| File name: | SetupVCD5520.exe |
| Full analysis: | https://app.any.run/tasks/7c67b371-5ea5-45d7-b06b-0144ba482204 |
| Verdict: | Malicious activity |
| Analysis date: | October 30, 2023, 15:08:13 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, Nullsoft Installer self-extracting archive |
| MD5: | DEC8EDA3A1AF6A8039987FE854A84A91 |
| SHA1: | B869A7C4F1F8E2CEEB9B248CCC41782F005B02A1 |
| SHA256: | B69AB416FA1C2DB43D9D4A900ABBF5E1AD6DAF0AB914AFCDFA74B25AF390747F |
| SSDEEP: | 24576:wihLOEdf7GOApNkiGz7CyNjP6xs1pBeNORUvL4nOTgr4EWl8DXfX8aGko77ISC4F:wiBOEdvvz7CyhgNrMn34ElXf0kxh4EW |
MALICIOUS
Drops the executable file immediately after the start
- SetupVCD5520.exe (PID: 2560)
- DevCon.exe (PID: 3884)
- nstFDB8.tmp (PID: 2996)
- drvinst.exe (PID: 3464)
- drvinst.exe (PID: 2472)
Application was dropped or rewritten from another process
- SetupVCD5520.exe (PID: 3836)
- nstFDB8.tmp (PID: 2996)
- SetupVCD5520.exe (PID: 2560)
- DevCon.exe (PID: 3884)
- SetRegACL.exe (PID: 4084)
- VCDDaemon.exe (PID: 2052)
- ExecuteWithUAC.exe (PID: 3196)
- ExecuteWithUAC.exe (PID: 2628)
- VCDDaemon.exe (PID: 1556)
- VCDPrefs.exe (PID: 4064)
- VCDPrefs.exe (PID: 3268)
- DevCon.exe (PID: 2680)
Creates a writable file the system directory
- nstFDB8.tmp (PID: 2996)
- drvinst.exe (PID: 2472)
- drvinst.exe (PID: 3464)
Loads dropped or rewritten executable
- nstFDB8.tmp (PID: 2996)
- VCDDaemon.exe (PID: 2052)
- VCDDaemon.exe (PID: 1556)
- VCDPrefs.exe (PID: 4064)
- VCDPrefs.exe (PID: 3268)
SUSPICIOUS
Starts itself from another location
- SetupVCD5520.exe (PID: 2560)
Starts application with an unusual extension
- SetupVCD5520.exe (PID: 2560)
The process creates files with name similar to system file names
- nstFDB8.tmp (PID: 2996)
Reads settings of System Certificates
- DevCon.exe (PID: 3884)
- rundll32.exe (PID: 3176)
Reads security settings of Internet Explorer
- DevCon.exe (PID: 3884)
Checks Windows Trust Settings
- DevCon.exe (PID: 3884)
- drvinst.exe (PID: 3464)
- drvinst.exe (PID: 2472)
- drvinst.exe (PID: 3472)
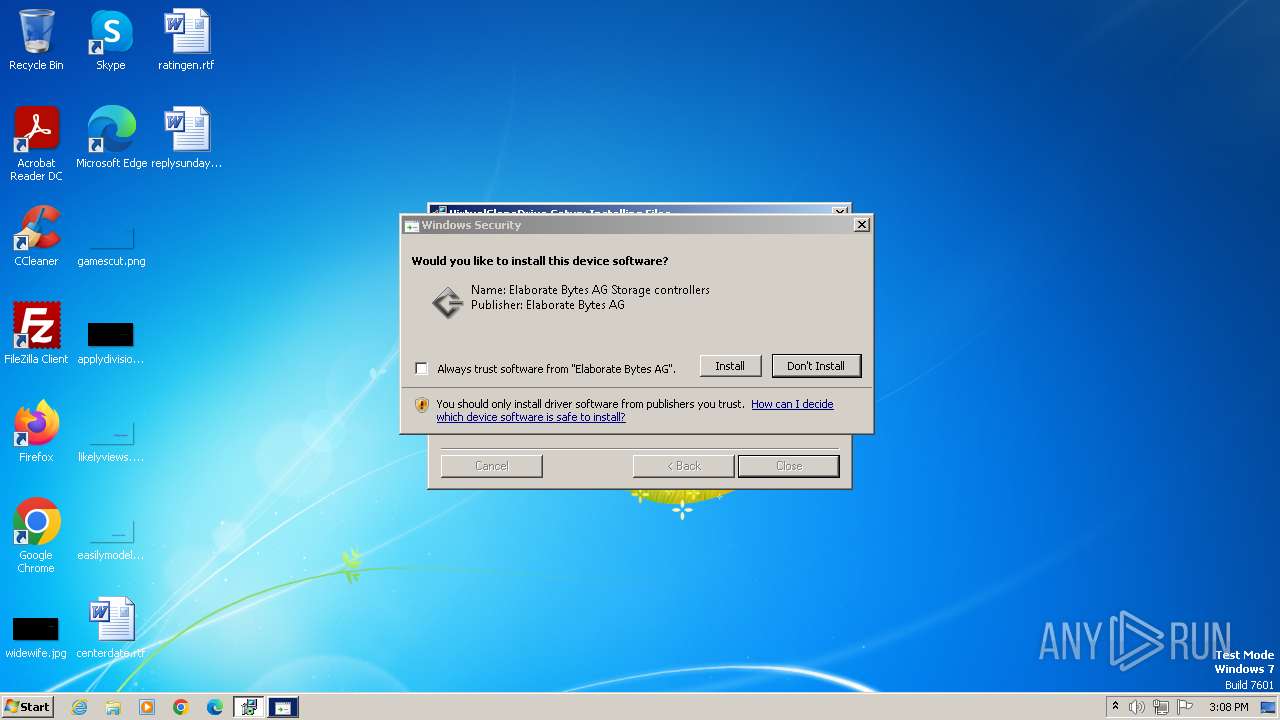
Drops a system driver (possible attempt to evade defenses)
- DevCon.exe (PID: 3884)
- drvinst.exe (PID: 3464)
- drvinst.exe (PID: 2472)
- nstFDB8.tmp (PID: 2996)
Creates files in the driver directory
- drvinst.exe (PID: 3464)
- drvinst.exe (PID: 2472)
- nstFDB8.tmp (PID: 2996)
Image mount is detect
- drvinst.exe (PID: 2472)
- drvinst.exe (PID: 3472)
- explorer.exe (PID: 1400)
Executes as Windows Service
- VSSVC.exe (PID: 3824)
The process executes via Task Scheduler
- ExecuteWithUAC.exe (PID: 2628)
INFO
Checks supported languages
- SetupVCD5520.exe (PID: 2560)
- nstFDB8.tmp (PID: 2996)
- DevCon.exe (PID: 2680)
- DevCon.exe (PID: 3884)
- drvinst.exe (PID: 2472)
- drvinst.exe (PID: 3472)
- VCDDaemon.exe (PID: 2052)
- SetRegACL.exe (PID: 4084)
- ExecuteWithUAC.exe (PID: 3196)
- ExecuteWithUAC.exe (PID: 2628)
- VCDDaemon.exe (PID: 1556)
- VCDPrefs.exe (PID: 3268)
- VCDPrefs.exe (PID: 4064)
- drvinst.exe (PID: 3464)
Create files in a temporary directory
- SetupVCD5520.exe (PID: 2560)
- nstFDB8.tmp (PID: 2996)
- DevCon.exe (PID: 3884)
Reads the computer name
- nstFDB8.tmp (PID: 2996)
- DevCon.exe (PID: 3884)
- drvinst.exe (PID: 3464)
- drvinst.exe (PID: 2472)
- VCDDaemon.exe (PID: 2052)
- drvinst.exe (PID: 3472)
- ExecuteWithUAC.exe (PID: 3196)
- VCDDaemon.exe (PID: 1556)
- VCDPrefs.exe (PID: 3268)
- VCDPrefs.exe (PID: 4064)
- DevCon.exe (PID: 2680)
Creates files in the program directory
- nstFDB8.tmp (PID: 2996)
Reads the machine GUID from the registry
- DevCon.exe (PID: 3884)
- drvinst.exe (PID: 3464)
- drvinst.exe (PID: 2472)
- drvinst.exe (PID: 3472)
- VCDDaemon.exe (PID: 1556)
Reads security settings of Internet Explorer
- rundll32.exe (PID: 3176)
Manual execution by a user
- VCDPrefs.exe (PID: 4064)
- VCDPrefs.exe (PID: 3268)
Process checks computer location settings
- drvinst.exe (PID: 3472)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | NSIS - Nullsoft Scriptable Install System (87.8) |
|---|---|---|
| .exe | | | InstallShield setup (4.4) |
| .exe | | | Win32 Executable MS Visual C++ (generic) (3.2) |
| .exe | | | Win64 Executable (generic) (2.8) |
| .dll | | | Win32 Dynamic Link Library (generic) (0.6) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2019:02:22 16:43:00+01:00 |
| ImageFileCharacteristics: | No relocs, Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 8 |
| CodeSize: | 59392 |
| InitializedDataSize: | 23040 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x9723 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
Total processes
65
Monitored processes
19
Malicious processes
14
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1400 | C:\Windows\Explorer.EXE | C:\Windows\explorer.exe | — | — | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1556 | "C:\Program Files\Elaborate Bytes\VirtualCloneDrive\VCDDaemon.exe" /s | C:\Program Files\Elaborate Bytes\VirtualCloneDrive\VCDDaemon.exe | — | ExecuteWithUAC.exe | |||||||||||
User: admin Company: Elaborate Bytes AG Integrity Level: MEDIUM Description: Virtual CloneDrive Daemon Exit code: 0 Version: 5.5.1.0 Modules
| |||||||||||||||
| 2052 | "C:\Program Files\Elaborate Bytes\VirtualCloneDrive\VCDDaemon.exe" /u | C:\Program Files\Elaborate Bytes\VirtualCloneDrive\VCDDaemon.exe | — | nstFDB8.tmp | |||||||||||
User: admin Company: Elaborate Bytes AG Integrity Level: HIGH Description: Virtual CloneDrive Daemon Exit code: 0 Version: 5.5.1.0 Modules
| |||||||||||||||
| 2472 | DrvInst.exe "2" "211" "ROOT\SCSIADAPTER\0000" "C:\Windows\INF\oem2.inf" "vclone.inf:Models:miniport:5.4.7.0:root\vclone" "64f288aa3" "000002BC" "000005DC" "000005E0" | C:\Windows\System32\drvinst.exe | — | svchost.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Driver Installation Module Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2560 | "C:\Users\admin\AppData\Local\Temp\SetupVCD5520.exe" | C:\Users\admin\AppData\Local\Temp\SetupVCD5520.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 2628 | "C:\Program Files\Elaborate Bytes\VirtualCloneDrive\ExecuteWithUAC.exe" /e | C:\Program Files\Elaborate Bytes\VirtualCloneDrive\ExecuteWithUAC.exe | — | taskeng.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: ElbyCDIO install helper process Exit code: 0 Version: 1, 0, 1, 1 Modules
