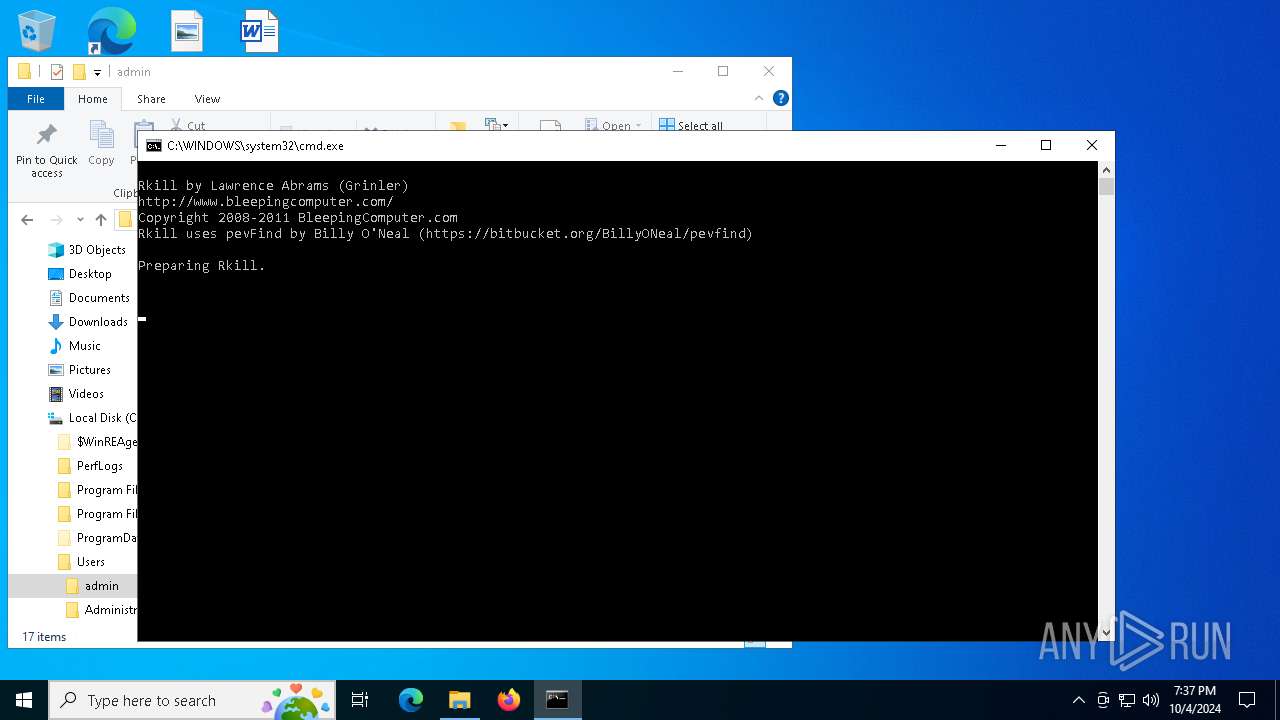
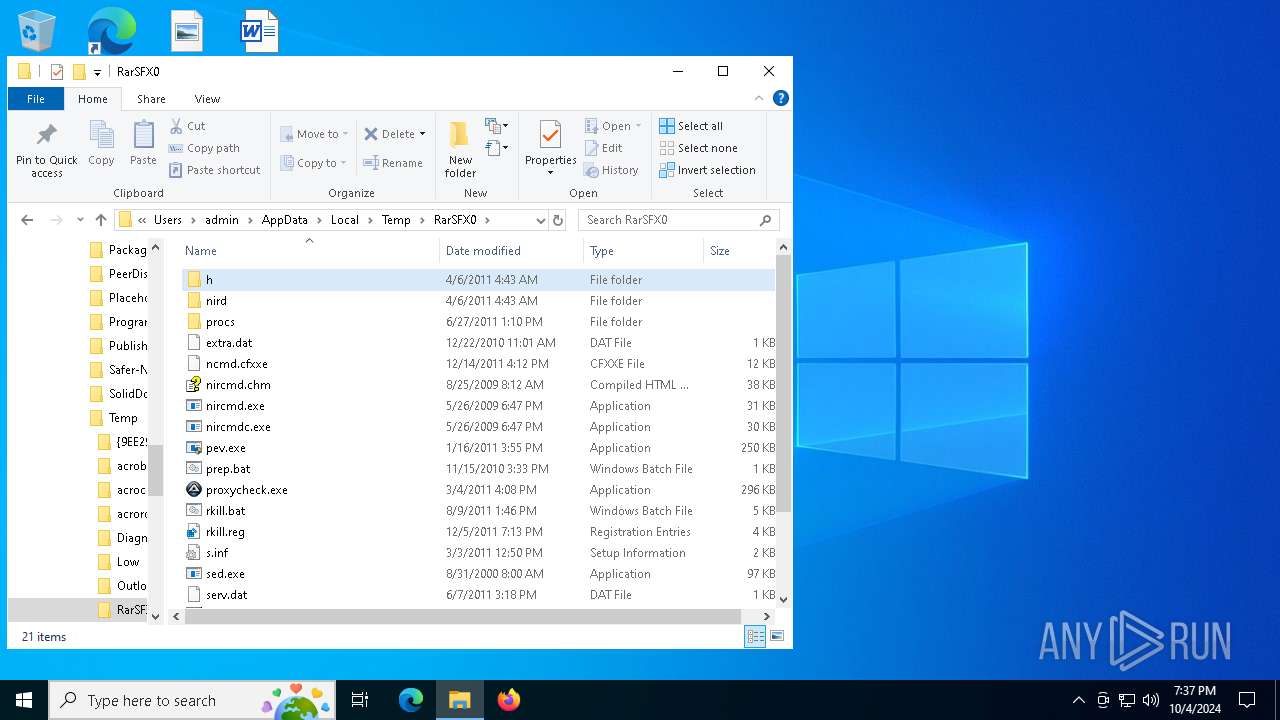
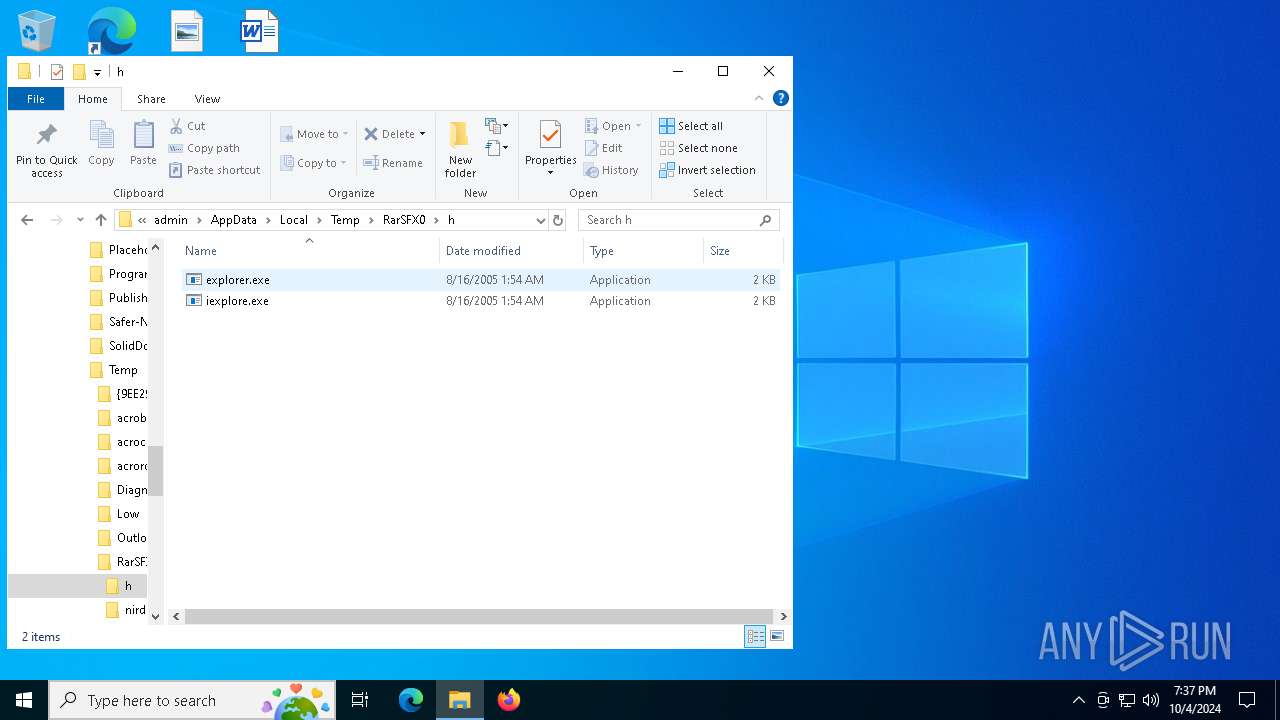
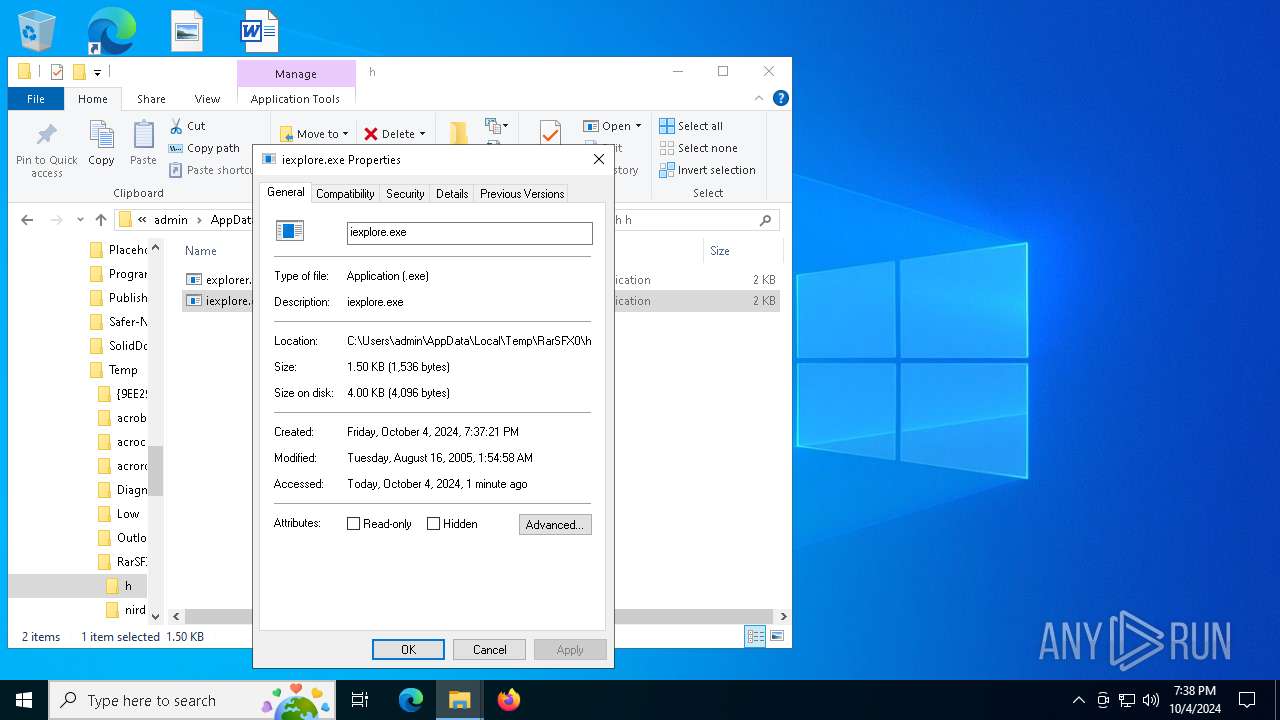
| File name: | rkill (1).exe |
| Full analysis: | https://app.any.run/tasks/6aa87eaa-2ce8-4fb7-9067-95a9d009e06e |
| Verdict: | Malicious activity |
| Analysis date: | October 04, 2024, 19:37:13 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, UPX compressed, RAR self-extracting archive |
| MD5: | 28C253A0212B221E96F6A17499B91651 |
| SHA1: | 4592DE27B3D46BD32BF6779420FE441E990A45A4 |
| SHA256: | B7FC473EB8029EA559315300F953995B126B0E1942762CAFCA96B80E8D1A4207 |
| SSDEEP: | 49152:QrYgzgxsD3EiOFafuN07tHY7q11LRt6fiiycZnhnu41lSCauZkEHHwDp1OhABgdv:ATgxsDUPFaWNgtJ1bkfBi43SoZkEnwDw |
MALICIOUS
No malicious indicators.SUSPICIOUS
Starts application with an unusual extension
- rkill (1).exe (PID: 3936)
Executable content was dropped or overwritten
- rkill (1).exe (PID: 3936)
Starts CMD.EXE for commands execution
- iexplore.exe (PID: 2628)
- rkill (1).exe (PID: 3936)
Executing commands from a ".bat" file
- iexplore.exe (PID: 2628)
- rkill (1).exe (PID: 3936)
The executable file from the user directory is run by the CMD process
- nircmd.exe (PID: 4092)
INFO
NirSoft software is detected
- iexplore.exe (PID: 3916)
- winlogon.exe (PID: 5852)
- iexplore.exe (PID: 6388)
- iexplore.exe (PID: 3116)
- userinit.exe (PID: 2032)
- iexplore.exe (PID: 1336)
- iexplore.exe (PID: 2480)
- iexplore.exe (PID: 6216)
- iexplore.exe (PID: 4668)
- iexplore.exe (PID: 5280)
- iexplore.exe (PID: 1656)
- iexplore.exe (PID: 5184)
- iexplore.exe (PID: 4248)
- nircmd.exe (PID: 4092)
UPX packer has been detected
- rkill (1).exe (PID: 3936)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | UPX compressed Win32 Executable (39.3) |
|---|---|---|
| .exe | | | Win32 EXE Yoda's Crypter (38.6) |
| .dll | | | Win32 Dynamic Link Library (generic) (9.5) |
| .exe | | | Win32 Executable (generic) (6.5) |
| .exe | | | Generic Win/DOS Executable (2.9) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2010:03:15 06:27:50+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 9 |
| CodeSize: | 49152 |
| InitializedDataSize: | 143360 |
| UninitializedDataSize: | 241664 |
| EntryPoint: | 0x471c0 |
| OSVersion: | 5 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
Total processes
251
Monitored processes
127
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 68 | "C:\Users\admin\AppData\Local\Temp\RarSFX0\h\iexplore.exe" procs\iexplore.exe -k "antivirus plus*" | C:\Users\admin\AppData\Local\Temp\RarSFX0\h\iexplore.exe | — | rkill (1).exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 188 | procs\iexplore.exe -loadline"extra.dat" and not "C:\Users\admin\AppData\Local\Temp\rkill (1).exe" | C:\Users\admin\AppData\Local\Temp\RarSFX0\procs\iexplore.exe | — | iexplore.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 304 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 832 | procs\explorer.exe plist C:\Users\admin\AppData\Local\Temp\rks1.log | C:\Users\admin\AppData\Local\Temp\RarSFX0\procs\explorer.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 1072 | procs\iexplore.exe -k "C:\NetworkControl\*.exe" | C:\Users\admin\AppData\Local\Temp\RarSFX0\procs\iexplore.exe | — | iexplore.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 4 Modules
| |||||||||||||||
| 1132 | procs\iexplore.exe RIMPORT rkill.reg | C:\Users\admin\AppData\Local\Temp\RarSFX0\procs\iexplore.exe | — | iexplore.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 1132 | procs\iexplore.exe -k *sysguard.exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\procs\iexplore.exe | — | iexplore.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 4 Modules
