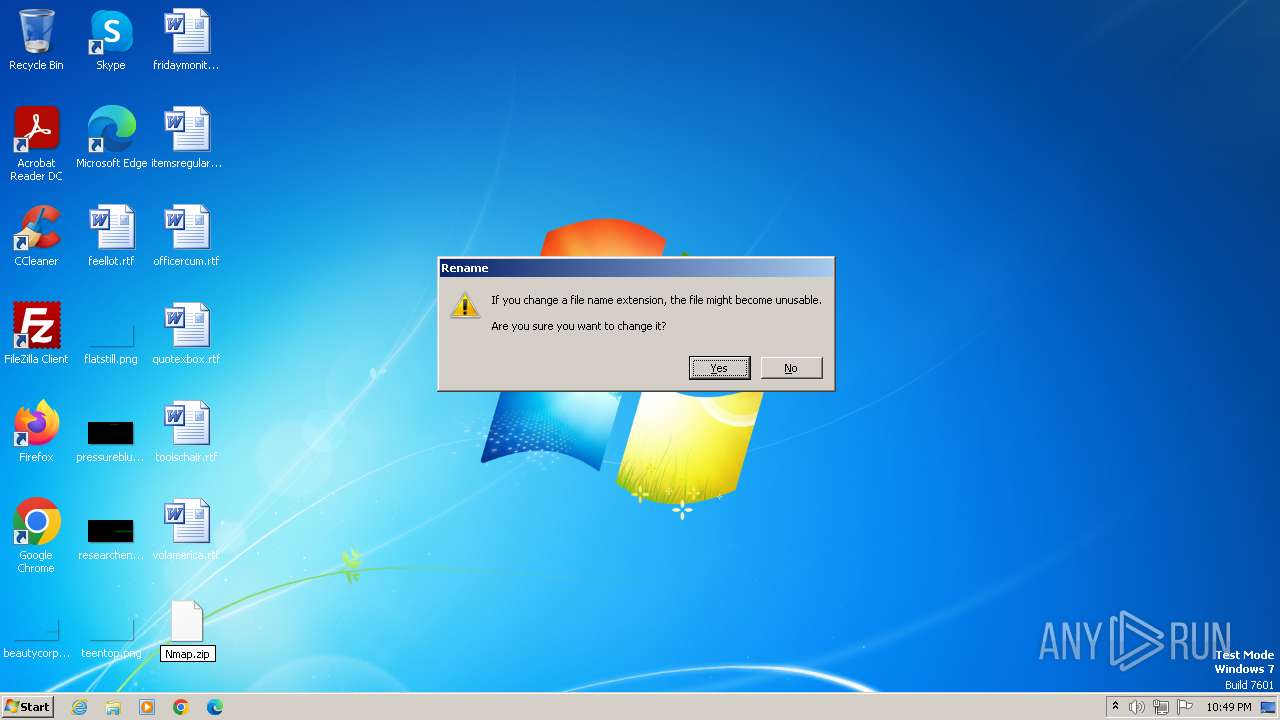
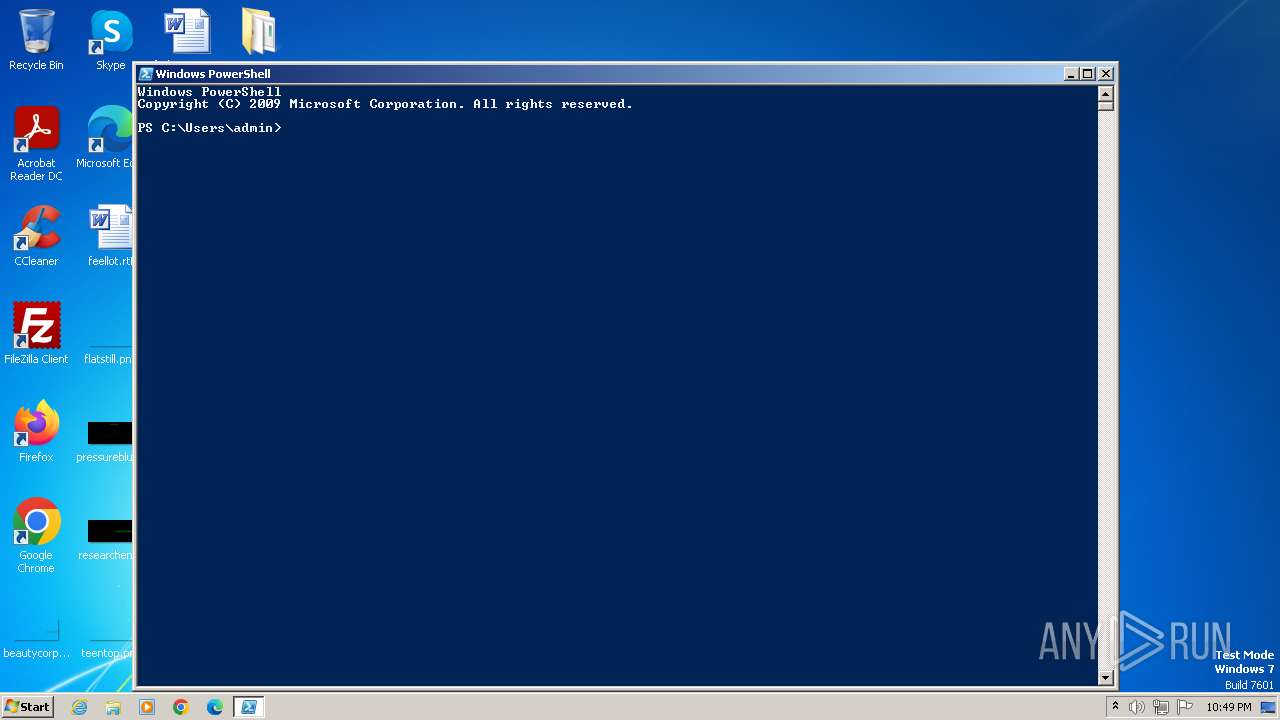
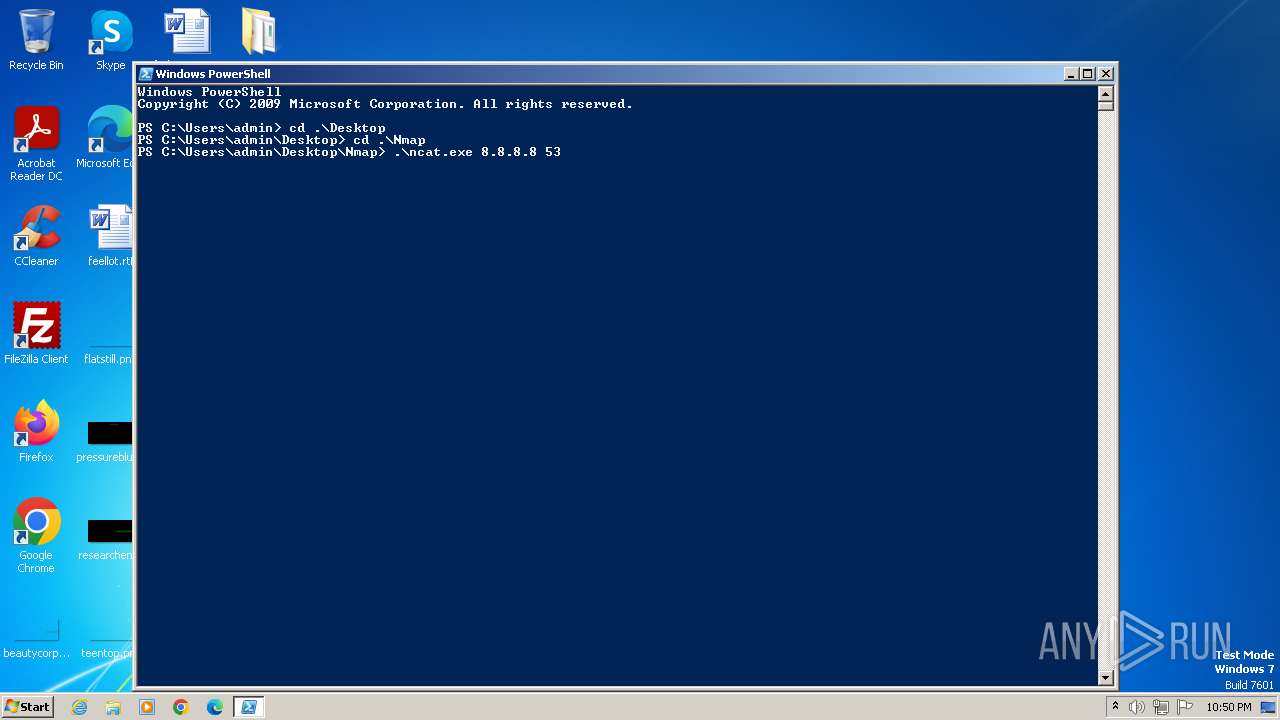
| File name: | Nmap.zip |
| Full analysis: | https://app.any.run/tasks/41420147-8396-4170-9508-5c2373dc497b |
| Verdict: | Malicious activity |
| Analysis date: | October 24, 2023, 21:48:33 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
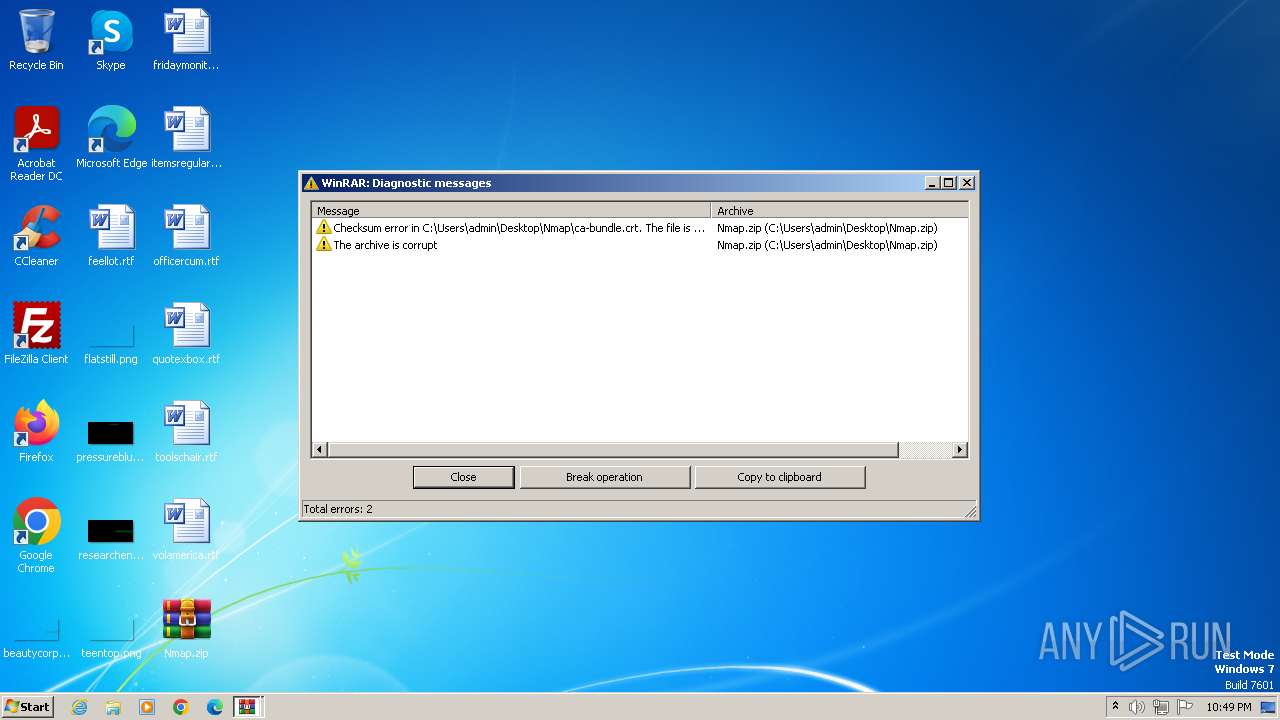
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | 395F5B80315F425D42E55A41C36F6CC0 |
| SHA1: | CB55D75218B160099F8DA5DD1A97F904674BC72D |
| SHA256: | B80F40238A5B9310CFFCC140951F3DBA0153124C79393013796AC7F071634E54 |
| SSDEEP: | 196608:YTpvMsA2YgWCCuE8ukpouLVhLSZMcTJ6blczcBgYfg:OpEd2YXCLBoKhm1QbbFg |
MALICIOUS
Application was dropped or rewritten from another process
- ncat.exe (PID: 2480)
- ncat.exe (PID: 3940)
SUSPICIOUS
The process creates files with name similar to system file names
- WinRAR.exe (PID: 3688)
Powershell version downgrade attack
- powershell.exe (PID: 3836)
Loads Python modules
- SearchProtocolHost.exe (PID: 276)
INFO
Drops the executable file immediately after the start
- WinRAR.exe (PID: 3688)
Manual execution by a user
- WinRAR.exe (PID: 3688)
- cmd.exe (PID: 2300)
- powershell.exe (PID: 3836)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .xpi | | | Mozilla Firefox browser extension (42.1) |
|---|---|---|
| .zip | | | ZIP compressed archive (21) |
EXIF
ZIP
| ZipFileName: | 3rd-party-licenses.txt |
|---|---|
| ZipUncompressedSize: | 56784 |
| ZipCompressedSize: | 14192 |
| ZipCRC: | 0x1c164bf7 |
| ZipModifyDate: | 2023:05:19 21:13:34 |
| ZipCompression: | Deflated |
| ZipBitFlag: | - |
| ZipRequiredVersion: | 20 |
Total processes
47
Monitored processes
7
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 276 | "C:\Windows\system32\SearchProtocolHost.exe" Global\UsGthrFltPipeMssGthrPipe6_ Global\UsGthrCtrlFltPipeMssGthrPipe6 1 -2147483646 "Software\Microsoft\Windows Search" "Mozilla/4.0 (compatible; MSIE 6.0; Windows NT; MS Search 4.0 Robot)" "C:\ProgramData\Microsoft\Search\Data\Temp\usgthrsvc" "DownLevelDaemon" | C:\Windows\System32\SearchProtocolHost.exe | — | SearchIndexer.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft Windows Search Protocol Host Exit code: 0 Version: 7.00.7601.24542 (win7sp1_ldr_escrow.191209-2211) Modules
| |||||||||||||||
| 1824 | "C:\Windows\system32\rundll32.exe" C:\Windows\system32\shell32.dll,OpenAs_RunDLL "C:\Users\admin\Desktop\Nmap.zip.xpi" | C:\Windows\System32\rundll32.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2300 | "C:\Windows\system32\cmd.exe" | C:\Windows\System32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
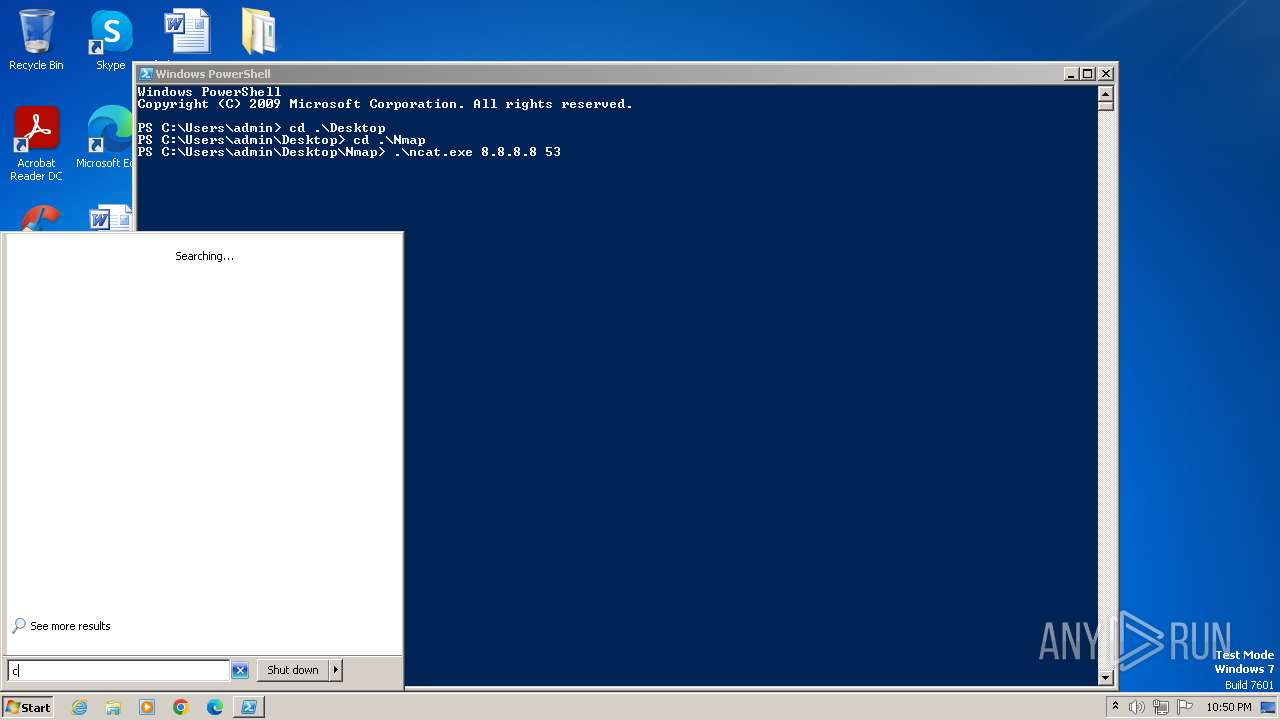
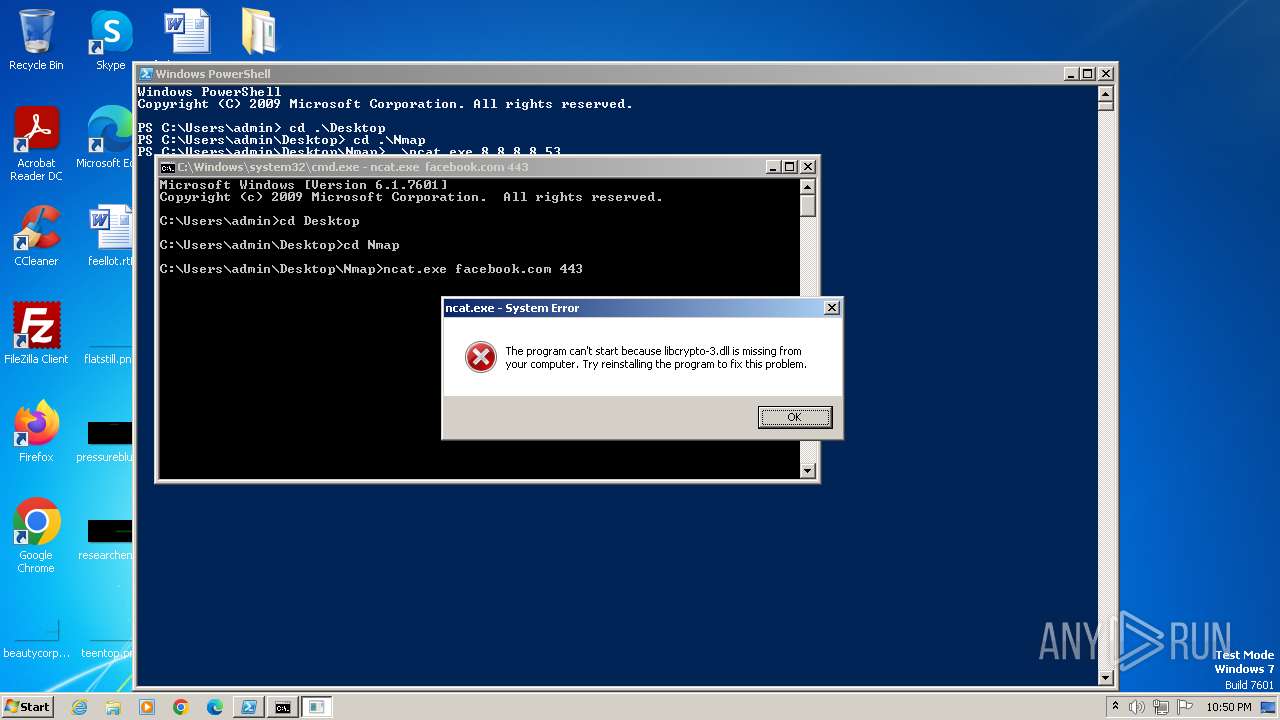
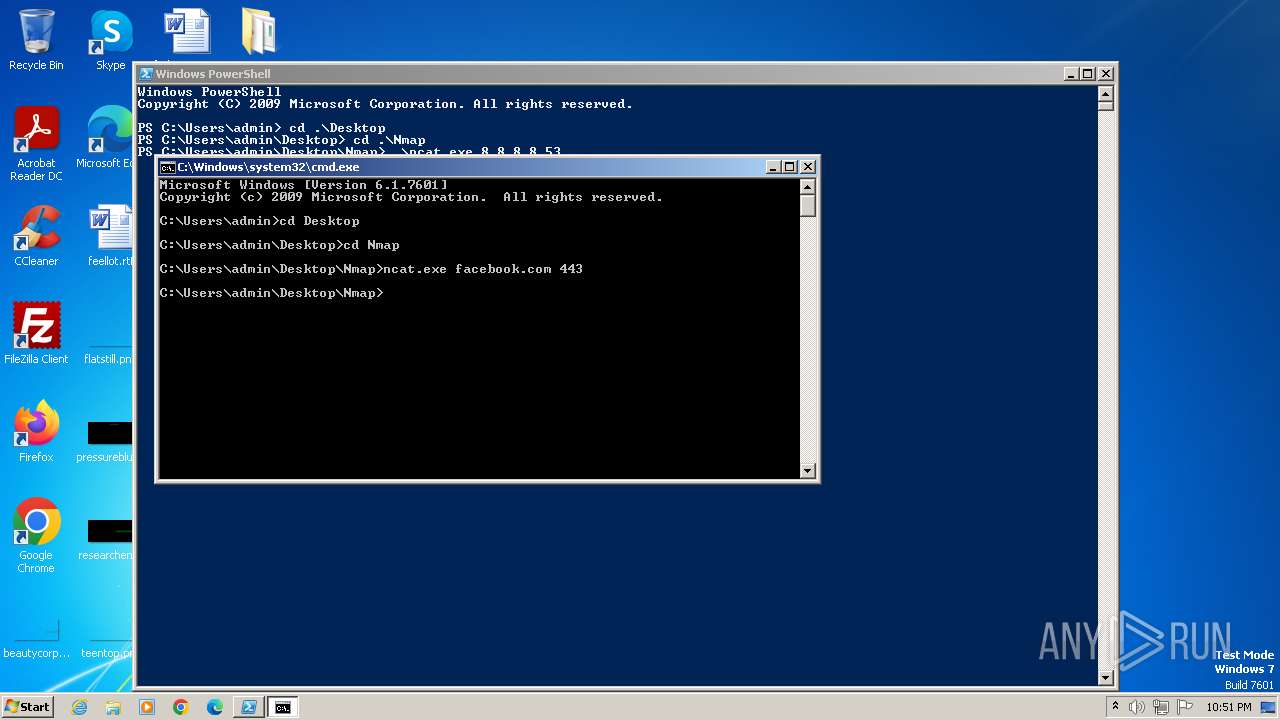
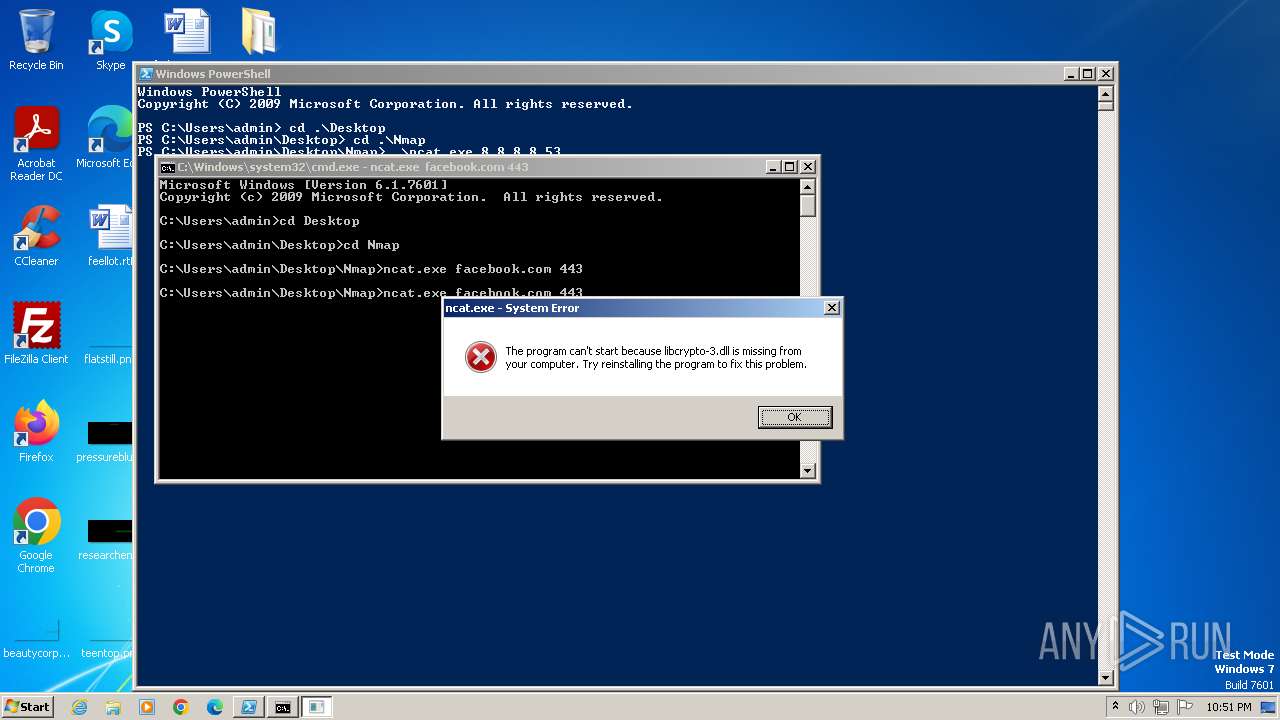
| 2480 | ncat.exe facebook.com 443 | C:\Users\admin\Desktop\Nmap\ncat.exe | — | cmd.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221225781 Modules
| |||||||||||||||
| 3688 | "C:\Program Files\WinRAR\WinRAR.exe" x -iext -ow -ver -- "C:\Users\admin\Desktop\Nmap.zip" "?\" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 3 Version: 5.91.0 Modules
| |||||||||||||||
| 3836 | "C:\WINDOWS\system32\WindowsPowerShell\v1.0\powershell.exe" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3940 | ncat.exe facebook.com 443 | C:\Users\admin\Desktop\Nmap\ncat.exe | — | cmd.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
Total events
1 766
Read events
1 704
Write events
62
Delete events
0
Modification events
| (PID) Process: | (3688) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\178\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (276) SearchProtocolHost.exe | Key: | HKEY_USERS\.DEFAULT\Software\Classes\Local Settings\MuiCache\178\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3688) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3688) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3688) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3688) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3836) powershell.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\178\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
Executable files
10
Suspicious files
4
Text files
623
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3688 | WinRAR.exe | C:\Users\admin\Desktop\Nmap\nmap-os-db | — | |
MD5:— | SHA256:— | |||
| 3688 | WinRAR.exe | C:\Users\admin\Desktop\Nmap\libssl-3.dll | executable | |
MD5:2D8E9C95D4CC267545EB3CBBACC9B75A | SHA256:2E0225D6C9FF673A269C045298DA1B3E0D938363B1F6F081F147B5BB7524CF59 | |||
| 3688 | WinRAR.exe | C:\Users\admin\Desktop\Nmap\NDIFF_README | text | |
MD5:A0CC54A07CAD1437FCEF49450F5A3C4F | SHA256:9EFF628277B55521BDD08D793740A4AA11776C66023957F262D5FE074DFE77BD | |||
| 3688 | WinRAR.exe | C:\Users\admin\Desktop\Nmap\ndiff.bat | text | |
MD5:70B99BC88A99F1EE8211380B485B051F | SHA256:AFB370AB44802EDA5A317A9042F66AF72EF522E0C70A2132565335F50F0ACE7F | |||
| 3688 | WinRAR.exe | C:\Users\admin\Desktop\Nmap\ndiff.py | text | |
MD5:982340036667C7073392FC5CBAE01029 | SHA256:88F7EC04DFD35525379E635617929F13D5C938E7E773F9E018C3AEBFDB0C10A6 | |||
| 3688 | WinRAR.exe | C:\Users\admin\Desktop\Nmap\ca-bundle.crt | text | |
MD5:04EF759DFE8AECE732DEC61EF1EE389E | SHA256:6B52A20F1702977C90617A1A186D209AD363137DA00F630D978B597F85C17490 | |||
| 3688 | WinRAR.exe | C:\Users\admin\Desktop\Nmap\LICENSE | text | |
MD5:895AF8527FE4BCB72F271FD1841FD2F6 | SHA256:9D9A9A763C0E6145172CFE7D8483E23B38CE60B6C79A82E4894242917BDAE6D3 | |||
| 3688 | WinRAR.exe | C:\Users\admin\Desktop\Nmap\libssh2.dll | executable | |
MD5:ACD39913BDE7D7A0D593781CC1268235 | SHA256:D6A56CE17BF87DE8559413A773F0863FAB19AF14E35E911FF0B362DB02529ED4 | |||
| 3688 | WinRAR.exe | C:\Users\admin\Desktop\Nmap\nmap-rpc | text | |
MD5:D6DF2606C915CB158559AF45BD05995C | SHA256:D8B7619AC646F65766A6BEEAB7D6D98D54880C84982A1E6AAA38E6311CFCB254 | |||
| 3688 | WinRAR.exe | C:\Users\admin\Desktop\Nmap\nmap_performance.reg | text | |
MD5:3CD4A36A0DCC9E0E79D1DF1D6CC712DF | SHA256:E77D7B5158EC99D19E552025FACF50F477A2F2B1DC3EF2F198520CFA76E9707F | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
2
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |