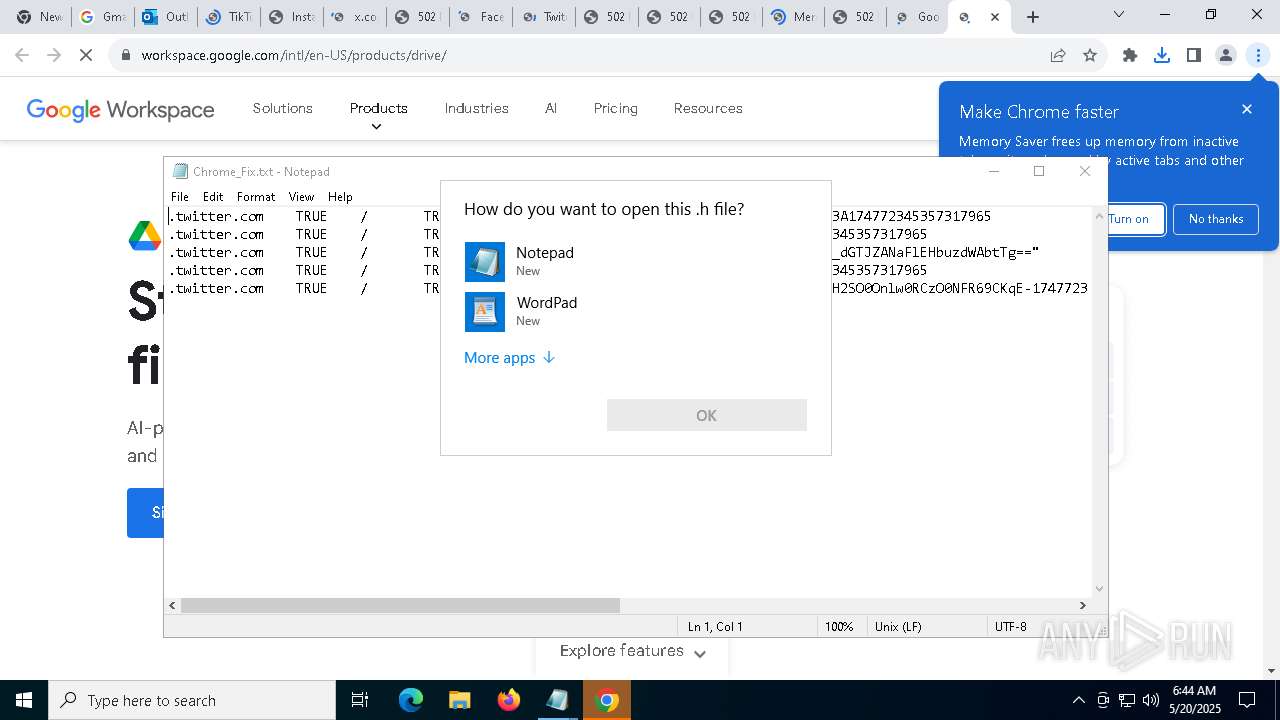
| File name: | TomoEndless.msi |
| Full analysis: | https://app.any.run/tasks/04b34158-ded9-4f45-83d6-a8f9a0329e9c |
| Verdict: | Malicious activity |
| Threats: | Stealers are a group of malicious software that are intended for gaining unauthorized access to users’ information and transferring it to the attacker. The stealer malware category includes various types of programs that focus on their particular kind of data, including files, passwords, and cryptocurrency. Stealers are capable of spying on their targets by recording their keystrokes and taking screenshots. This type of malware is primarily distributed as part of phishing campaigns. |
| Analysis date: | May 20, 2025, 06:42:14 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-msi |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 6.2, MSI Installer, Code page: 1252, Title: Installation Database, Subject: TomoEndLess, Author: TomoEndLess Inc., Keywords: Installer, Comments: This installer database contains the logic and data required to install TomoEndLess., Template: x64;1033, Revision Number: {8A4297E2-2FDF-4209-968A-94D824847737}, Create Time/Date: Fri May 16 21:03:28 2025, Last Saved Time/Date: Fri May 16 21:03:28 2025, Number of Pages: 500, Number of Words: 2, Name of Creating Application: WiX Toolset (4.0.0.5512), Security: 2 |
| MD5: | 09748B3543BCE7557CA826910F6A28DA |
| SHA1: | 5DAF6947C64F8128BA7FB4E702AAE179F561C19D |
| SHA256: | B6D9E593A48BBAC4079D7BED14C3519D6BF669F736BB9EB16542F01AA8025D6E |
| SSDEEP: | 786432:zR5XqJfsGyAWgw/rgjS577CKlPGXVFOqmA9OYxd:z/KfsGyft/rgjS577CKlPGXVFOqmA9O |
MALICIOUS
Bypass execution policy to execute commands
- powershell.exe (PID: 840)
Changes powershell execution policy (Bypass)
- cmd.exe (PID: 1672)
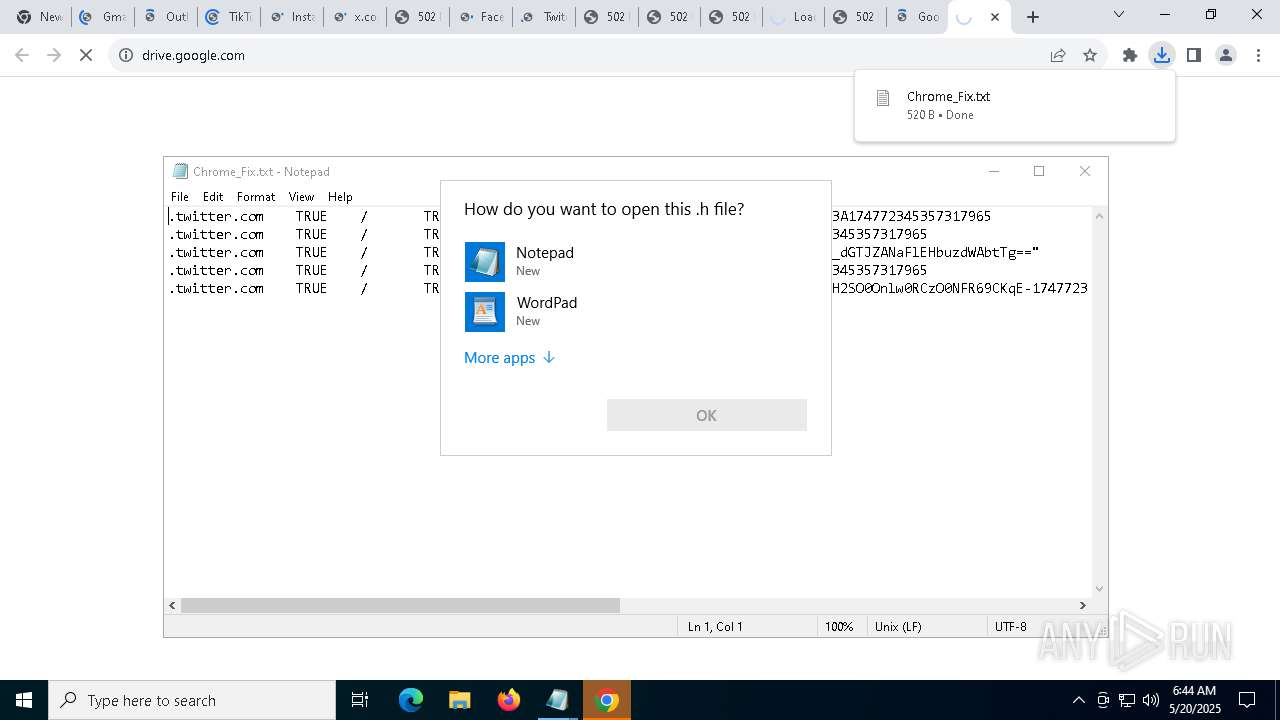
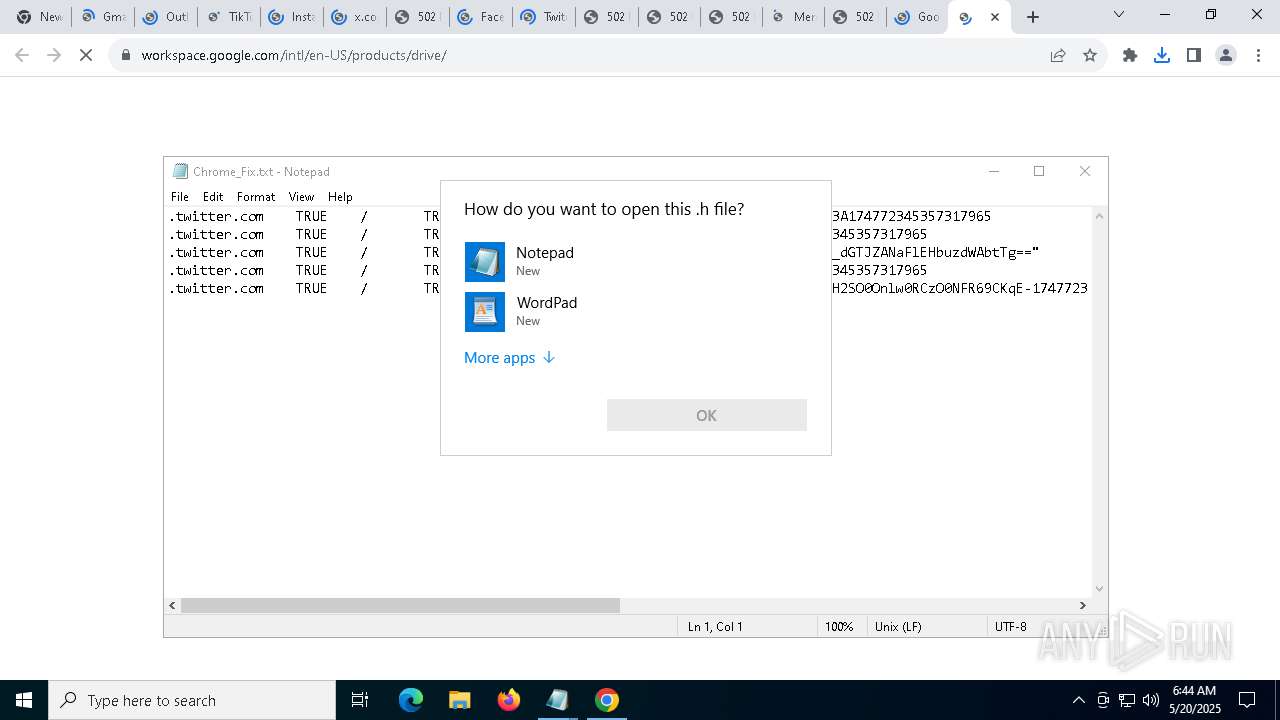
Suspicious browser debugging (Possible cookie theft)
- chrome.exe (PID: 4376)
- msedge.exe (PID: 8732)
SUSPICIOUS
Executes as Windows Service
- VSSVC.exe (PID: 4812)
Process drops legitimate windows executable
- msiexec.exe (PID: 4452)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 4300)
- cmd.exe (PID: 1672)
- cmd.exe (PID: 5084)
- cmd.exe (PID: 2776)
The process executes Powershell scripts
- cmd.exe (PID: 1672)
CSC.EXE is used to compile C# code
- csc.exe (PID: 6724)
Executable content was dropped or overwritten
- csc.exe (PID: 6724)
The process executes VB scripts
- cmd.exe (PID: 3100)
- cmd.exe (PID: 6392)
- cmd.exe (PID: 6724)
- cmd.exe (PID: 4464)
Starts CMD.EXE for commands execution
- TomoEndLess.exe (PID: 6136)
Cryptography encrypted command line is found
- powershell.exe (PID: 2552)
- cmd.exe (PID: 5084)
- cmd.exe (PID: 2776)
- powershell.exe (PID: 5360)
Uses TASKKILL.EXE to kill Browsers
- cmd.exe (PID: 3760)
- cmd.exe (PID: 7648)
- cmd.exe (PID: 8484)
- cmd.exe (PID: 9328)
- cmd.exe (PID: 7540)
Application launched itself
- TomoEndLess.exe (PID: 6136)
MS Edge headless start
- msedge.exe (PID: 9036)
- msedge.exe (PID: 8732)
Potential Corporate Privacy Violation
- TomoEndLess.exe (PID: 6136)
Checks for external IP
- TomoEndLess.exe (PID: 6136)
INFO
Checks supported languages
- msiexec.exe (PID: 4452)
Reads the computer name
- msiexec.exe (PID: 4452)
The sample compiled with english language support
- msiexec.exe (PID: 4452)
Executable content was dropped or overwritten
- msiexec.exe (PID: 4452)
Manages system restore points
- SrTasks.exe (PID: 4400)
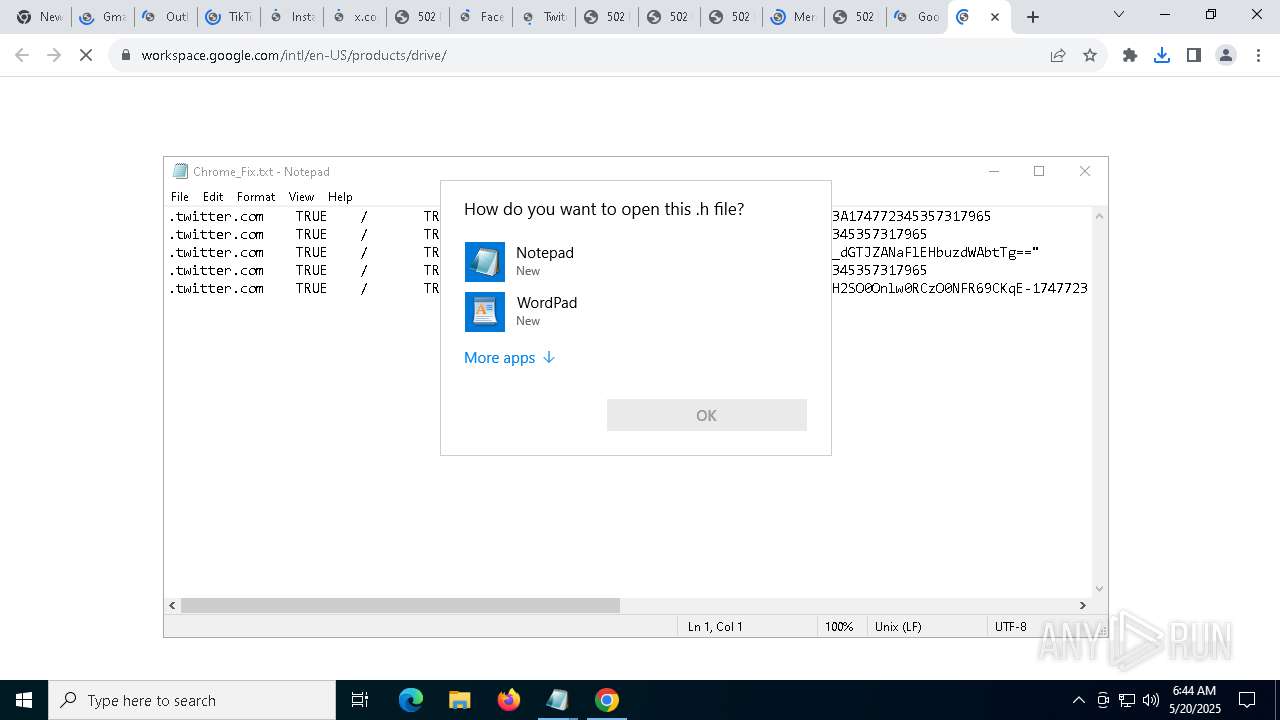
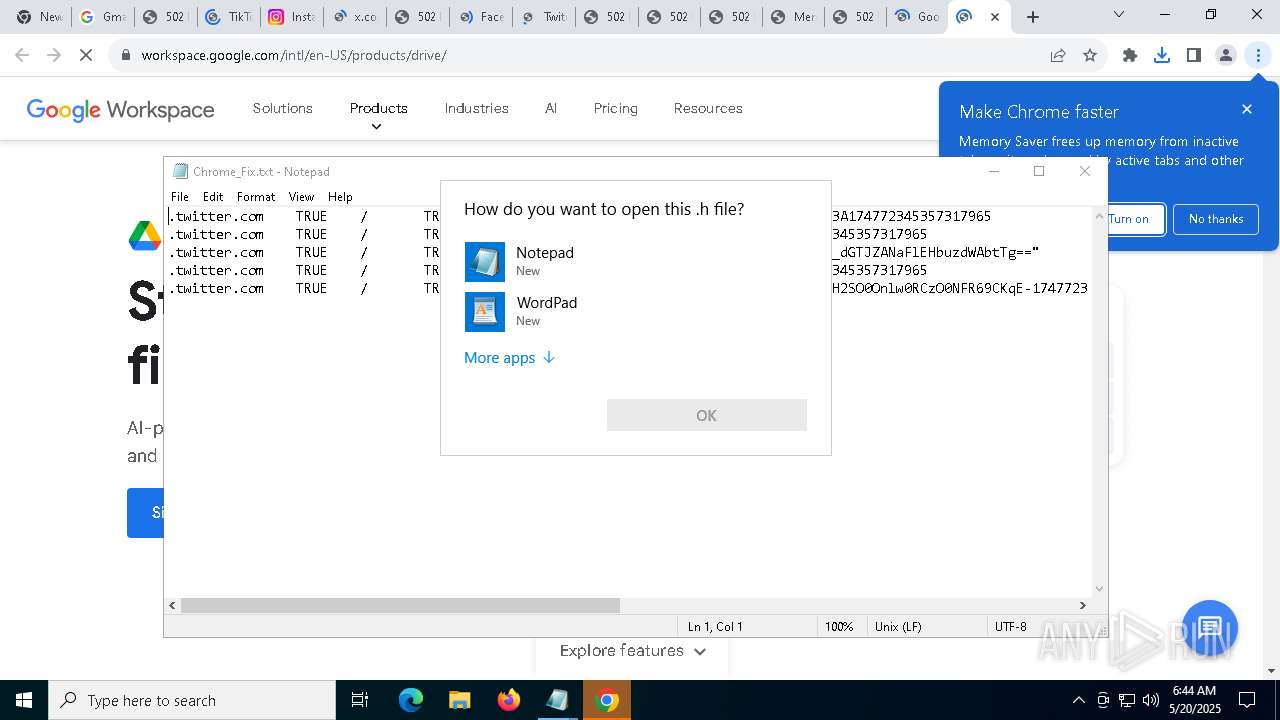
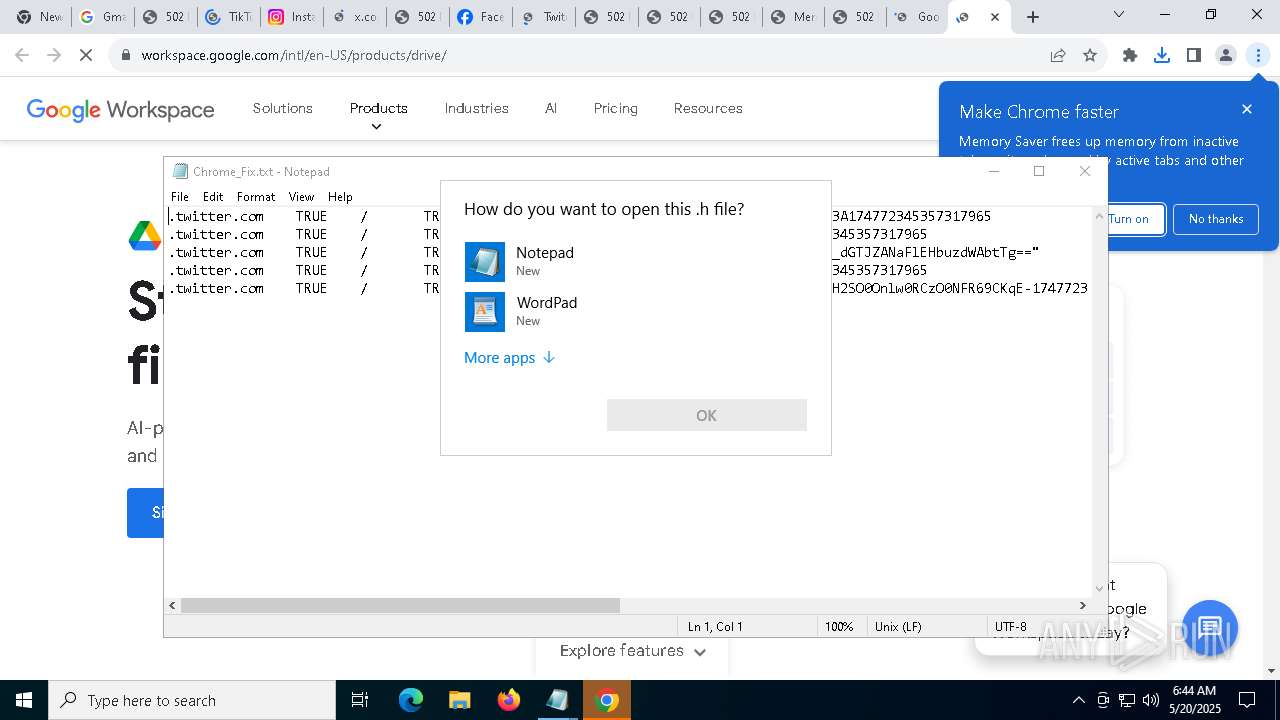
Manual execution by a user
- notepad.exe (PID: 2288)
- OpenWith.exe (PID: 6080)
- OpenWith.exe (PID: 904)
- OpenWith.exe (PID: 4268)
- OpenWith.exe (PID: 6252)
- OpenWith.exe (PID: 1812)
- OpenWith.exe (PID: 5056)
- OpenWith.exe (PID: 2088)
- OpenWith.exe (PID: 6872)
- OpenWith.exe (PID: 2344)
- OpenWith.exe (PID: 6980)
- notepad.exe (PID: 8132)
Application launched itself
- chrome.exe (PID: 5376)
- chrome.exe (PID: 4376)
- chrome.exe (PID: 7772)
- msedge.exe (PID: 8732)
Attempting to use instant messaging service
- chrome.exe (PID: 7924)
- svchost.exe (PID: 2196)
Auto-launch of the file from Downloads directory
- chrome.exe (PID: 7772)
- chrome.exe (PID: 8424)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .msi | | | Microsoft Installer (100) |
|---|
EXIF
FlashPix
| CodePage: | Windows Latin 1 (Western European) |
|---|---|
| Title: | Installation Database |
| Subject: | TomoEndLess |
| Author: | TomoEndLess Inc. |
| Keywords: | Installer |
| Comments: | This installer database contains the logic and data required to install TomoEndLess. |
| Template: | x64;1033 |
| RevisionNumber: | {8A4297E2-2FDF-4209-968A-94D824847737} |
| CreateDate: | 2025:05:16 21:03:28 |
| ModifyDate: | 2025:05:16 21:03:28 |
| Pages: | 500 |
| Words: | 2 |
| Software: | WiX Toolset (4.0.0.5512) |
| Security: | Read-only recommended |
Total processes
273
Monitored processes
145
Malicious processes
4
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 668 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --no-appcompat-clear --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=18 --mojo-platform-channel-handle=5836 --field-trial-handle=1928,i,9022316466366216446,3525644067413028807,262144 --variations-seed-version /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Version: 122.0.6261.70 Modules
| |||||||||||||||
| 684 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 684 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --noerrdialogs --user-data-dir="C:\Users\admin\AppData\Local\Google\Chrome\User Data" --no-appcompat-clear --remote-debugging-port=9522 --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=5 --mojo-platform-channel-handle=3936 --field-trial-handle=1936,i,6912656179932911375,4999448098330190176,262144 --disable-features=PaintHolding --variations-seed-version /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 1 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 720 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --noerrdialogs --user-data-dir="C:\Users\admin\AppData\Local\Google\Chrome\User Data" --extension-process --no-appcompat-clear --remote-debugging-port=9522 --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=8 --mojo-platform-channel-handle=4328 --field-trial-handle=1936,i,6912656179932911375,4999448098330190176,262144 --disable-features=PaintHolding --variations-seed-version /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 1 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 840 | powershell.exe -ExecutionPolicy Bypass -File "C:\Users\admin\AppData\Local\Temp\nrb52b2qv4.ps1" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 904 | "C:\WINDOWS\System32\OpenWith.exe" C:\Users\admin\Desktop\config.guess | C:\Windows\System32\OpenWith.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Pick an app Exit code: 2147943623 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 968 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1072 | cscript //Nologo "C:\Users\admin\AppData\Local\Temp\5558823176.vbs" | C:\Windows\System32\cscript.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Console Based Script Host Exit code: 0 Version: 5.812.10240.16384 Modules
| |||||||||||||||
| 1132 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --no-appcompat-clear --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=15 --mojo-platform-channel-handle=5388 --field-trial-handle=1928,i,9022316466366216446,3525644067413028807,262144 --variations-seed-version /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 1240 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --no-appcompat-clear --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=24 --mojo-platform-channel-handle=6716 --field-trial-handle=1928,i,9022316466366216446,3525644067413028807,262144 --variations-seed-version /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Version: 122.0.6261.70 Modules
| |||||||||||||||
Total events
60 286
Read events
59 869
Write events
397
Delete events
20
Modification events
| (PID) Process: | (4452) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SystemRestore |
| Operation: | write | Name: | SrCreateRp (Enter) |
Value: 480000000000000055A5CB6F52C9DB016411000054140000D50700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (4452) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGetSnapshots (Enter) |
Value: 480000000000000055A5CB6F52C9DB016411000054140000D20700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (4452) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGetSnapshots (Leave) |
Value: 4800000000000000ADA1287052C9DB016411000054140000D20700000100000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (4452) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppEnumGroups (Enter) |
Value: 4800000000000000ADA1287052C9DB016411000054140000D10700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (4452) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppEnumGroups (Leave) |
Value: 48000000000000003AD12F7052C9DB016411000054140000D10700000100000000000000010000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (4452) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppCreate (Enter) |
Value: 48000000000000007D82347052C9DB016411000054140000D00700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (4452) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\SPP |
| Operation: | write | Name: | LastIndex |
Value: 11 | |||
| (PID) Process: | (4452) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGatherWriterMetadata (Enter) |
Value: 4800000000000000B95DA97052C9DB016411000054140000D30700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (4452) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\VssapiPublisher |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 4800000000000000FB24AE7052C9DB016411000078020000E8030000010000000000000000000000EC659214E52757429B14E42A7758952200000000000000000000000000000000 | |||
| (PID) Process: | (4812) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\Shadow Copy Optimization Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 48000000000000002CA2B77052C9DB01CC120000780C0000E80300000100000001000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
Executable files
22
Suspicious files
1 056
Text files
196
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4452 | msiexec.exe | C:\System Volume Information\SPP\metadata-2 | — | |
MD5:— | SHA256:— | |||
| 4452 | msiexec.exe | C:\Windows\Installer\117ed2.msi | — | |
MD5:— | SHA256:— | |||
| 4452 | msiexec.exe | C:\Users\admin\AppData\Local\Programs\TomoEndLess\LICENSES.chromium.html | — | |
MD5:— | SHA256:— | |||
| 4452 | msiexec.exe | C:\Users\admin\AppData\Local\Programs\TomoEndLess\TomoEndLess.exe | — | |
MD5:— | SHA256:— | |||
| 4452 | msiexec.exe | C:\Users\admin\AppData\Local\Programs\TomoEndLess\icudtl.dat | — | |
MD5:— | SHA256:— | |||
| 4452 | msiexec.exe | C:\Users\admin\AppData\Local\Programs\TomoEndLess\resources.pak | — | |
MD5:— | SHA256:— | |||
| 4452 | msiexec.exe | C:\Users\admin\AppData\Local\Programs\TomoEndLess\resources\app.asar | — | |
MD5:— | SHA256:— | |||
| 4452 | msiexec.exe | C:\Windows\Temp\~DF8FEB77D9C2889462.TMP | binary | |
MD5:EBECFF660BC5B28D789D64AD9CF225DB | SHA256:453CE2375DBBCE7AF6FE2AB9D536907DDA1CA71BAEDBE61C0B59F181FAF308D7 | |||
| 4452 | msiexec.exe | C:\Windows\Temp\~DFE90972D5EFD982B5.TMP | binary | |
MD5:BF619EAC0CDF3F68D496EA9344137E8B | SHA256:076A27C79E5ACE2A3D47F9DD2E83E4FF6EA8872B3C2218F66C92B89B55F36560 | |||
| 4452 | msiexec.exe | C:\Users\admin\AppData\Local\Programs\TomoEndLess\chrome_100_percent.pak | binary | |
MD5:FACAE785097B1C688DA1DD683207B47E | SHA256:0ED41F76ACAEFBE6B2C1E79875D86A4FFE2875BC9040BC91C77E494F63A872CA | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
15
TCP/UDP connections
539
DNS requests
325
Threats
43
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4880 | SIHClient.exe | GET | 200 | 23.216.77.6:80 | http://crl.microsoft.com/pki/crl/products/MicTimStaPCA_2010-07-01.crl | unknown | — | — | whitelisted |
4880 | SIHClient.exe | GET | 200 | 23.216.77.6:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut_2010-06-23.crl | unknown | — | — | whitelisted |
4880 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20Update%20Signing%20CA%202.1.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.16.164.107:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4880 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
4880 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Signing%20CA%202.1.crl | unknown | — | — | whitelisted |
4880 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20Update%20Signing%20CA%202.2.crl | unknown | — | — | whitelisted |
4880 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Signing%20CA%202.2.crl | unknown | — | — | whitelisted |
— | — | HEAD | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/imoffpf67hel7kbknqflao2oo4_1.0.2738.0/neifaoindggfcjicffkgpmnlppeffabd_1.0.2738.0_win64_kj4dp5kifwxbdodqls7e5nzhtm.crx3 | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 172.211.123.249:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
— | — | 40.126.31.129:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 2.16.164.107:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
— | — | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4880 | SIHClient.exe | 52.149.20.212:443 | slscr.update.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
3216 | svchost.exe | 172.211.123.249:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
7924 | chrome.exe | Misc activity | ET INFO Observed Discord Domain in DNS Lookup (discord .com) |
7924 | chrome.exe | Misc activity | ET INFO Observed Discord Domain in DNS Lookup (discord .com) |
7924 | chrome.exe | Misc activity | ET INFO Discord Chat Service Domain in DNS Lookup (discord .com) |
7924 | chrome.exe | Misc activity | ET INFO Discord Chat Service Domain in DNS Lookup (discord .com) |
7924 | chrome.exe | Misc activity | ET INFO Observed Discord Domain (discord .com in TLS SNI) |
7924 | chrome.exe | Misc activity | ET INFO Observed Discord Service Domain (discord .com) in TLS SNI |
7924 | chrome.exe | Misc activity | ET INFO Observed Discord Domain (discord .com in TLS SNI) |
7924 | chrome.exe | Misc activity | ET INFO Observed Discord Service Domain (discord .com) in TLS SNI |
6136 | TomoEndLess.exe | Misc activity | ET INFO Observed Discord Domain (discord .com in TLS SNI) |
6136 | TomoEndLess.exe | Misc activity | ET INFO Observed Discord Domain (discord .com in TLS SNI) |