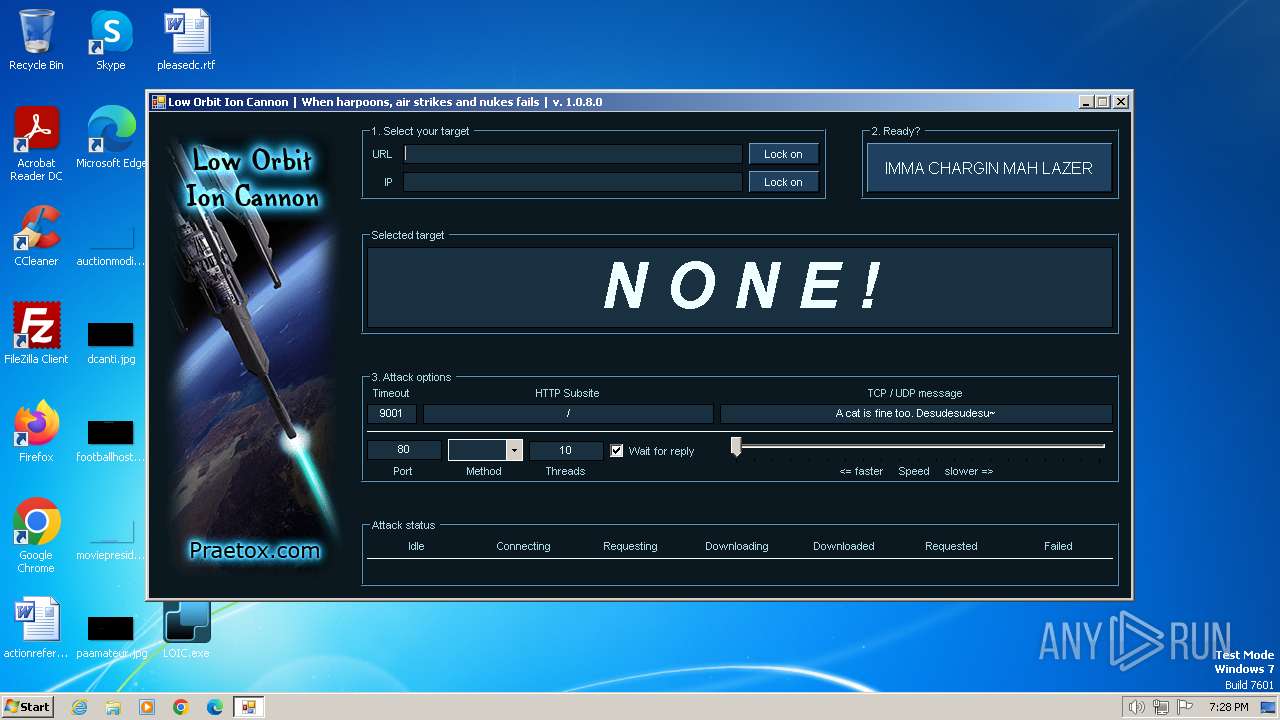
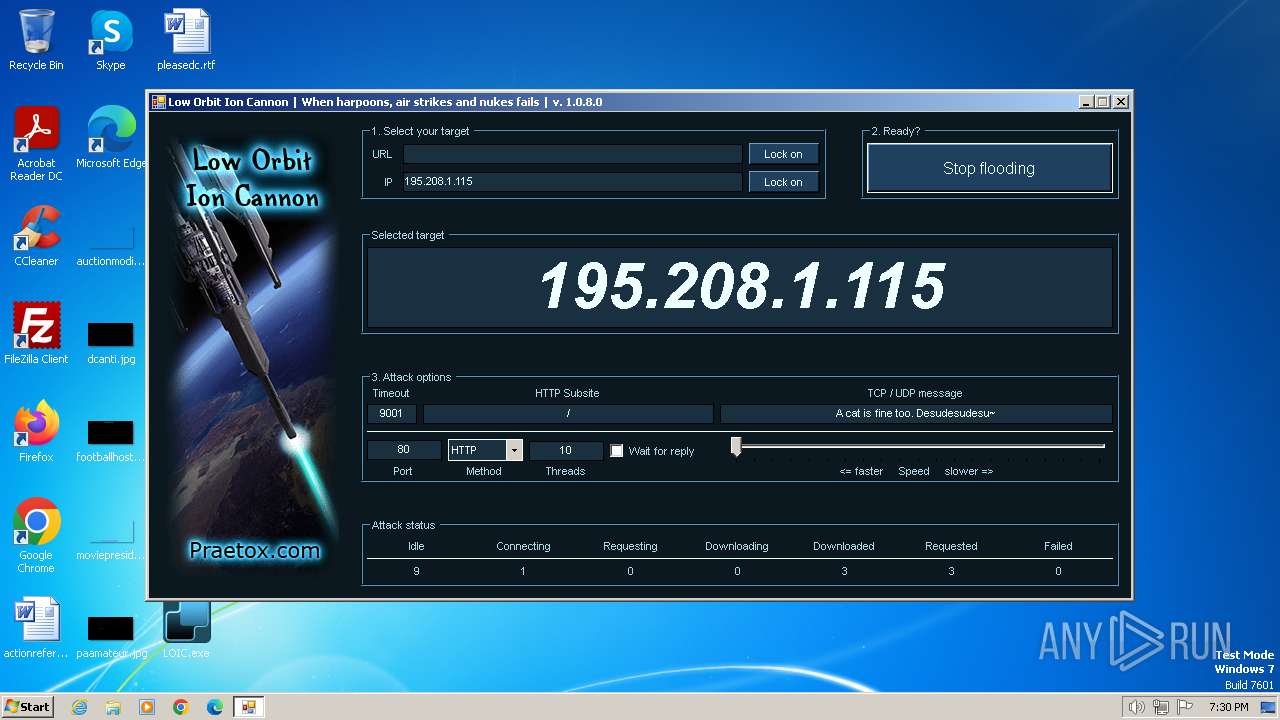
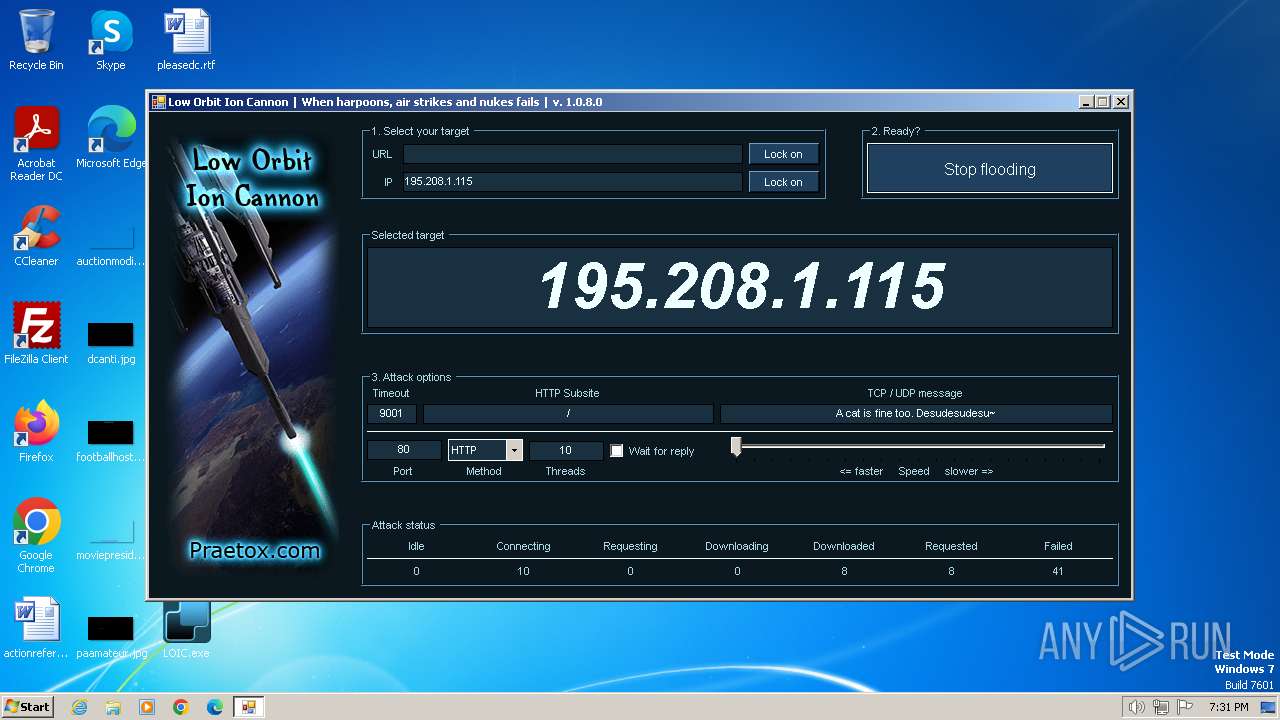
| File name: | LOIC-1.0.8-binary.zip |
| Full analysis: | https://app.any.run/tasks/8216fe40-b479-4d46-be9f-20525089cc87 |
| Verdict: | Malicious activity |
| Analysis date: | February 24, 2024, 19:28:06 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | C615DA1584CF050CF81A08D40309D735 |
| SHA1: | FF00F68B03F7BBC785284ABD95A54D5B98F7DB9B |
| SHA256: | B6D6E0D1DCE867836A684A0AF278E46ED4A50BE49A784AB7BFCB3ED59841C9D0 |
| SSDEEP: | 3072:n1sQ9BKWms487f1j/XjSGrJmjJ7cAs1QRls:nuQ9Tmd41jfD0lgXQRG |
MALICIOUS
Drops the executable file immediately after the start
- WinRAR.exe (PID: 4052)
SUSPICIOUS
Reads the Internet Settings
- LOIC.exe (PID: 2840)
Reads security settings of Internet Explorer
- LOIC.exe (PID: 2840)
Reads settings of System Certificates
- LOIC.exe (PID: 2840)
Reads Microsoft Outlook installation path
- LOIC.exe (PID: 2840)
Checks Windows Trust Settings
- LOIC.exe (PID: 2840)
Reads Internet Explorer settings
- LOIC.exe (PID: 2840)
INFO
Checks supported languages
- LOIC.exe (PID: 2840)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 4052)
Reads the computer name
- LOIC.exe (PID: 2840)
Manual execution by a user
- LOIC.exe (PID: 2840)
Reads the machine GUID from the registry
- LOIC.exe (PID: 2840)
Checks proxy server information
- LOIC.exe (PID: 2840)
Reads the software policy settings
- LOIC.exe (PID: 2840)
Creates files or folders in the user directory
- LOIC.exe (PID: 2840)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2014:12:12 21:09:00 |
| ZipCRC: | 0x3aef8268 |
| ZipCompressedSize: | 103047 |
| ZipUncompressedSize: | 136192 |
| ZipFileName: | LOIC.exe |
Total processes
39
Monitored processes
2
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
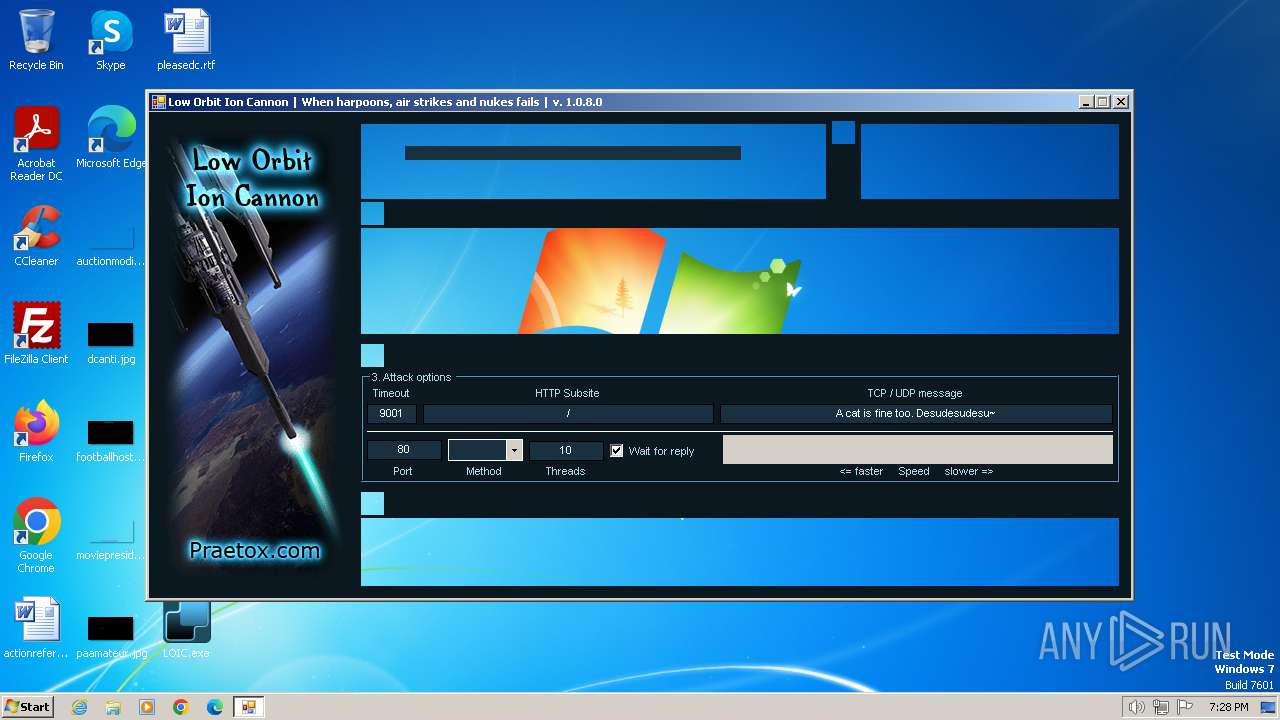
| 2840 | "C:\Users\admin\Desktop\LOIC.exe" | C:\Users\admin\Desktop\LOIC.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: Low Orbit Ion Cannon Exit code: 0 Version: 1.0.8.0 Modules
| |||||||||||||||
| 4052 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\LOIC-1.0.8-binary.zip" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
Total events
9 211
Read events
9 136
Write events
66
Delete events
9
Modification events
| (PID) Process: | (4052) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (4052) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (4052) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (4052) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (4052) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (4052) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\curl-8.5.0_1-win32-mingw.zip | |||
| (PID) Process: | (4052) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\LOIC-1.0.8-binary.zip | |||
| (PID) Process: | (4052) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (4052) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (4052) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
Executable files
1
Suspicious files
12
Text files
5
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2840 | LOIC.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\E2C6CBAF0AF08CF203BA74BF0D0AB6D5_49536AB5156BDD74EFF881D01C36A419 | der | |
MD5:2FBC662D98DCDDE356596A6191947E76 | SHA256:148C0B28E76E64CE51E809009DF3775BAFBC3E91625AFAE9A610420F03AA08AF | |||
| 2840 | LOIC.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\80237EE4964FC9C409AAF55BF996A292_C5130A0BDC8C859A2757D77746C10868 | binary | |
MD5:29234F108F40836DE6B705E3195CAA35 | SHA256:5BCF1ECB4F6B29FA52EE4AD3768CA68D8002DC8322DE0086453CF56B3CD33A41 | |||
| 2840 | LOIC.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\24BD96D5497F70B3F510A6B53CD43F3E_3A89246FB90C5EE6620004F1AE0EB0EA | binary | |
MD5:8E90FB596AC18BE055F83B072D37316E | SHA256:01910B4904EB9DCD601631CC65882F56F04E032FA8BBF441306450BF8CAB14AA | |||
| 2840 | LOIC.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\59D76868C250B3240414CE3EFBB12518_B59D7D4433266DE253365EA22B317141 | binary | |
MD5:0CBF52D24AED2A857DA73919A1678360 | SHA256:E87801146B5235869F4824E566878A986DA931326F57A8DAF1BDC3D50BACCDC4 | |||
| 4052 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa4052.38621\LOIC.exe | executable | |
MD5:E6FA3028CD03318496852718143D256F | SHA256:F60A52512773B52DEF9BA9CE8AAD61144D2CF351F6BC04D1C5A13ABEF8F3B89B | |||
| 2840 | LOIC.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\E2C6CBAF0AF08CF203BA74BF0D0AB6D5_49536AB5156BDD74EFF881D01C36A419 | binary | |
MD5:AB1AD56436B9AB634F5B5489B2D54E93 | SHA256:AF9675AFA8C657FDF461552F0B828D2732E225CDFD13405EBF870AE5871E7588 | |||
| 2840 | LOIC.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\59D76868C250B3240414CE3EFBB12518_B59D7D4433266DE253365EA22B317141 | der | |
MD5:BA189CE946977D4C67254CFF7490B017 | SHA256:EAEF96ADA14DCDE4B09958C38CE98B16A16786A23108EBD2C7742CC9EC2CF4A4 | |||
| 2840 | LOIC.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\loicweb[1].htm | html | |
MD5:73772A56FA102A6889F0F1749691F2AC | SHA256:DB4D28D45DF153EC62ABDF2233D1AB5BFD73F4DC1B364625C2839E68FEB23C24 | |||
| 2840 | LOIC.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\80237EE4964FC9C409AAF55BF996A292_C5130A0BDC8C859A2757D77746C10868 | der | |
MD5:CFCA9350CDDF94225C37AF50CFA3F4FD | SHA256:DD6BB2F0B9BA74B18B23143EDD5D0F09885930F137DE7C1821E41B2C1D765698 | |||
| 2840 | LOIC.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\6Z2BCOUL\GU5NQZT8.htm | html | |
MD5:1F653862E2CFCF2E480F2307BED3099E | SHA256:B739866DF8F6FB0EC6E8A7769A6D67502B4407C5EBEB4A3D765825EB3C4EC8B5 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
3 520
TCP/UDP connections
3 658
DNS requests
8
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
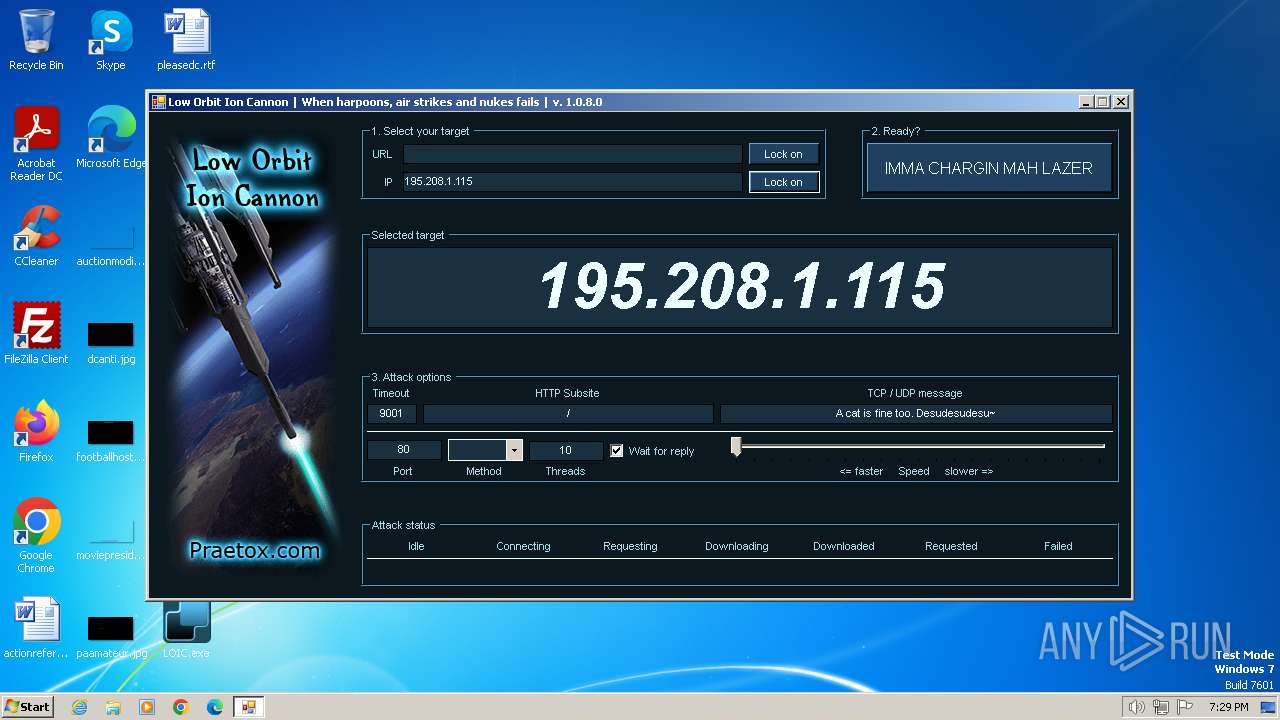
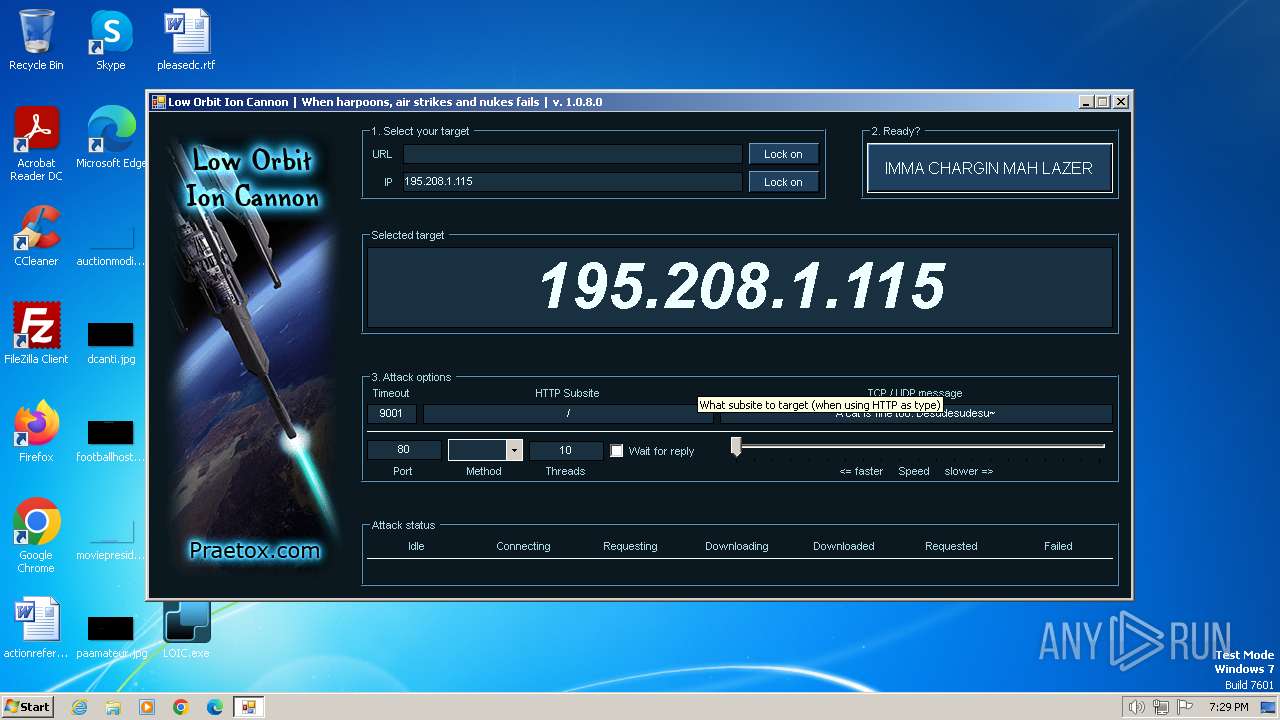
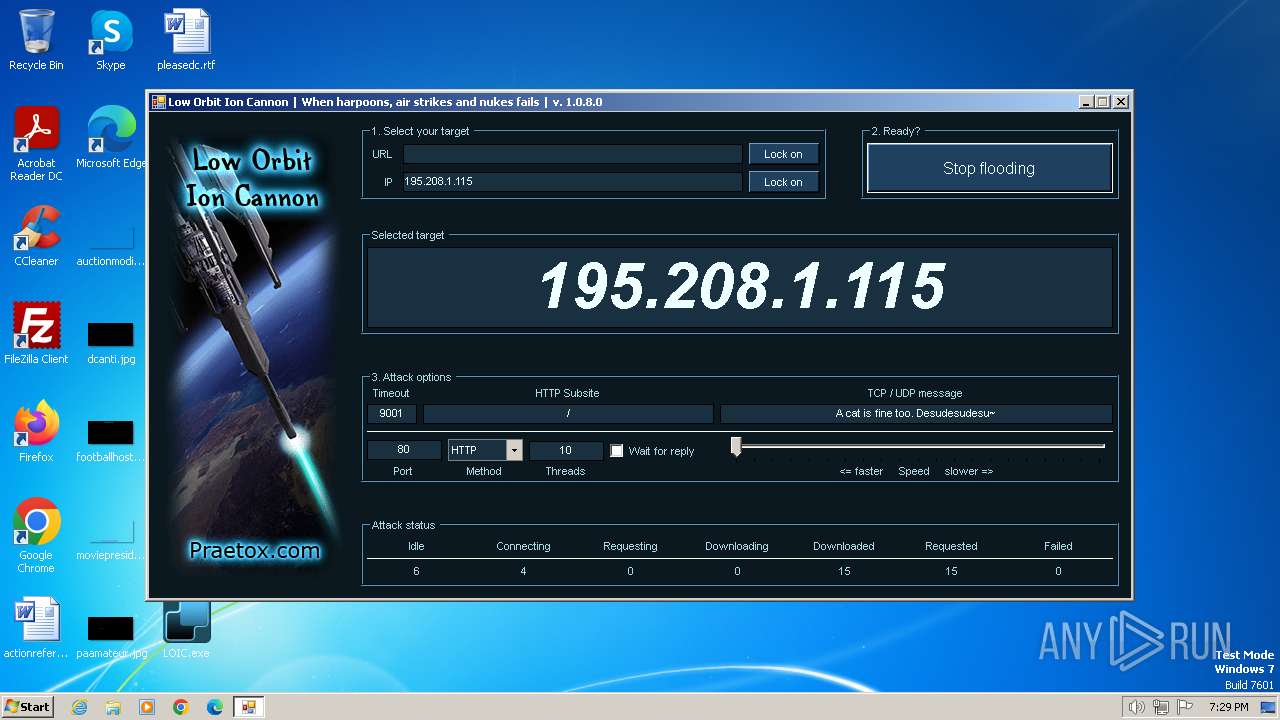
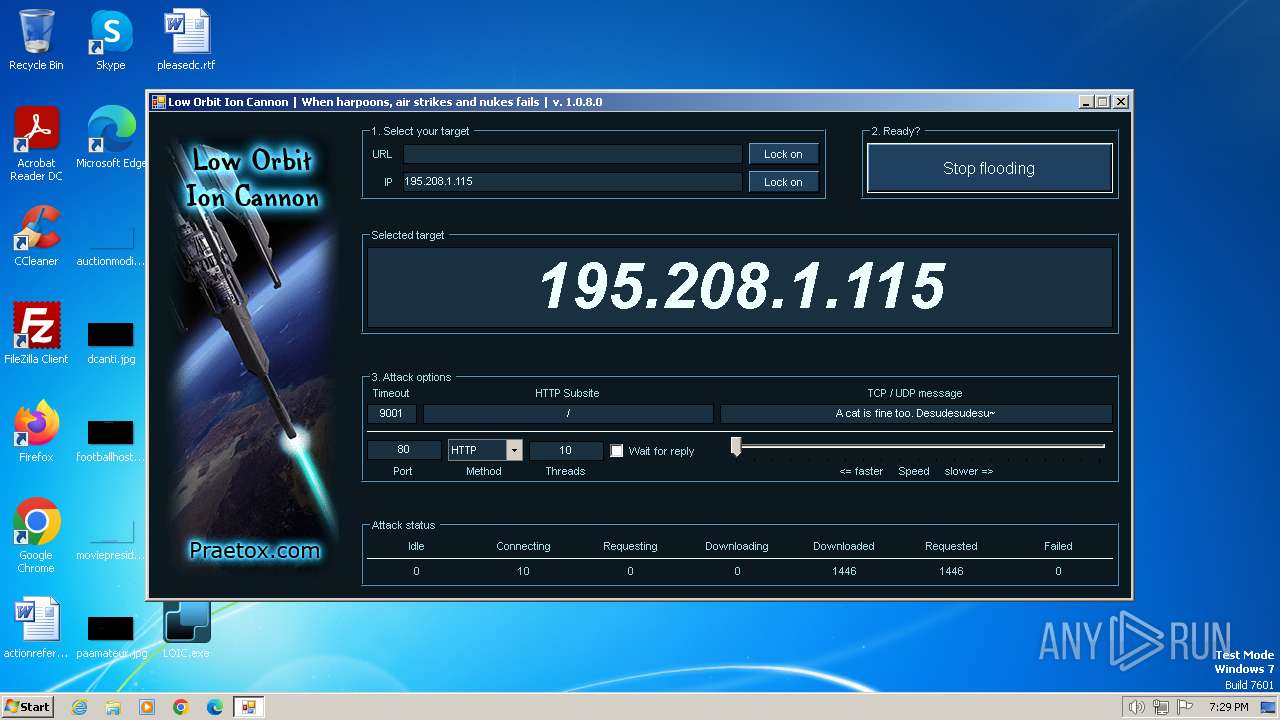
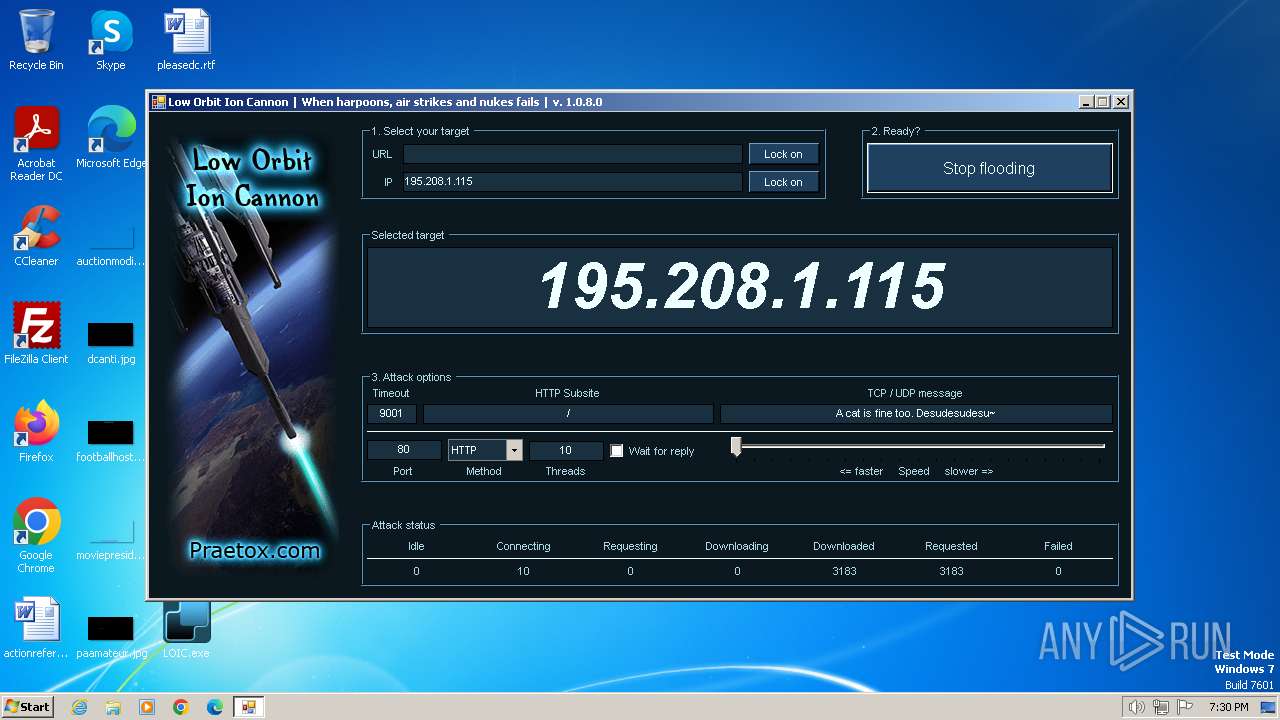
2840 | LOIC.exe | GET | — | 195.208.1.115:80 | http://195.208.1.115:80/ | unknown | — | — | unknown |
2840 | LOIC.exe | GET | — | 195.208.1.115:80 | http://195.208.1.115:80/ | unknown | — | — | unknown |
2840 | LOIC.exe | GET | — | 195.208.1.115:80 | http://195.208.1.115:80/ | unknown | — | — | unknown |
2840 | LOIC.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAz1vQYrVgL0erhQLCPM8GY%3D | unknown | binary | 471 b | unknown |
2840 | LOIC.exe | GET | — | 195.208.1.115:80 | http://195.208.1.115:80/ | unknown | — | — | unknown |
2840 | LOIC.exe | GET | — | 195.208.1.115:80 | http://195.208.1.115:80/ | unknown | — | — | unknown |
2840 | LOIC.exe | GET | — | 195.208.1.115:80 | http://195.208.1.115:80/ | unknown | — | — | unknown |
2840 | LOIC.exe | GET | — | 195.208.1.115:80 | http://195.208.1.115:80/ | unknown | — | — | unknown |
2840 | LOIC.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSnxLiz3Fu1WB6n1%2FE6xWn1b0jXiQQUdIWAwGbH3zfez70pN6oDHb7tzRcCEAjBbMJ9cbDkwwNGsRu7SXg%3D | unknown | binary | 471 b | unknown |
2840 | LOIC.exe | GET | — | 195.208.1.115:80 | http://195.208.1.115:80/ | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2840 | LOIC.exe | 195.208.1.115:80 | — | Jsc ru-center | RU | unknown |
2840 | LOIC.exe | 67.199.248.17:443 | j.mp | GOOGLE-CLOUD-PLATFORM | US | shared |
2840 | LOIC.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
2840 | LOIC.exe | 93.184.221.240:80 | ctldl.windowsupdate.com | EDGECAST | GB | whitelisted |
2840 | LOIC.exe | 52.179.188.206:443 | loicweb.azurewebsites.net | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
2840 | LOIC.exe | 142.250.184.232:443 | www.googletagmanager.com | GOOGLE | US | unknown |
2840 | LOIC.exe | 152.199.19.161:443 | az416426.vo.msecnd.net | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
j.mp |
| shared |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
loicweb.azurewebsites.net |
| whitelisted |
www.googletagmanager.com |
| whitelisted |
az416426.vo.msecnd.net |
| whitelisted |
ocsp.pki.goog |
| whitelisted |