| |||||||||||||||
| 1144 | "C:\Windows\System32\grpconv.exe" -o | C:\Windows\SysWOW64\grpconv.exe | — | runonce.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Progman Group Converter Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1256 | procs\iexplore.exe -k "antivirus plus*" | C:\Users\admin\AppData\Local\Temp\RarSFX0\procs\iexplore.exe | — | iexplore.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 4 Modules
| |||||||||||||||
| 1336 | "C:\Users\admin\AppData\Local\Temp\RarSFX0\nird\iexplore.exe" win close stitle "Antivirus Suite" | C:\Users\admin\AppData\Local\Temp\RarSFX0\nird\iexplore.exe | — | rkill (1).exe | |||||||||||
User: admin Company: NirSoft Integrity Level: HIGH Description: NirCmd Exit code: 0 Version: 2.37 Modules
| |||||||||||||||
Total events
7 487
Read events
7 383
Write events
10
Delete events
94
Modification events
| (PID) Process: | (3300) explorer.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\exefile\shell\open\command |
| Operation: | delete value | Name: | IsolatedCommand |
Value: | |||
| (PID) Process: | (3300) explorer.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\exefile\shell\runas\command |
| Operation: | delete value | Name: | IsolatedCommand |
Value: | |||
| (PID) Process: | (3300) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System |
| Operation: | delete value | Name: | DisableRegistryTools |
Value: | |||
| (PID) Process: | (3300) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System |
| Operation: | delete value | Name: | DisableTaskMgr |
Value: | |||
| (PID) Process: | (3300) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\Explorer |
| Operation: | delete value | Name: | NoRun |
Value: | |||
| (PID) Process: | (3300) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\Explorer |
| Operation: | delete value | Name: | NoDesktop |
Value: | |||
| (PID) Process: | (3300) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\Explorer |
| Operation: | delete value | Name: | NoActiveDesktopChanges |
Value: | |||
| (PID) Process: | (3300) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\Explorer |
| Operation: | delete value | Name: | NoSetActiveDesktop |
Value: | |||
| (PID) Process: | (3300) explorer.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\Explorer |
| Operation: | delete value | Name: | NoRun |
Value: | |||
| (PID) Process: | (3300) explorer.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\Explorer |
| Operation: | delete value | Name: | NoDesktop |
Value: | |||
Executable files
14
Suspicious files
2
Text files
12
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3936 | rkill (1).exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\prep.bat | text | |
MD5:F35850B4789BB34B8413482FD878C2D0 | SHA256:2CFC5667BFB0E8A1403102FF15EF83E62A0B5FDC288363CEB5D782C5271E66AD | |||
| 3936 | rkill (1).exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\procs\iexplore.exe | executable | |
MD5:3C33B26F2F7FA61D882515F2D6078691 | SHA256:908FDB876715F0A77014A37396D9E964FA6359D98099929BAB4086E66D72BB9F | |||
| 3936 | rkill (1).exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\pev.exe | executable | |
MD5:3C33B26F2F7FA61D882515F2D6078691 | SHA256:908FDB876715F0A77014A37396D9E964FA6359D98099929BAB4086E66D72BB9F | |||
| 3936 | rkill (1).exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\proxycheck.exe | executable | |
MD5:43FEE8A7DA368EAAF5019443382D450D | SHA256:77E590CA7680C7C35A895FCD870EDB4CBD4C2A920D01739C21331D9FF874A9A6 | |||
| 3936 | rkill (1).exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\sed.exe | executable | |
MD5:2B657A67AEBB84AEA5632C53E61E23BF | SHA256:95A2E2CACFB63D095DE385A98F1D5D4A21F0E7E8DE485CBAF5B872434D43FB73 | |||
| 3936 | rkill (1).exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\swreg.exe | executable | |
MD5:01D95A1F8CF13D07CC564AABB36BCC0B | SHA256:1EED7A2498943B7303DE1F085820EDBABAE4A414DB6125862C1BA2DB269EE3E3 | |||
| 3936 | rkill (1).exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\procs\proc.dat | text | |
MD5:D6DEAC6DEE3BF5CDD4BA00C184CFEB0D | SHA256:D5246407BDC43774F146595E3E902C30FD53E6CF726155EB26AC71BE6A624280 | |||
| 3936 | rkill (1).exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\extra.dat | text | |
MD5:E817F8566C3D4B9F12E8749C892E3C61 | SHA256:EAA0729A02C9568F80AE4377C4DAE33EDCC48AAF39364E0001513399B9AFAD63 | |||
| 3936 | rkill (1).exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\userinit.exe | executable | |
MD5:AC6094297CD882B8626466CDEB64F19F | SHA256:27C7FFD8367AAA73155FBB287A7DF1F157F2D0C3323DBB176D02B36FF616FCA5 | |||
| 3936 | rkill (1).exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\winlogon.exe | executable | |
MD5:AC6094297CD882B8626466CDEB64F19F | SHA256:27C7FFD8367AAA73155FBB287A7DF1F157F2D0C3323DBB176D02B36FF616FCA5 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
14
DNS requests
4
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 92.122.76.122:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 92.122.76.122:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
3888 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4324 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5388 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |