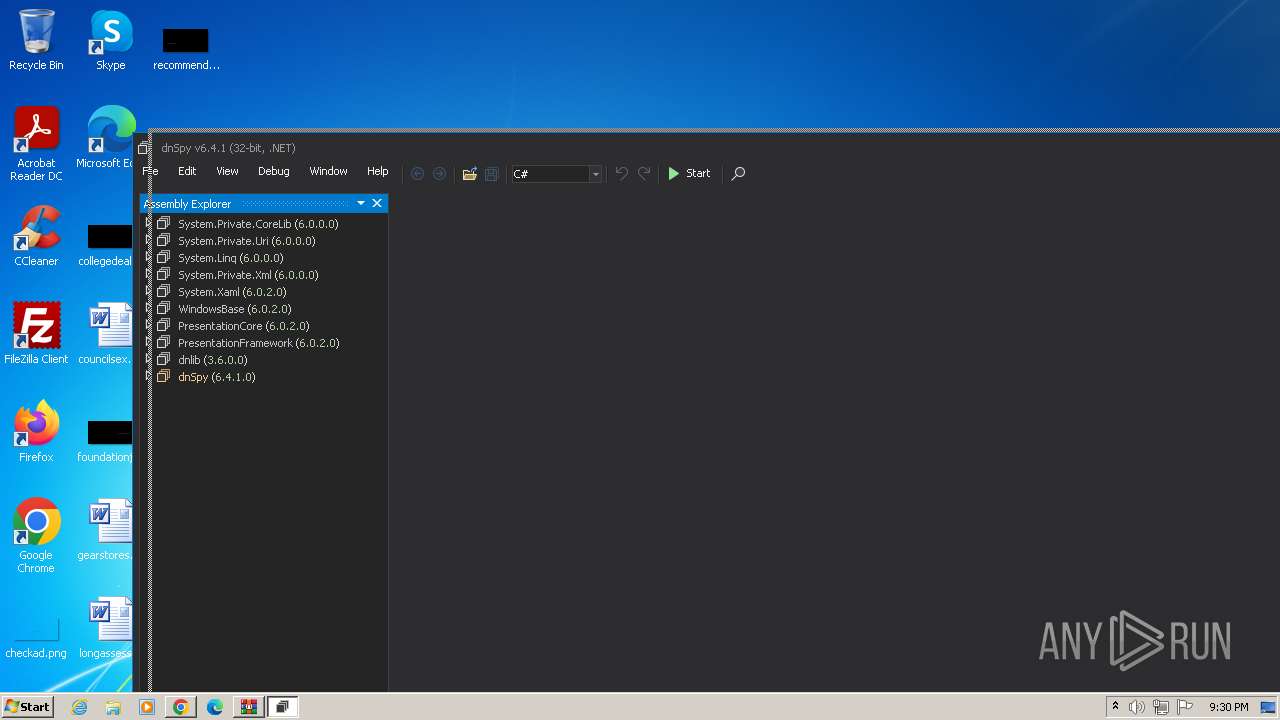
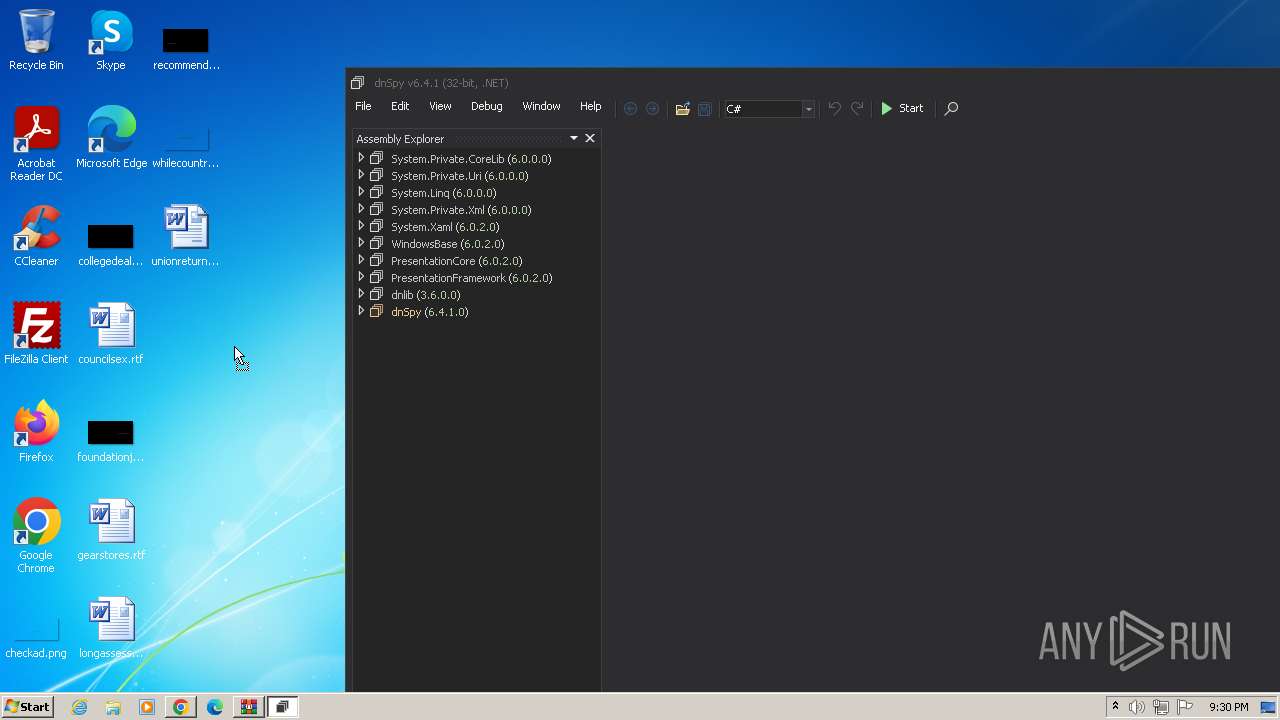
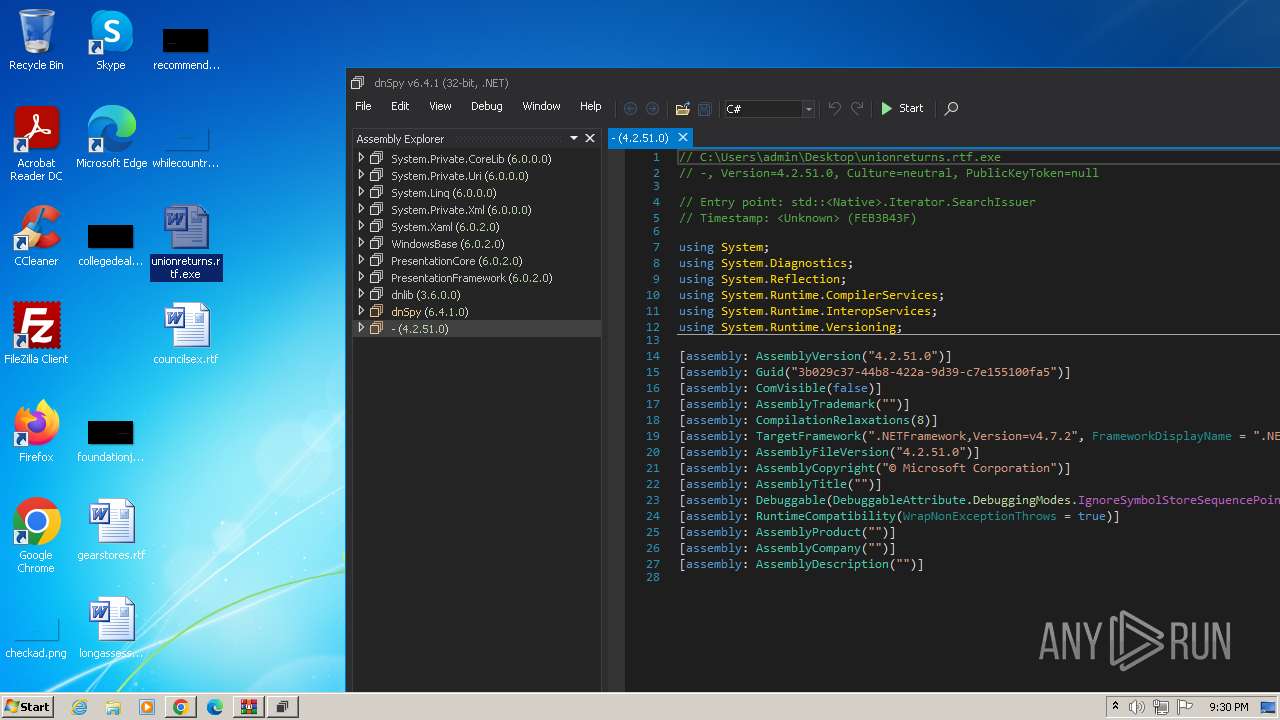
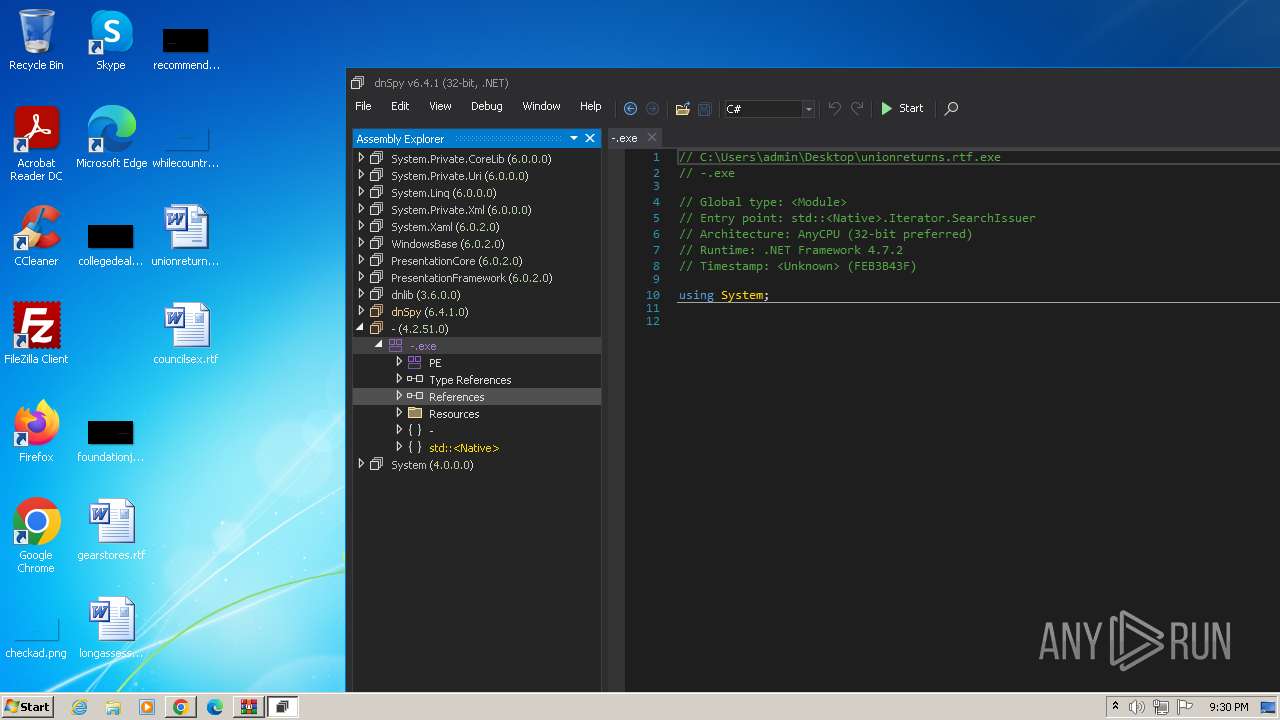
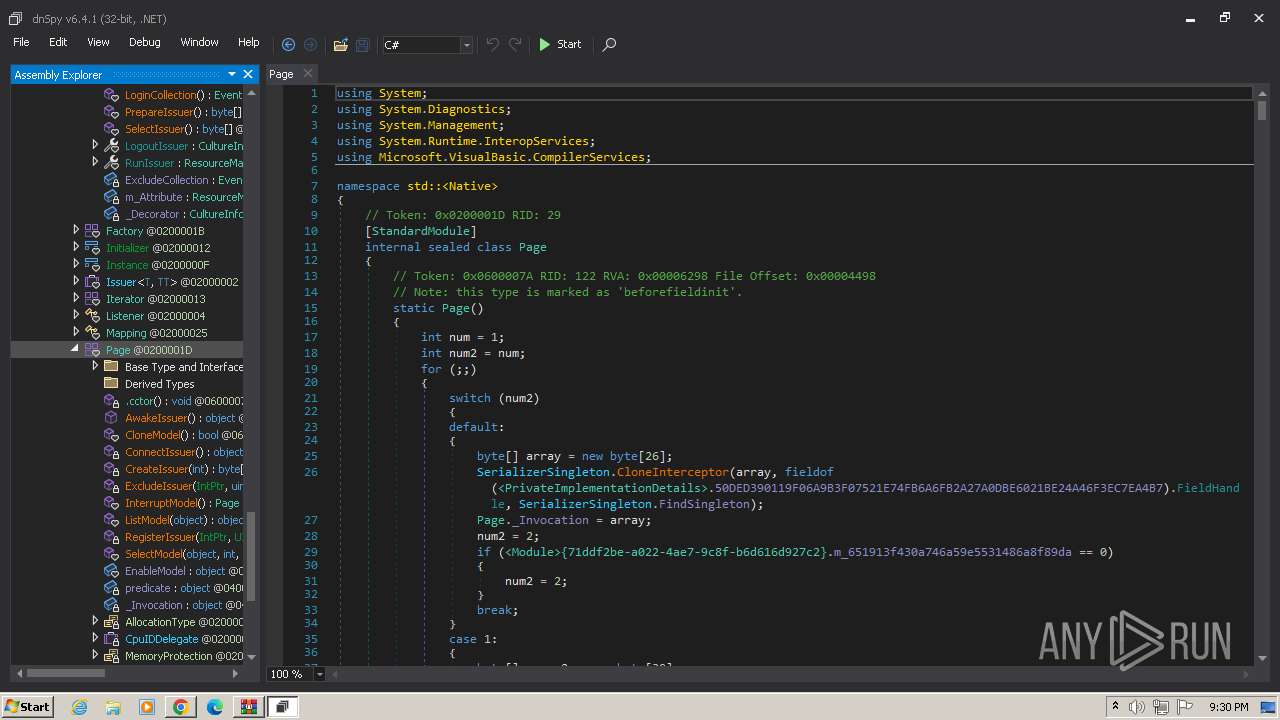
| File name: | unionreturns.rtf.exe |
| Full analysis: | https://app.any.run/tasks/7ccab669-6116-4527-a983-848eca6ad626 |
| Verdict: | Malicious activity |
| Analysis date: | December 02, 2023, 21:28:07 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386 Mono/.Net assembly, for MS Windows |
| MD5: | 4C2ED6148F7E4787FD8D1017BD81CC11 |
| SHA1: | 6ACF9A455C5CABE93D4AA625E7B70BC42200A533 |
| SHA256: | B73C950CCC87F4C49A9A5AC1B5E28936B07F40CEF46CFAC60C0ED43D15F2D994 |
| SSDEEP: | 24576:1oFbrcrnIxMfzcayo389j1GwZlZ/Zvi4z/v6HsEnWeonu2NAz1tsliem9B:1oFbrcrnIxMfzcayo389j1GwZlZ/ZviL |
MALICIOUS
Changes appearance of the Explorer extensions
- unionreturns.rtf.exe (PID: 2428)
Drops the executable file immediately after the start
- devenv.exe (PID: 1116)
- unionreturns.rtf.exe (PID: 2428)
REVENGERAT has been detected (YARA)
- admtools.exe (PID: 2184)
SUSPICIOUS
Reads the Internet Settings
- unionreturns.rtf.exe (PID: 2428)
- devenv.exe (PID: 1116)
- dnSpy.exe (PID: 3536)
Process drops legitimate windows executable
- WinRAR.exe (PID: 1160)
Connects to unusual port
- admtools.exe (PID: 2184)
The process creates files with name similar to system file names
- WinRAR.exe (PID: 1160)
INFO
Checks supported languages
- unionreturns.rtf.exe (PID: 2428)
- devenv.exe (PID: 1116)
- admtools.exe (PID: 2184)
- dnSpy.exe (PID: 3536)
- wmpnscfg.exe (PID: 3012)
Reads the computer name
- unionreturns.rtf.exe (PID: 2428)
- devenv.exe (PID: 1116)
- admtools.exe (PID: 2184)
- wmpnscfg.exe (PID: 3012)
- dnSpy.exe (PID: 3536)
Reads the machine GUID from the registry
- unionreturns.rtf.exe (PID: 2428)
- devenv.exe (PID: 1116)
- admtools.exe (PID: 2184)
- dnSpy.exe (PID: 3536)
The process uses the downloaded file
- chrome.exe (PID: 988)
- WinRAR.exe (PID: 1160)
Manual execution by a user
- dnSpy.exe (PID: 3536)
- chrome.exe (PID: 3452)
- wmpnscfg.exe (PID: 3012)
Application launched itself
- chrome.exe (PID: 3452)
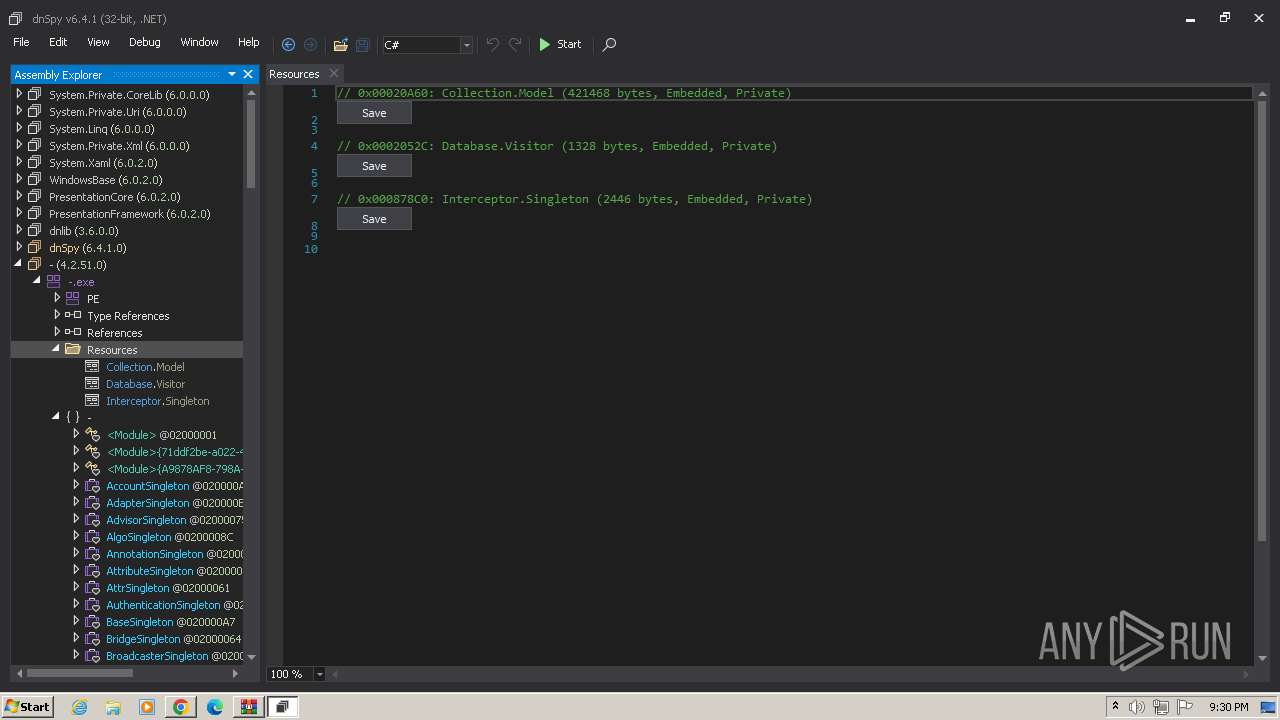
Creates files or folders in the user directory
- dnSpy.exe (PID: 3536)
Creates files in the program directory
- dnSpy.exe (PID: 3536)
Drops the executable file immediately after the start
- chrome.exe (PID: 4060)
- WinRAR.exe (PID: 1160)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Generic CIL Executable (.NET, Mono, etc.) (62) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (23.3) |
| .dll | | | Win32 Dynamic Link Library (generic) (5.5) |
| .exe | | | Win32 Executable (generic) (3.8) |
| .exe | | | Win16/32 Executable Delphi generic (1.7) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2105:05:31 07:12:31+02:00 |
| ImageFileCharacteristics: | Executable, No line numbers, No symbols, Large address aware, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 80 |
| CodeSize: | 558080 |
| InitializedDataSize: | 117248 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x8a2ce |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 4.2.51.0 |
| ProductVersionNumber: | 4.2.51.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | - |
| CompanyName: | - |
| FileDescription: | - |
| FileVersion: | 4.2.51.0 |
| InternalName: | -.exe |
| LegalCopyright: | © Microsoft Corporation |
| LegalTrademarks: | - |
| OriginalFileName: | -.exe |
| ProductName: | - |
| ProductVersion: | 4.2.51.0 |
| AssemblyVersion: | 4.2.51.0 |
Total processes
73
Monitored processes
29
Malicious processes
5
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 124 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --disable-quic --mojo-platform-channel-handle=1992 --field-trial-handle=1136,i,1764999150789524893,5813773545488116793,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 372 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --disable-quic --mojo-platform-channel-handle=992 --field-trial-handle=1136,i,1764999150789524893,5813773545488116793,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
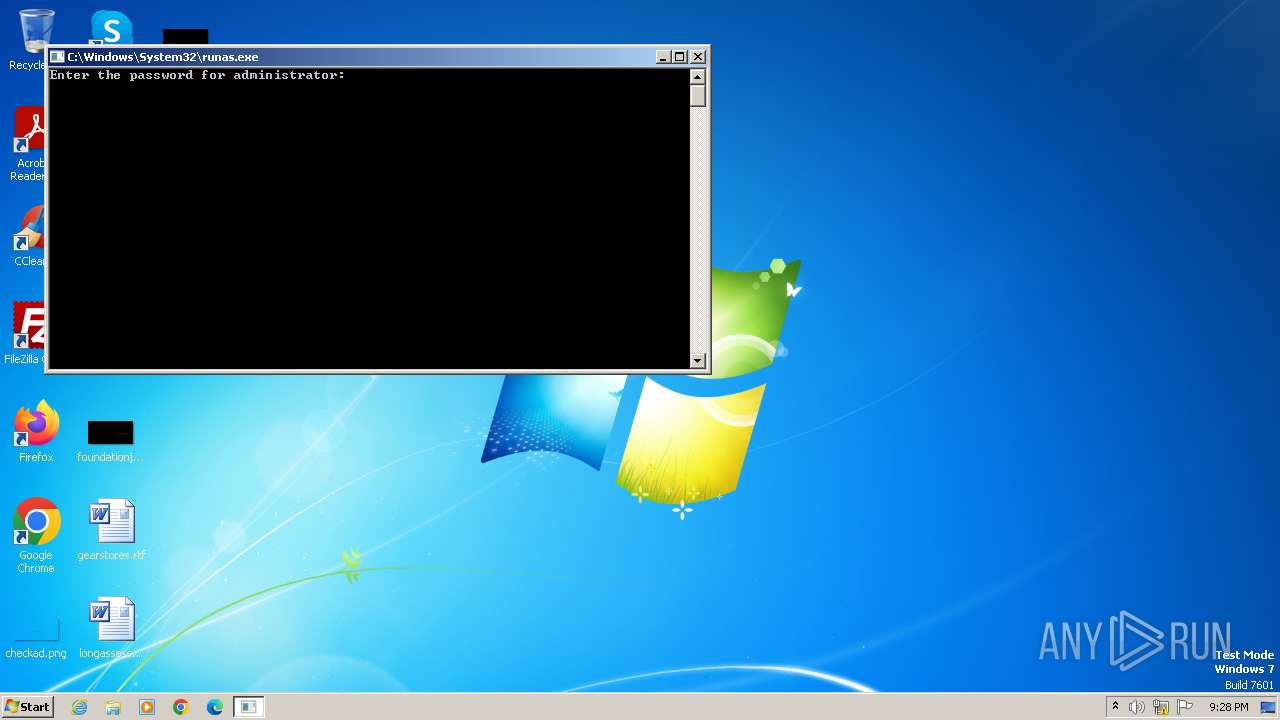
| 844 | "C:\Windows\System32\runas.exe" /user:administrator C:\Users\admin\Desktop\unionreturns.rtf.exe | C:\Windows\System32\runas.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Run As Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 860 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.FileUtilService --lang=en-US --service-sandbox-type=service --disable-quic --mojo-platform-channel-handle=1240 --field-trial-handle=1136,i,1764999150789524893,5813773545488116793,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 988 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=quarantine.mojom.Quarantine --lang=en-US --service-sandbox-type=none --disable-quic --mojo-platform-channel-handle=3652 --field-trial-handle=1136,i,1764999150789524893,5813773545488116793,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1116 | "C:\Users\Public\Documents\devenv.exe" | C:\Users\Public\Documents\devenv.exe | — | unionreturns.rtf.exe | |||||||||||
User: Administrator Integrity Level: HIGH Description: Exit code: 0 Version: 0.0.0.0 Modules
| |||||||||||||||
| 1160 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Downloads\dnSpy-net-win32.zip" | C:\Program Files\WinRAR\WinRAR.exe | — | chrome.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 1752 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --lang=en-US --service-sandbox-type=none --disable-quic --mojo-platform-channel-handle=3116 --field-trial-handle=1136,i,1764999150789524893,5813773545488116793,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1832 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --disable-quic --mojo-platform-channel-handle=3944 --field-trial-handle=1136,i,1764999150789524893,5813773545488116793,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 2184 | "C:\Users\Public\Documents\admtools.exe" | C:\Users\Public\Documents\admtools.exe | unionreturns.rtf.exe | ||||||||||||
User: Administrator Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
Total events
7 085
Read events
6 978
Write events
104
Delete events
3
Modification events
| (PID) Process: | (2428) unionreturns.rtf.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | delete value | Name: | ProxyBypass |
Value: 0 | |||
| (PID) Process: | (2428) unionreturns.rtf.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | delete value | Name: | IntranetName |
Value: 0 | |||
| (PID) Process: | (2428) unionreturns.rtf.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (2428) unionreturns.rtf.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (2428) unionreturns.rtf.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\Advanced |
| Operation: | write | Name: | Hidden |
Value: 2 | |||
| (PID) Process: | (2428) unionreturns.rtf.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\Advanced |
| Operation: | write | Name: | HideFileExt |
Value: 1 | |||
| (PID) Process: | (1116) devenv.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (1116) devenv.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (1116) devenv.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (1116) devenv.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
Executable files
1 686
Suspicious files
247
Text files
51
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2428 | unionreturns.rtf.exe | C:\Users\Administrator\ntuser.dat.LOG2.exe | executable | |
MD5:4C2ED6148F7E4787FD8D1017BD81CC11 | SHA256:B73C950CCC87F4C49A9A5AC1B5E28936B07F40CEF46CFAC60C0ED43D15F2D994 | |||
| 2428 | unionreturns.rtf.exe | C:\RCX77F8.tmp | executable | |
MD5:1EFB8BF8256E1FC52E81CF0BEFDE0258 | SHA256:8A2D9A2D15D9132AAAE4F188D122D7E9F9AB10C18213BD265D44DF17EA484798 | |||
| 2428 | unionreturns.rtf.exe | C:\RCX78C9.tmp | executable | |
MD5:4D6908776FE690E020A5A200C44F637D | SHA256:B83AFC9D7F09956714C40AB676A474838AED0D0F14265DBA6A386702F8239BF6 | |||
| 2428 | unionreturns.rtf.exe | C:\RCX7818.tmp | executable | |
MD5:4C2ED6148F7E4787FD8D1017BD81CC11 | SHA256:B73C950CCC87F4C49A9A5AC1B5E28936B07F40CEF46CFAC60C0ED43D15F2D994 | |||
| 2428 | unionreturns.rtf.exe | C:\RCX77C8.tmp | executable | |
MD5:F42955F7E4FCD31F7A9743A5A1E1D228 | SHA256:BE8EB4911479B562B160328D1FB533B195020783B14DBBE9AD13442BC364B899 | |||
| 2428 | unionreturns.rtf.exe | C:\Users\Public\Documents\devenv.exe | executable | |
MD5:3FE2B1337F824DFCBF545CCFFB5454F3 | SHA256:001D3941132DD30110E1A650ABBC4DD49D352F06D08D491A4F6503ACFF875E67 | |||
| 2428 | unionreturns.rtf.exe | C:\RCX7848.tmp | executable | |
MD5:1444A3DC0CCD19FE027F7001AC1AC39E | SHA256:7AB6E72F83C7581A4AE6E03BDC51F6D4E4BEC8274AC9285C17FBF5935D7A45F2 | |||
| 2428 | unionreturns.rtf.exe | C:\Users\Public\Documents\admtools.exe | executable | |
MD5:86CA40FFE87618AD86BD49E5A9B6DA69 | SHA256:9BD3D486E541B5C7E9EEC713B6162FAF97B21C0CF61A56A996F838A6F4F0BE59 | |||
| 2428 | unionreturns.rtf.exe | C:\RCX76CA.tmp | executable | |
MD5:4C2ED6148F7E4787FD8D1017BD81CC11 | SHA256:B73C950CCC87F4C49A9A5AC1B5E28936B07F40CEF46CFAC60C0ED43D15F2D994 | |||
| 2428 | unionreturns.rtf.exe | C:\RCX78A9.tmp | executable | |
MD5:469EFCC91BE9C53AA80E0E170FFBEB78 | SHA256:9E26960FDAA595FE4C417910C1F13A1AA30068A2BB55385290ABD145F159F576 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
32
TCP/UDP connections
40
DNS requests
47
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
868 | svchost.exe | HEAD | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/adhioj45hzjkfunn7ccrbqyyhu3q_20230916.567854667.14/obedbbhbpmojnkanicioggnmelmoomoc_20230916.567854667.14_all_ENUS500000_lr7434qyx46lykosg2elaepqdi.crx3 | unknown | — | — | unknown |
868 | svchost.exe | GET | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/ad3rm3ciqs3fjr4bc4x5vwuildeq_9.49.1/gcmjkmgdlgnkkcocmoeiminaijmmjnii_9.49.1_all_ixzyrcu7pvmgu5pjv6enfqq6wa.crx3 | unknown | binary | 34.2 Kb | unknown |
868 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/adhioj45hzjkfunn7ccrbqyyhu3q_20230916.567854667.14/obedbbhbpmojnkanicioggnmelmoomoc_20230916.567854667.14_all_ENUS500000_lr7434qyx46lykosg2elaepqdi.crx3 | unknown | binary | 582 Kb | unknown |
868 | svchost.exe | HEAD | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/ad3rm3ciqs3fjr4bc4x5vwuildeq_9.49.1/gcmjkmgdlgnkkcocmoeiminaijmmjnii_9.49.1_all_ixzyrcu7pvmgu5pjv6enfqq6wa.crx3 | unknown | binary | 582 Kb | unknown |
868 | svchost.exe | HEAD | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/k4ldha5kevpu7qn7k4s3mznvgu_4.10.2710.0/oimompecagnajdejgnnjijobebaeigek_4.10.2710.0_win32_ad2kbvs6jks3au5dsxn7cqflsiiq.crx3 | unknown | binary | 34.2 Kb | unknown |
868 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/adhioj45hzjkfunn7ccrbqyyhu3q_20230916.567854667.14/obedbbhbpmojnkanicioggnmelmoomoc_20230916.567854667.14_all_ENUS500000_lr7434qyx46lykosg2elaepqdi.crx3 | unknown | binary | 1.46 Mb | unknown |
868 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/adhioj45hzjkfunn7ccrbqyyhu3q_20230916.567854667.14/obedbbhbpmojnkanicioggnmelmoomoc_20230916.567854667.14_all_ENUS500000_lr7434qyx46lykosg2elaepqdi.crx3 | unknown | binary | 10.0 Kb | unknown |
868 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/adhioj45hzjkfunn7ccrbqyyhu3q_20230916.567854667.14/obedbbhbpmojnkanicioggnmelmoomoc_20230916.567854667.14_all_ENUS500000_lr7434qyx46lykosg2elaepqdi.crx3 | unknown | binary | 6.74 Kb | unknown |
868 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/adhioj45hzjkfunn7ccrbqyyhu3q_20230916.567854667.14/obedbbhbpmojnkanicioggnmelmoomoc_20230916.567854667.14_all_ENUS500000_lr7434qyx46lykosg2elaepqdi.crx3 | unknown | binary | 9.96 Kb | unknown |
868 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/adhioj45hzjkfunn7ccrbqyyhu3q_20230916.567854667.14/obedbbhbpmojnkanicioggnmelmoomoc_20230916.567854667.14_all_ENUS500000_lr7434qyx46lykosg2elaepqdi.crx3 | unknown | binary | 9.87 Kb | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2588 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
2184 | admtools.exe | 45.84.227.157:50 | pex.0x01.cf | Beget LLC | RU | unknown |
3452 | chrome.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
3288 | chrome.exe | 66.102.1.84:443 | accounts.google.com | GOOGLE | US | unknown |
3288 | chrome.exe | 142.250.185.99:443 | clientservices.googleapis.com | GOOGLE | US | whitelisted |
3288 | chrome.exe | 142.250.187.100:443 | www.google.com | GOOGLE | US | whitelisted |
3288 | chrome.exe | 172.217.16.131:443 | update.googleapis.com | GOOGLE | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
pex.0x01.cf |
| unknown |
api.peer2profit.com |
| unknown |
clientservices.googleapis.com |
| whitelisted |
accounts.google.com |
| shared |
www.google.com |
| whitelisted |
update.googleapis.com |
| whitelisted |
github.com |
| shared |
safebrowsing.googleapis.com |
| whitelisted |
github.githubassets.com |
| whitelisted |
avatars.githubusercontent.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1080 | svchost.exe | Misc activity | ET INFO DNS Query for Suspicious .cf Domain |
Process | Message |
|---|---|
dnSpy.exe | Profiler was prevented from loading notification profiler due to app settings.
Process ID (decimal): 3536. Message ID: [0x2509].
|