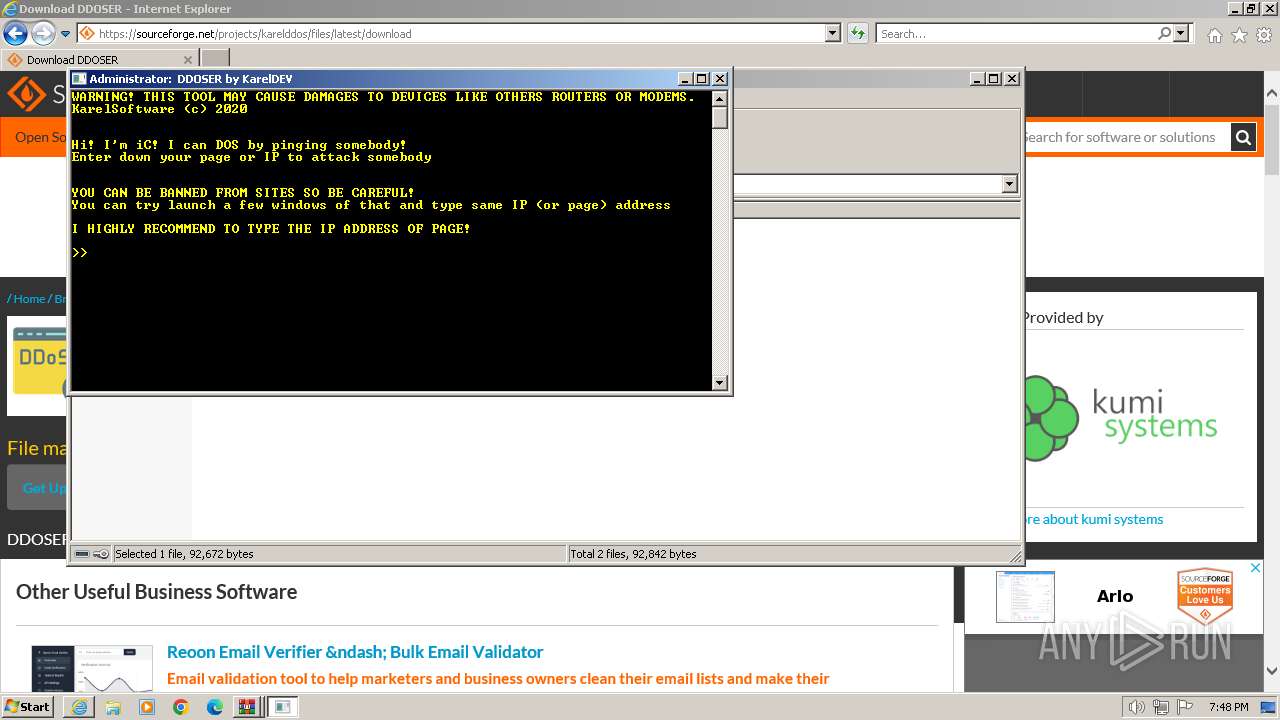
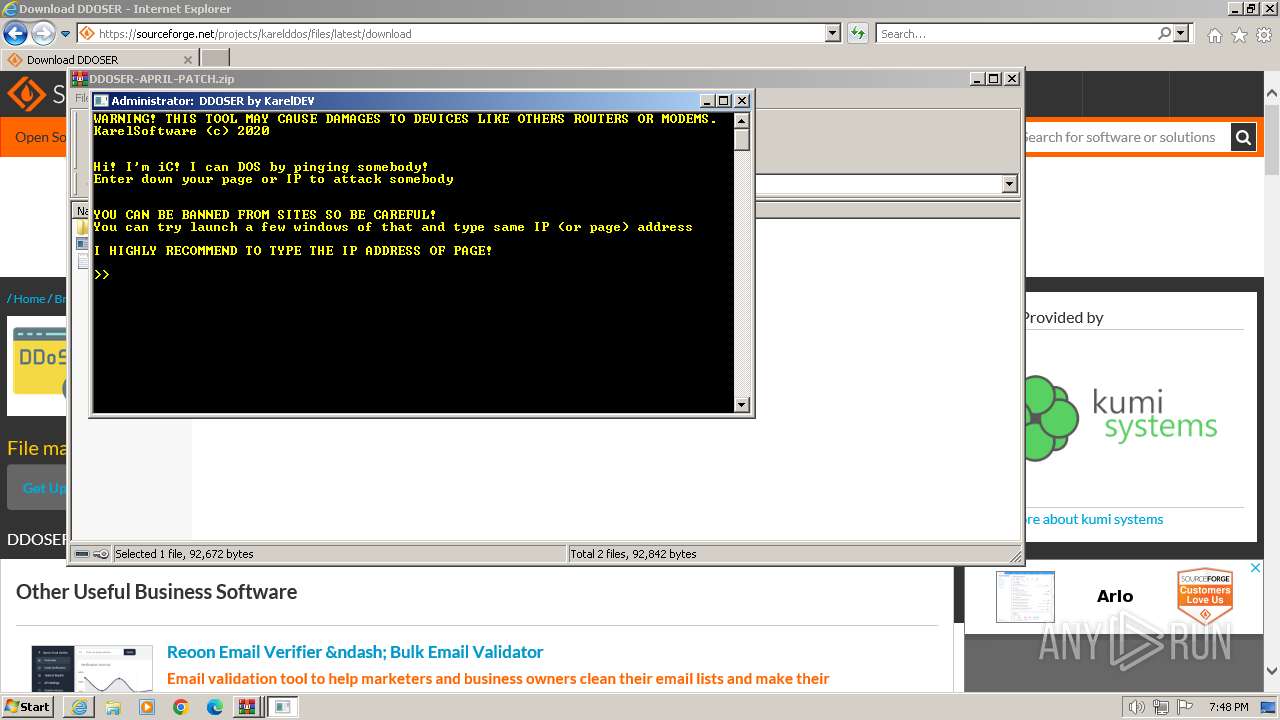
MALICIOUS
Drops the executable file immediately after the start
- WinRAR.exe (PID: 4052)
SUSPICIOUS
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 4052)
- WinRAR.exe (PID: 1572)
- XOIC_1.3.exe (PID: 3716)
Reads the Internet Settings
- XOIC_1.3.exe (PID: 3716)
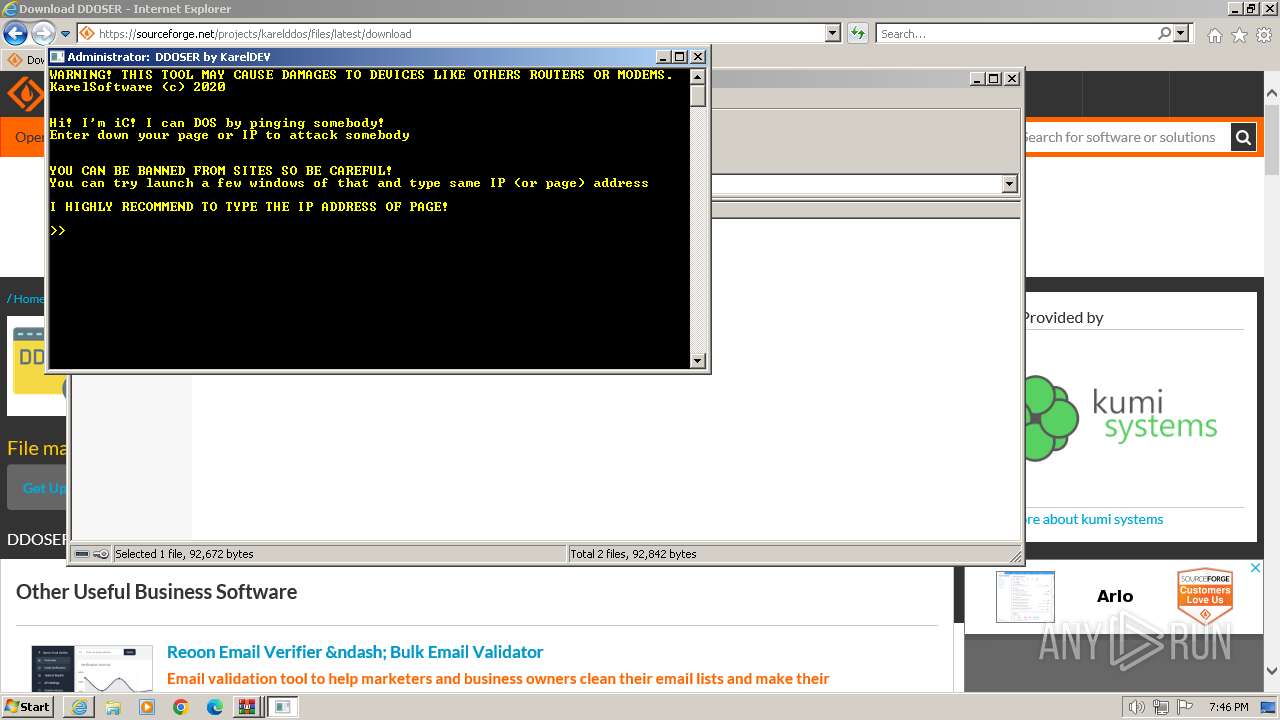
Start notepad (likely ransomware note)
- WinRAR.exe (PID: 1572)
Starts CMD.EXE for commands execution
- DDOSER-APRIL2-PATCH.exe (PID: 2244)
- DDOSER-APRIL2-PATCH.exe (PID: 3352)
- DDOSER-APRIL2-PATCH.exe (PID: 2560)
Executing commands from a ".bat" file
- DDOSER-APRIL2-PATCH.exe (PID: 2560)
- DDOSER-APRIL2-PATCH.exe (PID: 3352)
- DDOSER-APRIL2-PATCH.exe (PID: 2244)
INFO
Checks supported languages
- wmpnscfg.exe (PID: 3864)
- XOIC_1.3.exe (PID: 3716)
- DDOSER-APRIL2-PATCH.exe (PID: 2244)
- DDOSER-APRIL2-PATCH.exe (PID: 2560)
- DDOSER-APRIL2-PATCH.exe (PID: 3352)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 4052)
- WinRAR.exe (PID: 1572)
Reads the computer name
- wmpnscfg.exe (PID: 3864)
- XOIC_1.3.exe (PID: 3716)
Reads the machine GUID from the registry
- XOIC_1.3.exe (PID: 3716)
Creates files in the program directory
- XOIC_1.3.exe (PID: 3716)
The process uses the downloaded file
- iexplore.exe (PID: 2036)
- WinRAR.exe (PID: 1572)
Create files in a temporary directory
- XOIC_1.3.exe (PID: 3716)
- DDOSER-APRIL2-PATCH.exe (PID: 2244)
- DDOSER-APRIL2-PATCH.exe (PID: 2560)
