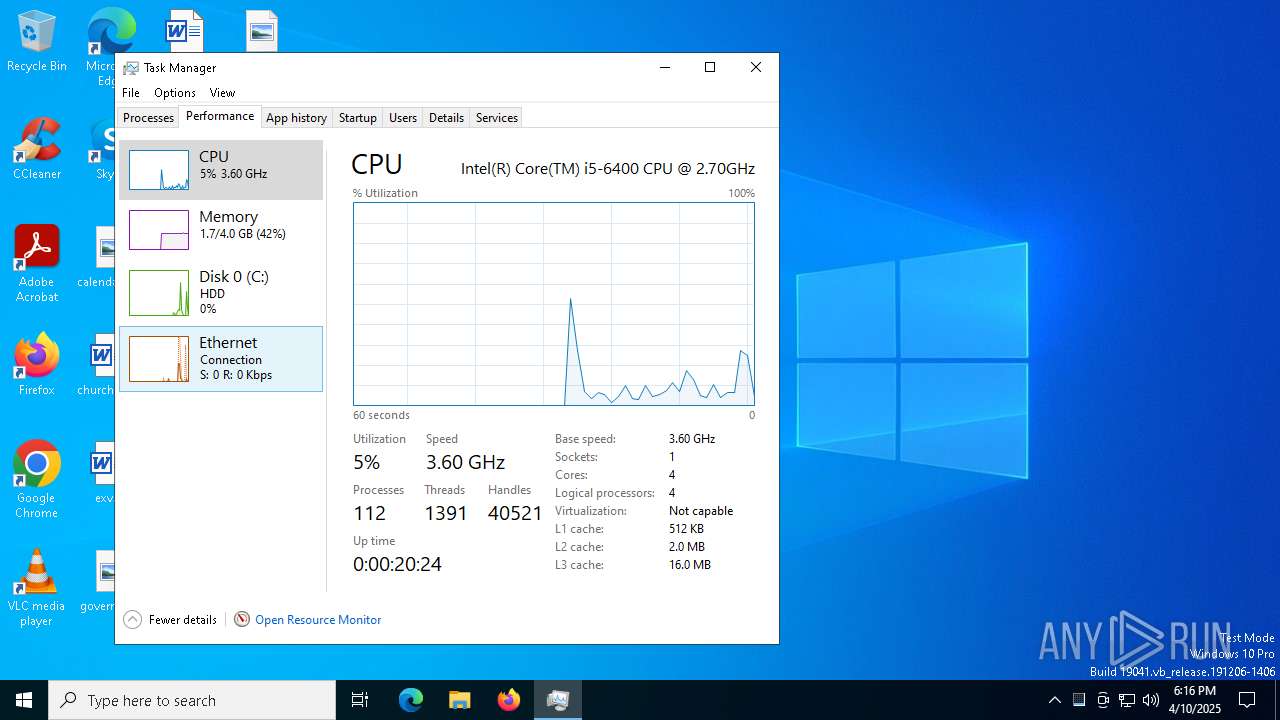
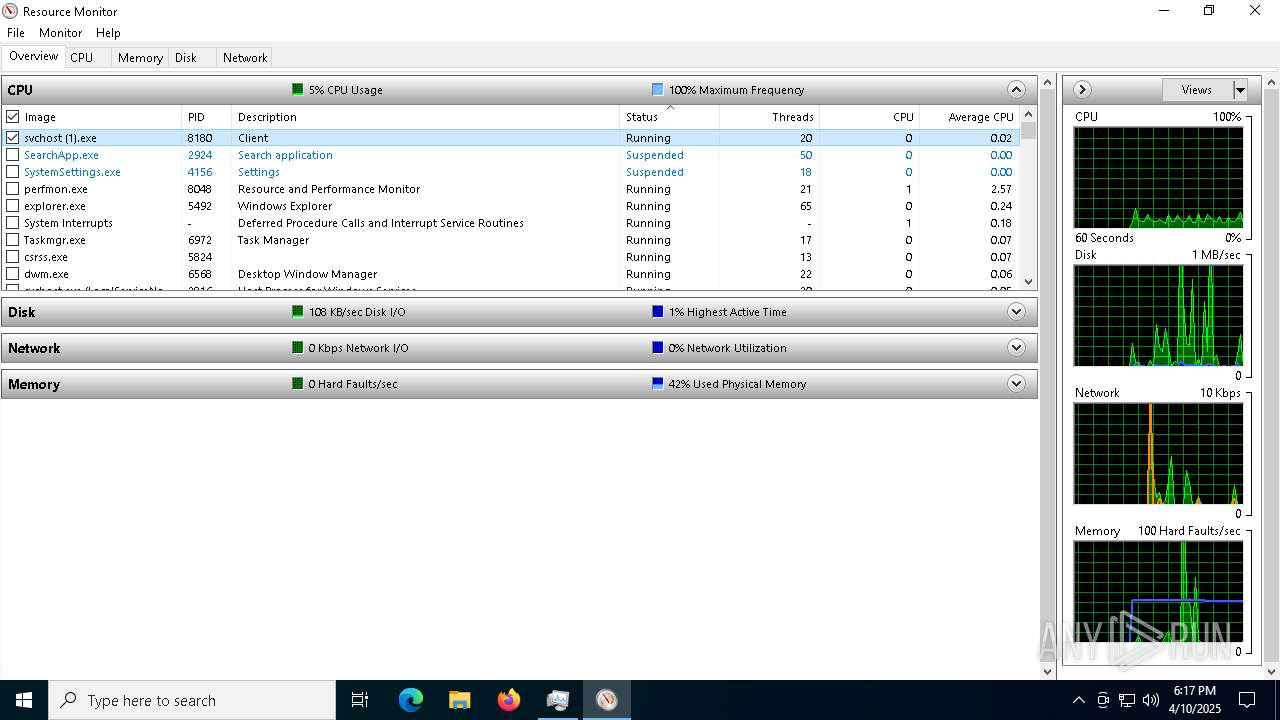
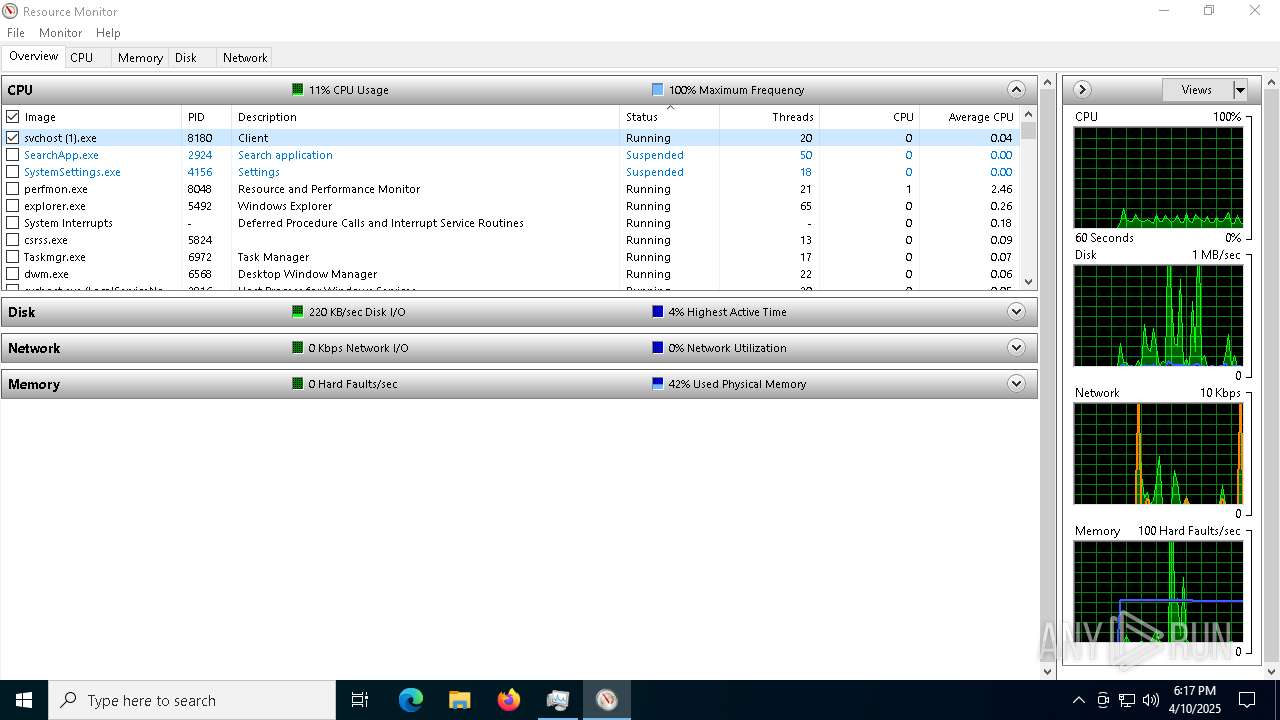
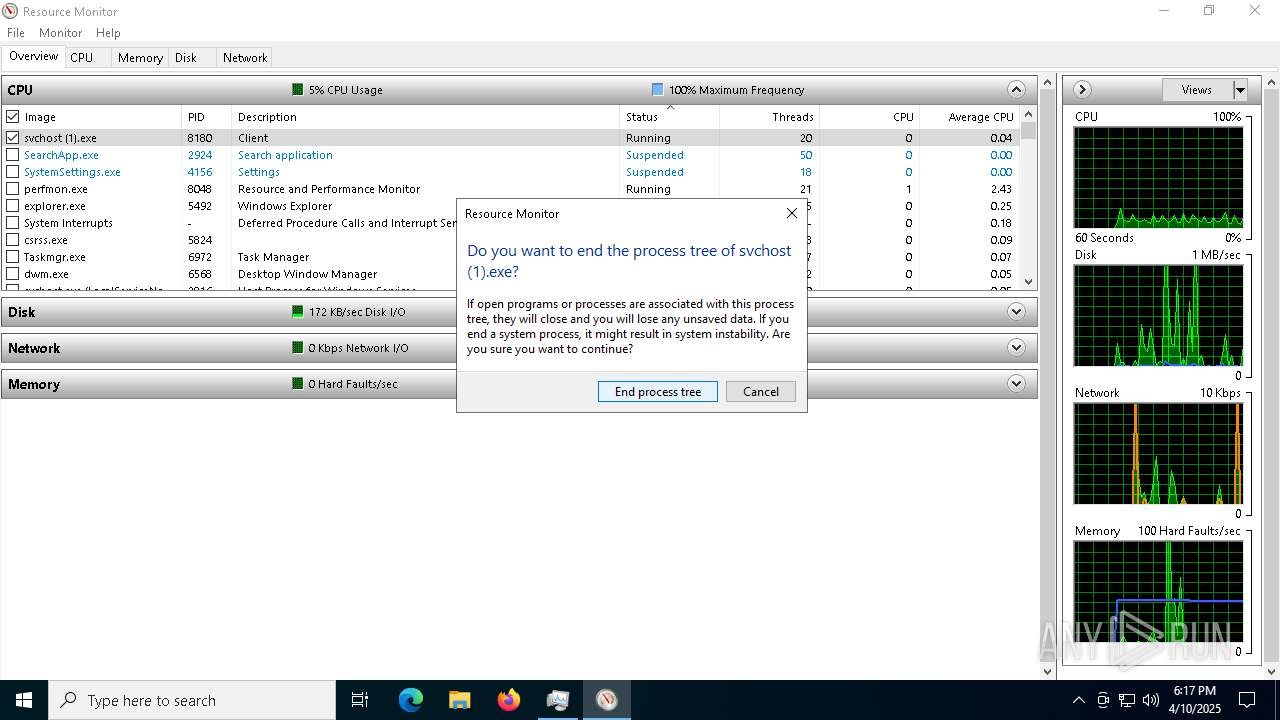
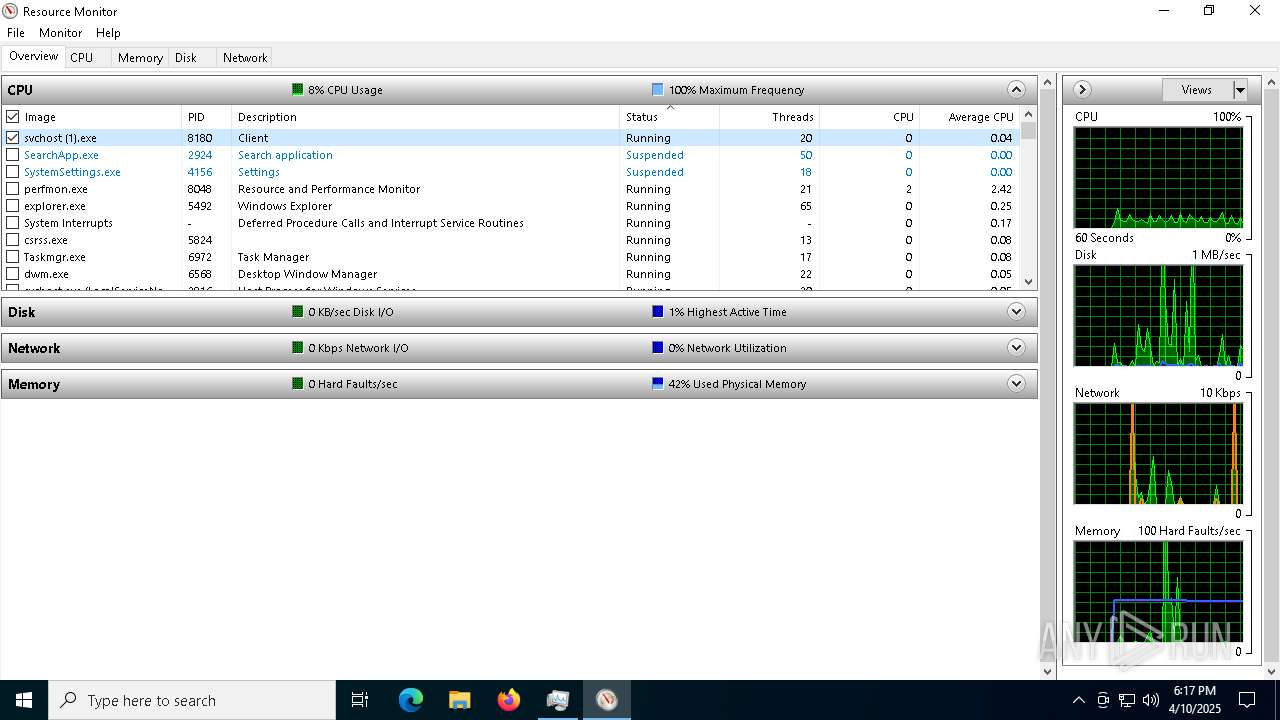
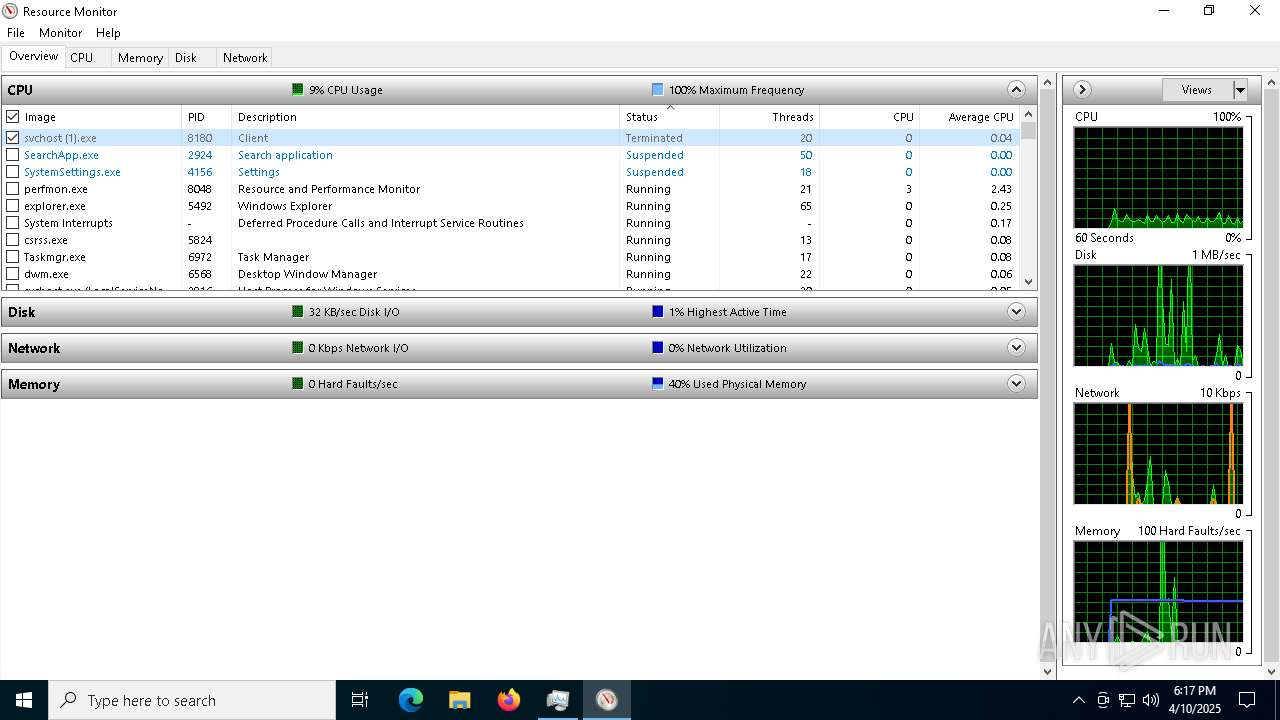
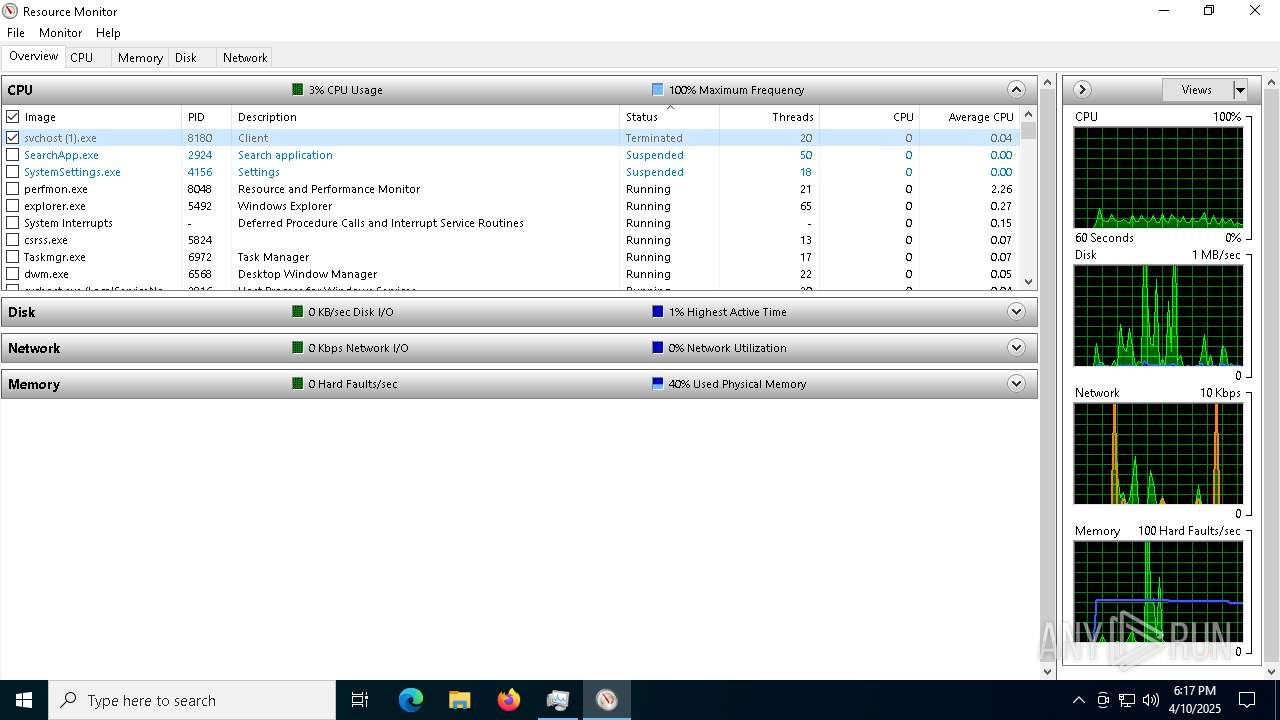
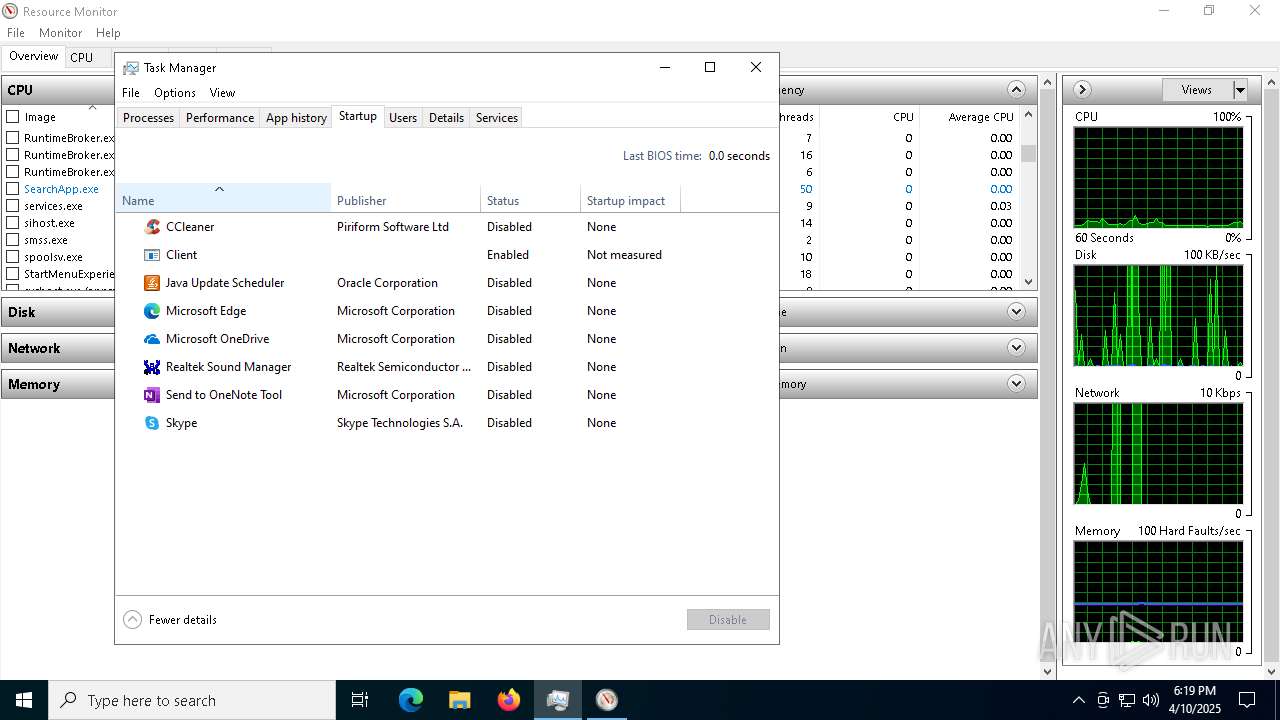
| File name: | svchost (1).exe |
| Full analysis: | https://app.any.run/tasks/abcb8cd2-6abc-43dd-bfc9-dde884a0d31a |
| Verdict: | Malicious activity |
| Threats: | DCrat, also known as Dark Crystal RAT, is a remote access trojan (RAT), which was first introduced in 2018. It is a modular malware that can be customized to perform different tasks. For instance, it can steal passwords, crypto wallet information, hijack Telegram and Steam accounts, and more. Attackers may use a variety of methods to distribute DCrat, but phishing email campaigns are the most common. |
| Analysis date: | April 10, 2025, 18:14:36 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386 Mono/.Net assembly, for MS Windows, 3 sections |
| MD5: | 1DD68DE30F0E798A13A242DB3ECF6E5B |
| SHA1: | ADBDDEFAD10AD3625B2F5C1BFBC5B8ADB798DDD9 |
| SHA256: | B76950CC24A54DF20F1ACB0228D582BF82CC717AB41A594D8C0AF7B62262F41F |
| SSDEEP: | 6144:tiRkuBqL7cI07ZkZsDJp1XKHv3UFDqE16QC/QiKZ+Ub7blhMJ7Hp:siEqHcIqZkZG16Hv3hE8ZDwlhk |
MALICIOUS
Executing a file with an untrusted certificate
- svchost (1).exe (PID: 7488)
- svchost (1).exe (PID: 8180)
SHEETRAT mutex has been found
- svchost (1).exe (PID: 8180)
Uses Task Scheduler to autorun other applications
- cmd.exe (PID: 7244)
Changes the AppInit_DLLs value (autorun option)
- svchost (1).exe (PID: 8180)
Changes the login/logoff helper path in the registry
- svchost (1).exe (PID: 8180)
Changes the autorun value in the registry
- svchost (1).exe (PID: 8180)
DARKCRYSTAL has been detected (SURICATA)
- svchost (1).exe (PID: 8180)
Connects to the CnC server
- svchost (1).exe (PID: 8180)
SHEETRAT has been detected (SURICATA)
- svchost (1).exe (PID: 8180)
SUSPICIOUS
Reads security settings of Internet Explorer
- svchost (1).exe (PID: 7488)
Reads the date of Windows installation
- svchost (1).exe (PID: 7488)
Application launched itself
- svchost (1).exe (PID: 7488)
Starts CMD.EXE for commands execution
- svchost (1).exe (PID: 8180)
Executable content was dropped or overwritten
- svchost (1).exe (PID: 8180)
The process creates files with name similar to system file names
- svchost (1).exe (PID: 8180)
Contacting a server suspected of hosting an CnC
- svchost (1).exe (PID: 8180)
Executes as Windows Service
- WmiApSrv.exe (PID: 4228)
Checks for external IP
- svchost.exe (PID: 2196)
- svchost (1).exe (PID: 8180)
Connects to unusual port
- svchost (1).exe (PID: 8180)
The process checks if it is being run in the virtual environment
- svchost (1).exe (PID: 8180)
- perfmon.exe (PID: 8048)
INFO
Checks supported languages
- svchost (1).exe (PID: 7488)
- svchost (1).exe (PID: 8180)
- perfmon.exe (PID: 8048)
Reads the machine GUID from the registry
- svchost (1).exe (PID: 7488)
- svchost (1).exe (PID: 8180)
Process checks computer location settings
- svchost (1).exe (PID: 7488)
Reads the computer name
- svchost (1).exe (PID: 7488)
- svchost (1).exe (PID: 8180)
- perfmon.exe (PID: 8048)
Creates files or folders in the user directory
- svchost (1).exe (PID: 8180)
Reads Environment values
- svchost (1).exe (PID: 8180)
Disables trace logs
- svchost (1).exe (PID: 8180)
Reads the software policy settings
- svchost (1).exe (PID: 8180)
- slui.exe (PID: 6184)
- slui.exe (PID: 7696)
Reads CPU info
- svchost (1).exe (PID: 8180)
- perfmon.exe (PID: 8048)
Reads the time zone
- svchost (1).exe (PID: 8180)
- perfmon.exe (PID: 8048)
Checks proxy server information
- svchost (1).exe (PID: 8180)
- slui.exe (PID: 6184)
Manual execution by a user
- Taskmgr.exe (PID: 6972)
- Taskmgr.exe (PID: 7736)
Reads security settings of Internet Explorer
- Taskmgr.exe (PID: 6972)
- resmon.exe (PID: 8004)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .scr | | | Windows screen saver (46.4) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (23.3) |
| .exe | | | Win32 Executable (generic) (15.9) |
| .exe | | | Generic Win/DOS Executable (7.1) |
| .exe | | | DOS Executable Generic (7) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2100:10:13 03:20:15+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32 |
| LinkerVersion: | 48 |
| CodeSize: | 611328 |
| InitializedDataSize: | 2048 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x9735e |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.0.0.0 |
| ProductVersionNumber: | 1.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | - |
| CompanyName: | - |
| FileDescription: | Client |
| FileVersion: | 1.0.0.0 |
| InternalName: | Client.exe |
| LegalCopyright: | Copyright © 2022 |
| LegalTrademarks: | - |
| OriginalFileName: | Client.exe |
| ProductName: | Client |
| ProductVersion: | 1.0.0.0 |
| AssemblyVersion: | 1.0.0.0 |
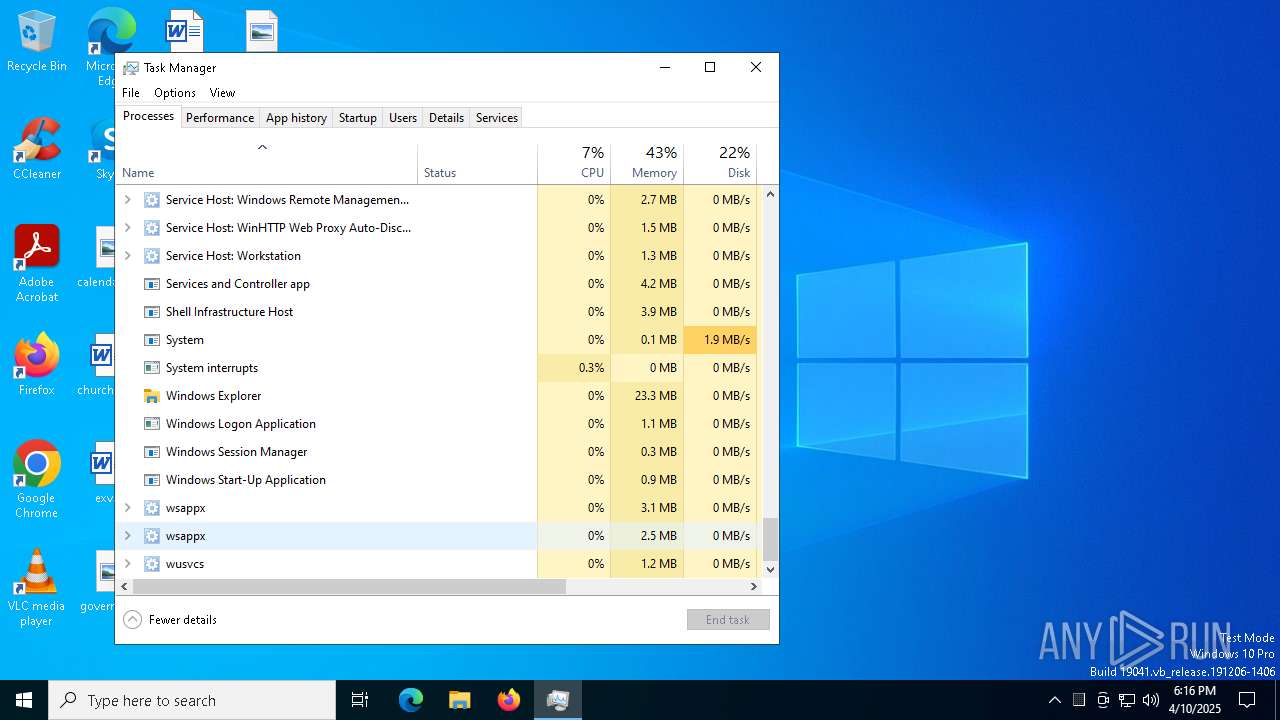
Total processes
150
Monitored processes
15
Malicious processes
3
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2196 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4228 | C:\WINDOWS\system32\wbem\WmiApSrv.exe | C:\Windows\System32\wbem\WmiApSrv.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: WMI Performance Reverse Adapter Exit code: 0 Version: 10.0.19041.3758 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4560 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4784 | SchTaSKs /CrEAte /F /sc OnLoGoN /rl HighEst /tn "svchost" /tr "C:\Users\admin\AppData\Roaming\Microsoft\Windows\Templates\Sub\svchost.exe" | C:\Windows\System32\schtasks.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Task Scheduler Configuration Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6184 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6972 | "C:\WINDOWS\system32\taskmgr.exe" /4 | C:\Windows\System32\Taskmgr.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Task Manager Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7244 | "CMD" /C SchTaSKs /CrEAte /F /sc OnLoGoN /rl HighEst /tn "svchost" /tr "C:\Users\admin\AppData\Roaming\Microsoft\Windows\Templates\Sub\svchost.exe" & exit | C:\Windows\System32\cmd.exe | svchost (1).exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7260 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7488 | "C:\Users\admin\AppData\Local\Temp\svchost (1).exe" | C:\Users\admin\AppData\Local\Temp\svchost (1).exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Client Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 7652 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
18 070
Read events
18 022
Write events
47
Delete events
1
Modification events
| (PID) Process: | (7488) svchost (1).exe | Key: | HKEY_CURRENT_USER\SOFTWARE |
| Operation: | write | Name: | hwid |
Value: MUFFQ0EyRTVDODhDMzgzNkJFQkZBM0M= | |||
| (PID) Process: | (8180) svchost (1).exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\svchost (1)_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (8180) svchost (1).exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\svchost (1)_RASAPI32 |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
| (PID) Process: | (8180) svchost (1).exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\svchost (1)_RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (8180) svchost (1).exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\svchost (1)_RASAPI32 |
| Operation: | write | Name: | FileTracingMask |
Value: | |||
| (PID) Process: | (8180) svchost (1).exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\svchost (1)_RASAPI32 |
| Operation: | write | Name: | ConsoleTracingMask |
Value: | |||
| (PID) Process: | (8180) svchost (1).exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\svchost (1)_RASAPI32 |
| Operation: | write | Name: | MaxFileSize |
Value: 1048576 | |||
| (PID) Process: | (8180) svchost (1).exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\svchost (1)_RASAPI32 |
| Operation: | write | Name: | FileDirectory |
Value: %windir%\tracing | |||
| (PID) Process: | (8180) svchost (1).exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\svchost (1)_RASMANCS |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (8180) svchost (1).exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\svchost (1)_RASMANCS |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
