| File name: | hwi_766.exe |
| Full analysis: | https://app.any.run/tasks/e072f1ce-9665-42ee-80b6-03124b0dca9e |
| Verdict: | Malicious activity |
| Analysis date: | July 09, 2024, 07:08:29 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 2CE1AEE9CFA0B85833CF6BC50C294D74 |
| SHA1: | 804E4F905A84E24A657853A2D522C5EBD06E980A |
| SHA256: | B80E121E032E1BF6F4974048C4A8B7842E70518AB394E272F21175420AF7C1BC |
| SSDEEP: | 98304:WDls87PLgJr9dwvsYQVrF9LM3Zf2csHXAynmZ+1mEBsPlBl5Jktw5oU2ncivmR1h:yzoF/9o86MKzaY |
MALICIOUS
Drops the executable file immediately after the start
- hwi_766.exe (PID: 3392)
- hwi_766.exe (PID: 2108)
- hwi_766.tmp (PID: 2300)
- HWiNFO32.EXE (PID: 2980)
SUSPICIOUS
Executable content was dropped or overwritten
- hwi_766.exe (PID: 3392)
- hwi_766.exe (PID: 2108)
- hwi_766.tmp (PID: 2300)
- HWiNFO32.EXE (PID: 2980)
Reads the Windows owner or organization settings
- hwi_766.tmp (PID: 2300)
Reads security settings of Internet Explorer
- hwi_766.tmp (PID: 3424)
- HWiNFO32.EXE (PID: 2980)
Reads the Internet Settings
- hwi_766.tmp (PID: 3424)
- HWiNFO32.EXE (PID: 2980)
Drops a system driver (possible attempt to evade defenses)
- HWiNFO32.EXE (PID: 2980)
Checks Windows Trust Settings
- HWiNFO32.EXE (PID: 2980)
Adds/modifies Windows certificates
- HWiNFO32.EXE (PID: 2980)
There is functionality for VM detection (antiVM strings)
- HWiNFO32.EXE (PID: 2980)
Reads the BIOS version
- HWiNFO32.EXE (PID: 2980)
Reads settings of System Certificates
- HWiNFO32.EXE (PID: 2980)
INFO
Checks supported languages
- hwi_766.exe (PID: 3392)
- hwi_766.tmp (PID: 3424)
- hwi_766.exe (PID: 2108)
- hwi_766.tmp (PID: 2300)
- HWiNFO32.EXE (PID: 2980)
Create files in a temporary directory
- hwi_766.exe (PID: 3392)
- hwi_766.exe (PID: 2108)
- HWiNFO32.EXE (PID: 2980)
Reads the computer name
- hwi_766.tmp (PID: 3424)
- hwi_766.tmp (PID: 2300)
- HWiNFO32.EXE (PID: 2980)
Creates files in the program directory
- hwi_766.tmp (PID: 2300)
- HWiNFO32.EXE (PID: 2980)
Creates a software uninstall entry
- hwi_766.tmp (PID: 2300)
Reads the machine GUID from the registry
- HWiNFO32.EXE (PID: 2980)
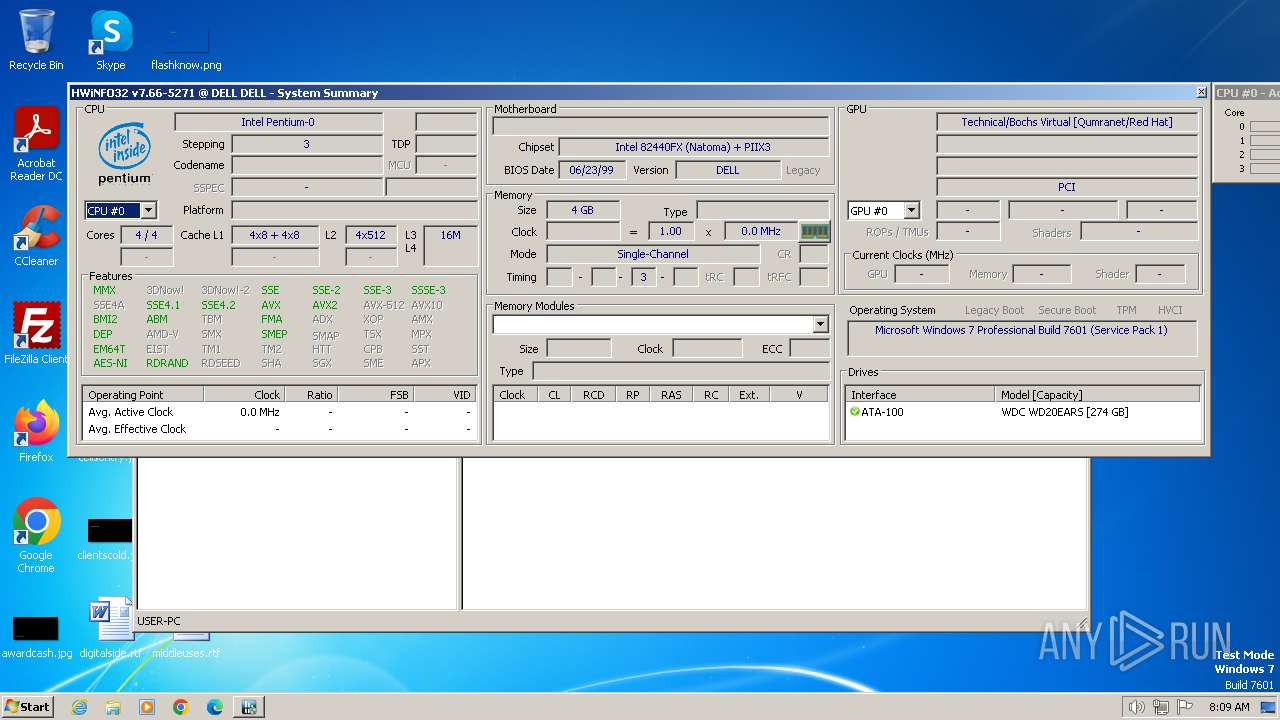
Reads CPU info
- HWiNFO32.EXE (PID: 2980)
Checks proxy server information
- HWiNFO32.EXE (PID: 2980)
UPX packer has been detected
- HWiNFO32.EXE (PID: 2980)
Creates files or folders in the user directory
- HWiNFO32.EXE (PID: 2980)
Reads the software policy settings
- HWiNFO32.EXE (PID: 2980)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Inno Setup installer (67.9) |
|---|---|---|
| .exe | | | UPX compressed Win32 Executable (16.7) |
| .exe | | | Win32 Executable Delphi generic (8.7) |
| .exe | | | Win32 Executable (generic) (2.7) |
