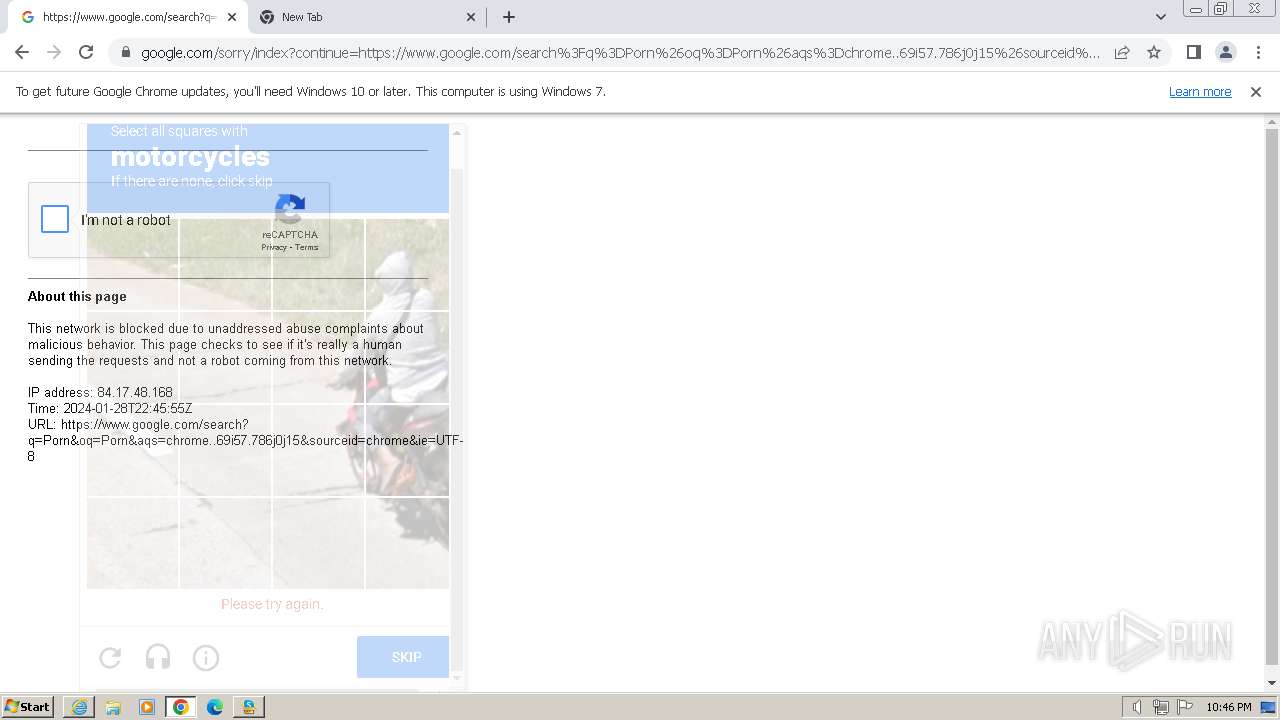
| URL: | https://loot-link.com/s?nHhL |
| Full analysis: | https://app.any.run/tasks/1891628d-0df1-4868-9607-581762f98bbe |
| Verdict: | Malicious activity |
| Analysis date: | January 28, 2024, 22:43:23 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 37A0347F82DEC40914BAC653962EF822 |
| SHA1: | FD482845F43240646484369C2AD516EFB420B48D |
| SHA256: | B75B7A471BB6CF8EE2E6EC956F2188EA032AD39D4DFA4D8A2A5E01E8BD00502C |
| SSDEEP: | 3:N8KK0KkKKvn:2KskNn |
MALICIOUS
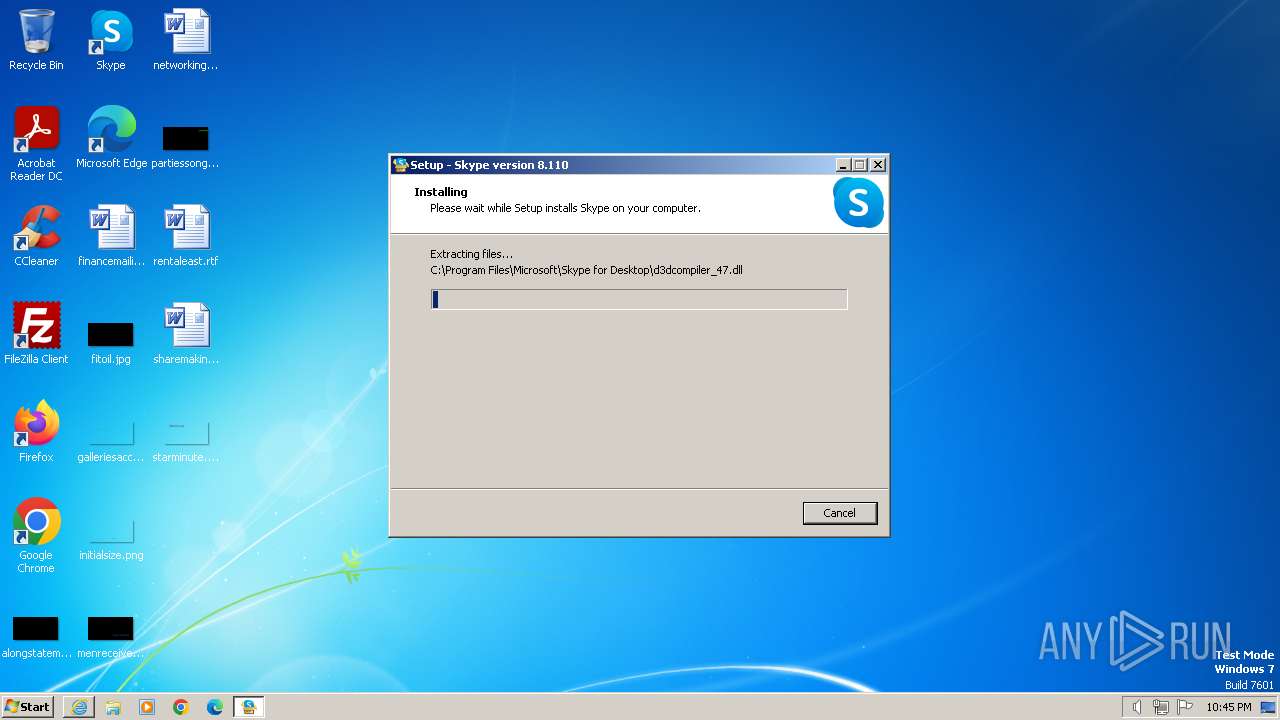
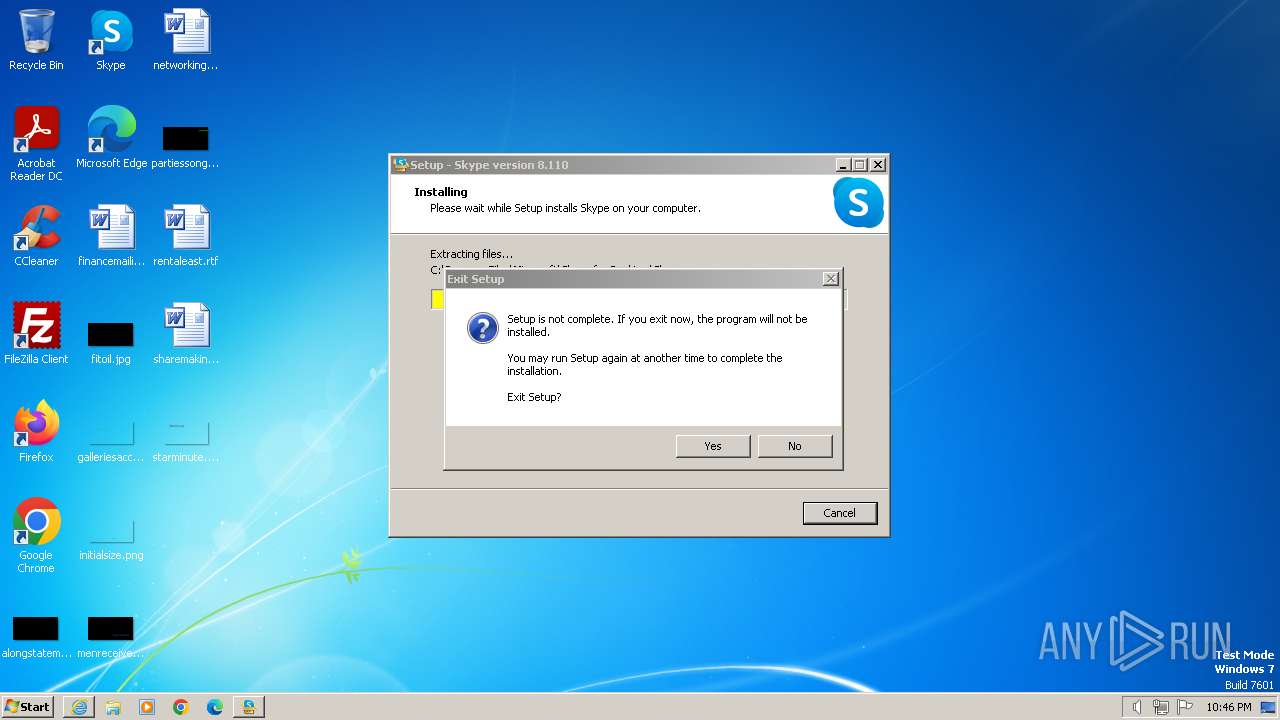
Drops the executable file immediately after the start
- Skype-Setup.exe (PID: 3728)
- Skype-Setup.exe (PID: 3956)
- Skype-Setup.tmp (PID: 2044)
SUSPICIOUS
Reads the Internet Settings
- Skype.exe (PID: 2380)
- Skype-Setup.tmp (PID: 2044)
Executable content was dropped or overwritten
- Skype-Setup.exe (PID: 3728)
- Skype-Setup.exe (PID: 3956)
- Skype-Setup.tmp (PID: 2044)
Searches for installed software
- Skype-Setup.tmp (PID: 2044)
Uses TASKKILL.EXE to kill process
- Skype-Setup.tmp (PID: 2044)
Process drops legitimate windows executable
- Skype-Setup.tmp (PID: 2044)
The process drops C-runtime libraries
- Skype-Setup.tmp (PID: 2044)
Reads the Windows owner or organization settings
- Skype-Setup.tmp (PID: 2044)
Application launched itself
- Skype.exe (PID: 2380)
INFO
Manual execution by a user
- SndVol.exe (PID: 2564)
- Skype.exe (PID: 2380)
- chrome.exe (PID: 3768)
Checks supported languages
- Skype.exe (PID: 3388)
- Skype.exe (PID: 3088)
- Skype.exe (PID: 3612)
- Skype.exe (PID: 2380)
- Skype.exe (PID: 3788)
- Skype-Setup.tmp (PID: 3868)
- Skype.exe (PID: 2812)
- Skype-Setup.exe (PID: 3956)
- Skype-Setup.tmp (PID: 2044)
- Skype-Setup.exe (PID: 3728)
Reads Environment values
- Skype.exe (PID: 2380)
Reads product name
- Skype.exe (PID: 2380)
Reads the computer name
- Skype.exe (PID: 3612)
- Skype.exe (PID: 3788)
- Skype.exe (PID: 3088)
- Skype.exe (PID: 2812)
- Skype-Setup.tmp (PID: 3868)
- Skype-Setup.tmp (PID: 2044)
- Skype.exe (PID: 2380)
Create files in a temporary directory
- Skype-Setup.exe (PID: 3728)
- Skype-Setup.exe (PID: 3956)
- Skype-Setup.tmp (PID: 2044)
Creates files in the program directory
- Skype-Setup.tmp (PID: 2044)
Application launched itself
- chrome.exe (PID: 3768)
- iexplore.exe (PID: 1936)
Creates files or folders in the user directory
- Skype.exe (PID: 2380)
Reads CPU info
- Skype.exe (PID: 2380)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
71
Monitored processes
28
Malicious processes
5
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 948 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --disable-quic --mojo-platform-channel-handle=3344 --field-trial-handle=1188,i,12688494637459489010,12552107149251144148,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1596 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --lang=en-US --service-sandbox-type=none --disable-quic --mojo-platform-channel-handle=1312 --field-trial-handle=1188,i,12688494637459489010,12552107149251144148,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | chrome.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1936 | "C:\Program Files\Internet Explorer\iexplore.exe" "https://loot-link.com/s?nHhL" | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2044 | "C:\Users\admin\AppData\Local\Temp\is-VBQES.tmp\Skype-Setup.tmp" /SL5="$70220,88729071,404480,C:\Users\admin\AppData\Roaming\Microsoft\Skype for Desktop\Skype-Setup.exe" /SPAWNWND=$401C4 /NOTIFYWND=$501E4 /silent !desktopicon | C:\Users\admin\AppData\Local\Temp\is-VBQES.tmp\Skype-Setup.tmp | Skype-Setup.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Setup/Uninstall Exit code: 0 Version: 51.1052.0.0 Modules
| |||||||||||||||
| 2204 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --lang=en-US --service-sandbox-type=none --disable-quic --mojo-platform-channel-handle=3932 --field-trial-handle=1188,i,12688494637459489010,12552107149251144148,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 2380 | "C:\Program Files\Microsoft\Skype for Desktop\Skype.exe" | C:\Program Files\Microsoft\Skype for Desktop\Skype.exe | explorer.exe | ||||||||||||
User: admin Company: Skype Technologies S.A. Integrity Level: MEDIUM Description: Skype Exit code: 1 Version: 8.110.0.215 Modules
