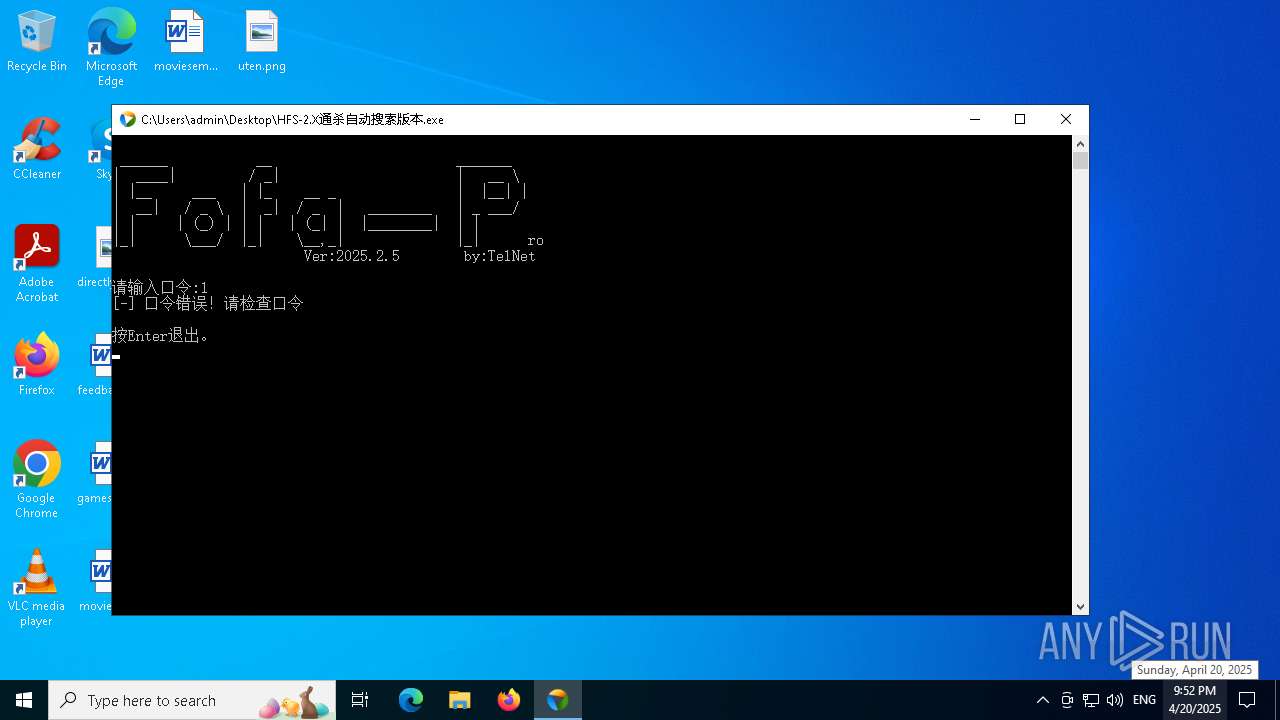
| File name: | HFS-2.X通杀自动搜索版本.exe |
| Full analysis: | https://app.any.run/tasks/6d3116f2-71ec-49f5-a1e3-7b1e9cd0ea0b |
| Verdict: | Malicious activity |
| Analysis date: | April 20, 2025, 21:50:17 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32+ executable (console) x86-64, for MS Windows, 6 sections |
| MD5: | 1EA6A21EA2D6AA5803293FC389EA2296 |
| SHA1: | 9575A411B49B9C103E332ABB50647734CE9ED854 |
| SHA256: | B6CA0A08B398951FDF0F3E9DFD850773168A14BE71C1A6185D4199E34B263C31 |
| SSDEEP: | 98304:1cdJZgYftJg1YWlJzsNq3ymTbOfggNRU5YgUFk3PkRpl49YjW/gZH/DmC2powOm1:Nx6mFBXZhK7 |
MALICIOUS
No malicious indicators.SUSPICIOUS
Process drops python dynamic module
- HFS-2.X通杀自动搜索版本.exe (PID: 6964)
- HFS-2.X通杀自动搜索版本.exe (PID: 6624)
- HFS-2.X通杀自动搜索版本.exe (PID: 5972)
Application launched itself
- HFS-2.X通杀自动搜索版本.exe (PID: 6964)
- HFS-2.X通杀自动搜索版本.exe (PID: 6624)
- HFS-2.X通杀自动搜索版本.exe (PID: 5972)
Loads Python modules
- HFS-2.X通杀自动搜索版本.exe (PID: 1272)
- HFS-2.X通杀自动搜索版本.exe (PID: 6788)
- HFS-2.X通杀自动搜索版本.exe (PID: 6608)
The process executes via Task Scheduler
- PLUGScheduler.exe (PID: 4152)
Process drops legitimate windows executable
- HFS-2.X通杀自动搜索版本.exe (PID: 6624)
- HFS-2.X通杀自动搜索版本.exe (PID: 5972)
- HFS-2.X通杀自动搜索版本.exe (PID: 6964)
The process drops C-runtime libraries
- HFS-2.X通杀自动搜索版本.exe (PID: 6624)
- HFS-2.X通杀自动搜索版本.exe (PID: 5972)
- HFS-2.X通杀自动搜索版本.exe (PID: 6964)
Executable content was dropped or overwritten
- HFS-2.X通杀自动搜索版本.exe (PID: 6624)
- HFS-2.X通杀自动搜索版本.exe (PID: 5972)
- HFS-2.X通杀自动搜索版本.exe (PID: 6964)
Uses RUNDLL32.EXE to load library
- explorer.exe (PID: 5332)
INFO
Checks supported languages
- HFS-2.X通杀自动搜索版本.exe (PID: 6964)
- HFS-2.X通杀自动搜索版本.exe (PID: 1272)
- PLUGScheduler.exe (PID: 4152)
- HFS-2.X通杀自动搜索版本.exe (PID: 6624)
- HFS-2.X通杀自动搜索版本.exe (PID: 6788)
- HFS-2.X通杀自动搜索版本.exe (PID: 5972)
- HFS-2.X通杀自动搜索版本.exe (PID: 6608)
Reads the computer name
- HFS-2.X通杀自动搜索版本.exe (PID: 6964)
- PLUGScheduler.exe (PID: 4152)
- HFS-2.X通杀自动搜索版本.exe (PID: 6624)
- HFS-2.X通杀自动搜索版本.exe (PID: 5972)
Create files in a temporary directory
- HFS-2.X通杀自动搜索版本.exe (PID: 6964)
- HFS-2.X通杀自动搜索版本.exe (PID: 6624)
- HFS-2.X通杀自动搜索版本.exe (PID: 5972)
The sample compiled with english language support
- HFS-2.X通杀自动搜索版本.exe (PID: 6964)
- HFS-2.X通杀自动搜索版本.exe (PID: 6624)
- HFS-2.X通杀自动搜索版本.exe (PID: 5972)
PyInstaller has been detected (YARA)
- HFS-2.X通杀自动搜索版本.exe (PID: 6964)
Reads the machine GUID from the registry
- HFS-2.X通杀自动搜索版本.exe (PID: 1272)
- HFS-2.X通杀自动搜索版本.exe (PID: 6788)
- HFS-2.X通杀自动搜索版本.exe (PID: 6608)
Checks transactions between databases Windows and Oracle
- rundll32.exe (PID: 1300)
Reads security settings of Internet Explorer
- dllhost.exe (PID: 2344)
Creates files in the program directory
- PLUGScheduler.exe (PID: 4152)
Reads the software policy settings
- dllhost.exe (PID: 2344)
Manual execution by a user
- HFS-2.X通杀自动搜索版本.exe (PID: 6624)
- HFS-2.X通杀自动搜索版本.exe (PID: 5972)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | InstallShield setup (57.6) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (36.9) |
| .exe | | | Generic Win/DOS Executable (2.6) |
| .exe | | | DOS Executable Generic (2.6) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2025:02:05 10:42:54+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 14.41 |
| CodeSize: | 176640 |
| InitializedDataSize: | 115712 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xc380 |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows command line |
Total processes
297
Monitored processes
17
Malicious processes
0
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1052 | C:\WINDOWS\SysWOW64\DllHost.exe /Processid:{06622D85-6856-4460-8DE1-A81921B41C4B} | C:\Windows\SysWOW64\dllhost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: COM Surrogate Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1272 | "C:\Users\admin\Desktop\HFS-2.X通杀自动搜索版本.exe" | C:\Users\admin\Desktop\HFS-2.X通杀自动搜索版本.exe | — | HFS-2.X通杀自动搜索版本.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 1300 | "C:\WINDOWS\System32\rundll32.exe" C:\WINDOWS\System32\shell32.dll,Control_RunDLL C:\WINDOWS\System32\intl.cpl | C:\Windows\System32\rundll32.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1852 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | HFS-2.X通杀自动搜索版本.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2344 | C:\WINDOWS\system32\DllHost.exe /Processid:{514B5E31-5596-422F-BE58-D804464683B5} | C:\Windows\System32\dllhost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: COM Surrogate Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4024 | C:\Windows\System32\InputMethod\CHS\ChsIME.exe -Embedding | C:\Windows\System32\InputMethod\CHS\ChsIME.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft IME Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4152 | "C:\Program Files\RUXIM\PLUGscheduler.exe" | C:\Program Files\RUXIM\PLUGScheduler.exe | — | svchost.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Update LifeCycle Component Scheduler Exit code: 0 Version: 10.0.19041.3623 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4920 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | — | SppExtComObj.Exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5332 | C:\WINDOWS\explorer.exe /factory,{5BD95610-9434-43C2-886C-57852CC8A120} -Embedding | C:\Windows\explorer.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 0 Version: 10.0.19041.3758 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5972 | "C:\Users\admin\Desktop\HFS-2.X通杀自动搜索版本.exe" | C:\Users\admin\Desktop\HFS-2.X通杀自动搜索版本.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
Total events
12 219
Read events
10 992
Write events
1 124
Delete events
103
Modification events
| (PID) Process: | (5332) explorer.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | NodeSlots |
Value: 02020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202 | |||
| (PID) Process: | (5332) explorer.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | MRUListEx |
Value: 0000000004000000030000000E000000100000000F0000000C0000000D0000000B000000050000000A000000090000000800000001000000070000000600000002000000FFFFFFFF | |||
| (PID) Process: | (5332) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\Toolbar |
| Operation: | write | Name: | Locked |
Value: 1 | |||
| (PID) Process: | (2344) dllhost.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\FontLink |
| Operation: | write | Name: | FontLinkControl |
Value: 0 | |||
| (PID) Process: | (2344) dllhost.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\FontLink |
| Operation: | write | Name: | FontLinkDefaultChar |
Value: 12539 | |||
| (PID) Process: | (2344) dllhost.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\FontLink\SystemLink |
| Operation: | delete value | Name: | Lucida Sans Unicode |
Value: MSGOTHIC.TTC,MS UI Gothic | |||
| (PID) Process: | (2344) dllhost.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\FontLink\SystemLink |
| Operation: | write | Name: | Lucida Sans Unicode |
Value: MSGOTHIC.TTC,MS UI Gothic | |||
| (PID) Process: | (2344) dllhost.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\FontLink\SystemLink |
| Operation: | delete value | Name: | Microsoft Sans Serif |
Value: MSGOTHIC.TTC,MS UI Gothic | |||
| (PID) Process: | (2344) dllhost.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\FontLink\SystemLink |
| Operation: | write | Name: | Microsoft Sans Serif |
Value: MSGOTHIC.TTC,MS UI Gothic | |||
| (PID) Process: | (2344) dllhost.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\FontLink\SystemLink |
| Operation: | delete value | Name: | Tahoma |
Value: MSGOTHIC.TTC,MS UI Gothic | |||
Executable files
36
Suspicious files
47
Text files
3
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6964 | HFS-2.X通杀自动搜索版本.exe | C:\Users\admin\AppData\Local\Temp\_MEI69642\_ssl.pyd | executable | |
MD5:84DEA8D0ACCE4A707B094A3627B62EAB | SHA256:DCF6B3FF84B55C3859D0F176C4CE6904C0D7D4643A657B817C6322933DBF82F6 | |||
| 6964 | HFS-2.X通杀自动搜索版本.exe | C:\Users\admin\AppData\Local\Temp\_MEI69642\libcrypto-1_1.dll | executable | |
MD5:CC4CBF715966CDCAD95A1E6C95592B3D | SHA256:594303E2CE6A4A02439054C84592791BF4AB0B7C12E9BBDB4B040E27251521F1 | |||
| 6964 | HFS-2.X通杀自动搜索版本.exe | C:\Users\admin\AppData\Local\Temp\_MEI69642\certifi\cacert.pem | text | |
MD5:EA4EE2AF66C4C57B8A275867E9DC07CD | SHA256:FA883829EBB8CD2A602F9B21C1F85DE24CF47949D520BCEB1828B4CD1CB6906C | |||
| 4152 | PLUGScheduler.exe | C:\ProgramData\PLUG\Logs\RUXIMLog.050.etl | binary | |
MD5:C8834D365FAE073DEDE1F1620454CE71 | SHA256:C6DD793EEE1D5551CA507A3C5BFFECA82DD3E29C63C2C6DD218A7D4BFB37046B | |||
| 6964 | HFS-2.X通杀自动搜索版本.exe | C:\Users\admin\AppData\Local\Temp\_MEI69642\libssl-1_1.dll | executable | |
MD5:BC778F33480148EFA5D62B2EC85AAA7D | SHA256:9D4CF1C03629F92662FC8D7E3F1094A7FC93CB41634994464B853DF8036AF843 | |||
| 6964 | HFS-2.X通杀自动搜索版本.exe | C:\Users\admin\AppData\Local\Temp\_MEI69642\unicodedata.pyd | executable | |
MD5:549C9EEDA8546CD32D0713C723ABD12A | SHA256:5D5E733397EF7C4946CF26C84B07312CB12EAF339374613D4381E694EF38169B | |||
| 6964 | HFS-2.X通杀自动搜索版本.exe | C:\Users\admin\AppData\Local\Temp\_MEI69642\select.pyd | executable | |
MD5:A2AB334E18222738DCB05BF820725938 | SHA256:7BA95624370216795EA4A087C326422CFCBCCC42B5ADA21F4D85C532C71AFAD7 | |||
| 4152 | PLUGScheduler.exe | C:\ProgramData\PLUG\Logs\RUXIMLog.046.etl | binary | |
MD5:A7A21FBC9D00F33F186B34A50E170C13 | SHA256:64CAC91E46D4FC832958232A658431CBF9D8D9F265653ACA2BEB32428D4688EC | |||
| 4152 | PLUGScheduler.exe | C:\ProgramData\PLUG\Logs\RUXIMLog.049.etl | binary | |
MD5:5EA68411BF8E9EAF4621BAF73F61449E | SHA256:9D4CA5A1D871F819C139A498BB910A63576C2FE6367853544F8D172D8B6EBFF7 | |||
| 6964 | HFS-2.X通杀自动搜索版本.exe | C:\Users\admin\AppData\Local\Temp\_MEI69642\base_library.zip | compressed | |
MD5:BCC06D24C2C806A06E861D9020E65B30 | SHA256:A0FCCBE44E5B9D3AABD6E955C2ECB5FF52492C469EBED61EA3CAD5EC5642AA5D | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
12
TCP/UDP connections
77
DNS requests
32
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 2.18.121.147:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.18.121.147:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
2924 | SearchApp.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
1628 | backgroundTaskHost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
1452 | backgroundTaskHost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
5964 | BackgroundTransferHost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
5984 | SIHClient.exe | GET | 200 | 23.52.120.96:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 2.18.121.147:80 | crl.microsoft.com | AKAMAI-AS | FR | whitelisted |
— | — | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
3216 | svchost.exe | 172.211.123.250:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 40.126.31.130:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6544 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
2104 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2924 | SearchApp.exe | 104.126.37.144:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
www.bing.com |
| whitelisted |
fp.msedge.net |
| whitelisted |
th.bing.com |
| whitelisted |