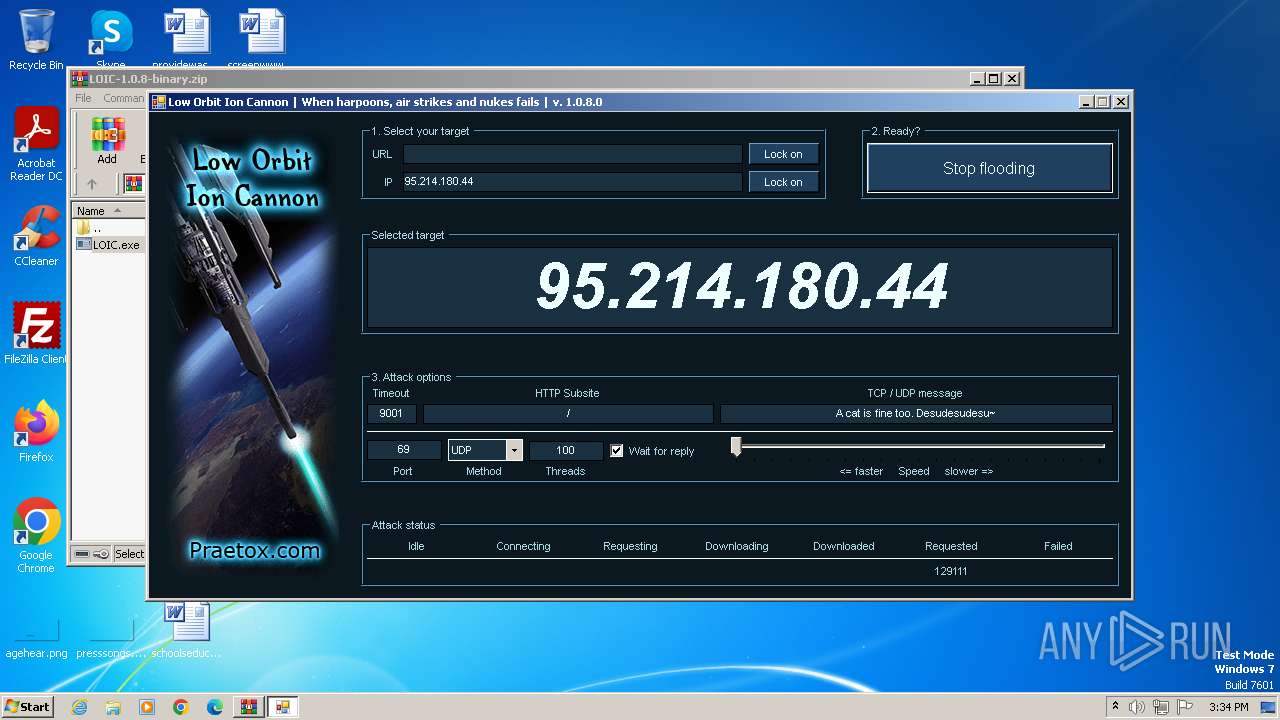
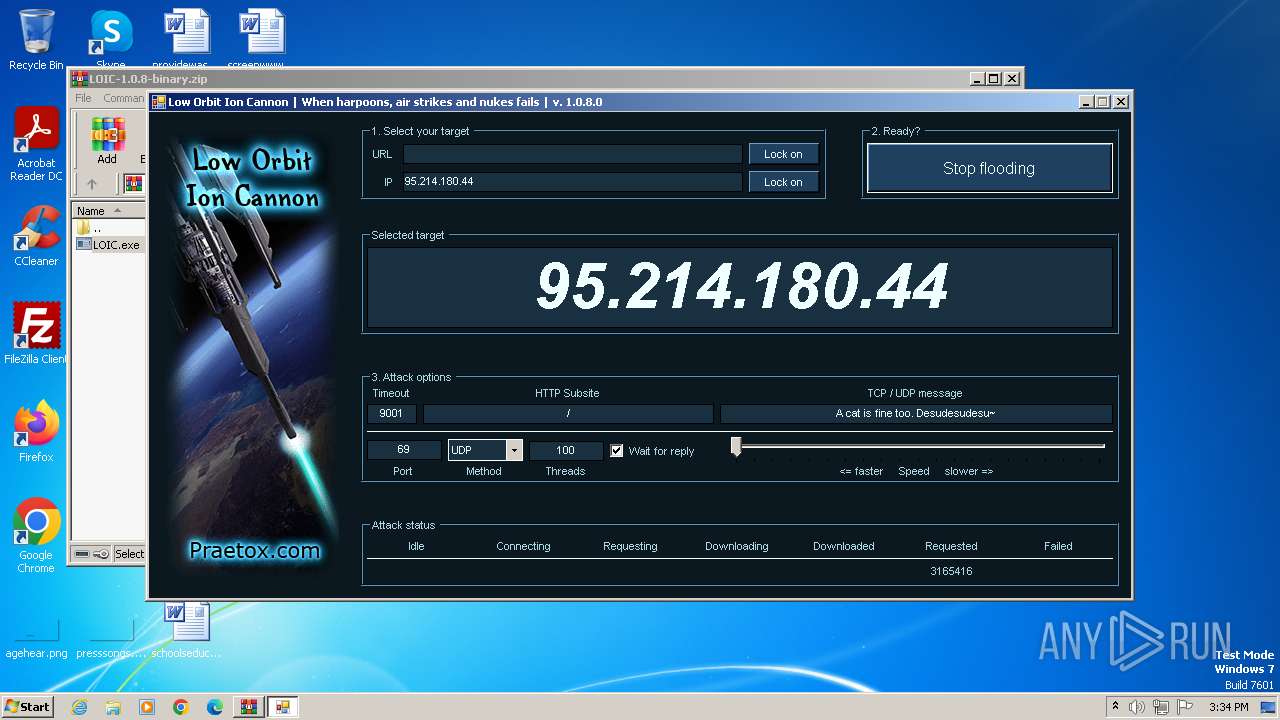
| File name: | LOIC-1.0.8-binary.zip |
| Full analysis: | https://app.any.run/tasks/a426b625-8754-418f-9479-dc144720bd63 |
| Verdict: | Malicious activity |
| Analysis date: | December 02, 2023, 15:33:29 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | C615DA1584CF050CF81A08D40309D735 |
| SHA1: | FF00F68B03F7BBC785284ABD95A54D5B98F7DB9B |
| SHA256: | B6D6E0D1DCE867836A684A0AF278E46ED4A50BE49A784AB7BFCB3ED59841C9D0 |
| SSDEEP: | 3072:n1sQ9BKWms487f1j/XjSGrJmjJ7cAs1QRls:nuQ9Tmd41jfD0lgXQRG |
MALICIOUS
No malicious indicators.SUSPICIOUS
Checks Windows Trust Settings
- LOIC.exe (PID: 3872)
Reads settings of System Certificates
- LOIC.exe (PID: 3872)
Reads the Internet Settings
- LOIC.exe (PID: 3872)
Reads Microsoft Outlook installation path
- LOIC.exe (PID: 3872)
Reads security settings of Internet Explorer
- LOIC.exe (PID: 3872)
Connects to unusual port
- LOIC.exe (PID: 3872)
Reads Internet Explorer settings
- LOIC.exe (PID: 3872)
INFO
Drops the executable file immediately after the start
- WinRAR.exe (PID: 2144)
Reads the computer name
- LOIC.exe (PID: 3872)
- wmpnscfg.exe (PID: 1360)
Checks supported languages
- LOIC.exe (PID: 3872)
- wmpnscfg.exe (PID: 1360)
Checks proxy server information
- LOIC.exe (PID: 3872)
Reads the machine GUID from the registry
- LOIC.exe (PID: 3872)
Creates files or folders in the user directory
- LOIC.exe (PID: 3872)
Manual execution by a user
- wmpnscfg.exe (PID: 1360)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2014:12:12 21:09:00 |
| ZipCRC: | 0x3aef8268 |
| ZipCompressedSize: | 103047 |
| ZipUncompressedSize: | 136192 |
| ZipFileName: | LOIC.exe |
Total processes
39
Monitored processes
3
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1360 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2144 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\LOIC-1.0.8-binary.zip" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 3872 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa2144.20390\LOIC.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa2144.20390\LOIC.exe | WinRAR.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: Low Orbit Ion Cannon Exit code: 0 Version: 1.0.8.0 Modules
| |||||||||||||||
Total events
6 370
Read events
6 310
Write events
60
Delete events
0
Modification events
| (PID) Process: | (2144) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\17F\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2144) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (2144) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (2144) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (2144) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2144) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2144) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2144) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2144) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (2144) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
Executable files
1
Suspicious files
16
Text files
5
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3872 | LOIC.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\E2C6CBAF0AF08CF203BA74BF0D0AB6D5_49536AB5156BDD74EFF881D01C36A419 | binary | |
MD5:F24C0B580B6A72F8E70CCA79515686DB | SHA256:ED187EEF98104F97E7B1391F21E52552F359FBB630D6FB83C38868DAA880ADDF | |||
| 3872 | LOIC.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\80237EE4964FC9C409AAF55BF996A292_C5130A0BDC8C859A2757D77746C10868 | binary | |
MD5:5F4130C766294375E7D2B34BB99770F5 | SHA256:AA06B6419E25311AB730DC05513AF28DD8112CA7F209415EFED269B201F4E1E1 | |||
| 3872 | LOIC.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\7423F88C7F265F0DEFC08EA88C3BDE45_AA1E8580D4EBC816148CE81268683776 | binary | |
MD5:A7FA5AE756EA7D229AD8C62037E57BF6 | SHA256:008A3975E933B1C836C291C6620950C211B4A3CB7D76B186CB4619F35A5DABCF | |||
| 3872 | LOIC.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\59D76868C250B3240414CE3EFBB12518_B59D7D4433266DE253365EA22B317141 | binary | |
MD5:A3F8E62A9399121D7FE0C38DB8C00C5D | SHA256:EB454829C6FB3C07E2C1292A561058AF7C98B6ADF304A7763293430AFB29A616 | |||
| 3872 | LOIC.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\80237EE4964FC9C409AAF55BF996A292_C5130A0BDC8C859A2757D77746C10868 | binary | |
MD5:FD8F9807BD355CD565B287B9F332F2A9 | SHA256:EAF24EBB5CD1859D7D590AA73F0D3D24ABB8A64E30F9DCF19E88C39DA12116B6 | |||
| 3872 | LOIC.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\loicweb[1].htm | html | |
MD5:73772A56FA102A6889F0F1749691F2AC | SHA256:DB4D28D45DF153EC62ABDF2233D1AB5BFD73F4DC1B364625C2839E68FEB23C24 | |||
| 3872 | LOIC.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\6Z2BCOUL\900DHKTG.htm | html | |
MD5:1F653862E2CFCF2E480F2307BED3099E | SHA256:B739866DF8F6FB0EC6E8A7769A6D67502B4407C5EBEB4A3D765825EB3C4EC8B5 | |||
| 3872 | LOIC.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\CAF4703619713E3F18D8A9D5D88D6288_A7725538C46DE2D0088EE44974E2CEBA | binary | |
MD5:AC89A852C2AAA3D389B2D2DD312AD367 | SHA256:0B720E19270C672F9B6E0EC40B468AC49376807DE08A814573FE038779534F45 | |||
| 3872 | LOIC.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\7423F88C7F265F0DEFC08EA88C3BDE45_AA1E8580D4EBC816148CE81268683776 | binary | |
MD5:E56B854D47719A2CDEC70FB36DAA97AE | SHA256:EBCB8FAB892A4F54F3C2332C38C0794EE21F1C0FA7C639F7B7D337B48F243A05 | |||
| 3872 | LOIC.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\PO2HN1X2\ai.0[1].js | text | |
MD5:1DD63DE72CF1F702324245441844BE13 | SHA256:5201C813C37A4168CC5C20C701D4391FD0A55625F97EB9F263A74FB52B52FD0E | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
8
TCP/UDP connections
26
DNS requests
7
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3872 | LOIC.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSnxLiz3Fu1WB6n1%2FE6xWn1b0jXiQQUdIWAwGbH3zfez70pN6oDHb7tzRcCEAjBbMJ9cbDkwwNGsRu7SXg%3D | unknown | binary | 471 b | unknown |
3872 | LOIC.exe | GET | 200 | 87.248.204.0:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?e91561ec8996c2c7 | unknown | compressed | 4.66 Kb | unknown |
3872 | LOIC.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAz1vQYrVgL0erhQLCPM8GY%3D | unknown | binary | 471 b | unknown |
3872 | LOIC.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAqvpsXKY8RRQeo74ffHUxc%3D | unknown | binary | 471 b | unknown |
3872 | LOIC.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | binary | 471 b | unknown |
3872 | LOIC.exe | GET | 200 | 142.250.185.131:80 | http://ocsp.pki.goog/gsr1/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCEHe9DWzbNvka6iEPxPBY0w0%3D | unknown | binary | 1.41 Kb | unknown |
3872 | LOIC.exe | GET | 200 | 142.250.185.131:80 | http://ocsp.pki.goog/gtsr1/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBQwkcLWD4LqGJ7bE7B1XZsEbmfwUAQU5K8rJnEaK0gnhS9SZizv8IkTcT4CDQIDvFNZazTHGPUBUGY%3D | unknown | binary | 724 b | unknown |
3872 | LOIC.exe | GET | 200 | 142.250.185.131:80 | http://ocsp.pki.goog/gts1c3/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEQChuVoVf7HVAxLxWCb2kXo7 | unknown | binary | 472 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2588 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
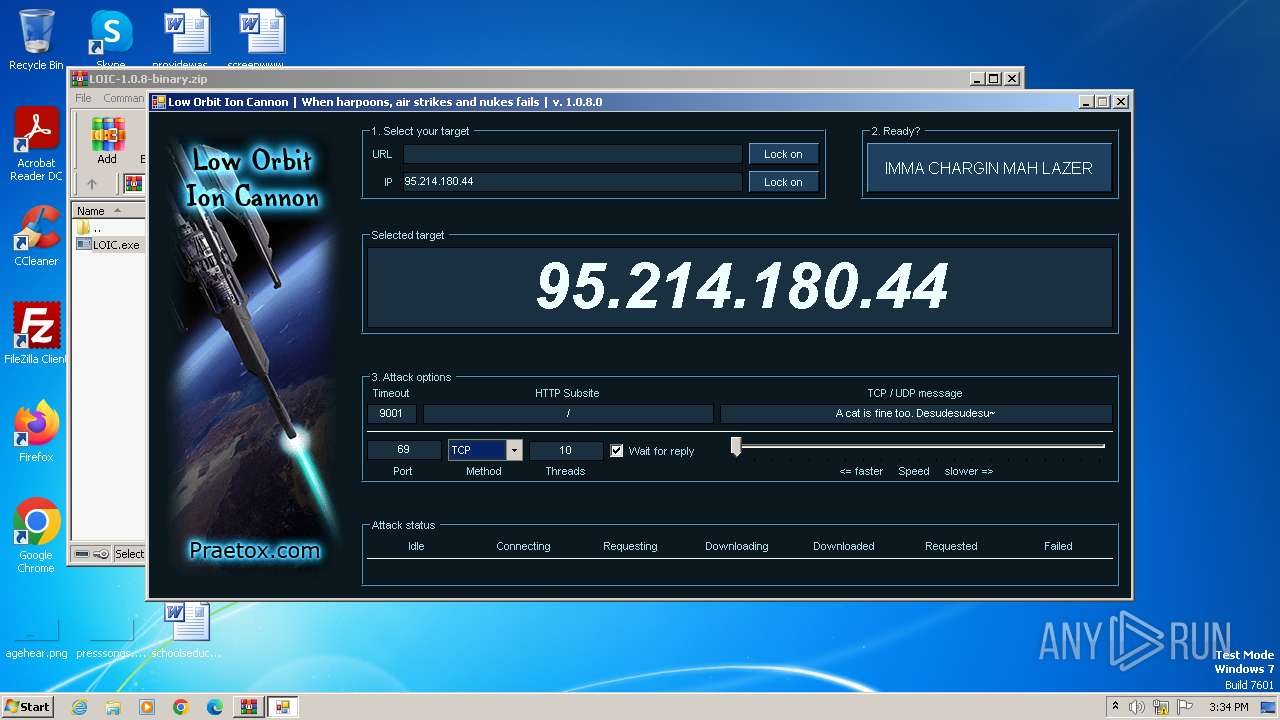
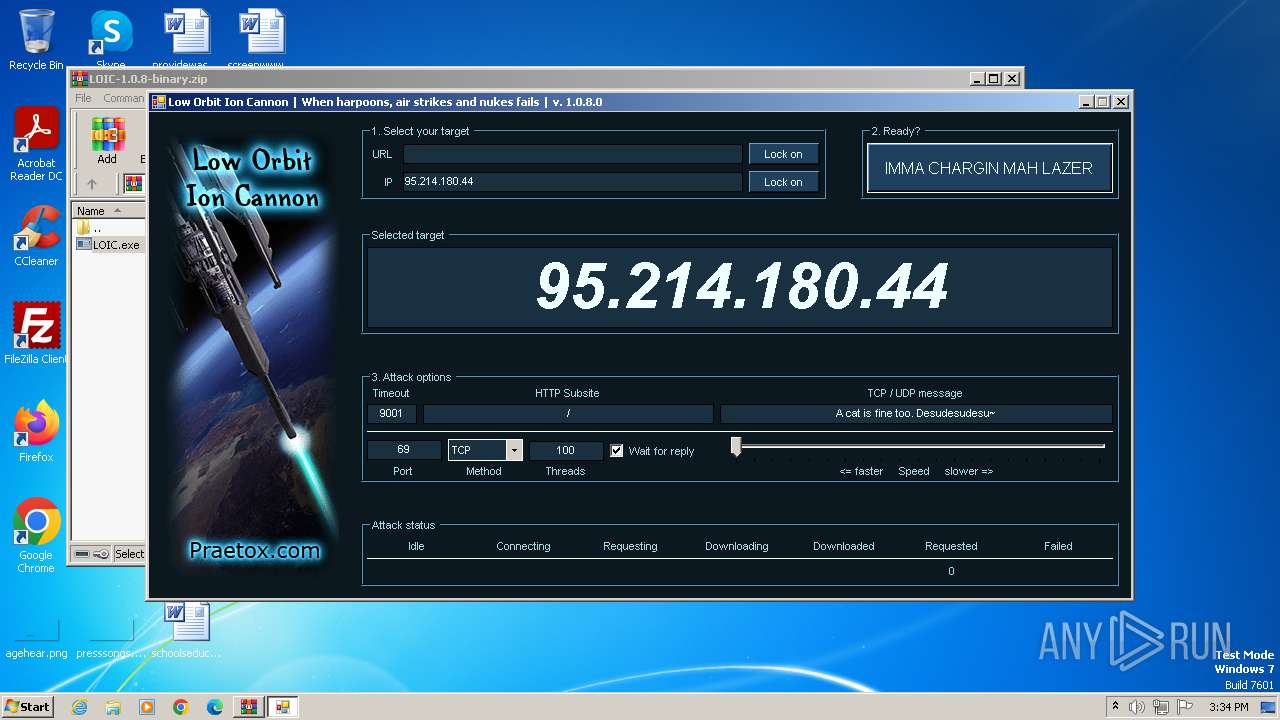
3872 | LOIC.exe | 95.214.180.44:69 | — | Aaron Smith | HK | unknown |
3872 | LOIC.exe | 67.199.248.16:443 | j.mp | GOOGLE-CLOUD-PLATFORM | US | shared |
3872 | LOIC.exe | 87.248.204.0:80 | ctldl.windowsupdate.com | LLNW | US | unknown |
3872 | LOIC.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
3872 | LOIC.exe | 52.179.188.206:443 | loicweb.azurewebsites.net | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
3872 | LOIC.exe | 216.58.206.40:443 | www.googletagmanager.com | GOOGLE | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
j.mp |
| shared |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
loicweb.azurewebsites.net |
| whitelisted |
www.googletagmanager.com |
| whitelisted |
az416426.vo.msecnd.net |
| whitelisted |
ocsp.pki.goog |
| whitelisted |
Threats
1 ETPRO signatures available at the full report