| File name: | (jumpstart).exe |
| Full analysis: | https://app.any.run/tasks/1ac95308-769f-47b2-af42-8c1bfed89f1d |
| Verdict: | Malicious activity |
| Analysis date: | February 16, 2024, 18:43:30 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, RAR self-extracting archive |
| MD5: | 467F3354F86757A0EEE774D0C978DF9B |
| SHA1: | D06FED3616ED78ADD3909AF5F5C0FFDF4B5AB041 |
| SHA256: | B6C76C3AC73B73D59A033ABEEFD338EA537644AB349A9F4BBF56DD0DE50FD312 |
| SSDEEP: | 98304:C+paRFN/3ci0NbvduzwxdzyX9QIFlgV2z02+U5YBIW5Jh8s1RXoQ73aOJ0U6CnyI:scf |
MALICIOUS
Drops the executable file immediately after the start
- (jumpstart).exe (PID: 3672)
- Jumpstar.exe (PID: 3652)
- Jumpstar.exe (PID: 2848)
- (jumpstart).exe (PID: 796)
SUSPICIOUS
Executable content was dropped or overwritten
- (jumpstart).exe (PID: 3672)
- Jumpstar.exe (PID: 3652)
- Jumpstar.exe (PID: 2848)
- (jumpstart).exe (PID: 796)
Starts itself from another location
- (jumpstart).exe (PID: 3672)
- (jumpstart).exe (PID: 796)
Reads security settings of Internet Explorer
- (jumpstart).exe (PID: 3672)
- (jumpstart).exe (PID: 796)
Reads the Internet Settings
- (jumpstart).exe (PID: 3672)
- HelpPane.exe (PID: 3960)
- (jumpstart).exe (PID: 796)
Drops a system driver (possible attempt to evade defenses)
- Jumpstar.exe (PID: 3652)
Reads Microsoft Outlook installation path
- HelpPane.exe (PID: 3960)
Reads Internet Explorer settings
- HelpPane.exe (PID: 3960)
INFO
Checks supported languages
- (jumpstart).exe (PID: 3672)
- Jumpstar.exe (PID: 3652)
- Jumpstar.exe (PID: 2848)
- jswtrayutil.exe (PID: 1040)
- jswscapp.exe (PID: 864)
- jswpbapi.exe (PID: 4008)
- Jumpstar.exe (PID: 2960)
- (jumpstart).exe (PID: 796)
- jswpsapi.exe (PID: 1692)
- Jumpstar.exe (PID: 3684)
Reads the computer name
- (jumpstart).exe (PID: 3672)
- Jumpstar.exe (PID: 3652)
- Jumpstar.exe (PID: 2848)
- jswscapp.exe (PID: 864)
- Jumpstar.exe (PID: 2960)
- Jumpstar.exe (PID: 3684)
- (jumpstart).exe (PID: 796)
Manual execution by a user
- Jumpstar.exe (PID: 2848)
- jswtrayutil.exe (PID: 1040)
- jswscapp.exe (PID: 864)
- jswpsapi.exe (PID: 1692)
- jswpbapi.exe (PID: 4008)
- winhlp32.exe (PID: 2856)
- (jumpstart).exe (PID: 796)
- Jumpstar.exe (PID: 2960)
Reads the machine GUID from the registry
- jswscapp.exe (PID: 864)
- HelpPane.exe (PID: 3960)
- winhlp32.exe (PID: 2856)
Reads security settings of Internet Explorer
- HelpPane.exe (PID: 3960)
Checks proxy server information
- HelpPane.exe (PID: 3960)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (42.2) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (37.3) |
| .dll | | | Win32 Dynamic Link Library (generic) (8.8) |
| .exe | | | Win32 Executable (generic) (6) |
| .exe | | | Generic Win/DOS Executable (2.7) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2010:02:10 13:09:37+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 9 |
| CodeSize: | 67584 |
| InitializedDataSize: | 72704 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xa785 |
| OSVersion: | 5 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
Total processes
51
Monitored processes
13
Malicious processes
4
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 796 | "C:\Users\admin\Desktop\(jumpstart).exe" | C:\Users\admin\Desktop\(jumpstart).exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 864 | "C:\Users\admin\Desktop\jswscapp.exe" | C:\Users\admin\Desktop\jswscapp.exe | — | explorer.exe | |||||||||||
User: admin Company: Atheros Communications, Inc. Integrity Level: MEDIUM Description: Jumpstart for Wireless Exit code: 0 Version: 2.1.0.18 Modules
| |||||||||||||||
| 1040 | "C:\Users\admin\Desktop\jswtrayutil.exe" | C:\Users\admin\Desktop\jswtrayutil.exe | — | explorer.exe | |||||||||||
User: admin Company: Atheros Communications, Inc. Integrity Level: MEDIUM Description: Tray Utility for JumpStart for Wireless Exit code: 0 Version: 2.1.0.18 Modules
| |||||||||||||||
| 1576 | C:\Windows\system32\DllHost.exe /Processid:{76D0CB12-7604-4048-B83C-1005C7DDC503} | C:\Windows\System32\dllhost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: COM Surrogate Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
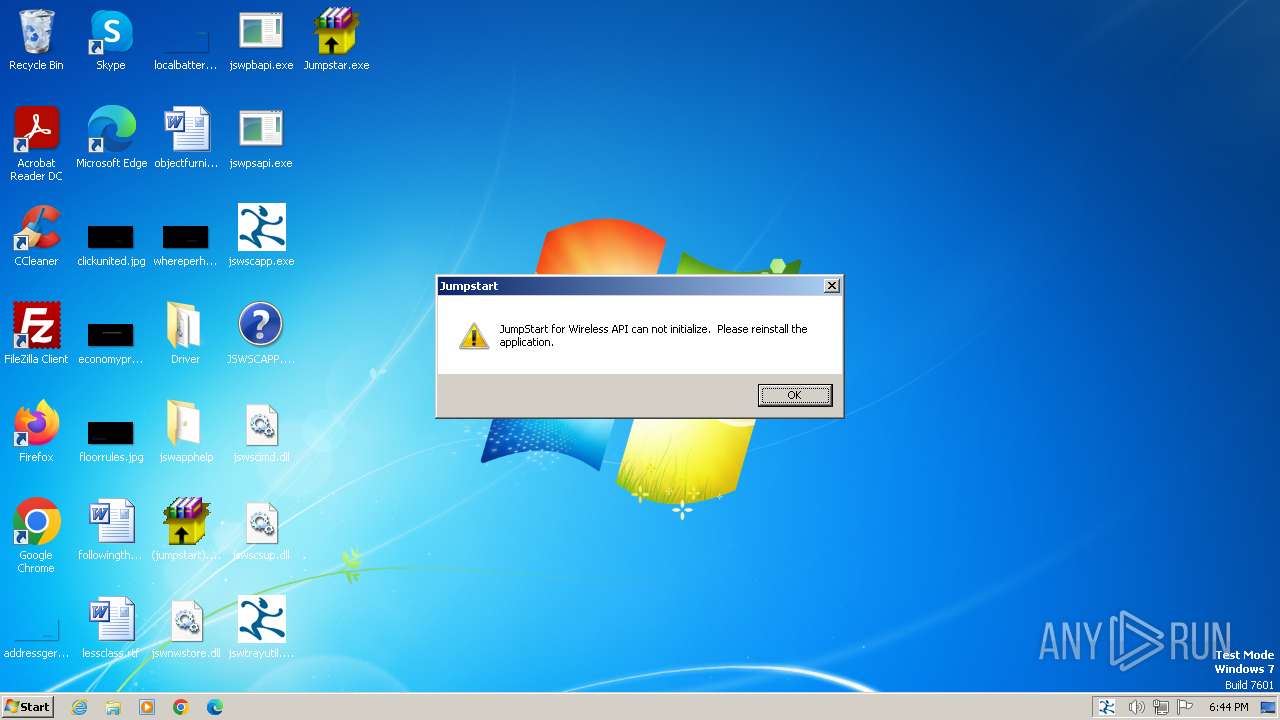
| 1692 | "C:\Users\admin\Desktop\jswpsapi.exe" | C:\Users\admin\Desktop\jswpsapi.exe | — | explorer.exe | |||||||||||
User: admin Company: Atheros Communications, Inc. Integrity Level: MEDIUM Description: Jumpstart for Wireless API Exit code: 2 Version: 2.1.0.18 Modules
| |||||||||||||||
| 2848 | "C:\Users\admin\Desktop\Jumpstar.exe" | C:\Users\admin\Desktop\Jumpstar.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2856 | "C:\Windows\winhlp32.exe" C:\Users\admin\Desktop\JSWSCAPP.HLP | C:\Windows\winhlp32.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Winhlp32 Stub Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2960 | "C:\Users\admin\Desktop\Jumpstar.exe" | C:\Users\admin\Desktop\Jumpstar.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 1 Modules
| |||||||||||||||
| 3652 | "C:\Users\admin\Desktop\Jumpstar.exe" | C:\Users\admin\Desktop\Jumpstar.exe | (jumpstart).exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 3672 | "C:\Users\admin\Desktop\(jumpstart).exe" | C:\Users\admin\Desktop\(jumpstart).exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
Total events
2 788
Read events
2 747
Write events
39
Delete events
2
Modification events
| (PID) Process: | (3672) (jumpstart).exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (3672) (jumpstart).exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (3672) (jumpstart).exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (3672) (jumpstart).exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (864) jswscapp.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Multimedia\DrawDib |
| Operation: | write | Name: | vga.drv 1280x720x32(BGR 0) |
Value: 31,31,31,31 | |||
| (PID) Process: | (3960) HelpPane.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Assistance\Client\1.0\Settings |
| Operation: | write | Name: | OnlineAssist |
Value: 0 | |||
| (PID) Process: | (3960) HelpPane.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Assistance\Client\1.0\Settings |
| Operation: | write | Name: | ImplicitFeedback |
Value: 0 | |||
| (PID) Process: | (3960) HelpPane.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Assistance\Client\1.0\Settings |
| Operation: | write | Name: | FirstTimeHelppaneStartup |
Value: 0 | |||
| (PID) Process: | (3960) HelpPane.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Assistance\Client\1.0\Settings |
| Operation: | write | Name: | IsConnected |
Value: 0 | |||
| (PID) Process: | (3960) HelpPane.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
17
Suspicious files
5
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3672 | (jumpstart).exe | C:\Users\admin\Desktop\Jumpstar.exe | executable | |
MD5:98ABD9B7C9E8F4C3773DF7C85BE47BED | SHA256:F1893EE7F051B307D6E7634030F0D032C46AA82ACAEAB8A334F553B91C008D45 | |||
| 3652 | Jumpstar.exe | C:\Users\admin\Desktop\jswtrayutil.exe | executable | |
MD5:F6F03907366C9589756B1DB56E0F2B31 | SHA256:149942B86097DBBDC01419B20D263E534D632030480561DE1B948124B3EF67A6 | |||
| 3672 | (jumpstart).exe | C:\Users\admin\Desktop\jumpstart .exe | executable | |
MD5:F807F0F92F391CB17ECE07176869D5BA | SHA256:03C231D31243996BC888E98290FFE1C2BB6C18BBF40F15F243F2C811DDE76765 | |||
| 3652 | Jumpstar.exe | C:\Users\admin\Desktop\jswpbapi.exe | executable | |
MD5:670D6F56BA218AE78CD526AFCC530E2A | SHA256:85A676492687F8BCE42F82FF50852658698F1987A0BAFB71034D0755C1C80526 | |||
| 3652 | Jumpstar.exe | C:\Users\admin\Desktop\jswpsapi.exe | executable | |
MD5:CD9F4E53DA79ED4CD7562604FE9523A6 | SHA256:94C6C89CD73F6D052EB498EB00BFC826D8E521C2138D8840BB7667234A658401 | |||
| 3652 | Jumpstar.exe | C:\Users\admin\Desktop\jswscsup.dll | executable | |
MD5:90B4EFE34262CF33F1212F42AB50F5C8 | SHA256:1496486ED2701A546D91BB8819069D4A0CBC6A51D41C58DC44A073133AC86600 | |||
| 3652 | Jumpstar.exe | C:\Users\admin\Desktop\jswnwstore.dll | executable | |
MD5:4E274D073033A3EF0710918BF5411B21 | SHA256:80315B6D55E086A2ED0D21326F94B6E0A285FE3D9F9EF336D8E1D1917EB5E183 | |||
| 3652 | Jumpstar.exe | C:\Users\admin\Desktop\Driver\jswpslwf.inf | binary | |
MD5:7886830F25B31D10917195EB1F6F6613 | SHA256:459E2DA1FADF34FED1E8E48BB5140CA4AA382D83012F893EDE57A2062D63D57A | |||
| 3652 | Jumpstar.exe | C:\Users\admin\Desktop\jswscapp.exe | executable | |
MD5:6AAD3F9C4636D4E43902EA7593B5A117 | SHA256:6C1999E8D32B0DBB5A61E0AB0BF8A1DB36F49339319A9C7BFE7CF58679F38894 | |||
| 3652 | Jumpstar.exe | C:\Users\admin\Desktop\jswscimd.dll | executable | |
MD5:3F4D6FDD38F96A0353D8961B4576627A | SHA256:61E8E262A78DA2C8933F16323F772C1C97E3E10691409672F568F1D6EC902E7B | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
4
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |