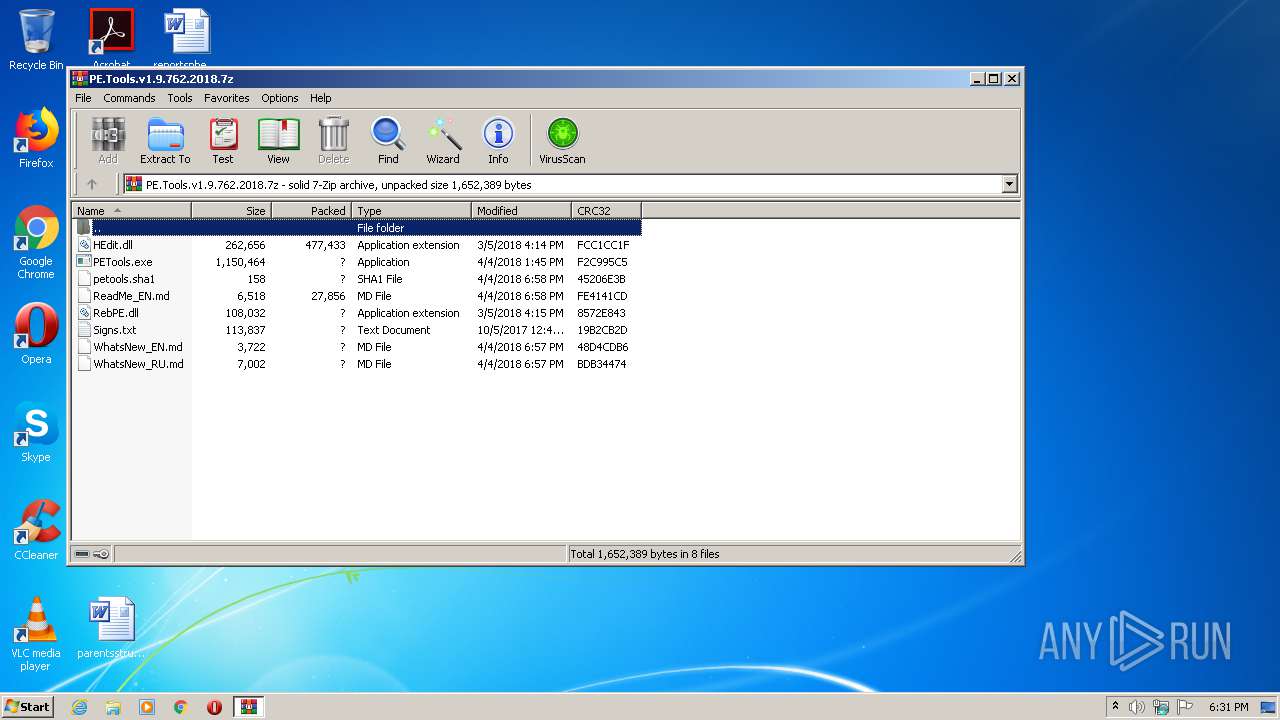
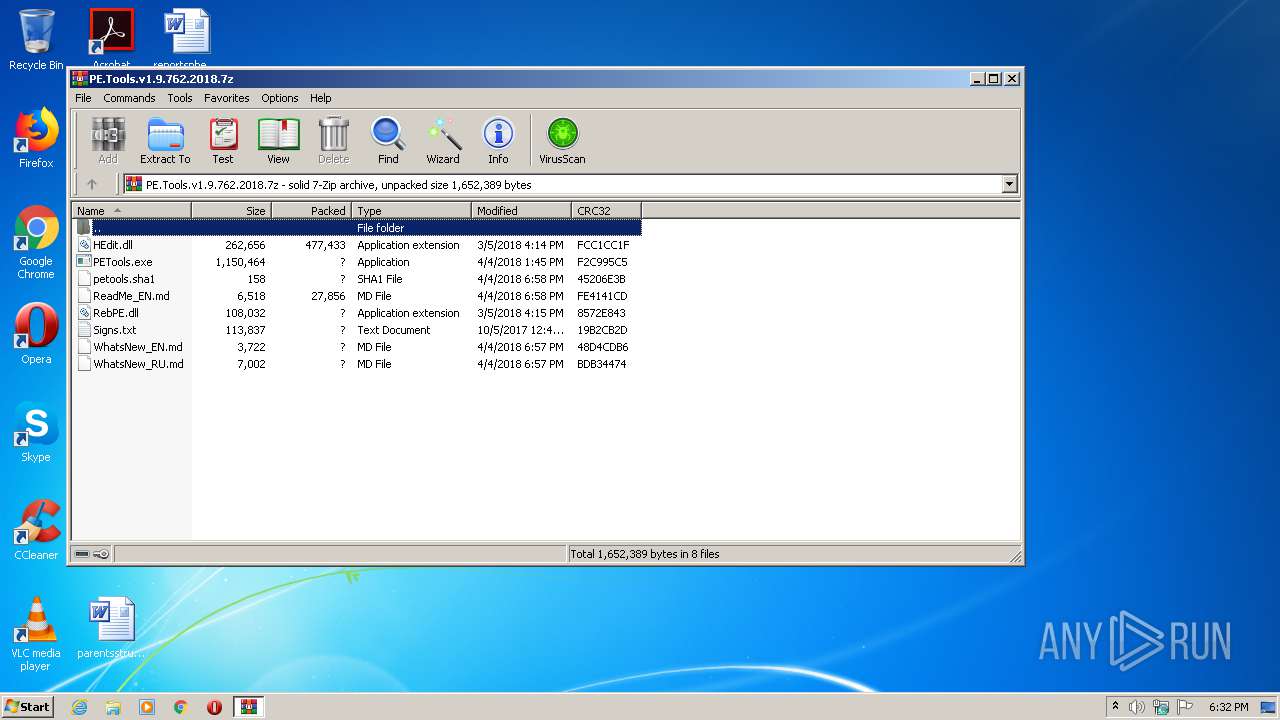
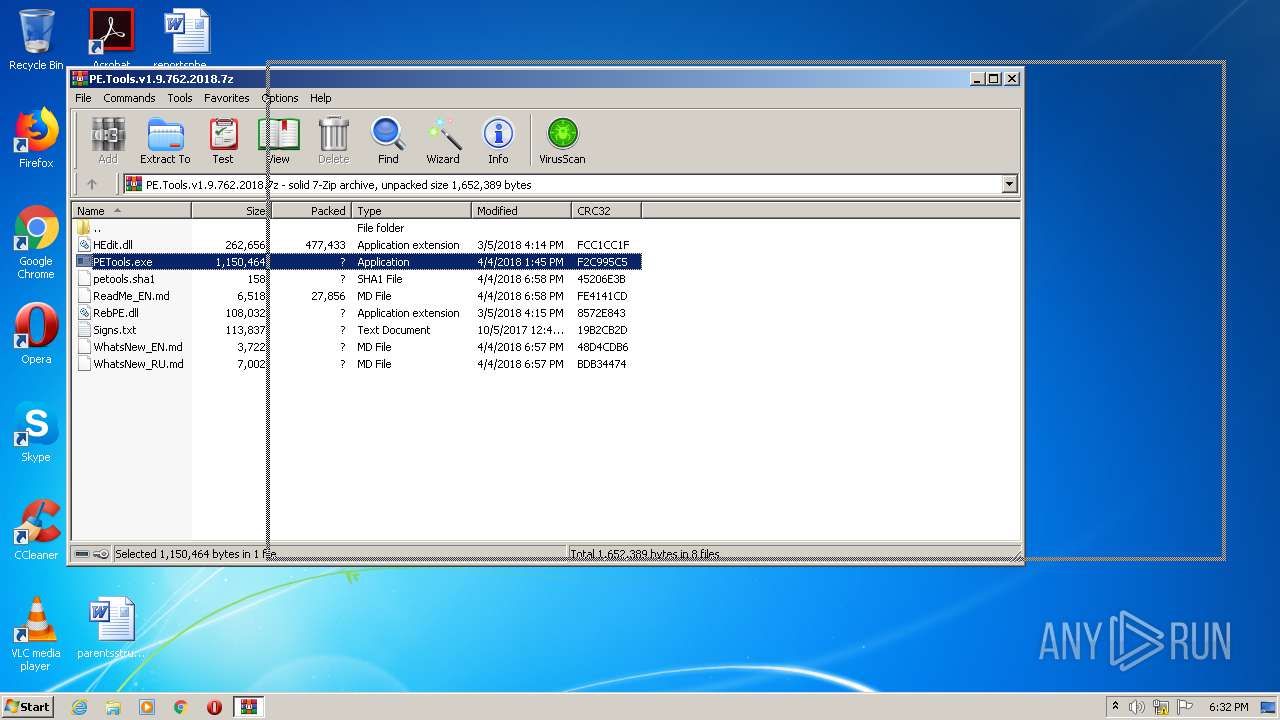
| download: | PE.Tools.v1.9.762.2018.7z |
| Full analysis: | https://app.any.run/tasks/7ec77525-8088-4fba-a7b6-a09e8d17f06b |
| Verdict: | Malicious activity |
| Analysis date: | February 24, 2021, 18:31:17 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-7z-compressed |
| File info: | 7-zip archive data, version 0.4 |
| MD5: | 153B77CF7850E3CFDF2BAFBF2C59646B |
| SHA1: | 57CD37AA66AB6B72E1FF68E47111142EC50AFB41 |
| SHA256: | B831343A1441039C68A60777CEF9ECB1F41381BFF369C2F993CD3DB6BF8C9FB8 |
| SSDEEP: | 12288:sJlC8bvliexxSe2jYEy7ZQo8mgiMK2bATiNCH/4yG1+0ccOh5:sS8EPjfytQ2giMK2bOuCH/4ydFv |
MALICIOUS
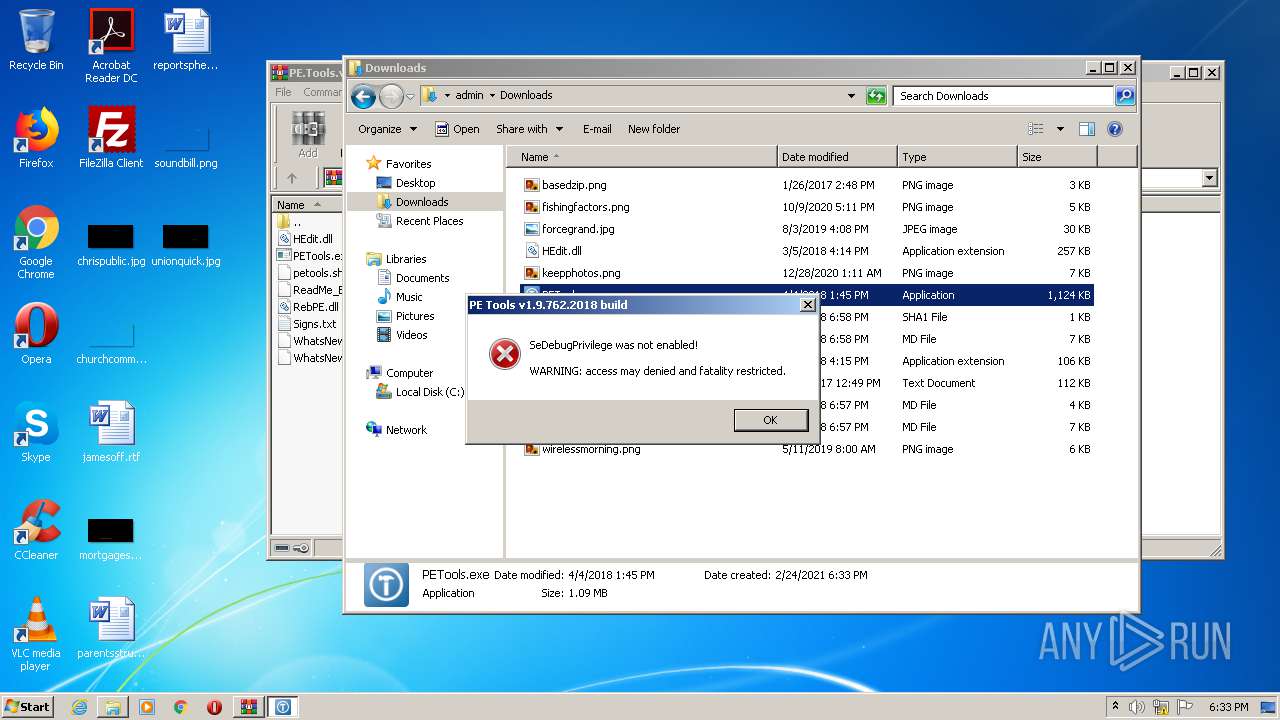
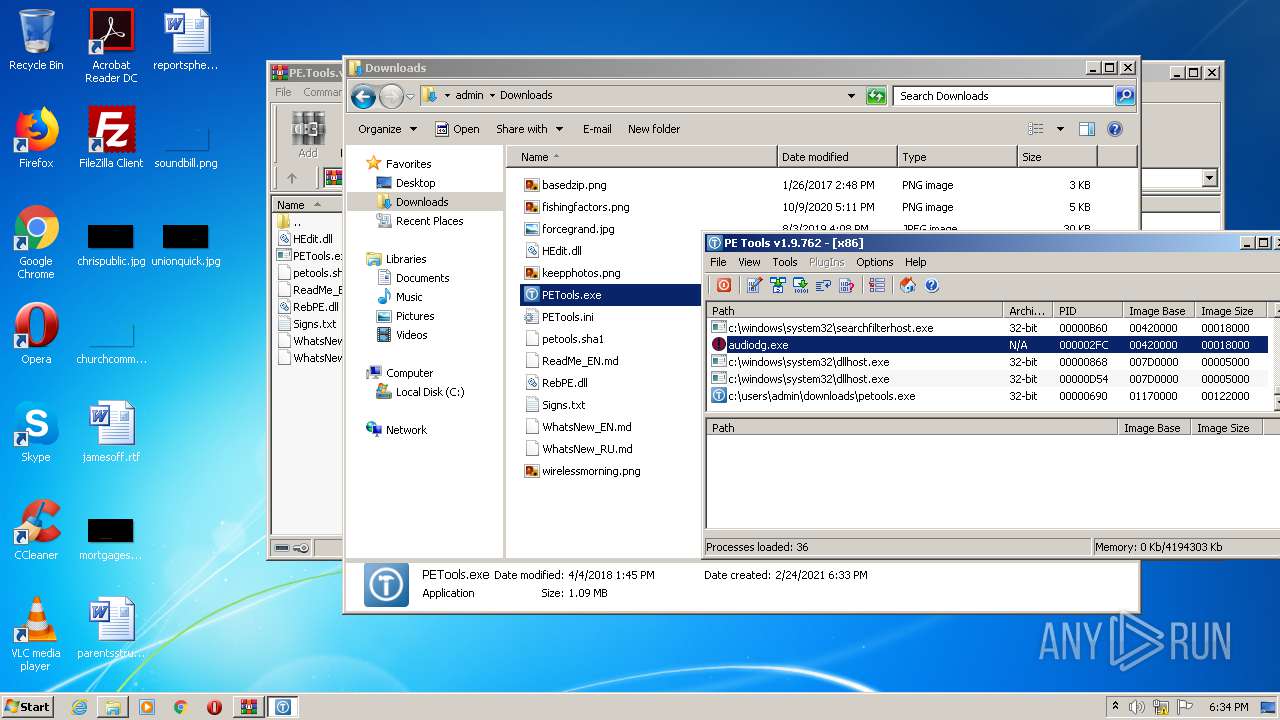
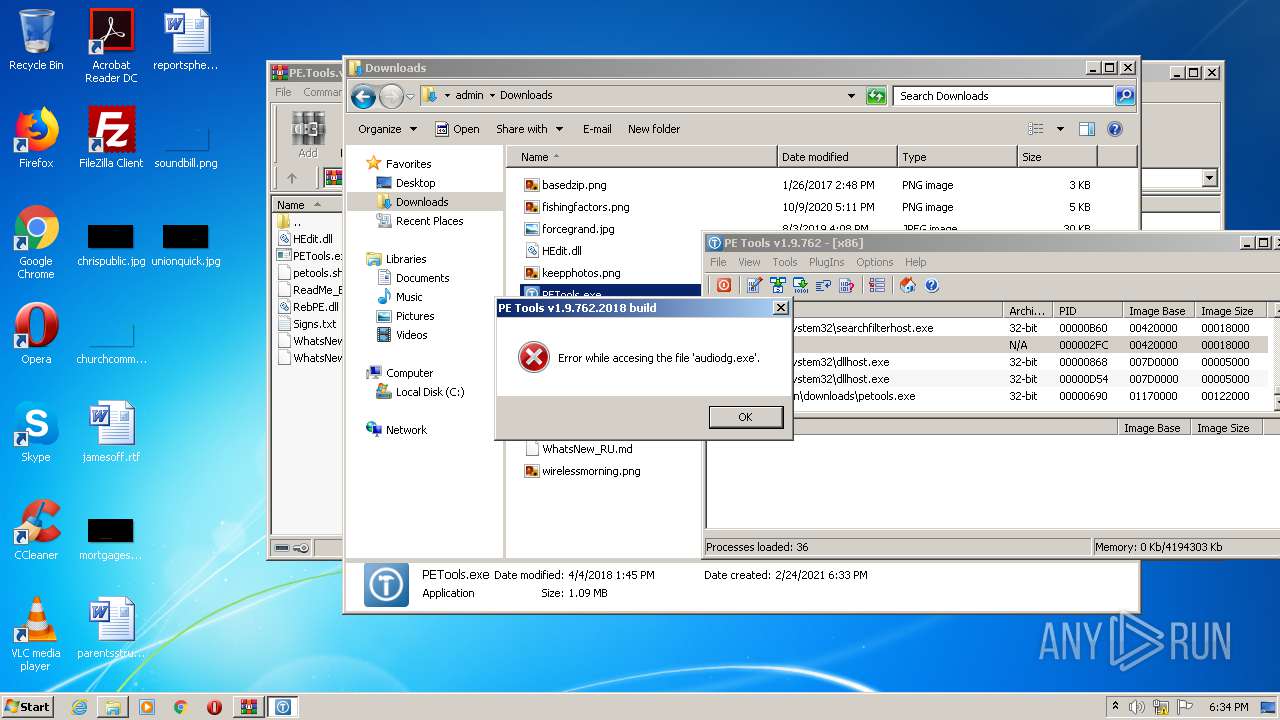
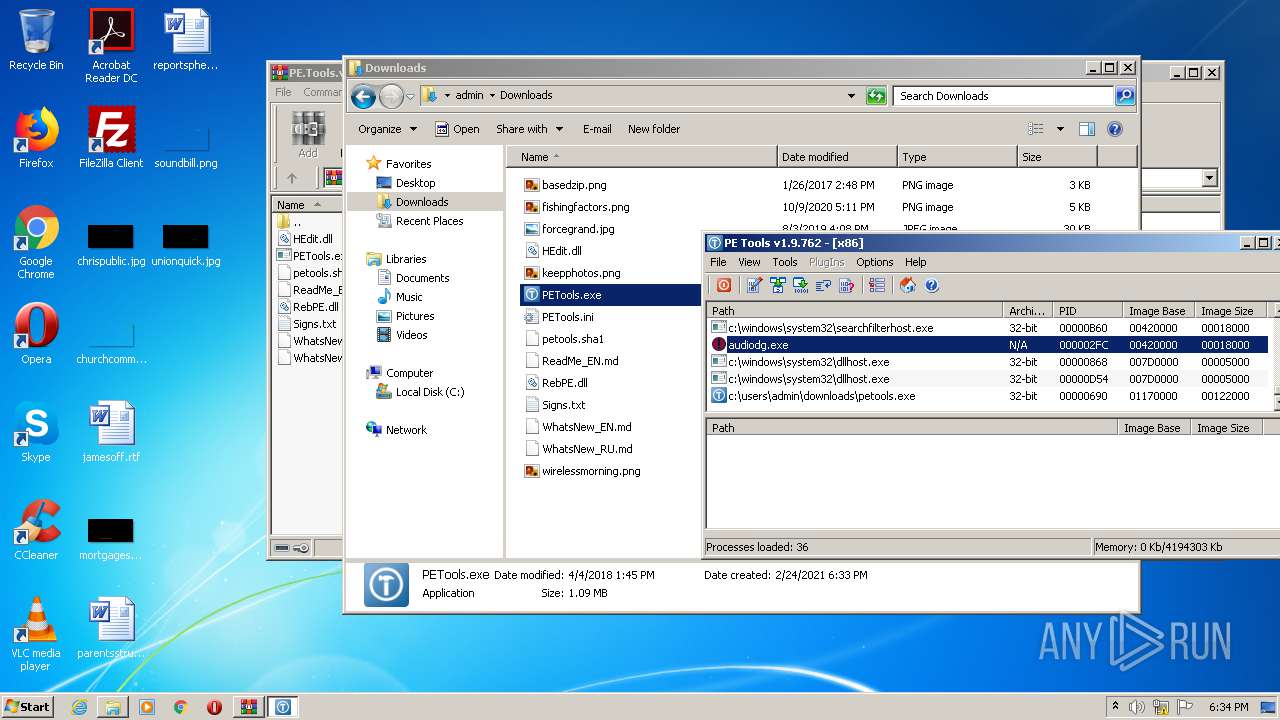
Application was dropped or rewritten from another process
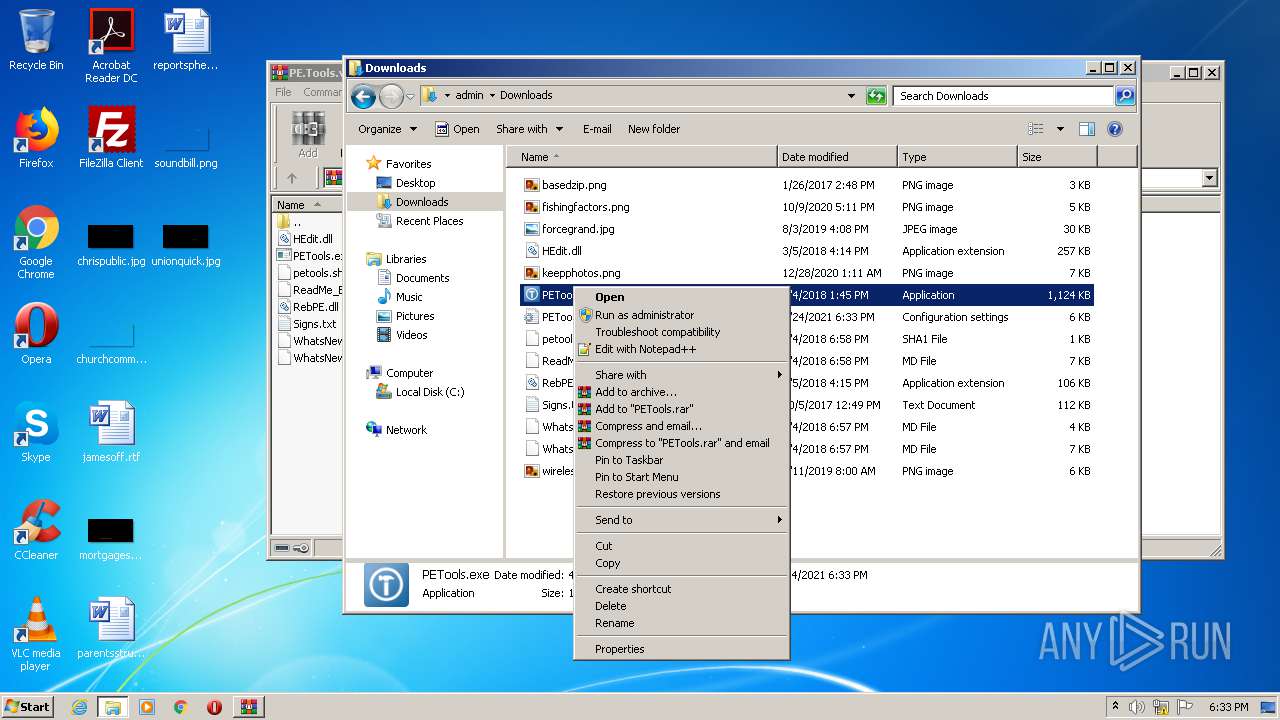
- PETools.exe (PID: 2016)
- PETools.exe (PID: 1680)
- PETools.exe (PID: 3712)
Loads dropped or rewritten executable
- PETools.exe (PID: 2016)
- PETools.exe (PID: 3712)
- SearchProtocolHost.exe (PID: 3932)
- PETools.exe (PID: 1680)
SUSPICIOUS
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3384)
INFO
Manual execution by user
- explorer.exe (PID: 1696)
- PETools.exe (PID: 3712)
- PETools.exe (PID: 1680)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .7z | | | 7-Zip compressed archive (v0.4) (57.1) |
|---|---|---|
| .7z | | | 7-Zip compressed archive (gen) (42.8) |
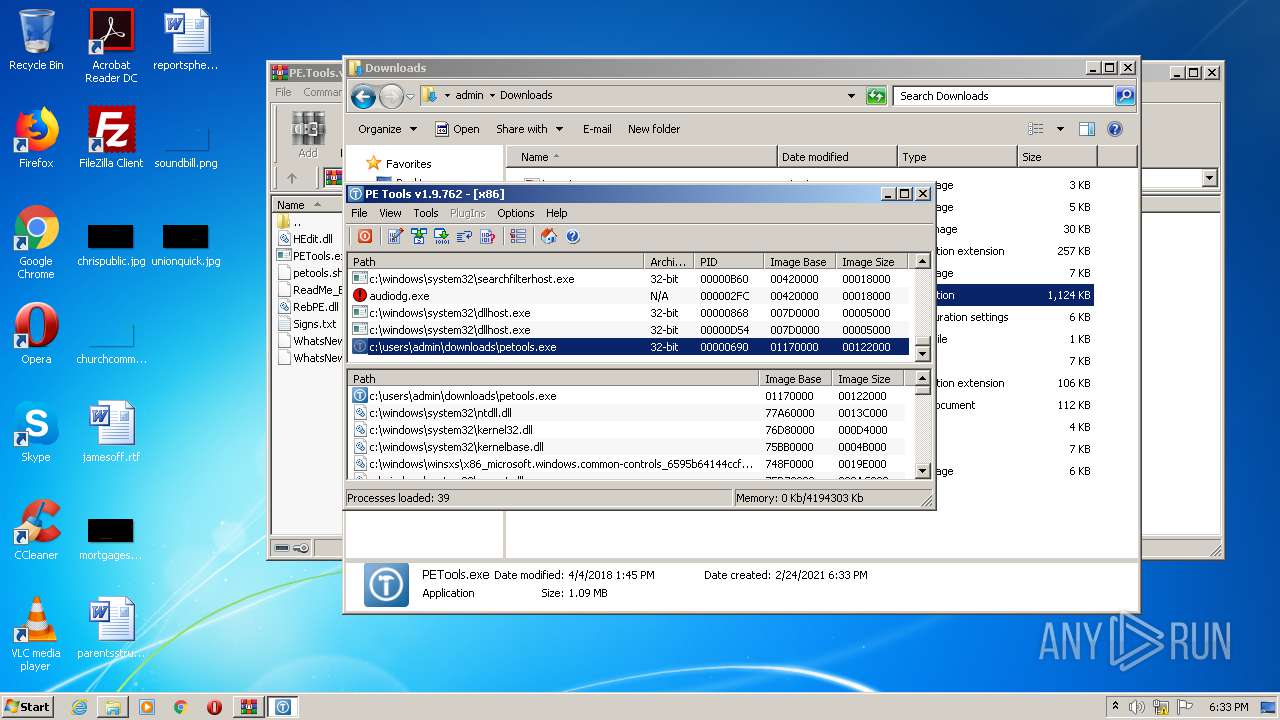
Total processes
50
Monitored processes
6
Malicious processes
3
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
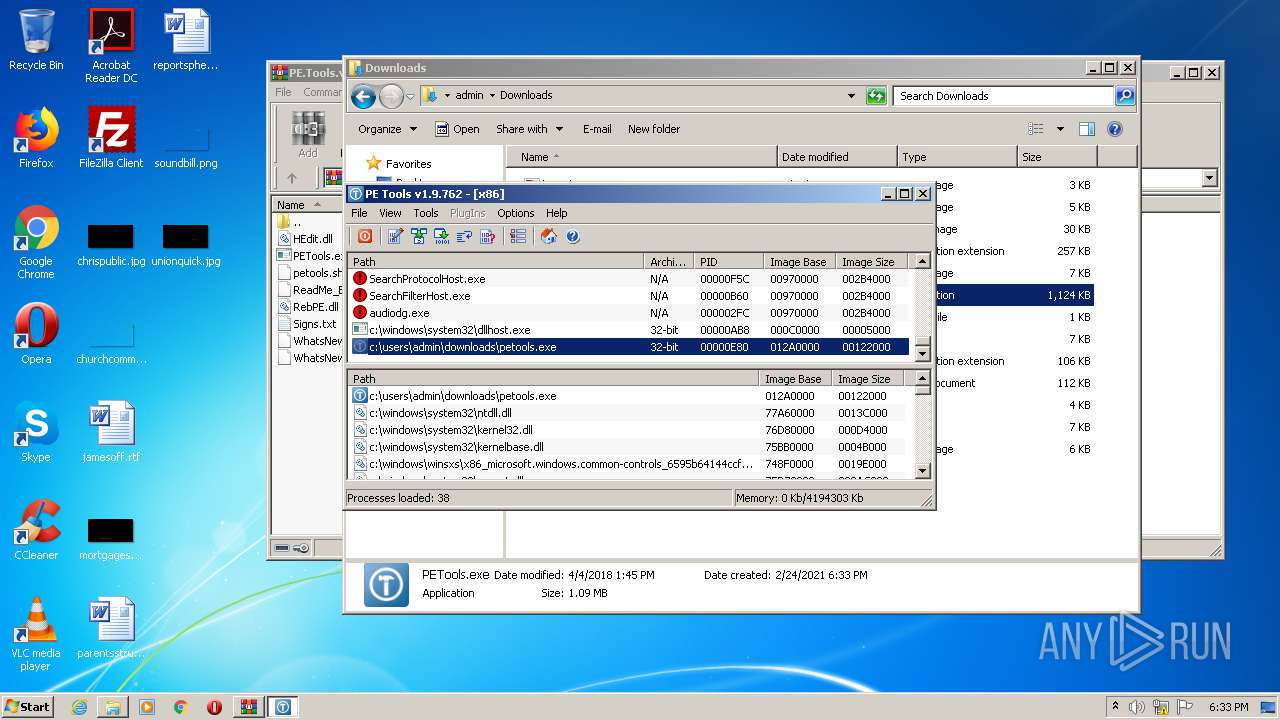
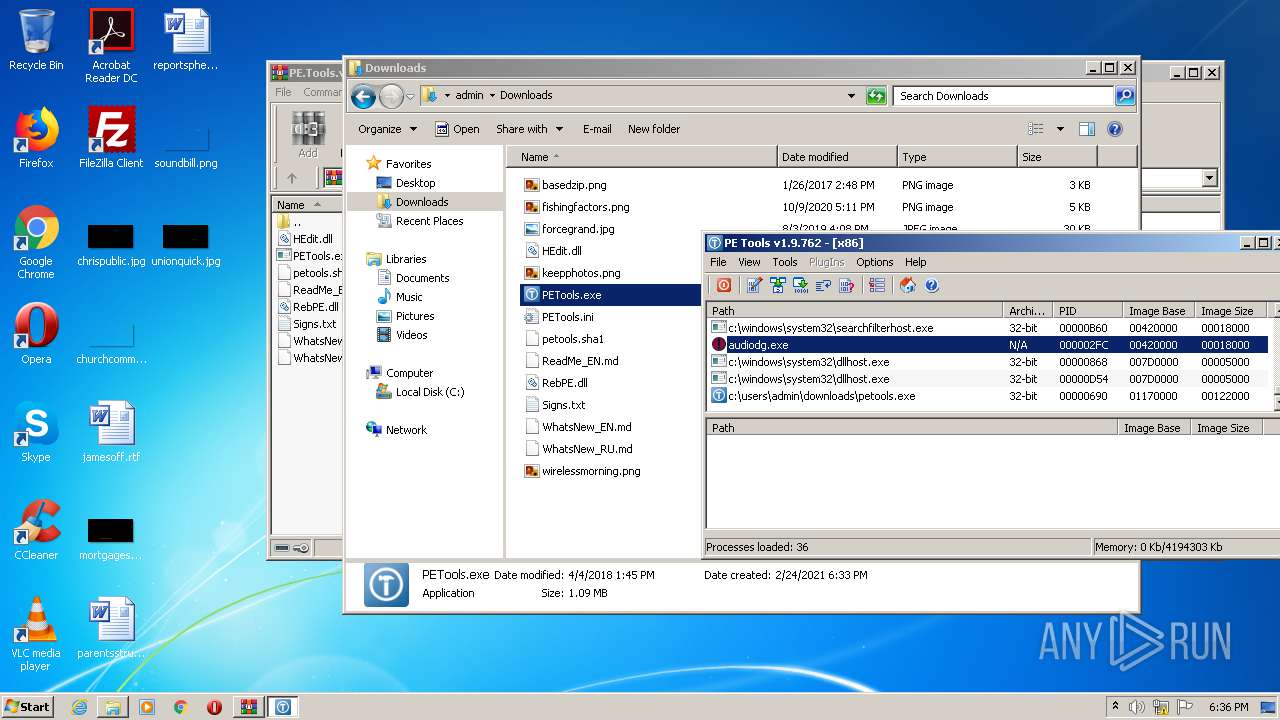
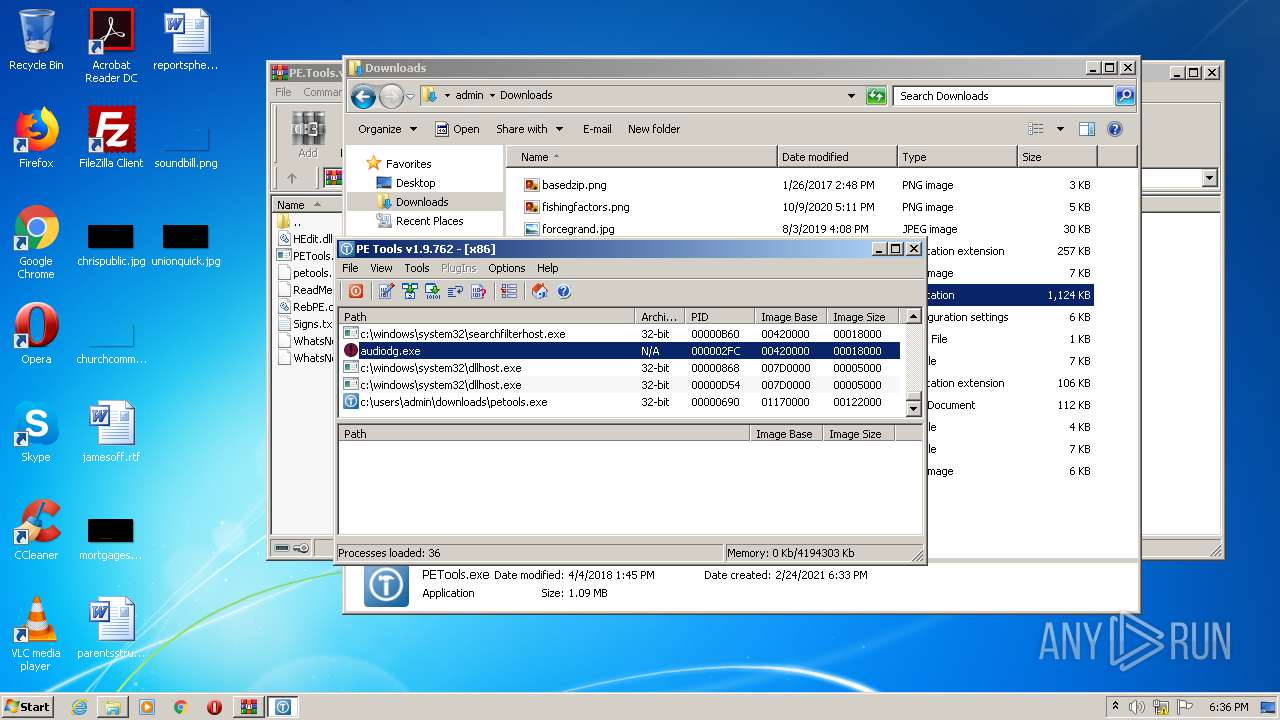
| 1680 | "C:\Users\admin\Downloads\PETools.exe" | C:\Users\admin\Downloads\PETools.exe | explorer.exe | ||||||||||||
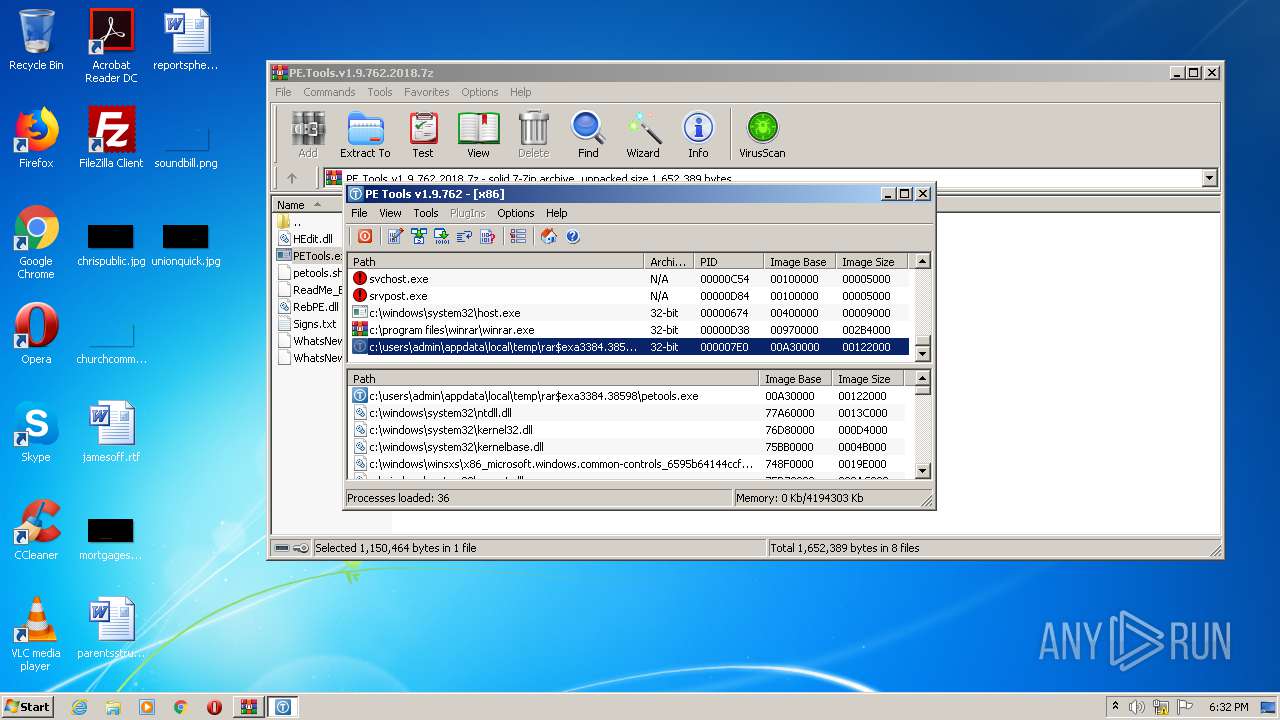
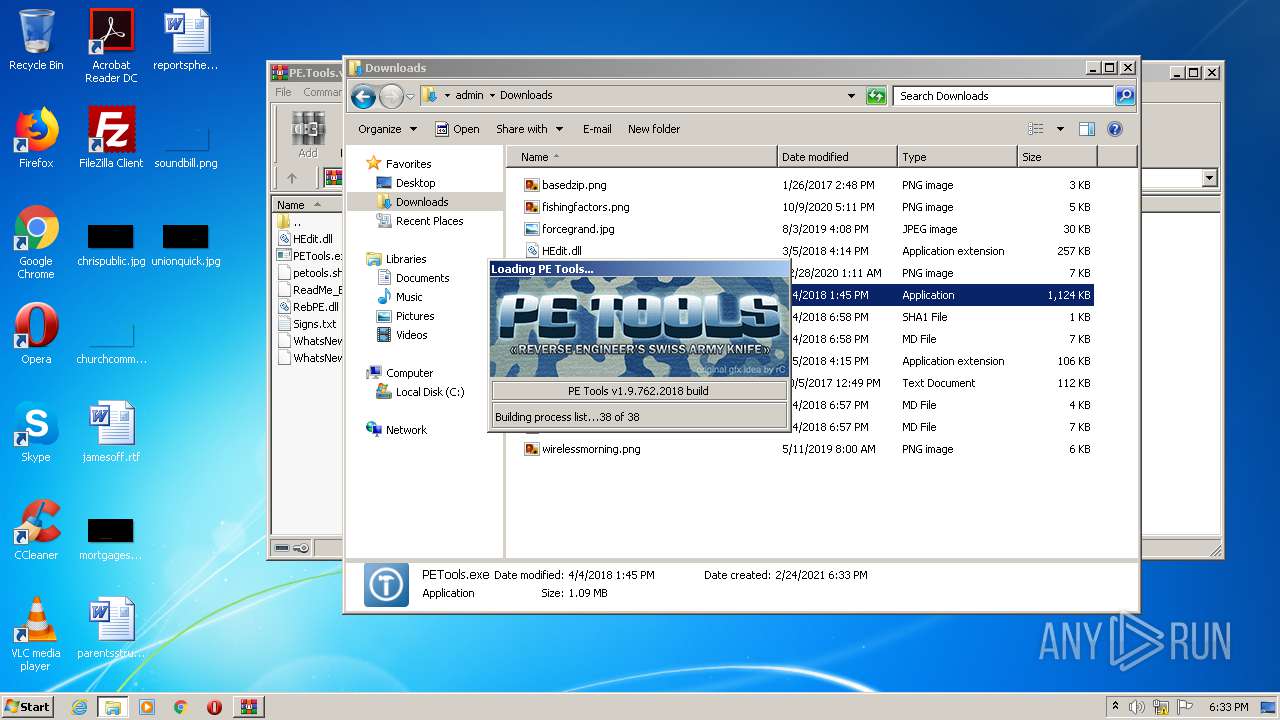
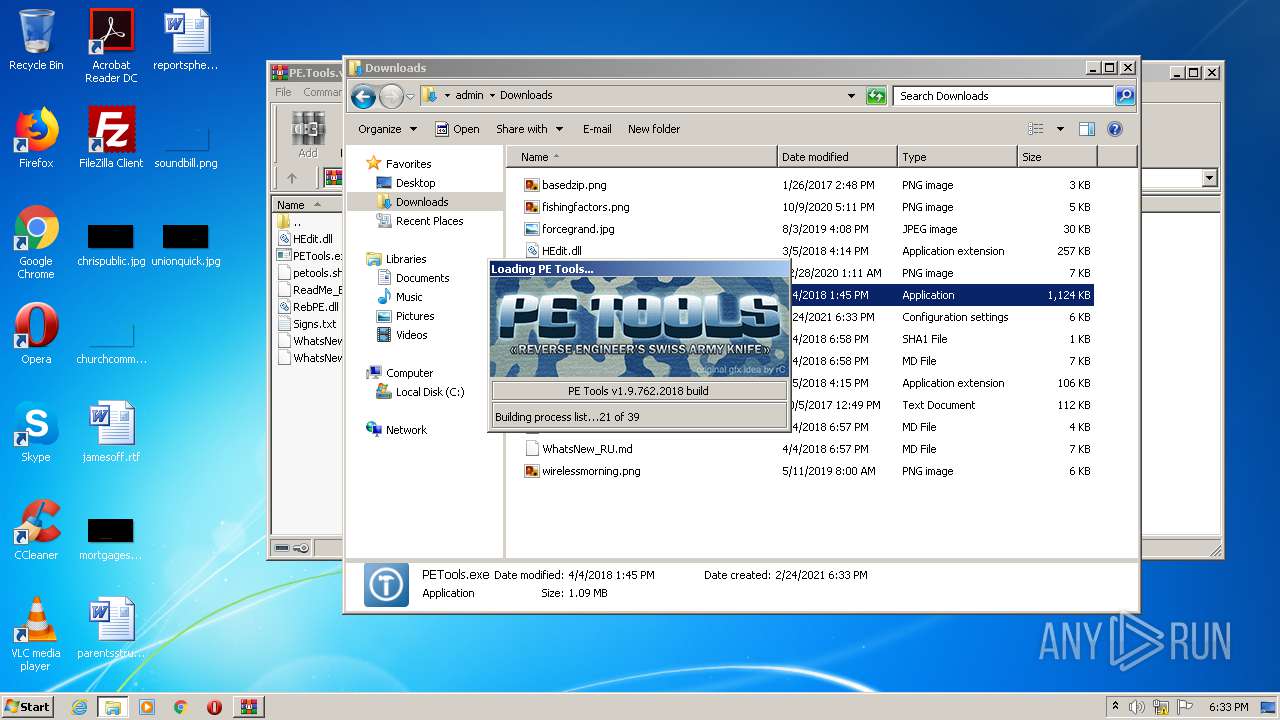
User: admin Company: painter and Jupiter <RnD> Integrity Level: HIGH Description: PE Tools - oldschool reverse engineering tool! Exit code: 0 Version: PE Tools v1.9.762 Modules
| |||||||||||||||
| 1696 | "C:\Windows\explorer.exe" | C:\Windows\explorer.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2016 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa3384.38598\PETools.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa3384.38598\PETools.exe | — | WinRAR.exe | |||||||||||
