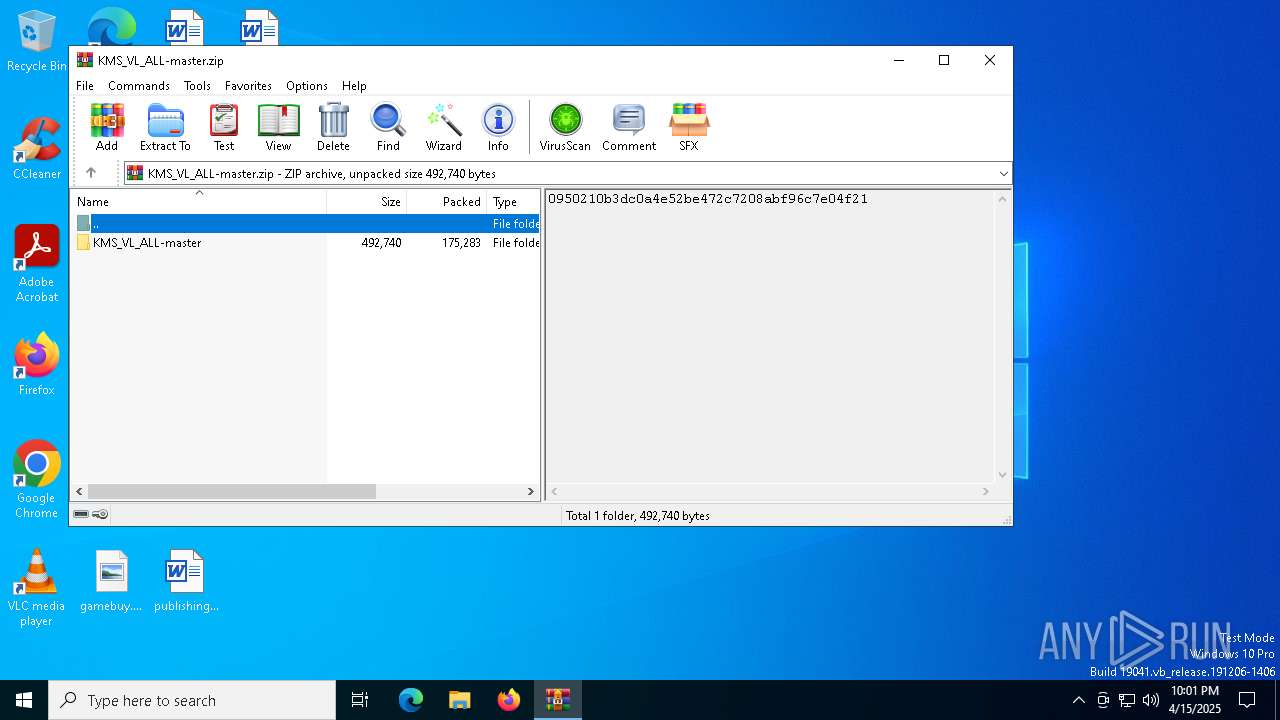
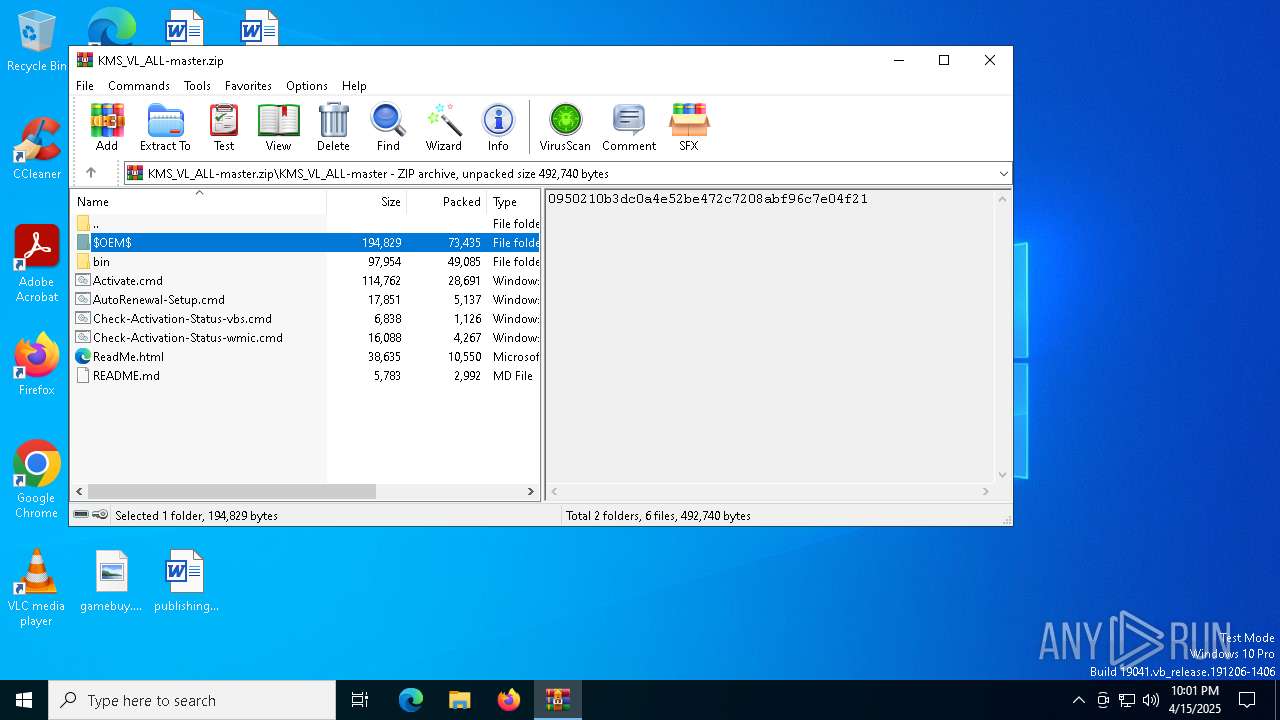
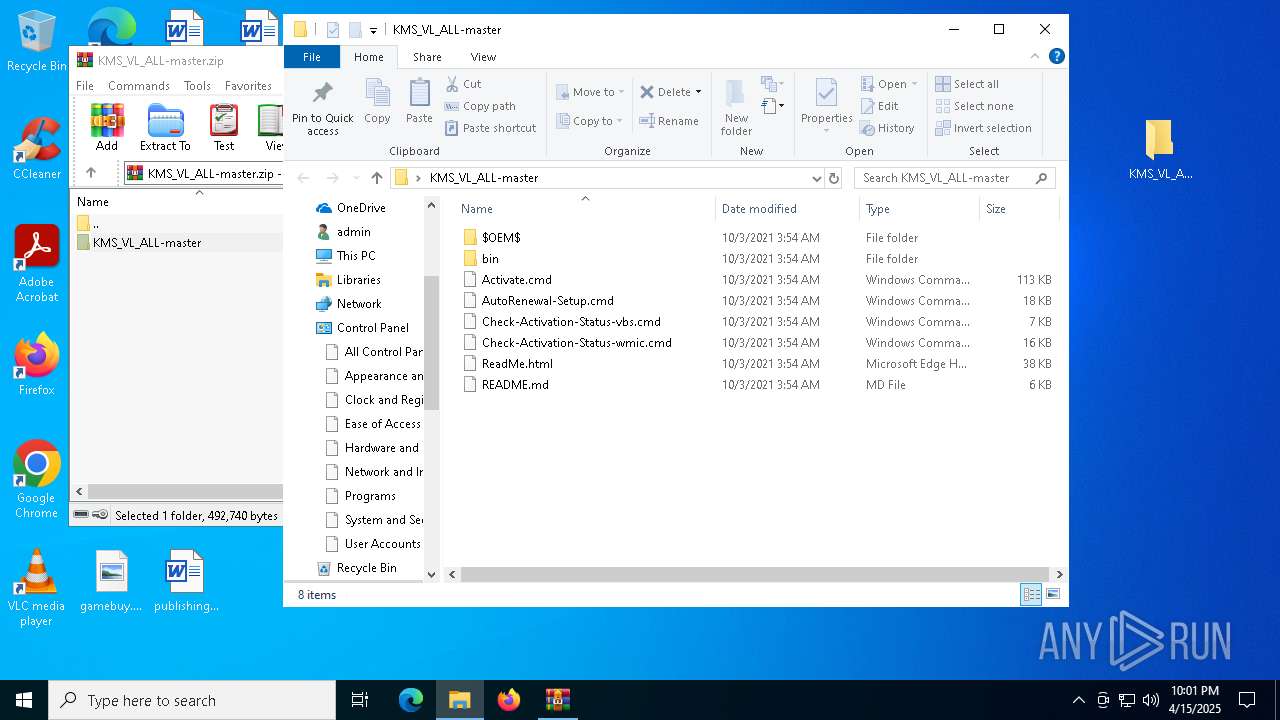
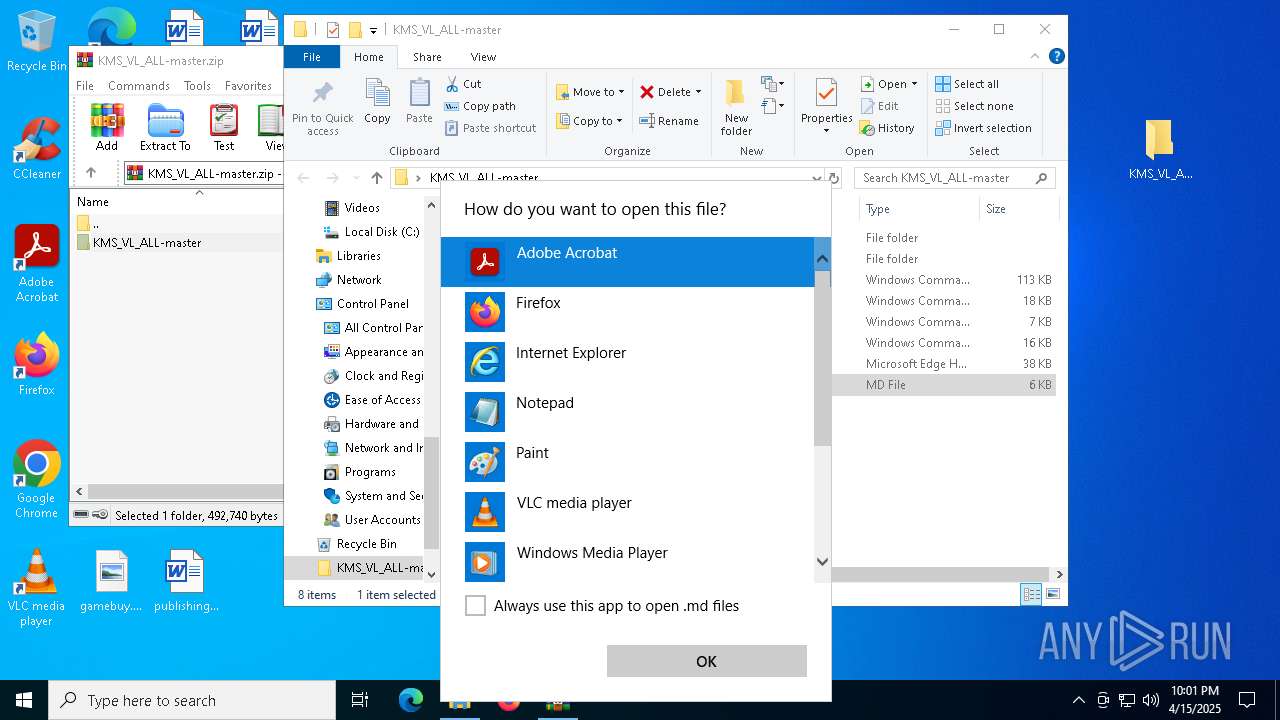
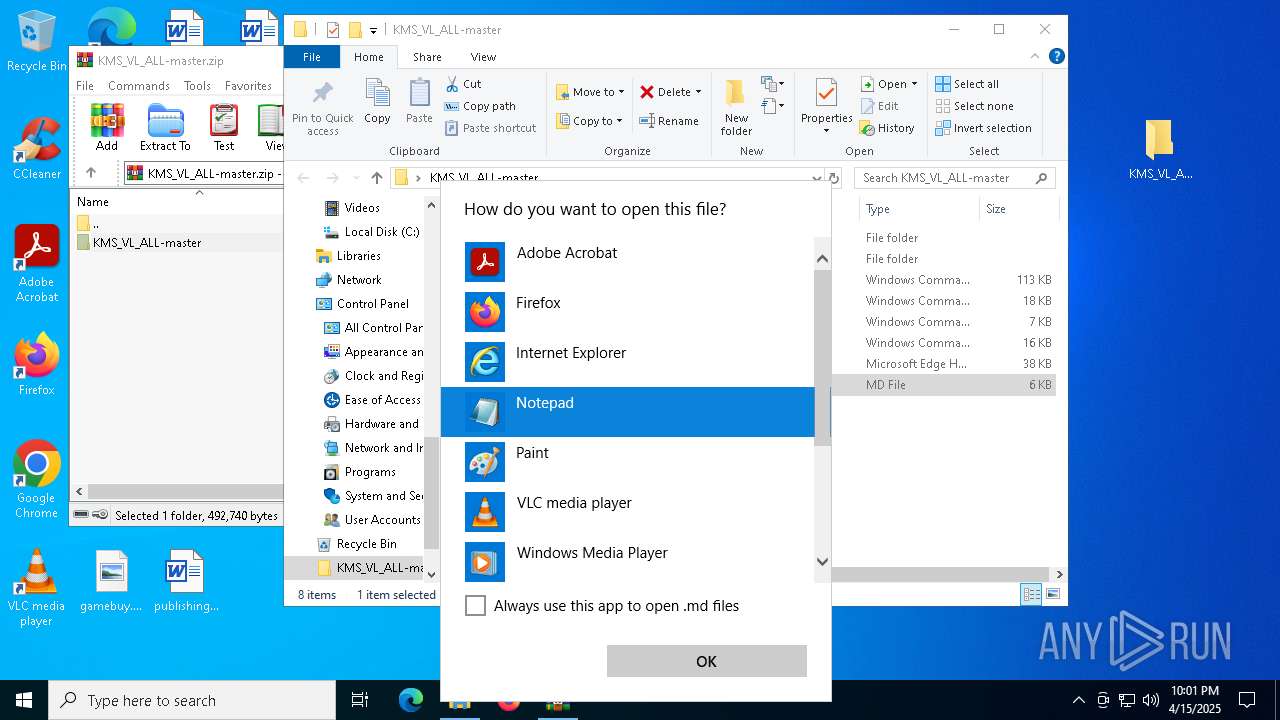
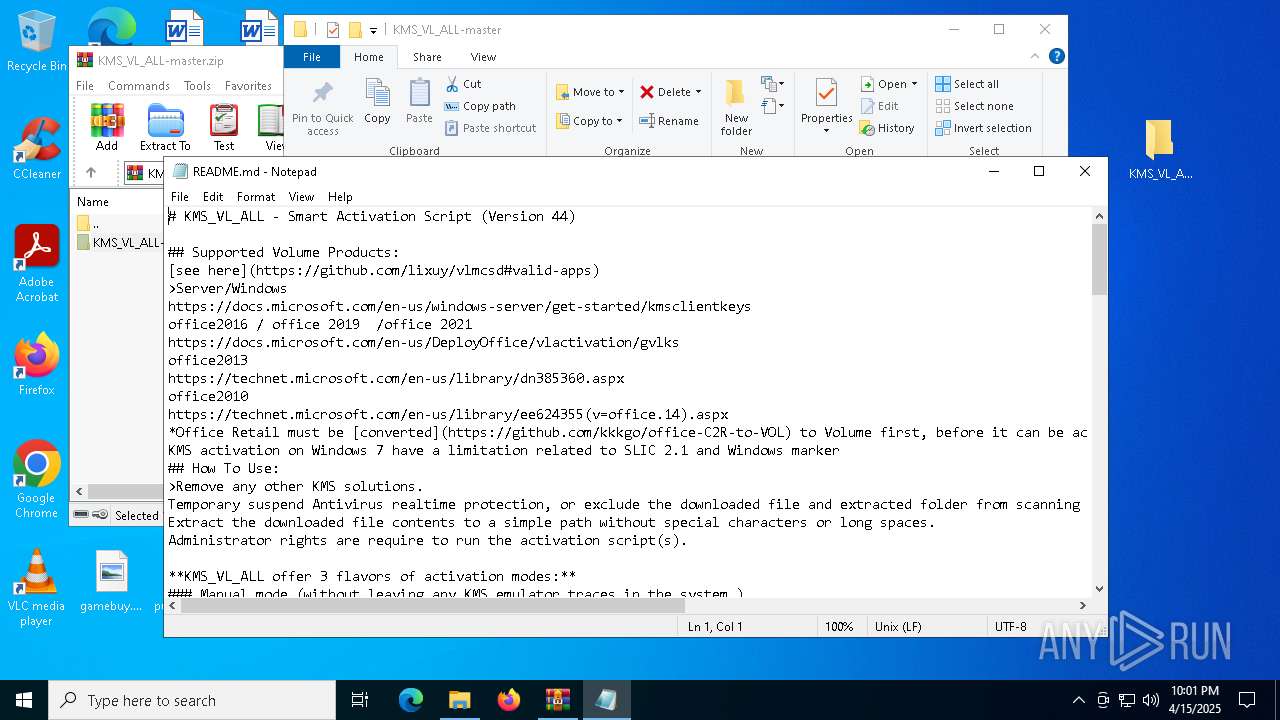
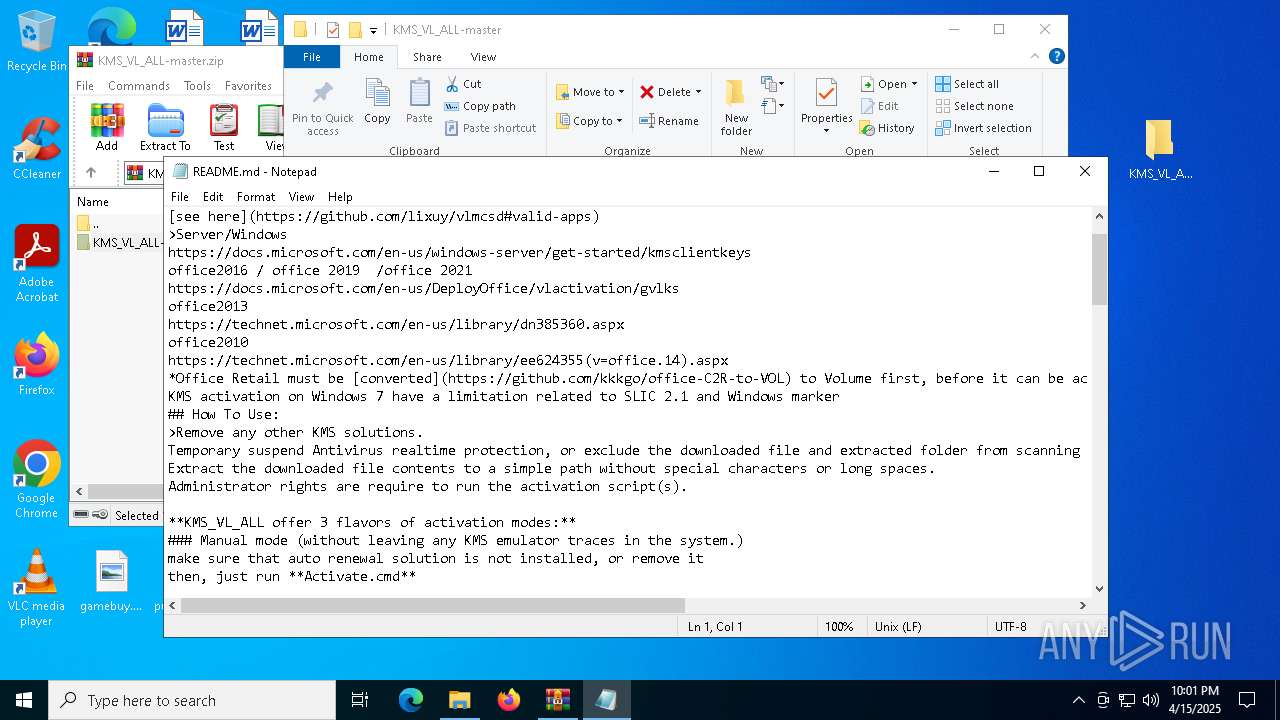
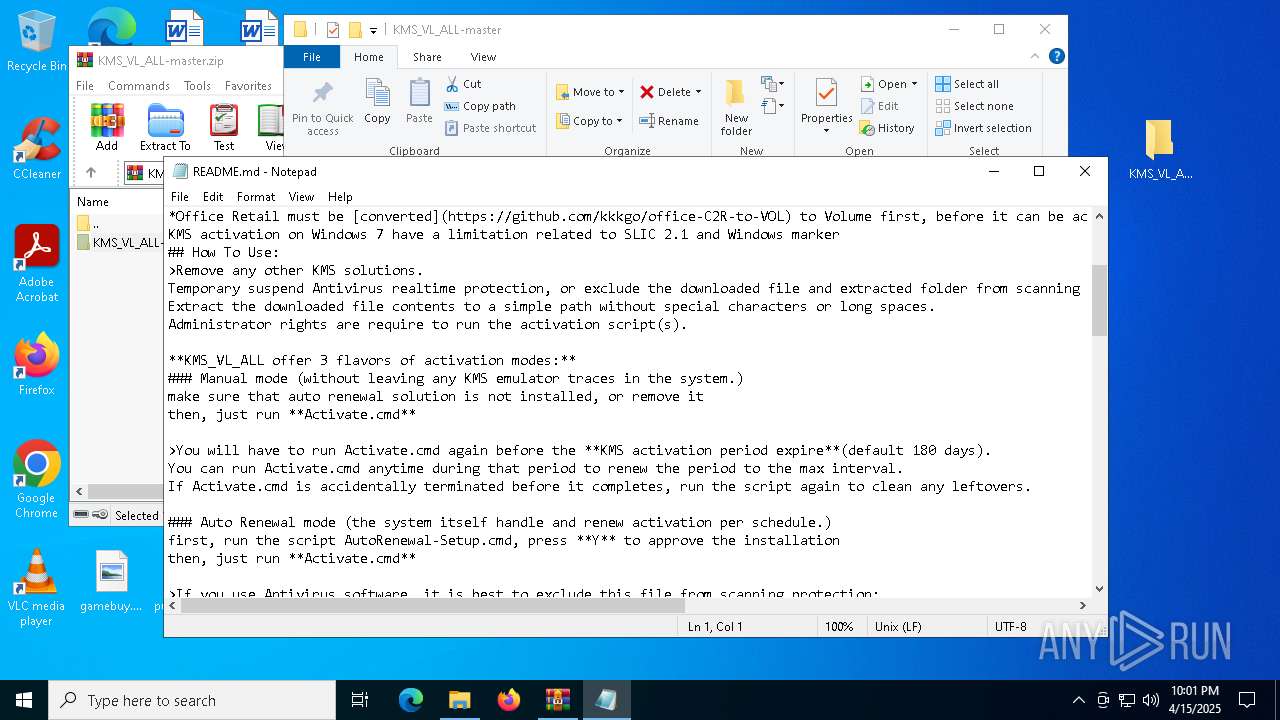
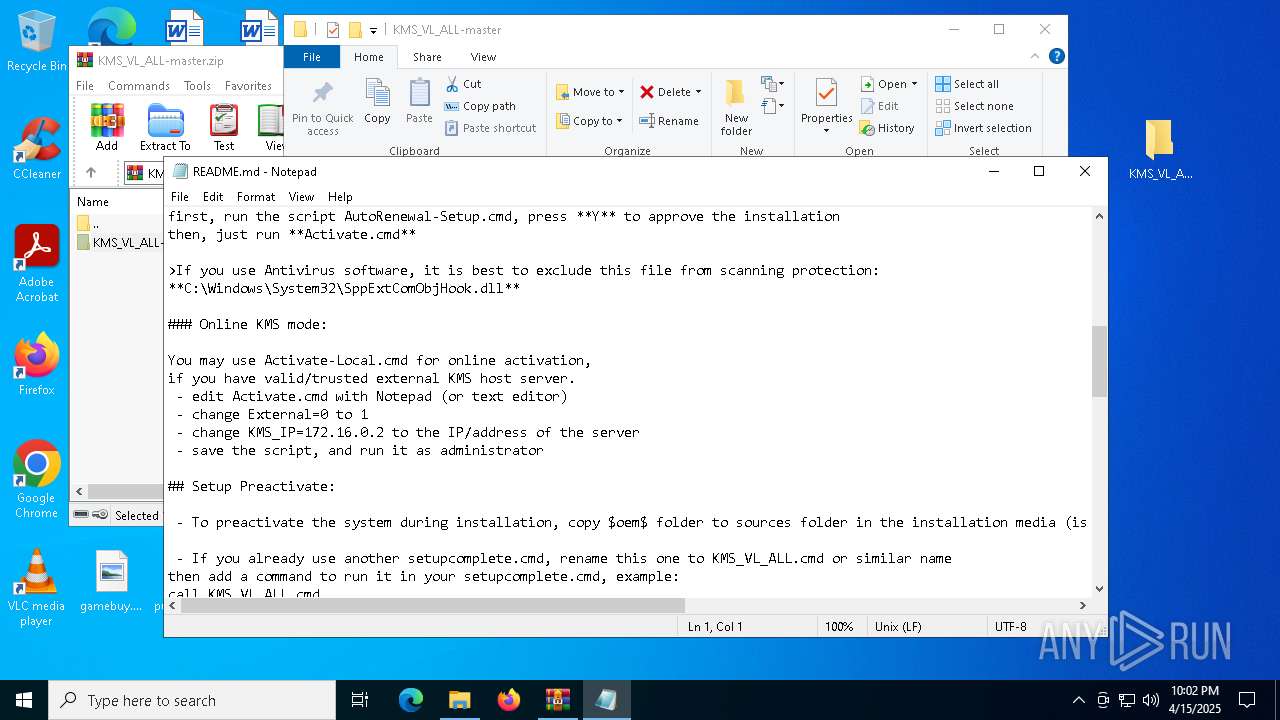
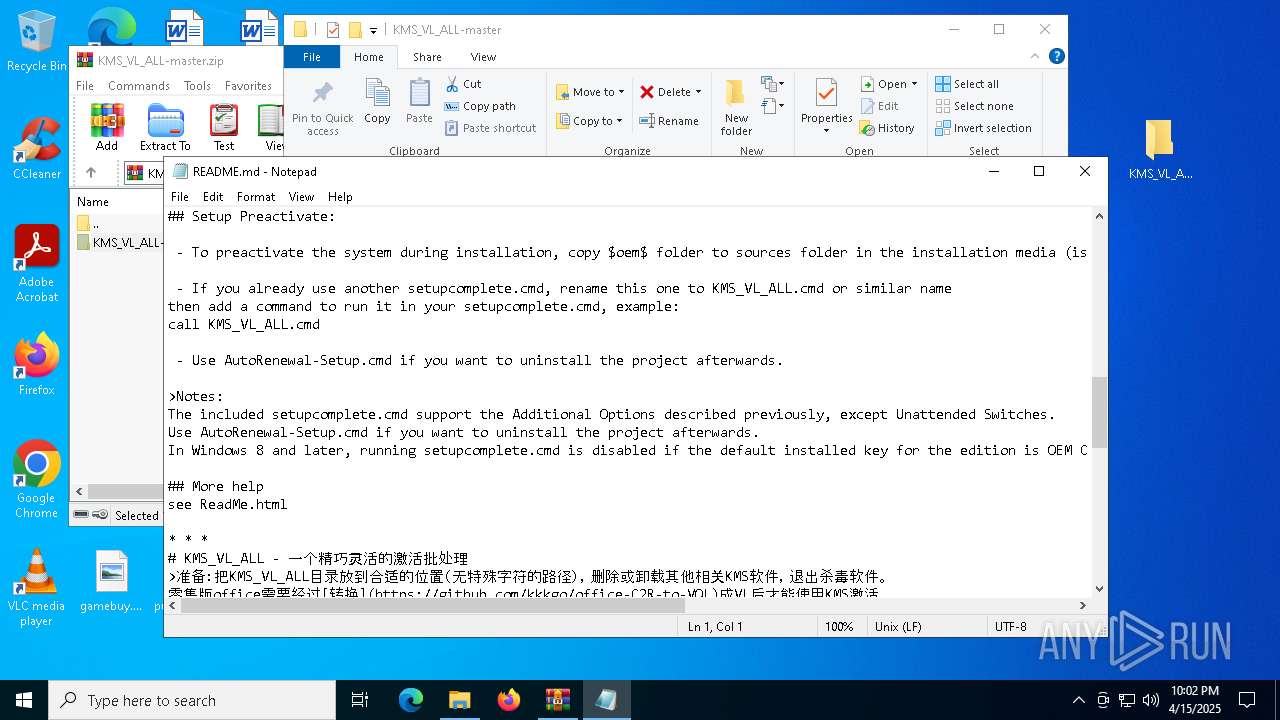
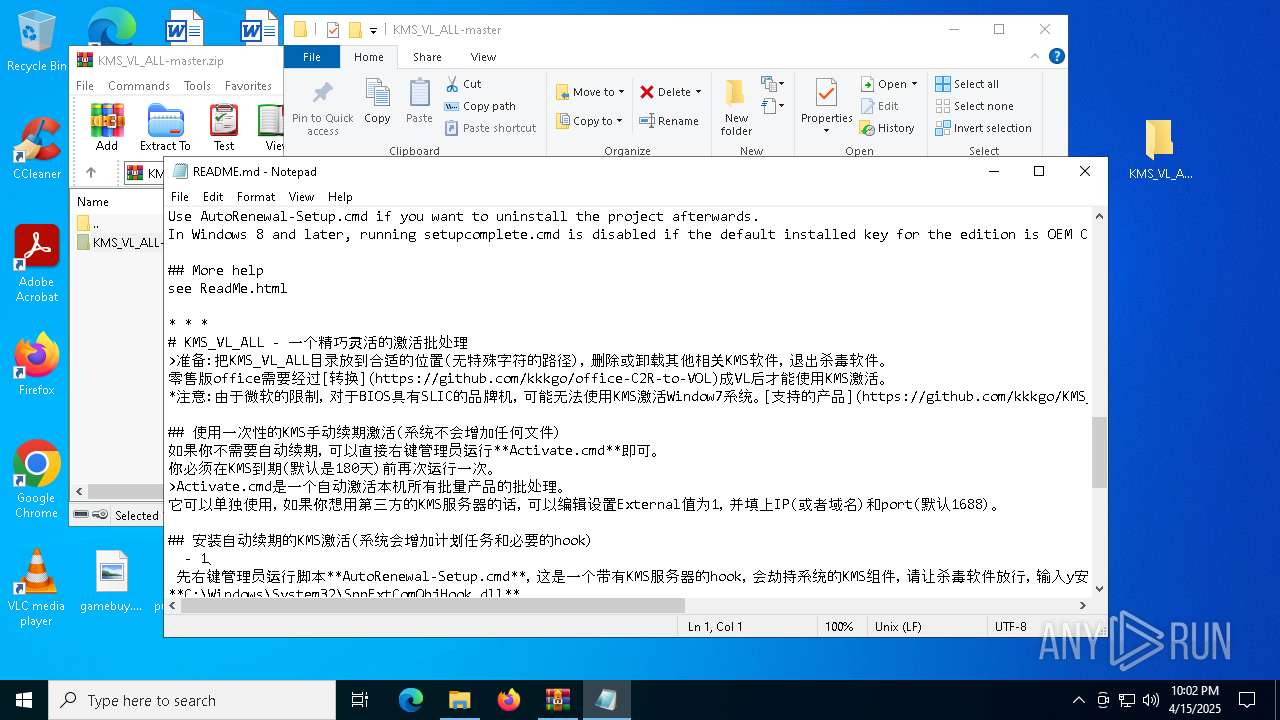
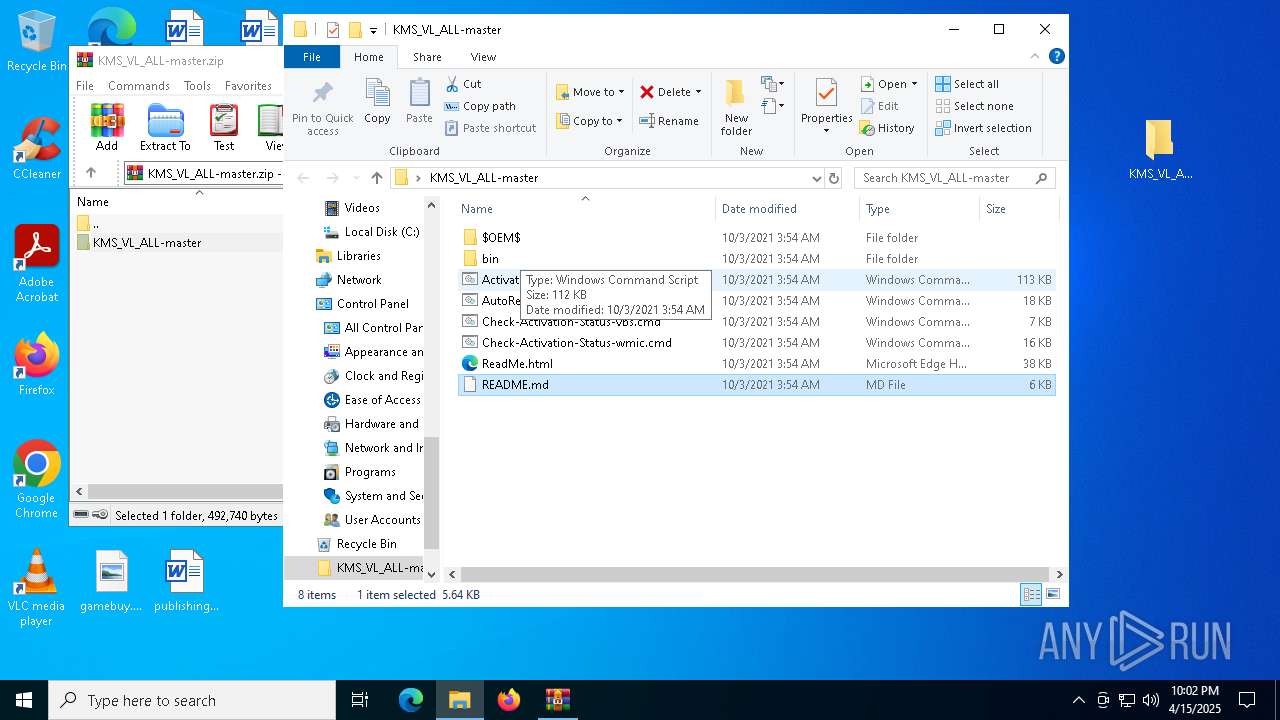
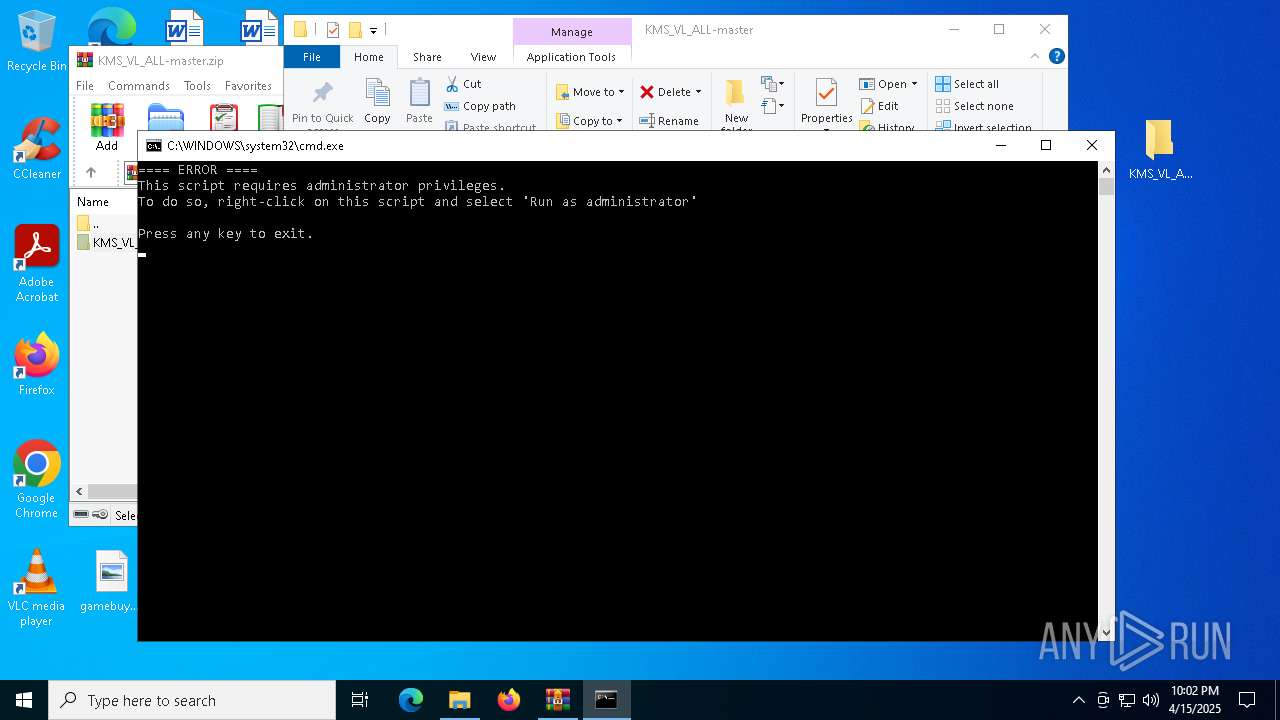
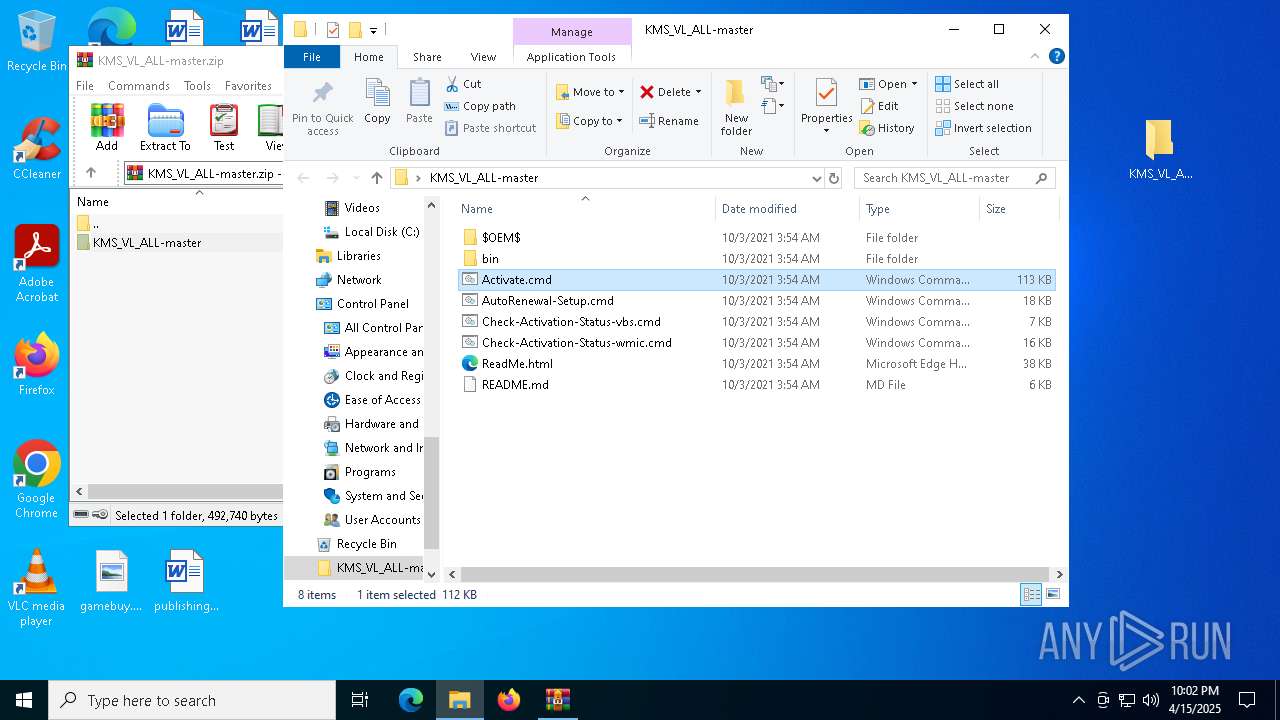
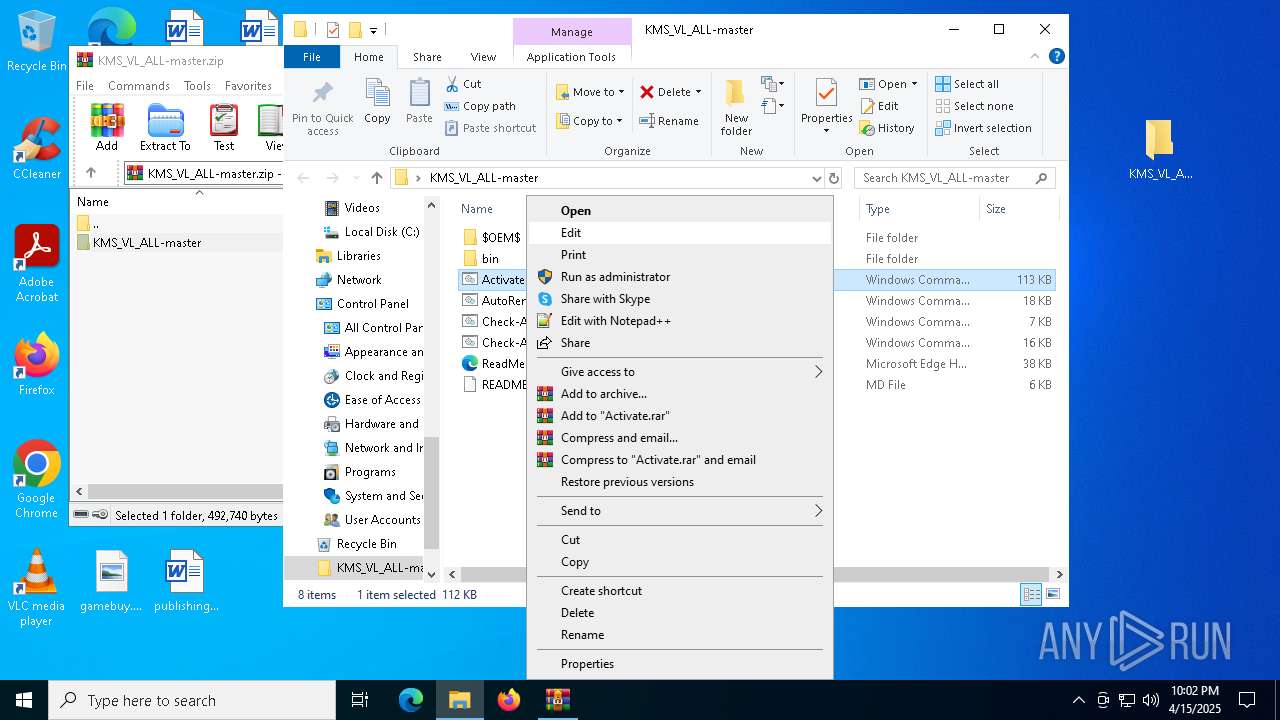
| File name: | KMS_VL_ALL-master.zip |
| Full analysis: | https://app.any.run/tasks/aac2f789-ea0a-4c56-ab3f-941505510af0 |
| Verdict: | Malicious activity |
| Analysis date: | April 15, 2025, 22:01:16 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v1.0 to extract, compression method=store |
| MD5: | 8A848B909D3C248599A1C7FF87E218F9 |
| SHA1: | 25AB3CFEE6EDE8B191773E23C50B63098EEDD0AC |
| SHA256: | B6C178C80442479E58C38E3D987EFE6BFD2BE5B3C8C05AA3C3E91106A57F6066 |
| SSDEEP: | 6144:R2DIukdJtk8oEfFaHxMzNMbCyK0t2D7x/5:4DWdd3fFaHxMz2br5kDV5 |
MALICIOUS
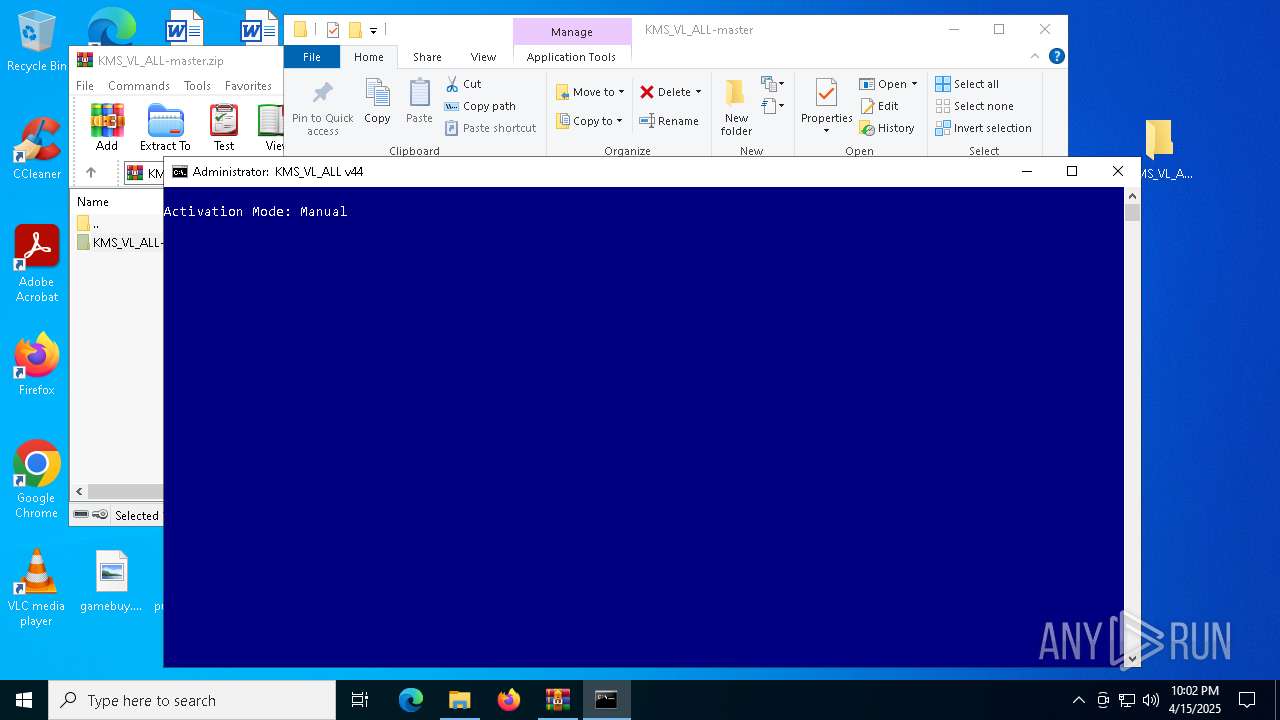
Starts NET.EXE for service management
- net.exe (PID: 728)
- cmd.exe (PID: 1764)
- net.exe (PID: 736)
SUSPICIOUS
Starts CMD.EXE for commands execution
- cmd.exe (PID: 8160)
- cmd.exe (PID: 1764)
Windows service management via SC.EXE
- sc.exe (PID: 7228)
- sc.exe (PID: 5968)
- sc.exe (PID: 6184)
- sc.exe (PID: 6148)
- sc.exe (PID: 1272)
Application launched itself
- cmd.exe (PID: 8160)
- cmd.exe (PID: 1764)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 8160)
- cmd.exe (PID: 1764)
Starts SC.EXE for service management
- cmd.exe (PID: 1764)
Hides command output
- cmd.exe (PID: 7780)
- cmd.exe (PID: 7892)
- cmd.exe (PID: 7576)
- cmd.exe (PID: 7916)
- cmd.exe (PID: 8028)
- cmd.exe (PID: 8144)
- cmd.exe (PID: 7888)
- cmd.exe (PID: 7676)
- cmd.exe (PID: 7984)
- cmd.exe (PID: 7912)
- cmd.exe (PID: 5136)
- cmd.exe (PID: 7888)
- cmd.exe (PID: 7852)
- cmd.exe (PID: 8080)
- cmd.exe (PID: 7924)
- cmd.exe (PID: 4164)
- cmd.exe (PID: 8028)
- cmd.exe (PID: 924)
- cmd.exe (PID: 8124)
- cmd.exe (PID: 3332)
- cmd.exe (PID: 8104)
Uses ICACLS.EXE to modify access control lists
- cmd.exe (PID: 1764)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 1764)
Uses WMIC.EXE to obtain service application data
- cmd.exe (PID: 8124)
Uses WMIC.EXE to obtain Windows Installer data
- cmd.exe (PID: 1764)
- cmd.exe (PID: 3332)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 1348)
Reads security settings of Internet Explorer
- OpenWith.exe (PID: 8004)
- notepad.exe (PID: 8112)
- WMIC.exe (PID: 812)
- WMIC.exe (PID: 7608)
- WMIC.exe (PID: 6576)
- WMIC.exe (PID: 8184)
- WMIC.exe (PID: 5988)
- WMIC.exe (PID: 5176)
- WMIC.exe (PID: 4892)
Manual execution by a user
- cmd.exe (PID: 1764)
- cmd.exe (PID: 8160)
Reads Microsoft Office registry keys
- OpenWith.exe (PID: 8004)
- reg.exe (PID: 5600)
- reg.exe (PID: 4944)
- reg.exe (PID: 4220)
- reg.exe (PID: 7896)
- reg.exe (PID: 2192)
Checks operating system version
- cmd.exe (PID: 1764)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 10 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2021:10:02 20:54:26 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | KMS_VL_ALL-master/ |
Total processes
363
Monitored processes
233
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 456 | findstr /I /C:"O365EduCloudRetail" "C:\WINDOWS\Temp\c2rchk.txt" | C:\Windows\System32\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Find String (QGREP) Utility Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 632 | REG QUERY "HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Component Based Servicing\Packages" /f "Microsoft-Windows-*Edition~31bf3856ad364e35" /k | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 632 | findstr /I /C:"HomeBusiness2019Retail" "C:\WINDOWS\Temp\crvProductIds.txt" | C:\Windows\System32\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Find String (QGREP) Utility Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 660 | findstr /I /C:"PowerPointVolume" "C:\WINDOWS\Temp\c2rchk.txt" | C:\Windows\System32\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Find String (QGREP) Utility Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 728 | net stop sppsvc /y | C:\Windows\System32\net.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Net Command Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 728 | findstr /I /C:"ProjectPro2019Retail" "C:\WINDOWS\Temp\crvProductIds.txt" | C:\Windows\System32\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Find String (QGREP) Utility Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 736 | net start sppsvc /y | C:\Windows\System32\net.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Net Command Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 812 | WMIC PATH SoftwareLicensingProduct WHERE (ApplicationID='55c92734-d682-4d71-983e-d6ec3f16059f' AND PartialProductKey is not NULL) GET LicenseFamily /VALUE | C:\Windows\System32\wbem\WMIC.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: WMI Commandline Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 896 | findstr /I /C:"HomeStudent2021Retail" "C:\WINDOWS\Temp\crvProductIds.txt" | C:\Windows\System32\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Find String (QGREP) Utility Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 924 | C:\WINDOWS\system32\cmd.exe /c "reg query HKLM\SOFTWARE\Microsoft\Office\15.0\Common\InstallRoot /v Path" 2>nul | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
6 726
Read events
6 709
Write events
17
Delete events
0
Modification events
| (PID) Process: | (1348) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (1348) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (1348) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (1348) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\KMS_VL_ALL-master.zip | |||
| (PID) Process: | (1348) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (1348) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (1348) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (1348) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (7232) reg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows NT\CurrentVersion\Software Protection Platform |
| Operation: | write | Name: | NoGenTicket |
Value: 1 | |||
| (PID) Process: | (7360) reg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\SppExtComObj.exe |
| Operation: | write | Name: | VerifierDlls |
Value: SppExtComObjHook.dll | |||
Executable files
10
Suspicious files
0
Text files
14
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1348 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1348.31089\KMS_VL_ALL-master\$OEM$\$\Setup\Scripts\bin\cleanosppx86.exe | executable | |
MD5:5FD363D52D04AC200CD24F3BCC903200 | SHA256:3FDEFE2AD092A9A7FE0EDF0AC4DC2DE7E5B9CE6A0804F6511C06564194966CF9 | |||
| 1348 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1348.31089\KMS_VL_ALL-master\$OEM$\$\Setup\Scripts\bin\cleanosppx64.exe | executable | |
MD5:162AB955CB2F002A73C1530AA796477F | SHA256:5CE462E5F34065FC878362BA58617FAB28C22D631B9D836DDDCF43FB1AD4DE6E | |||
| 1348 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1348.31089\KMS_VL_ALL-master\$OEM$\$\Setup\Scripts\bin\x64.dll | executable | |
MD5:2914300A6E0CDF7ED242505958AC0BB5 | SHA256:29AE6F149E581F8DBDC01EED2D5D20B82B597C4B4C7E102CAB6D012B168DF4D8 | |||
| 1348 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1348.31089\KMS_VL_ALL-master\Activate.cmd | text | |
MD5:27DBBEDA34FA7260A3DC9F6FD1398FDD | SHA256:79731E75607973ED0CF7FB89174785691711DCB8032527B3CC70C72D3A61118D | |||
| 1348 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1348.31089\KMS_VL_ALL-master\bin\x86.dll | executable | |
MD5:2A2BBC30D8E715C3C29E728989498469 | SHA256:81F8FC4AEF686DBC4E2B1F6B08FBAC33BF877610C268564E9ECFBAE1425D5E5C | |||
| 1348 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1348.31089\KMS_VL_ALL-master\bin\SvcTrigger.xml | xml | |
MD5:ADE0007995DA8218A924EAE18DD5FFA4 | SHA256:6C4C7816D99652A6248E8877AC24D341B3D87BB1E7A6BE159EACBB6B6BC61352 | |||
| 1348 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1348.31089\KMS_VL_ALL-master\$OEM$\$\Setup\Scripts\bin\A64.dll | executable | |
MD5:698D2D01011110B0BA4AAB62F92B9909 | SHA256:3FB8DC2FA316CA1E7244EB34E95F591AA39A6E4B6EB0416692691AEB3D0C429B | |||
| 1348 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1348.31089\KMS_VL_ALL-master\$OEM$\$\Setup\Scripts\setupcomplete.cmd | text | |
MD5:65BC53900C0B960220A5AF59B3AB9EB6 | SHA256:3B5A7C0317EA3B79988A6A554574DA43F6FFE0CCA6BC9DA16140CDD6F8A6C296 | |||
| 1348 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1348.31089\KMS_VL_ALL-master\$OEM$\$\Setup\Scripts\bin\SvcTrigger.xml | xml | |
MD5:ADE0007995DA8218A924EAE18DD5FFA4 | SHA256:6C4C7816D99652A6248E8877AC24D341B3D87BB1E7A6BE159EACBB6B6BC61352 | |||
| 1348 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1348.31089\KMS_VL_ALL-master\bin\x64.dll | executable | |
MD5:2914300A6E0CDF7ED242505958AC0BB5 | SHA256:29AE6F149E581F8DBDC01EED2D5D20B82B597C4B4C7E102CAB6D012B168DF4D8 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
18
DNS requests
12
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 2.16.168.124:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
7884 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
7884 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2104 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5496 | MoUsoCoreWorker.exe | 2.16.168.124:80 | crl.microsoft.com | Akamai International B.V. | RU | whitelisted |
2112 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3216 | svchost.exe | 172.211.123.249:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 40.126.32.133:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 2.23.77.188:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
2104 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |