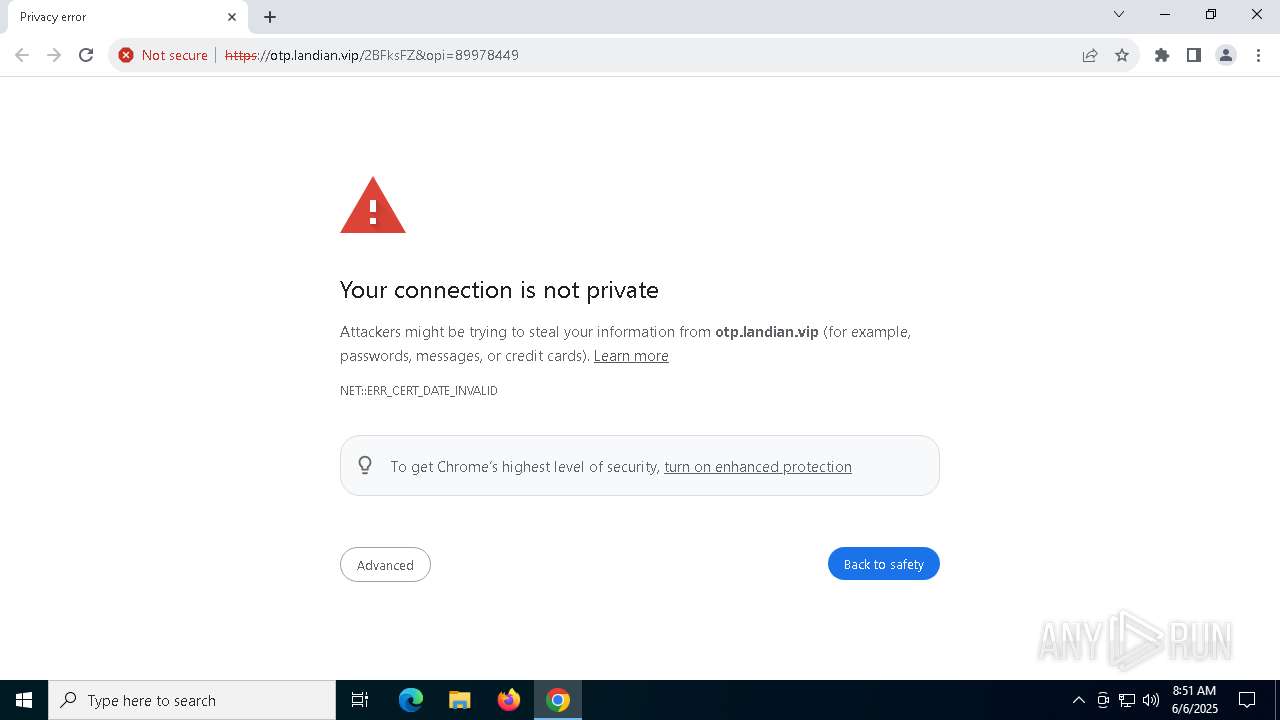
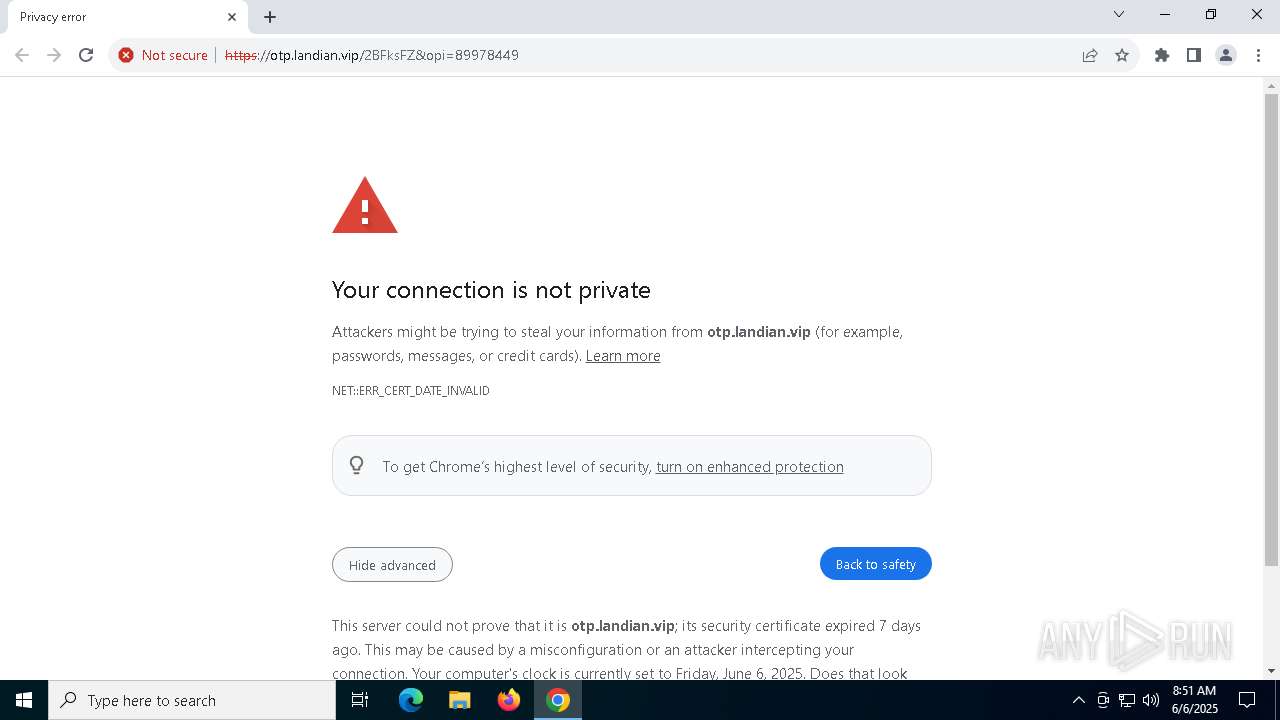
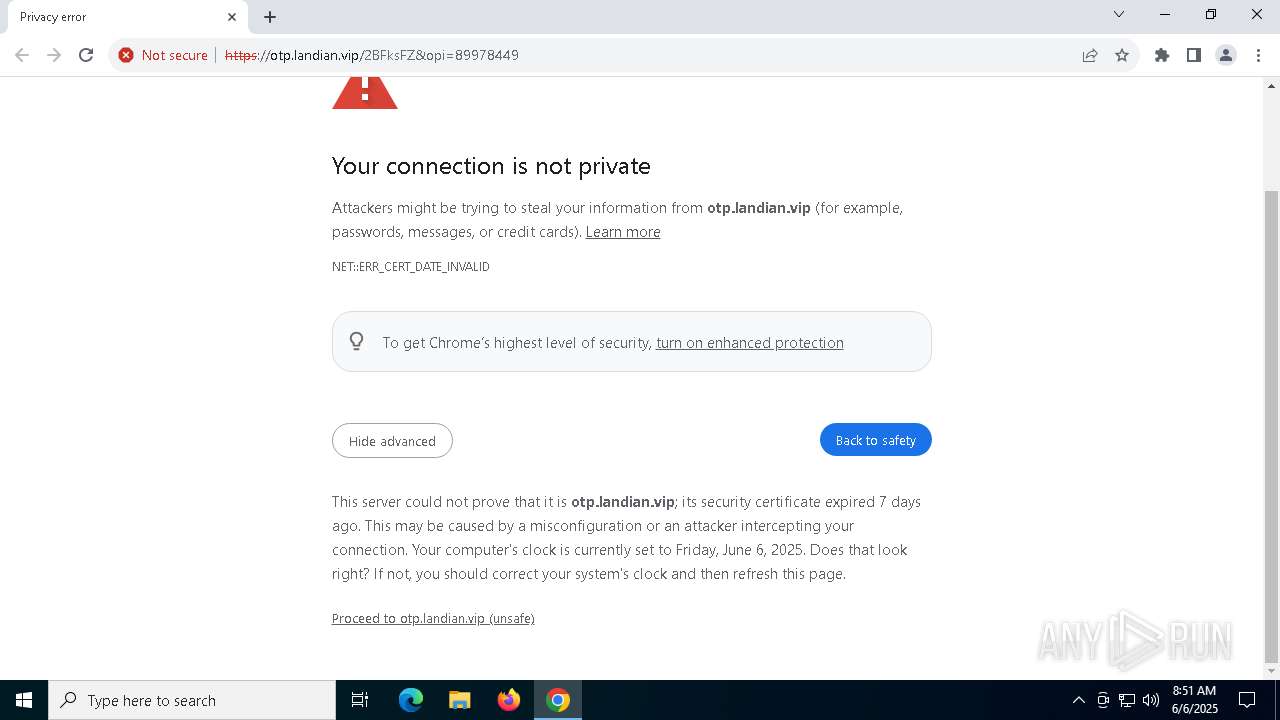
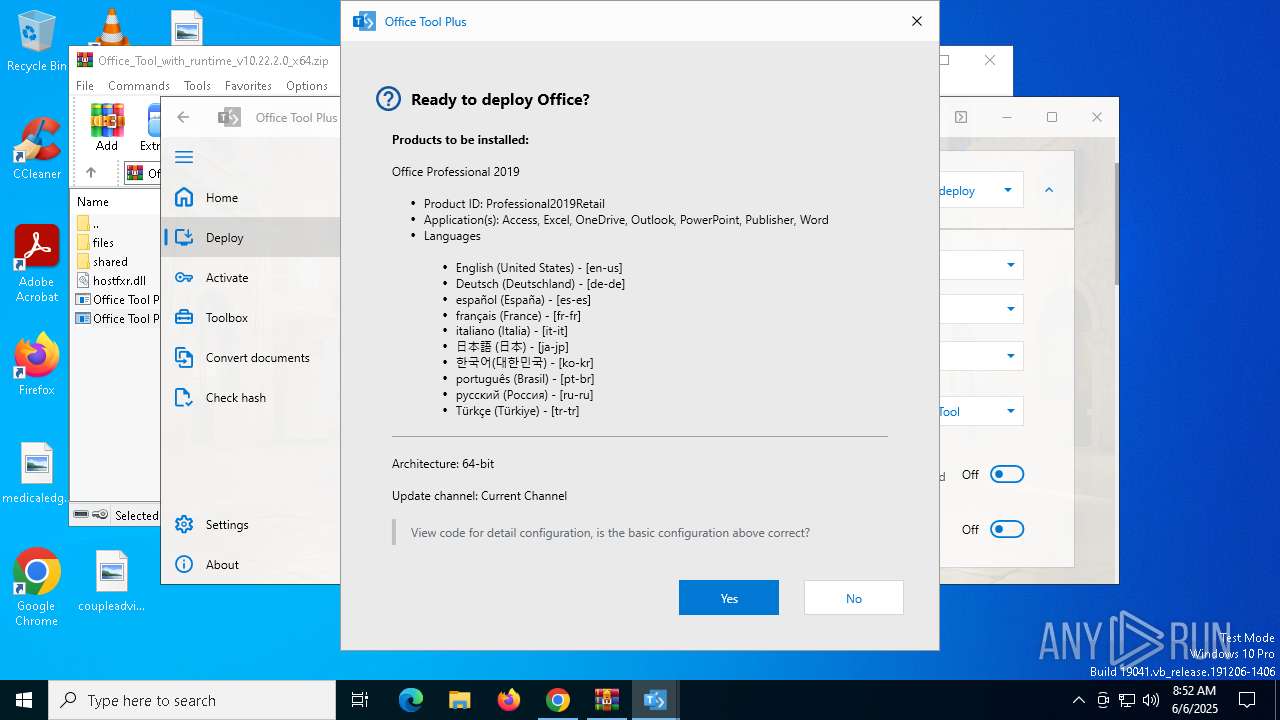
| URL: | https://otp.landian.vip/2BFksFZ&opi=89978449 |
| Full analysis: | https://app.any.run/tasks/bd5dc479-0d80-4f04-a400-3c6d0bf05425 |
| Verdict: | Malicious activity |
| Analysis date: | June 06, 2025, 08:51:29 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | FE51BFEE83935FCF766579ED38FF4F8D |
| SHA1: | 3A24872974BDE7F800085224C302102292EA9389 |
| SHA256: | B6DF4F9215BC64E0C0CCA4257E070FDE6C622F0A52E7BFD372D3B7DEFAC9263B |
| SSDEEP: | 3:N8YinU0+Fca:2YOVAca |
MALICIOUS
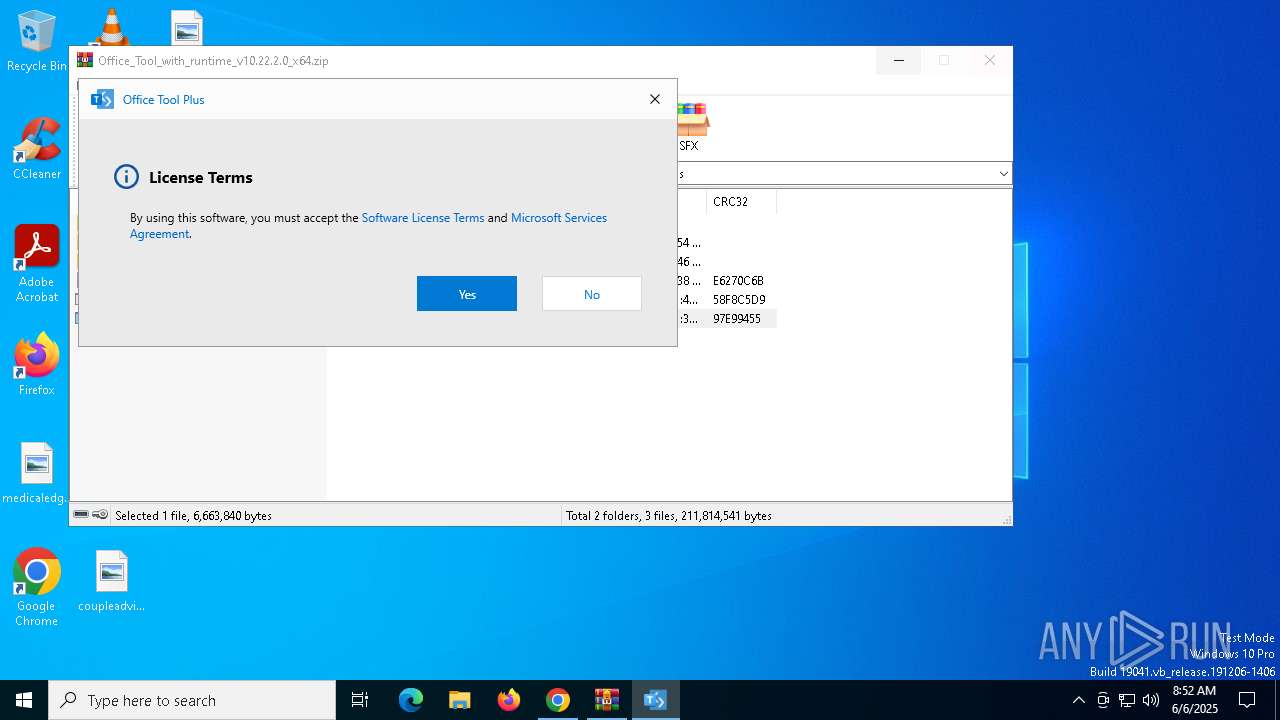
Executing a file with an untrusted certificate
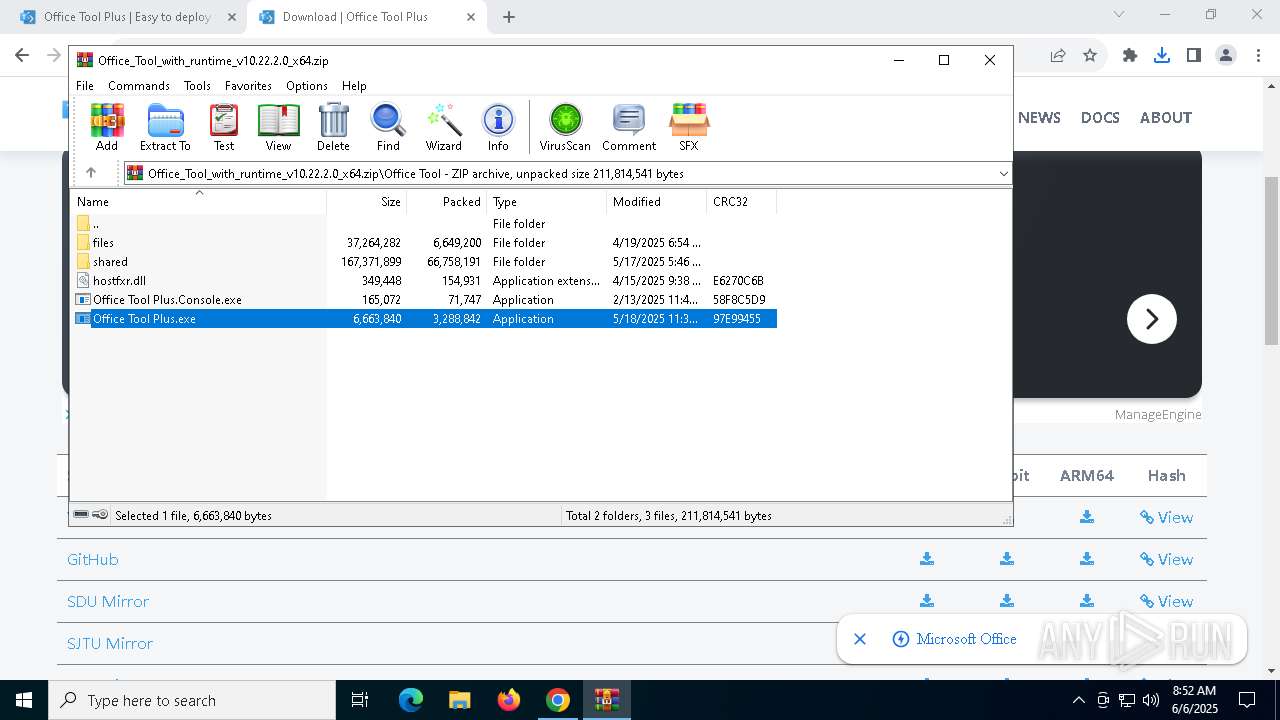
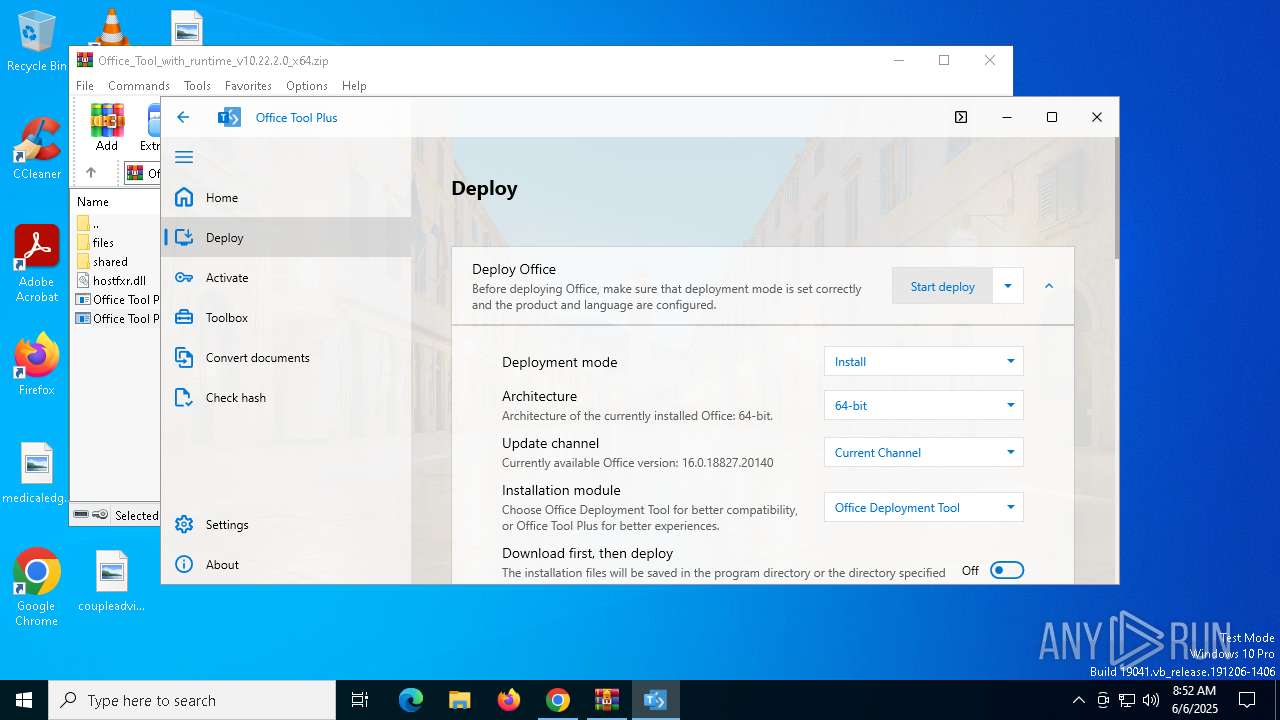
- Office Tool Plus.exe (PID: 4028)
- Office Tool Plus.exe (PID: 4724)
Scans artifacts that could help determine the target
- setup.exe (PID: 3156)
GENERIC has been found (auto)
- OfficeClickToRun.exe (PID: 5056)
SUSPICIOUS
The process creates files with name similar to system file names
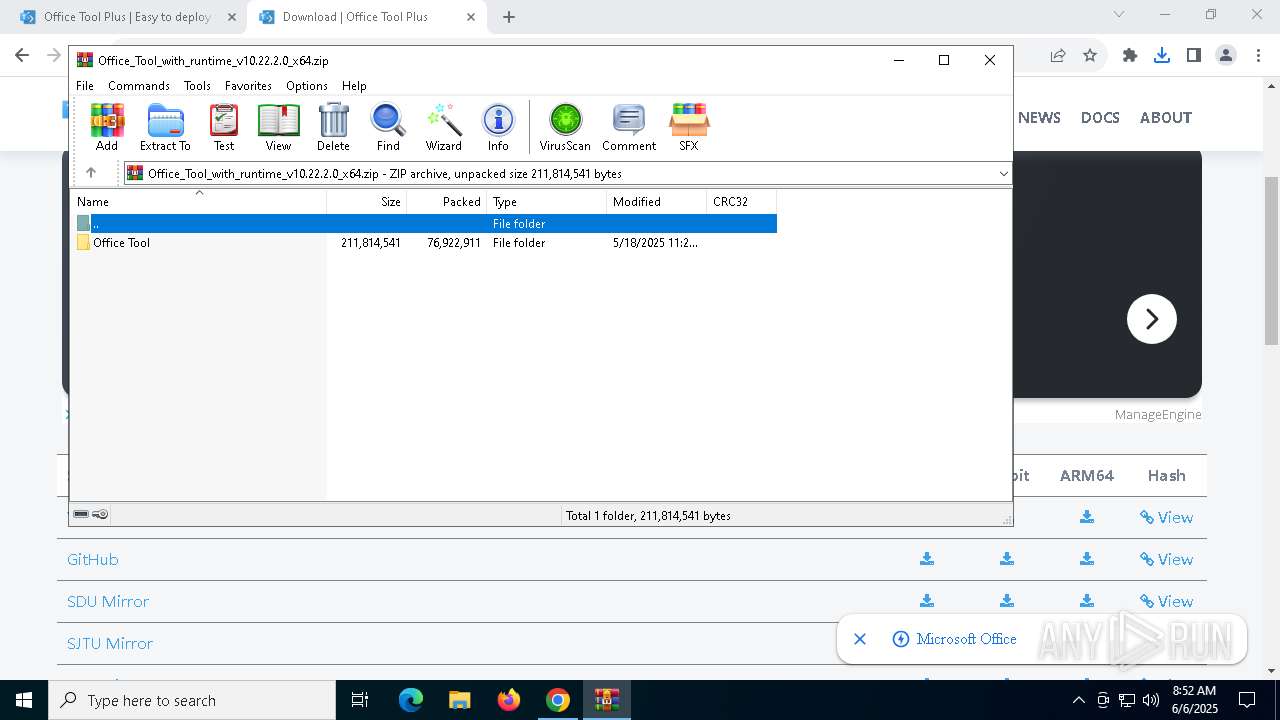
- WinRAR.exe (PID: 4172)
Process drops legitimate windows executable
- WinRAR.exe (PID: 4172)
- OfficeClickToRun.exe (PID: 5056)
- OfficeClickToRun.exe (PID: 7248)
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 4172)
- Office Tool Plus.exe (PID: 4028)
- setup.exe (PID: 3156)
Reads the date of Windows installation
- Office Tool Plus.exe (PID: 4028)
Application launched itself
- setup.exe (PID: 8060)
Starts a Microsoft application from unusual location
- setup.exe (PID: 3156)
- setup.exe (PID: 8060)