- DDOSER-APRIL2-PATCH.exe (PID: 3352)
Drops the executable file immediately after the start
- WinRAR.exe (PID: 1572)
Modifies the phishing filter of IE
- iexplore.exe (PID: 2036)
Application launched itself
- iexplore.exe (PID: 2036)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .7z | | | 7-Zip compressed archive (v0.4) (57.1) |
|---|---|---|
| .7z | | | 7-Zip compressed archive (gen) (42.8) |
Total processes
67
Monitored processes
18
Malicious processes
0
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 784 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa1572.30087\DDOSER-APRIL2-PATCH.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa1572.30087\DDOSER-APRIL2-PATCH.exe | — | WinRAR.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 984 | "C:\Windows\system32\cmd" /c "C:\Users\admin\AppData\Local\Temp\CF2D.tmp\CF2E.tmp\CF2F.bat C:\Users\admin\AppData\Local\Temp\Rar$EXa1572.27429\DDOSER-APRIL2-PATCH.exe" | C:\Windows\System32\cmd.exe | — | DDOSER-APRIL2-PATCH.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1216 | ping miamc.pl -t -l 65535 | C:\Windows\System32\PING.EXE | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: TCP/IP Ping Command Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1572 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\PO2HN1X2\DDOSER-APRIL-PATCH.zip" | C:\Program Files\WinRAR\WinRAR.exe | iexplore.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 1576 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa1572.19358\DDOSER-APRIL2-PATCH.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa1572.19358\DDOSER-APRIL2-PATCH.exe | — | WinRAR.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
