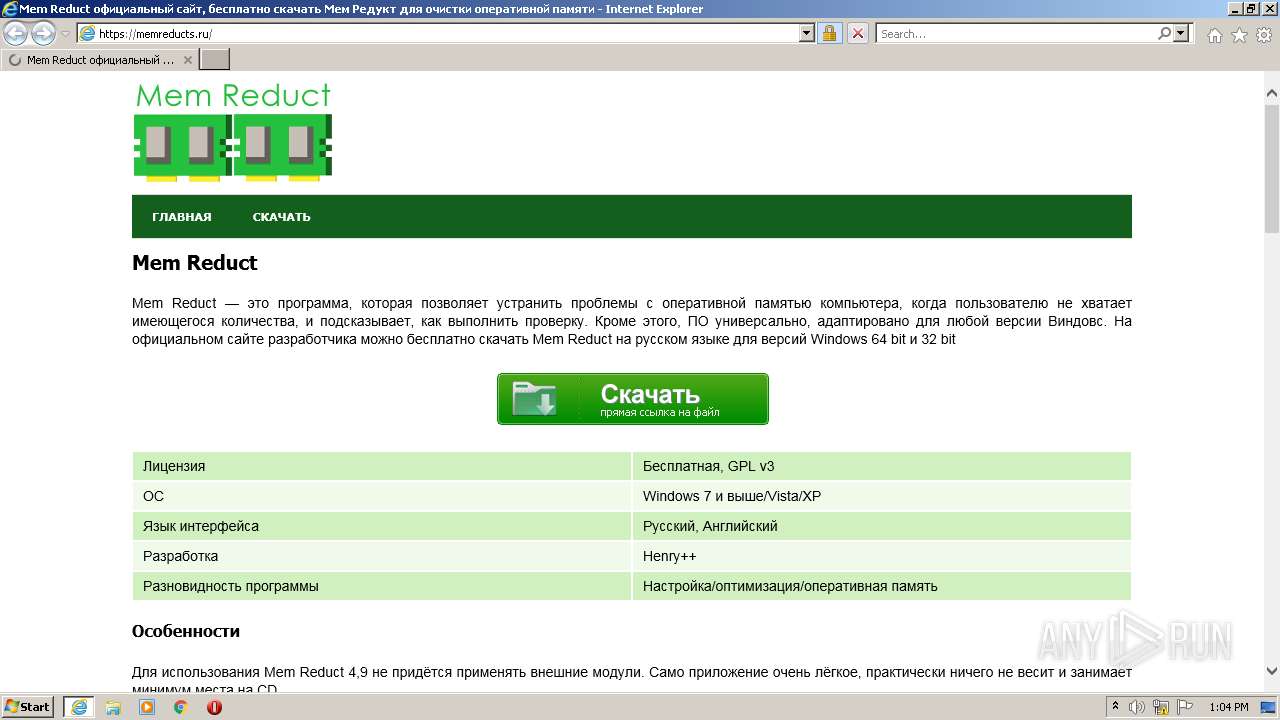
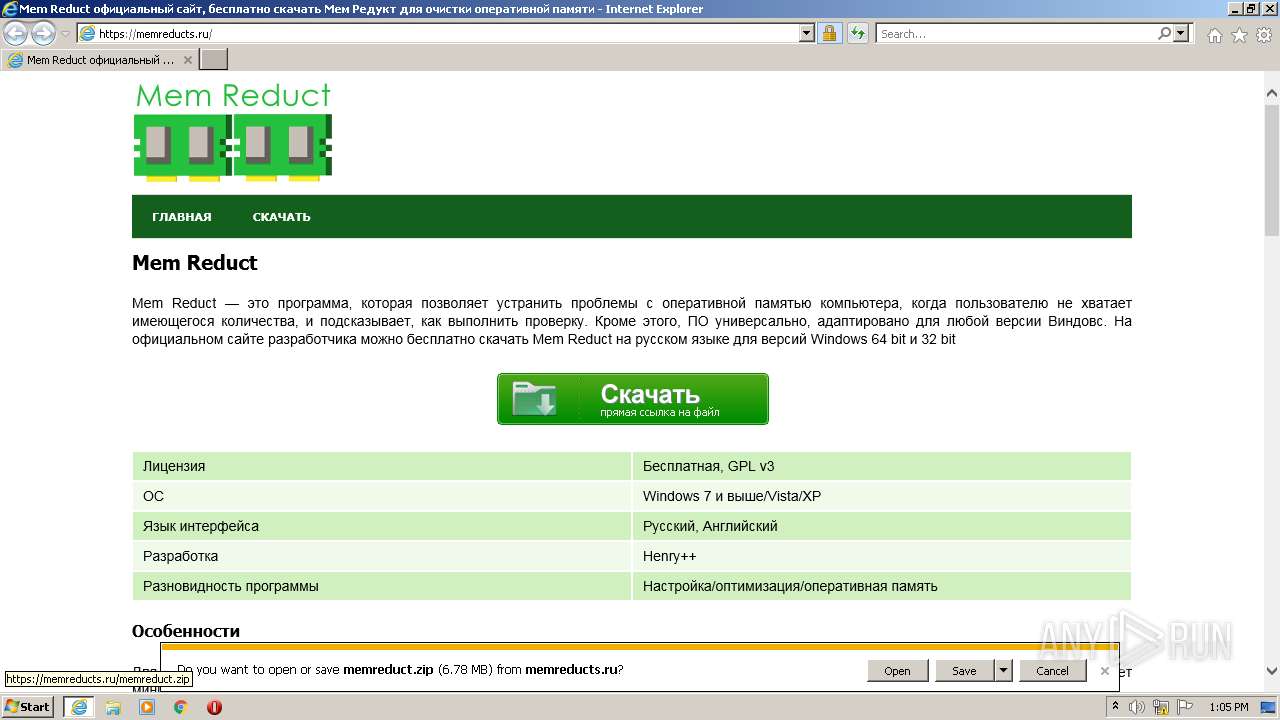
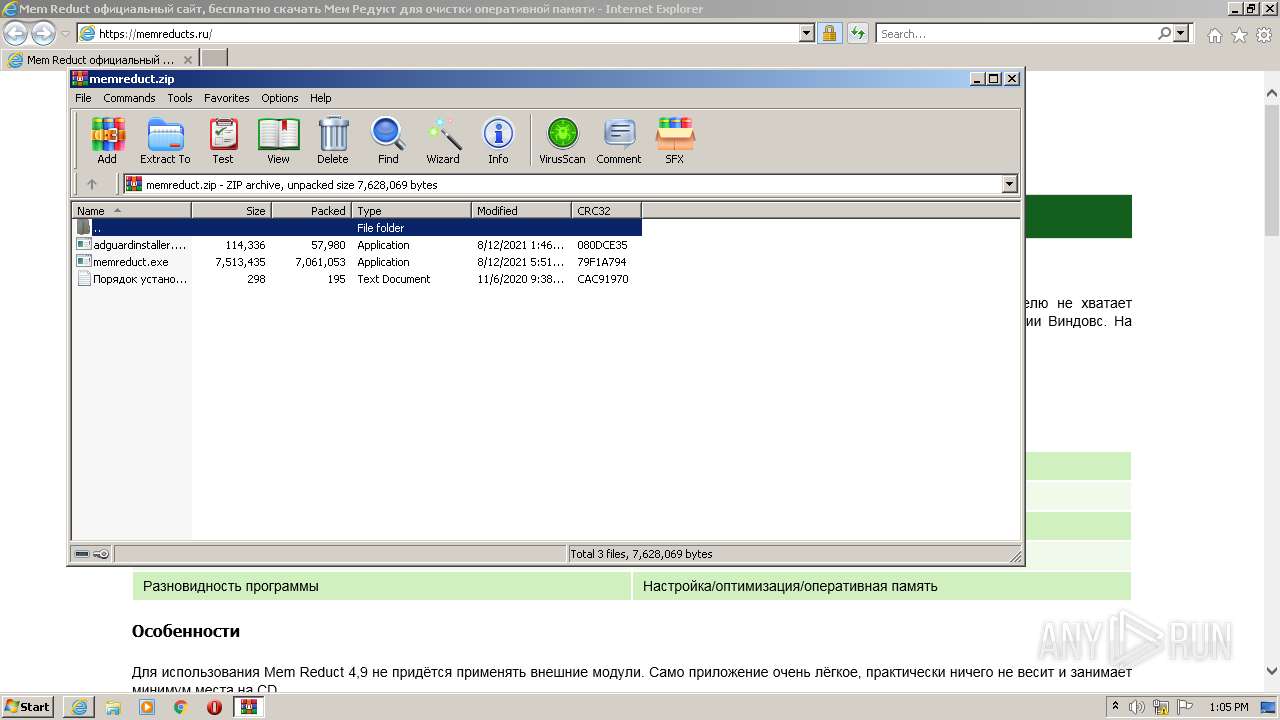
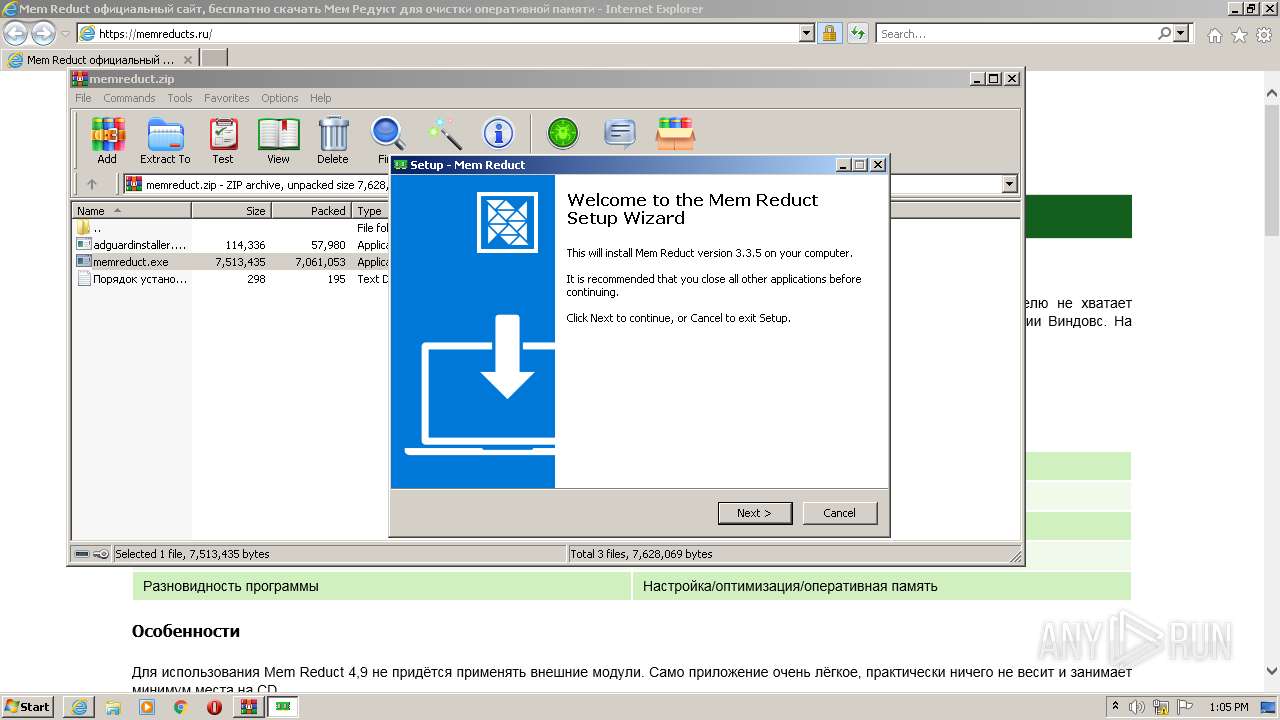
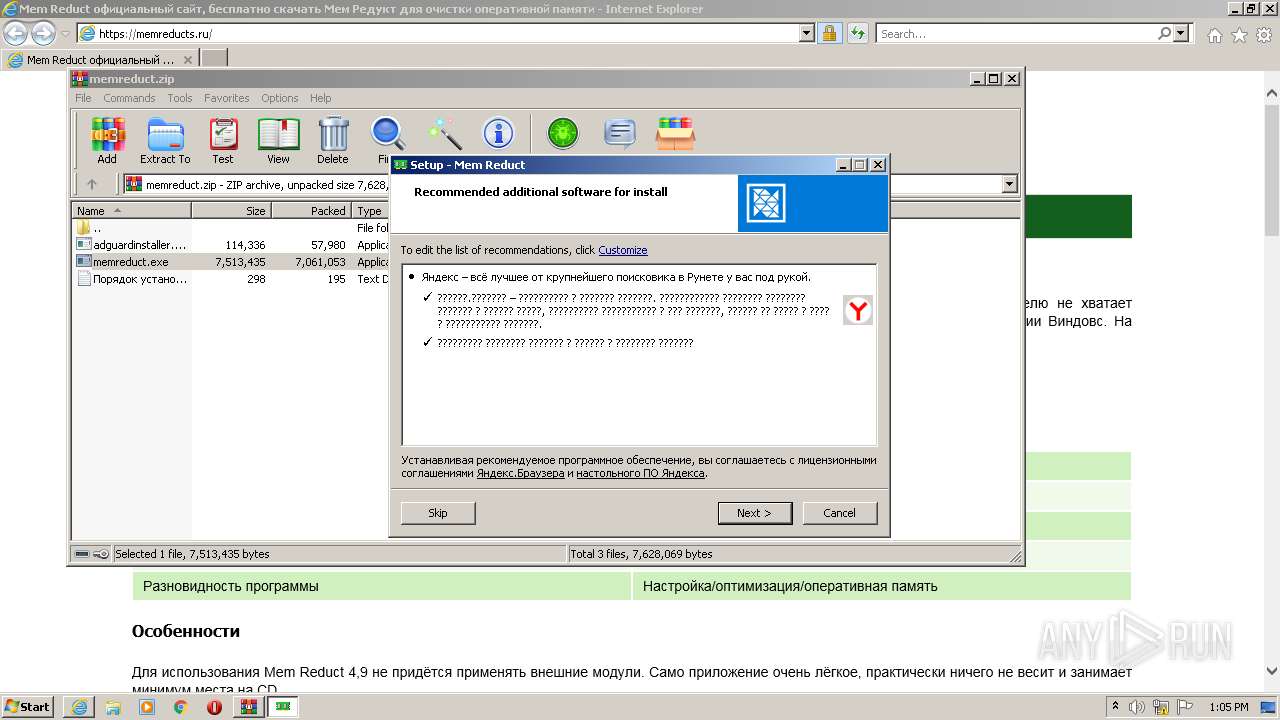
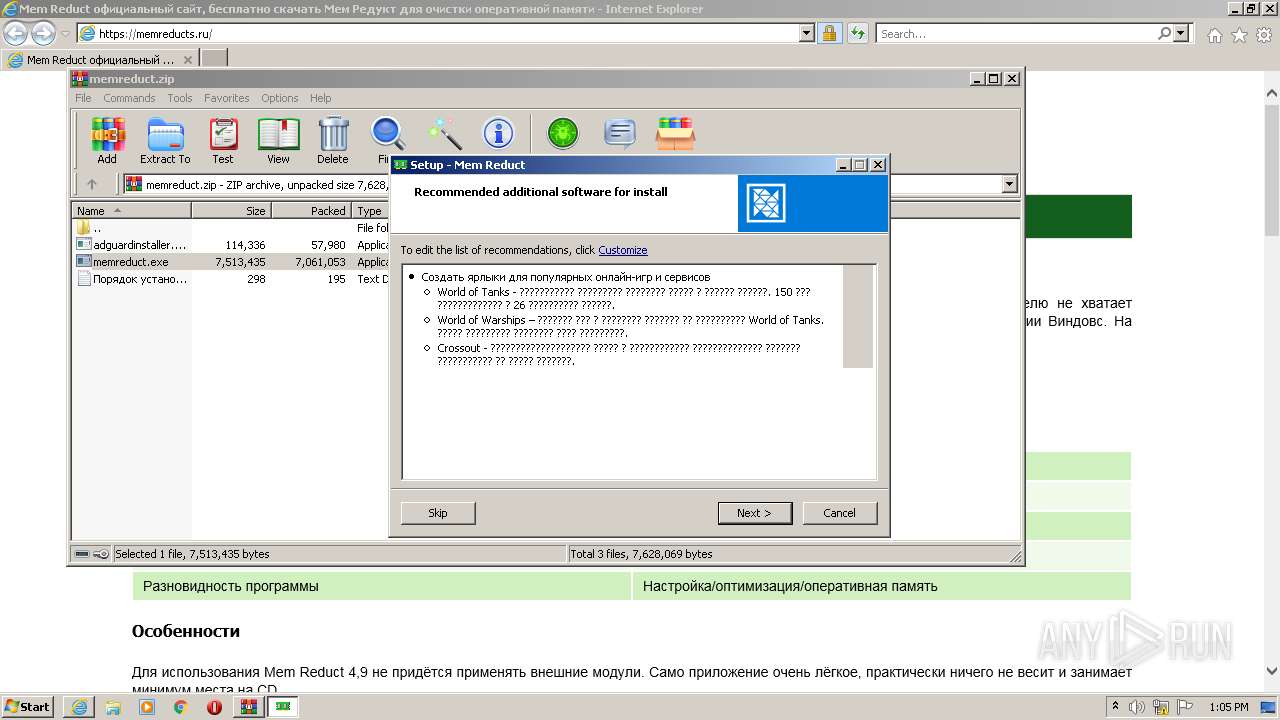
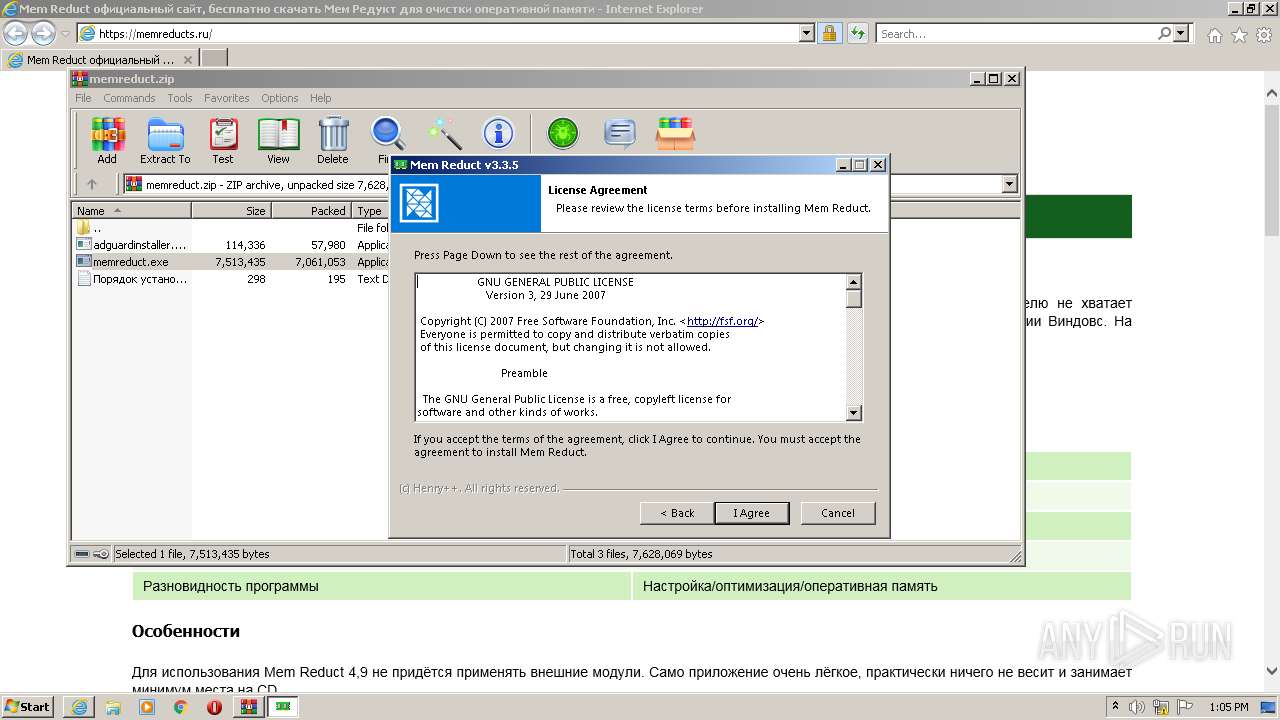
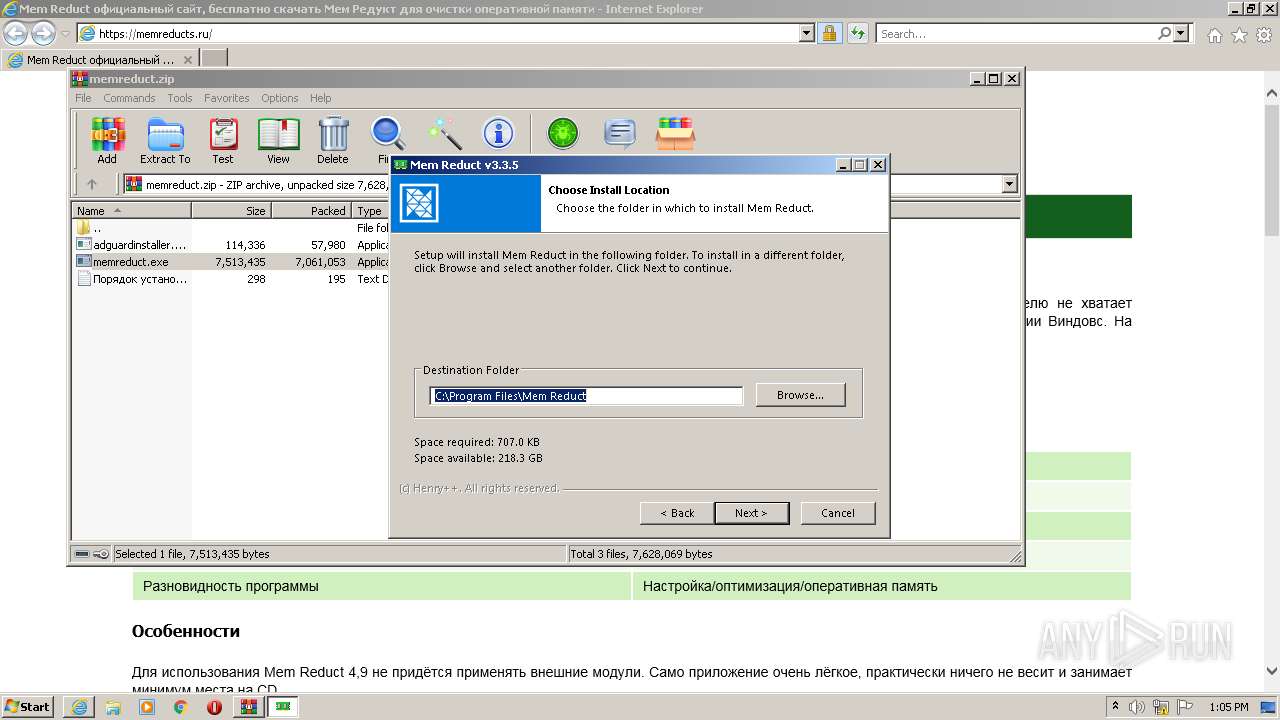
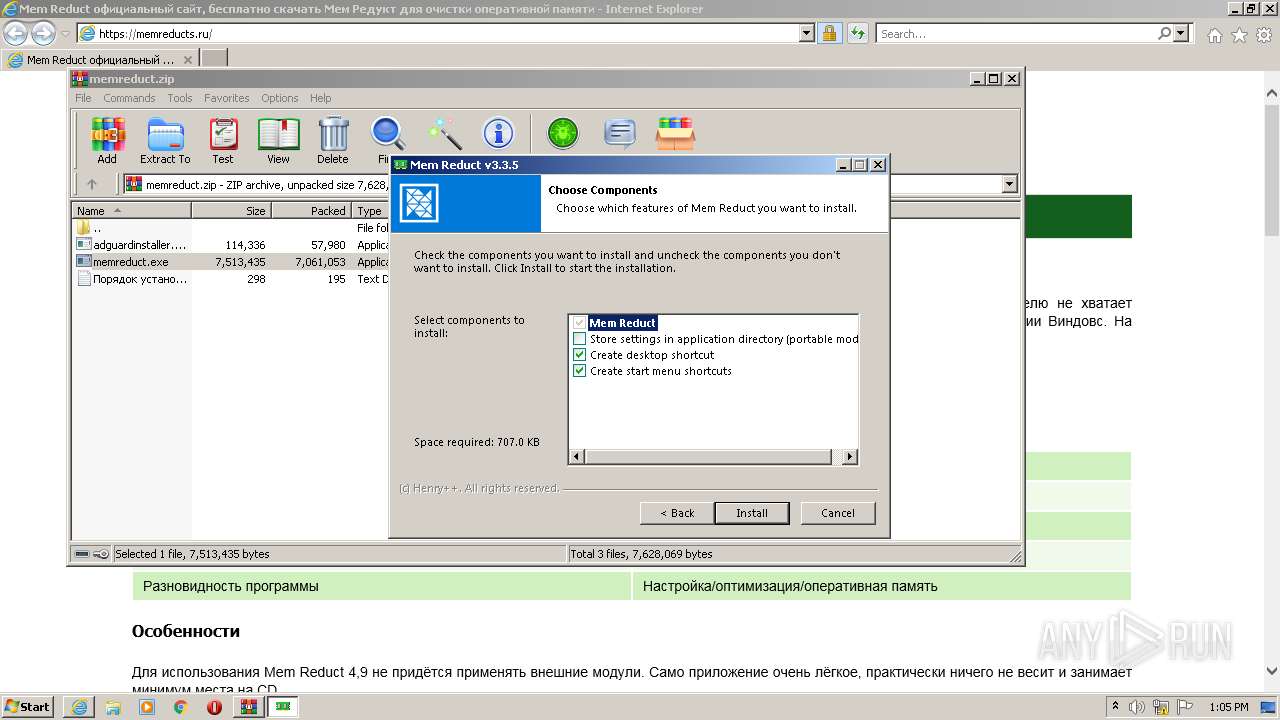
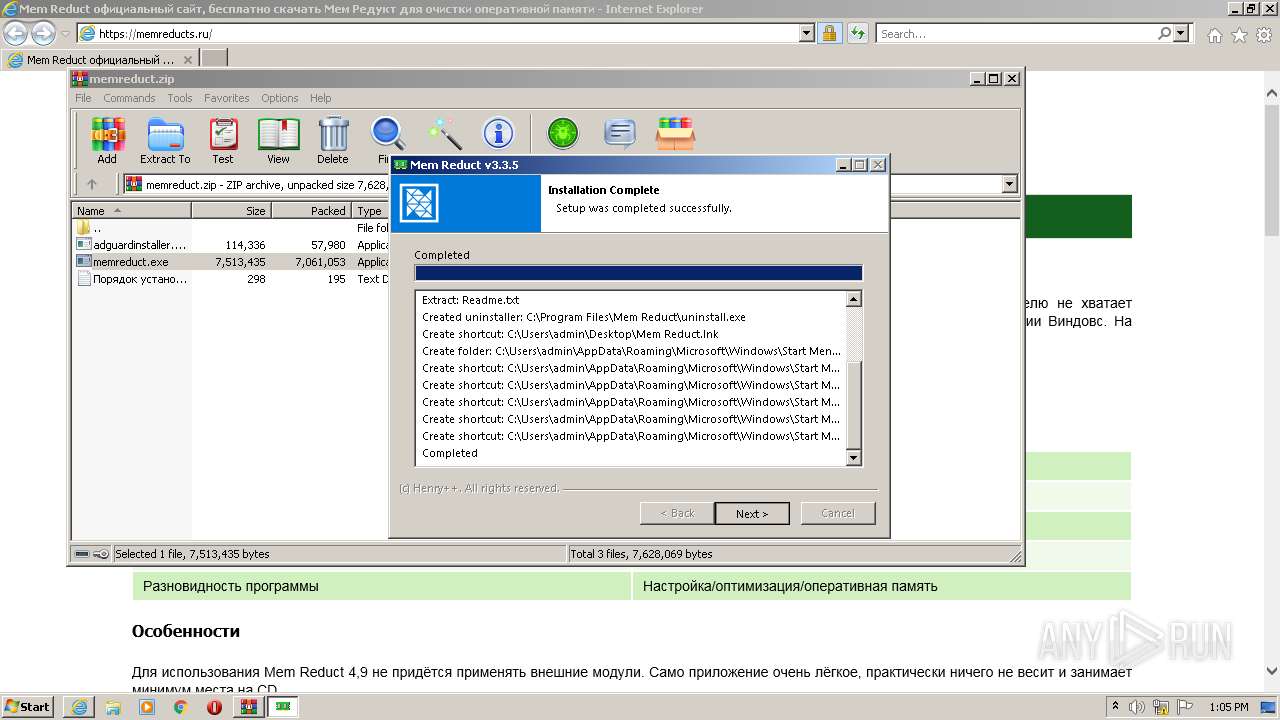
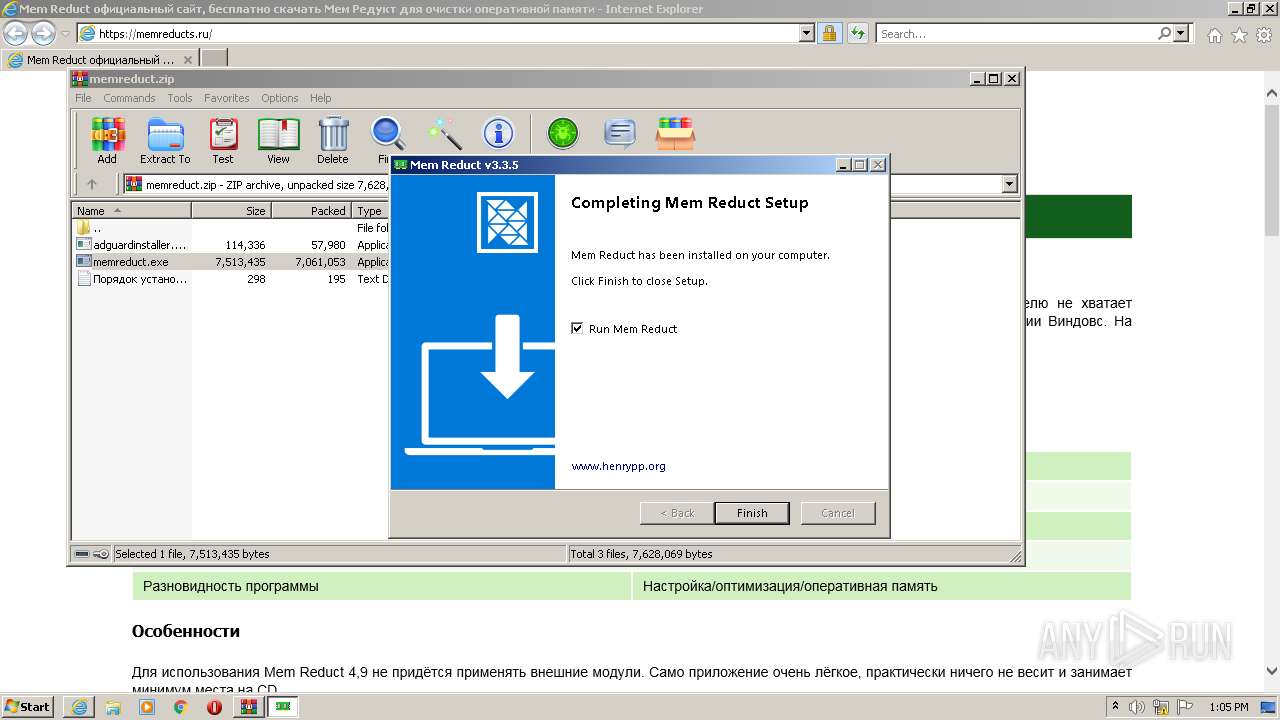
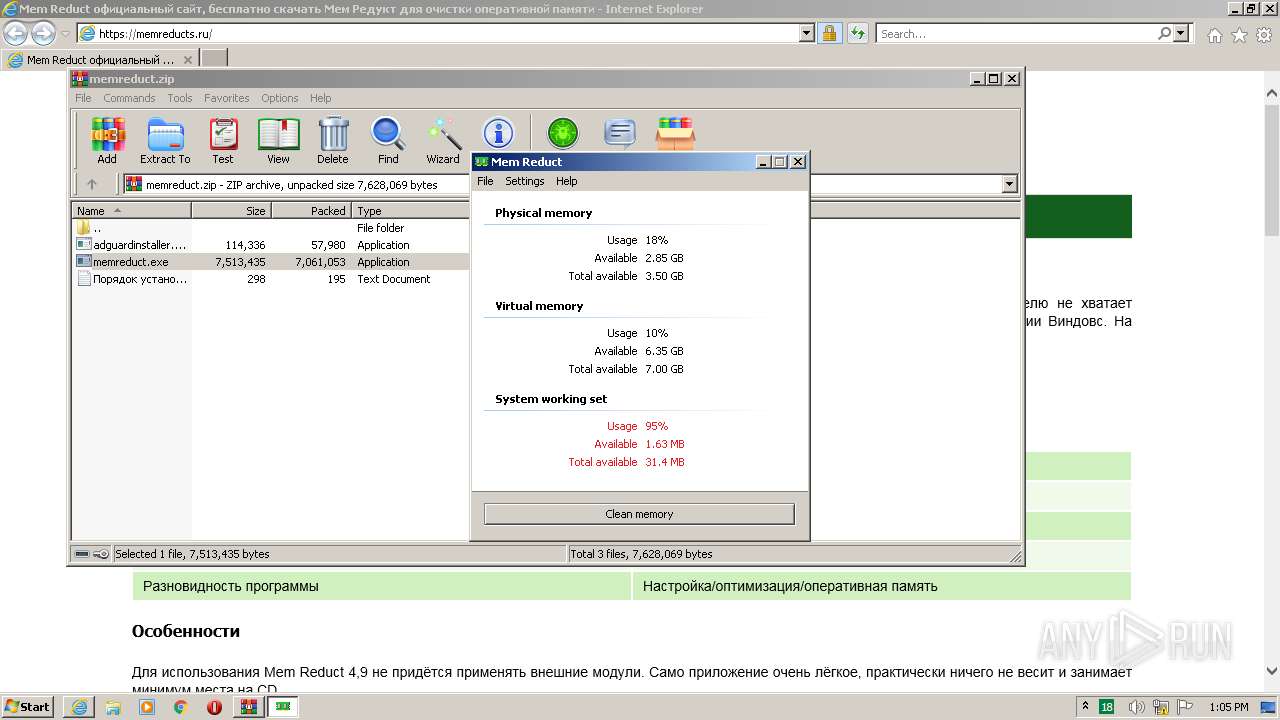
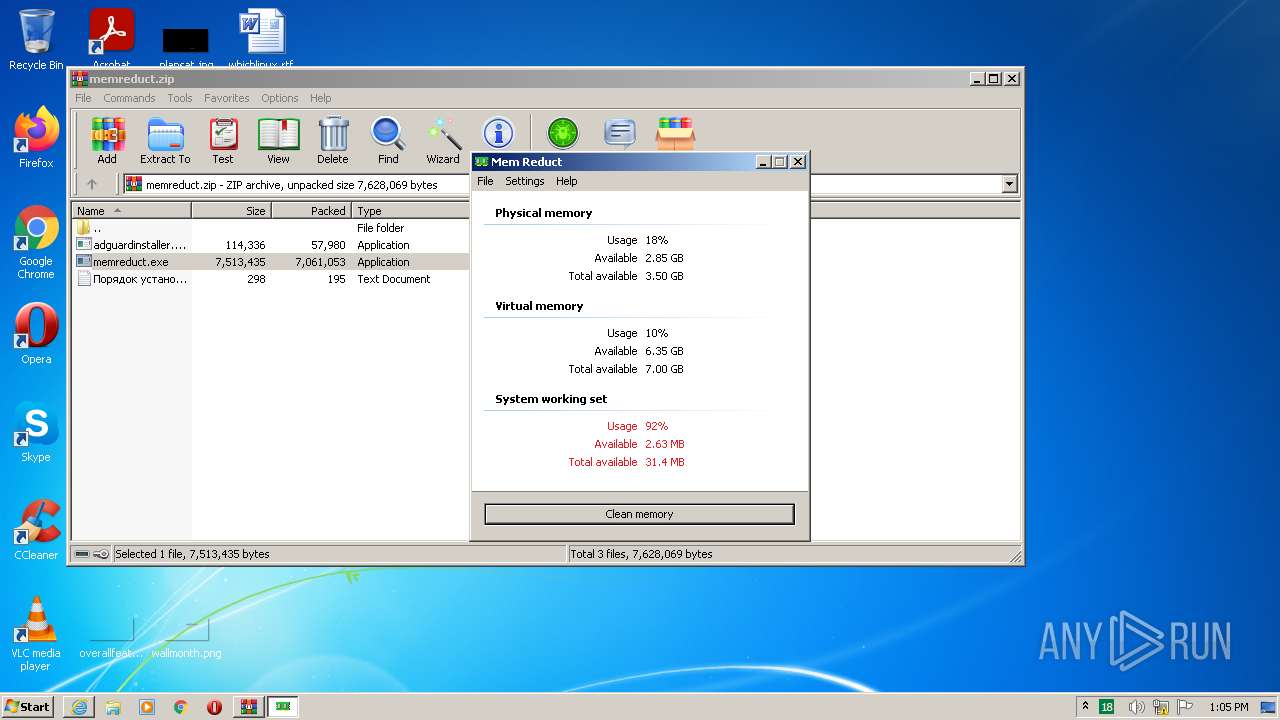
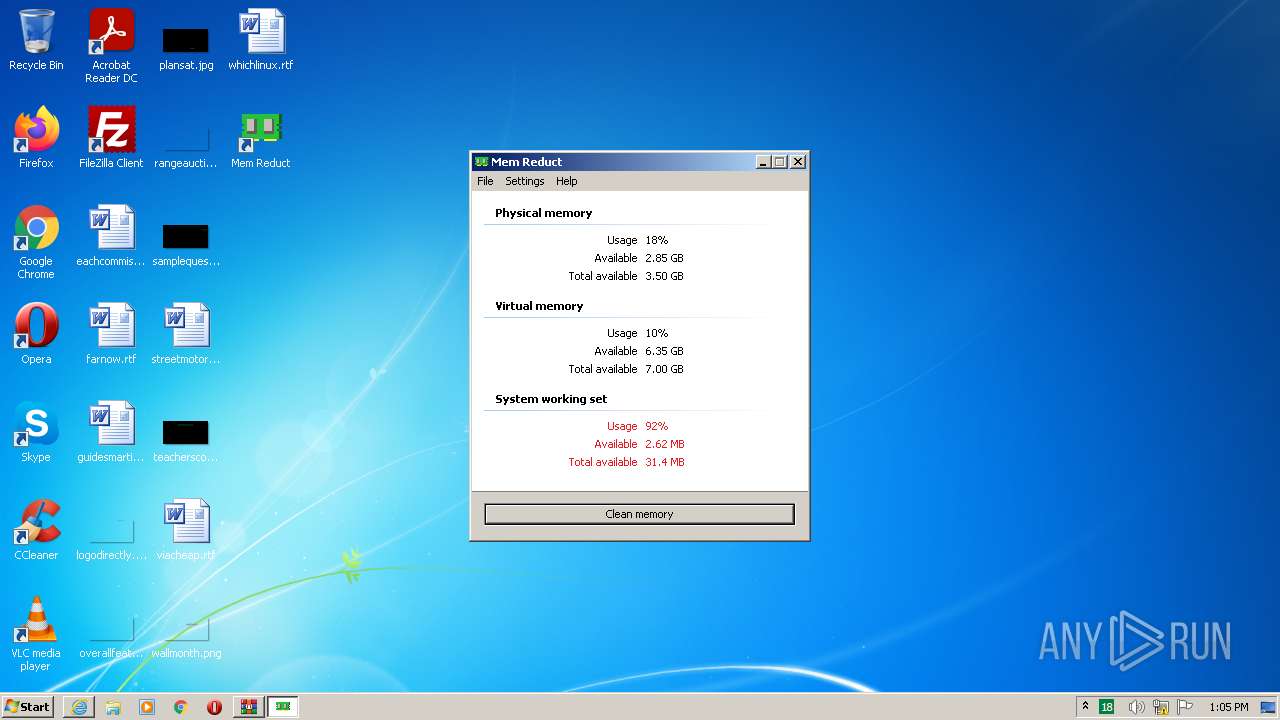
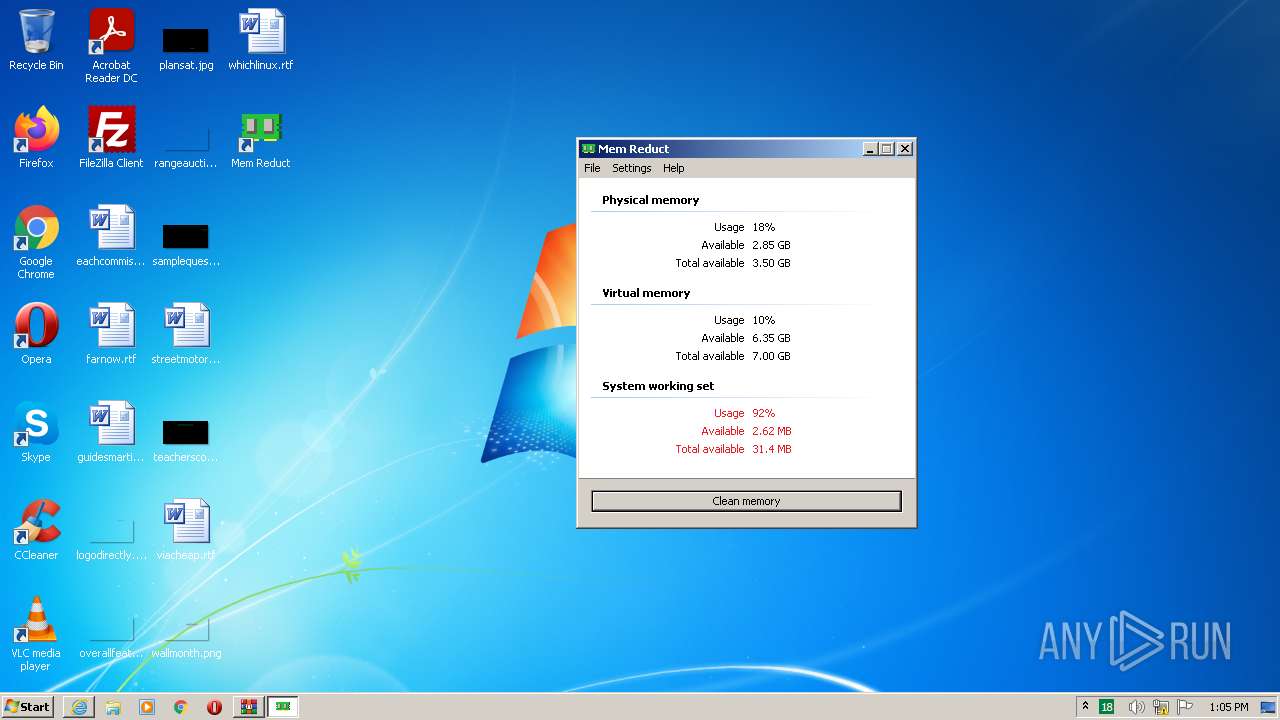
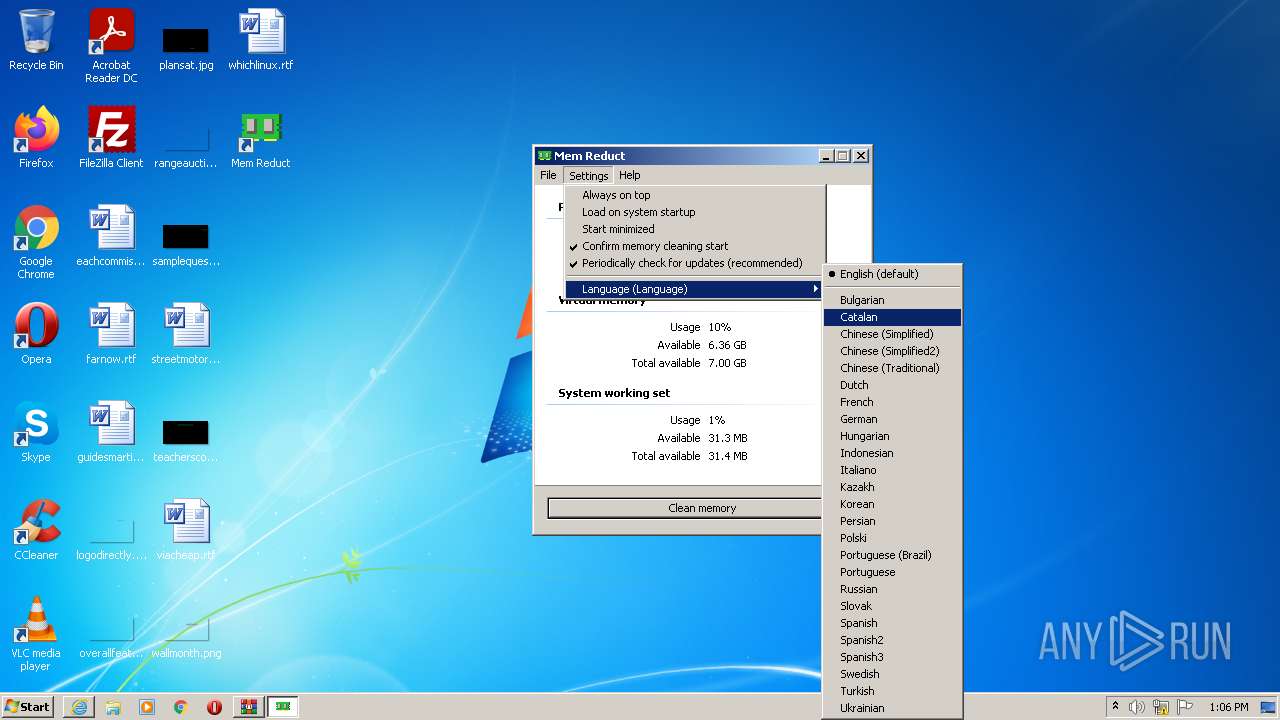
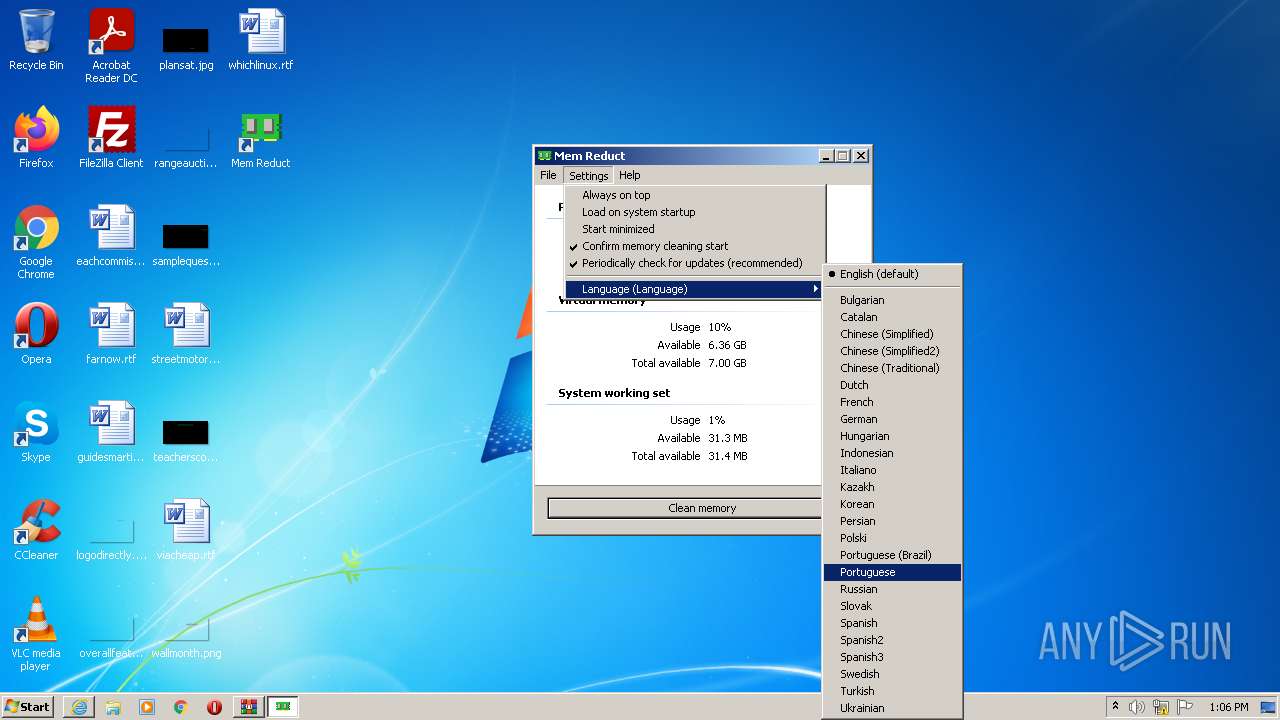
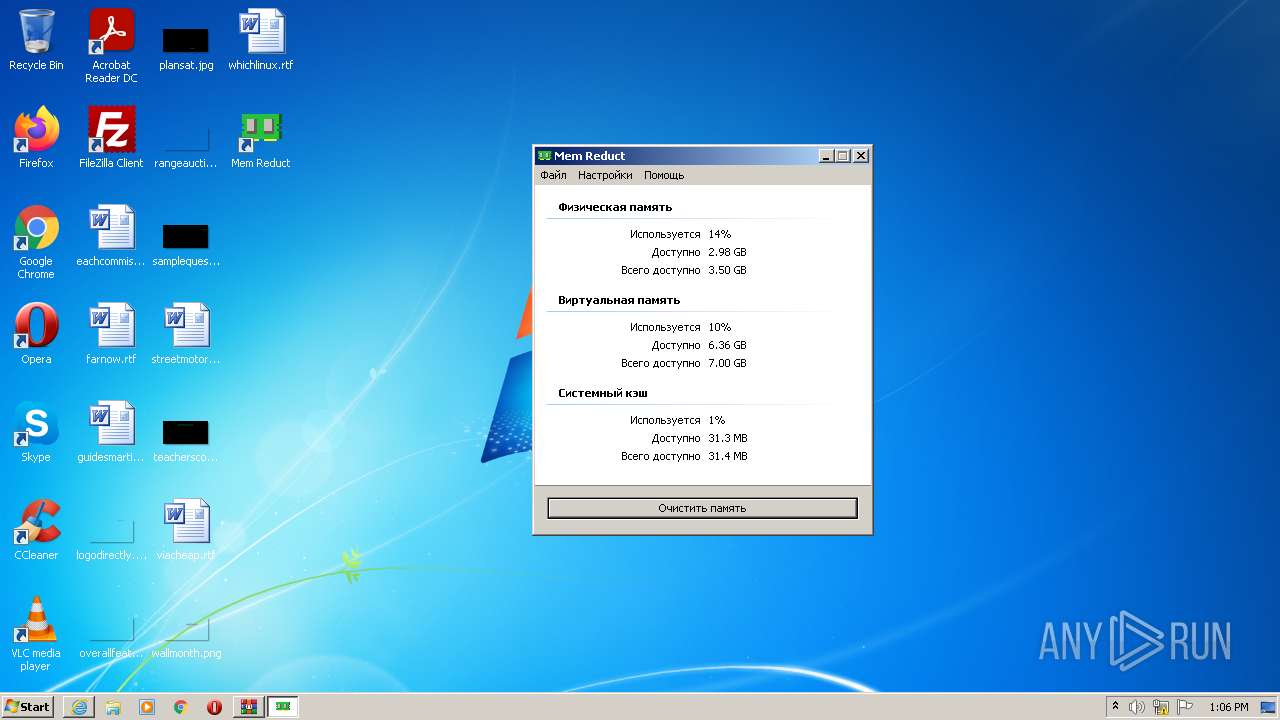
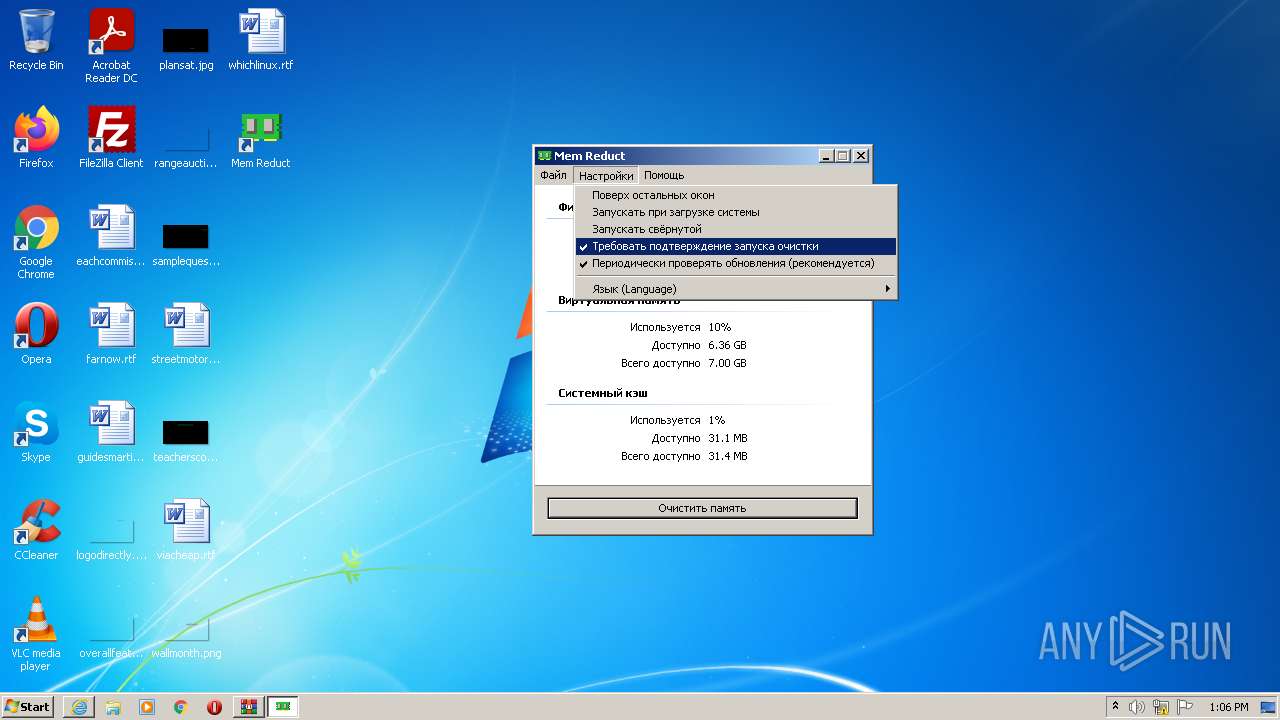
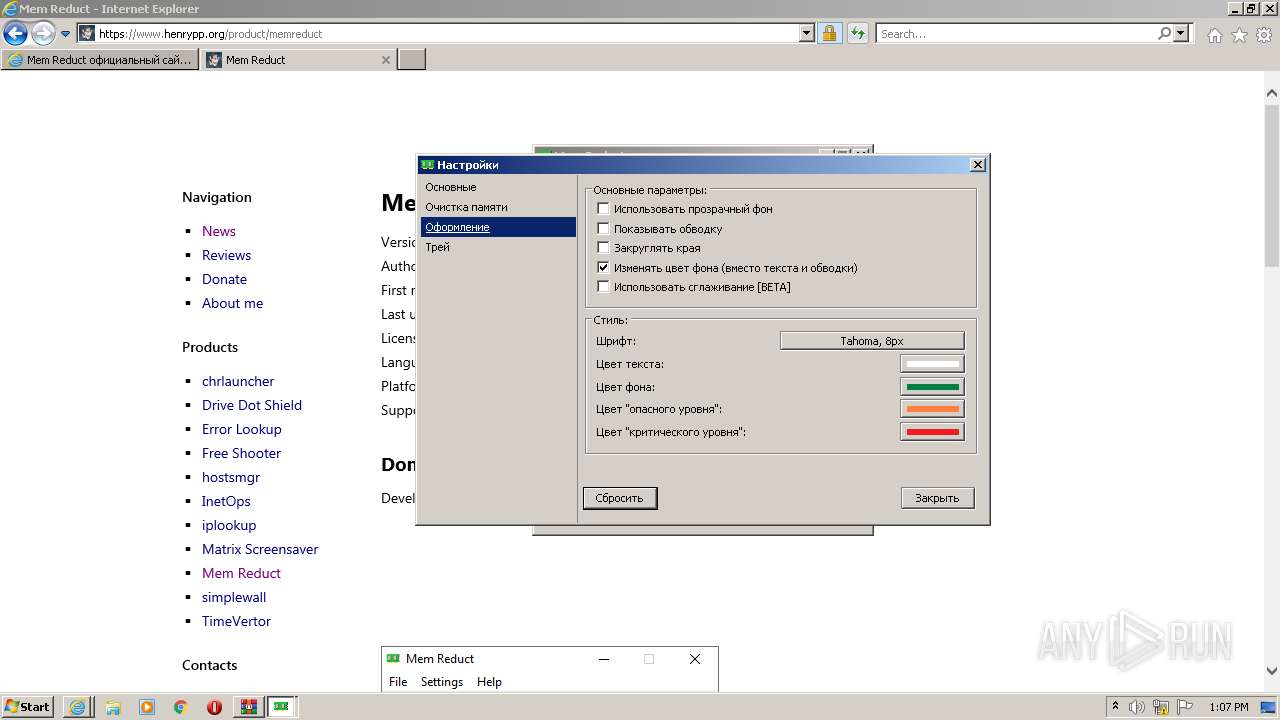
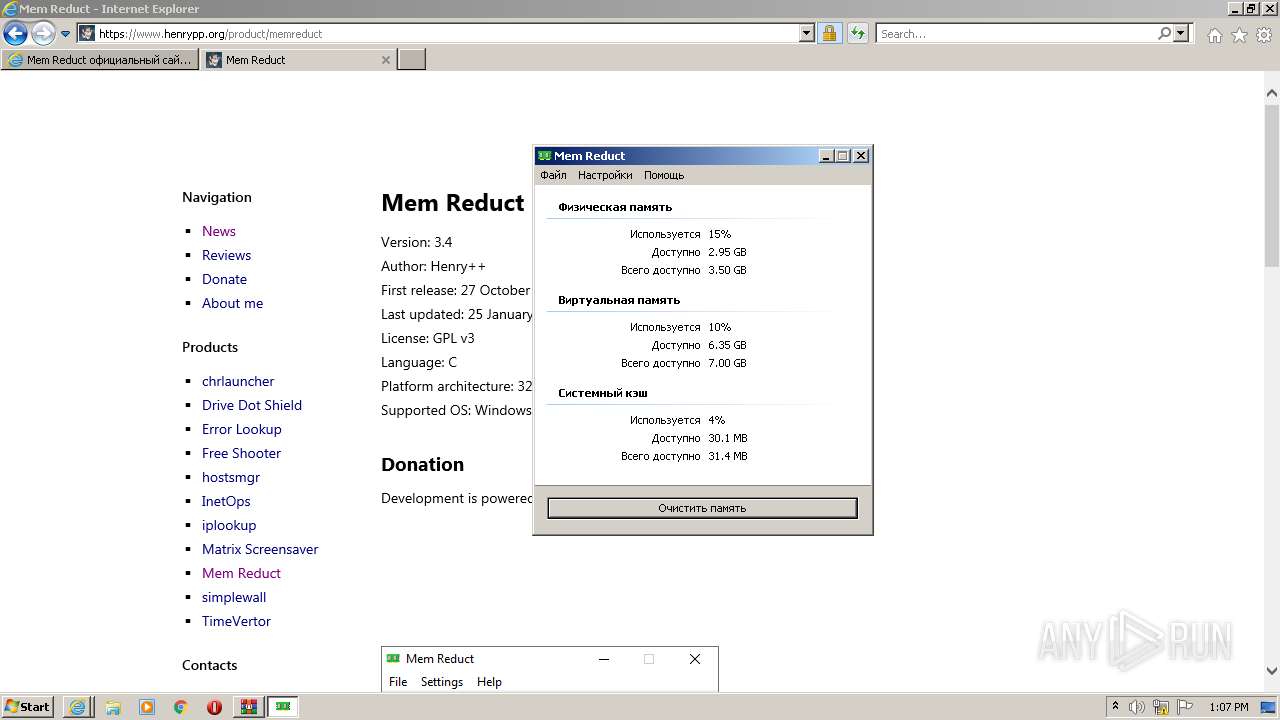
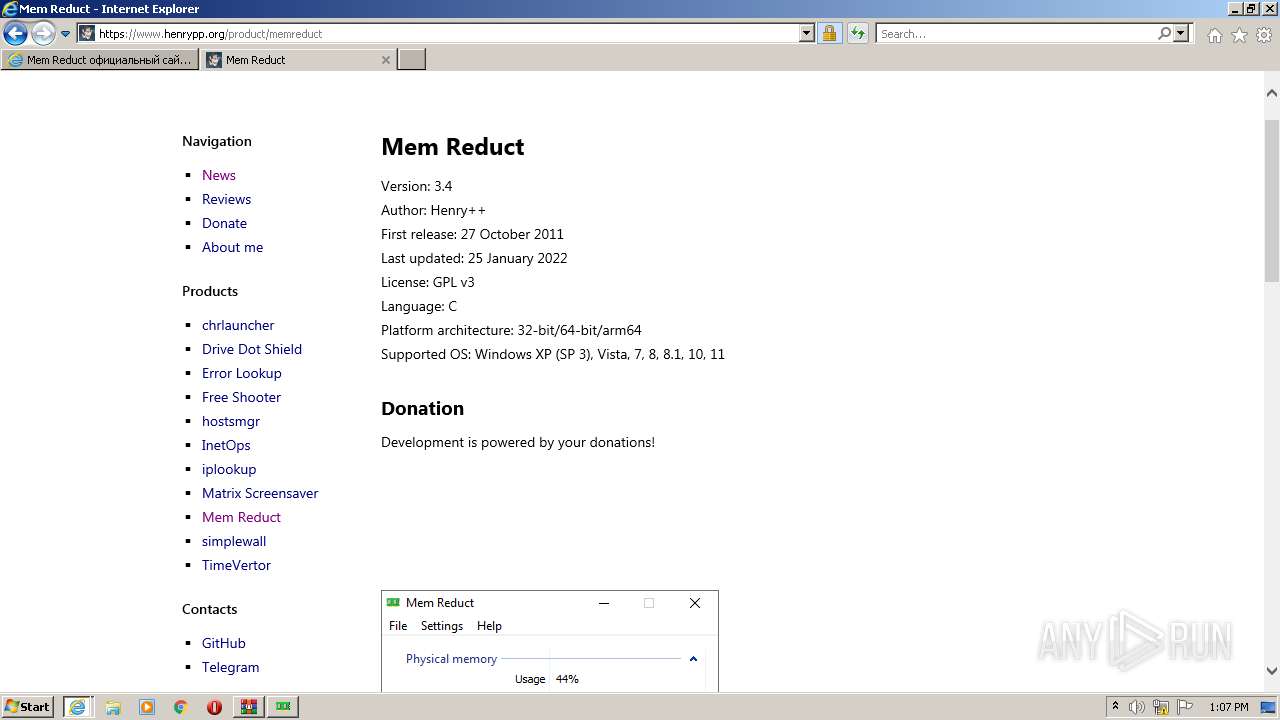
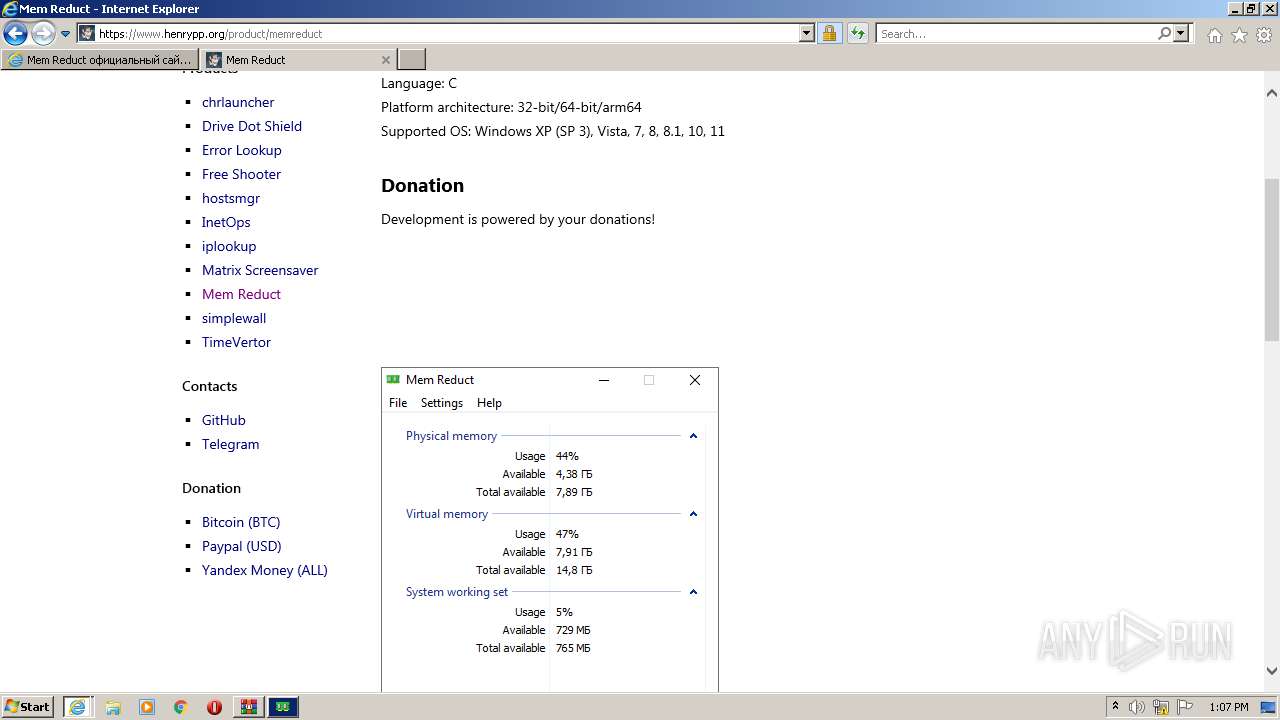
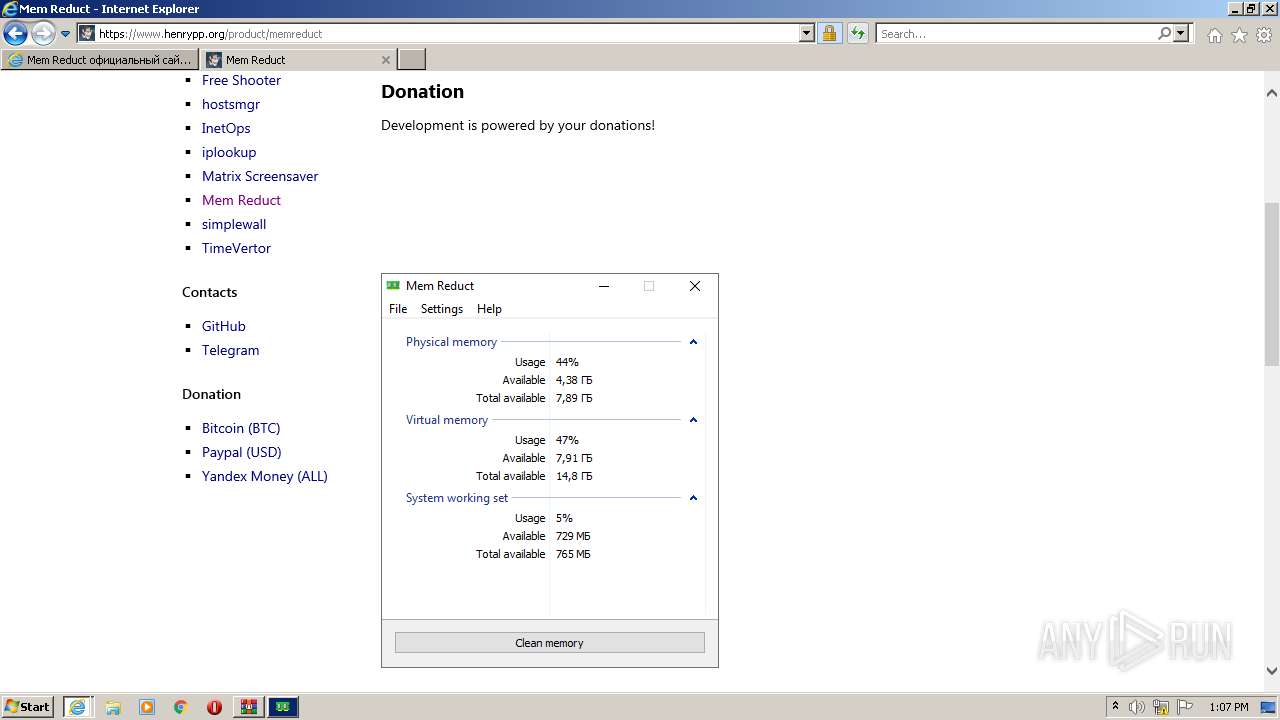
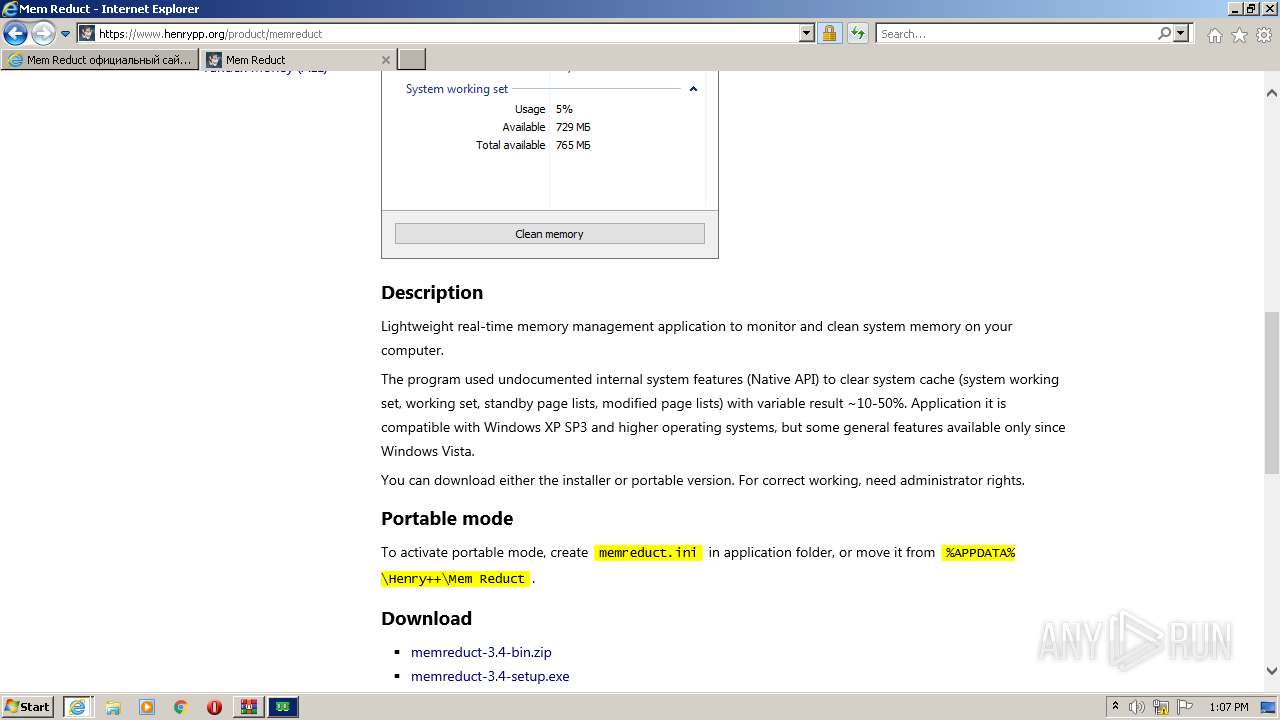
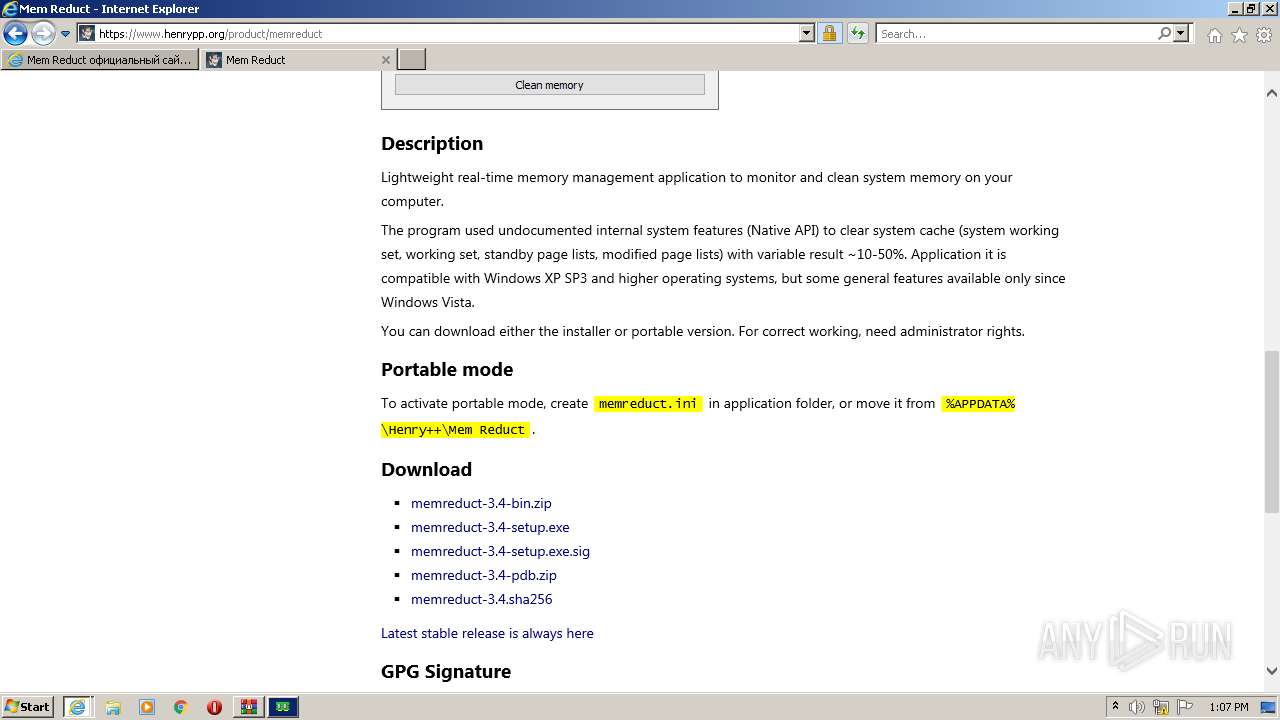
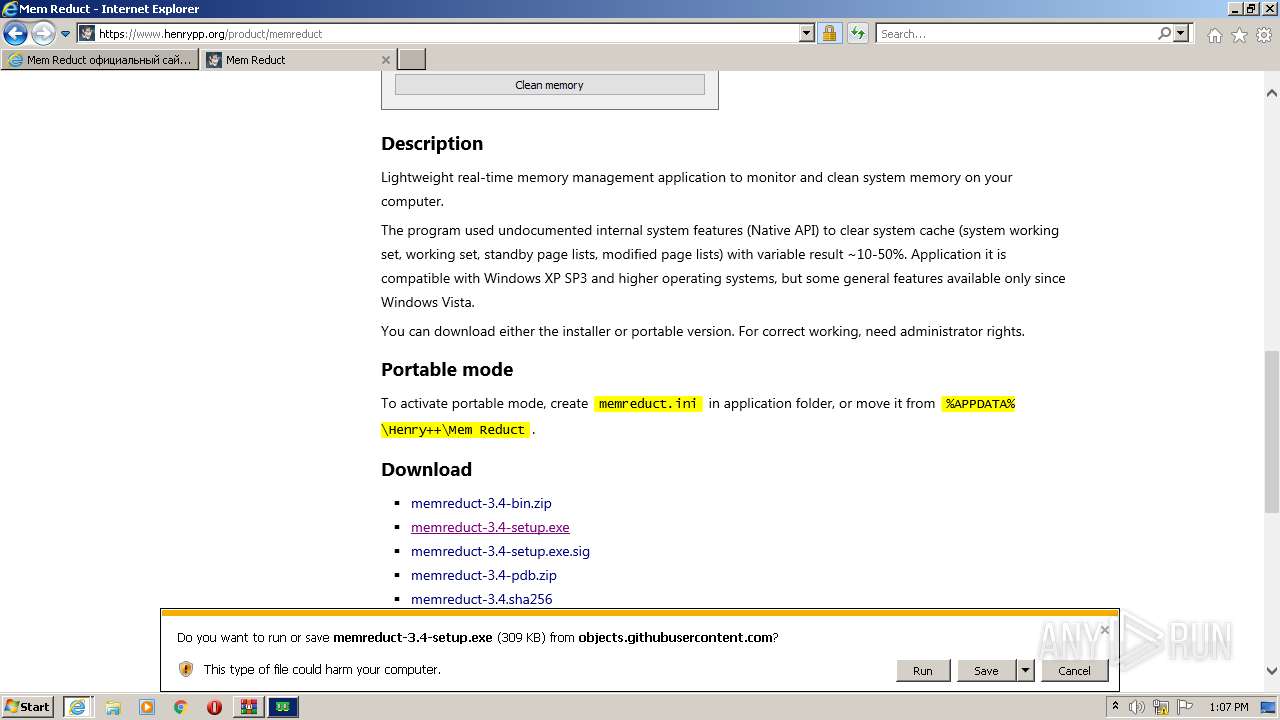
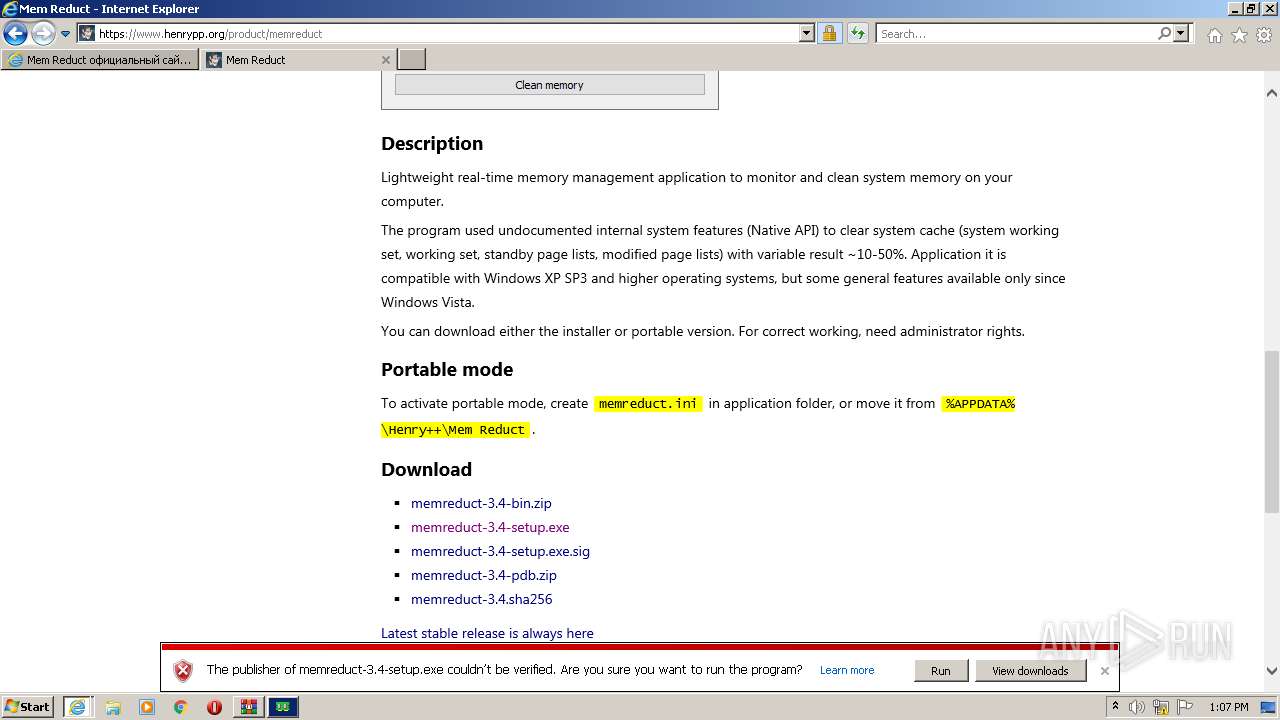
| URL: | https://memreducts.ru/ |
| Full analysis: | https://app.any.run/tasks/75a1de3a-7004-4dd3-a49a-c90199fb8553 |
| Verdict: | Malicious activity |
| Analysis date: | January 30, 2022, 13:04:53 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | F5E684D10E27BE3FBAD45FA4E4DC63CA |
| SHA1: | 5670E4343FBA295E6478E70B7DAFFE7F0177E126 |
| SHA256: | B734C6F4F404F9B9CE55E9BB329B13387F97F6CE5CE8658CFD802B15A1C113C3 |
| SSDEEP: | 3:N81QBr:21Ur |
MALICIOUS
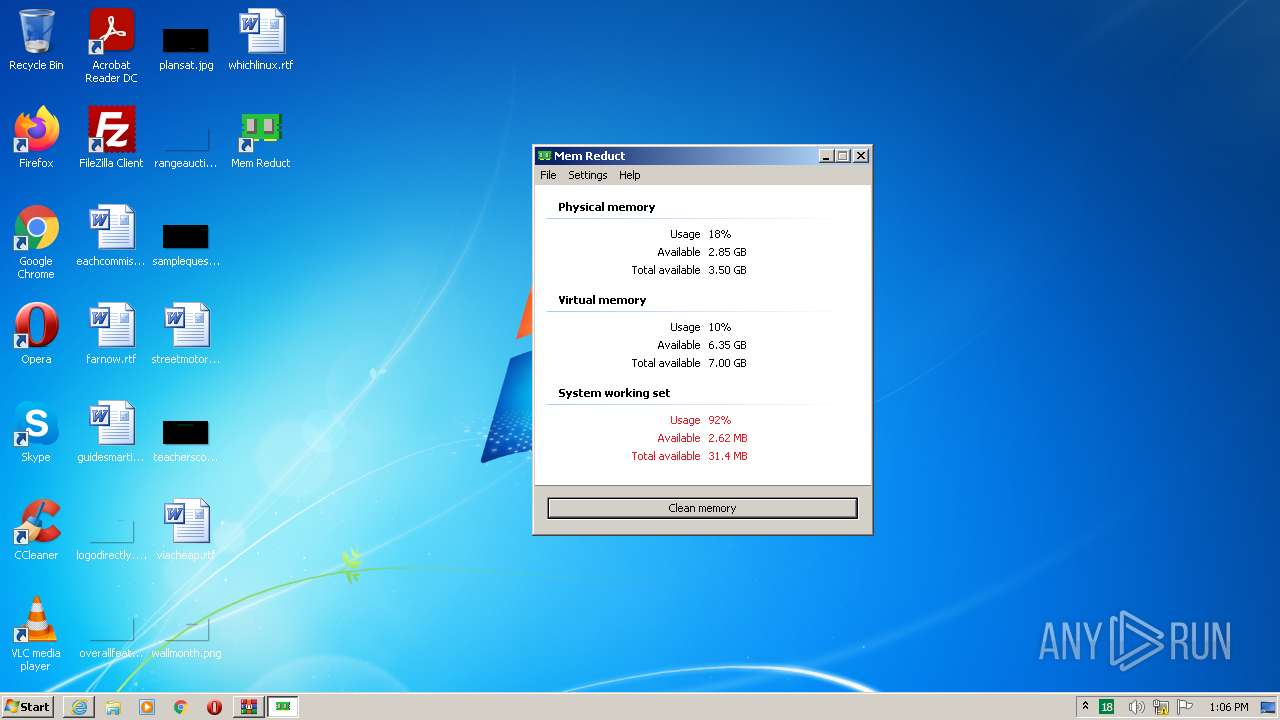
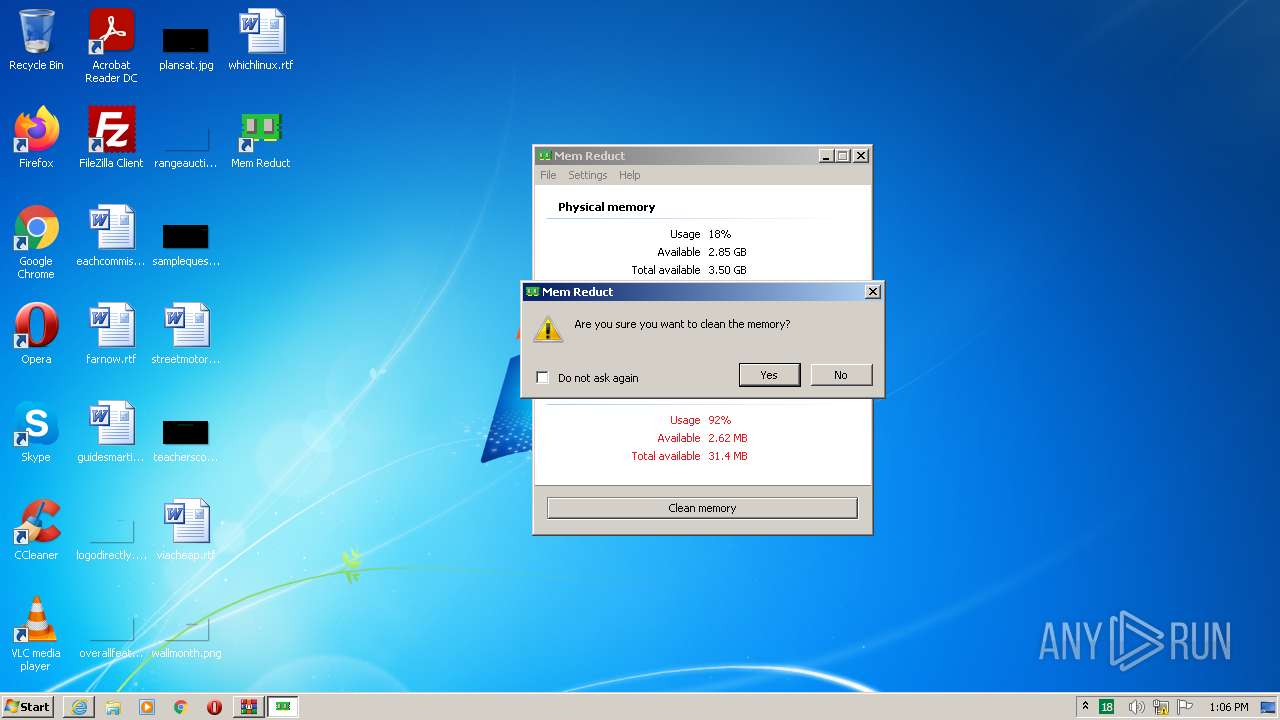
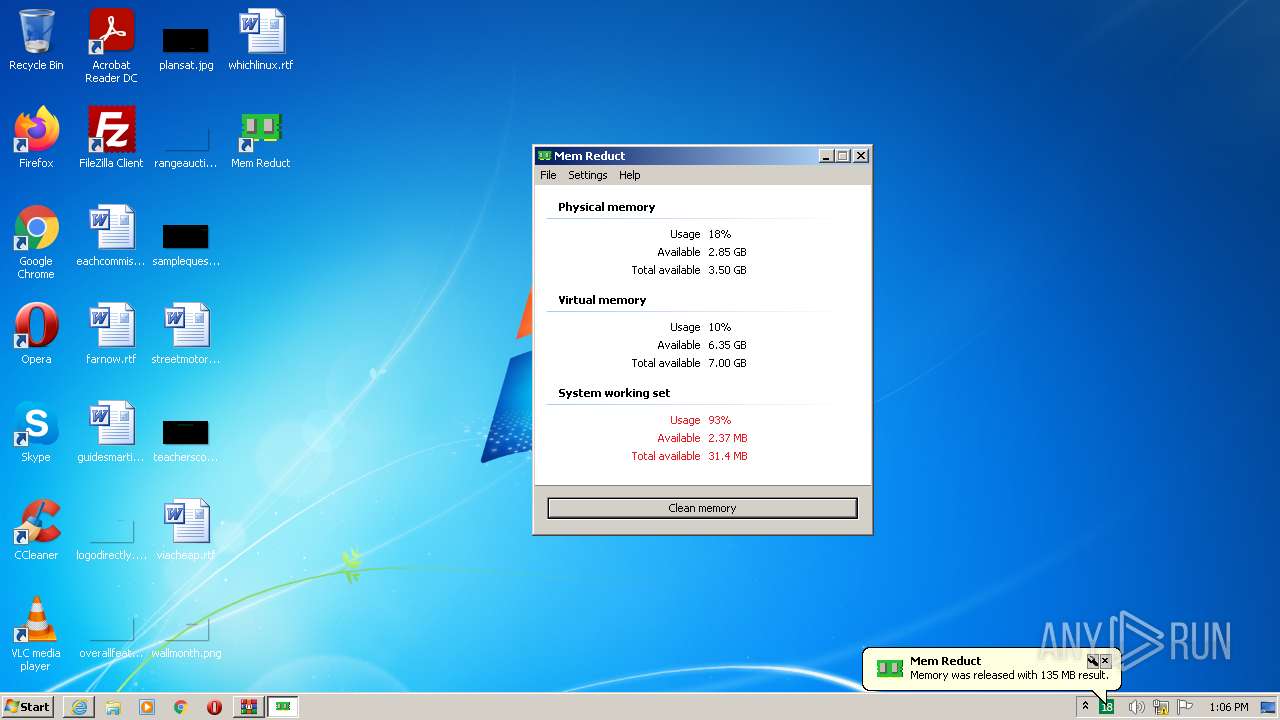
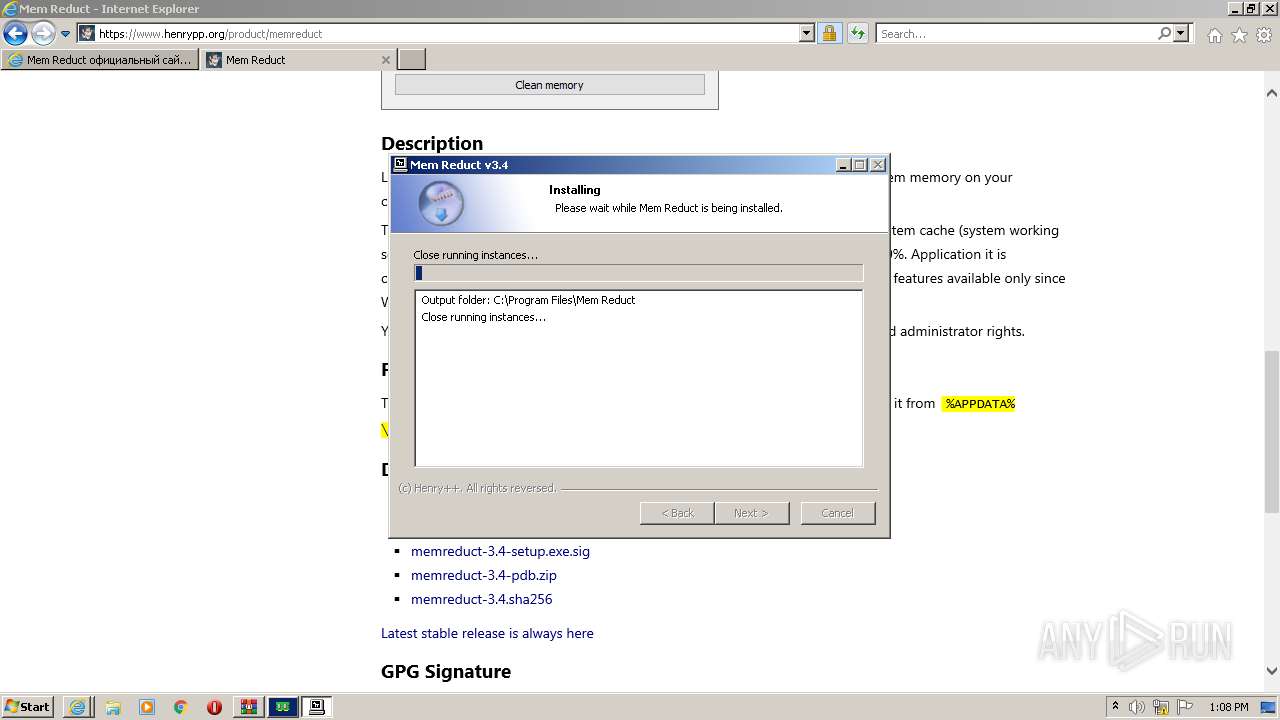
Drops executable file immediately after starts
- memreduct.exe (PID: 2424)
- memreduct.exe (PID: 1332)
- memreduct.tmp (PID: 2868)
- memreduct.exe (PID: 3488)
- memreduct-3.4-setup.exe (PID: 320)
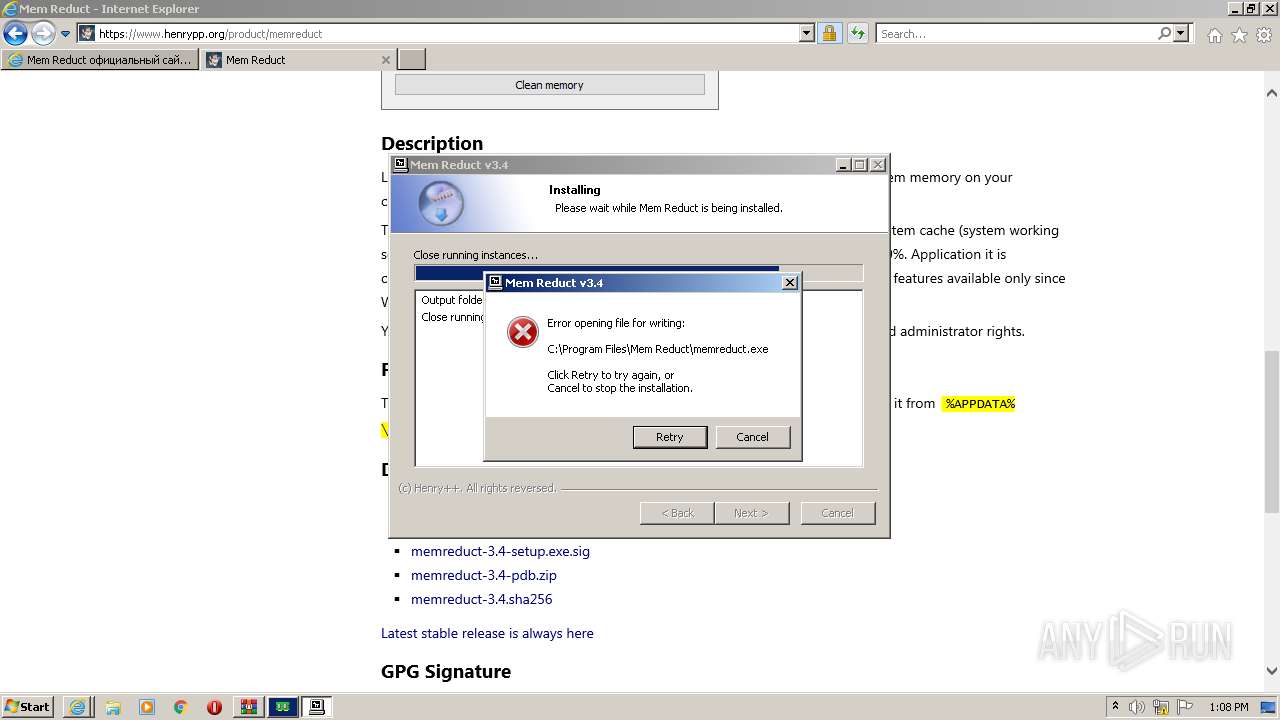
Application was dropped or rewritten from another process
- memreduct.exe (PID: 1332)
- memreduct.exe (PID: 2424)
- memreduct.exe (PID: 3488)
- memreduct.exe (PID: 488)
- memreduct-3.4-setup.exe (PID: 2872)
- memreduct-3.4-setup.exe (PID: 320)
Changes settings of System certificates
- memreduct.tmp (PID: 2868)
Loads dropped or rewritten executable
- memreduct.exe (PID: 3488)
- memreduct-3.4-setup.exe (PID: 320)
SUSPICIOUS
Reads Microsoft Outlook installation path
- iexplore.exe (PID: 3444)
- iexplore.exe (PID: 3992)
Reads the computer name
- WinRAR.exe (PID: 2924)
- memreduct.tmp (PID: 1068)
- memreduct.tmp (PID: 2868)
- memreduct.exe (PID: 3488)
- memreduct.exe (PID: 488)
- memreduct-3.4-setup.exe (PID: 320)
Checks supported languages
- memreduct.exe (PID: 2424)
- WinRAR.exe (PID: 2924)
- memreduct.tmp (PID: 1068)
- memreduct.exe (PID: 1332)
- memreduct.tmp (PID: 2868)
- memreduct.exe (PID: 3488)
- memreduct.exe (PID: 488)
- memreduct-3.4-setup.exe (PID: 320)
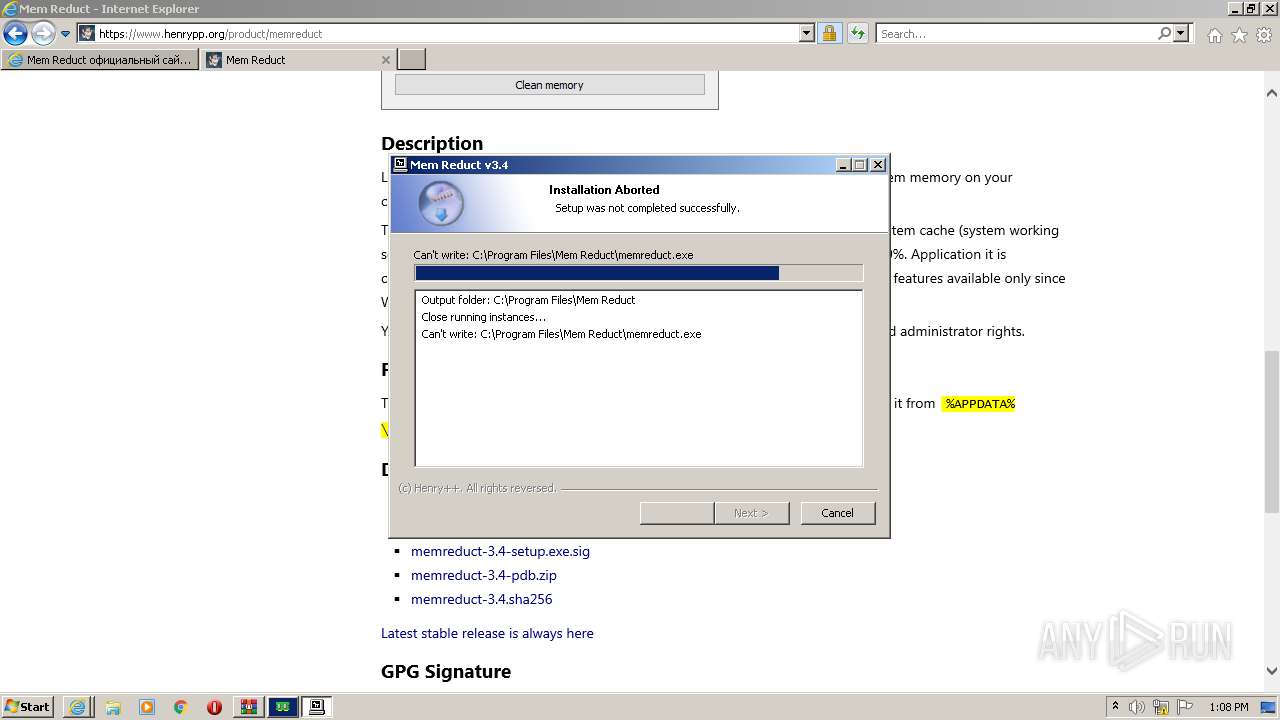
Executable content was dropped or overwritten
- memreduct.exe (PID: 2424)
- WinRAR.exe (PID: 2924)
- memreduct.exe (PID: 1332)
- memreduct.tmp (PID: 2868)
- memreduct.exe (PID: 3488)
- iexplore.exe (PID: 2920)
- iexplore.exe (PID: 3992)
- memreduct-3.4-setup.exe (PID: 320)
Reads the Windows organization settings
- memreduct.tmp (PID: 2868)
Reads Windows owner or organization settings
- memreduct.tmp (PID: 2868)
Drops a file that was compiled in debug mode
- memreduct.tmp (PID: 2868)
Adds / modifies Windows certificates
- memreduct.tmp (PID: 2868)
Creates a directory in Program Files
- memreduct.exe (PID: 3488)
Creates files in the program directory
- memreduct.exe (PID: 3488)
Drops a file with a compile date too recent
- memreduct.exe (PID: 3488)
Creates a software uninstall entry
- memreduct.exe (PID: 3488)
Creates files in the user directory
- memreduct.exe (PID: 3488)
- memreduct.exe (PID: 488)
Searches for installed software
- memreduct-3.4-setup.exe (PID: 320)
Executed via COM
- DllHost.exe (PID: 3340)
Drops a file with too old compile date
- memreduct.tmp (PID: 2868)
INFO
Reads the computer name
- iexplore.exe (PID: 2920)
- iexplore.exe (PID: 3992)
- iexplore.exe (PID: 3444)
- DllHost.exe (PID: 3340)
Checks supported languages
- iexplore.exe (PID: 3444)
- iexplore.exe (PID: 3992)
- iexplore.exe (PID: 2920)
- DllHost.exe (PID: 3340)
Reads internet explorer settings
- iexplore.exe (PID: 3444)
- iexplore.exe (PID: 3992)
Checks Windows Trust Settings
- iexplore.exe (PID: 2920)
- iexplore.exe (PID: 3444)
- iexplore.exe (PID: 3992)
Reads settings of System Certificates
- iexplore.exe (PID: 2920)
- iexplore.exe (PID: 3992)
- iexplore.exe (PID: 3444)
- memreduct.tmp (PID: 2868)
- memreduct.exe (PID: 488)
Application launched itself
- iexplore.exe (PID: 2920)
Changes internet zones settings
- iexplore.exe (PID: 2920)
Creates files in the user directory
- iexplore.exe (PID: 3444)
- iexplore.exe (PID: 2920)
Modifies the phishing filter of IE
- iexplore.exe (PID: 2920)
Application was dropped or rewritten from another process
- memreduct.tmp (PID: 1068)
- memreduct.tmp (PID: 2868)
Loads dropped or rewritten executable
- memreduct.tmp (PID: 2868)
Adds / modifies Windows certificates
- iexplore.exe (PID: 2920)
Changes settings of System certificates
- iexplore.exe (PID: 2920)
Dropped object may contain Bitcoin addresses
- iexplore.exe (PID: 3992)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
57
Monitored processes
13
Malicious processes
4
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 320 | "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\PO2HN1X2\memreduct-3.4-setup.exe" | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\PO2HN1X2\memreduct-3.4-setup.exe | iexplore.exe | ||||||||||||
User: admin Company: Henry++ Integrity Level: HIGH Description: Mem Reduct Exit code: 2 Version: 3.4 Modules
| |||||||||||||||
| 488 | "C:\Program Files\Mem Reduct\memreduct.exe" | C:\Program Files\Mem Reduct\memreduct.exe | memreduct.exe | ||||||||||||
User: admin Company: Henry++ Integrity Level: HIGH Description: Mem Reduct Exit code: 0 Version: 3.3.5 Modules
| |||||||||||||||
| 1068 | "C:\Users\admin\AppData\Local\Temp\is-IHDDB.tmp\memreduct.tmp" /SL5="$3024E,6760135,159232,C:\Users\admin\AppData\Local\Temp\Rar$EXa2924.8555\memreduct.exe" | C:\Users\admin\AppData\Local\Temp\is-IHDDB.tmp\memreduct.tmp | — | memreduct.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Setup/Uninstall Exit code: 0 Version: 51.1052.0.0 Modules
| |||||||||||||||
| 1332 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa2924.8555\memreduct.exe" /SPAWNWND=$20258 /NOTIFYWND=$3024E | C:\Users\admin\AppData\Local\Temp\Rar$EXa2924.8555\memreduct.exe | memreduct.tmp | ||||||||||||
User: admin Company: Integrity Level: HIGH Description: Mem Reduct Setup (r2108042017) Exit code: 0 Version: 3.3.5 Modules
| |||||||||||||||
| 2424 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa2924.8555\memreduct.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa2924.8555\memreduct.exe | WinRAR.exe | ||||||||||||
User: admin Company: Integrity Level: MEDIUM Description: Mem Reduct Setup (r2108042017) Exit code: 0 Version: 3.3.5 Modules
| |||||||||||||||
| 2868 | "C:\Users\admin\AppData\Local\Temp\is-UUU01.tmp\memreduct.tmp" /SL5="$30256,6760135,159232,C:\Users\admin\AppData\Local\Temp\Rar$EXa2924.8555\memreduct.exe" /SPAWNWND=$20258 /NOTIFYWND=$3024E | C:\Users\admin\AppData\Local\Temp\is-UUU01.tmp\memreduct.tmp | memreduct.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Setup/Uninstall Exit code: 0 Version: 51.1052.0.0 Modules
| |||||||||||||||
| 2872 | "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\PO2HN1X2\memreduct-3.4-setup.exe" | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\PO2HN1X2\memreduct-3.4-setup.exe | — | iexplore.exe | |||||||||||
User: admin Company: Henry++ Integrity Level: MEDIUM Description: Mem Reduct Exit code: 3221226540 Version: 3.4 Modules
| |||||||||||||||
| 2920 | "C:\Program Files\Internet Explorer\iexplore.exe" "https://memreducts.ru/" | C:\Program Files\Internet Explorer\iexplore.exe | Explorer.EXE | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2924 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\PO2HN1X2\memreduct.zip" | C:\Program Files\WinRAR\WinRAR.exe | iexplore.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 3340 | C:\Windows\system32\DllHost.exe /Processid:{76D0CB12-7604-4048-B83C-1005C7DDC503} | C:\Windows\system32\DllHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: COM Surrogate Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
39 340
Read events
38 950
Write events
382
Delete events
8
Modification events
| (PID) Process: | (2920) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 1 | |||
| (PID) Process: | (2920) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchLowDateTime |
Value: | |||
| (PID) Process: | (2920) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 30938585 | |||
| (PID) Process: | (2920) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: 216763653 | |||
| (PID) Process: | (2920) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30938586 | |||
| (PID) Process: | (2920) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (2920) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (2920) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (2920) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (2920) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
18
Suspicious files
46
Text files
98
Unknown types
39
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3444 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\5A07ECF0226EA781EA737B3DEFBF959F | binary | |
MD5:— | SHA256:— | |||
| 3444 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\2D3B485B.htm | html | |
MD5:— | SHA256:— | |||
| 3444 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\103621DE9CD5414CC2538780B4B75751 | binary | |
MD5:— | SHA256:— | |||
| 3444 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\logo[1].png | image | |
MD5:— | SHA256:— | |||
| 3444 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\5A07ECF0226EA781EA737B3DEFBF959F | der | |
MD5:— | SHA256:— | |||
| 3444 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:— | SHA256:— | |||
| 3444 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\002[1].png | image | |
MD5:— | SHA256:— | |||
| 3444 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\5IWPIAR9\style[1].css | text | |
MD5:— | SHA256:— | |||
| 3444 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\24BD96D5497F70B3F510A6B53CD43F3E_3A89246FB90C5EE6620004F1AE0EB0EA | der | |
MD5:— | SHA256:— | |||
| 3444 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\5IWPIAR9\003[1].jpg | image | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
38
TCP/UDP connections
116
DNS requests
43
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3444 | iexplore.exe | GET | 200 | 172.217.18.99:80 | http://ocsp.pki.goog/gsr1/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCEHe9DWzbNvka6iEPxPBY0w0%3D | US | der | 1.41 Kb | whitelisted |
3444 | iexplore.exe | GET | 200 | 2.16.186.163:80 | http://subca.ocsp-certum.com/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBR5iK7tYk9tqQEoeQhZNkKcAol9bgQUjEPEy22YwaechGnr30oNYJY6w%2FsCEQCTkoVAAWVxX5R%2FKI%2FvyZso | unknown | der | 1.50 Kb | whitelisted |
3444 | iexplore.exe | GET | 200 | 172.217.18.99:80 | http://ocsp.pki.goog/gtsr1/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBQwkcLWD4LqGJ7bE7B1XZsEbmfwUAQU5K8rJnEaK0gnhS9SZizv8IkTcT4CDQIDvFNZazTHGPUBUGY%3D | US | der | 724 b | whitelisted |
3444 | iexplore.exe | GET | 200 | 172.217.18.99:80 | http://ocsp.pki.goog/gts1c3/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEQCBOXNTLJE8wAoAAAABK34H | US | der | 472 b | whitelisted |
3444 | iexplore.exe | GET | 200 | 2.16.186.163:80 | http://subca.ocsp-certum.com/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTYOkzrrCGQj08njZXbUQQpkoUmuQQUCHbNywf%2FJPbFze27kLzihDdGdfcCEQDkBUeDDgxkUpdvejVJwN1I | unknown | der | 1.54 Kb | whitelisted |
3444 | iexplore.exe | GET | 200 | 172.217.18.99:80 | http://ocsp.pki.goog/gts1c3/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEQC04WHG3wyS9QoAAAABK3x8 | US | der | 472 b | whitelisted |
3444 | iexplore.exe | GET | 200 | 172.217.18.99:80 | http://ocsp.pki.goog/gts1c3/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEEFKxQHtEPcBCgAAAAErfHU%3D | US | der | 471 b | whitelisted |
2920 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA8Ull8gIGmZT9XHrHiJQeI%3D | US | der | 1.47 Kb | whitelisted |
3444 | iexplore.exe | GET | 200 | 23.32.238.27:80 | http://r3.o.lencr.org/MFMwUTBPME0wSzAJBgUrDgMCGgUABBRI2smg%2ByvTLU%2Fw3mjS9We3NfmzxAQUFC6zF7dYVsuuUAlA5h%2BvnYsUwsYCEgPah55KjaxsBoJnUG0SVSVEYA%3D%3D | US | der | 503 b | shared |
3444 | iexplore.exe | GET | 200 | 23.32.238.27:80 | http://r3.o.lencr.org/MFMwUTBPME0wSzAJBgUrDgMCGgUABBRI2smg%2ByvTLU%2Fw3mjS9We3NfmzxAQUFC6zF7dYVsuuUAlA5h%2BvnYsUwsYCEgMhDytFv2lFb61n36w6dXUODg%3D%3D | US | der | 503 b | shared |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3444 | iexplore.exe | 23.105.236.220:443 | memreducts.ru | Servers.com, Inc. | RU | malicious |
3444 | iexplore.exe | 23.32.238.208:80 | ctldl.windowsupdate.com | XO Communications | US | unknown |
3444 | iexplore.exe | 23.32.238.201:80 | ctldl.windowsupdate.com | XO Communications | US | suspicious |
3444 | iexplore.exe | 95.181.171.231:443 | cdn-rtb.sape.ru | QWARTA LLC | RU | unknown |
3444 | iexplore.exe | 172.217.18.99:80 | ocsp.pki.goog | Google Inc. | US | whitelisted |
3444 | iexplore.exe | 2.16.186.163:80 | subca.ocsp-certum.com | Akamai International B.V. | — | whitelisted |
3444 | iexplore.exe | 88.212.201.216:443 | counter.yadro.ru | United Network LLC | RU | suspicious |
3444 | iexplore.exe | 142.250.185.162:443 | partner.googleadservices.com | Google Inc. | US | whitelisted |
3444 | iexplore.exe | 104.18.30.182:80 | ocsp.comodoca.com | Cloudflare Inc | US | suspicious |
3444 | iexplore.exe | 172.217.23.98:443 | googleads.g.doubleclick.net | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
memreducts.ru |
| malicious |
ctldl.windowsupdate.com |
| whitelisted |
x1.c.lencr.org |
| whitelisted |
r3.o.lencr.org |
| shared |
pagead2.googlesyndication.com |
| whitelisted |
allstat-pp.ru |
| whitelisted |
yandex.ru |
| whitelisted |
cdn-rtb.sape.ru |
| unknown |
mc.yandex.ru |
| whitelisted |
counter.yadro.ru |
| whitelisted |