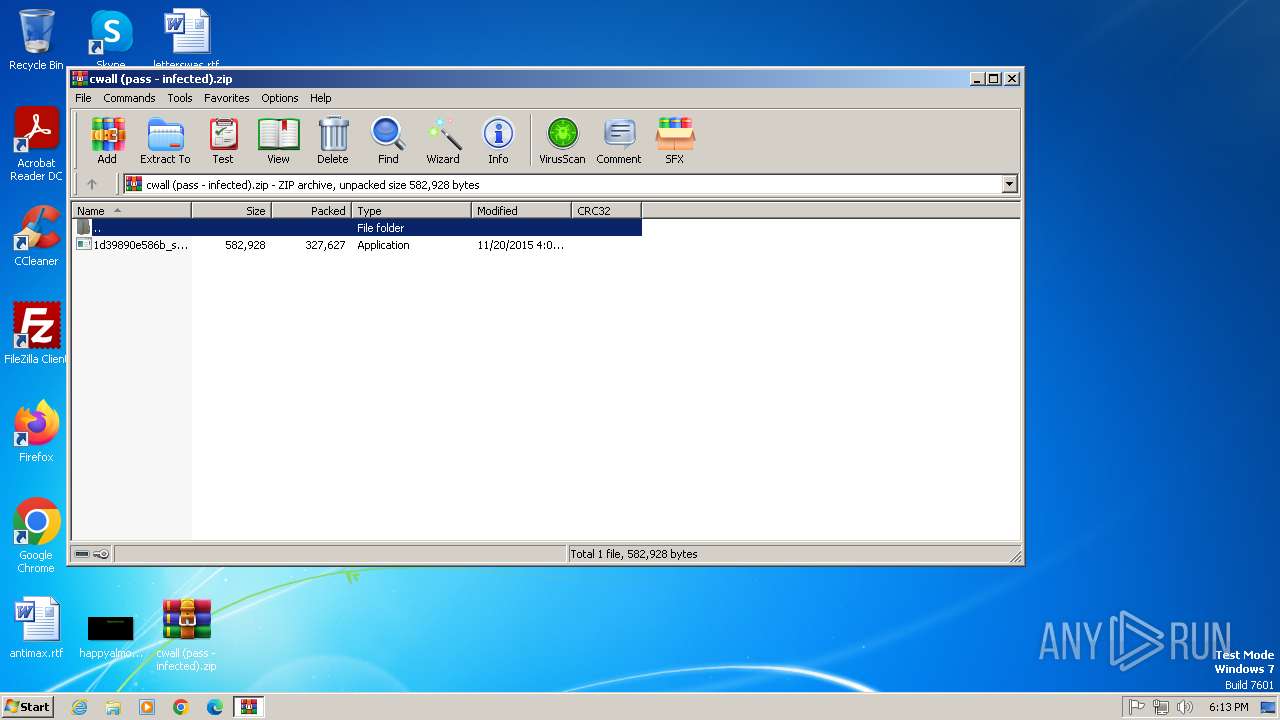
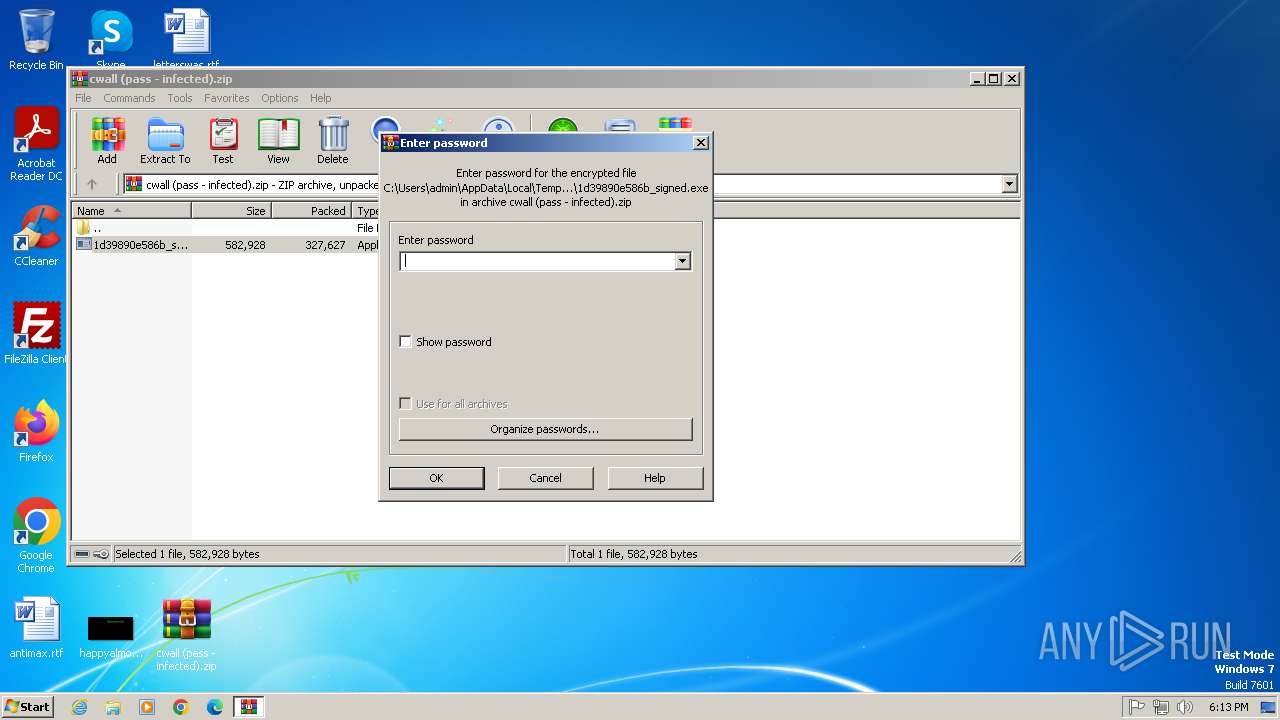
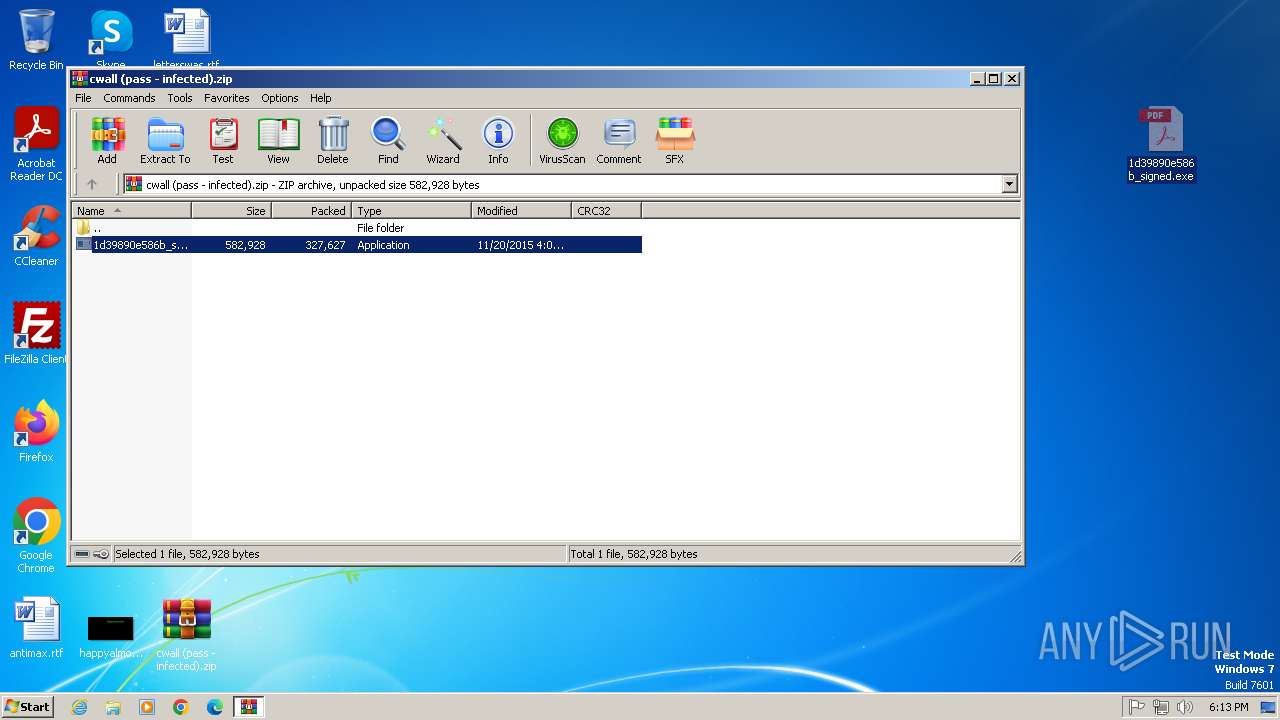
| File name: | cwall (pass - infected).zip |
| Full analysis: | https://app.any.run/tasks/4e976eab-821b-4a2f-b355-d38c0d72d768 |
| Verdict: | Malicious activity |
| Analysis date: | May 02, 2025, 17:13:42 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v5.1 to extract, compression method=AES Encrypted |
| MD5: | B279576EE4929D7CC3C73BCED39F3B71 |
| SHA1: | 1F6CC85951755A0A0FD50B60A6EC7357E58F6DC7 |
| SHA256: | B7C52716D6EDB1F22F6C2980A992263975D0F8A693A498AF45A5CF242C57DC73 |
| SSDEEP: | 12288:i3+daIoFcON+4iNzALvaxRhSxMk64TgVx7nBtjhMLYxEJ:i3vZFlN+4fLaxRhSxMk64TynBtjhMLYC |
MALICIOUS
Changes the autorun value in the registry
- explorer.exe (PID: 2516)
Deletes shadow copies
- explorer.exe (PID: 2516)
Disables Windows System Restore
- explorer.exe (PID: 2516)
SUSPICIOUS
Executable content was dropped or overwritten
- explorer.exe (PID: 2516)
Executes as Windows Service
- VSSVC.exe (PID: 988)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2840)
Creates files or folders in the user directory
- explorer.exe (PID: 2516)
Checks supported languages
- 1d39890e586b_signed.exe (PID: 3160)
Reads security settings of Internet Explorer
- svchost.exe (PID: 328)
Checks proxy server information
- svchost.exe (PID: 328)
Reads the machine GUID from the registry
- 1d39890e586b_signed.exe (PID: 3160)
Reads the computer name
- 1d39890e586b_signed.exe (PID: 3160)
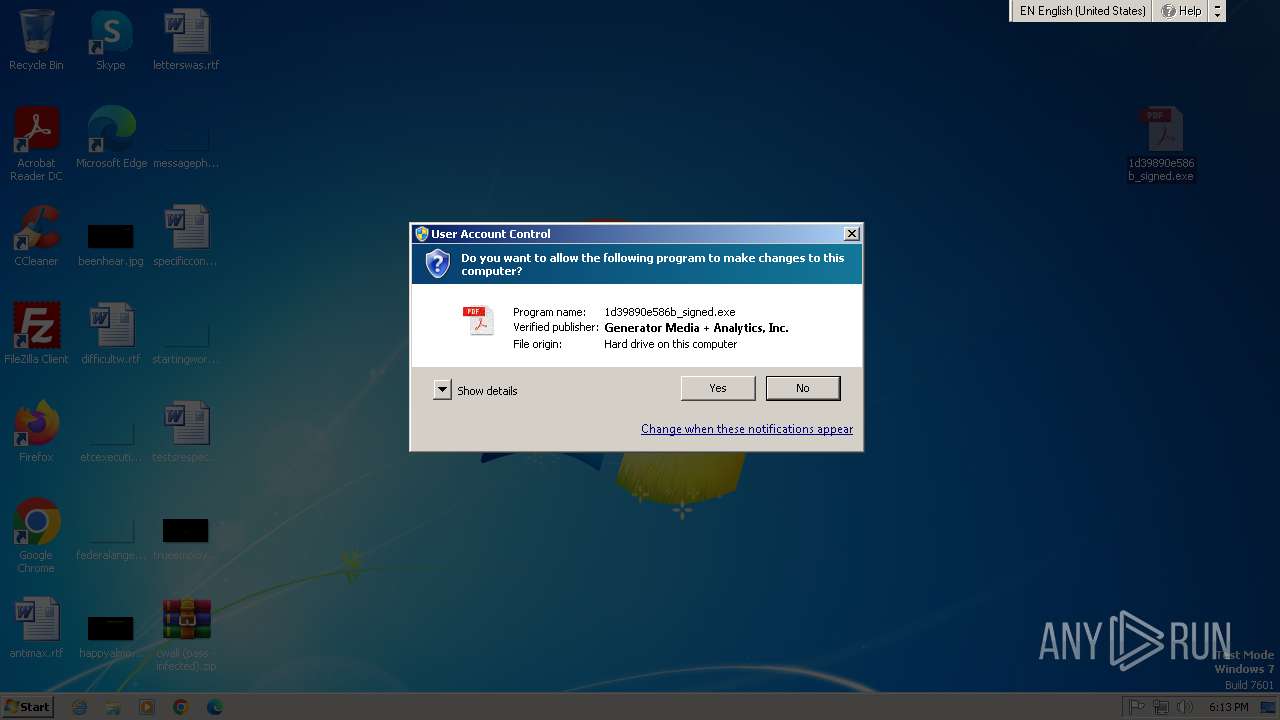
Manual execution by a user
- 1d39890e586b_signed.exe (PID: 3160)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 51 |
|---|---|
| ZipBitFlag: | 0x0001 |
| ZipCompression: | Unknown (99) |
| ZipModifyDate: | 2015:11:20 11:05:22 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | 327627 |
| ZipUncompressedSize: | 582928 |
| ZipFileName: | 1d39890e586b_signed.exe |
Total processes
47
Monitored processes
6
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 328 | -k netsvcs | C:\Windows\System32\svchost.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Host Process for Windows Services Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 988 | C:\Windows\system32\vssvc.exe | C:\Windows\System32\VSSVC.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Volume Shadow Copy Service Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2516 | "C:\Windows\explorer.exe" | C:\Windows\explorer.exe | 1d39890e586b_signed.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Explorer Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2840 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Desktop\cwall (pass - infected).zip" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 2940 | vssadmin.exe Delete Shadows /All /Quiet | C:\Windows\System32\vssadmin.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Command Line Interface for Microsoft® Volume Shadow Copy Service Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3160 | "C:\Users\admin\Desktop\1d39890e586b_signed.exe" | C:\Users\admin\Desktop\1d39890e586b_signed.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
Total events
21 055
Read events
16 964
Write events
4 079
Delete events
12
Modification events
| (PID) Process: | (2840) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (2840) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\cwall (pass - infected).zip | |||
| (PID) Process: | (2840) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2840) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2840) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2840) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2840) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2840) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2840) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2840) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
Executable files
2
Suspicious files
12
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2516 | explorer.exe | C:\Users\admin\AppData\Roaming\aed05aec2\428d7c7132.exe | executable | |
MD5:5DEE46F039CE190AD01456CE6FD11FBC | SHA256:1D39890E586BD3AF03BB31ED307AF378FBC58CC61FDDD9BBC4DE4FB738BB4D93 | |||
| 328 | svchost.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\92C56FD406FB7E3899926CC03EF0DC90 | binary | |
MD5:A279004CFD283AEDE3DE98B8552099AF | SHA256:E44213EAD7503DD2708C3C844A129D7F2882BA9FECB8D5BCA1D365F26811F5B7 | |||
| 2840 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb2840.33921\1d39890e586b_signed.exe | executable | |
MD5:5DEE46F039CE190AD01456CE6FD11FBC | SHA256:1D39890E586BD3AF03BB31ED307AF378FBC58CC61FDDD9BBC4DE4FB738BB4D93 | |||
| 328 | svchost.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | compressed | |
MD5:77B20B5CD41BC6BB475CCA3F91AE6E3C | SHA256:5511A9B9F9144ED7BDE4CCB074733B7C564D918D2A8B10D391AFC6BE5B3B1509 | |||
| 328 | svchost.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:29038C57A7DA51E47706A31441E897D0 | SHA256:2C912FED74C770325842FDECA41640FA8B8273FBD87E222001EADBB8B1A49738 | |||
| 328 | svchost.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\103621DE9CD5414CC2538780B4B75751 | binary | |
MD5:E192462F281446B5D1500D474FBACC4B | SHA256:F1BA9F1B63C447682EBF9DE956D0DA2A027B1B779ABEF9522D347D3479139A60 | |||
| 328 | svchost.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\103621DE9CD5414CC2538780B4B75751 | binary | |
MD5:894A78CDEFC826396A5E074CCF8B77A4 | SHA256:C10607C9184FB9C60601A9D54E6CD2D0169D01CA0C227F6C14DB4BBB23952023 | |||
| 328 | svchost.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\9C969A855026DC1B5F2B631F410872DE_A769FE5698012AC9AF35700392D15028 | binary | |
MD5:1C3D3C99341A58F6890644F6C61C2EFD | SHA256:B9A06E49CDDFA645EB7579F638677C787D4C78ADA78084C4A01817C6D31E26FA | |||
| 328 | svchost.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\92C56FD406FB7E3899926CC03EF0DC90 | binary | |
MD5:F2DEAEDE730F89B75346B41D0613FCFE | SHA256:D3DEFCFA05C38880EE32C7A27FAF13A4C8F1EABA5679CDACA81EB84BB4C3CE39 | |||
| 328 | svchost.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\E0090E0CC4617100153DB5DCE7955D84_3FCD5F6174F3F227F203168FC91623F1 | binary | |
MD5:26804E67D933C71A2FE28A2E475C598B | SHA256:7E5CE117422CD1BBB6B83EEDBC356B1AE0D38B69875AF68558540DB275F75871 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
14
TCP/UDP connections
24
DNS requests
22
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
328 | svchost.exe | POST | 301 | 212.84.168.97:80 | http://westburyim.com/wp-content/themes/twentyeleven/P8ND70.php?f=70z5mn3hpl | unknown | — | — | unknown |
328 | svchost.exe | GET | 200 | 69.192.161.44:80 | http://x1.c.lencr.org/ | unknown | — | — | whitelisted |
328 | svchost.exe | GET | 200 | 199.232.210.172:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?1839c5e9cb851190 | unknown | — | — | whitelisted |
328 | svchost.exe | GET | 200 | 184.24.77.56:80 | http://r10.o.lencr.org/MFMwUTBPME0wSzAJBgUrDgMCGgUABBRpD%2BQVZ%2B1vf7U0RGQGBm8JZwdxcgQUdKR2KRcYVIUxN75n5gZYwLzFBXICEgRYb9KAk5uT7ynucd40NFZQeA%3D%3D | unknown | — | — | whitelisted |
328 | svchost.exe | GET | 301 | 212.84.168.97:80 | http://westburyproperty.net/wp-content/themes/twentyeleven/P8ND70.php?f=70z5mn3hpl | unknown | — | — | unknown |
328 | svchost.exe | GET | 200 | 184.24.77.56:80 | http://r10.o.lencr.org/MFMwUTBPME0wSzAJBgUrDgMCGgUABBRpD%2BQVZ%2B1vf7U0RGQGBm8JZwdxcgQUdKR2KRcYVIUxN75n5gZYwLzFBXICEgVHbQ14lrmnPlOYO8PucXRrAg%3D%3D | unknown | — | — | whitelisted |
328 | svchost.exe | POST | 404 | 213.249.67.10:80 | http://sofiaki.com/wp-content/plugins/wp-db-backup-made/pZ_cus.php?t=70z5mn3hpl | unknown | — | — | unknown |
328 | svchost.exe | POST | 301 | 213.171.164.42:80 | http://factotum.it/wp-content/plugins/wp-db-backup-made1/GBo9mq.php?w=70z5mn3hpl | unknown | — | — | unknown |
328 | svchost.exe | GET | 200 | 184.24.77.79:80 | http://r11.o.lencr.org/MFMwUTBPME0wSzAJBgUrDgMCGgUABBQaUrm0WeTDM5ghfoZtS72KO9ZnzgQUCLkRO6XQhRi06g%2BgrZ%2BGHo78OCcCEgVFLMjXJS1fLgE3Z1yE%2FFQoCg%3D%3D | unknown | — | — | whitelisted |
328 | svchost.exe | POST | 409 | 141.193.213.11:80 | http://cmc-photo.com/wp-content/plugins/wp-db-backup-made/9WZ082.php?q=70z5mn3hpl | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
328 | svchost.exe | 212.84.168.97:80 | westburyim.com | Iomart Cloud Services Limited | GB | unknown |
328 | svchost.exe | 212.84.168.97:443 | westburyim.com | Iomart Cloud Services Limited | GB | unknown |
328 | svchost.exe | 199.232.210.172:80 | ctldl.windowsupdate.com | FASTLY | US | whitelisted |
328 | svchost.exe | 69.192.161.44:80 | x1.c.lencr.org | AKAMAI-AS | DE | whitelisted |
328 | svchost.exe | 184.24.77.56:80 | r10.o.lencr.org | Akamai International B.V. | DE | whitelisted |
328 | svchost.exe | 213.249.67.10:80 | sofiaki.com | Metaregistrar B.V. | NL | unknown |
328 | svchost.exe | 213.171.164.42:80 | factotum.it | SEEWEB s.r.l. | IT | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
squashacademy.ro |
| unknown |
westburyim.com |
| unknown |
ctldl.windowsupdate.com |
| whitelisted |
x1.c.lencr.org |
| whitelisted |
r10.o.lencr.org |
| whitelisted |
westburyproperty.net |
| unknown |
sofiaki.com |
| unknown |
cpd4adi.com |
| unknown |
weblaboratory.org |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
328 | svchost.exe | Potentially Bad Traffic | ET INFO HTTP POST to WP Theme Directory Without Referer |