| |||||||||||||||
| 2560 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:1936 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2564 | SndVol.exe -f 46269548 21962 | C:\Windows\System32\SndVol.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Volume Mixer Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2812 | "C:\Program Files\Microsoft\Skype for Desktop\Skype.exe" --type=gpu-process --user-data-dir="C:\Users\admin\AppData\Roaming\Microsoft\Skype for Desktop" --gpu-preferences=UAAAAAAAAADgAAAYAAAAAAAAAAAAAAAAAABgAAAAAAAwAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAEgAAAAAAAAASAAAAAAAAAAYAAAAAgAAABAAAAAAAAAAGAAAAAAAAAAQAAAAAAAAAAAAAAAOAAAAEAAAAAAAAAABAAAADgAAAAgAAAAAAAAACAAAAAAAAAA= --use-gl=angle --use-angle=swiftshader-webgl --mojo-platform-channel-handle=1860 --field-trial-handle=1304,i,9747442464012832337,5902488414071956311,131072 --enable-features=WinUseBrowserSpellChecker,WinUseHybridSpellChecker,WinrtGeolocationImplementation --disable-features=SpareRendererForSitePerProcess,WinRetrieveSuggestionsOnlyOnDemand /prefetch:2 | C:\Program Files\Microsoft\Skype for Desktop\Skype.exe | — | Skype.exe | |||||||||||
User: admin Company: Skype Technologies S.A. Integrity Level: LOW Description: Skype Exit code: 1 Version: 8.110.0.215 Modules
| |||||||||||||||
| 2972 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=8 --mojo-platform-channel-handle=1324 --field-trial-handle=1188,i,12688494637459489010,12552107149251144148,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
Total events
16 860
Read events
16 738
Write events
117
Delete events
5
Modification events
| (PID) Process: | (1936) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 0 | |||
| (PID) Process: | (1936) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 30847387 | |||
| (PID) Process: | (1936) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30847437 | |||
| (PID) Process: | (1936) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (1936) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (1936) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (1936) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (1936) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (1936) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (1936) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
Executable files
97
Suspicious files
107
Text files
59
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2560 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\24BD96D5497F70B3F510A6B53CD43F3E_3A89246FB90C5EE6620004F1AE0EB0EA | binary | |
MD5:595F36D0C4F118E1CC63BBFAB984681A | SHA256:C45D234100E2DD19DFB27E7EE6B83B92C0AC2A99CDE986CC6AB4E7F47D2A3D64 | |||
| 2560 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\24BD96D5497F70B3F510A6B53CD43F3E_3A89246FB90C5EE6620004F1AE0EB0EA | binary | |
MD5:28BAF5FD68DF59A9964B94CB39FFEE77 | SHA256:C5DFF2B8854FB9ED981EBDB1D6B621CF681BD1AC18AC44B14C138CD05352365B | |||
| 2560 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\s[1].htm | html | |
MD5:22F222E13F3F2222ED39AD6D6180E919 | SHA256:952BE296E36BA7D333C9842308936B310F8ECE4385E4B51223D113EE6D7B1DD9 | |||
| 2560 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\CAF4703619713E3F18D8A9D5D88D6288_F2DAF19C1F776537105D08FC8D978464 | binary | |
MD5:F635A309D3AC0BF9F315C6FE47E51EC0 | SHA256:1D25AB382026C1308EE8AFF9CD6C73C45815931093290308BD003A42AFCF4ECC | |||
| 2560 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\6BADA8974A10C4BD62CC921D13E43B18_28DEA62A0AE77228DD387E155AD0BA27 | binary | |
MD5:302A2BD8CB9F66F20AE5DC46E3A00B3C | SHA256:5FAD6489DAEF386887E5A43F496D6AF9E1B41DFD29DE5CE48FF3E2E1C00E6D0C | |||
| 2560 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\5IWPIAR9\detect-gpu.umd[1].js | text | |
MD5:8FB79352AE5DDEA93240F80C77375F68 | SHA256:7D042698109FAE4EB3BBD499AD3B4612FBB210072870AEA3713DC8D60D7C1363 | |||
| 2560 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\F2DDCD2B5F37625B82E81F4976CEE400_39B83AB13ED8E512BB8030E3672AA4B8 | der | |
MD5:2000765F318D5C015B2C7D6041AE4A35 | SHA256:F7C6BD25C9721C8284B379AD3E34189407EAEBBF1DC7CF2BF0AF00986D4899FD | |||
| 2560 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\6BADA8974A10C4BD62CC921D13E43B18_28DEA62A0AE77228DD387E155AD0BA27 | binary | |
MD5:288F50A0ED3E2F7E746236669F7430C4 | SHA256:081CBA7D6907A2E3E7927FBCC1516B64E44437F9D22E7A58D9ED30A517A4C987 | |||
| 2560 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\CAF4703619713E3F18D8A9D5D88D6288_A7725538C46DE2D0088EE44974E2CEBA | binary | |
MD5:AC89A852C2AAA3D389B2D2DD312AD367 | SHA256:0B720E19270C672F9B6E0EC40B468AC49376807DE08A814573FE038779534F45 | |||
| 2560 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\1[1].js | text | |
MD5:0898234CA853B910CC2D45936A17F40E | SHA256:778B51F624707370A20DDC334B27B545A30A4D9E3655065685262D41E8E915CF | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
16
TCP/UDP connections
54
DNS requests
38
Threats
3
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2560 | iexplore.exe | GET | 304 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?3c3c95d3439d4674 | unknown | — | — | unknown |
2560 | iexplore.exe | GET | 304 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?098bd4f8ce551810 | unknown | — | — | unknown |
2560 | iexplore.exe | GET | 200 | 142.250.185.99:80 | http://ocsp.pki.goog/gtsr1/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBQwkcLWD4LqGJ7bE7B1XZsEbmfwUAQU5K8rJnEaK0gnhS9SZizv8IkTcT4CDQIDvFCjJ1PwkYAi7fE%3D | unknown | binary | 724 b | unknown |
2560 | iexplore.exe | GET | 200 | 142.250.185.99:80 | http://ocsp.pki.goog/gsr1/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCEHe9DWzbNvka6iEPxPBY0w0%3D | unknown | binary | 1.41 Kb | unknown |
2560 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEAo3h2ReX7SMIk79G%2B0UDDw%3D | unknown | binary | 1.47 Kb | unknown |
2560 | iexplore.exe | GET | 200 | 142.250.185.99:80 | http://ocsp.pki.goog/gtsr1/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBQwkcLWD4LqGJ7bE7B1XZsEbmfwUAQU5K8rJnEaK0gnhS9SZizv8IkTcT4CDQIDvFNZazTHGPUBUGY%3D | unknown | binary | 724 b | unknown |
2560 | iexplore.exe | GET | 200 | 142.250.185.99:80 | http://ocsp.pki.goog/gts1c3/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEQDSGL5P0jvZghCoV3kPjCsM | unknown | binary | 472 b | unknown |
2560 | iexplore.exe | GET | 200 | 142.250.185.99:80 | http://ocsp.pki.goog/gts1c3/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEQDGBsq9RX4RYRKLGuOfdeTt | unknown | binary | 472 b | unknown |
1936 | iexplore.exe | GET | 304 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?d5d480e07c288d98 | unknown | — | — | unknown |
1936 | iexplore.exe | GET | 304 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?8456b65343b70b39 | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2560 | iexplore.exe | 172.67.134.201:443 | loot-link.com | CLOUDFLARENET | US | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2560 | iexplore.exe | 93.184.221.240:80 | ctldl.windowsupdate.com | EDGECAST | GB | whitelisted |
2560 | iexplore.exe | 142.250.185.99:80 | ocsp.pki.goog | GOOGLE | US | whitelisted |
2560 | iexplore.exe | 104.16.89.20:443 | cdn.jsdelivr.net | CLOUDFLARENET | — | shared |
2560 | iexplore.exe | 104.16.125.175:443 | unpkg.com | CLOUDFLARENET | — | shared |
2560 | iexplore.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
2560 | iexplore.exe | 142.250.186.42:443 | fonts.googleapis.com | GOOGLE | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
loot-link.com |
| unknown |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.pki.goog |
| whitelisted |
cdn.jsdelivr.net |
| whitelisted |
unpkg.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
fonts.googleapis.com |
| whitelisted |
fonts.gstatic.com |
| whitelisted |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2560 | iexplore.exe | Not Suspicious Traffic | INFO [ANY.RUN] A free CDN for open source projects (jsdelivr .net) |
2560 | iexplore.exe | Not Suspicious Traffic | INFO [ANY.RUN] Global content delivery network (unpkg .com) |
2560 | iexplore.exe | Not Suspicious Traffic | INFO [ANY.RUN] A free CDN for open source projects (jsdelivr .net) |
Process | Message |
|---|---|
Skype.exe | [0128/224538.272:ERROR:filesystem_win.cc(130)] GetFileAttributes C:\Users\admin\AppData\Roaming\Microsoft\Skype for Desktop\Crashpad\attachments\3a0ee62b-79ac-4cc3-bbd5-f65252e7a91f: The system cannot find the file specified. (0x2)
|