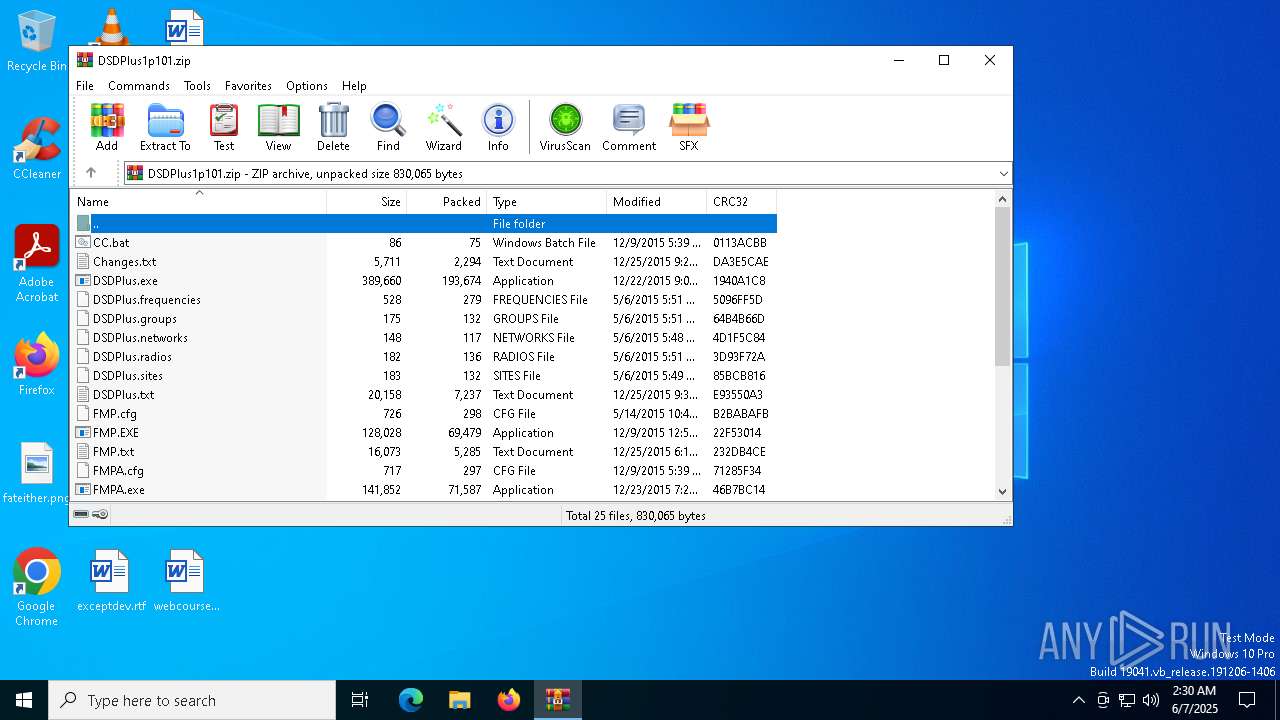
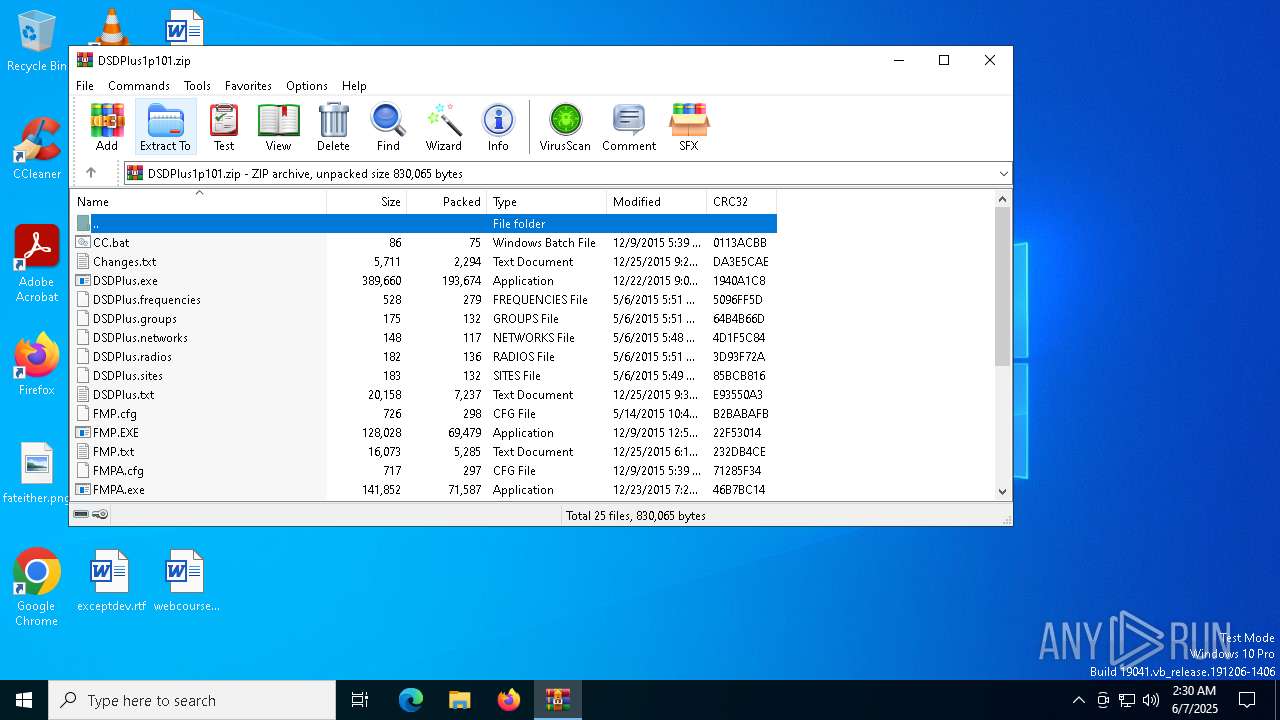
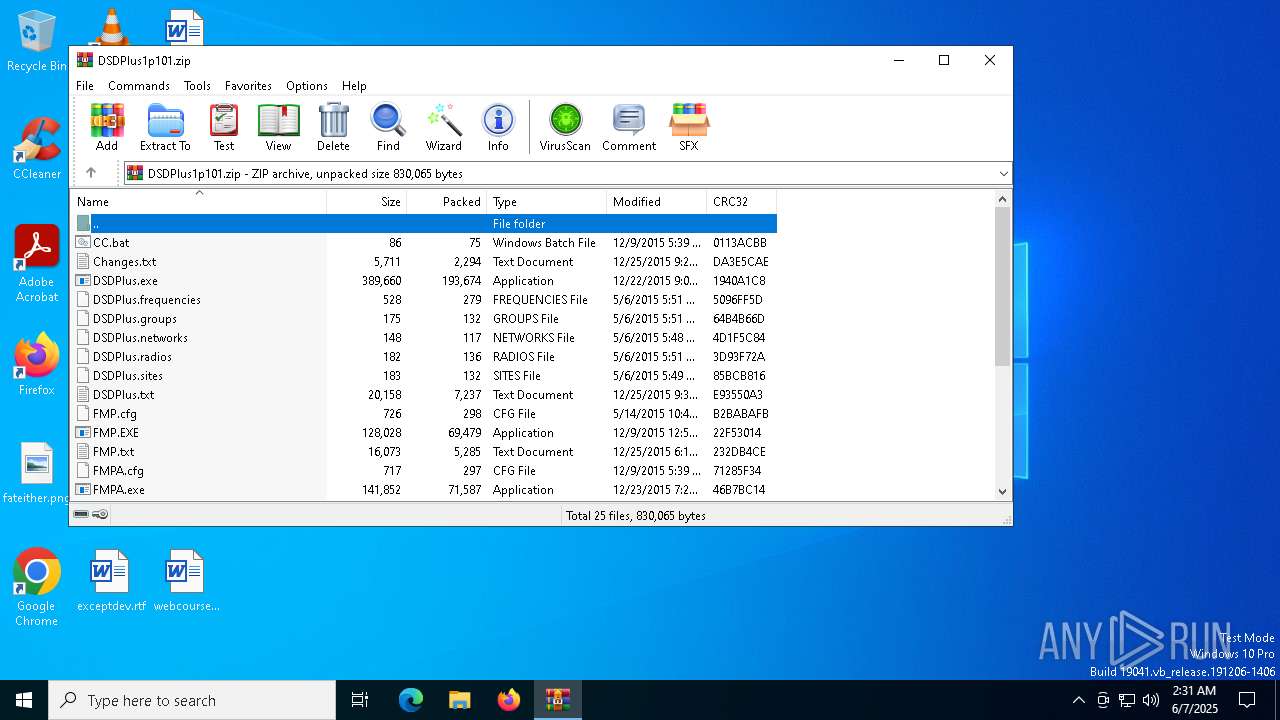
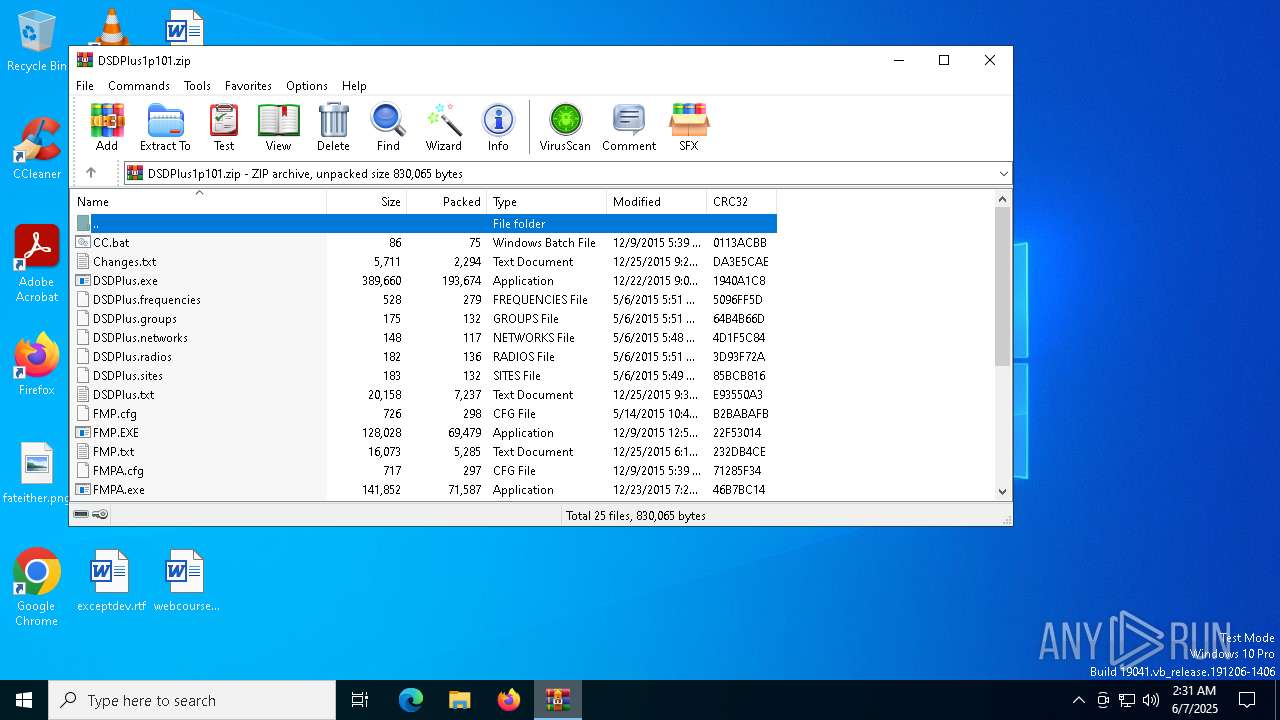
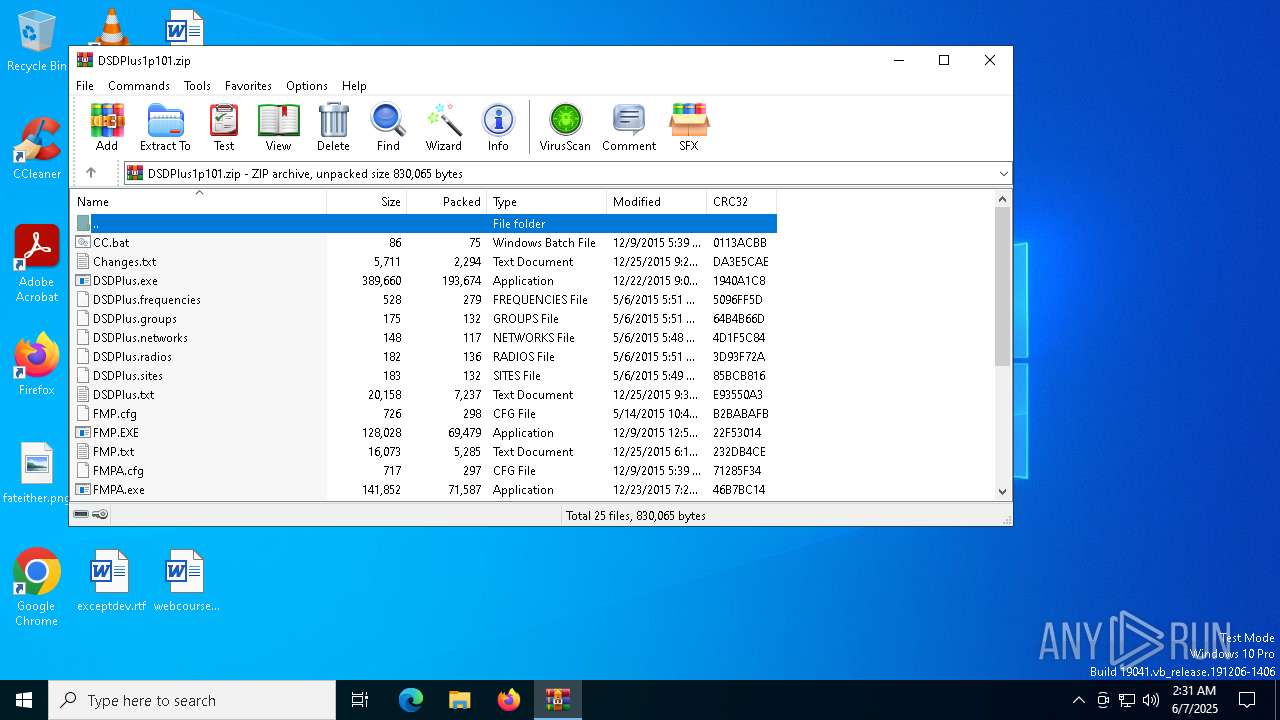
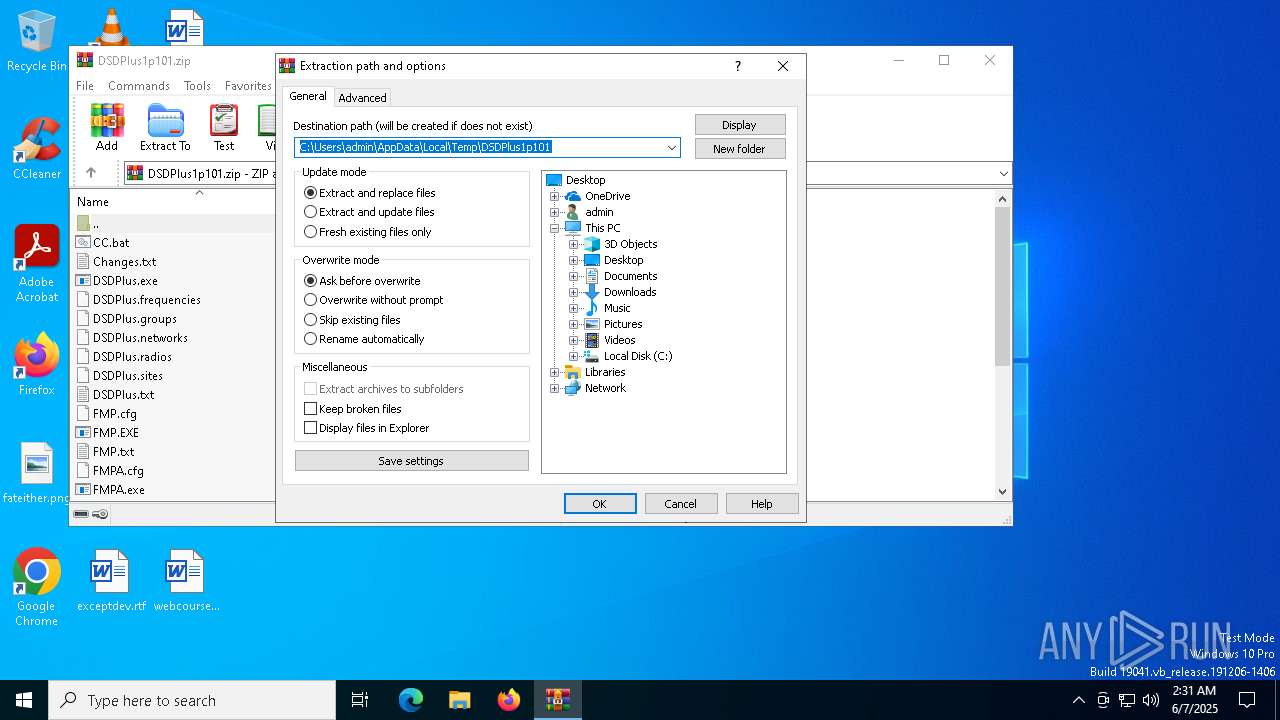
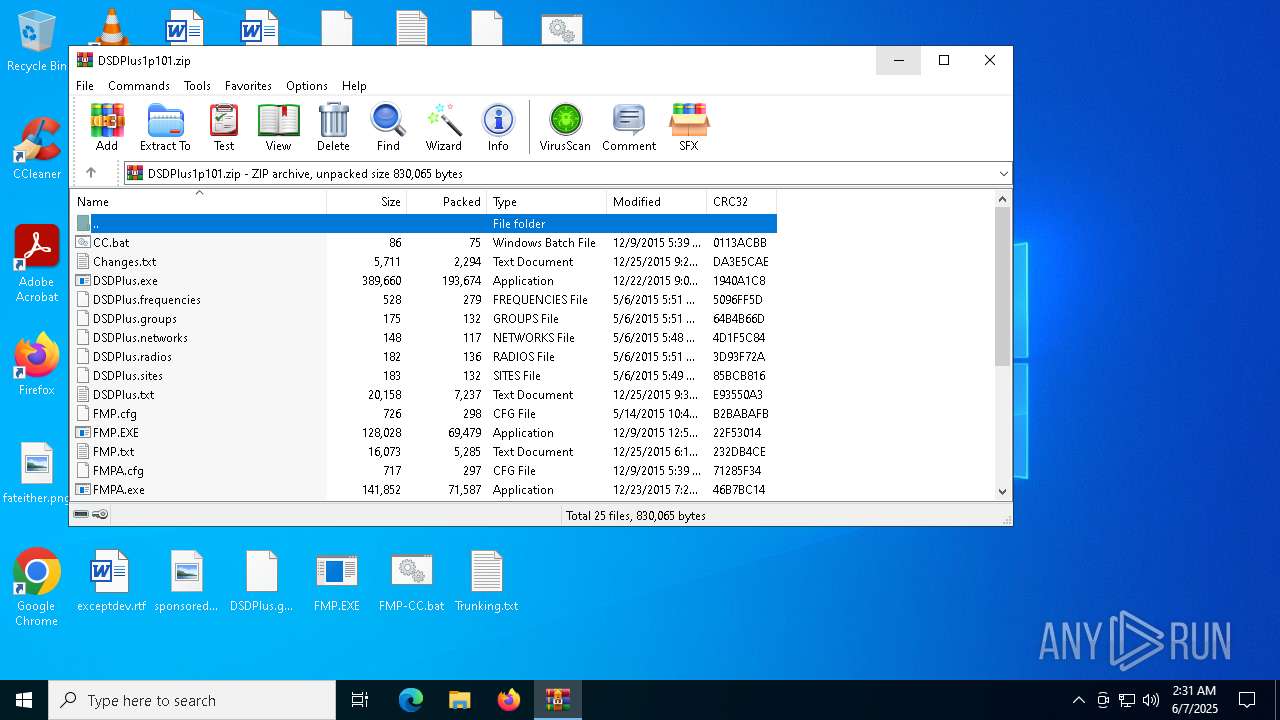
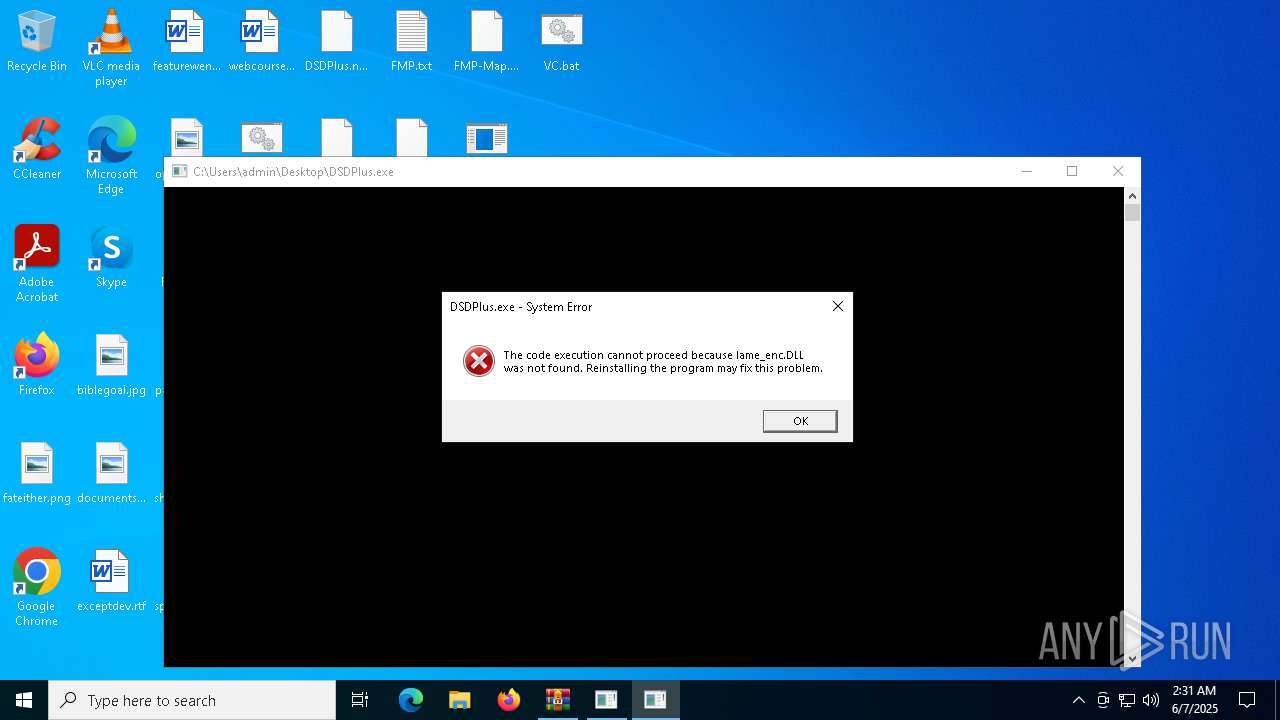
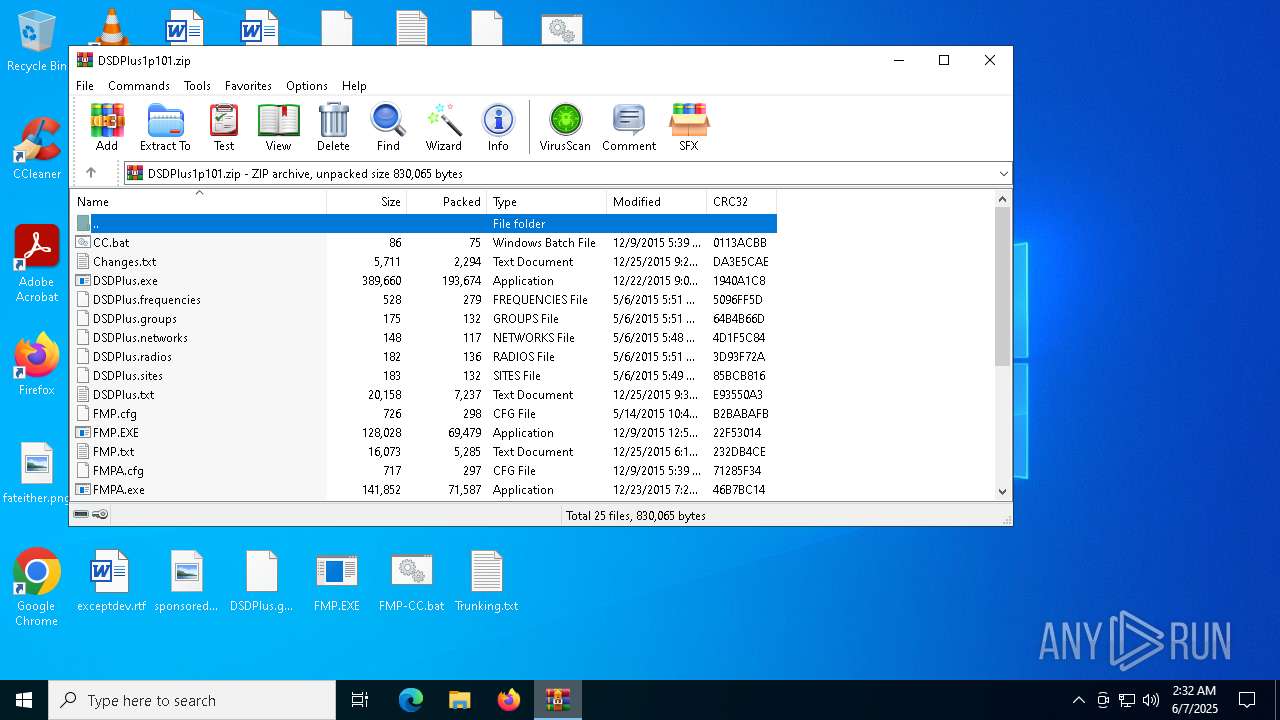
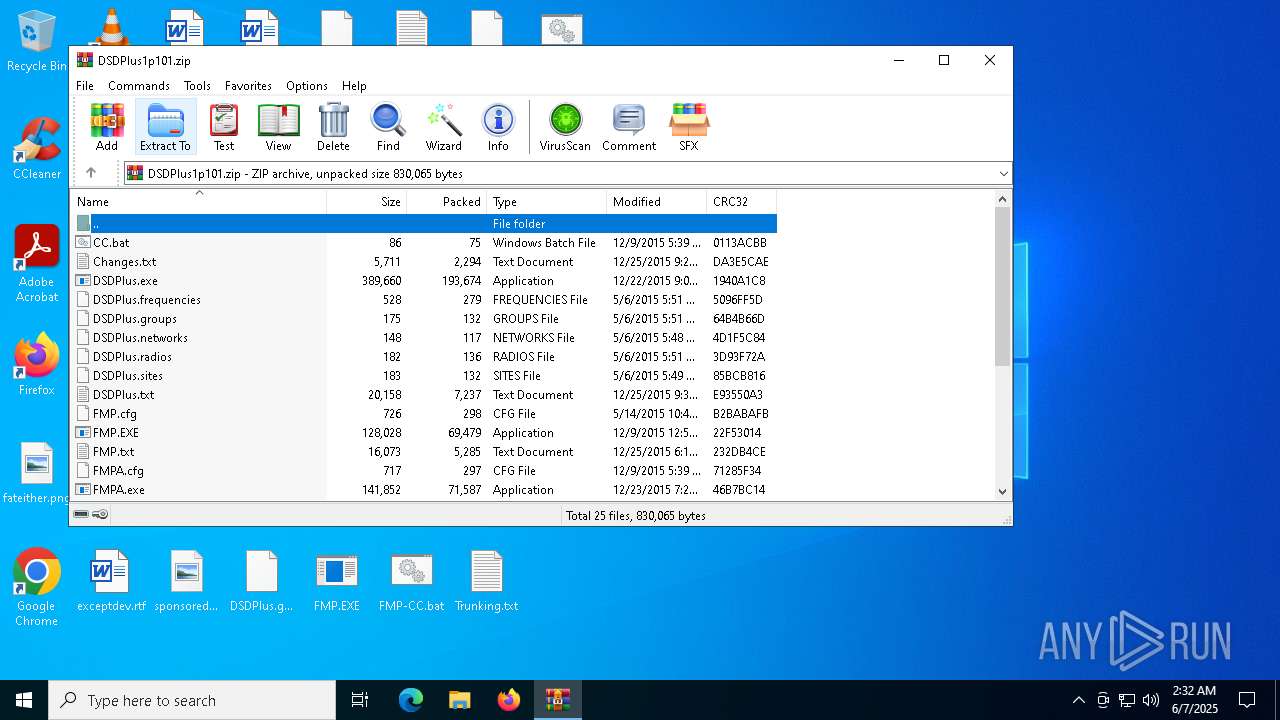
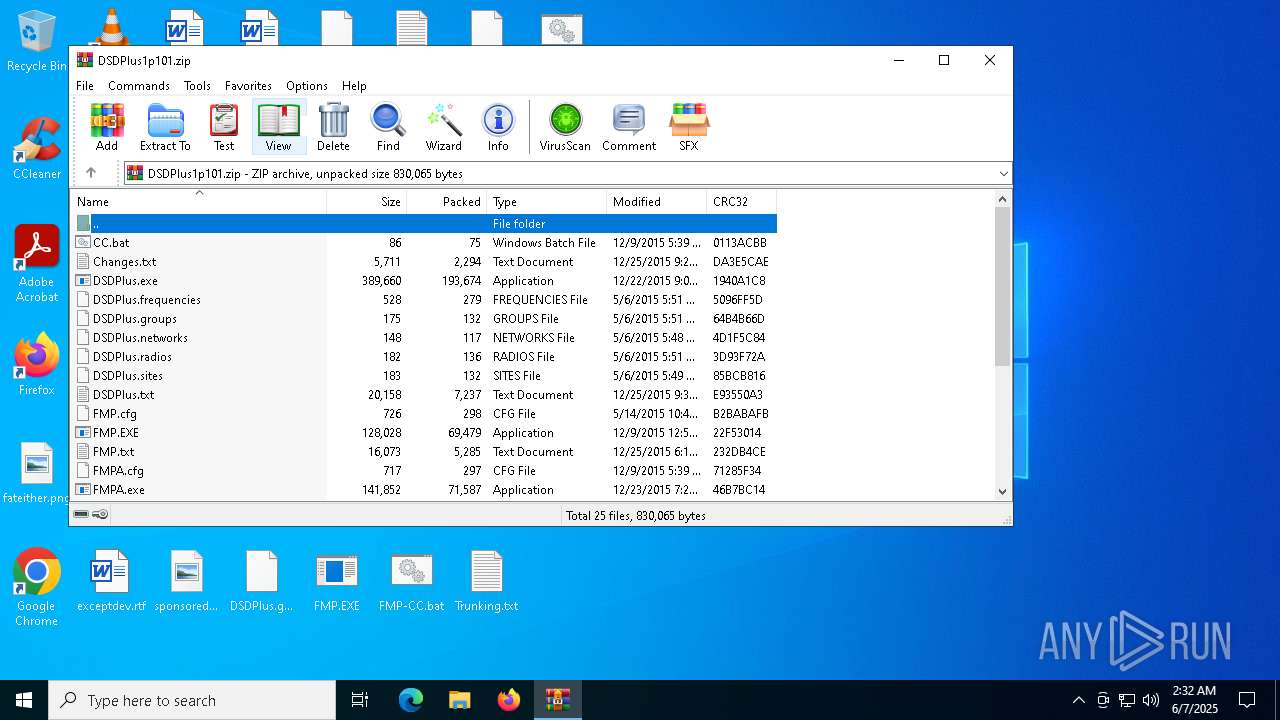
| File name: | DSDPlus1p101.zip |
| Full analysis: | https://app.any.run/tasks/c337b9a6-bab9-49e8-aa72-325d17868123 |
| Verdict: | Malicious activity |
| Analysis date: | June 07, 2025, 02:30:49 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | 26CA7823D786794564A11E892E0971E6 |
| SHA1: | 9B7B654B9AA0DDCC8FE2B5B60C1736267D413626 |
| SHA256: | B7BB00B3DEBD5CCCF44B795C4C004BE34D9F88300CB86B31E19D630D09DE215C |
| SSDEEP: | 24576:+bQTQnrs5WtEp6qBkvP/PW8Wd7YhVe96vb6sZ7FiGqk63/c:+bQTQrs5EEp6qBkvPHW8Wd7YhVe96vbb |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 1052)
SUSPICIOUS
No suspicious indicators.INFO
Manual execution by a user
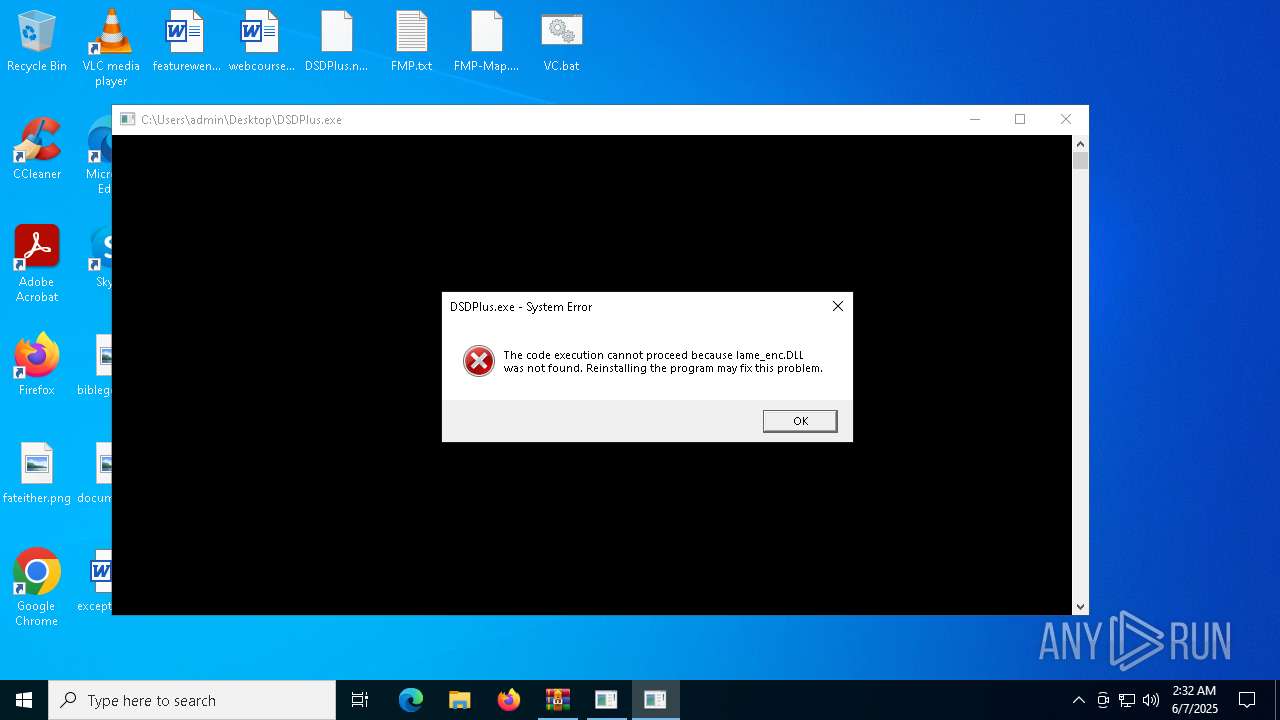
- DSDPlus.exe (PID: 1472)
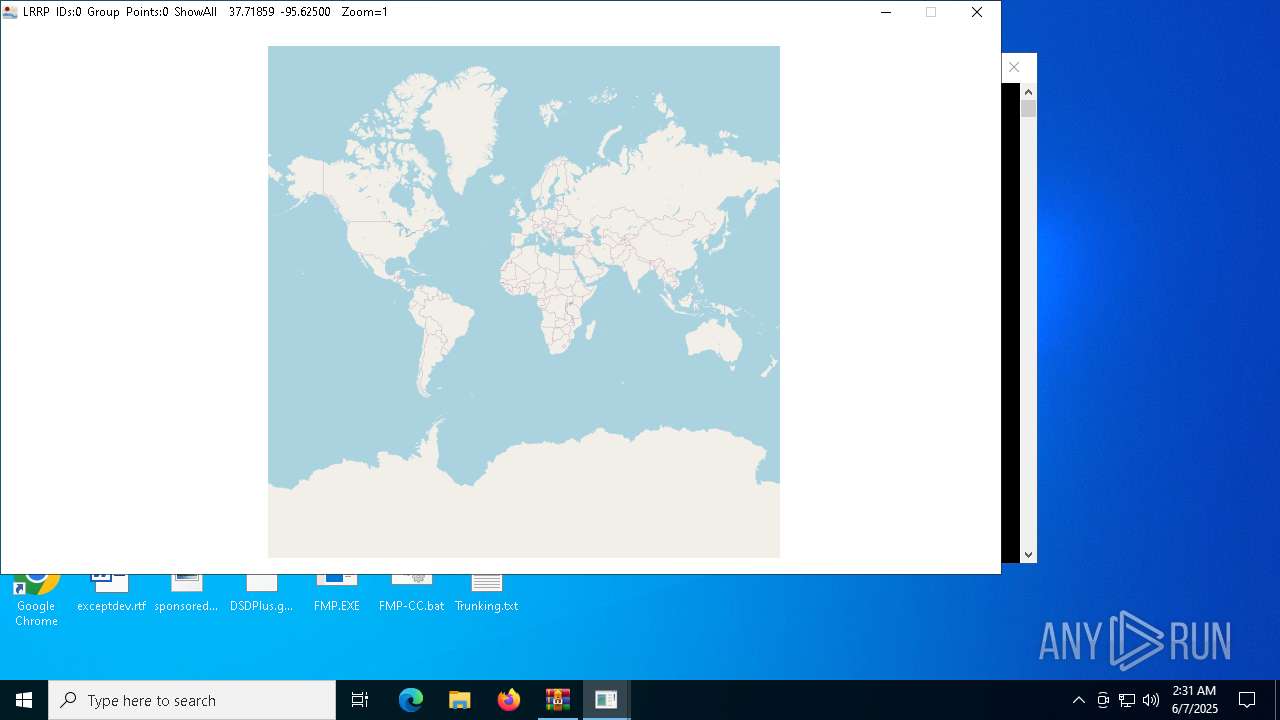
- LRRP.EXE (PID: 7852)
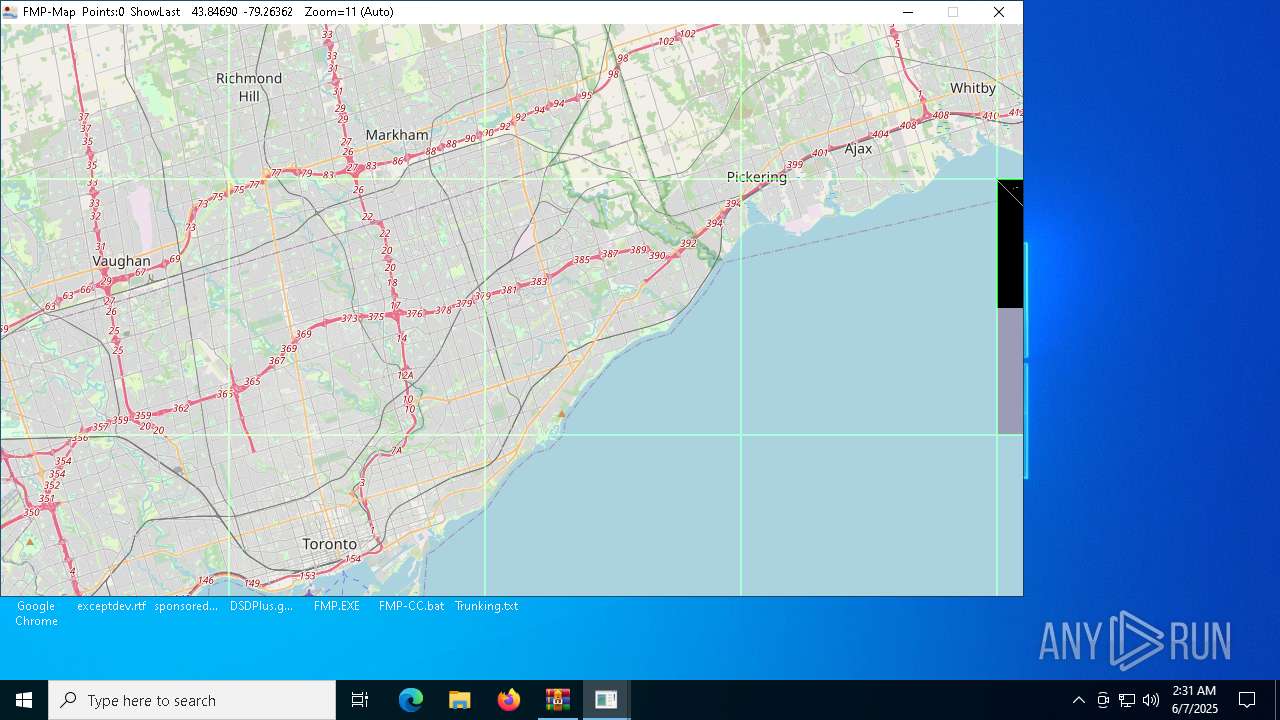
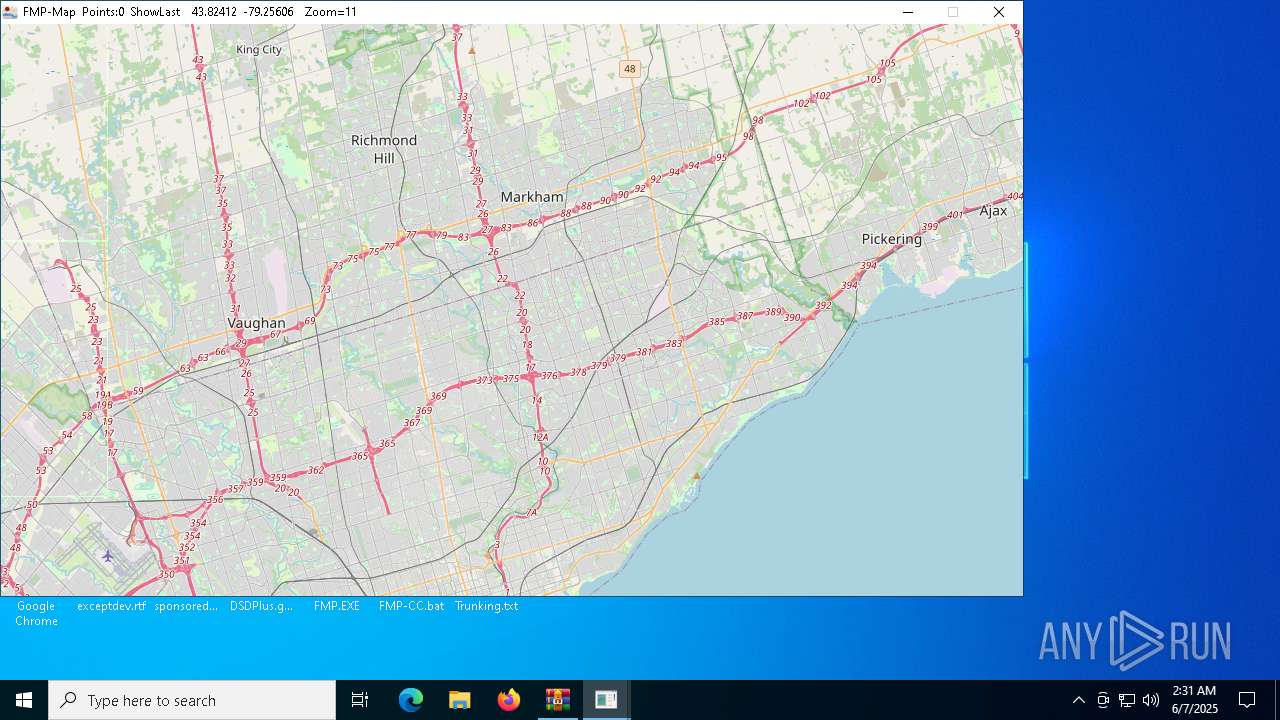
- FMP-Map.EXE (PID: 6620)
- FMP.EXE (PID: 7268)
- DSDPlus.exe (PID: 3364)
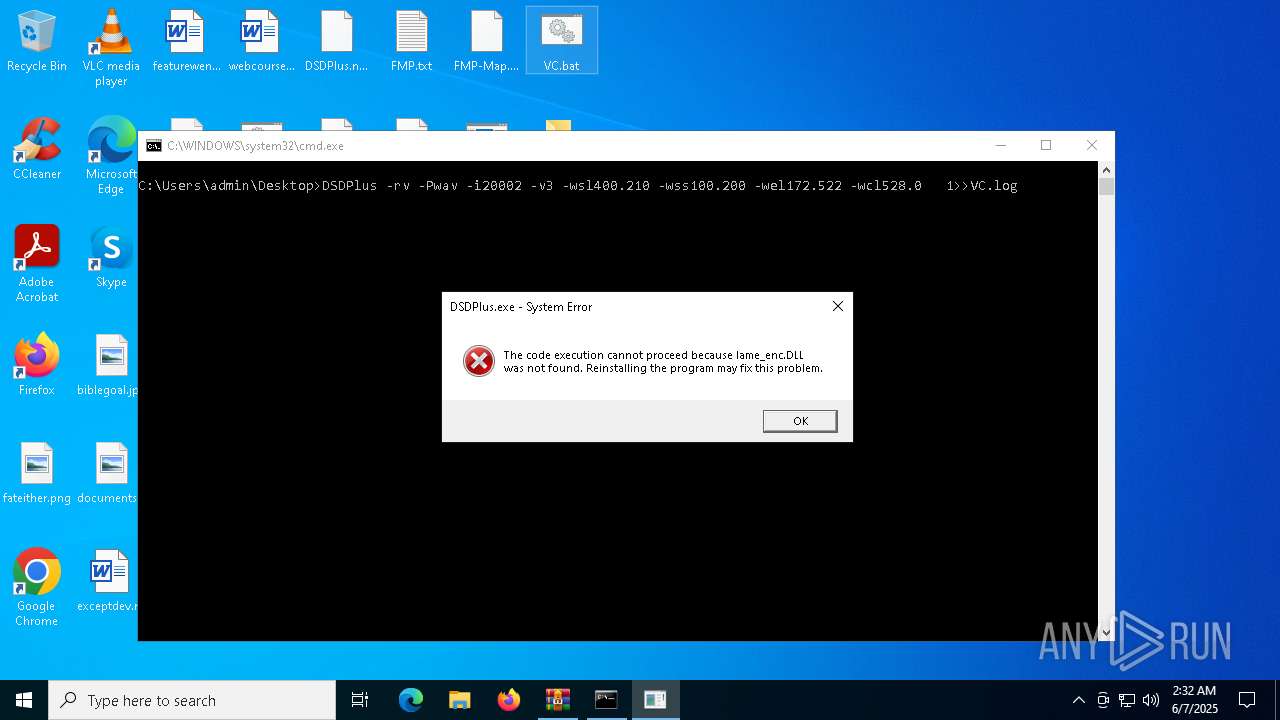
- cmd.exe (PID: 8148)
- cmd.exe (PID: 2552)
- cmd.exe (PID: 7904)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 1052)
Reads the computer name
- FMP-Map.EXE (PID: 6620)
- LRRP.EXE (PID: 7852)
- FMP.EXE (PID: 7268)
Checks supported languages
- FMP-Map.EXE (PID: 6620)
- LRRP.EXE (PID: 7852)
- FMP.EXE (PID: 7268)
- FMPA.exe (PID: 4040)
Reads the software policy settings
- slui.exe (PID: 5776)
- slui.exe (PID: 7184)
Checks proxy server information
- slui.exe (PID: 7184)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2015:12:09 00:39:32 |
| ZipCRC: | 0x0113acbb |
| ZipCompressedSize: | 75 |
| ZipUncompressedSize: | 86 |
| ZipFileName: | CC.bat |
Total processes
149
Monitored processes
23
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1052 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\DSDPlus1p101.zip | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 1472 | "C:\Users\admin\Desktop\DSDPlus.exe" | C:\Users\admin\Desktop\DSDPlus.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221225781 Modules
| |||||||||||||||
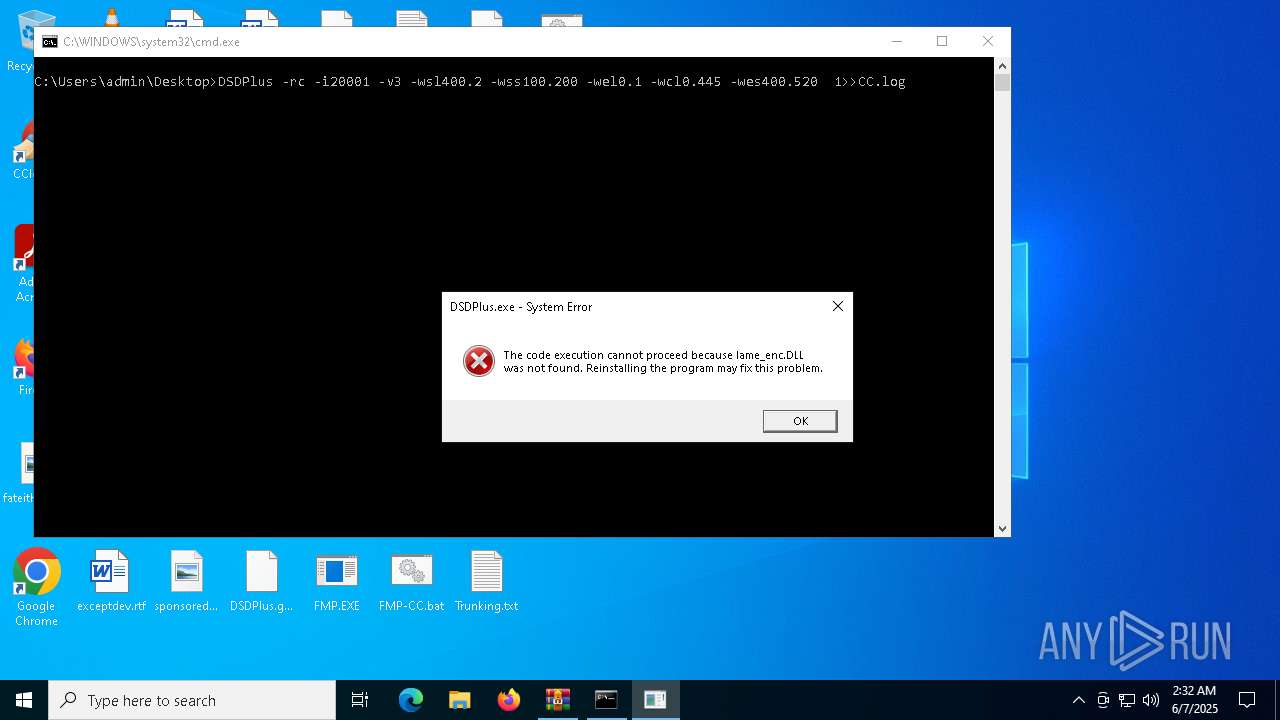
| 2552 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\Desktop\FMPA-CC.bat" " | C:\Windows\System32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 3221225547 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3096 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | FMP-Map.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3364 | "C:\Users\admin\Desktop\DSDPlus.exe" | C:\Users\admin\Desktop\DSDPlus.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221225781 Modules
| |||||||||||||||
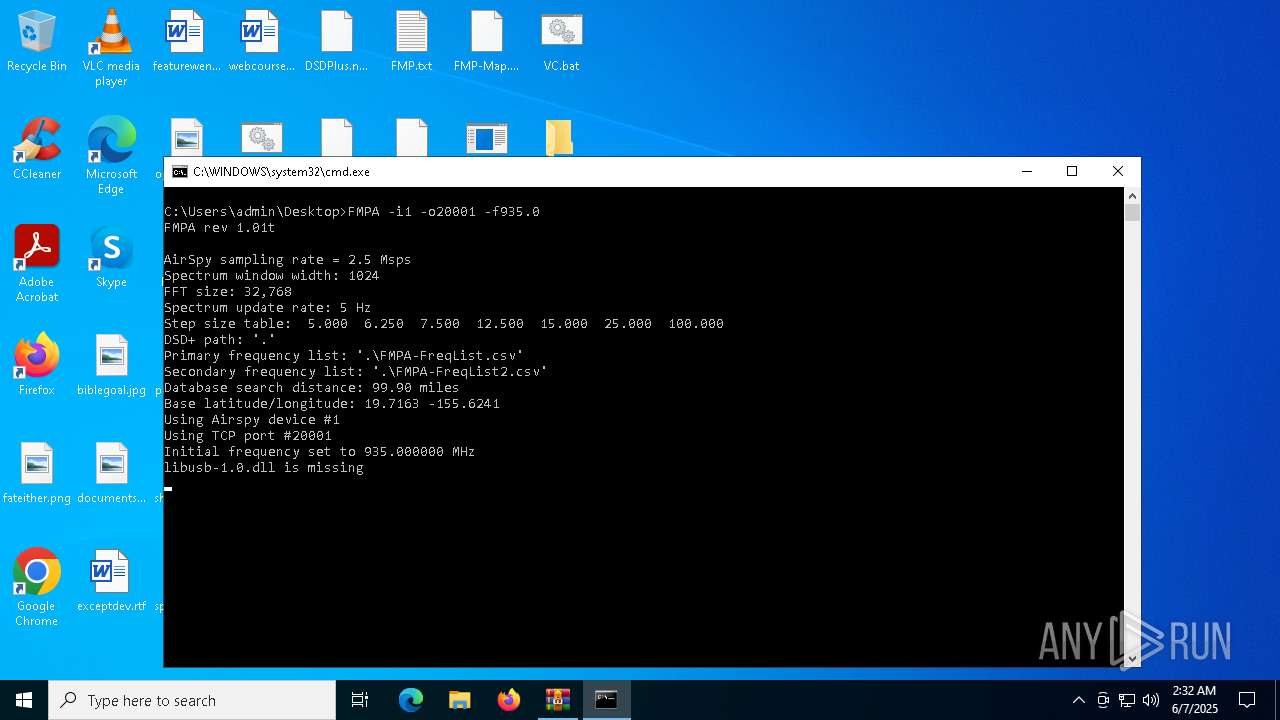
| 4040 | FMPA -i1 -o20001 -f935.0 | C:\Users\admin\Desktop\FMPA.exe | — | cmd.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221225786 Modules
| |||||||||||||||
| 4844 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5376 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5720 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | DSDPlus.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5776 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | SppExtComObj.Exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
4 795
Read events
4 755
Write events
15
Delete events
25
Modification events
| (PID) Process: | (1052) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (1052) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (1052) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (1052) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\DSDPlus1p101.zip | |||
| (PID) Process: | (1052) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (1052) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (1052) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (1052) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (1052) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 15 |
Value: | |||
| (PID) Process: | (1052) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 14 |
Value: | |||
Executable files
10
Suspicious files
4
Text files
94
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1052 | WinRAR.exe | C:\Users\admin\Downloads\FMP-VC.bat | text | |
MD5:B11E9C83204E4B01413A12DFF51F8B13 | SHA256:20F7B6A2A518CA223C473A07F3AC793009FB271952E567955231BC743F166CED | |||
| 1052 | WinRAR.exe | C:\Users\admin\Downloads\DSDPlus.exe | executable | |
MD5:41581C8A47C3120F09BC5D12960968E2 | SHA256:E53FDF243CD17589C42199712138EABF5101A28500ACD9A8ADC2DF3667F37B1B | |||
| 1052 | WinRAR.exe | C:\Users\admin\Downloads\Changes.txt | text | |
MD5:88638C35111ECDA5C60405B8ABDB195E | SHA256:42CAC16134AC72CCB71E89E00BAB555080EDB5DB3AE8574FF8A1C8720A363D30 | |||
| 1052 | WinRAR.exe | C:\Users\admin\Downloads\DSDPlus.networks | text | |
MD5:A9BC802BAD9A062681542A6D15C497CA | SHA256:578C5B308EE845F973C90B9F361F127426485F17005EFFC8B4D79080ABF4DA7D | |||
| 1052 | WinRAR.exe | C:\Users\admin\Downloads\CC.bat | text | |
MD5:297F0F99FD2D2ABD647A109470B0DD40 | SHA256:21140CCE2D1E5799C8E1907072489C0617B5949FA7A4F585B931D4AE222768A7 | |||
| 1052 | WinRAR.exe | C:\Users\admin\Downloads\DSDPlus.groups | text | |
MD5:EEF5AC872E522EA5624134B41BE0136A | SHA256:BA06CC3527F4FFB2663CF30ED9C982F8CAB456DC8F98D84BFB0DF5909ACEFE81 | |||
| 1052 | WinRAR.exe | C:\Users\admin\Downloads\DSDPlus.radios | text | |
MD5:5A56F1044C6C10F78F662B533A06AD96 | SHA256:B5299C5845EB9C3E4327CEBA48B7DE2C5889F39FFF534B1E904C2C21247B6542 | |||
| 1052 | WinRAR.exe | C:\Users\admin\Downloads\DSDPlus.txt | text | |
MD5:BFE3AF63067A2EC6692DD6A17300131F | SHA256:1FED8C73CA0DE111FBF61AEE5425FCC0A995939E3A3564F82857670CC155D797 | |||
| 1052 | WinRAR.exe | C:\Users\admin\Downloads\FMP-CC.bat | text | |
MD5:E29C46459244E6C8AC5F3687F2D10E59 | SHA256:D1586224A1C222AFB5364837C625E62A0830805E7AAAD79CB3394057C6674C08 | |||
| 1052 | WinRAR.exe | C:\Users\admin\Downloads\DSDPlus.frequencies | text | |
MD5:1A95F610CA103ED53563674BA06E28ED | SHA256:908B73000C78508E2A8953812ED735A4076C7D98E09362841BEB99D84F0FC621 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
37
TCP/UDP connections
53
DNS requests
16
Threats
31
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 2.20.245.139:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
7600 | svchost.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
1452 | SIHClient.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
1452 | SIHClient.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
6620 | FMP-Map.EXE | GET | 200 | 151.101.1.91:80 | http://tile.openstreetmap.org/11/571/745.png | unknown | — | — | unknown |
6620 | FMP-Map.EXE | GET | 200 | 151.101.1.91:80 | http://tile.openstreetmap.org/11/572/745.png | unknown | — | — | unknown |
6620 | FMP-Map.EXE | GET | 200 | 151.101.1.91:80 | http://tile.openstreetmap.org/11/574/745.png | unknown | — | — | unknown |
6620 | FMP-Map.EXE | GET | 200 | 151.101.1.91:80 | http://tile.openstreetmap.org/11/573/745.png | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
5604 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5496 | MoUsoCoreWorker.exe | 2.20.245.139:80 | crl.microsoft.com | Akamai International B.V. | SE | whitelisted |
5496 | MoUsoCoreWorker.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
7600 | svchost.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
7600 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6544 | svchost.exe | 40.126.32.68:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 2.23.77.188:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
tile.openstreetmap.org |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
6620 | FMP-Map.EXE | Potentially Bad Traffic | ET USER_AGENTS User-Agent (Internet Explorer) |
6620 | FMP-Map.EXE | Potentially Bad Traffic | ET USER_AGENTS User-Agent (Internet Explorer) |
6620 | FMP-Map.EXE | Potentially Bad Traffic | ET USER_AGENTS User-Agent (Internet Explorer) |
6620 | FMP-Map.EXE | Potentially Bad Traffic | ET USER_AGENTS User-Agent (Internet Explorer) |
6620 | FMP-Map.EXE | Potentially Bad Traffic | ET USER_AGENTS User-Agent (Internet Explorer) |
6620 | FMP-Map.EXE | Potentially Bad Traffic | ET USER_AGENTS User-Agent (Internet Explorer) |
6620 | FMP-Map.EXE | Potentially Bad Traffic | ET USER_AGENTS User-Agent (Internet Explorer) |
6620 | FMP-Map.EXE | Potentially Bad Traffic | ET USER_AGENTS User-Agent (Internet Explorer) |
6620 | FMP-Map.EXE | Potentially Bad Traffic | ET USER_AGENTS User-Agent (Internet Explorer) |
6620 | FMP-Map.EXE | Potentially Bad Traffic | ET USER_AGENTS User-Agent (Internet Explorer) |