| File name: | unknown.zip |
| Full analysis: | https://app.any.run/tasks/6e469306-b09d-4ed4-9c19-5b1d863692d9 |
| Verdict: | Malicious activity |
| Analysis date: | April 12, 2024, 03:50:11 |
| OS: | Windows 11 Professional (build: 22000, 64 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | AB3DF5CA7D7333709FDA3D3A99C12072 |
| SHA1: | C0B0628D094C493E32F746AD7EFC9D8ABEB68BDE |
| SHA256: | B7896750F0F09CBE63DD4A898A2FBBB4195D578B88BB592A3CD306E8B9DC323F |
| SSDEEP: | 1536:LfNSQnb0qWb0sZWGU1orjK9Ffspfd9j+7FFlZtJTVh5DYFco6pQPOMtEHUZH8DNd:DkQbUb0AWH2K8StJP54coTPZEH46NUu9 |
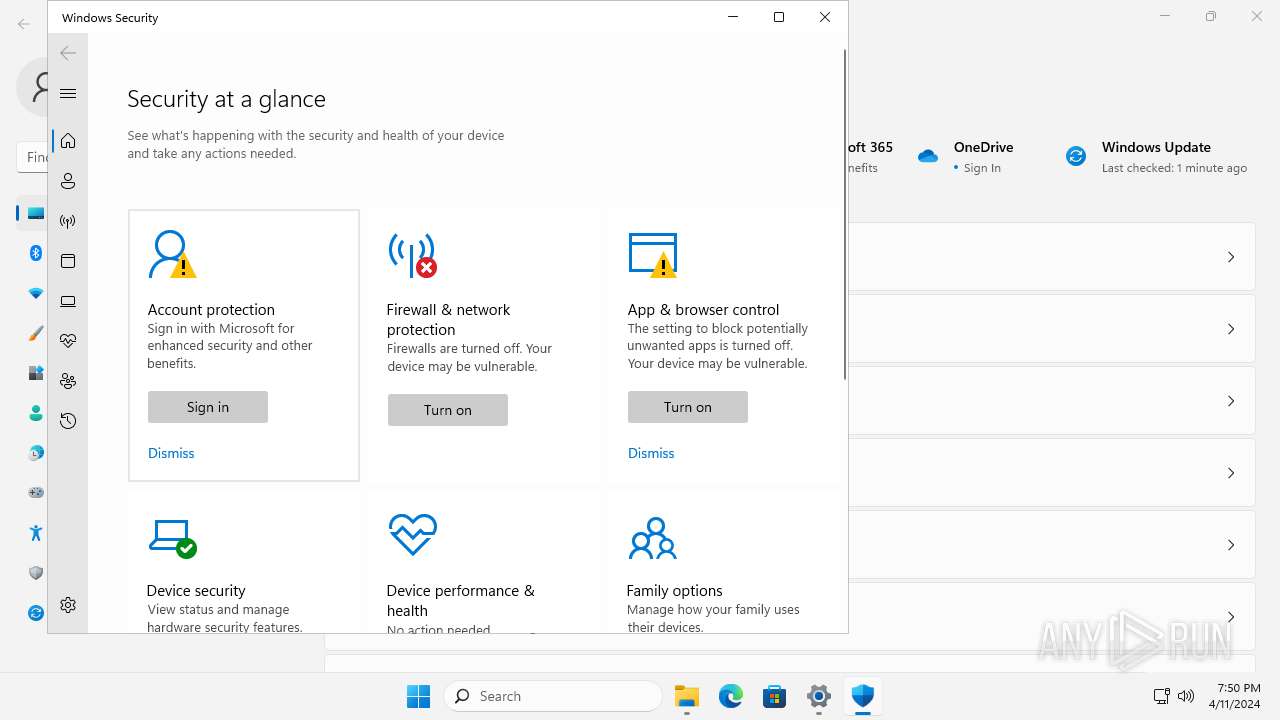
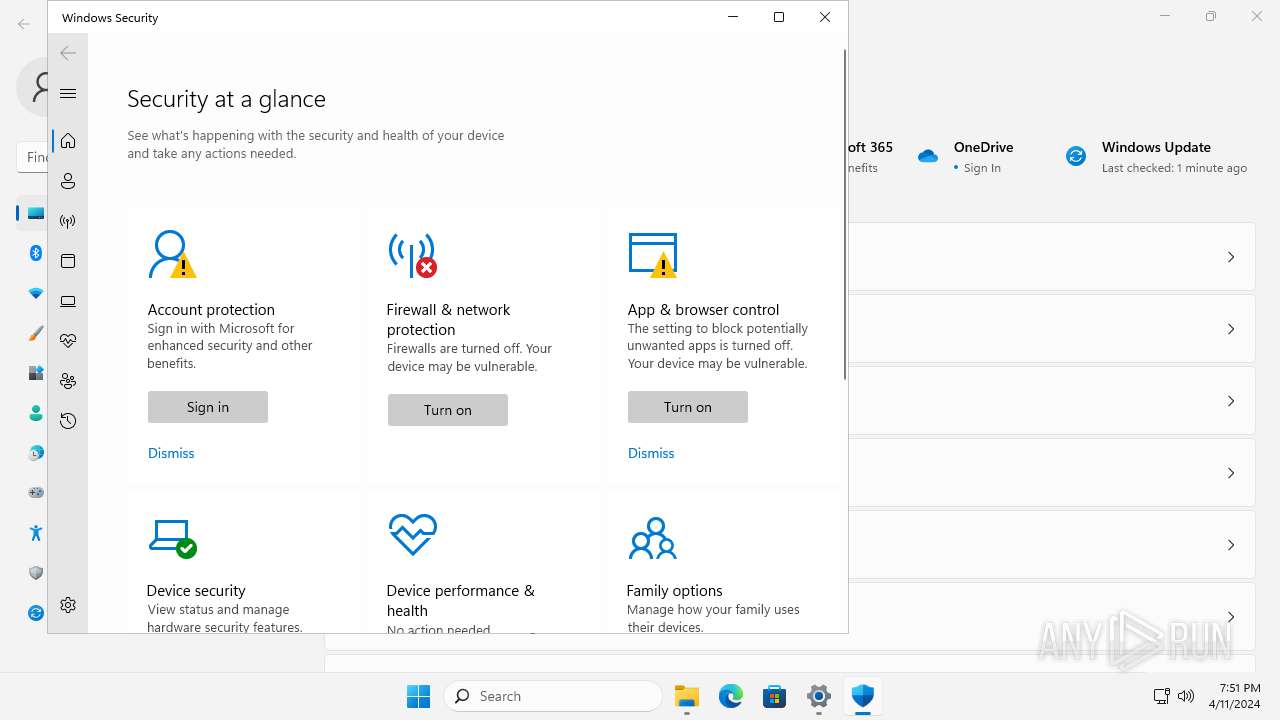
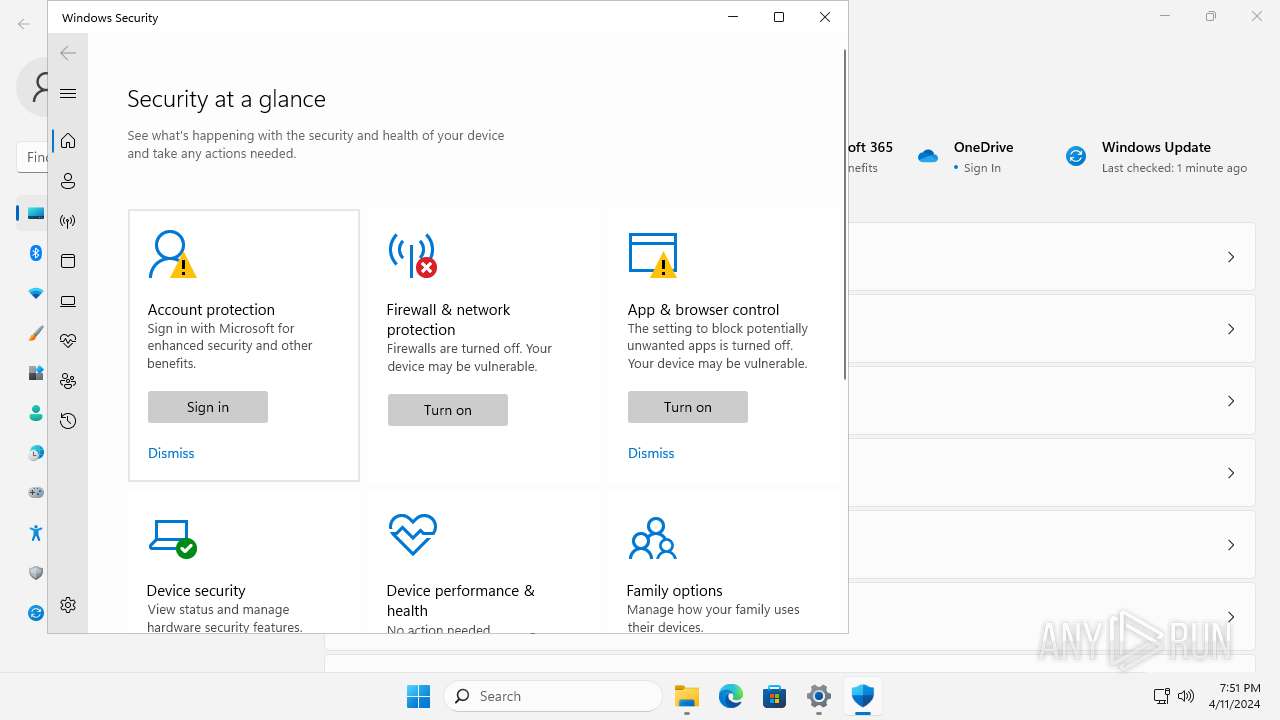
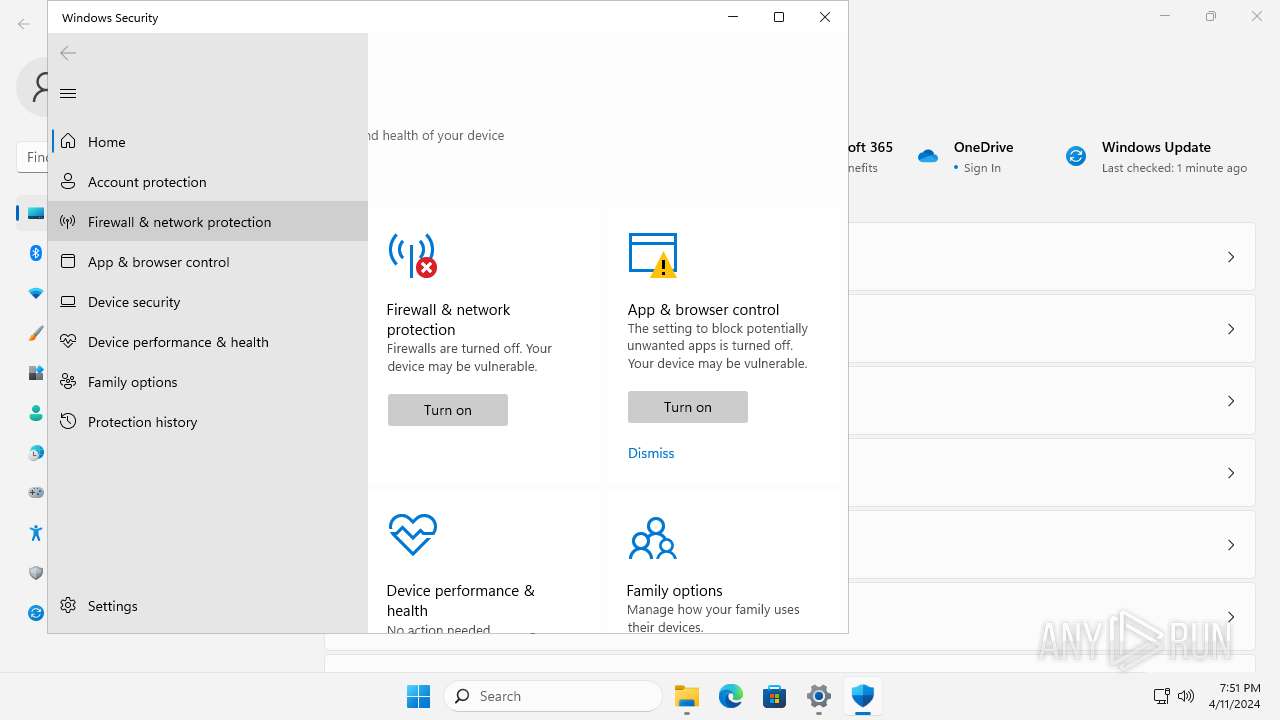
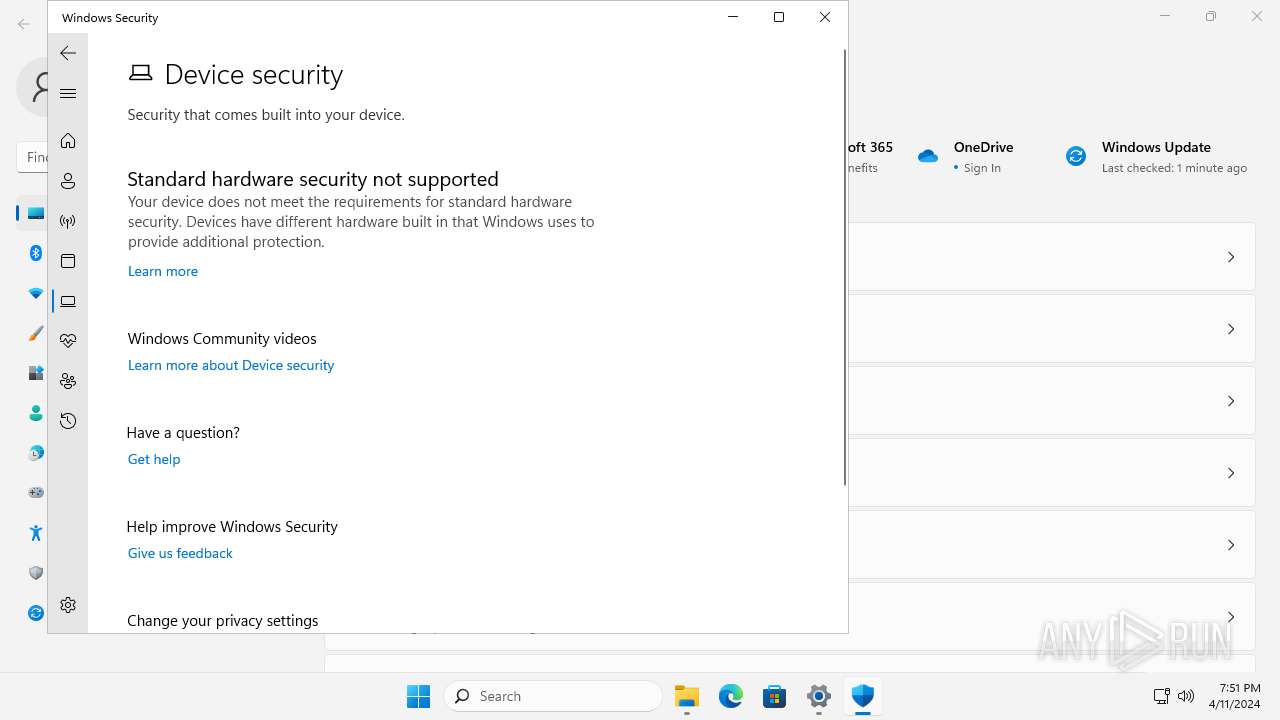
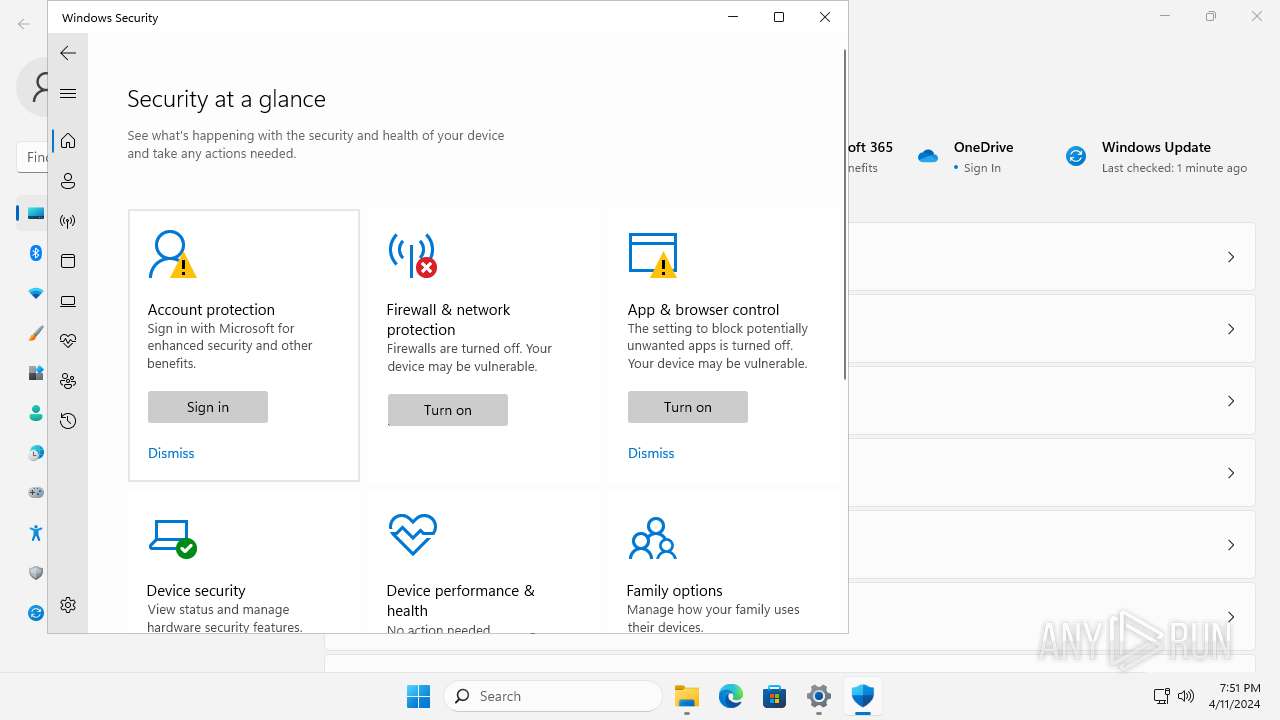
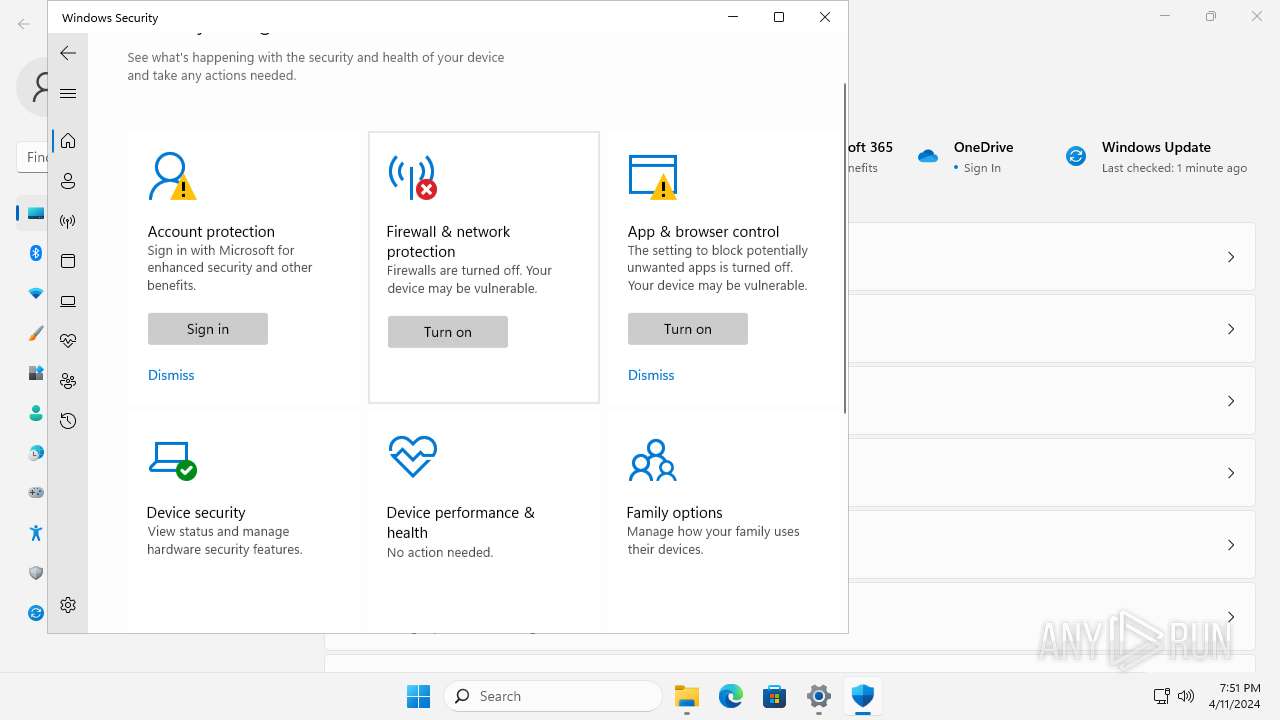
MALICIOUS
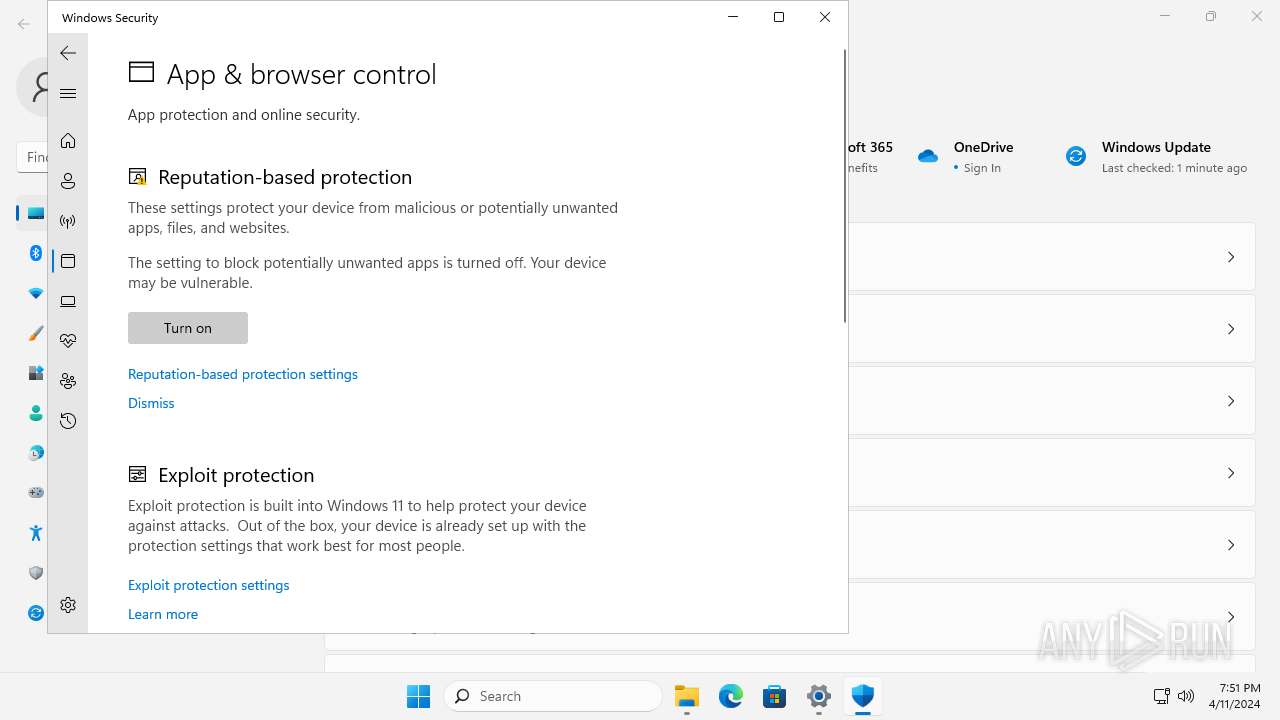
Drops the executable file immediately after the start
- explorer.exe (PID: 5572)
Scans artifacts that could help determine the target
- SystemSettings.exe (PID: 1972)
SUSPICIOUS
Reads the Internet Settings
- SystemSettings.exe (PID: 1972)
Executes as Windows Service
- SecurityHealthService.exe (PID: 6952)
The process executes via Task Scheduler
- sc.exe (PID: 6512)
INFO
Checks supported languages
- SystemSettings.exe (PID: 1972)
- SecHealthUI.exe (PID: 6440)
Reads the computer name
- SystemSettings.exe (PID: 1972)
- SecHealthUI.exe (PID: 6440)
Reads CPU info
- SystemSettings.exe (PID: 1972)
Reads the machine GUID from the registry
- SystemSettings.exe (PID: 1972)
Creates files or folders in the user directory
- SystemSettings.exe (PID: 1972)
Creates files in the program directory
- SecurityHealthService.exe (PID: 6952)
Reads product name
- SecHealthUI.exe (PID: 6440)
Reads Environment values
- SecHealthUI.exe (PID: 6440)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0001 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2024:03:17 13:09:10 |
| ZipCRC: | 0x9f0e727b |
| ZipCompressedSize: | 96191 |
| ZipUncompressedSize: | 108032 |
| ZipFileName: | unknown.exe |
Total processes
121
Monitored processes
12
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1100 | C:\Windows\System32\rundll32.exe C:\Windows\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.22000.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1972 | "C:\Windows\ImmersiveControlPanel\SystemSettings.exe" -ServerName:microsoft.windows.immersivecontrolpanel | C:\Windows\ImmersiveControlPanel\SystemSettings.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Settings Exit code: 1 Version: 10.0.22000.2124 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2748 | C:\Windows\system32\ApplicationFrameHost.exe -Embedding | C:\Windows\System32\ApplicationFrameHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Application Frame Host Version: 10.0.22000.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5572 | "C:\Windows\Explorer.exe" /idlist,:31523:3238,"C:\Users\admin\Desktop\unknown.zip" | C:\Windows\explorer.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1 Version: 10.0.22000.184 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5700 | C:\Windows\System32\oobe\UserOOBEBroker.exe -Embedding | C:\Windows\System32\oobe\UserOOBEBroker.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: User OOBE Broker Exit code: 0 Version: 10.0.22000.2482 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6320 | "C:\Users\admin\AppData\Local\Microsoft\OneDrive\22.186.0904.0001\FileCoAuth.exe" -Embedding | C:\Users\admin\AppData\Local\Microsoft\OneDrive\22.186.0904.0001\FileCoAuth.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft OneDriveFile Co-Authoring Executable Exit code: 0 Version: 22.186.0904.0001 Modules
| |||||||||||||||
| 6440 | "C:\Program Files\WindowsApps\Microsoft.SecHealthUI_1000.22000.1.0_neutral__8wekyb3d8bbwe\SecHealthUI.exe" -ServerName:SecHealthUI.AppX8tam42xc7v2czs3s1nt0nkxvfjtepzp9.mca | C:\Program Files\WindowsApps\Microsoft.SecHealthUI_1000.22000.1.0_neutral__8wekyb3d8bbwe\SecHealthUI.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Defender application Version: 10.0.22000.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6500 | \\?\C:\Windows\System32\SecurityHealthHost.exe {E041C90B-68BA-42C9-991E-477B73A75C90} -Embedding | C:\Windows\System32\SecurityHealthHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Security Health Host Version: 10.0.22000.1042 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6512 | "C:\Windows\system32\sc.exe" start wuauserv | C:\Windows\System32\sc.exe | — | svchost.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Service Control Manager Configuration Tool Exit code: 0 Version: 10.0.22000.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6788 | \??\C:\Windows\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | sc.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Exit code: 0 Version: 10.0.22000.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
13 099
Read events
12 969
Write events
125
Delete events
5
Modification events
| (PID) Process: | (2748) ApplicationFrameHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppModel\SystemAppData\windows.immersivecontrolpanel_cw5n1h2txyewy\PersistedTitleBarData\windows.immersivecontrolpanel_cw5n1h2txyewy!microsoft.windows.immersivecontrolpanel |
| Operation: | write | Name: | AppVersion |
Value: E803060000000A00 | |||
| (PID) Process: | (1972) SystemSettings.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\WSX\WSXPacks\Windows.Settings.Account\1.1.651.580 |
| Operation: | write | Name: | packOpenedCount |
Value: 5 | |||
| (PID) Process: | (1972) SystemSettings.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Themes\HighContrast |
| Operation: | write | Name: | Pre-High Contrast Scheme |
Value: C:\Windows\resources\Themes\aero.theme | |||
| (PID) Process: | (1972) SystemSettings.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Themes |
| Operation: | write | Name: | CurrentTheme |
Value: C:\Windows\resources\Themes\aero.theme | |||
| (PID) Process: | (1972) SystemSettings.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\Wallpapers |
| Operation: | delete value | Name: | BackgroundHistoryPath4 |
Value: c:\windows\web\wallpaper\themed\img32.jpg | |||
| (PID) Process: | (1972) SystemSettings.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\Wallpapers |
| Operation: | delete value | Name: | BackgroundHistoryPath3 |
Value: c:\windows\web\wallpaper\themec\img28.jpg | |||
| (PID) Process: | (1972) SystemSettings.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\Wallpapers |
| Operation: | delete value | Name: | BackgroundHistoryPath2 |
Value: c:\windows\web\wallpaper\themeb\img24.jpg | |||
| (PID) Process: | (1972) SystemSettings.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\Wallpapers |
| Operation: | delete value | Name: | BackgroundHistoryPath1 |
Value: c:\windows\web\wallpaper\themea\img20.jpg | |||
| (PID) Process: | (1972) SystemSettings.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\Wallpapers |
| Operation: | delete value | Name: | BackgroundHistoryPath0 |
Value: c:\windows\web\wallpaper\windows\img0.jpg | |||
| (PID) Process: | (1972) SystemSettings.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\IrisService |
| Operation: | write | Name: | LastContextDate |
Value: 2024-03-04T07:00:30Z | |||
Executable files
0
Suspicious files
4
Text files
11
Unknown types
4
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1972 | SystemSettings.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\RV81NDA7TQZIXEXQ7B0X.temp | binary | |
MD5:— | SHA256:— | |||
| 1972 | SystemSettings.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\f18460fded109990.customDestinations-ms~RF1bfb1.TMP | binary | |
MD5:— | SHA256:— | |||
| 1972 | SystemSettings.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\f18460fded109990.customDestinations-ms | binary | |
MD5:— | SHA256:— | |||
| 1972 | SystemSettings.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Themes\Custom.theme | text | |
MD5:— | SHA256:— | |||
| 1972 | SystemSettings.exe | C:\Users\admin\AppData\Local\D3DSCache\d1045fa42060dcaf\F4EB2D6C-ED2B-4BDD-AD9D-F913287E6768.lock | text | |
MD5:— | SHA256:— | |||
| 6320 | FileCoAuth.exe | C:\USERS\ADMIN\APPDATA\LOCAL\MICROSOFT\ONEDRIVE\LOGS\COMMON\DEVICEHEALTHSUMMARYCONFIGURATION.INI | text | |
MD5:— | SHA256:— | |||
| 1972 | SystemSettings.exe | C:\USERS\ADMIN\APPDATA\LOCALLOW\MICROSOFT\CRYPTNETURLCACHE\CONTENT\E2C6CBAF0AF08CF203BA74BF0D0AB6D5_CBDCCBFE4F7A916411C1E69BDD97BB04 | binary | |
MD5:— | SHA256:— | |||
| 1972 | SystemSettings.exe | C:\USERS\ADMIN\APPDATA\LOCALLOW\MICROSOFT\CRYPTNETURLCACHE\METADATA\E2C6CBAF0AF08CF203BA74BF0D0AB6D5_CBDCCBFE4F7A916411C1E69BDD97BB04 | binary | |
MD5:— | SHA256:— | |||
| 1972 | SystemSettings.exe | C:\Users\admin\AppData\Roaming\Microsoft\Spelling\en-US\default.dic | text | |
MD5:— | SHA256:— | |||
| 1972 | SystemSettings.exe | C:\Users\admin\AppData\Roaming\Microsoft\Spelling\en-US\default.exc | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
16
TCP/UDP connections
60
DNS requests
20
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1052 | svchost.exe | POST | 302 | 23.211.9.234:80 | http://go.microsoft.com/fwlink/?LinkID=252669&clcid=0x409 | unknown | — | — | unknown |
1052 | svchost.exe | POST | — | 138.91.171.81:80 | http://dmd.metaservices.microsoft.com/metadata.svc | unknown | — | — | unknown |
4336 | smartscreen.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | unknown |
4640 | SearchHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAzlnDD9eoNTLi0BRrMy%2BWU%3D | unknown | — | — | unknown |
1052 | svchost.exe | POST | 302 | 23.211.9.234:80 | http://go.microsoft.com/fwlink/?LinkID=252669&clcid=0x409 | unknown | — | — | unknown |
1972 | SystemSettings.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEApDqVCbATUviZV57HIIulA%3D | unknown | — | — | unknown |
1052 | svchost.exe | POST | — | 138.91.171.81:80 | http://dmd.metaservices.microsoft.com/metadata.svc | unknown | — | — | unknown |
1052 | svchost.exe | POST | 302 | 23.211.9.234:80 | http://go.microsoft.com/fwlink/?LinkID=252669&clcid=0x409 | unknown | — | — | unknown |
1052 | svchost.exe | POST | — | 138.91.171.81:80 | http://dmd.metaservices.microsoft.com/metadata.svc | unknown | — | — | unknown |
2920 | svchost.exe | GET | 200 | 95.101.54.128:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/pinrulesstl.cab?320b3e0b8c402932 | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 20.190.159.68:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 52.143.87.28:443 | geo.prod.do.dsp.mp.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
— | — | 40.127.240.158:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
4740 | svchost.exe | 20.190.159.68:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
2680 | svchost.exe | 23.212.88.32:443 | kv601.prod.do.dsp.mp.microsoft.com | AKAMAI-AS | MX | unknown |
1052 | svchost.exe | 23.211.9.234:80 | go.microsoft.com | AKAMAI-AS | DE | unknown |
4336 | smartscreen.exe | 20.105.95.163:443 | checkappexec.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
1052 | svchost.exe | 138.91.171.81:80 | dmd.metaservices.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
2680 | svchost.exe | 51.104.167.245:443 | array608.prod.do.dsp.mp.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
geo.prod.do.dsp.mp.microsoft.com |
| whitelisted |
kv601.prod.do.dsp.mp.microsoft.com |
| whitelisted |
cp601.prod.do.dsp.mp.microsoft.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
checkappexec.microsoft.com |
| whitelisted |
disc601.prod.do.dsp.mp.microsoft.com |
| whitelisted |
dmd.metaservices.microsoft.com |
| whitelisted |
array608.prod.do.dsp.mp.microsoft.com |
| whitelisted |
array613.prod.do.dsp.mp.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Misc activity | ET INFO Microsoft Connection Test |
Process | Message |
|---|---|
SystemSettings.exe | |
SystemSettings.exe | SKU MDM licensing allow list string from SLAPI:
|
SystemSettings.exe | AboveLock|Accounts|ActiveXControls|ADMXIngest|AllowMessageSync|AppHVSI|ApplicationDefaults|AllowAllTrustedApps|AllowAppStoreAutoUpdate|AllowAutomaticAppArchiving|AllowDeveloperUnlock|AllowGameDVR|AllowSharedUserAppData|ApplicationRestrictions|Audit|ConfigureChatIcon|LaunchAppAfterLogOn|MSIAllowUserControlOverInstall|MSIAlwaysInstallWithElevatedPrivileges|RestrictAppDataToSystemVolume|RestrictAppToSystemVolume|AppRuntime|AttachmentManager|Authentication|Autoplay|BitLocker|BITS|Bluetooth|Browser|Camera|Cellular|Connectivity|ControlPolicyConflict|CredentialProviders|CredentialsDelegation|CredentialsUI|Cryptography|DataProtection|DataUsage|Defender|DeliveryOptimization|Desktop|ConfigureSystemGuardLaunch|EnableVirtualizationBasedSecurity|DeviceHealthMonitoring|DeviceInstallation|DeviceLock|Display|DmaGuard|ErrorReporting|Eap|Education|EnterpriseCloudPrint|EventLogService|AllowClipboardHistory|AllowCopyPaste|AllowCortana|AllowDeviceDiscovery|AllowManualMDMUnenrollment|AllowSaveAsOfOfficeFiles|AllowScreenCapture|AllowSharingOfOfficeFiles|AllowSIMErrorDialogPromptWhenNoSIM|AllowSyncMySettings|AllowTailoredExperiencesWithDiagnosticData|AllowTaskSwitcher|AllowThirdPartySuggestionsInWindowsSpotlight|AllowVoiceRecording|DoNotShowFeedbackNotifications|DoNotSyncBrowserSettings|AllowFindMyDevice|ExploitGuard|Feeds|FileExplorer|Games|Handwriting|HumanPresence|InternetExplorer|Kerberos|KioskBrowser|Knobs|LanmanWorkstation|Licensing|LocalPoliciesSecurityOptions|LocalUsersAndGroups|Lockdown|Maps|MemoryDump|MSSecurityGuide|MSSLegacy|Multitasking|NetworkIsolation|NetworkListManager|NewsAndInterests|Notifications|OneDrive|Power|Printers|Privacy|RemoteAssistance|RemoteDesktopServices|RemoteDesktop|RemoteManagement|RemoteProcedureCall|RemoteShell|RestrictedGroups|Search|Security|Settings|SmartScreen|Speech|Start|Storage|System|SystemServices|TaskManager|TaskScheduler|TenantRestrictions|TextInput|TimeLanguageSettings|Troubleshooting|Update|UserRights|VirtualizationBasedTechnology|WiFi|WindowsLogon|WirelessDisplay|Location|WindowsAutopilot|WindowsConnectionManager|WindowsDefenderSecurityCenter|WindowsInkWorkspace|WindowsPowerShell|WindowsSandbox|WiredNetwork|ADMX_ |
SystemSettings.exe | All policies are allowed
|
SystemSettings.exe | Populating UpdatePolicy AllowList |