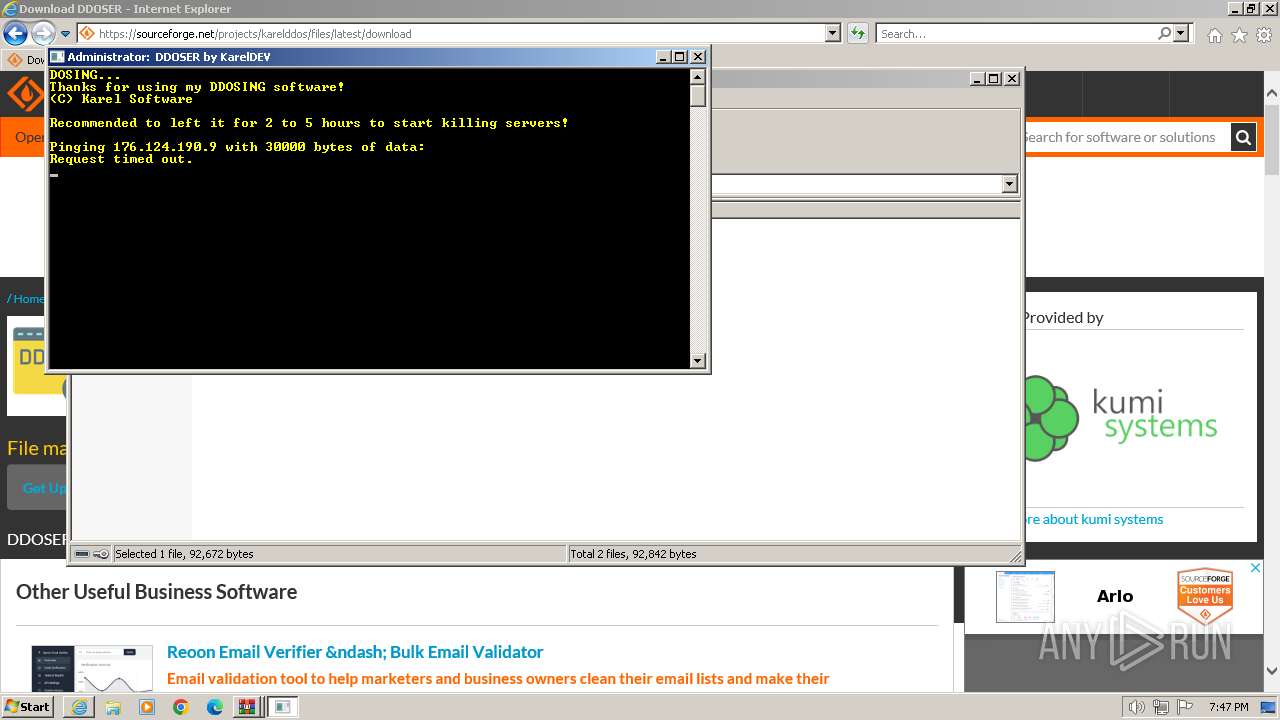
| 1864 | ping 176.124.190.9 -t -l 30000 | C:\Windows\System32\PING.EXE | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: TCP/IP Ping Command Exit code: 3221225786 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1956 | "C:\Windows\system32\cmd" /c "C:\Users\admin\AppData\Local\Temp\36F0.tmp\36F1.tmp\36F2.bat C:\Users\admin\AppData\Local\Temp\Rar$EXa1572.30087\DDOSER-APRIL2-PATCH.exe" | C:\Windows\System32\cmd.exe | — | DDOSER-APRIL2-PATCH.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2036 | "C:\Program Files\Internet Explorer\iexplore.exe" http://sourceforge.net/projects/xoic/ | C:\Program Files\Internet Explorer\iexplore.exe | XOIC_1.3.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2244 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa1572.19358\DDOSER-APRIL2-PATCH.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa1572.19358\DDOSER-APRIL2-PATCH.exe | WinRAR.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 2560 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa1572.27429\DDOSER-APRIL2-PATCH.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa1572.27429\DDOSER-APRIL2-PATCH.exe | WinRAR.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 1 Modules
| |||||||||||||||
Total events
33 459
Read events
33 256
Write events
167
Delete events
36
Modification events
| (PID) Process: | (4052) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (4052) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (4052) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (4052) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (4052) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (4052) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\curl-8.5.0_1-win32-mingw.zip | |||
| (PID) Process: | (4052) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\AppNee.com.XOIC.v1.3.Final.7z | |||
| (PID) Process: | (4052) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (4052) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (4052) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
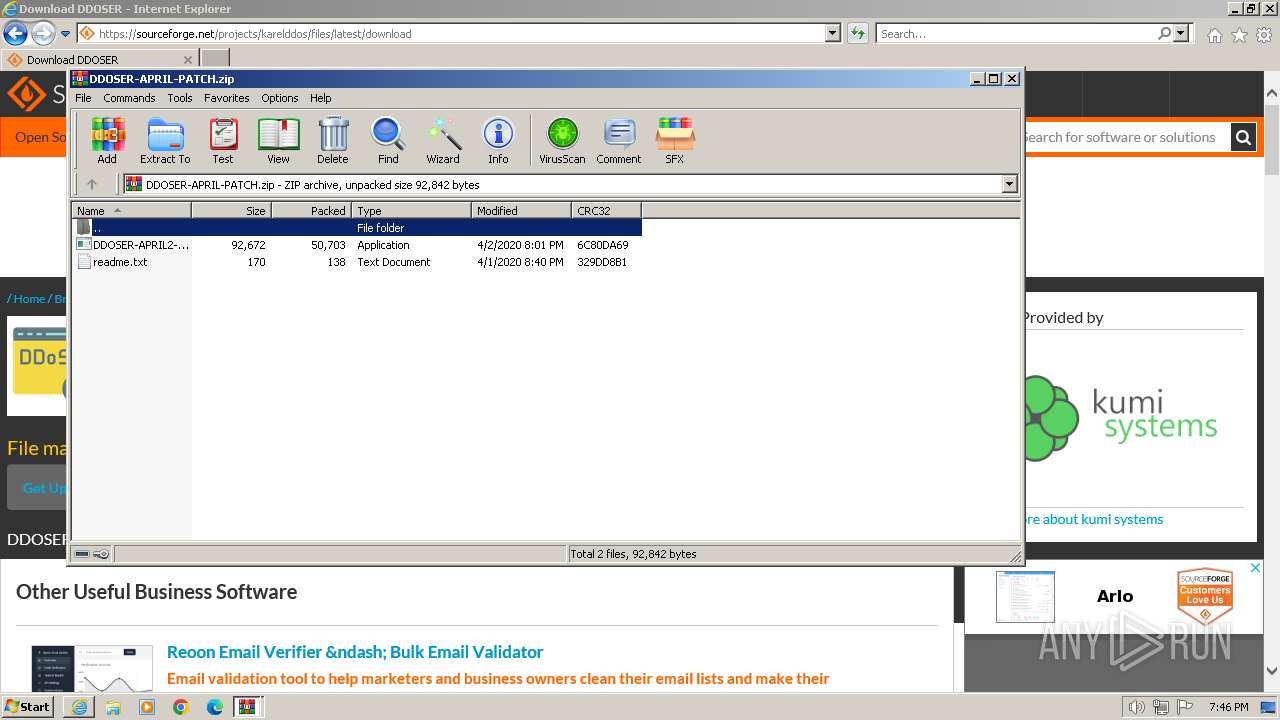
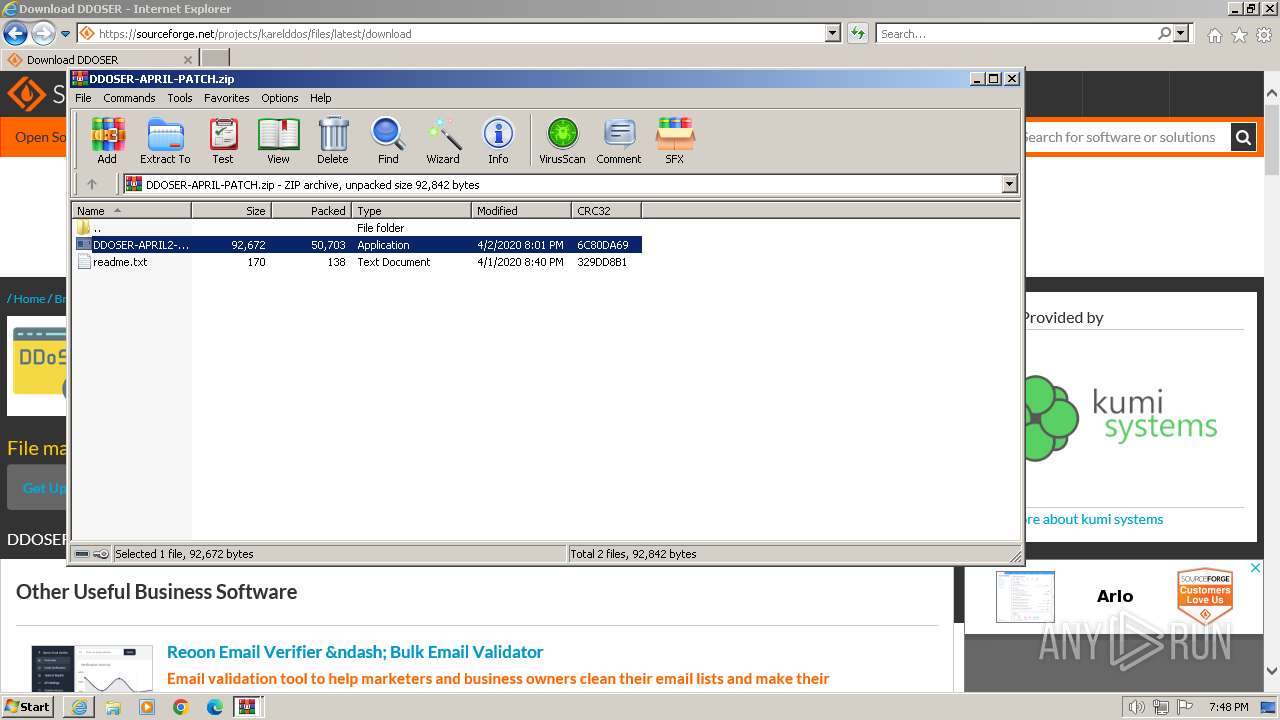
Executable files
4
Suspicious files
38
Text files
134
Unknown types
22
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4052 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa4052.16498\XOIC_1.3.exe | executable | |
MD5:B6C4E2C4FA384212126D7DBB832460C9 | SHA256:1AB7EDE95C3811F3019114853291E46AD6E041E9E20AC640AC1A4A45B3743484 | |||
| 3948 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\YTOWV792\karelddos[1].htm | html | |
MD5:A4F71271C83C40A8930E760A7F7F576F | SHA256:692A99BEE26296A772AFD0EAFD759898417746EBABB27C6B79C3A3AD006F0102 | |||
| 4052 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa4052.16498\Original source.url | url | |
MD5:1BFB173207BEF41F4E5CB389A2420C91 | SHA256:0C44EDAC72838E4D4DC074ADA81299972B55CB207BF77800CAD322EC80958834 | |||
| 3948 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\6BADA8974A10C4BD62CC921D13E43B18_28DEA62A0AE77228DD387E155AD0BA27 | binary | |
MD5:5B2BF76C3734460EF71A0D79F4EDF0E7 | SHA256:0A48D1D9204BBDEE420840308388FEC1059DEB01C5515642656FEC26601659A4 | |||
| 3948 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\xoic[1].htm | html | |
MD5:225679F4AB850DD73F9C06465F5B3BCE | SHA256:073B76B51C5AEFB15CCE3BFDCC9D9322A872B84AEB7A7CCDF20B9C271BA3EF12 | |||
| 3948 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\YTOWV792\lato[1].css | text | |
MD5:8F61F228AD51184B5F8BBBF14B436DF9 | SHA256:DA04907546EDDC4640039BB9EFBBB483D220B1E4EC553F9830A9510B7FF14899 | |||
| 3948 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:9A89FA89ACE220C2D7415E2C0BDCB73E | SHA256:A2FF6F910A58E2FA5BC32EFF5B4365394AEF60A5585201D36974DF29CBC104C5 | |||
| 3948 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\3ZC5OO25.txt | text | |
MD5:FA89083DBFEB17CCADD24B299EB3872D | SHA256:E0320AB2CAEA4ED50C949358599D908C7F3C135BF383C7FF0BDABD31008EA4E4 | |||
| 3948 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\cmp[1].css | text | |
MD5:38C8ACF2B4EF7DEF65BACFB6E9A26E8E | SHA256:4BAAE150A27BC5716BA8F5160FBD2414F5B731C470D8EE0956612DAFA106E950 | |||
| 3948 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\sf.sandiego-foundation-tooltip[1].js | text | |
MD5:4A124B39D226B45BD81EBE53D6F2E404 | SHA256:E71F9ED65E086AB36B4243D164B94D967AF8C2D646D8D892BF6AE91CF5DDF28B | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
27
TCP/UDP connections
74
DNS requests
33
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3948 | iexplore.exe | GET | 301 | 104.18.37.111:80 | http://sourceforge.net/projects/xoic/ | unknown | html | 155 b | unknown |
3948 | iexplore.exe | GET | 304 | 95.100.155.18:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?347ff5da01d15dfa | unknown | — | — | unknown |
3948 | iexplore.exe | GET | 200 | 95.100.155.18:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?d2c34cf216b6a9ce | unknown | compressed | 67.5 Kb | unknown |
3948 | iexplore.exe | GET | 200 | 23.218.185.6:80 | http://x1.c.lencr.org/ | unknown | binary | 717 b | unknown |
3948 | iexplore.exe | GET | 200 | 95.100.155.18:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?ce33215c677fb6f4 | unknown | compressed | 67.5 Kb | unknown |
2036 | iexplore.exe | GET | 304 | 95.100.155.18:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?b2852a8256b664f1 | unknown | — | — | unknown |
3948 | iexplore.exe | GET | 200 | 2.19.51.203:80 | http://r3.o.lencr.org/MFMwUTBPME0wSzAJBgUrDgMCGgUABBRI2smg%2ByvTLU%2Fw3mjS9We3NfmzxAQUFC6zF7dYVsuuUAlA5h%2BvnYsUwsYCEgOvW5TnAsKWJdPl7O5crgrcOg%3D%3D | unknown | binary | 503 b | unknown |
3948 | iexplore.exe | GET | 200 | 142.250.74.195:80 | http://ocsp.pki.goog/gsr1/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCEHe9DWzbNvka6iEPxPBY0w0%3D | unknown | binary | 1.41 Kb | unknown |
3948 | iexplore.exe | GET | 200 | 142.250.74.195:80 | http://ocsp.pki.goog/gtsr1/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBQwkcLWD4LqGJ7bE7B1XZsEbmfwUAQU5K8rJnEaK0gnhS9SZizv8IkTcT4CDQIDvFCjJ1PwkYAi7fE%3D | unknown | binary | 724 b | unknown |
2036 | iexplore.exe | GET | 304 | 95.100.155.18:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?88f31c7f87962ef8 | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
3948 | iexplore.exe | 104.18.37.111:80 | sourceforge.net | CLOUDFLARENET | — | unknown |
3948 | iexplore.exe | 104.18.37.111:443 | sourceforge.net | CLOUDFLARENET | — | unknown |
3948 | iexplore.exe | 95.100.155.18:80 | ctldl.windowsupdate.com | Akamai International B.V. | DK | unknown |
3948 | iexplore.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
3948 | iexplore.exe | 104.18.40.209:443 | a.fsdn.com | CLOUDFLARENET | — | shared |
3948 | iexplore.exe | 87.230.98.76:443 | d.delivery.consentmanager.net | PlusServer GmbH | DE | unknown |
3948 | iexplore.exe | 156.146.33.138:443 | cdn.consentmanager.net | Datacamp Limited | DE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
sourceforge.net |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
a.fsdn.com |
| whitelisted |
d.delivery.consentmanager.net |
| unknown |
cdn.consentmanager.net |
| malicious |
x1.c.lencr.org |
| whitelisted |
c.sf-syn.com |
| whitelisted |
r3.o.lencr.org |
| shared |
api.bing.com |
| whitelisted |