| |||||||||||||||
| 2680 | "C:\Users\admin\AppData\Local\Temp\nstFE24.tmp\DevCon.exe" status "root\vclone" | C:\Users\admin\AppData\Local\Temp\nstFE24.tmp\DevCon.exe | — | nstFDB8.tmp | |||||||||||
User: admin Company: Windows (R) Codename Longhorn DDK provider Integrity Level: HIGH Description: Windows Setup API Exit code: 0 Version: 6.0.6001.18000 built by: WinDDK Modules
| |||||||||||||||
| 2996 | nstFDB8.tmp /DOIT | C:\Users\admin\AppData\Local\Temp\nstFDA7.tmp\nstFDB8.tmp | — | SetupVCD5520.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 3176 | rundll32.exe C:\Windows\system32\pnpui.dll,InstallSecurityPromptRunDllW 20 Global\{42117fd2-f306-56cd-b084-a1347fcbc534} Global\{25c5d455-e287-789f-aeea-2818ecd54b14} C:\Windows\System32\DriverStore\Temp\{1a670ef0-774b-28d0-2b81-6f70f3ce7659}\vclone.inf C:\Windows\System32\DriverStore\Temp\{1a670ef0-774b-28d0-2b81-6f70f3ce7659}\VClone.cat | C:\Windows\System32\rundll32.exe | — | drvinst.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3196 | "C:\Program Files\Elaborate Bytes\VirtualCloneDrive\ExecuteWithUAC.exe" /s | C:\Program Files\Elaborate Bytes\VirtualCloneDrive\ExecuteWithUAC.exe | — | nstFDB8.tmp | |||||||||||
User: admin Integrity Level: HIGH Description: ElbyCDIO install helper process Exit code: 0 Version: 1, 0, 1, 1 Modules
| |||||||||||||||
Total events
20 479
Read events
20 351
Write events
121
Delete events
7
Modification events
| (PID) Process: | (1400) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Action Center\Checks\{C8E6F269-B90A-4053-A3BE-499AFCEC98C4}.check.0 |
| Operation: | write | Name: | CheckSetting |
Value: 01000000D08C9DDF0115D1118C7A00C04FC297EB01000000F6D6788197A75D498472ACE88906AC8D0000000002000000000010660000000100002000000048832D3FD0459F35F292D4F0571B992C6EB9F500D4ED7BC3B99927FC5331D217000000000E80000000020000200000003EFBFF3AEC091353AF9E58D48DF2D06E9D1BDED94E4937159293C20E513DDF0F3000000087034FE3522EDDAC6E83C331CAE7E3CB92B187260C4DAD8D1C31F9039AB30BE9E56E6C6EE2A54DD7C0FCB3257D6FF55F4000000040B806FFF8B32ABD66EABA7F35A86503B0F300E1B9A976FC4B3F6328F133A31ACB461ADFC86BE84974CB3AD9119C225504F24589D1CDC1655DA54BABE9CEF265 | |||
| (PID) Process: | (1400) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\StartPage\NewShortcuts |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (1400) explorer.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\178\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2996) nstFDB8.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer |
| Operation: | write | Name: | GlobalAssocChangedCounter |
Value: 114 | |||
| (PID) Process: | (3884) DevCon.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\178\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3464) drvinst.exe | Key: | HKEY_USERS\.DEFAULT\Software\Classes\Local Settings\MuiCache\178\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3176) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\178\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3464) drvinst.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SystemRestore |
| Operation: | write | Name: | SrCreateRp (Enter) |
Value: 4000000000000000F2B487BA16B0D901C80700002C0A0000D5070000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3464) drvinst.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SPP |
| Operation: | write | Name: | SppCreate (Enter) |
Value: 4000000000000000F2B487BA16B0D901C80700002C0A0000D0070000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3464) drvinst.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\SPP |
| Operation: | write | Name: | LastIndex |
Value: 72 | |||
Executable files
30
Suspicious files
66
Text files
93
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2560 | SetupVCD5520.exe | C:\Users\admin\AppData\Local\Temp\nstFDA7.tmp\nstFDB8.tmp | executable | |
MD5:DEC8EDA3A1AF6A8039987FE854A84A91 | SHA256:B69AB416FA1C2DB43D9D4A900ABBF5E1AD6DAF0AB914AFCDFA74B25AF390747F | |||
| 2996 | nstFDB8.tmp | C:\Users\admin\AppData\Local\Temp\nstFE24.tmp\ExecuteWithUAC.exe | executable | |
MD5:549E70189FA7B3034A8E58A48CB353C0 | SHA256:BB23AC0440D9DE37D035E68895C53C559DF4F31C8D0905033AB40AD0A2910E77 | |||
| 2996 | nstFDB8.tmp | C:\Program Files\Elaborate Bytes\VirtualCloneDrive\ExecuteWithUAC.exe | executable | |
MD5:549E70189FA7B3034A8E58A48CB353C0 | SHA256:BB23AC0440D9DE37D035E68895C53C559DF4F31C8D0905033AB40AD0A2910E77 | |||
| 2996 | nstFDB8.tmp | C:\Program Files\Elaborate Bytes\VirtualCloneDrive\DevCon.exe | executable | |
MD5:DD1232788611EF3471281C702A2FE90A | SHA256:0B329EF478FE62CD4A52290D0D892DA1FBE322039CBF64D75C051C32CD4271C7 | |||
| 2996 | nstFDB8.tmp | C:\Users\admin\AppData\Local\Temp\nstFE24.tmp\InstallHelp.dll | executable | |
MD5:E7715D8590B80E295D9168B1CF168C34 | SHA256:B7AA5E64BF55719817E08718D99D509014585A4336426D46F6BDC91957D836C2 | |||
| 2996 | nstFDB8.tmp | C:\Program Files\Elaborate Bytes\VirtualCloneDrive\manual\de\images\drive_verify.gif | image | |
MD5:96D1362C40FCC24F59AC003D0313582A | SHA256:29CF712474D747FDDB059BD6794AF360A1EF38B9522A0CD962F520009D54A64B | |||
| 2996 | nstFDB8.tmp | C:\Program Files\Elaborate Bytes\VirtualCloneDrive\manual\de\images\drive_select.gif | image | |
MD5:F8477BFE5372BEB19302BE80275288E8 | SHA256:6741EBD69674A1CA090A35D2B29127BEA1165666C47E39AA134DC6065C3272F3 | |||
| 2996 | nstFDB8.tmp | C:\Program Files\Elaborate Bytes\VirtualCloneDrive\manual\de\images\drive_install.gif | image | |
MD5:8BB7C851F6DE7B6183E890C57F7BFF04 | SHA256:7645AEEB29280B511C5343C2D8966CD95671A2C5FAF0C3F2C9AF78879A71CB53 | |||
| 2996 | nstFDB8.tmp | C:\Program Files\Elaborate Bytes\VirtualCloneDrive\manual\changes_vcd.txt | text | |
MD5:561BA6EE30C115343F3D1D6263B0C10D | SHA256:52544A14AB1B7548D6DCE7BAC7AA0877CA2E8DA005384EE7DAEC89B44C52CC8D | |||
| 2996 | nstFDB8.tmp | C:\Program Files\Elaborate Bytes\VirtualCloneDrive\HelpLauncher.exe | executable | |
MD5:9881A7049383E3C402ACD33D33B6D8E7 | SHA256:88ED5539A9F8D68A8557AEFD59DC2B03F174CEACDA0CB491CB6F79260B613D3F | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
2
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |