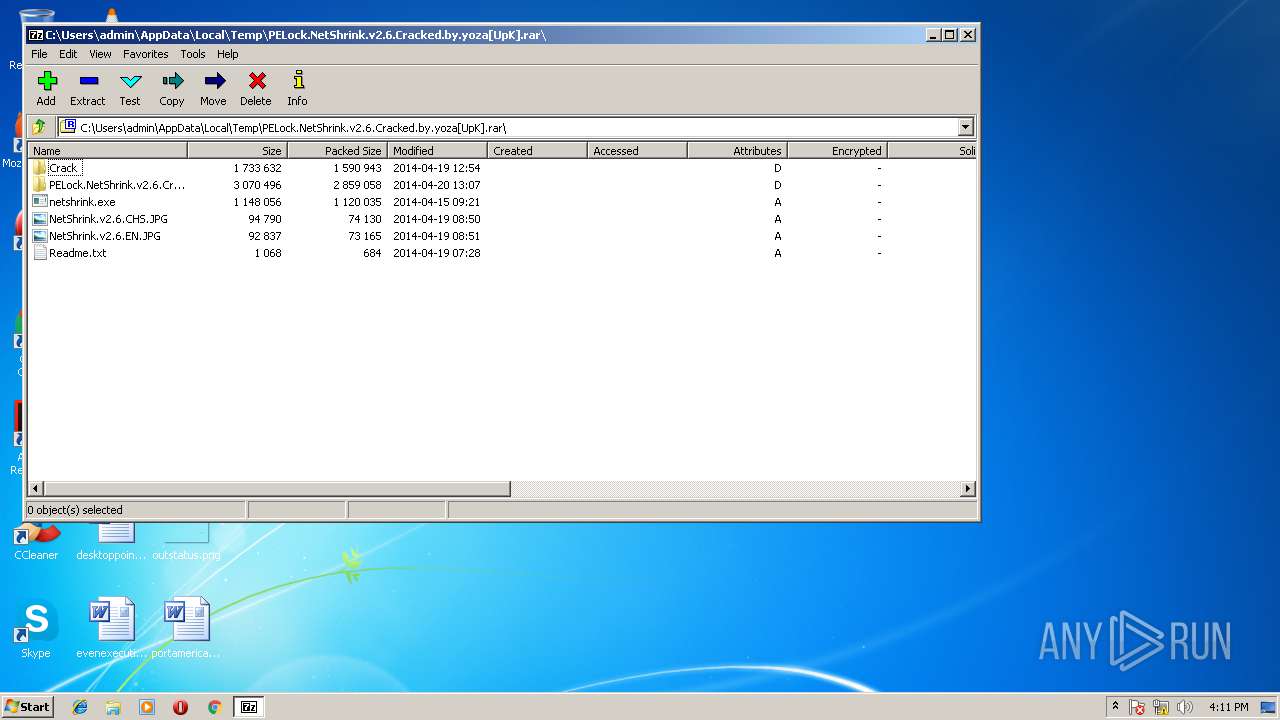
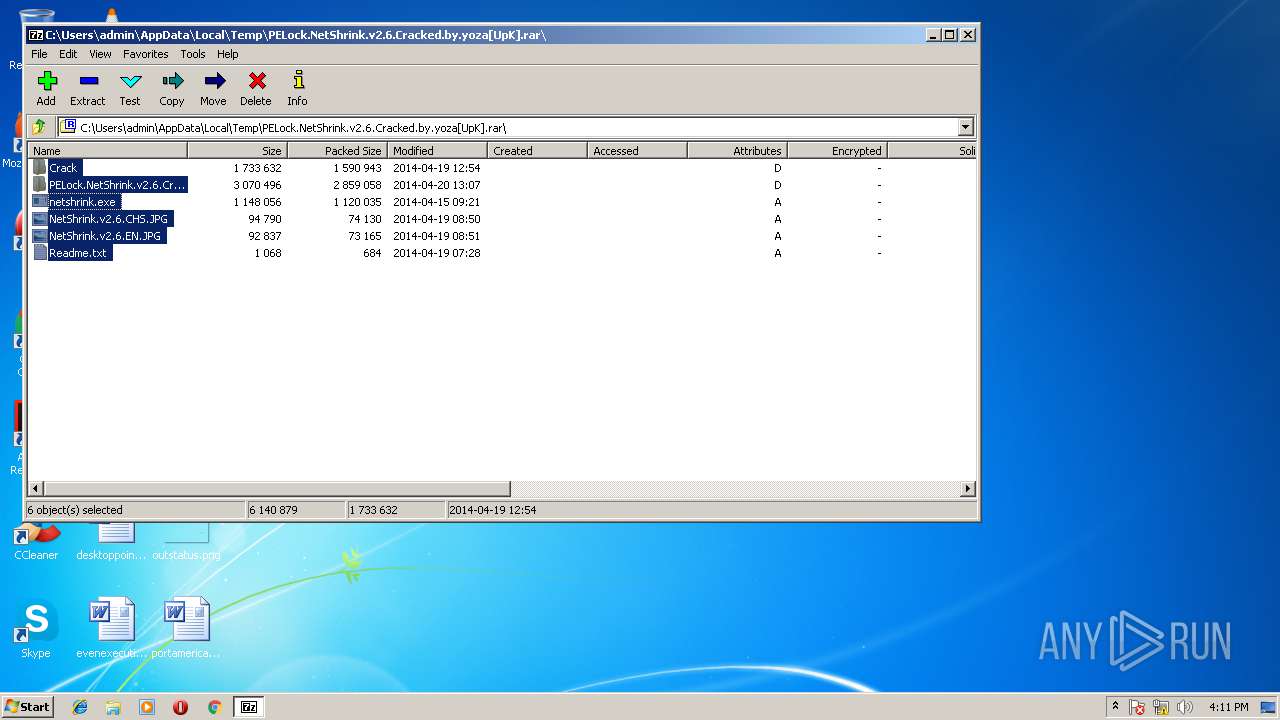
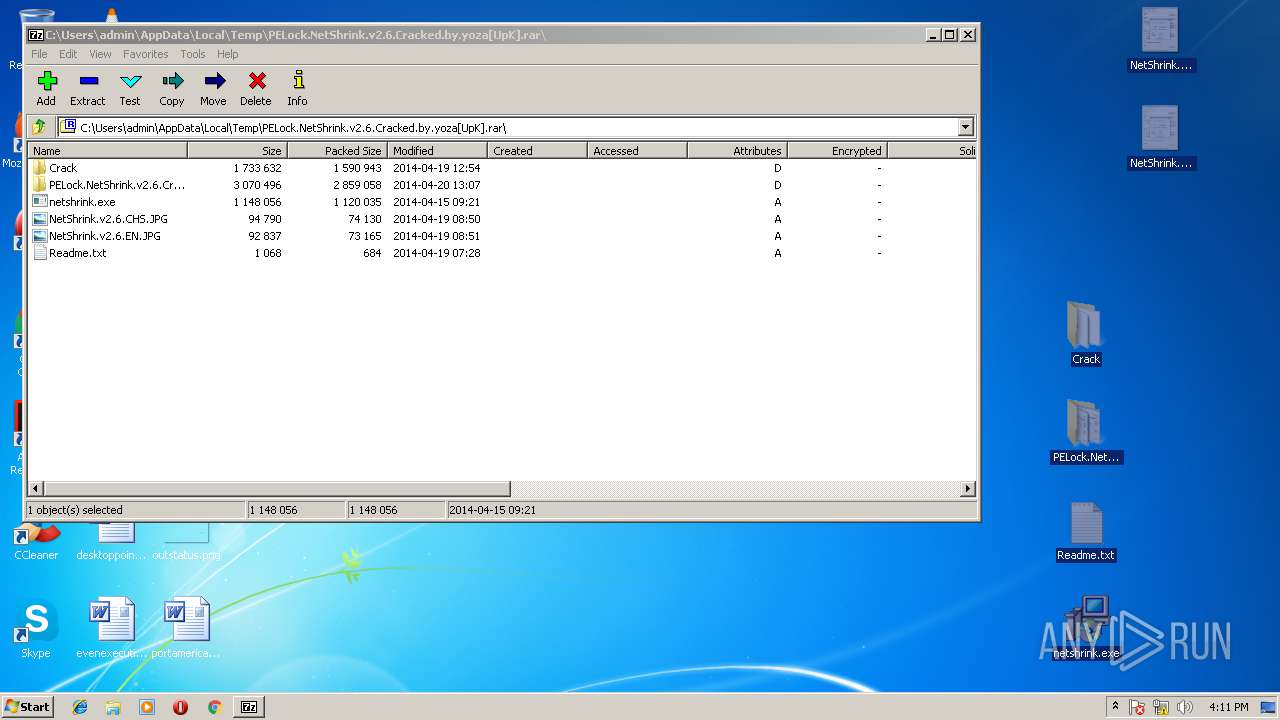
| File name: | PELock.NetShrink.v2.6.Cracked.by.yoza[UpK].rar |
| Full analysis: | https://app.any.run/tasks/0f9e66d5-5294-4e22-b9d6-4faf4159c7f1 |
| Verdict: | Malicious activity |
| Analysis date: | March 26, 2018, 15:10:59 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v4, os: Win32 |
| MD5: | 3C8C3AD35A6BC64BECDFC64123AAC220 |
| SHA1: | 24198ED771FD15477E3C41A11F1300F3A3C250C1 |
| SHA256: | B7BB450F7C1C619D6F853F9646F5E30C2C4E8204CD8B6503493E83126DC5362D |
| SSDEEP: | 98304:INli6cesrbMHAhDNazlCwBLnMNyQNli6XesrbMCAhDNazlCwBLnMcFl:kliVJrbJNaJNkLliEJrbuNaJNjl |
MALICIOUS
Application was dropped or rewritten from another process
- netshrink.exe (PID: 2448)
- netshrink.exe (PID: 2264)
- netshrink.exe (PID: 3948)
- Netshrink.CHS.exe (PID: 2512)
- Netshrink.exe (PID: 4004)
SUSPICIOUS
Modifies the open verb of a shell class
- netshrink.tmp (PID: 2672)
Creates a software uninstall entry
- netshrink.tmp (PID: 2672)
INFO
Dropped object may contain URL's
- netshrink.exe (PID: 2448)
- netshrink.exe (PID: 2264)
- netshrink.exe (PID: 3948)
- netshrink.tmp (PID: 2672)
Application was dropped or rewritten from another process
- netshrink.tmp (PID: 3140)
- netshrink.tmp (PID: 2672)
Application loaded dropped or rewritten executable
- netshrink.tmp (PID: 2672)
Creates files in the program directory
- netshrink.tmp (PID: 2672)
Loads the .NET runtime environment
- netshrink.exe (PID: 3948)
- Netshrink.exe (PID: 4004)
- Netshrink.CHS.exe (PID: 2512)
Loads rich edit control libraries
- netshrink.exe (PID: 3948)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v-4.x) (58.3) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (41.6) |
EXIF
ZIP
| CompressedSize: | 720 |
|---|---|
| UncompressedSize: | 1068 |
| OperatingSystem: | Win32 |
| ModifyDate: | 2014:04:19 07:28:14 |
| PackingMethod: | Normal |
| ArchivedFileName: | Readme.txt |
Total processes
45
Monitored processes
8
Malicious processes
4
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
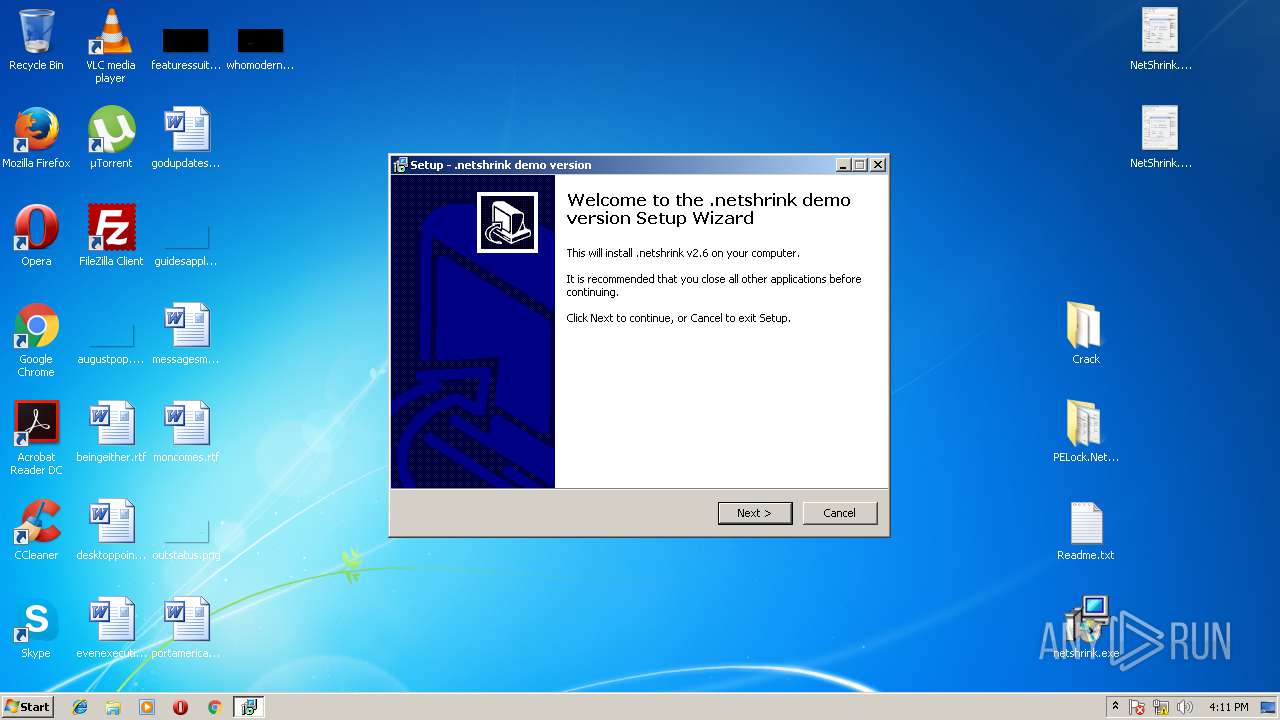
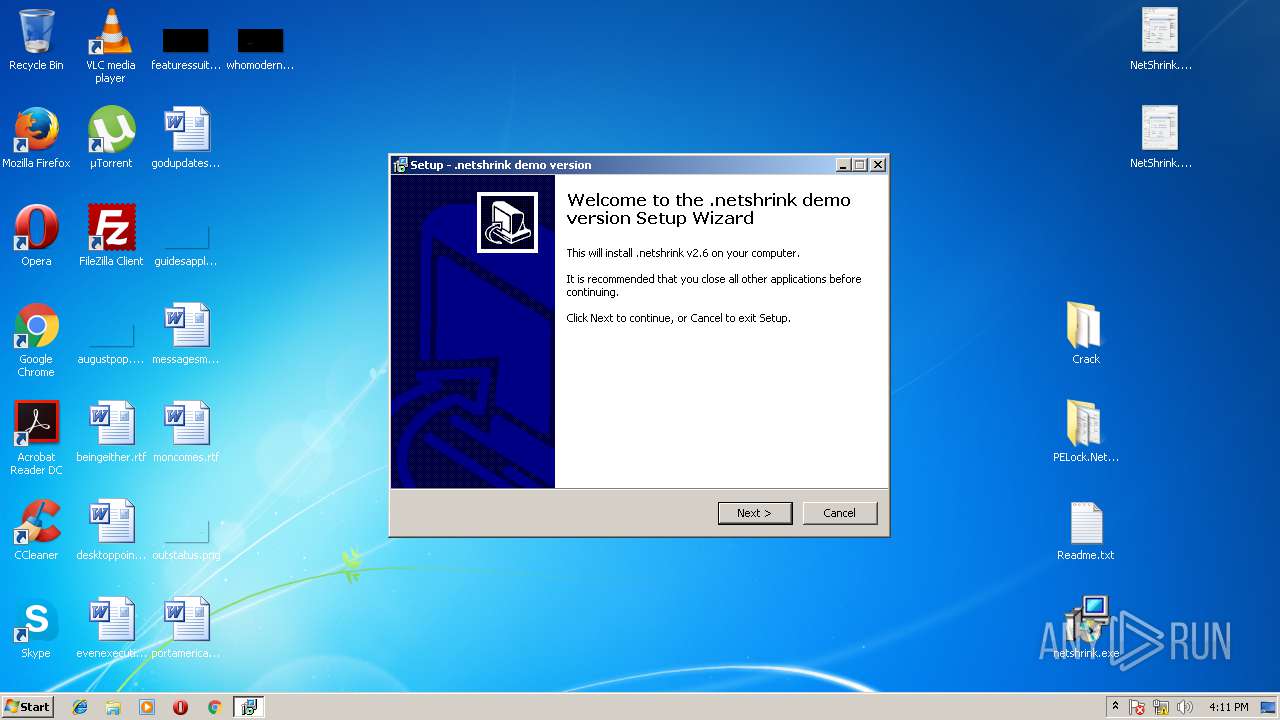
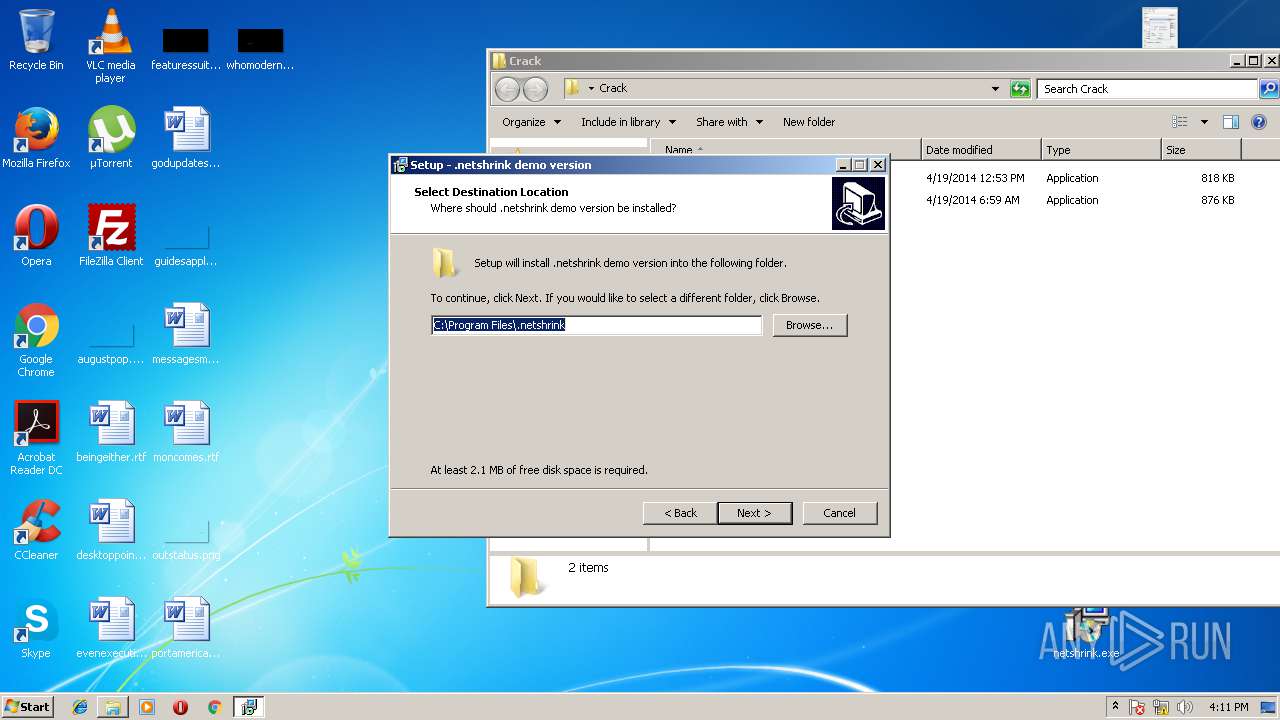
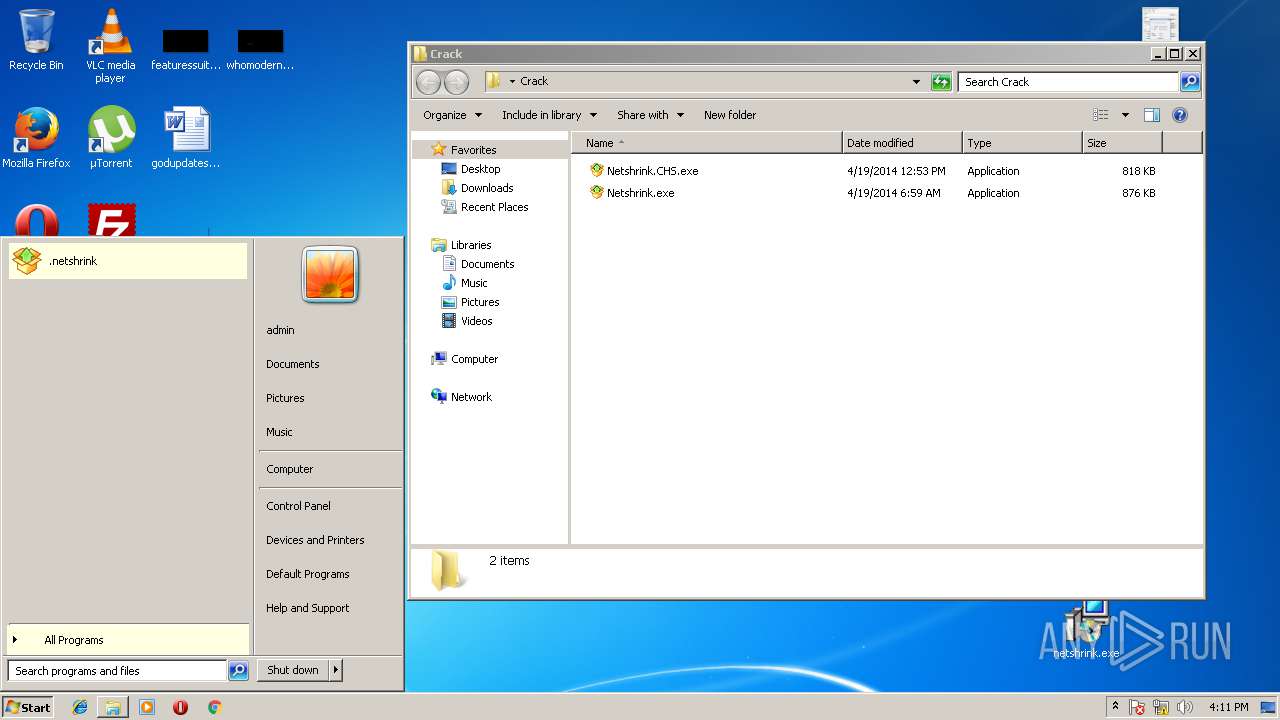
| 2264 | "C:\Users\admin\Desktop\netshrink.exe" /SPAWNWND=$9014C /NOTIFYWND=$A015A | C:\Users\admin\Desktop\netshrink.exe | netshrink.tmp | ||||||||||||
User: admin Company: Bartosz Wójcik Integrity Level: HIGH Description: .netshrink demo version Setup Exit code: 0 Version: Modules
| |||||||||||||||
| 2448 | "C:\Users\admin\Desktop\netshrink.exe" | C:\Users\admin\Desktop\netshrink.exe | explorer.exe | ||||||||||||
User: admin Company: Bartosz Wójcik Integrity Level: MEDIUM Description: .netshrink demo version Setup Exit code: 0 Version: Modules
| |||||||||||||||
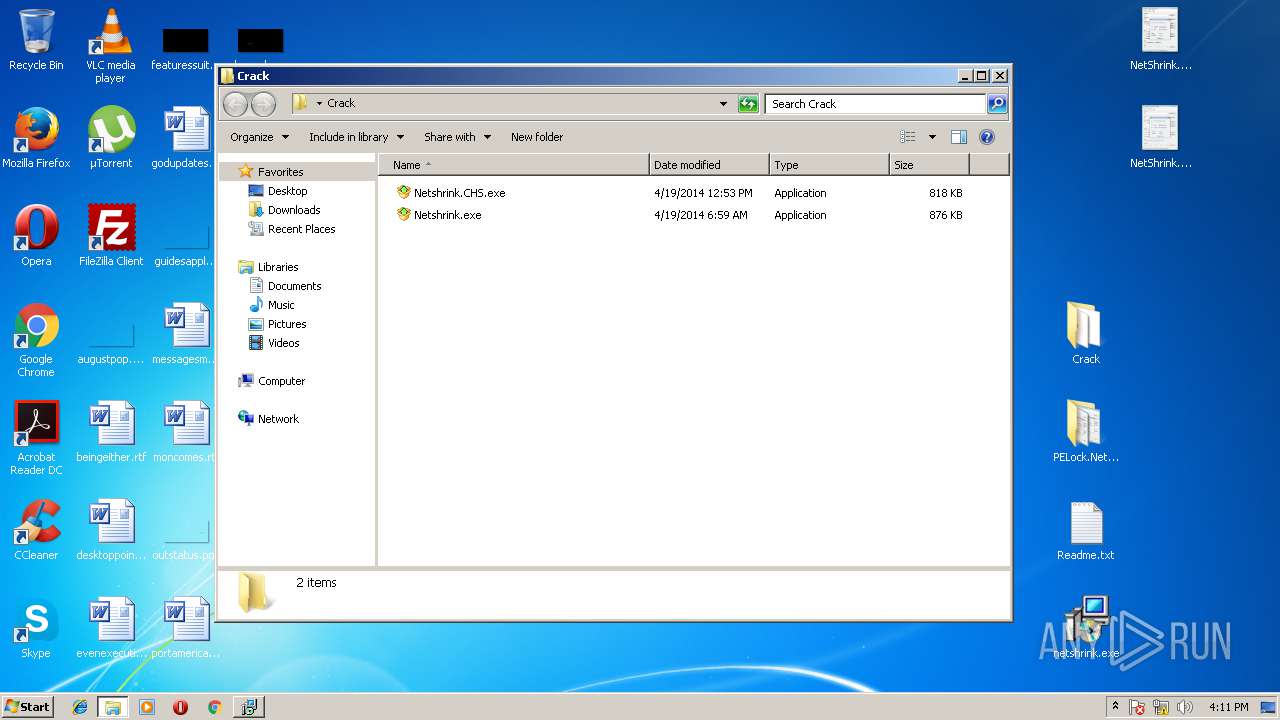
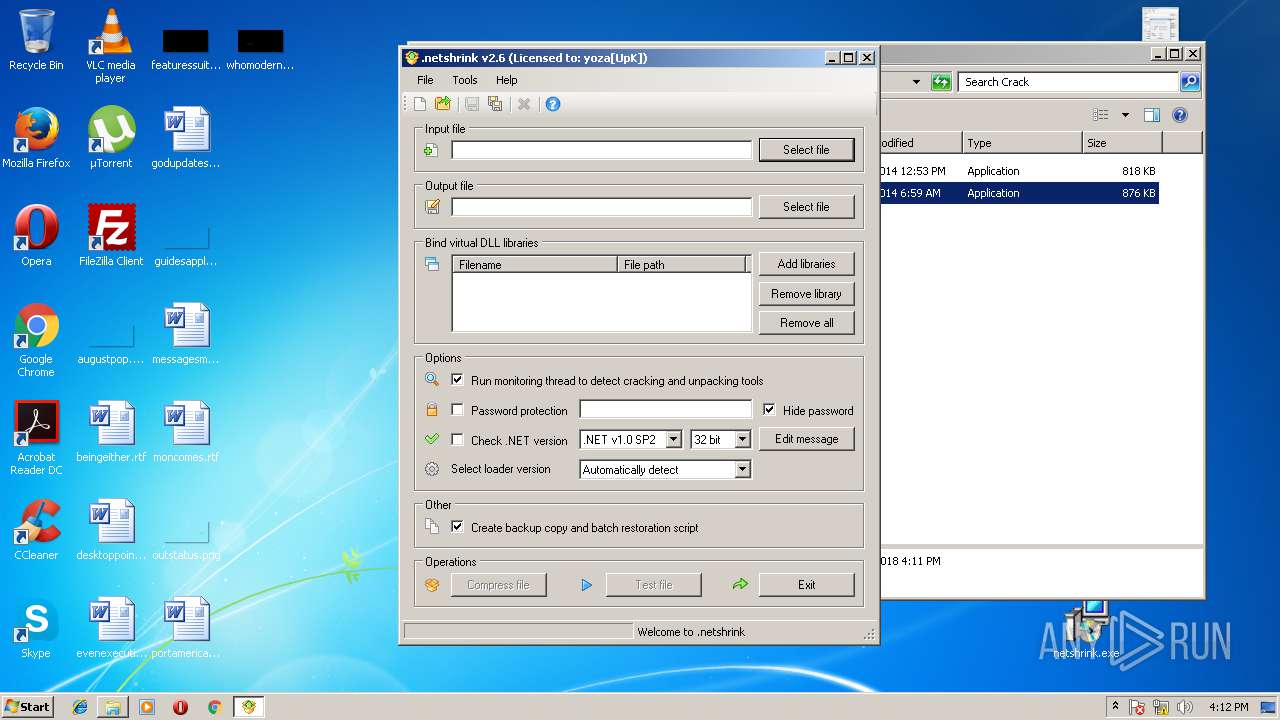
| 2512 | "C:\Users\admin\Desktop\Crack\Netshrink.CHS.exe" | C:\Users\admin\Desktop\Crack\Netshrink.CHS.exe | — | explorer.exe | |||||||||||
User: admin Company: PELock Software Integrity Level: MEDIUM Description: .netshrink exe compressor Exit code: 0 Version: 2.6.0.0 Modules
| |||||||||||||||
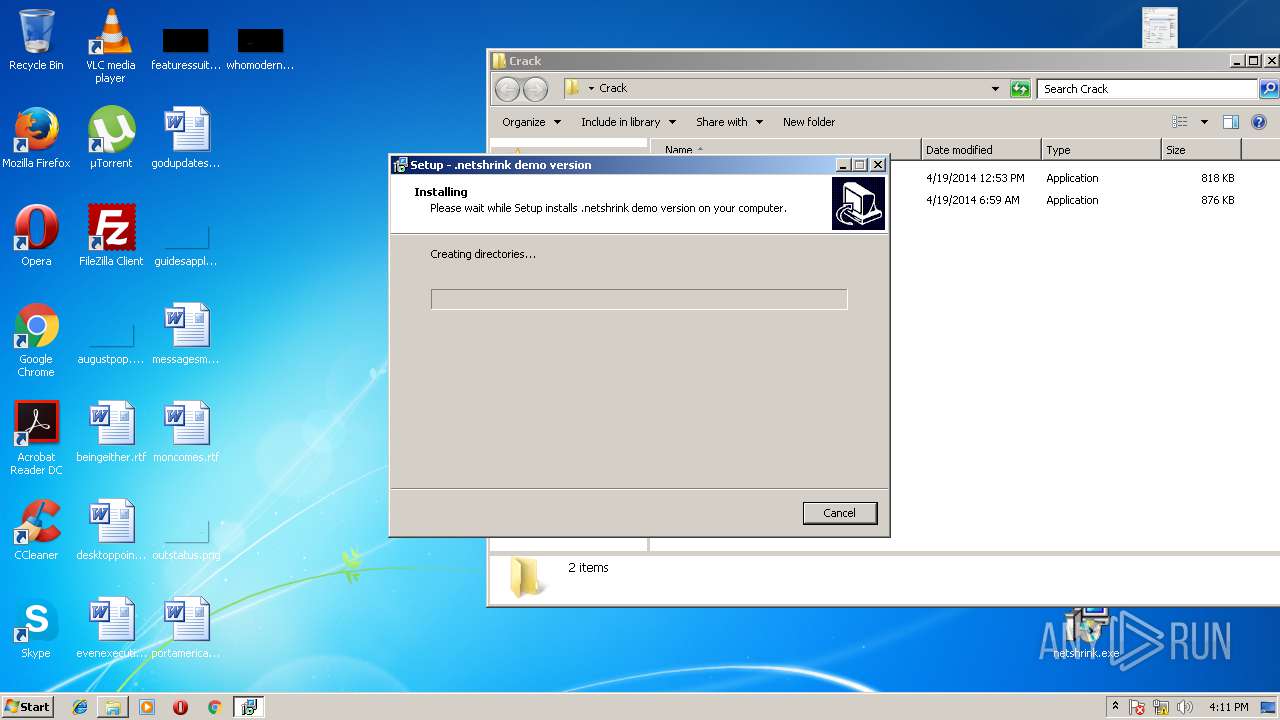
| 2672 | "C:\Users\admin\AppData\Local\Temp\is-SLSSE.tmp\netshrink.tmp" /SL5="$A0158,890955,56832,C:\Users\admin\Desktop\netshrink.exe" /SPAWNWND=$9014C /NOTIFYWND=$A015A | C:\Users\admin\AppData\Local\Temp\is-SLSSE.tmp\netshrink.tmp | netshrink.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Setup/Uninstall Exit code: 0 Version: 51.52.0.0 Modules
| |||||||||||||||
| 2868 | "C:\Program Files\7-Zip\7zFM.exe" "C:\Users\admin\AppData\Local\Temp\PELock.NetShrink.v2.6.Cracked.by.yoza[UpK].rar" | C:\Program Files\7-Zip\7zFM.exe | — | explorer.exe | |||||||||||
User: admin Company: Igor Pavlov Integrity Level: MEDIUM Description: 7-Zip File Manager Exit code: 0 Version: 16.04 Modules
| |||||||||||||||
| 3140 | "C:\Users\admin\AppData\Local\Temp\is-MH7QP.tmp\netshrink.tmp" /SL5="$A015A,890955,56832,C:\Users\admin\Desktop\netshrink.exe" | C:\Users\admin\AppData\Local\Temp\is-MH7QP.tmp\netshrink.tmp | — | netshrink.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Setup/Uninstall Exit code: 0 Version: 51.52.0.0 Modules
| |||||||||||||||
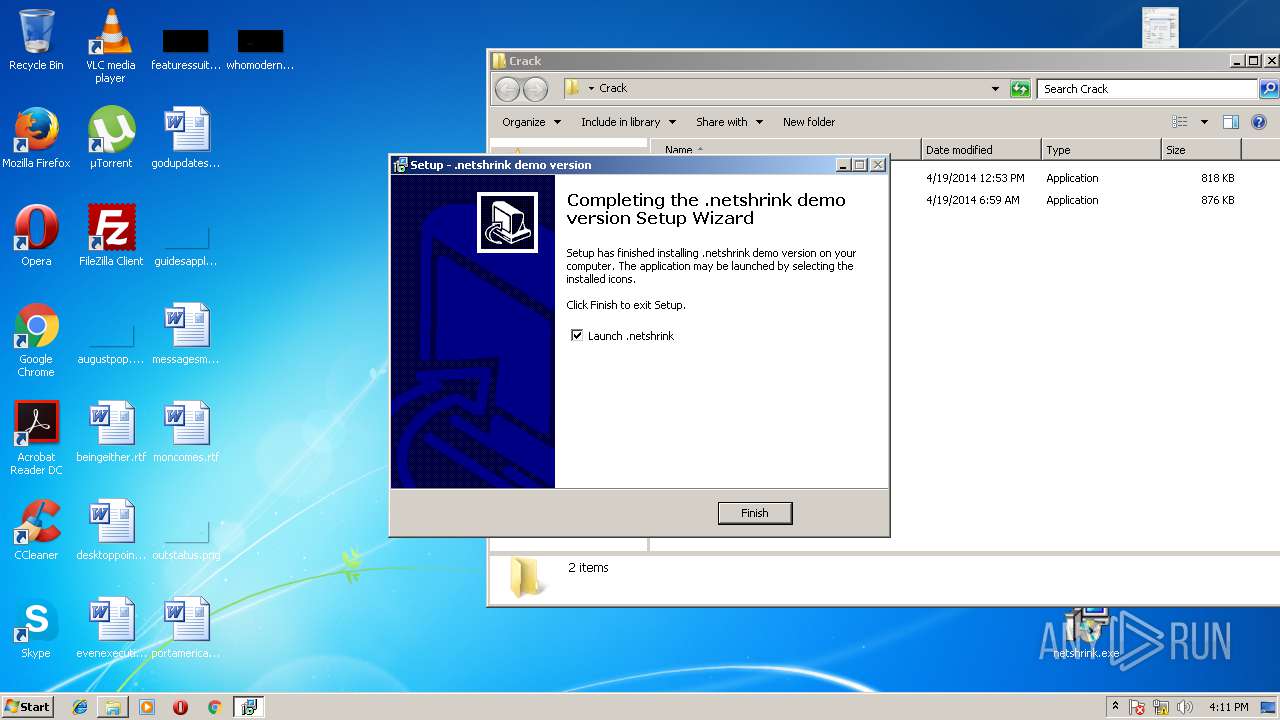
| 3948 | "C:\Program Files\.netshrink\netshrink.exe" | C:\Program Files\.netshrink\netshrink.exe | — | netshrink.tmp | |||||||||||
User: admin Company: PELock Software Integrity Level: MEDIUM Description: .netshrink exe compressor Exit code: 0 Version: 2.6.0.0 Modules
| |||||||||||||||
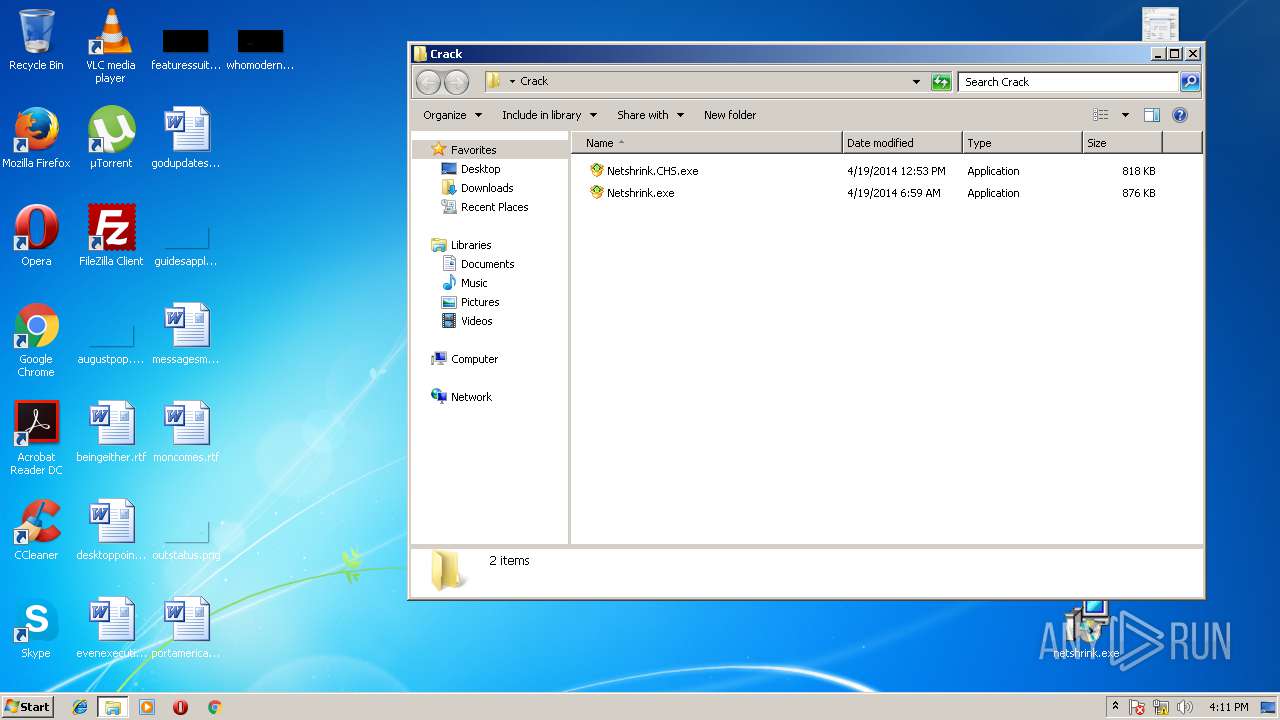
| 4004 | "C:\Users\admin\Desktop\Crack\Netshrink.exe" | C:\Users\admin\Desktop\Crack\Netshrink.exe | — | explorer.exe | |||||||||||
User: admin Company: PELock Software Integrity Level: MEDIUM Description: .netshrink exe compressor Exit code: 0 Version: 2.6.0.0 Modules
| |||||||||||||||
Total events
319
Read events
245
Write events
68
Delete events
6
Modification events
| (PID) Process: | (2868) 7zFM.exe | Key: | HKEY_CURRENT_USER\Software\7-Zip\FM |
| Operation: | write | Name: | FolderShortcuts |
Value: | |||
| (PID) Process: | (2868) 7zFM.exe | Key: | HKEY_CURRENT_USER\Software\7-Zip\FM |
| Operation: | write | Name: | FolderHistory |
Value: 43003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C004C006F00630061006C005C00540065006D0070005C00500045004C006F0063006B002E004E006500740053006800720069006E006B002E00760032002E0036002E0043007200610063006B00650064002E00620079002E0079006F007A0061005B00550070004B005D002E007200610072005C000000 | |||
| (PID) Process: | (2868) 7zFM.exe | Key: | HKEY_CURRENT_USER\Software\7-Zip\FM |
| Operation: | write | Name: | PanelPath0 |
Value: C:\Users\admin\AppData\Local\Temp\ | |||
| (PID) Process: | (2868) 7zFM.exe | Key: | HKEY_CURRENT_USER\Software\7-Zip\FM |
| Operation: | write | Name: | FlatViewArc0 |
Value: 0 | |||
| (PID) Process: | (2868) 7zFM.exe | Key: | HKEY_CURRENT_USER\Software\7-Zip\FM |
| Operation: | write | Name: | PanelPath1 |
Value: | |||
| (PID) Process: | (2868) 7zFM.exe | Key: | HKEY_CURRENT_USER\Software\7-Zip\FM |
| Operation: | write | Name: | FlatViewArc1 |
Value: 0 | |||
| (PID) Process: | (2868) 7zFM.exe | Key: | HKEY_CURRENT_USER\Software\7-Zip\FM |
| Operation: | write | Name: | ListMode |
Value: 771 | |||
| (PID) Process: | (2868) 7zFM.exe | Key: | HKEY_CURRENT_USER\Software\7-Zip\FM |
| Operation: | write | Name: | Position |
Value: 1600000016000000D60300000B02000000000000 | |||
| (PID) Process: | (2868) 7zFM.exe | Key: | HKEY_CURRENT_USER\Software\7-Zip\FM |
| Operation: | write | Name: | Panels |
Value: 0100000000000000DA010000 | |||
| (PID) Process: | (2868) 7zFM.exe | Key: | HKEY_CURRENT_USER\Software\7-Zip\FM\Columns |
| Operation: | write | Name: | 7-Zip.Rar |
Value: 0100000004000000010000000400000001000000A00000000700000001000000640000000800000001000000640000000C00000001000000640000000A00000001000000640000000B00000001000000640000000900000001000000640000000F00000001000000640000000D00000001000000640000000E00000001000000640000001000000001000000640000001100000001000000640000001300000001000000640000001700000001000000640000001600000001000000640000002100000001000000640000001F0000000100000064000000200000000100000064000000 | |||
Executable files
5
Suspicious files
8
Text files
2
Unknown types
10
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2868 | 7zFM.exe | C:\Users\admin\AppData\Local\Temp\7zE43B7C7F5\Readme.txt | — | |
MD5:— | SHA256:— | |||
| 2868 | 7zFM.exe | C:\Users\admin\AppData\Local\Temp\7zE43B7C7F5\Crack\Netshrink.CHS.exe | — | |
MD5:— | SHA256:— | |||
| 2868 | 7zFM.exe | C:\Users\admin\AppData\Local\Temp\7zE43B7C7F5\Crack\Netshrink.exe | — | |
MD5:— | SHA256:— | |||
| 2868 | 7zFM.exe | C:\Users\admin\AppData\Local\Temp\7zE43B7C7F5\netshrink.exe | — | |
MD5:— | SHA256:— | |||
| 2868 | 7zFM.exe | C:\Users\admin\AppData\Local\Temp\7zE43B7C7F5\NetShrink.v2.6.EN.JPG | — | |
MD5:— | SHA256:— | |||
| 2868 | 7zFM.exe | C:\Users\admin\AppData\Local\Temp\7zE43B7C7F5\NetShrink.v2.6.CHS.JPG | — | |
MD5:— | SHA256:— | |||
| 2868 | 7zFM.exe | C:\Users\admin\AppData\Local\Temp\7zE43B7C7F5\PELock.NetShrink.v2.6.Cracked.by.yoza[UpK]\Crack\Netshrink.CHS.exe | — | |
MD5:— | SHA256:— | |||
| 2868 | 7zFM.exe | C:\Users\admin\AppData\Local\Temp\7zE43B7C7F5\PELock.NetShrink.v2.6.Cracked.by.yoza[UpK]\Crack\Netshrink.exe | — | |
MD5:— | SHA256:— | |||
| 2868 | 7zFM.exe | C:\Users\admin\AppData\Local\Temp\7zE43B7C7F5\PELock.NetShrink.v2.6.Cracked.by.yoza[UpK]\LeVeL-23.Cc.url | — | |
MD5:— | SHA256:— | |||
| 2868 | 7zFM.exe | C:\Users\admin\AppData\Local\Temp\7zE43B7C7F5\PELock.NetShrink.v2.6.Cracked.by.yoza[UpK]\netshrink.exe | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
3
DNS requests
3
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 304 | 2.21.246.10:80 | http://www.download.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab | AT | — | — | whitelisted |
— | — | GET | 200 | 104.192.110.244:80 | http://www.startssl.com/sfsca.crl | US | der | 952 b | whitelisted |
— | — | GET | 200 | 104.192.110.244:80 | http://www.startssl.com/sfsca.crt | US | der | 1.95 Kb | whitelisted |
— | — | GET | 200 | 2.21.246.58:80 | http://ocsp.startssl.com/sub/class2/code/ca/MEMwQTA%2FMD0wOzAJBgUrDgMCGgUABBQSOgrhRCSnWfKxoWTjWxhk8hga9AQU0E4PQJlsuEsZbzsouODjiAc0qrcCAgoN | AT | der | 1.65 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 2.21.246.58:80 | ocsp.startssl.com | Akamai International B.V. | AT | whitelisted |
— | — | 2.21.246.10:80 | www.download.windowsupdate.com | Akamai International B.V. | AT | whitelisted |
— | — | 104.192.110.244:80 | www.startssl.com | Beijing Qihu Technology Company Limited | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.startssl.com |
| whitelisted |
www.download.windowsupdate.com |
| whitelisted |
ocsp.startssl.com |
| whitelisted |