User: admin Company: painter and Jupiter <RnD> Integrity Level: MEDIUM Description: PE Tools - oldschool reverse engineering tool! Exit code: 0 Version: PE Tools v1.9.762 Modules
| |||||||||||||||
| 3384 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\PE.Tools.v1.9.762.2018.7z" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 3712 | "C:\Users\admin\Downloads\PETools.exe" | C:\Users\admin\Downloads\PETools.exe | — | explorer.exe | |||||||||||
User: admin Company: painter and Jupiter <RnD> Integrity Level: MEDIUM Description: PE Tools - oldschool reverse engineering tool! Exit code: 0 Version: PE Tools v1.9.762 Modules
| |||||||||||||||
| 3932 | "C:\Windows\system32\SearchProtocolHost.exe" Global\UsGthrFltPipeMssGthrPipe3_ Global\UsGthrCtrlFltPipeMssGthrPipe3 1 -2147483646 "Software\Microsoft\Windows Search" "Mozilla/4.0 (compatible; MSIE 6.0; Windows NT; MS Search 4.0 Robot)" "C:\ProgramData\Microsoft\Search\Data\Temp\usgthrsvc" "DownLevelDaemon" | C:\Windows\system32\SearchProtocolHost.exe | — | SearchIndexer.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft Windows Search Protocol Host Exit code: 0 Version: 7.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
1 774
Read events
1 698
Write events
75
Delete events
1
Modification events
| (PID) Process: | (3384) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3384) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3384) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\13D\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3384) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\13D\52C64B7E |
| Operation: | write | Name: | @C:\Windows\system32\NetworkExplorer.dll,-1 |
Value: Network | |||