Executable files
3
Suspicious files
0
Text files
1
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 8180 | svchost (1).exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Templates\Sub\svchost.exe | executable | |
MD5:1DD68DE30F0E798A13A242DB3ECF6E5B | SHA256:B76950CC24A54DF20F1ACB0228D582BF82CC717AB41A594D8C0AF7B62262F41F | |||
| 8180 | svchost (1).exe | C:\Windows\xdwd.dll | executable | |
MD5:16E5A492C9C6AE34C59683BE9C51FA31 | SHA256:35C8D022E1D917F1AABDCEAE98097CCC072161B302F84C768CA63E4B32AC2B66 | |||
| 8180 | svchost (1).exe | C:\Windows\Sub\svchost.exe | executable | |
MD5:1DD68DE30F0E798A13A242DB3ECF6E5B | SHA256:B76950CC24A54DF20F1ACB0228D582BF82CC717AB41A594D8C0AF7B62262F41F | |||
| 6972 | Taskmgr.exe | C:\Users\admin\AppData\Local\D3DSCache\3534848bb9f4cb71\F4EB2D6C-ED2B-4BDD-AD9D-F913287E6768.lock | text | |
MD5:F49655F856ACB8884CC0ACE29216F511 | SHA256:7852FCE59C67DDF1D6B8B997EAA1ADFAC004A9F3A91C37295DE9223674011FBA | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
37
DNS requests
31
Threats
7
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.216.77.20:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
8180 | svchost (1).exe | GET | 200 | 104.16.184.241:80 | http://icanhazip.com/ | unknown | — | — | whitelisted |
1512 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
1512 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 23.216.77.20:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
2104 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2112 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3216 | svchost.exe | 172.211.123.248:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 40.126.31.73:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6544 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
2104 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
crl.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
pastebin.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Online Pastebin Text Storage |
2196 | svchost.exe | Misc activity | ET INFO DNS Query to a *.ngrok domain (ngrok.io) |
8180 | svchost (1).exe | Attempted Information Leak | ET INFO IP Check Domain (icanhazip. com in HTTP Host) |
2196 | svchost.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup Domain in DNS Lookup (icanhazip .com) |
8180 | svchost (1).exe | A Network Trojan was detected | ET MALWARE DcRAT/Sheet RAT CnC Checkin Using MessagePack |
8180 | svchost (1).exe | Malware Command and Control Activity Detected | REMOTE [ANY.RUN] SheetRat (Ping) |
8180 | svchost (1).exe | Device Retrieving External IP Address Detected | SUSPICIOUS [ANY.RUN] An IP address was received from the server as a result of an HTTP request |