| .exe | | | Win16/32 Executable Delphi generic (1.2) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 1992:06:19 22:22:17+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, Bytes reversed lo, 32-bit, Bytes reversed hi |
| PEType: | PE32 |
| LinkerVersion: | 2.25 |
| CodeSize: | 41984 |
| InitializedDataSize: | 84992 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xaad0 |
| OSVersion: | 1 |
| ImageVersion: | 6 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 7.66.0.0 |
| ProductVersionNumber: | 7.66.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | This installation was built with Inno Setup. |
| CompanyName: | Martin Malik, REALiX s.r.o. |
| FileDescription: | HWiNFO32/64 Installer |
| FileVersion: | 7.66 |
| LegalCopyright: | © 2019-2023 Martin Malik, REALiX s.r.o. |
| ProductName: | HWiNFO |
| ProductVersion: | 7.66 |
Total processes
49
Monitored processes
6
Malicious processes
5
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2108 | "C:\Users\admin\AppData\Local\Temp\hwi_766.exe" /SPAWNWND=$90144 /NOTIFYWND=$6015A | C:\Users\admin\AppData\Local\Temp\hwi_766.exe | hwi_766.tmp | ||||||||||||
User: admin Company: Martin Malik, REALiX s.r.o. Integrity Level: HIGH Description: HWiNFO32/64 Installer Exit code: 0 Version: 7.66 Modules
| |||||||||||||||
| 2300 | "C:\Users\admin\AppData\Local\Temp\is-I2JHP.tmp\hwi_766.tmp" /SL5="$E0168,11550023,128000,C:\Users\admin\AppData\Local\Temp\hwi_766.exe" /SPAWNWND=$90144 /NOTIFYWND=$6015A | C:\Users\admin\AppData\Local\Temp\is-I2JHP.tmp\hwi_766.tmp | hwi_766.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Setup/Uninstall Exit code: 0 Version: 51.52.0.0 Modules
| |||||||||||||||
| 2900 | "C:\Program Files\HWiNFO32\HWiNFO32.EXE" | C:\Program Files\HWiNFO32\HWiNFO32.EXE | — | hwi_766.tmp | |||||||||||
User: admin Company: REALiX s.r.o. Integrity Level: MEDIUM Description: HWiNFO32 Exit code: 3221226540 Version: 7.66-5271 Modules
| |||||||||||||||
| 2980 | "C:\Program Files\HWiNFO32\HWiNFO32.EXE" | C:\Program Files\HWiNFO32\HWiNFO32.EXE | hwi_766.tmp | ||||||||||||
User: admin Company: REALiX s.r.o. Integrity Level: HIGH Description: HWiNFO32 Version: 7.66-5271 Modules
| |||||||||||||||
| 3392 | "C:\Users\admin\AppData\Local\Temp\hwi_766.exe" | C:\Users\admin\AppData\Local\Temp\hwi_766.exe | explorer.exe | ||||||||||||
User: admin Company: Martin Malik, REALiX s.r.o. Integrity Level: MEDIUM Description: HWiNFO32/64 Installer Exit code: 0 Version: 7.66 Modules
| |||||||||||||||
| 3424 | "C:\Users\admin\AppData\Local\Temp\is-6B3UH.tmp\hwi_766.tmp" /SL5="$6015A,11550023,128000,C:\Users\admin\AppData\Local\Temp\hwi_766.exe" | C:\Users\admin\AppData\Local\Temp\is-6B3UH.tmp\hwi_766.tmp | — | hwi_766.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Setup/Uninstall Exit code: 0 Version: 51.52.0.0 Modules
| |||||||||||||||
Total events
9 072
Read events
8 962
Write events
90
Delete events
20
Modification events
| (PID) Process: | (2300) hwi_766.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | Owner |
Value: FC0800000481FED6CED1DA01 | |||
| (PID) Process: | (2300) hwi_766.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | SessionHash |
Value: 7098E9B5452295CD0F3C63B49EAAF377620FE81DE4C9A1CACDF787C9E002E1DC | |||
| (PID) Process: | (2300) hwi_766.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | Sequence |
Value: 1 | |||
| (PID) Process: | (2300) hwi_766.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | RegFiles0000 |
Value: C:\Program Files\HWiNFO32\HWiNFO32.EXE | |||
| (PID) Process: | (2300) hwi_766.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | RegFilesHash |
Value: 83413990FD0ED4756F952E725903C19B5A014547BB5903D888B81976D06131A2 | |||
| (PID) Process: | (2300) hwi_766.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\HWiNFO32_is1 |
| Operation: | write | Name: | Inno Setup: Setup Version |
Value: 5.6.1 (a) | |||
| (PID) Process: | (2300) hwi_766.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\HWiNFO32_is1 |
| Operation: | write | Name: | Inno Setup: App Path |
Value: C:\Program Files\HWiNFO32 | |||
| (PID) Process: | (2300) hwi_766.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\HWiNFO32_is1 |
| Operation: | write | Name: | InstallLocation |
Value: C:\Program Files\HWiNFO32\ | |||
| (PID) Process: | (2300) hwi_766.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\HWiNFO32_is1 |
| Operation: | write | Name: | Inno Setup: Icon Group |
Value: HWiNFO32 | |||
| (PID) Process: | (2300) hwi_766.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\HWiNFO32_is1 |
| Operation: | write | Name: | Inno Setup: User |
Value: admin | |||
Executable files
8
Suspicious files
7
Text files
1
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2108 | hwi_766.exe | C:\Users\admin\AppData\Local\Temp\is-I2JHP.tmp\hwi_766.tmp | executable | |
MD5:18265865058CB20E1EE0276F03A2B041 | SHA256:848B5F617FBD31674C710661B2E13A5C55A9DF06F25BF2D454ABB062687F7A9E | |||
| 2300 | hwi_766.tmp | C:\Program Files\HWiNFO32\unins000.exe | executable | |
MD5:18265865058CB20E1EE0276F03A2B041 | SHA256:848B5F617FBD31674C710661B2E13A5C55A9DF06F25BF2D454ABB062687F7A9E | |||
| 2300 | hwi_766.tmp | C:\ProgramData\Microsoft\Windows\Start Menu\Programs\HWiNFO32\HWiNFO32.lnk | binary | |
MD5:6ADA5348EB772E7AFB121FEFC266B4F0 | SHA256:2B27BD299EF8CE77FC1EEF6561AA1F56A506677FEDDFDE19508E80E5806B59F5 | |||
| 2300 | hwi_766.tmp | C:\Program Files\HWiNFO32\unins000.msg | binary | |
MD5:2019EFB38EB66ED6ECA1747CE0E0A7DC | SHA256:D816931A62CB3BC09FF5D8326D33DBE7C6129C3E804321DFD6C57F5BA93FB715 | |||
| 2300 | hwi_766.tmp | C:\Program Files\HWiNFO32\HWiNFO32.EXE | executable | |
MD5:8FD5F5FE08C1E980DBDD73D89B9FC17A | SHA256:0590ACC1EAEE911FB49AA22CB3FBA1FEE56A35188D23597B142F8E634F61F950 | |||
| 2300 | hwi_766.tmp | C:\Program Files\HWiNFO32\is-534HD.tmp | executable | |
MD5:8FD5F5FE08C1E980DBDD73D89B9FC17A | SHA256:0590ACC1EAEE911FB49AA22CB3FBA1FEE56A35188D23597B142F8E634F61F950 | |||
| 2980 | HWiNFO32.EXE | C:\Users\admin\AppData\Local\Temp\HWiNFO32_190.SYS | executable | |
MD5:468DCE999FE03F0C18E90E83A5EC83A2 | SHA256:57E2159EBA86A6C4C583152CE8520F3C59AB7D301E044598983F1F5A8C0D6037 | |||
| 3392 | hwi_766.exe | C:\Users\admin\AppData\Local\Temp\is-6B3UH.tmp\hwi_766.tmp | executable | |
MD5:18265865058CB20E1EE0276F03A2B041 | SHA256:848B5F617FBD31674C710661B2E13A5C55A9DF06F25BF2D454ABB062687F7A9E | |||
| 2980 | HWiNFO32.EXE | C:\Program Files\HWiNFO32\HWiNFO32.INI | text | |
MD5:31EA0D720B02F5BE9A0A8C843FA525B6 | SHA256:2B52116A161DB87EAD7FBA5329E113610A39EC5183D713A9D9A7222FE657C949 | |||
| 2980 | HWiNFO32.EXE | C:\Windows\INF\setupapi.app.log | text | |
MD5:46423359C30D2DBAE90674F58B178F77 | SHA256:9C791245A0D97E7D822763C0B28A4685C46984808ED45CDF7D190ED8F844B71B | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
10
DNS requests
7
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1372 | svchost.exe | GET | 304 | 199.232.210.172:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?33775f6043c93e33 | unknown | — | — | unknown |
1372 | svchost.exe | GET | 200 | 23.48.23.143:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | unknown |
1372 | svchost.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | unknown |
1060 | svchost.exe | GET | 304 | 199.232.210.172:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?5445ebff82c5850f | unknown | — | — | unknown |
2980 | HWiNFO32.EXE | GET | 200 | 142.250.186.35:80 | http://c.pki.goog/r/gsr1.crl | unknown | — | — | unknown |
2980 | HWiNFO32.EXE | GET | 200 | 142.250.186.35:80 | http://c.pki.goog/r/r4.crl | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1372 | svchost.exe | 51.104.136.2:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1372 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1372 | svchost.exe | 199.232.210.172:80 | ctldl.windowsupdate.com | FASTLY | US | unknown |
1372 | svchost.exe | 23.48.23.143:80 | crl.microsoft.com | Akamai International B.V. | DE | unknown |
1372 | svchost.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | unknown |
2980 | HWiNFO32.EXE | 172.67.205.235:443 | www.hwinfo.com | CLOUDFLARENET | US | unknown |
2980 | HWiNFO32.EXE | 142.250.186.35:80 | c.pki.goog | GOOGLE | US | whitelisted |
1060 | svchost.exe | 199.232.210.172:80 | ctldl.windowsupdate.com | FASTLY | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
dns.msftncsi.com |
| shared |
settings-win.data.microsoft.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
www.hwinfo.com |
| whitelisted |
c.pki.goog |
| unknown |