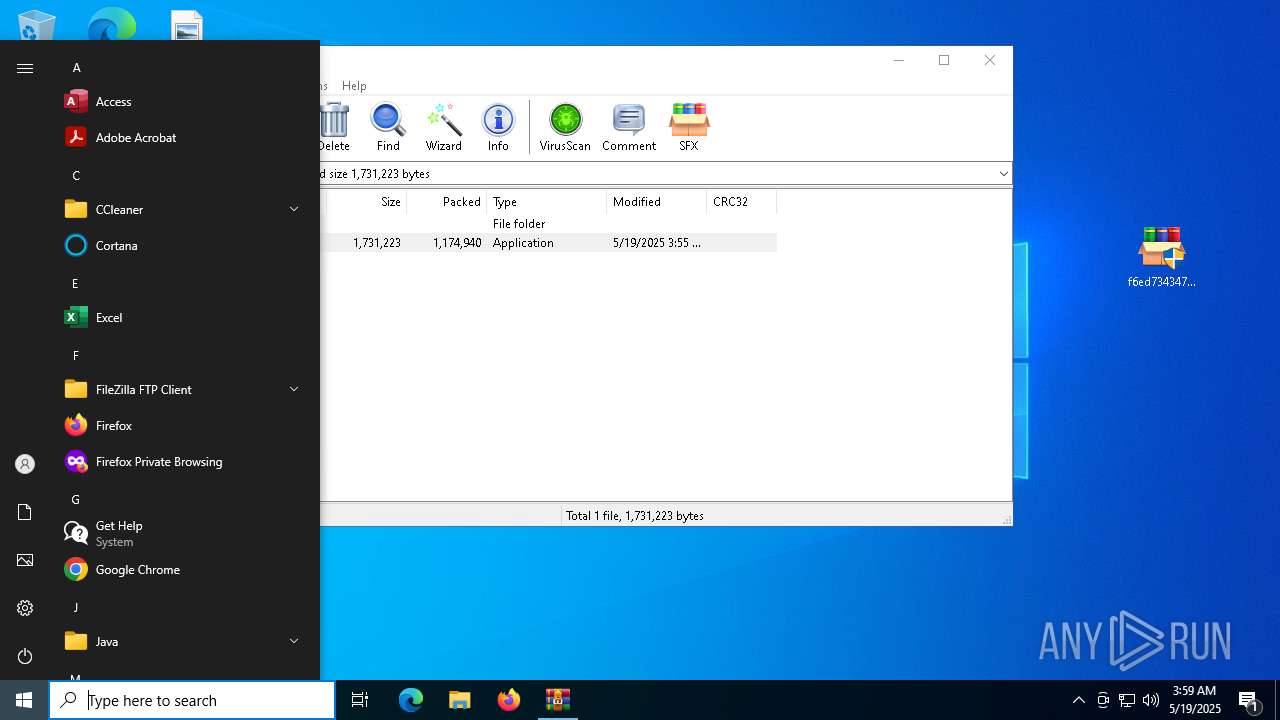
| File name: | DCRat.zip |
| Full analysis: | https://app.any.run/tasks/37209510-288c-454c-a2f5-98cb264740e3 |
| Verdict: | Malicious activity |
| Threats: | DCrat, also known as Dark Crystal RAT, is a remote access trojan (RAT), which was first introduced in 2018. It is a modular malware that can be customized to perform different tasks. For instance, it can steal passwords, crypto wallet information, hijack Telegram and Steam accounts, and more. Attackers may use a variety of methods to distribute DCrat, but phishing email campaigns are the most common. |
| Analysis date: | May 19, 2025, 03:57:36 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v5.1 to extract, compression method=AES Encrypted |
| MD5: | 6EE1A9CB1411EDB94792593A9C040993 |
| SHA1: | 2441E2FB0DA5CA217B4F290C3B17B536F3F59661 |
| SHA256: | B684FA6B84B1F6F96901B9A4E5A8A885F44C66D6F11D80CAD3B2EC351D632784 |
| SSDEEP: | 49152:RuyGgWgLVxb4dx0ji9gOnYTDHjmil7ZpZ1oHo7zKADZvtKt/Ii6fW1119Z6Shjpb:hGgWwV2dEi99Gjjzl7ZtSoX79vcRIrw1 |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 7328)
DCRAT has been detected (YARA)
- slui.exe (PID: 1276)
- dwm.exe (PID: 5332)
Uses sleep, probably for evasion detection (SCRIPT)
- wscript.exe (PID: 7440)
- wscript.exe (PID: 7192)
- wscript.exe (PID: 496)
UAC/LUA settings modification
- surrogatefontdriver.exe (PID: 5800)
- dwm.exe (PID: 5332)
DCRAT mutex has been found
- dwm.exe (PID: 5332)
SUSPICIOUS
Executable content was dropped or overwritten
- f6ed7343476246eb693d80b64bdc9b130af9c05dc260e907cc443c2be6693978.exe (PID: 4776)
- surrogatefontdriver.exe (PID: 5800)
- dwm.exe (PID: 5332)
- dwm.exe (PID: 4124)
Reads security settings of Internet Explorer
- f6ed7343476246eb693d80b64bdc9b130af9c05dc260e907cc443c2be6693978.exe (PID: 4776)
- ShellExperienceHost.exe (PID: 5640)
- surrogatefontdriver.exe (PID: 5800)
- dwm.exe (PID: 5332)
Starts CMD.EXE for commands execution
- wscript.exe (PID: 7440)
- surrogatefontdriver.exe (PID: 5800)
Executing commands from a ".bat" file
- wscript.exe (PID: 7440)
- surrogatefontdriver.exe (PID: 5800)
Runs shell command (SCRIPT)
- wscript.exe (PID: 7440)
Executed via WMI
- schtasks.exe (PID: 7696)
- schtasks.exe (PID: 6540)
- schtasks.exe (PID: 5552)
- schtasks.exe (PID: 7288)
- schtasks.exe (PID: 4428)
- schtasks.exe (PID: 1672)
- schtasks.exe (PID: 7276)
- schtasks.exe (PID: 7648)
- schtasks.exe (PID: 7720)
- schtasks.exe (PID: 7564)
- schtasks.exe (PID: 7736)
- schtasks.exe (PID: 7748)
- schtasks.exe (PID: 7840)
- schtasks.exe (PID: 4920)
- schtasks.exe (PID: 7836)
- schtasks.exe (PID: 2552)
- schtasks.exe (PID: 7816)
- schtasks.exe (PID: 7820)
- schtasks.exe (PID: 1388)
- schtasks.exe (PID: 2268)
- schtasks.exe (PID: 5984)
- schtasks.exe (PID: 5260)
- schtasks.exe (PID: 5436)
- schtasks.exe (PID: 6148)
- schtasks.exe (PID: 1912)
- schtasks.exe (PID: 5212)
- schtasks.exe (PID: 1300)
- schtasks.exe (PID: 4560)
- schtasks.exe (PID: 812)
- schtasks.exe (PID: 5048)
- schtasks.exe (PID: 7436)
- schtasks.exe (PID: 6564)
- schtasks.exe (PID: 968)
- schtasks.exe (PID: 684)
- schtasks.exe (PID: 3884)
- schtasks.exe (PID: 5244)
- schtasks.exe (PID: 5216)
- schtasks.exe (PID: 8056)
- schtasks.exe (PID: 8052)
- schtasks.exe (PID: 7996)
- schtasks.exe (PID: 2344)
- schtasks.exe (PID: 6660)
- schtasks.exe (PID: 7980)
- schtasks.exe (PID: 732)
- schtasks.exe (PID: 7560)
- schtasks.exe (PID: 7780)
- schtasks.exe (PID: 7316)
- schtasks.exe (PID: 2416)
- schtasks.exe (PID: 5364)
- schtasks.exe (PID: 7176)
- schtasks.exe (PID: 5232)
- schtasks.exe (PID: 1748)
- schtasks.exe (PID: 6208)
- schtasks.exe (PID: 5588)
The process creates files with name similar to system file names
- surrogatefontdriver.exe (PID: 5800)
Reads the date of Windows installation
- surrogatefontdriver.exe (PID: 5800)
- dwm.exe (PID: 5332)
Probably delay the execution using 'w32tm.exe'
- cmd.exe (PID: 1196)
The process executes VB scripts
- dwm.exe (PID: 5332)
- fontdrvhost.exe (PID: 2096)
- StartMenuExperienceHost.exe (PID: 4152)
- Memory Compression.exe (PID: 896)
- slui.exe (PID: 3044)
- SearchApp.exe (PID: 876)
- dllhost.exe (PID: 3964)
- csrss.exe (PID: 3012)
- conhost.exe (PID: 4100)
- surrogatefontdriver.exe (PID: 4144)
- dwm.exe (PID: 4124)
- UserOOBEBroker.exe (PID: 796)
- RuntimeBroker.exe (PID: 3612)
- sihost.exe (PID: 4108)
- spoolsv.exe (PID: 1636)
Creates FileSystem object to access computer's file system (SCRIPT)
- wscript.exe (PID: 7192)
- wscript.exe (PID: 496)
There is functionality for taking screenshot (YARA)
- dwm.exe (PID: 5332)
Uses WMI to retrieve WMI-managed resources (SCRIPT)
- wscript.exe (PID: 7192)
The process executes via Task Scheduler
- Memory Compression.exe (PID: 896)
- UserOOBEBroker.exe (PID: 796)
- PLUGScheduler.exe (PID: 2988)
- slui.exe (PID: 3044)
- csrss.exe (PID: 3012)
- spoolsv.exe (PID: 1636)
- dllhost.exe (PID: 3964)
- fontdrvhost.exe (PID: 2096)
- SearchApp.exe (PID: 876)
- surrogatefontdriver.exe (PID: 4144)
- conhost.exe (PID: 4100)
- sihost.exe (PID: 4108)
- dwm.exe (PID: 4124)
- StartMenuExperienceHost.exe (PID: 4152)
- RuntimeBroker.exe (PID: 3612)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 7328)
Reads the software policy settings
- slui.exe (PID: 7500)
Manual execution by a user
- f6ed7343476246eb693d80b64bdc9b130af9c05dc260e907cc443c2be6693978.exe (PID: 7152)
- f6ed7343476246eb693d80b64bdc9b130af9c05dc260e907cc443c2be6693978.exe (PID: 4776)
Reads the computer name
- f6ed7343476246eb693d80b64bdc9b130af9c05dc260e907cc443c2be6693978.exe (PID: 4776)
- surrogatefontdriver.exe (PID: 5800)
- ShellExperienceHost.exe (PID: 5640)
- dwm.exe (PID: 5332)
The sample compiled with english language support
- f6ed7343476246eb693d80b64bdc9b130af9c05dc260e907cc443c2be6693978.exe (PID: 4776)
- surrogatefontdriver.exe (PID: 5800)
- dwm.exe (PID: 5332)
- dwm.exe (PID: 4124)
Drops encrypted VBS script (Microsoft Script Encoder)
- f6ed7343476246eb693d80b64bdc9b130af9c05dc260e907cc443c2be6693978.exe (PID: 4776)
Checks supported languages
- f6ed7343476246eb693d80b64bdc9b130af9c05dc260e907cc443c2be6693978.exe (PID: 4776)
- surrogatefontdriver.exe (PID: 5800)
- ShellExperienceHost.exe (PID: 5640)
- dwm.exe (PID: 5332)
Process checks computer location settings
- f6ed7343476246eb693d80b64bdc9b130af9c05dc260e907cc443c2be6693978.exe (PID: 4776)
- surrogatefontdriver.exe (PID: 5800)
- dwm.exe (PID: 5332)
Reads Environment values
- surrogatefontdriver.exe (PID: 5800)
- dwm.exe (PID: 5332)
Reads the machine GUID from the registry
- surrogatefontdriver.exe (PID: 5800)
- dwm.exe (PID: 5332)
Process checks whether UAC notifications are on
- surrogatefontdriver.exe (PID: 5800)
- dwm.exe (PID: 5332)
Creates files in the program directory
- surrogatefontdriver.exe (PID: 5800)
Creates files or folders in the user directory
- surrogatefontdriver.exe (PID: 5800)
Create files in a temporary directory
- surrogatefontdriver.exe (PID: 5800)
- dwm.exe (PID: 5332)
Reads Microsoft Office registry keys
- dwm.exe (PID: 5332)
.NET Reactor protector has been detected
- dwm.exe (PID: 5332)
Found Base64 encoded access to Windows Defender via PowerShell (YARA)
- dwm.exe (PID: 5332)
Found Base64 encoded reference to AntiVirus WMI classes (YARA)
- dwm.exe (PID: 5332)
Found Base64 encoded reference to WMI classes (YARA)
- dwm.exe (PID: 5332)
Disables trace logs
- dwm.exe (PID: 5332)
Checks proxy server information
- dwm.exe (PID: 5332)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
DcRat
(PID) Process(5332) dwm.exe
C2 (1)http://a1127661.xsph.ru/ee9209f8
Options
MutexDCR_MUTEX-gmUAJxbXmouKblGJVVR7
searchpath%UsersFolder% - Fast
Targetals
C2 (1)http://a1127661.xsph.ru/ee9209f8
Options
MutexDCR_MUTEX-gmUAJxbXmouKblGJVVR7
Debugfalse
ServerConfigReplacementTable
1,
2^
4%
9@
H*
T(
V#
A<
J`
N|
C$
a>
o&
h_
n~
Z;
I!
U.
z)
L-
c
PluginConfigReplacementTable
0_
9#
U|
B.
Q>
E<
d-
h%
F`
e(
N!
W^
Y;
t@
H)
v*
L&
V$
l~
D
a,
GetWebcamsfalse
SleepTimeout5
InactivityTimeout2
CacheStorageRegistry
AutoRunSmart
StealerConfig
searchpath%UsersFolder% - Fast
StealerEnabledfalse
StealerOptionsfalse
SelfDeletefalse
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 51 |
|---|---|
| ZipBitFlag: | 0x0003 |
| ZipCompression: | Unknown (99) |
| ZipModifyDate: | 2025:05:19 03:55:24 |
| ZipCRC: | 0xd917b969 |
| ZipCompressedSize: | 1174940 |
| ZipUncompressedSize: | 1731223 |
| ZipFileName: | f6ed7343476246eb693d80b64bdc9b130af9c05dc260e907cc443c2be6693978.exe |
Total processes
412
Monitored processes
130
Malicious processes
8
Suspicious processes
15
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 468 | C:\found.000\dir_00000002.chk\dllhost.exe | C:\found.000\dir_00000002.chk\dllhost.exe | — | wscript.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Version: 5.15.2.0 Modules
| |||||||||||||||
| 496 | "C:\WINDOWS\System32\WScript.exe" "C:\Users\admin\AppData\Local\Temp\b359e3fb-e66a-4e9b-9609-810891d0d532.vbs" | C:\Windows\System32\wscript.exe | — | dwm.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft ® Windows Based Script Host Exit code: 1073807364 Version: 5.812.10240.16384 Modules
| |||||||||||||||
| 672 | C:\Users\admin\surrogatefontdriver.exe | C:\Users\admin\surrogatefontdriver.exe | — | wscript.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Version: 5.15.2.0 Modules
| |||||||||||||||
| 684 | schtasks.exe /create /tn "RuntimeBroker" /sc ONLOGON /tr "'C:\Program Files (x86)\Windows NT\Accessories\en-US\RuntimeBroker.exe'" /rl HIGHEST /f | C:\Windows\System32\schtasks.exe | — | WmiPrvSE.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Task Scheduler Configuration Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 720 | "C:\Program Files\Java\jre1.8.0_271\legal\jdk\csrss.exe" | C:\Program Files\Java\jre1.8.0_271\legal\jdk\csrss.exe | — | wscript.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Version: 5.15.2.0 Modules
| |||||||||||||||
| 732 | schtasks.exe /create /tn "sihost" /sc ONLOGON /tr "'C:\Users\admin\AppData\Local\D3DSCache\f4d41c5d09ae781\sihost.exe'" /rl HIGHEST /f | C:\Windows\System32\schtasks.exe | — | WmiPrvSE.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Task Scheduler Configuration Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 796 | "C:\Users\Administrator\Templates\UserOOBEBroker.exe" | C:\Users\Administrator\AppData\Roaming\Microsoft\Windows\Templates\UserOOBEBroker.exe | svchost.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Version: 5.15.2.0 Modules
| |||||||||||||||
| 812 | schtasks.exe /create /tn "surrogatefontdrivers" /sc MINUTE /mo 11 /tr "'C:\Users\admin\surrogatefontdriver.exe'" /rl HIGHEST /f | C:\Windows\System32\schtasks.exe | — | WmiPrvSE.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Task Scheduler Configuration Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 876 | "C:\Program Files (x86)\Mozilla Maintenance Service\SearchApp.exe" | C:\Program Files (x86)\Mozilla Maintenance Service\SearchApp.exe | svchost.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Version: 5.15.2.0 Modules
| |||||||||||||||
| 896 | "C:\Program Files (x86)\Opera\Memory Compression.exe" | C:\Program Files (x86)\Opera\Memory Compression.exe | svchost.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Version: 5.15.2.0 Modules
| |||||||||||||||
Total events
60 370
Read events
60 078
Write events
292
Delete events
0
Modification events
| (PID) Process: | (7328) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (7328) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (7328) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (7328) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\DCRat.zip | |||
| (PID) Process: | (7328) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (7328) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (7328) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (7328) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (7328) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 1 | |||
| (PID) Process: | (4776) f6ed7343476246eb693d80b64bdc9b130af9c05dc260e907cc443c2be6693978.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.vbe\OpenWithProgids |
| Operation: | write | Name: | VBEFile |
Value: | |||
Executable files
22
Suspicious files
45
Text files
51
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5800 | surrogatefontdriver.exe | C:\Users\Default\6cb0b6c459d5d3 | text | |
MD5:016BB8CCE21358D696D53B3B9E0D2F10 | SHA256:E036C941FE9E214A7A1CA2AC9E849A2754BD49EE9BC9AF1018F56DC5806F5664 | |||
| 4776 | f6ed7343476246eb693d80b64bdc9b130af9c05dc260e907cc443c2be6693978.exe | C:\hyperportServerWinnet\9j1iqp4X9tBF.bat | text | |
MD5:00C7EAC512963C3F70C5505F36B00AC6 | SHA256:67AD37B17C0405F599B55F429650BB37EF51B5FEEDC3AC8628CC8EC3CFB0C36F | |||
| 5800 | surrogatefontdriver.exe | C:\Windows\UpdateAssistantV2\6cb0b6c459d5d3 | text | |
MD5:4DF0349C915154BDD44DB6388822BC5E | SHA256:4019B8FD9DEE7BD4A9515102E230908A0697F4D81547003796BA8B6992DC08AB | |||
| 5800 | surrogatefontdriver.exe | C:\Users\Default\dwm.exe | executable | |
MD5:EBBCB7148CFDE980E845500CAD4C1A22 | SHA256:E766E9AAE6AEA105E78D0B211CF850C6340D3845E4F045260D5480F3A8256BC7 | |||
| 5800 | surrogatefontdriver.exe | C:\found.000\dir_00000002.chk\surrogatefontdriver.exe | executable | |
MD5:EBBCB7148CFDE980E845500CAD4C1A22 | SHA256:E766E9AAE6AEA105E78D0B211CF850C6340D3845E4F045260D5480F3A8256BC7 | |||
| 5800 | surrogatefontdriver.exe | C:\hyperportServerWinnet\088424020bedd6 | text | |
MD5:4F4548471C32DE5BF8F28C929AD6AE25 | SHA256:B4DCCA6A4BA06A2752CDC395319546C7C428C4DCF51FD1DD972C2F33C040F8F0 | |||
| 7328 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb7328.38796\f6ed7343476246eb693d80b64bdc9b130af9c05dc260e907cc443c2be6693978.exe | executable | |
MD5:17761EEFD75C92D5CE4B44A14F3C22FA | SHA256:F6ED7343476246EB693D80B64BDC9B130AF9C05DC260E907CC443C2BE6693978 | |||
| 5800 | surrogatefontdriver.exe | C:\Windows\UpdateAssistantV2\dwm.exe | executable | |
MD5:EBBCB7148CFDE980E845500CAD4C1A22 | SHA256:E766E9AAE6AEA105E78D0B211CF850C6340D3845E4F045260D5480F3A8256BC7 | |||
| 4776 | f6ed7343476246eb693d80b64bdc9b130af9c05dc260e907cc443c2be6693978.exe | C:\hyperportServerWinnet\YSYS1Ysf3wjZIjI26iuTC.vbe | binary | |
MD5:E95DEFBBCE436ADDEDCAE54C91E9A7D5 | SHA256:1436F672CCEE99B4648DF17AB83083FED80ADBD6491E576DA79D76C7ED662214 | |||
| 5800 | surrogatefontdriver.exe | C:\Program Files (x86)\Mozilla Maintenance Service\SearchApp.exe | executable | |
MD5:EBBCB7148CFDE980E845500CAD4C1A22 | SHA256:E766E9AAE6AEA105E78D0B211CF850C6340D3845E4F045260D5480F3A8256BC7 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
10
TCP/UDP connections
81
DNS requests
38
Threats
4
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 2.20.245.139:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
8024 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
8024 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
5520 | SearchApp.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
5520 | SearchApp.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEApDqVCbATUviZV57HIIulA%3D | unknown | — | — | whitelisted |
7720 | SystemSettings.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
7720 | SystemSettings.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
5520 | SearchApp.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2104 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 2.20.245.139:80 | crl.microsoft.com | Akamai International B.V. | SE | whitelisted |
— | — | 2.23.246.101:80 | www.microsoft.com | Ooredoo Q.S.C. | QA | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2112 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3216 | svchost.exe | 172.211.123.248:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 40.126.31.73:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6544 | svchost.exe | 2.23.77.188:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2196 | svchost.exe | A Network Trojan was detected | MALWARE [ANY.RUN] Suspected domain Associated with Malware Distribution (xsph .ru) |
2196 | svchost.exe | Misc activity | ET INFO Observed DNS Query to xsph .ru Domain |
2168 | svchost.exe | A Network Trojan was detected | MALWARE [ANY.RUN] Suspected domain Associated with Malware Distribution (xsph .ru) |
2168 | svchost.exe | Misc activity | ET INFO Observed DNS Query to xsph .ru Domain |