| (PID) Process: | (3384) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\PE.Tools.v1.9.762.2018.7z | |||
| (PID) Process: | (3384) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3384) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3384) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3384) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3384) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\13D\52C64B7E |
| Operation: | write | Name: | @C:\Windows\system32\notepad.exe,-469 |
Value: Text Document | |||
Executable files
6
Suspicious files
0
Text files
13
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3384 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3384.38598\ReadMe_EN.md | text | |
MD5:3ED0CFD828A52B04852264C73414F65B | SHA256:1CA2B07F9EA393C4566FAEDB1E8A1D3B2FE656FBBB821FD699F84833E725443C | |||
| 3384 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3384.38598\WhatsNew_RU.md | text | |
MD5:B120E55FE671EE19BBA1BEEFCD822157 | SHA256:D71F48F2057BD5E7D85DC211621F883218ECE93B3568C2074549B65ED36E2EFA | |||
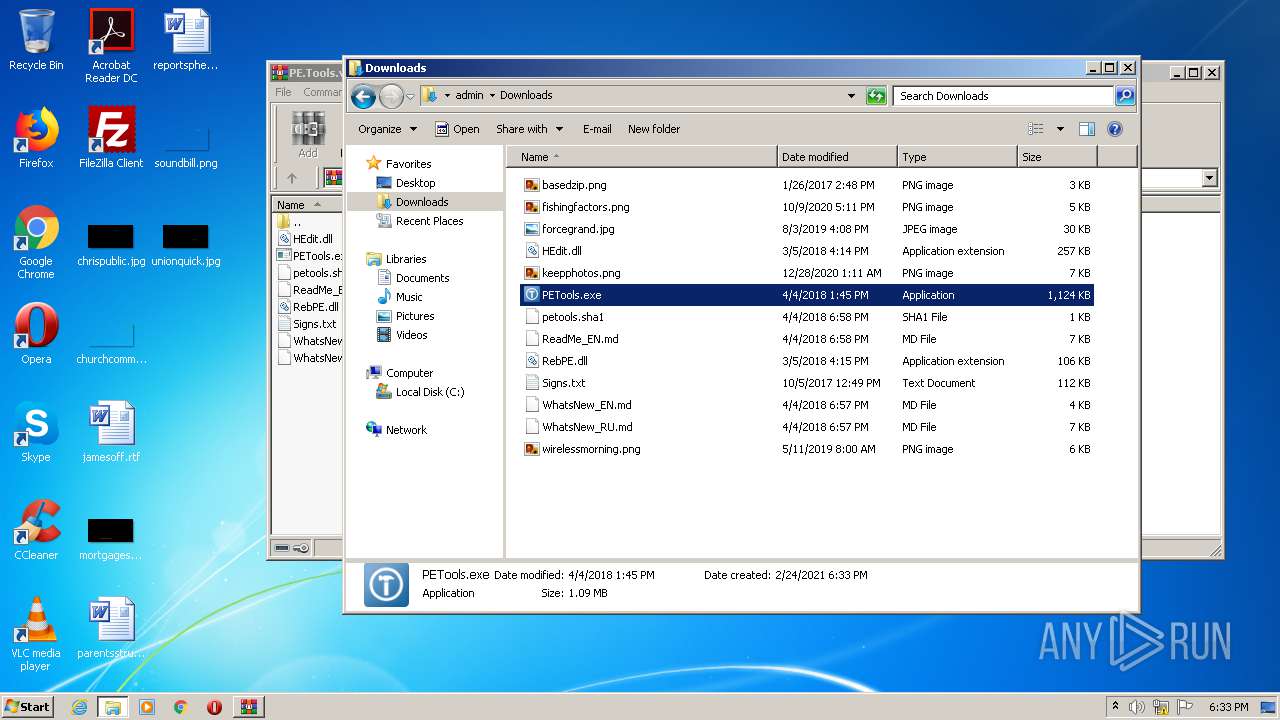
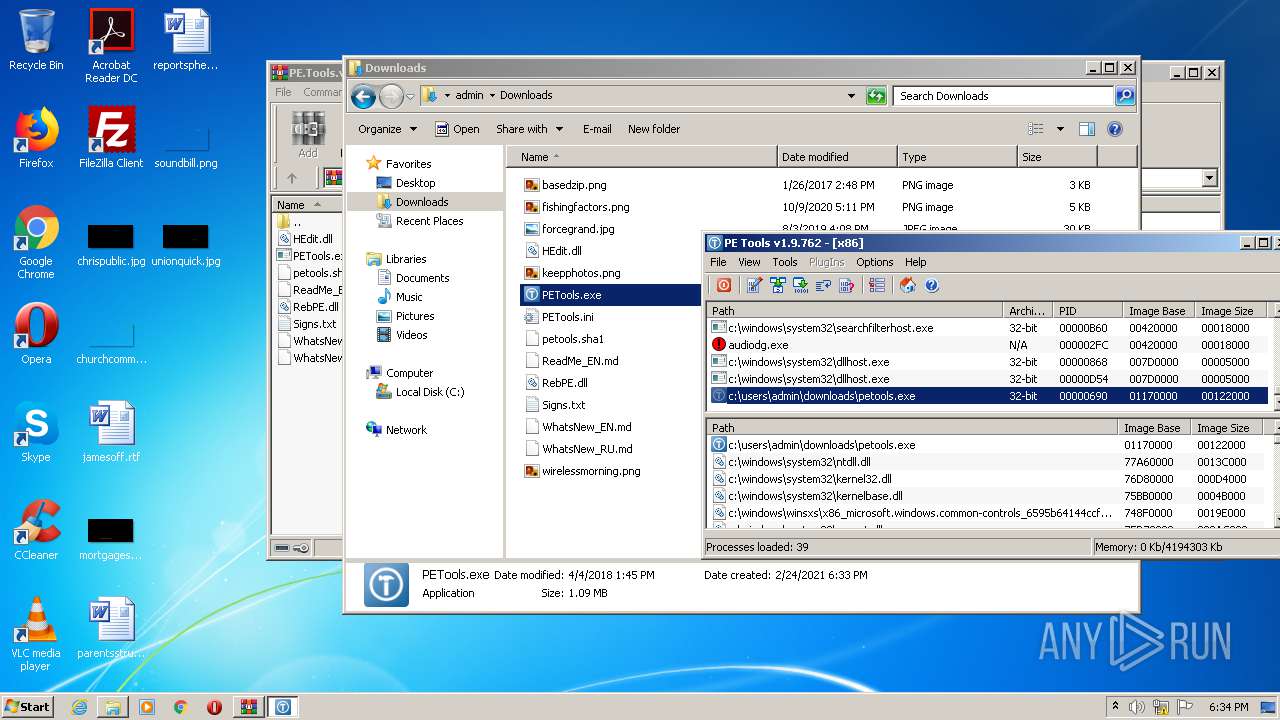
| 1680 | PETools.exe | C:\Users\admin\Downloads\PETools.ini | text | |
MD5:— | SHA256:— | |||
| 3384 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3384.38598\Signs.txt | text | |
MD5:847FAAC4828BFA31E27F7D963012BD25 | SHA256:75BD2C90B98A2641557D61AE02313D4C4D47D35393C3C8CD31EA8F38ED7F85D0 | |||
| 2016 | PETools.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3384.38598\PETools.ini | text | |
MD5:— | SHA256:— | |||
| 3384 | WinRAR.exe | C:\Users\admin\Downloads\WhatsNew_EN.md | text | |
MD5:608A7816F7E76A4B3499FE460480AEA6 | SHA256:D8F08DF8D9837F7BC006D58344A4AD03FFDD4A50E63DE930C8E61337E39FEE83 | |||
| 3384 | WinRAR.exe | C:\Users\admin\Downloads\Signs.txt | text | |
MD5:847FAAC4828BFA31E27F7D963012BD25 | SHA256:75BD2C90B98A2641557D61AE02313D4C4D47D35393C3C8CD31EA8F38ED7F85D0 | |||
| 3384 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3384.38598\petools.sha1 | text | |
MD5:22D647711A0D7E7C76F7EC7FFE150207 | SHA256:5B310D7004B289D16B53FC6E4848C84B53FE5656A16231A662A64BD57E95EEC0 | |||
| 3384 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3384.38598\RebPE.dll | executable | |
MD5:EBBDB1BEF4A8FE9ADF118F5C37ACF936 | SHA256:4AB5A64EB0109794E25AED020135D8A090214C0A1C298D8B44A5F08715706FA1 | |||
| 3384 | WinRAR.exe | C:\Users\admin\Downloads\ReadMe_EN.md | text | |
MD5:3ED0CFD828A52B04852264C73414F65B | SHA256:1CA2B07F9EA393C4566FAEDB1E8A1D3B2FE656FBBB821FD699F84833E725443C | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report