There is functionality for taking screenshot (YARA)
- Office Tool Plus.exe (PID: 4028)
Executable content was dropped or overwritten
- OfficeClickToRun.exe (PID: 5056)
- OfficeClickToRun.exe (PID: 7248)
The process drops C-runtime libraries
- OfficeClickToRun.exe (PID: 5056)
Searches for installed software
- setup.exe (PID: 3156)
INFO
Reads Microsoft Office registry keys
- chrome.exe (PID: 8056)
- Office Tool Plus.exe (PID: 4028)
- setup.exe (PID: 3156)
- OfficeClickToRun.exe (PID: 5056)
Application launched itself
- chrome.exe (PID: 8056)
Creates files in the program directory
- Office Tool Plus.exe (PID: 4028)
Reads the software policy settings
- Office Tool Plus.exe (PID: 4028)
- setup.exe (PID: 3156)
- slui.exe (PID: 4652)
Checks supported languages
- Office Tool Plus.exe (PID: 4028)
- setup.exe (PID: 8060)
- setup.exe (PID: 3156)
- OfficeClickToRun.exe (PID: 5056)
Create files in a temporary directory
- Office Tool Plus.exe (PID: 4028)
- setup.exe (PID: 3156)
- OfficeClickToRun.exe (PID: 5056)
Checks proxy server information
- Office Tool Plus.exe (PID: 4028)
- setup.exe (PID: 3156)
- OfficeClickToRun.exe (PID: 5056)
Reads the machine GUID from the registry
- Office Tool Plus.exe (PID: 4028)
- setup.exe (PID: 3156)
Creates files or folders in the user directory
- Office Tool Plus.exe (PID: 4028)
- setup.exe (PID: 3156)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 4172)
- chrome.exe (PID: 8132)
- chrome.exe (PID: 6404)
The sample compiled with english language support
- WinRAR.exe (PID: 4172)
- OfficeClickToRun.exe (PID: 5056)
- chrome.exe (PID: 8132)
- chrome.exe (PID: 6404)
Reads the computer name
- Office Tool Plus.exe (PID: 4028)
- setup.exe (PID: 3156)
- OfficeClickToRun.exe (PID: 5056)
Process checks computer location settings
- Office Tool Plus.exe (PID: 4028)
- setup.exe (PID: 3156)
Reads Environment values
- setup.exe (PID: 3156)
.NET Reactor protector has been detected
- Office Tool Plus.exe (PID: 4028)
The sample compiled with arabic language support
- OfficeClickToRun.exe (PID: 5056)
The sample compiled with bulgarian language support
- OfficeClickToRun.exe (PID: 5056)
The sample compiled with czech language support
- OfficeClickToRun.exe (PID: 5056)
The sample compiled with french language support
- OfficeClickToRun.exe (PID: 5056)
The sample compiled with Indonesian language support
- OfficeClickToRun.exe (PID: 5056)
The sample compiled with german language support
- OfficeClickToRun.exe (PID: 5056)
The sample compiled with polish language support
- OfficeClickToRun.exe (PID: 5056)
The sample compiled with Italian language support
- OfficeClickToRun.exe (PID: 5056)
The sample compiled with japanese language support
- OfficeClickToRun.exe (PID: 5056)
The sample compiled with korean language support
- OfficeClickToRun.exe (PID: 5056)
The sample compiled with russian language support
- OfficeClickToRun.exe (PID: 5056)
The sample compiled with portuguese language support
- OfficeClickToRun.exe (PID: 5056)
The sample compiled with swedish language support
- OfficeClickToRun.exe (PID: 5056)
The sample compiled with turkish language support
- OfficeClickToRun.exe (PID: 5056)
The sample compiled with slovak language support
- OfficeClickToRun.exe (PID: 5056)
The sample compiled with chinese language support
- OfficeClickToRun.exe (PID: 5056)
Executes as Windows Service
- OfficeClickToRun.exe (PID: 7248)
Manual execution by a user
- OfficeC2RClient.exe (PID: 6744)
- Taskmgr.exe (PID: 872)
- Taskmgr.exe (PID: 2560)
The sample compiled with spanish language support
- OfficeClickToRun.exe (PID: 5056)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
188
Monitored processes
53
Malicious processes
6
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 872 | "C:\WINDOWS\system32\taskmgr.exe" /4 | C:\Windows\System32\Taskmgr.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Task Manager Exit code: 3221226540 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1804 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --no-appcompat-clear --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=11 --mojo-platform-channel-handle=4356 --field-trial-handle=1900,i,11824752276604751028,17728555006186162926,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 2196 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2332 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --no-appcompat-clear --gpu-preferences=WAAAAAAAAADgABAMAAAAAAAAAAAAAAAAAABgAAAAAAA4AAAAAAAAAAAAAAAEAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAGAAAAAAAAAAYAAAAAAAAAAgAAAAAAAAACAAAAAAAAAAIAAAAAAAAAA== --mojo-platform-channel-handle=1896 --field-trial-handle=1900,i,11824752276604751028,17728555006186162926,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Version: 122.0.6261.70 Modules
| |||||||||||||||
| 2432 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --extension-process --no-appcompat-clear --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=7 --mojo-platform-channel-handle=3452 --field-trial-handle=1900,i,11824752276604751028,17728555006186162926,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 2560 | "C:\WINDOWS\system32\taskmgr.exe" /4 | C:\Windows\System32\Taskmgr.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Task Manager Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3156 | setup.exe RELAUNCHED /configure "C:\Users\admin\AppData\Local\Office Tool Plus\Temp_5656\Configuration.xml" | C:\Users\admin\AppData\Local\Temp\Rar$EXa4172.25638\Office Tool\files\setup.exe | setup.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft 365 and Office Version: 16.0.18730.20142 Modules
| |||||||||||||||
| 3268 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.FileUtilService --lang=en-US --service-sandbox-type=service --disable-quic --no-appcompat-clear --mojo-platform-channel-handle=6068 --field-trial-handle=1900,i,11824752276604751028,17728555006186162926,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 3448 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --disable-quic --no-appcompat-clear --mojo-platform-channel-handle=5824 --field-trial-handle=1900,i,11824752276604751028,17728555006186162926,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 3464 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --disable-quic --no-appcompat-clear --mojo-platform-channel-handle=6612 --field-trial-handle=1900,i,11824752276604751028,17728555006186162926,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
Total events
54 002
Read events
53 500
Write events
300
Delete events
202
Modification events
| (PID) Process: | (8056) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (8056) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (8056) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (8056) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (8056) chrome.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Google\Update\ClientStateMedium\{8A69D345-D564-463C-AFF1-A69D9E530F96} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
| (PID) Process: | (5404) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Shell Extensions\Cached |
| Operation: | write | Name: | {2781761E-28E0-4109-99FE-B9D127C57AFE} {56FFCC30-D398-11D0-B2AE-00A0C908FA49} 0xFFFF |
Value: 0100000000000000EAF88B4FC0D6DB01 | |||
| (PID) Process: | (8056) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.zip\OpenWithProgids |
| Operation: | write | Name: | WinRAR.ZIP |
Value: | |||
| (PID) Process: | (4172) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (4172) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (4172) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
Executable files
885
Suspicious files
737
Text files
120
Unknown types
8
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 8056 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Sync Data\LevelDB\LOG.old~RF11f4ec.TMP | — | |
MD5:— | SHA256:— | |||
| 8056 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Sync Data\LevelDB\LOG.old | — | |
MD5:— | SHA256:— | |||
| 8056 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\PersistentOriginTrials\LOG.old~RF11f4ec.TMP | — | |
MD5:— | SHA256:— | |||
| 8056 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
| 8056 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old~RF11f4fc.TMP | — | |
MD5:— | SHA256:— | |||
| 8056 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 8056 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Service Worker\Database\LOG.old~RF11f4ec.TMP | — | |
MD5:— | SHA256:— | |||
| 8056 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Site Characteristics Database\LOG.old~RF11f50b.TMP | — | |
MD5:— | SHA256:— | |||
| 8056 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Service Worker\Database\LOG.old | — | |
MD5:— | SHA256:— | |||
| 8056 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Site Characteristics Database\LOG.old | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
123
TCP/UDP connections
303
DNS requests
218
Threats
6
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 2.16.241.19:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5956 | chrome.exe | GET | 200 | 2.19.105.127:80 | http://x1.i.lencr.org/ | unknown | — | — | whitelisted |
5956 | chrome.exe | GET | 200 | 172.217.18.14:80 | http://clients2.google.com/time/1/current?cup2key=7:WCHEr1XpmxHHUC3bjfZA8R6tJ2FpvXNn8jOsEIgv9O8&cup2hreq=e3b0c44298fc1c149afbf4c8996fb92427ae41e4649b934ca495991b7852b855 | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
2244 | SIHClient.exe | GET | 200 | 23.219.150.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
5956 | chrome.exe | GET | 204 | 142.250.185.195:80 | http://www.gstatic.com/generate_204 | unknown | — | — | whitelisted |
2244 | SIHClient.exe | GET | 200 | 23.219.150.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
8032 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/lnu3li27zsanbe2hcsfjuvm5fq_1.0.7.1744928549/laoigpblnllgcgjnjnllmfolckpjlhki_1.0.7.1744928549_all_ady56p6vtubsna6mhkx6lu2qml3a.crx3 | unknown | — | — | whitelisted |
8032 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/lnu3li27zsanbe2hcsfjuvm5fq_1.0.7.1744928549/laoigpblnllgcgjnjnllmfolckpjlhki_1.0.7.1744928549_all_ady56p6vtubsna6mhkx6lu2qml3a.crx3 | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
7548 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
7852 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5496 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5496 | MoUsoCoreWorker.exe | 2.16.241.19:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
8056 | chrome.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
5956 | chrome.exe | 74.125.71.84:443 | accounts.google.com | GOOGLE | US | whitelisted |
5956 | chrome.exe | 47.251.16.102:443 | otp.landian.vip | Alibaba US Technology Co., Ltd. | US | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
otp.landian.vip |
| unknown |
accounts.google.com |
| whitelisted |
x1.i.lencr.org |
| whitelisted |
r11.i.lencr.org |
| whitelisted |
clients2.google.com |
| whitelisted |
www.gstatic.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
5956 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] Google Tag Manager analytics (googletagmanager .com) |
5956 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] Google Tag Manager analytics (googletagmanager .com) |
5956 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] Google Tag Manager analytics (googletagmanager .com) |
5956 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] Google Tag Manager analytics (googletagmanager .com) |
5956 | chrome.exe | Potentially Bad Traffic | ET DNS Query to a *.top domain - Likely Hostile |
2196 | svchost.exe | Potentially Bad Traffic | ET DNS Query to a *.top domain - Likely Hostile |