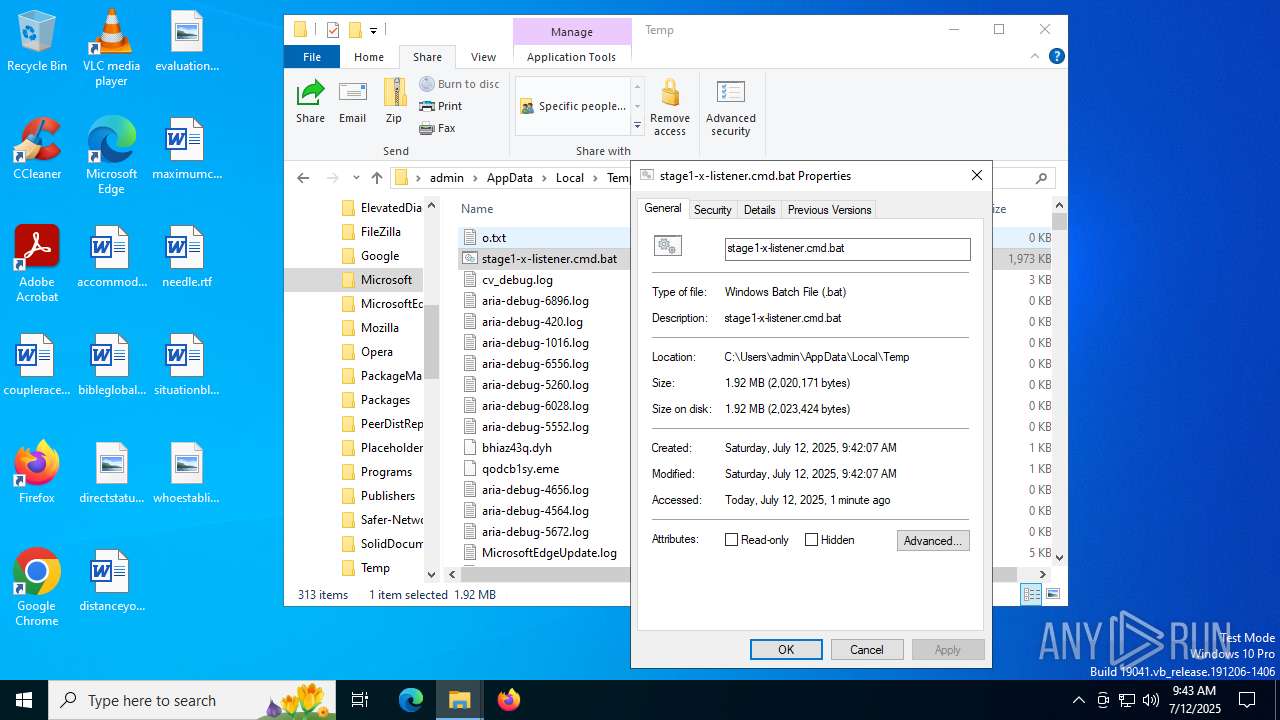
| File name: | stage1-x-listener.cmd |
| Full analysis: | https://app.any.run/tasks/2bc8b14e-3514-495c-b0a2-8b23aa9f2708 |
| Verdict: | Malicious activity |
| Analysis date: | July 12, 2025, 09:42:03 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | text/x-msdos-batch |
| File info: | DOS batch file, ASCII text, with very long lines (599), with CRLF line terminators |
| MD5: | 5A8E086117F38EA410C32E89E9A22137 |
| SHA1: | 592E6FD9B2D0E3E3BF4107F8DCF3BB424CF171B4 |
| SHA256: | B760F325BFAD16722CB29C3A5CD737AE9F7DD9DEE8F49CA7D72507BEF8A6E4D7 |
| SSDEEP: | 49152:QplUZzmCGNv6QwK64LwvROab2O0qHz7SG:1 |
MALICIOUS
Run PowerShell with an invisible window
- powershell.exe (PID: 6652)
- powershell.exe (PID: 3980)
- powershell.exe (PID: 3608)
- powershell.exe (PID: 4120)
- powershell.exe (PID: 2148)
- powershell.exe (PID: 7080)
- powershell.exe (PID: 6768)
- powershell.exe (PID: 4160)
- powershell.exe (PID: 6384)
- powershell.exe (PID: 7324)
- powershell.exe (PID: 6460)
Bypass execution policy to execute commands
- powershell.exe (PID: 6652)
- powershell.exe (PID: 3980)
- powershell.exe (PID: 3608)
- powershell.exe (PID: 4120)
- powershell.exe (PID: 2148)
- powershell.exe (PID: 7080)
- powershell.exe (PID: 6768)
- powershell.exe (PID: 6384)
- powershell.exe (PID: 4160)
- powershell.exe (PID: 7324)
- powershell.exe (PID: 6460)
Changes powershell execution policy (Bypass)
- cmd.exe (PID: 6612)
- cmd.exe (PID: 5416)
- cmd.exe (PID: 4156)
- cmd.exe (PID: 5896)
- cmd.exe (PID: 2124)
- cmd.exe (PID: 1728)
Uses AES cipher (POWERSHELL)
- powershell.exe (PID: 3980)
- powershell.exe (PID: 4120)
- powershell.exe (PID: 7080)
- $syt-powershell.exe (PID: 4820)
- powershell.exe (PID: 6384)
- powershell.exe (PID: 7324)
Dynamically loads an assembly (POWERSHELL)
- powershell.exe (PID: 3980)
- powershell.exe (PID: 4120)
- powershell.exe (PID: 7080)
- $syt-powershell.exe (PID: 4820)
- powershell.exe (PID: 6384)
- powershell.exe (PID: 7324)
Gets or sets the symmetric key that is used for encryption and decryption (POWERSHELL)
- powershell.exe (PID: 3980)
- powershell.exe (PID: 4120)
- powershell.exe (PID: 7080)
- $syt-powershell.exe (PID: 4820)
- powershell.exe (PID: 6384)
- powershell.exe (PID: 7324)
Gets or sets the initialization vector for the symmetric algorithm (POWERSHELL)
- powershell.exe (PID: 3980)
- powershell.exe (PID: 4120)
- powershell.exe (PID: 7080)
- $syt-powershell.exe (PID: 4820)
- powershell.exe (PID: 6384)
- powershell.exe (PID: 7324)
Known privilege escalation attack
- dllhost.exe (PID: 1232)
Starts PowerShell from an unusual location
- cmd.exe (PID: 5896)
Application was injected by another process
- winlogon.exe (PID: 672)
Runs injected code in another process
- $syt-powershell.exe (PID: 4820)
SUSPICIOUS
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 6612)
- cmd.exe (PID: 5416)
- powershell.exe (PID: 4120)
- cmd.exe (PID: 4156)
- cmd.exe (PID: 5896)
- cmd.exe (PID: 2124)
- cmd.exe (PID: 1728)
- powershell.exe (PID: 7324)
BASE64 encoded PowerShell command has been detected
- cmd.exe (PID: 6612)
- cmd.exe (PID: 5416)
- cmd.exe (PID: 4156)
- cmd.exe (PID: 2124)
- cmd.exe (PID: 1728)
Base64-obfuscated command line is found
- cmd.exe (PID: 6612)
- cmd.exe (PID: 5416)
- cmd.exe (PID: 4156)
- cmd.exe (PID: 2124)
- cmd.exe (PID: 1728)
The process bypasses the loading of PowerShell profile settings
- cmd.exe (PID: 6612)
- cmd.exe (PID: 4156)
- cmd.exe (PID: 5416)
- cmd.exe (PID: 2124)
- cmd.exe (PID: 1728)
Uses base64 encoding (POWERSHELL)
- powershell.exe (PID: 3980)
- powershell.exe (PID: 4120)
- powershell.exe (PID: 7080)
- $syt-powershell.exe (PID: 4820)
- powershell.exe (PID: 6384)
- powershell.exe (PID: 7324)
Uses sleep to delay execution (POWERSHELL)
- powershell.exe (PID: 3980)
- powershell.exe (PID: 4120)
- powershell.exe (PID: 7080)
- $syt-powershell.exe (PID: 4820)
- powershell.exe (PID: 6384)
- powershell.exe (PID: 7324)
Gets content of a file (POWERSHELL)
- powershell.exe (PID: 3980)
- powershell.exe (PID: 4120)
- powershell.exe (PID: 7080)
- $syt-powershell.exe (PID: 4820)
- powershell.exe (PID: 6384)
- powershell.exe (PID: 7324)
Probably UAC bypass using CMSTP.exe (Connection Manager service profile)
- powershell.exe (PID: 3980)
- powershell.exe (PID: 6384)
Runs shell command (SCRIPT)
- wscript.exe (PID: 6780)
- wscript.exe (PID: 4936)
- wscript.exe (PID: 2272)
- wscript.exe (PID: 420)
- wscript.exe (PID: 5772)
Starts CMD.EXE for commands execution
- wscript.exe (PID: 6780)
- wscript.exe (PID: 2272)
- powershell.exe (PID: 7080)
- wscript.exe (PID: 5772)
Executing commands from a ".bat" file
- wscript.exe (PID: 6780)
- wscript.exe (PID: 5772)
Executing commands from ".cmd" file
- wscript.exe (PID: 6780)
- wscript.exe (PID: 2272)
- powershell.exe (PID: 7080)
- wscript.exe (PID: 5772)
The process executes VB scripts
- dllhost.exe (PID: 1232)
- powershell.exe (PID: 4120)
- powershell.exe (PID: 7324)
Uses TASKKILL.EXE to kill process
- wscript.exe (PID: 4936)
- wscript.exe (PID: 420)
Application launched itself
- powershell.exe (PID: 4120)
- powershell.exe (PID: 7324)
Executable content was dropped or overwritten
- powershell.exe (PID: 7080)
The process creates files with name similar to system file names
- powershell.exe (PID: 7080)
Renamed powershell base64 command
- $syt-powershell.exe (PID: 4820)
Process drops legitimate windows executable
- powershell.exe (PID: 7080)
Connects to unusual port
- $syt-powershell.exe (PID: 4820)
INFO
Uses string replace method (POWERSHELL)
- powershell.exe (PID: 3980)
- powershell.exe (PID: 4120)
- powershell.exe (PID: 7080)
- $syt-powershell.exe (PID: 4820)
- powershell.exe (PID: 6384)
- powershell.exe (PID: 7324)
Uses string split method (POWERSHELL)
- powershell.exe (PID: 3980)
- powershell.exe (PID: 4120)
- powershell.exe (PID: 7080)
- $syt-powershell.exe (PID: 4820)
- powershell.exe (PID: 6384)
- powershell.exe (PID: 7324)
Gets data length (POWERSHELL)
- powershell.exe (PID: 3980)
- powershell.exe (PID: 4120)
- powershell.exe (PID: 7080)
- $syt-powershell.exe (PID: 4820)
- powershell.exe (PID: 6384)
- powershell.exe (PID: 7324)
Disables trace logs
- cmstp.exe (PID: 5168)
- cmstp.exe (PID: 6256)
Creates files in the program directory
- dllhost.exe (PID: 1232)
Checks transactions between databases Windows and Oracle
- cmstp.exe (PID: 5168)
- cmstp.exe (PID: 6256)
Found Base64 encoded reflection usage via PowerShell (YARA)
- cmd.exe (PID: 6612)
Checks if a key exists in the options dictionary (POWERSHELL)
- powershell.exe (PID: 6268)
- powershell.exe (PID: 7456)
Manual execution by a user
- cmd.exe (PID: 2124)
- notepad.exe (PID: 632)
The sample compiled with english language support
- powershell.exe (PID: 7080)
Reads the software policy settings
- $syt-powershell.exe (PID: 4820)
Create files in a temporary directory
- $syt-powershell.exe (PID: 4820)
Reads security settings of Internet Explorer
- $syt-powershell.exe (PID: 4820)
- notepad.exe (PID: 632)
Reads Microsoft Office registry keys
- OpenWith.exe (PID: 7556)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
181
Monitored processes
47
Malicious processes
16
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 420 | wscript.exe C:\Users\admin\AppData\Local\Temp\killcmstp.vbs | C:\Windows\System32\wscript.exe | — | dllhost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.812.10240.16384 Modules
| |||||||||||||||
| 632 | "C:\WINDOWS\system32\NOTEPAD.EXE" C:\Users\admin\AppData\Local\Temp\o.txt | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 672 | winlogon.exe | C:\Windows\System32\winlogon.exe | — | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Logon Application Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1192 | "C:\Windows\System32\taskkill.exe" /IM cmstp.exe /F | C:\Windows\System32\taskkill.exe | — | wscript.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Terminates Processes Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1232 | C:\WINDOWS\system32\DllHost.exe /Processid:{3E5FC7F9-9A51-4367-9063-A120244FBEC7} | C:\Windows\System32\dllhost.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: COM Surrogate Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1612 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1660 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1728 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\AppData\Local\Temp\stage1-x-listener.cmd.bat" " | C:\Windows\System32\cmd.exe | — | wscript.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2124 | "C:\Windows\System32\cmd.exe" | C:\Windows\System32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2148 | powershell -w hidden -ep bypass -command "" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
67 904
Read events
67 887
Write events
17
Delete events
0
Modification events
| (PID) Process: | (5168) cmstp.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\CMSTP |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (5168) cmstp.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\CMSTP |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
| (PID) Process: | (5168) cmstp.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\CMSTP |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (5168) cmstp.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\CMSTP |
| Operation: | write | Name: | FileTracingMask |
Value: | |||
| (PID) Process: | (5168) cmstp.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\CMSTP |
| Operation: | write | Name: | ConsoleTracingMask |
Value: | |||
| (PID) Process: | (5168) cmstp.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\CMSTP |
| Operation: | write | Name: | MaxFileSize |
Value: 1048576 | |||
| (PID) Process: | (5168) cmstp.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\CMSTP |
| Operation: | write | Name: | FileDirectory |
Value: %windir%\tracing | |||
| (PID) Process: | (5168) cmstp.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Network\Network Connections |
| Operation: | write | Name: | DesktopShortcut |
Value: 0 | |||
| (PID) Process: | (1232) dllhost.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\App Paths\cmmgr32.exe |
| Operation: | write | Name: | ProfileInstallPath |
Value: C:\ProgramData\Microsoft\Network\Connections\Cm | |||
| (PID) Process: | (1232) dllhost.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion |
| Operation: | write | Name: | SM_AccessoriesName |
Value: Accessories | |||
Executable files
1
Suspicious files
3
Text files
40
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6652 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_bw2otnhz.3ei.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 3608 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_fh5t1a5o.3ow.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 4120 | powershell.exe | C:\Users\admin\AppData\Roaming\$syt-MicrosoftFod.cmd | text | |
MD5:5A8E086117F38EA410C32E89E9A22137 | SHA256:B760F325BFAD16722CB29C3A5CD737AE9F7DD9DEE8F49CA7D72507BEF8A6E4D7 | |||
| 2148 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_lvc2wwxn.2h4.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 4120 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_q35r4fiz.4st.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 6268 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_0knftzu2.rha.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 6268 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_5kzgbgds.5xd.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 2148 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_j4oiozn0.ykl.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 3980 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_wpp0ptak.ib2.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 3980 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_s23jhtb4.i5p.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
23
DNS requests
17
Threats
3
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1268 | svchost.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 23.48.23.143:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5328 | SearchApp.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
6372 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
3400 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
3400 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1268 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6768 | RUXIMICS.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1268 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1268 | svchost.exe | 23.48.23.143:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
1268 | svchost.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
5328 | SearchApp.exe | 2.16.241.218:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
5328 | SearchApp.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2200 | svchost.exe | A Network Trojan was detected | MALWARE [ANY.RUN] Suspected domain Associated with Malware Distribution (.ply .gg) |
2200 | svchost.exe | Misc activity | ET TA_ABUSED_SERVICES Tunneling Service in DNS Lookup (* .ply .gg) |
2200 | svchost.exe | Potentially Bad Traffic | ET INFO playit .gg Tunneling Domain in DNS Lookup |