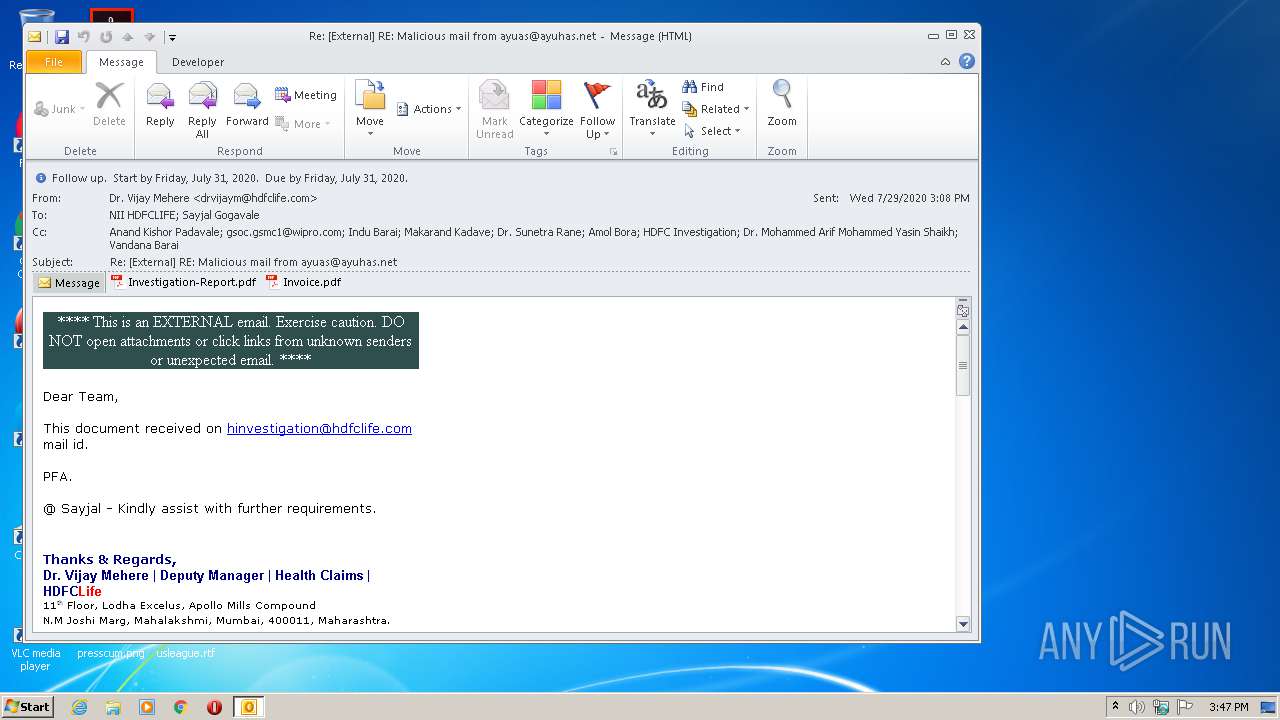
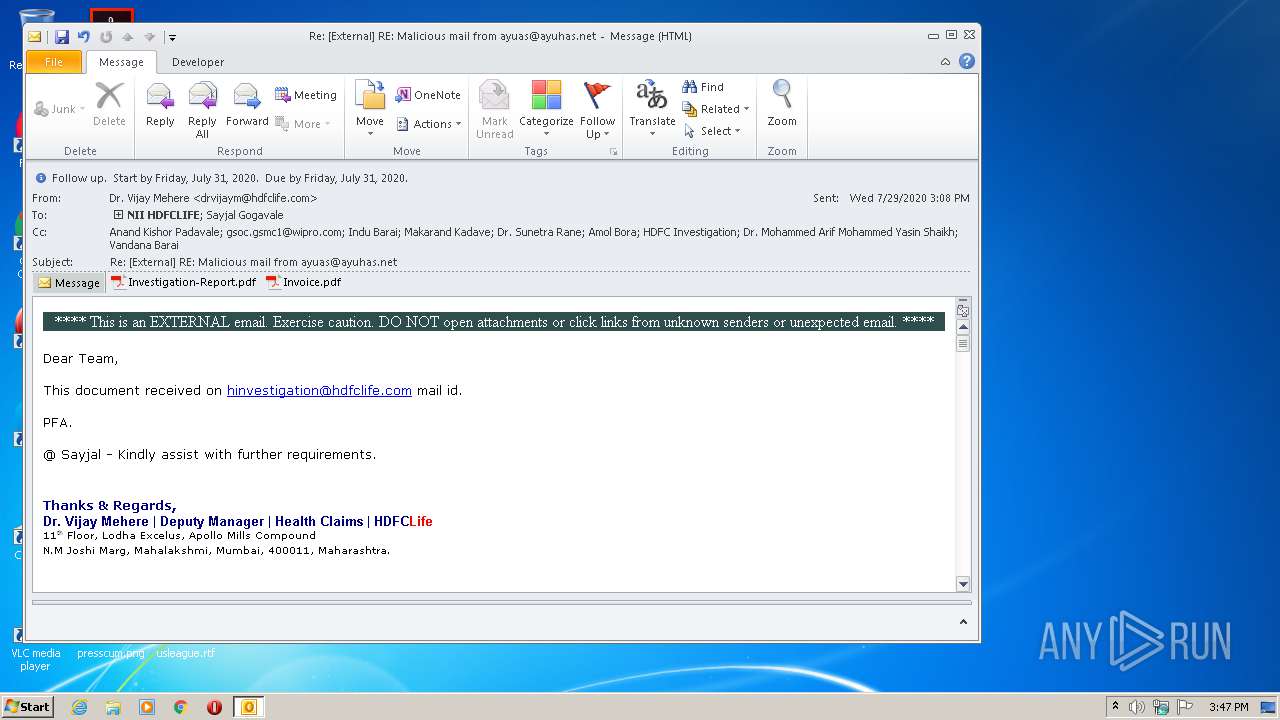
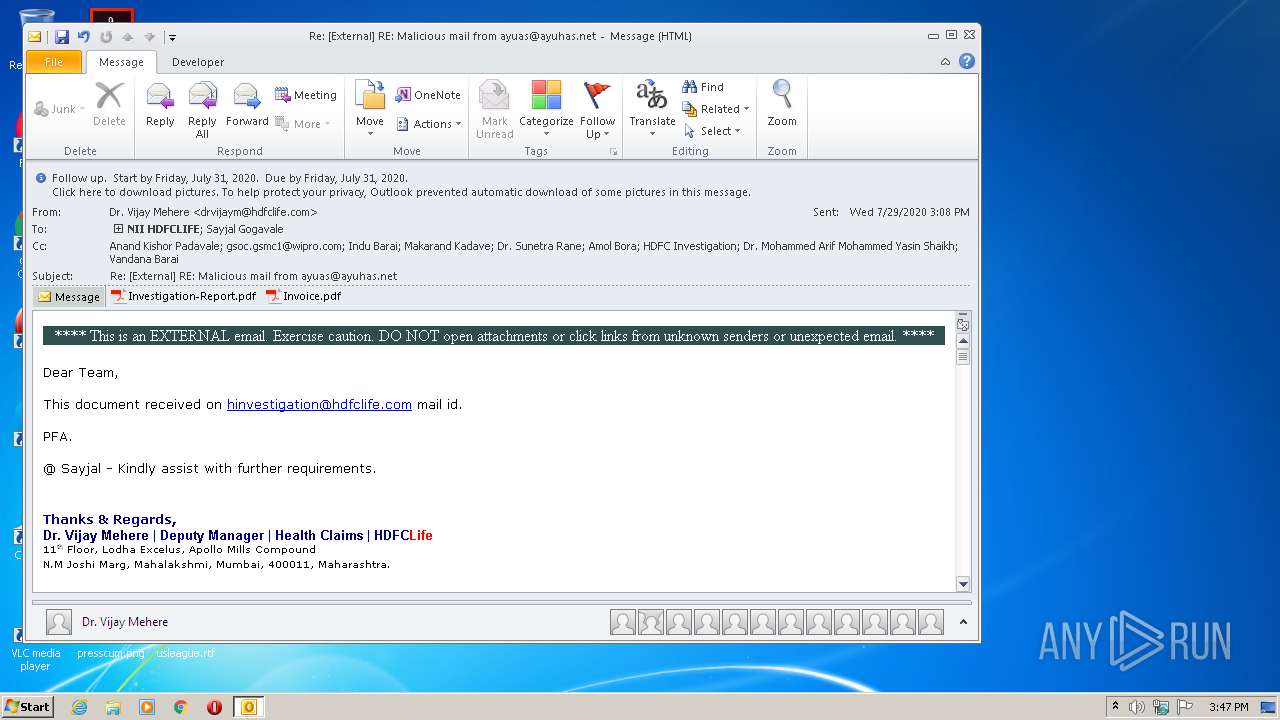
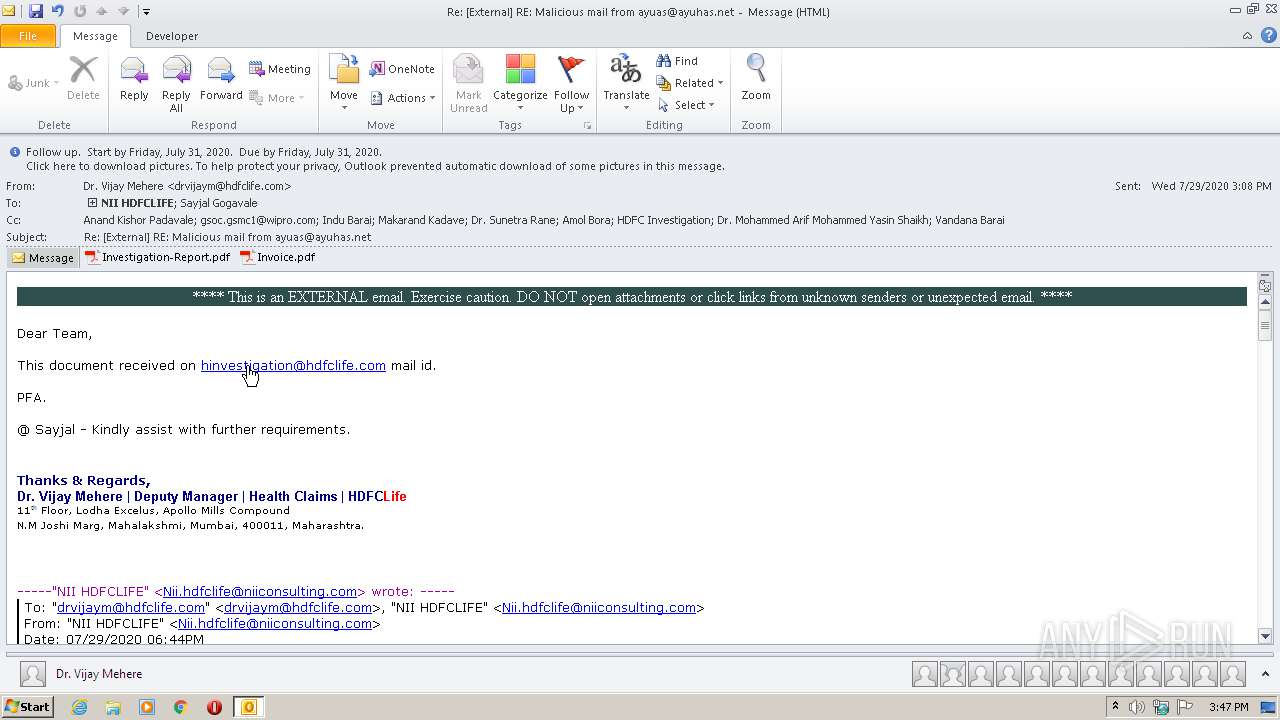
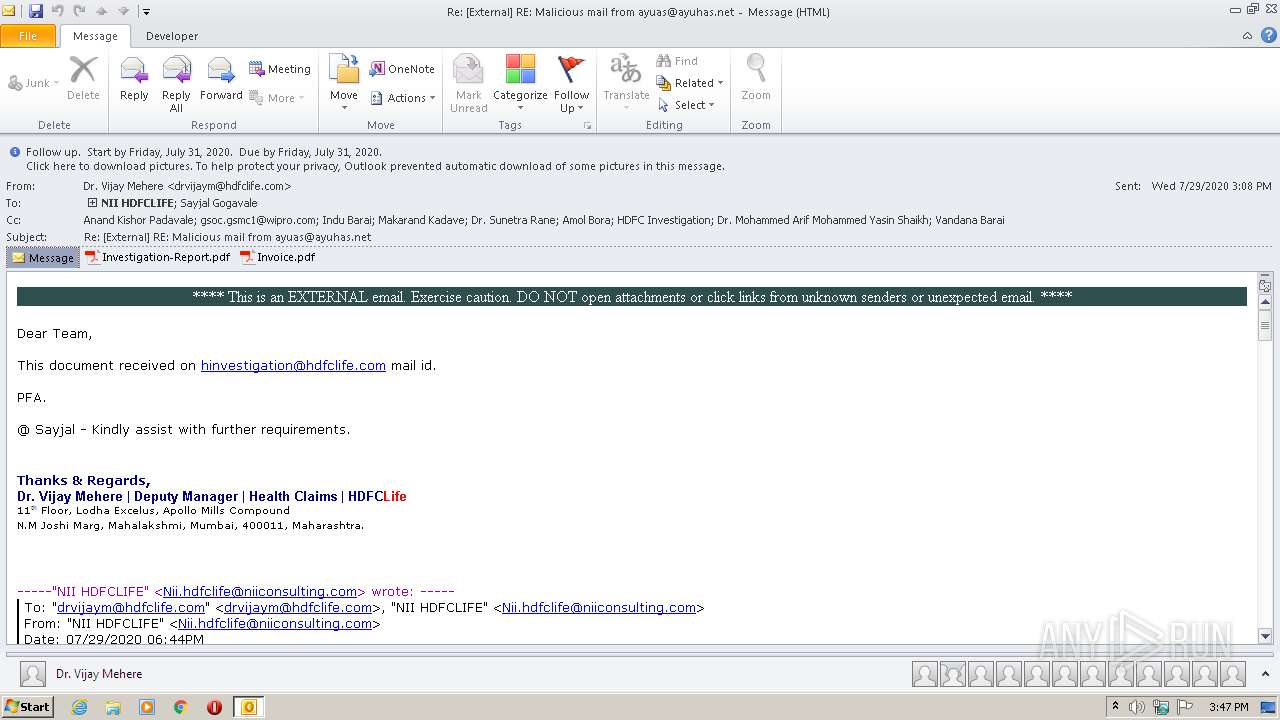
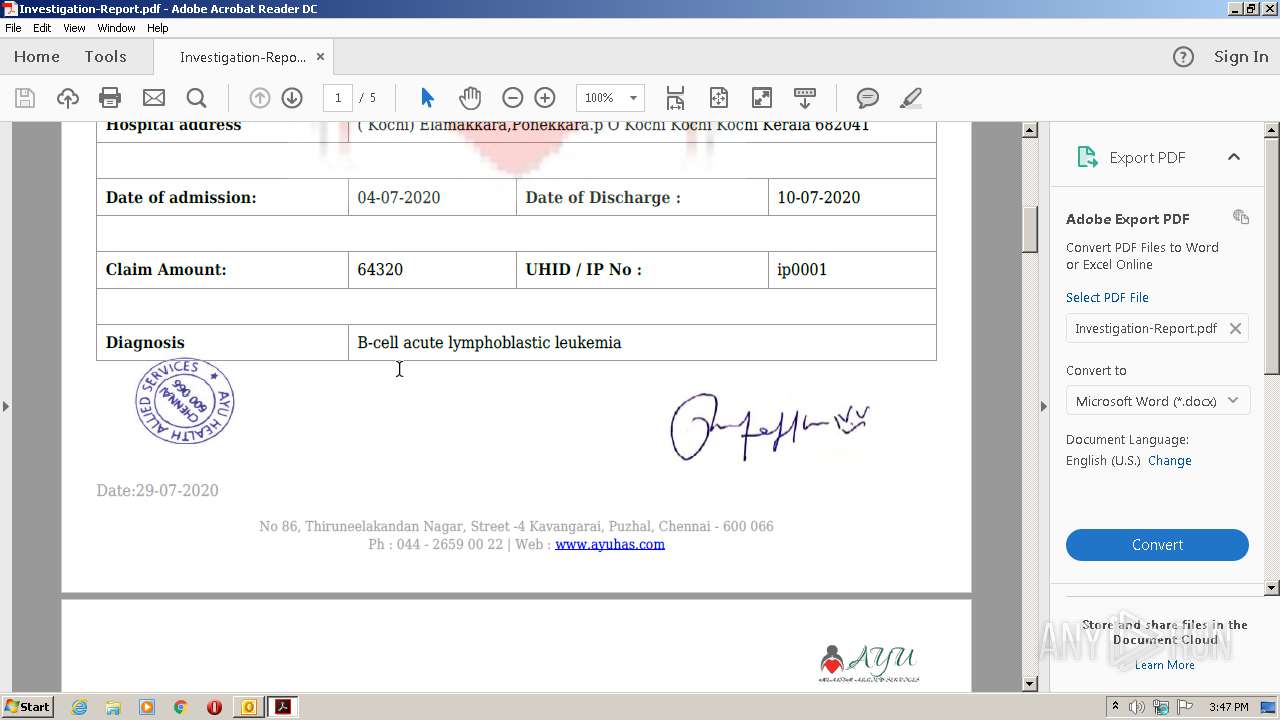
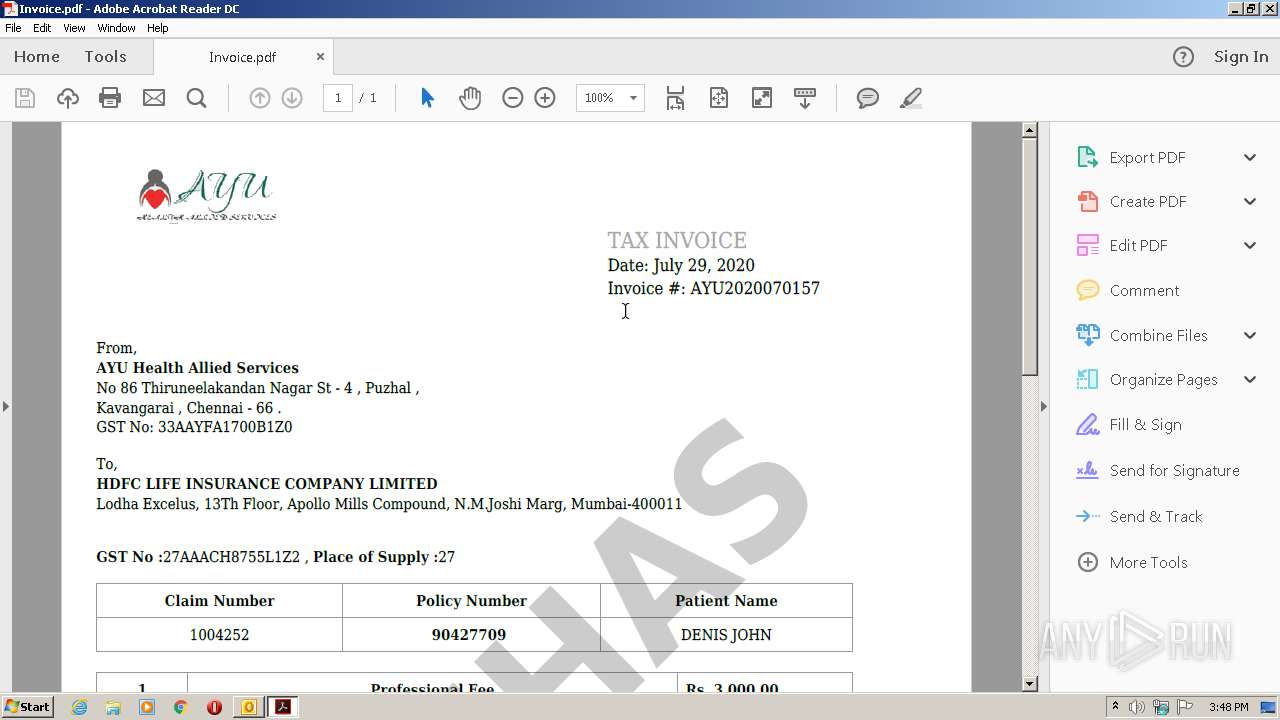
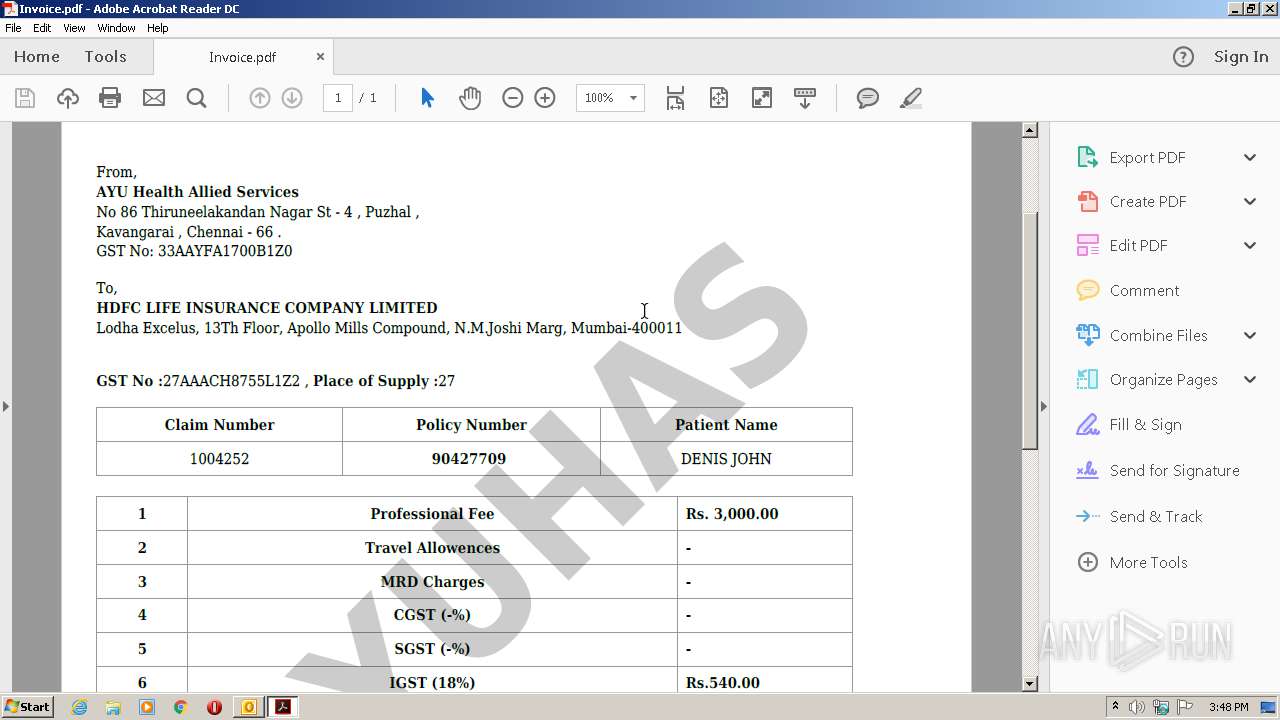
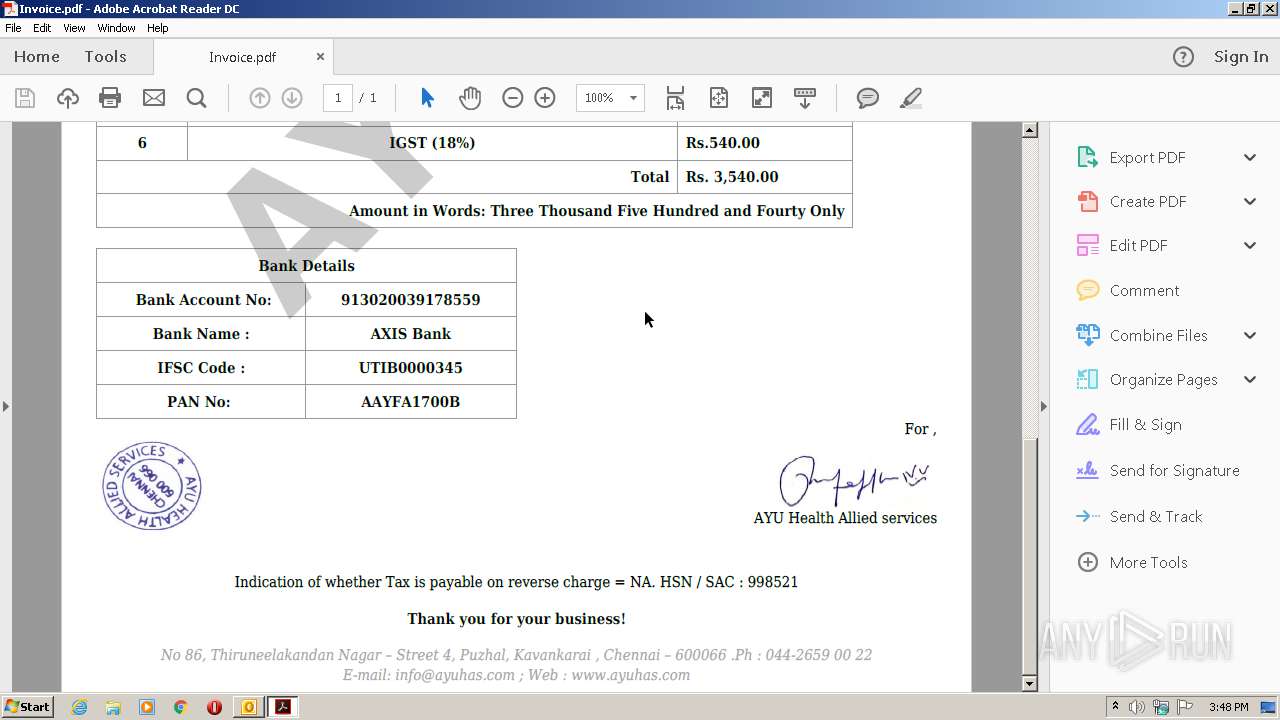
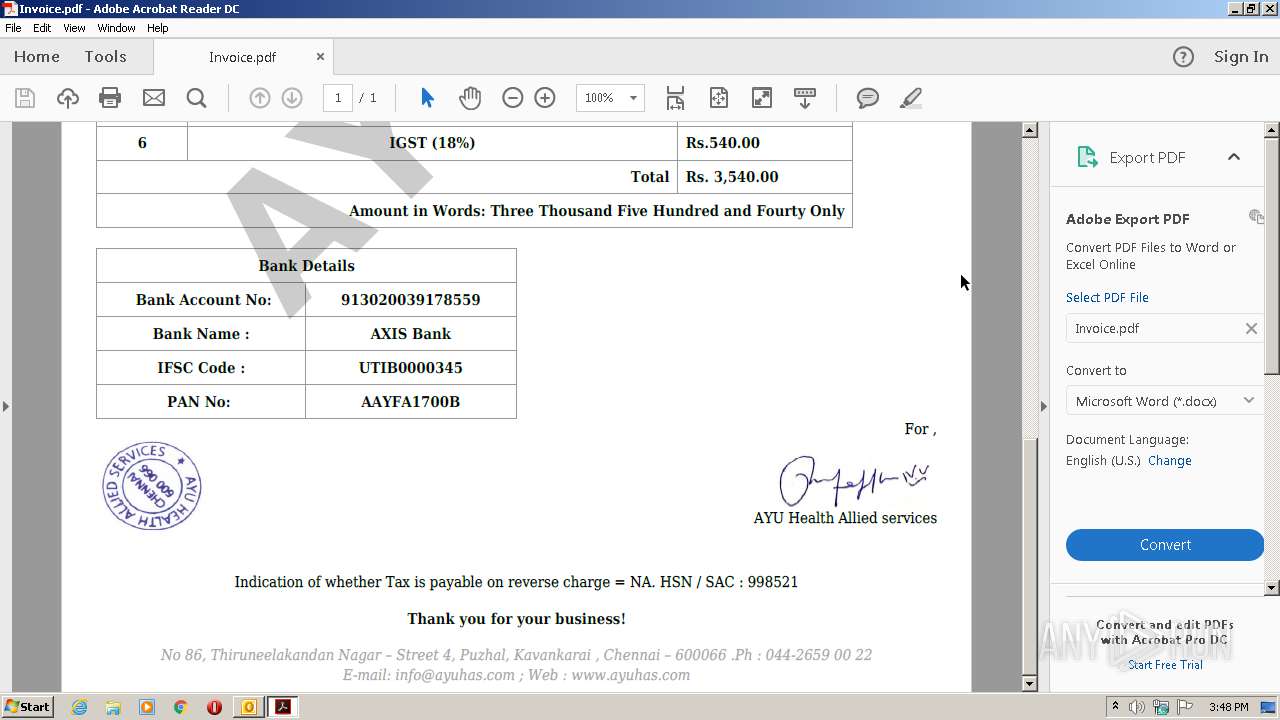
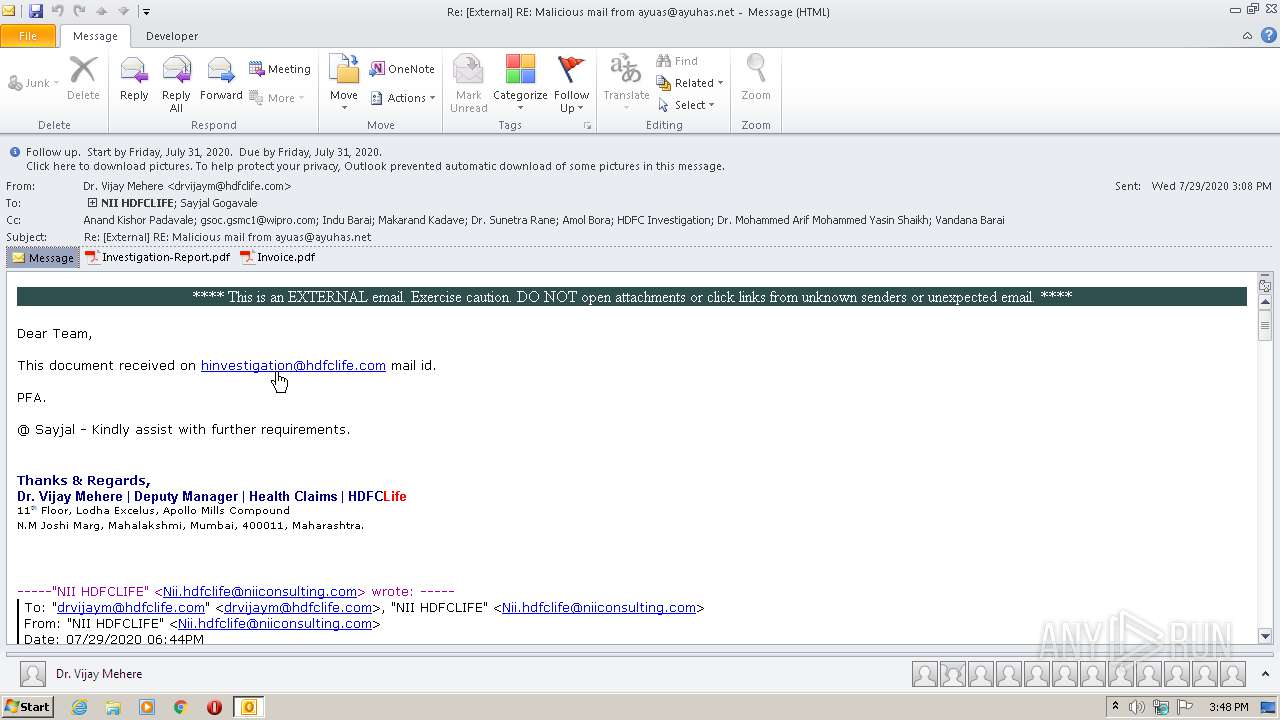
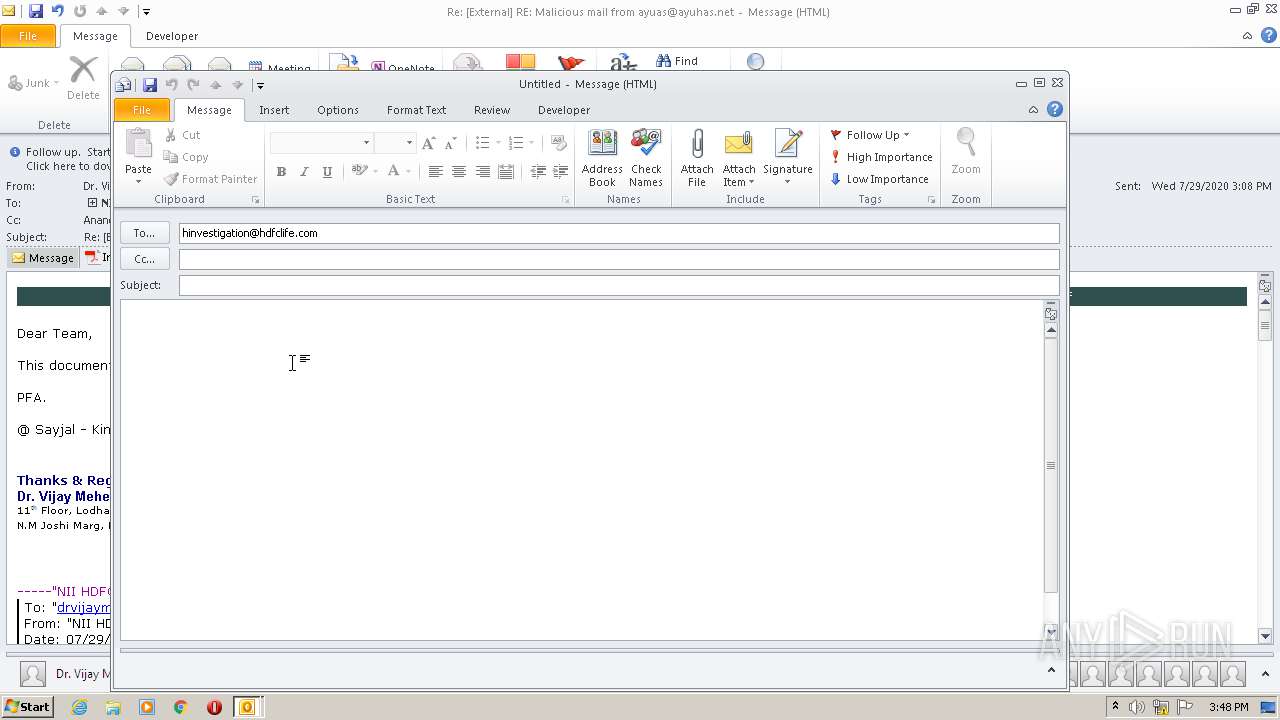
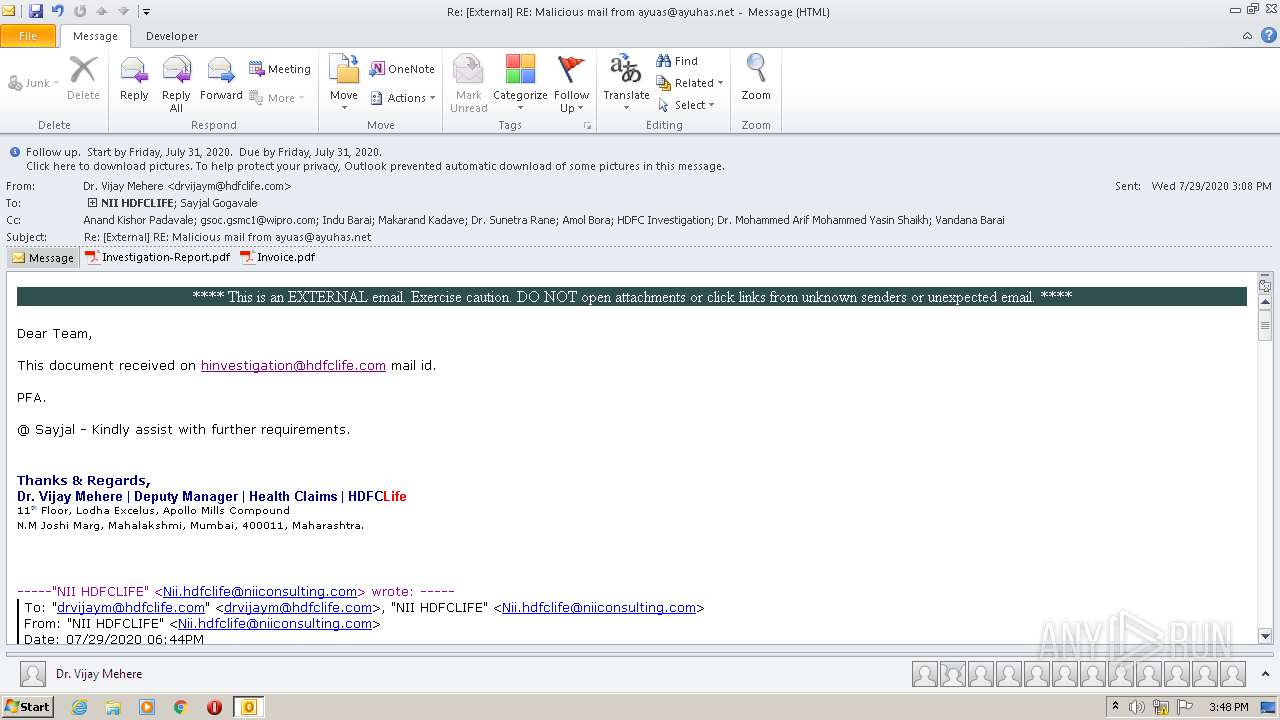
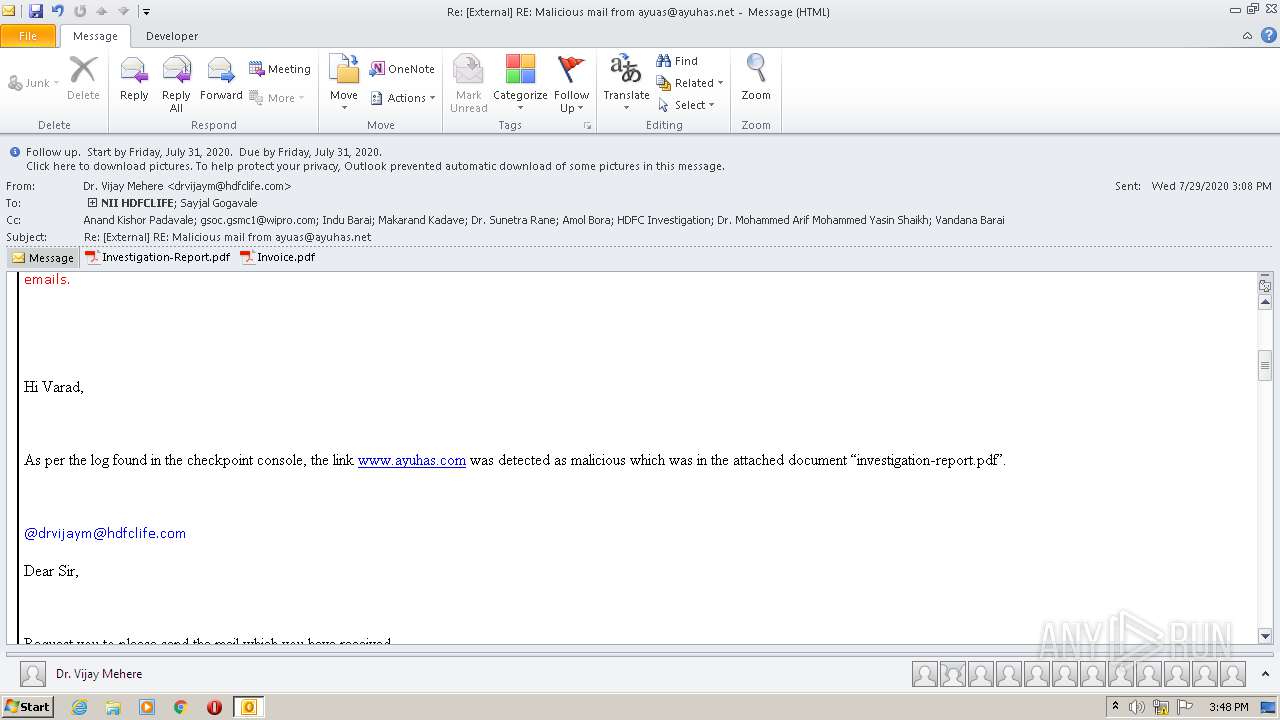
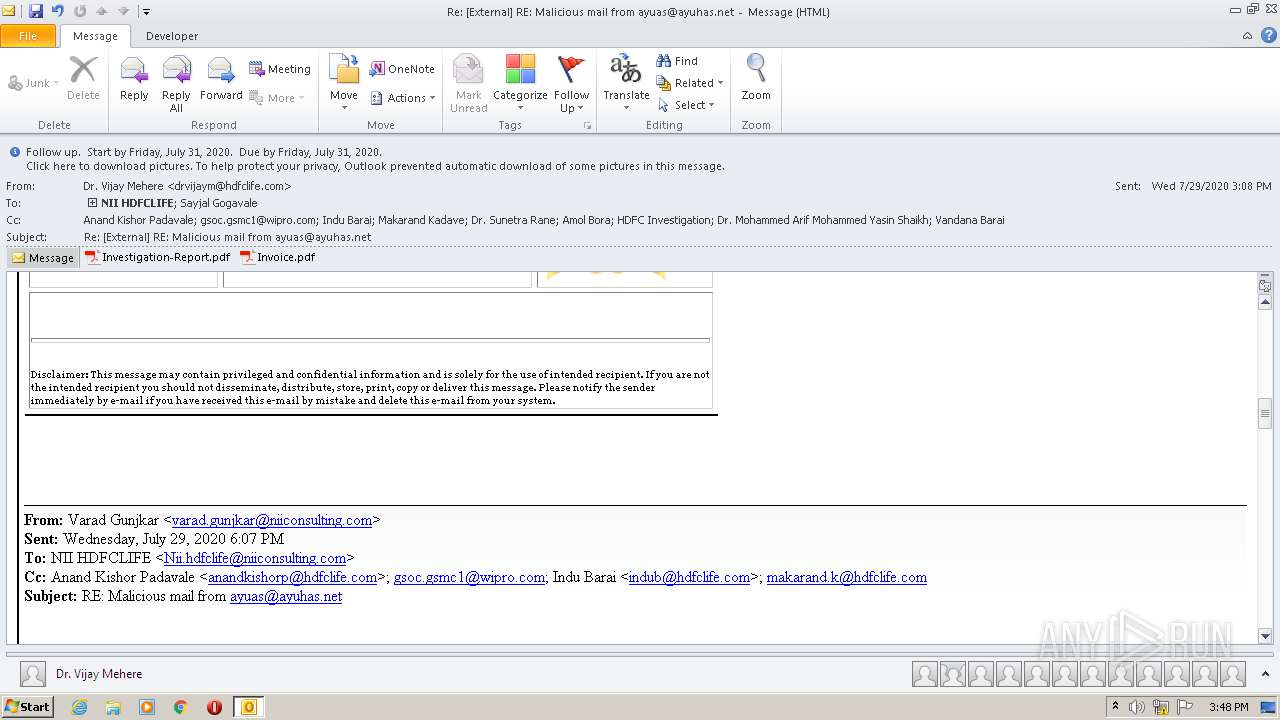
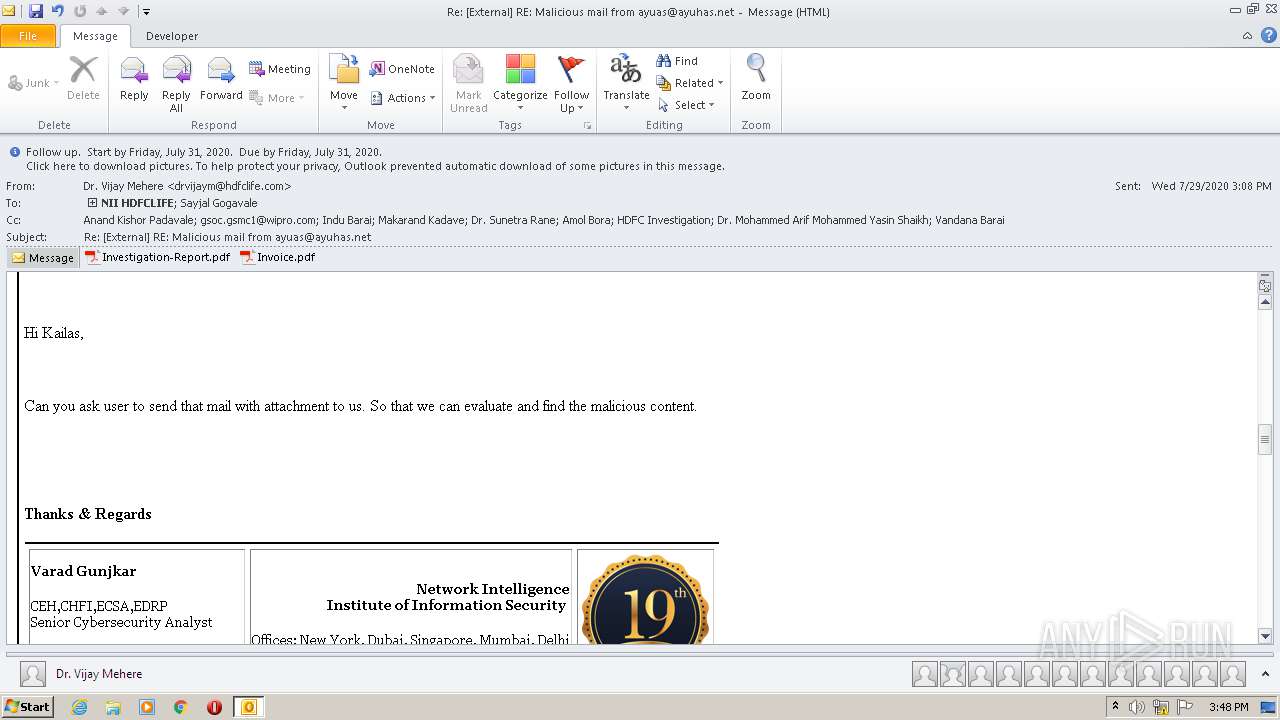
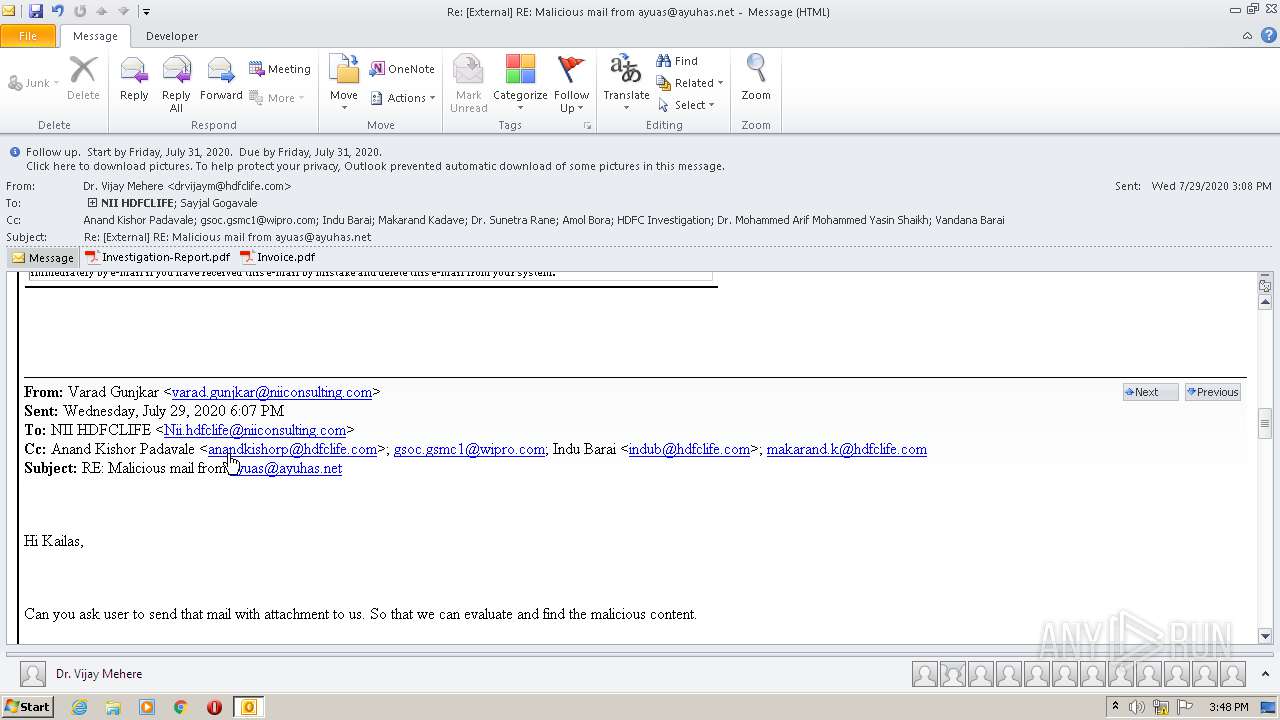
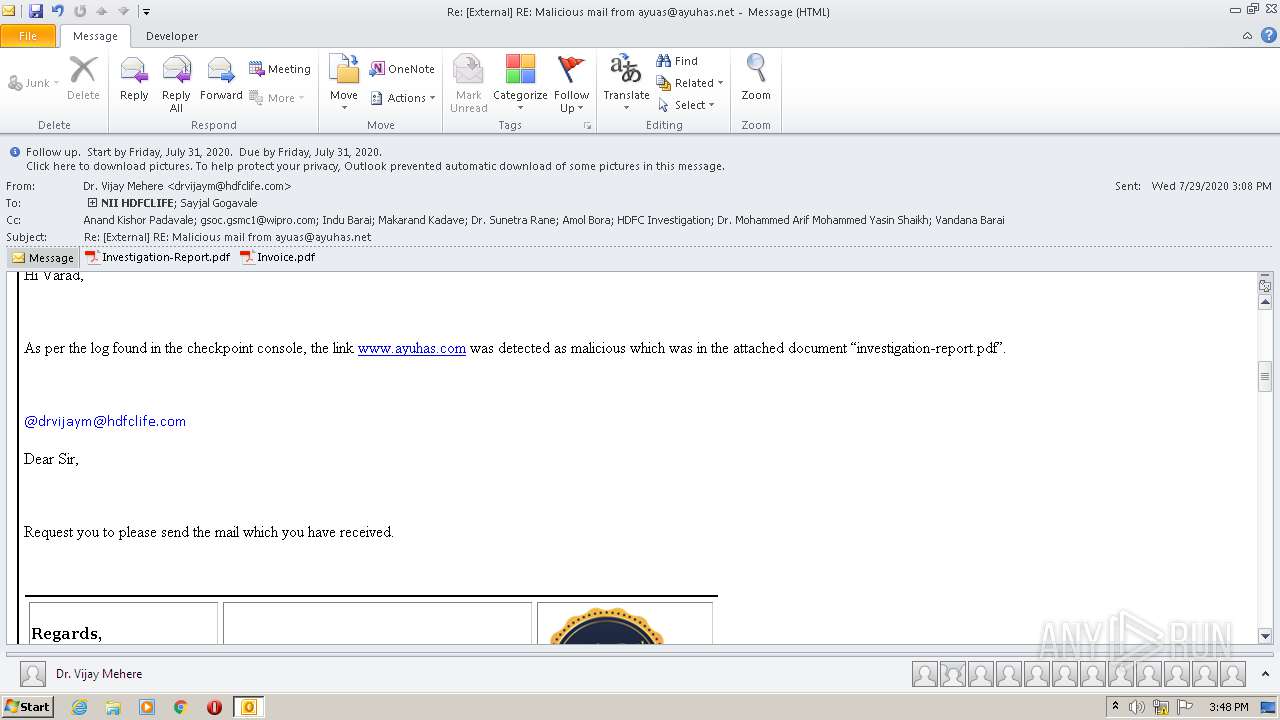
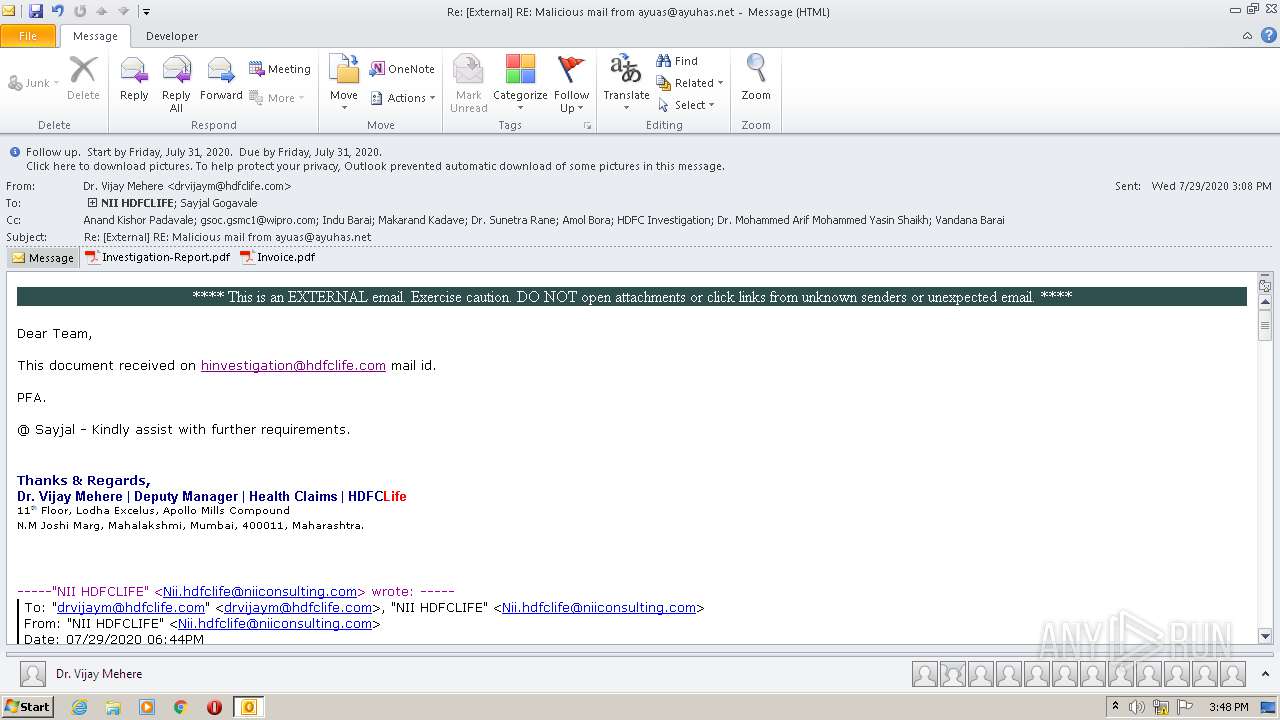
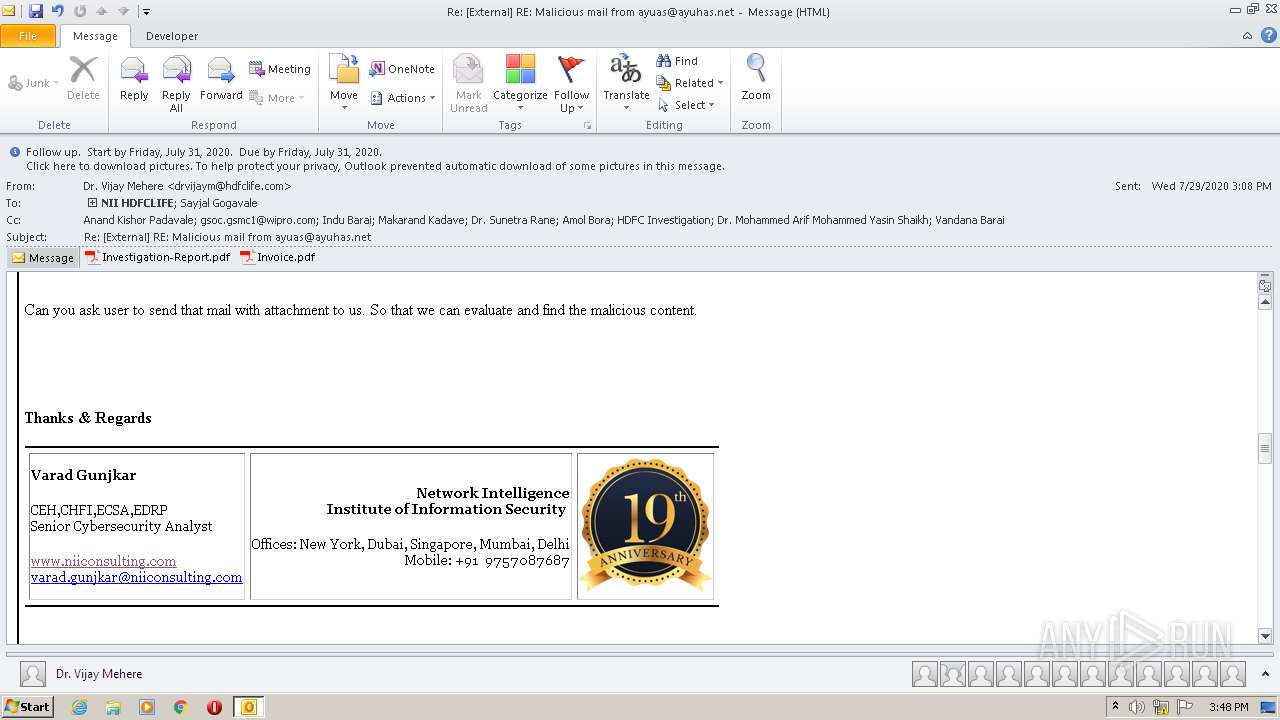
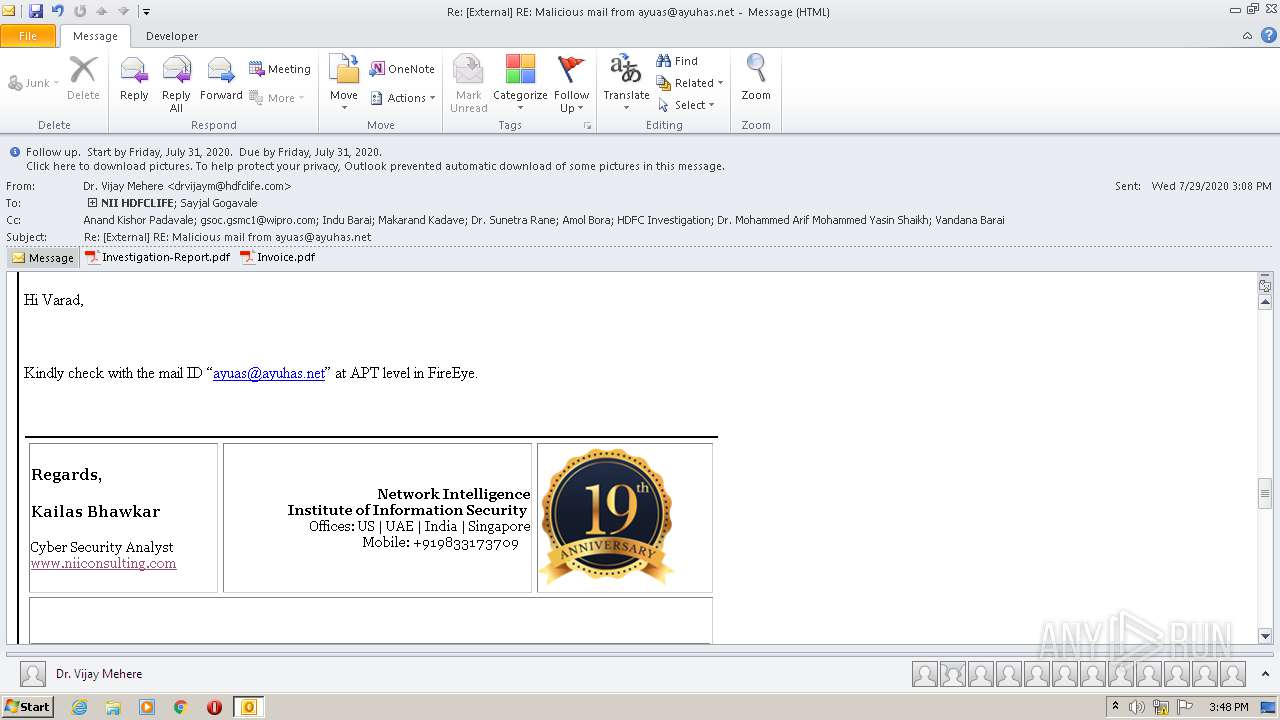
| File name: | Re External RE Malicious mail from ayuas@ayuhas.net.msg |
| Full analysis: | https://app.any.run/tasks/6f551177-6c88-4178-b9b8-5d4f31a5c7fd |
| Verdict: | Malicious activity |
| Analysis date: | August 08, 2020, 14:47:10 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/vnd.ms-outlook |
| File info: | CDFV2 Microsoft Outlook Message |
| MD5: | BB354C478113755686F752E43A3AE2BD |
| SHA1: | DF688557A81AED3A23B66966CD1C273DAE0C2D6D |
| SHA256: | B7D71D70AE7125EB4D594E015CBCA6664403E6536A5838C7D86524B4207F5E73 |
| SSDEEP: | 6144:bKVpxJaZsDSHl5nB5jffe8rzRF3hjDOrlsSI+JmQ5r:6zauDSFDJfG8rVrDOB3Fr |
MALICIOUS
Unusual execution from Microsoft Office
- OUTLOOK.EXE (PID: 2300)
SUSPICIOUS
Creates files in the user directory
- OUTLOOK.EXE (PID: 2300)
Starts itself from another location
- OUTLOOK.EXE (PID: 2300)
Changes IE settings (feature browser emulation)
- AcroRd32.exe (PID: 3428)
INFO
Reads Internet Cache Settings
- OUTLOOK.EXE (PID: 2300)
- AcroRd32.exe (PID: 3428)
- AcroRd32.exe (PID: 2700)
Application launched itself
- RdrCEF.exe (PID: 1804)
- AcroRd32.exe (PID: 2788)
- RdrCEF.exe (PID: 408)
- AcroRd32.exe (PID: 3428)
Reads the hosts file
- RdrCEF.exe (PID: 1804)
- RdrCEF.exe (PID: 408)
Creates files in the user directory
- AcroRd32.exe (PID: 3428)
Reads Microsoft Office registry keys
- OUTLOOK.EXE (PID: 2300)
- OUTLOOK.EXE (PID: 3968)
Reads settings of System Certificates
- AcroRd32.exe (PID: 3428)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .msg | | | Outlook Message (58.9) |
|---|---|---|
| .oft | | | Outlook Form Template (34.4) |
Total processes
51
Monitored processes
12
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 408 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe" --backgroundcolor=16448250 | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe | — | AcroRd32.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: MEDIUM Description: Adobe RdrCEF Exit code: 3221225547 Version: 15.23.20053.211670 Modules
| |||||||||||||||
| 656 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroRd32.exe" --type=renderer "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Outlook\OD1GGVFR\Invoice.pdf" | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroRd32.exe | — | AcroRd32.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe Acrobat Reader DC Exit code: 1 Version: 15.23.20070.215641 Modules
| |||||||||||||||
| 832 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe" --type=renderer --disable-3d-apis --disable-databases --disable-direct-npapi-requests --disable-file-system --disable-notifications --disable-shared-workers --disable-direct-write --lang=en-US --lang=en-US --log-severity=disable --product-version="ReaderServices/15.23.20053 Chrome/45.0.2454.85" --device-scale-factor=1 --enable-delegated-renderer --num-raster-threads=2 --gpu-rasterization-msaa-sample-count=8 --content-image-texture-target=3553 --video-image-texture-target=3553 --disable-accelerated-video-decode --disable-webrtc-hw-encoding --disable-gpu-compositing --channel="1804.1.1355575442\1417600310" --allow-no-sandbox-job /prefetch:673131151 | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe | — | RdrCEF.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe RdrCEF Exit code: 0 Version: 15.23.20053.211670 Modules
| |||||||||||||||
| 1804 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe" --backgroundcolor=16448250 | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe | — | AcroRd32.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: MEDIUM Description: Adobe RdrCEF Exit code: 0 Version: 15.23.20053.211670 Modules
| |||||||||||||||
| 1920 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe" --type=renderer --disable-3d-apis --disable-databases --disable-direct-npapi-requests --disable-file-system --disable-notifications --disable-shared-workers --disable-direct-write --lang=en-US --lang=en-US --log-severity=disable --product-version="ReaderServices/15.23.20053 Chrome/45.0.2454.85" --device-scale-factor=1 --enable-delegated-renderer --num-raster-threads=2 --gpu-rasterization-msaa-sample-count=8 --content-image-texture-target=3553 --video-image-texture-target=3553 --disable-accelerated-video-decode --disable-webrtc-hw-encoding --disable-gpu-compositing --channel="408.1.638202330\171365142" --allow-no-sandbox-job /prefetch:673131151 | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe | — | RdrCEF.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe RdrCEF Exit code: 0 Version: 15.23.20053.211670 Modules
| |||||||||||||||
| 2300 | "C:\Program Files\Microsoft Office\Office14\OUTLOOK.EXE" /f "C:\Users\admin\AppData\Local\Temp\Re External RE Malicious mail from ayuas@ayuhas.net.msg" | C:\Program Files\Microsoft Office\Office14\OUTLOOK.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Outlook Exit code: 0 Version: 14.0.6025.1000 Modules
| |||||||||||||||
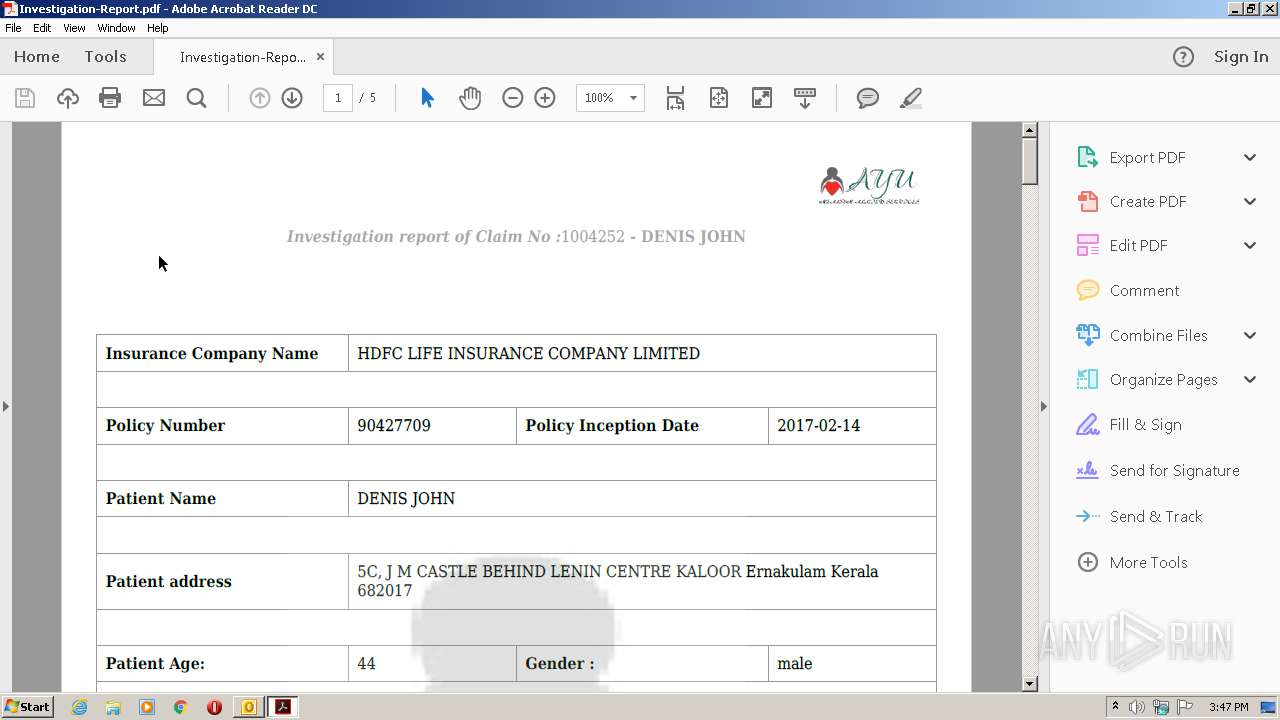
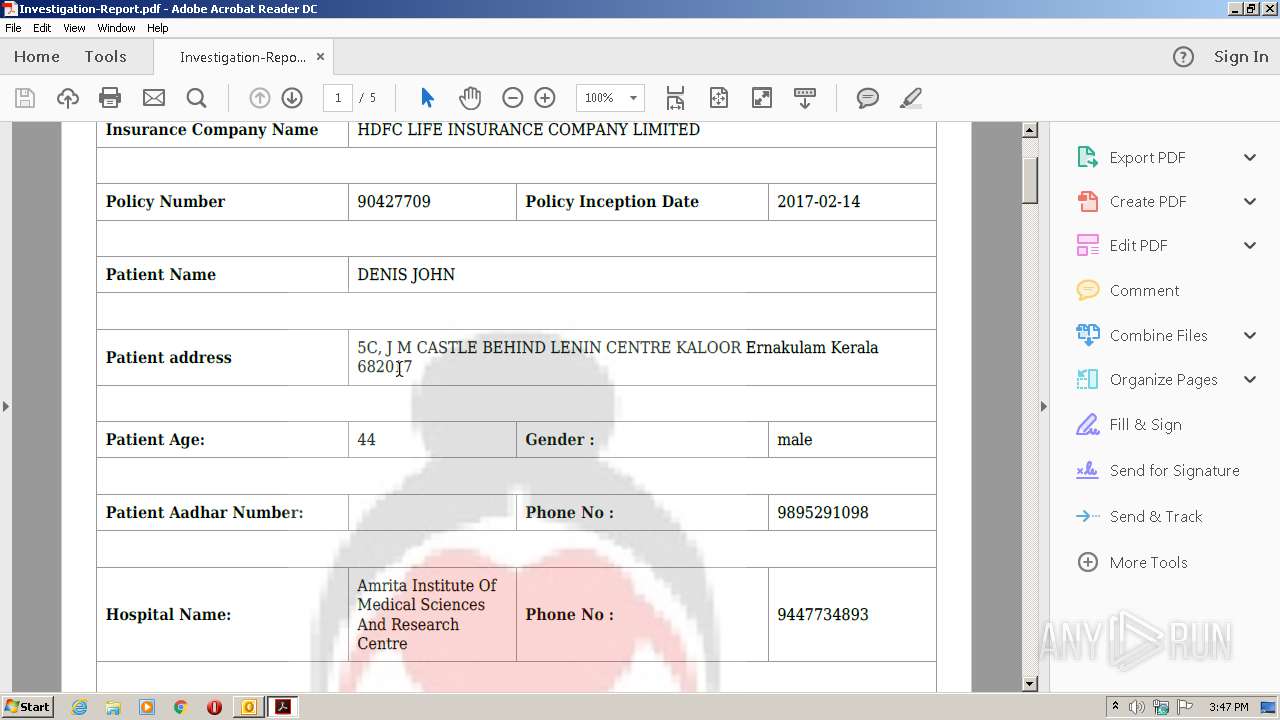
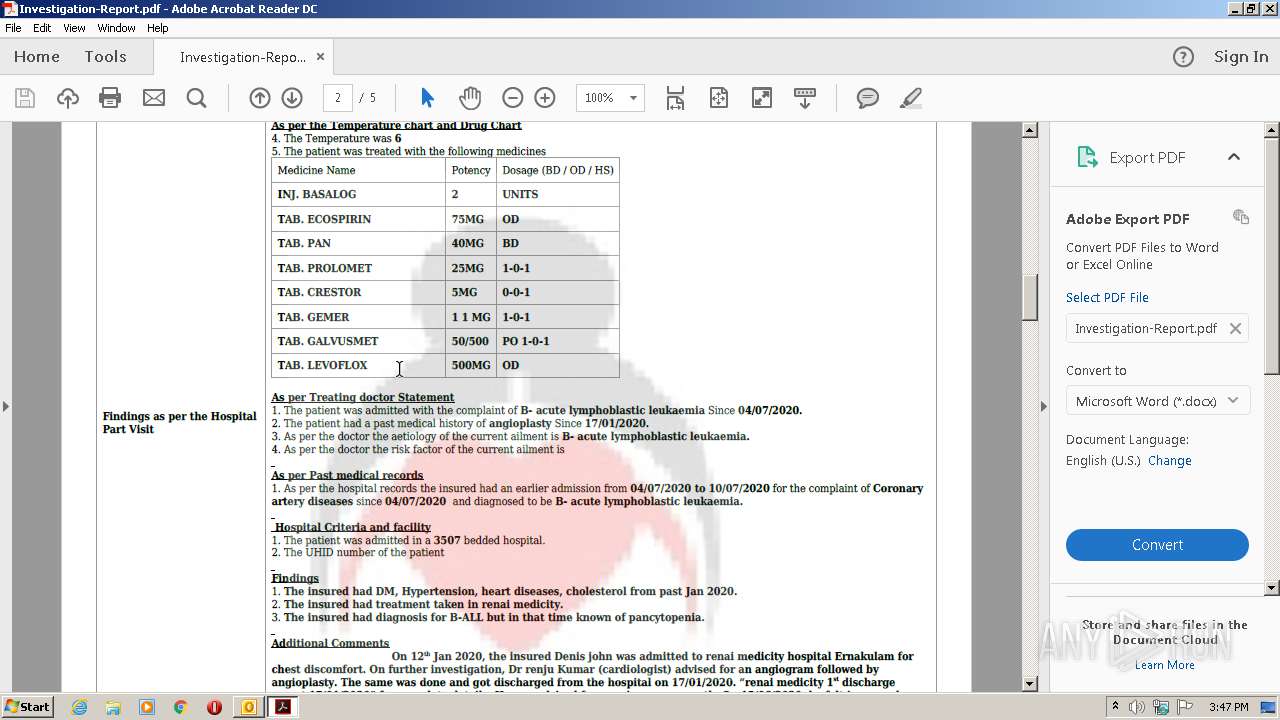
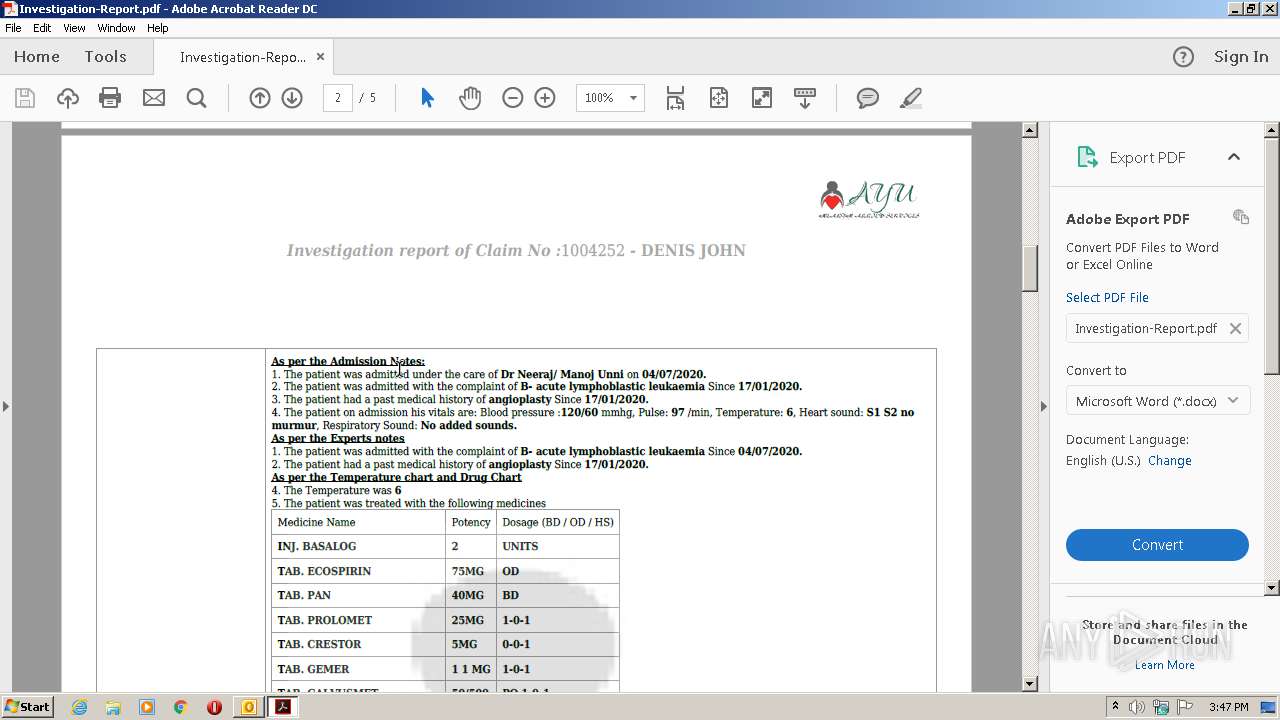
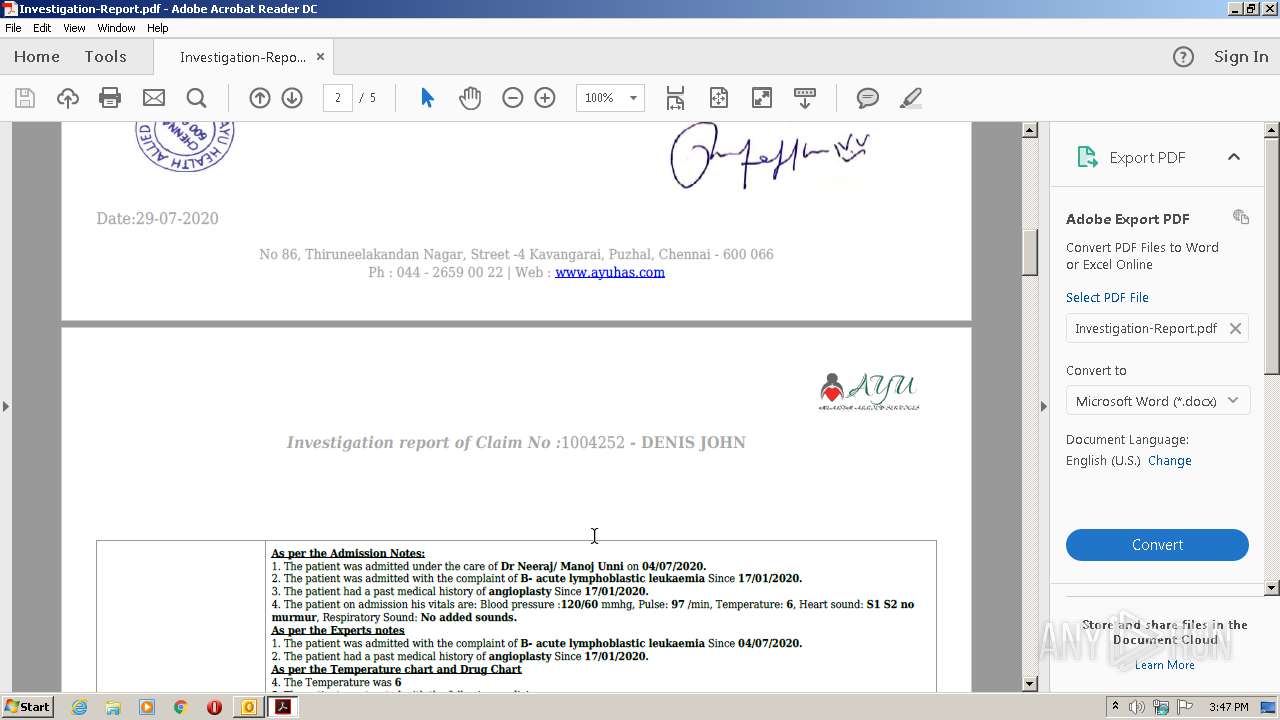
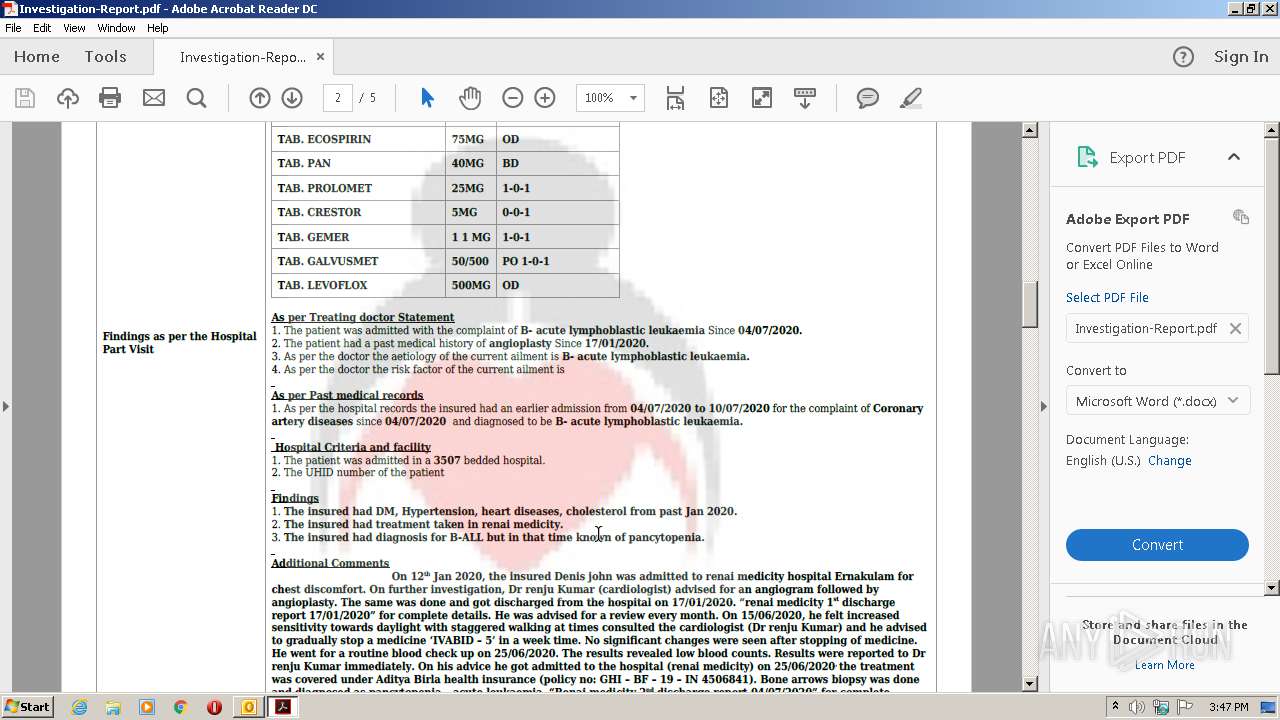
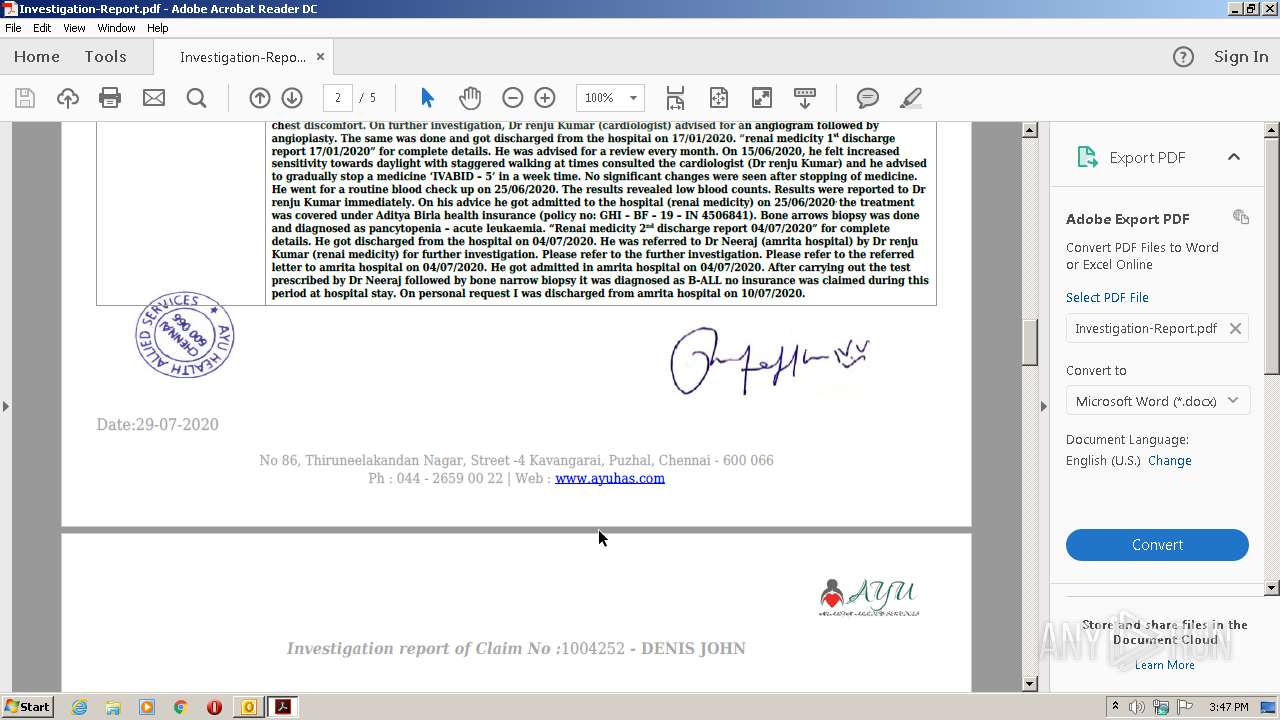
| 2700 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroRd32.exe" --type=renderer "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Outlook\OD1GGVFR\Investigation-Report.pdf" | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroRd32.exe | — | AcroRd32.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe Acrobat Reader DC Exit code: 1 Version: 15.23.20070.215641 Modules
| |||||||||||||||
| 2788 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroRd32.exe" "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Outlook\OD1GGVFR\Invoice.pdf" | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroRd32.exe | — | OUTLOOK.EXE | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: MEDIUM Description: Adobe Acrobat Reader DC Exit code: 1 Version: 15.23.20070.215641 Modules
| |||||||||||||||
| 3428 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroRd32.exe" "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Outlook\OD1GGVFR\Investigation-Report.pdf" | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroRd32.exe | OUTLOOK.EXE | ||||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: MEDIUM Description: Adobe Acrobat Reader DC Exit code: 1 Version: 15.23.20070.215641 Modules
| |||||||||||||||
| 3752 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe" --type=renderer --disable-3d-apis --disable-databases --disable-direct-npapi-requests --disable-file-system --disable-notifications --disable-shared-workers --disable-direct-write --lang=en-US --lang=en-US --log-severity=disable --product-version="ReaderServices/15.23.20053 Chrome/45.0.2454.85" --device-scale-factor=1 --enable-delegated-renderer --num-raster-threads=2 --gpu-rasterization-msaa-sample-count=8 --content-image-texture-target=3553 --video-image-texture-target=3553 --disable-accelerated-video-decode --disable-webrtc-hw-encoding --disable-gpu-compositing --channel="408.0.1158584408\320740795" --allow-no-sandbox-job /prefetch:673131151 | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe | — | RdrCEF.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe RdrCEF Exit code: 0 Version: 15.23.20053.211670 Modules
| |||||||||||||||
Total events
2 360
Read events
1 560
Write events
770
Delete events
30
Modification events
| (PID) Process: | (2300) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (2300) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1041 |
Value: Off | |||
| (PID) Process: | (2300) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1046 |
Value: Off | |||
| (PID) Process: | (2300) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1036 |
Value: Off | |||
| (PID) Process: | (2300) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1031 |
Value: Off | |||
| (PID) Process: | (2300) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1040 |
Value: Off | |||
| (PID) Process: | (2300) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1049 |
Value: Off | |||
| (PID) Process: | (2300) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 3082 |
Value: Off | |||
| (PID) Process: | (2300) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1042 |
Value: Off | |||
| (PID) Process: | (2300) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1055 |
Value: Off | |||
Executable files
0
Suspicious files
13
Text files
31
Unknown types
31
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2300 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\CVRBC2C.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 2300 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Outlook\OD1GGVFR\Investigation-Report (2).pdf\:Zone.Identifier:$DATA | — | |
MD5:— | SHA256:— | |||
| 2700 | AcroRd32.exe | C:\Users\admin\AppData\LocalLow\Adobe\Acrobat\DC\ReaderMessages-journal | — | |
MD5:— | SHA256:— | |||
| 2700 | AcroRd32.exe | C:\Users\admin\AppData\Local\Temp\acrord32_sbx\A9R4ksn7k_5gdmud_230.tmp | — | |
MD5:— | SHA256:— | |||
| 2700 | AcroRd32.exe | C:\Users\admin\AppData\Local\Temp\acrord32_sbx\A9R1cht6nu_5gdmuc_230.tmp | — | |
MD5:— | SHA256:— | |||
| 2700 | AcroRd32.exe | C:\Users\admin\AppData\Local\Temp\acrord32_sbx\A9R1kl5so2_5gdmuf_230.tmp | — | |
MD5:— | SHA256:— | |||
| 2700 | AcroRd32.exe | C:\Users\admin\AppData\Local\Temp\acrord32_sbx\A9R16l3k65_5gdmue_230.tmp | — | |
MD5:— | SHA256:— | |||
| 2300 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\5450ED82.dat | image | |
MD5:— | SHA256:— | |||
| 3428 | AcroRd32.exe | C:\Users\admin\AppData\Local\Temp\Cab2F78.tmp | — | |
MD5:— | SHA256:— | |||
| 3428 | AcroRd32.exe | C:\Users\admin\AppData\Local\Temp\Tar2F79.tmp | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
5
DNS requests
4
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3428 | AcroRd32.exe | GET | 304 | 2.16.177.91:80 | http://acroipm2.adobe.com/15/rdr/ENU/win/nooem/none/consumer/280_15_23_20070.zip | unknown | — | — | whitelisted |
3428 | AcroRd32.exe | GET | 304 | 2.16.177.91:80 | http://acroipm2.adobe.com/15/rdr/ENU/win/nooem/none/consumer/281_15_23_20070.zip | unknown | — | — | whitelisted |
3428 | AcroRd32.exe | GET | 304 | 2.16.177.91:80 | http://acroipm2.adobe.com/15/rdr/ENU/win/nooem/none/consumer/278_15_23_20070.zip | unknown | — | — | whitelisted |
3428 | AcroRd32.exe | GET | 304 | 2.16.177.91:80 | http://acroipm2.adobe.com/15/rdr/ENU/win/nooem/none/consumer/277_15_23_20070.zip | unknown | — | — | whitelisted |
3428 | AcroRd32.exe | GET | 200 | 2.16.177.91:80 | http://acroipm2.adobe.com/15/rdr/ENU/win/nooem/none/consumer/message.zip | unknown | compressed | 9.54 Kb | whitelisted |
3428 | AcroRd32.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAH9o%2BtuynXIiEOLckvPvJE%3D | US | der | 471 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3428 | AcroRd32.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
3428 | AcroRd32.exe | 2.16.177.91:80 | acroipm2.adobe.com | Akamai International B.V. | — | whitelisted |
2300 | OUTLOOK.EXE | 64.4.26.155:80 | config.messenger.msn.com | Microsoft Corporation | US | whitelisted |
3428 | AcroRd32.exe | 23.210.248.251:443 | armmf.adobe.com | Akamai International B.V. | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
config.messenger.msn.com |
| whitelisted |
acroipm2.adobe.com |
| whitelisted |
armmf.adobe.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |